| File name: | tester24.exe |
| Full analysis: | https://app.any.run/tasks/2798fcfa-e18a-449c-b16f-422f7440d306 |
| Verdict: | Malicious activity |
| Analysis date: | June 22, 2025, 09:04:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | D6523A9E76765E2CA19B6C4BF90F1537 |
| SHA1: | 470FFA8636DFCCABF5A9CEDD8D897676F19ADB34 |
| SHA256: | 950AA0E3E3F8C7784A72FFE9590E8B37240CF41DE147D48276B783A4F079FC69 |
| SSDEEP: | 98304:0C3CpAEVpbKQdLKbLylu/ZUmTv4I9XLDbenkuA83wpYp2tw9v4MWn7cBU4+rWbO2:R2dS881mwmNuEM491+jg |
MALICIOUS
Disables task manager
- reg.exe (PID: 2464)
Disables Windows Defender
- reg.exe (PID: 4768)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 4088)
Changes the autorun value in the registry
- reg.exe (PID: 6900)
Antivirus name has been found in the command line (generic signature)
- sfc.exe (PID: 5732)
SUSPICIOUS
Process drops legitimate windows executable
- tester24.exe (PID: 2148)
Loads Python modules
- tester24.exe (PID: 4172)
Process drops python dynamic module
- tester24.exe (PID: 2148)
Executable content was dropped or overwritten
- tester24.exe (PID: 2148)
The process drops C-runtime libraries
- tester24.exe (PID: 2148)
Application launched itself
- tester24.exe (PID: 2148)
- ClipUp.exe (PID: 1472)
- cmd.exe (PID: 7432)
- cmd.exe (PID: 6896)
- cmd.exe (PID: 9812)
- cmd.exe (PID: 536)
Starts CMD.EXE for commands execution
- tester24.exe (PID: 4172)
- cmd.exe (PID: 7432)
- cmd.exe (PID: 6896)
- cmd.exe (PID: 9812)
- cmd.exe (PID: 536)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2132)
- cmd.exe (PID: 3788)
- cmd.exe (PID: 6344)
- cmd.exe (PID: 4868)
- cmd.exe (PID: 5124)
- cmd.exe (PID: 6756)
- cmd.exe (PID: 6636)
- cmd.exe (PID: 3584)
- cmd.exe (PID: 1700)
- cmd.exe (PID: 1352)
- cmd.exe (PID: 5532)
- cmd.exe (PID: 3672)
- cmd.exe (PID: 3644)
Changes the desktop background image
- reg.exe (PID: 2368)
- reg.exe (PID: 1192)
- reg.exe (PID: 4824)
- reg.exe (PID: 2216)
- reg.exe (PID: 4768)
- reg.exe (PID: 6220)
- explorer.exe (PID: 7404)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 7076)
- cmd.exe (PID: 4192)
Found strings related to reading or modifying Windows Defender settings
- tester24.exe (PID: 4172)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6656)
- tester24.exe (PID: 4172)
Reads security settings of Internet Explorer
- tester24.exe (PID: 4172)
- StartMenuExperienceHost.exe (PID: 2220)
- StartMenuExperienceHost.exe (PID: 8928)
- wmplayer.exe (PID: 1720)
Executes as Windows Service
- dllhost.exe (PID: 3668)
- msdtc.exe (PID: 1488)
- FXSSVC.exe (PID: 5396)
- VSSVC.exe (PID: 9764)
Reads the date of Windows installation
- tester24.exe (PID: 4172)
- StartMenuExperienceHost.exe (PID: 2220)
- StartMenuExperienceHost.exe (PID: 8928)
- SearchApp.exe (PID: 5156)
Process uses IPCONFIG to get network configuration information
- tester24.exe (PID: 4172)
There is functionality for taking screenshot (YARA)
- tester24.exe (PID: 2148)
- tester24.exe (PID: 4172)
The process executes via Task Scheduler
- ShellAppRuntime.exe (PID: 2228)
- explorer.exe (PID: 7404)
Uses QWINSTA.EXE to read information about user sessions on remote desktops
- tester24.exe (PID: 4172)
Write to the desktop.ini file (may be used to cloak folders)
- WFS.exe (PID: 7396)
The process exported the data from the registry
- WSCollect.exe (PID: 8160)
Executes application which crashes
- WWAHost.exe (PID: 6364)
- WWAHost.exe (PID: 8540)
- MoUsoCoreWorker.exe (PID: 8928)
- WpcMon.exe (PID: 10564)
The process creates files with name similar to system file names
- WerFault.exe (PID: 2296)
- WerFault.exe (PID: 8568)
Creates file in the systems drive root
- bootcfg.exe (PID: 8476)
Detected use of alternative data streams (AltDS)
- WFS.exe (PID: 7396)
Uses TIMEOUT.EXE to delay execution
- tester24.exe (PID: 4172)
Process copies executable file
- tester24.exe (PID: 4172)
Reads Internet Explorer settings
- mmc.exe (PID: 10120)
Reads Microsoft Outlook installation path
- mmc.exe (PID: 10120)
The process checks if it is being run in the virtual environment
- mmc.exe (PID: 10120)
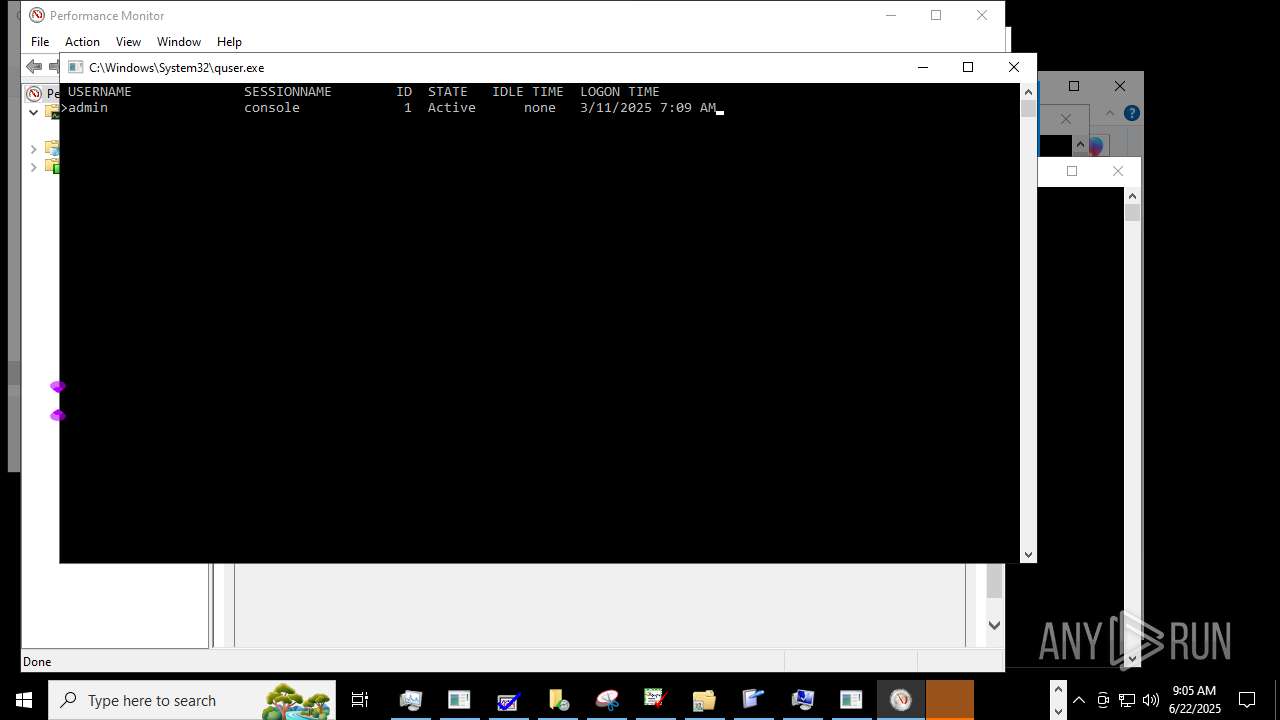
Uses QUSER.EXE to read information about current user sessions
- tester24.exe (PID: 4172)
Uses NLTEST.EXE to test domain trust
- tester24.exe (PID: 4172)
Uses ICACLS.EXE to modify access control lists
- tester24.exe (PID: 4172)
SQL CE related mutex has been found
- unregmp2.exe (PID: 8288)
INFO
Checks supported languages
- tester24.exe (PID: 2148)
- tester24.exe (PID: 4172)
- TpmTool.exe (PID: 1148)
- StartMenuExperienceHost.exe (PID: 2220)
- SearchApp.exe (PID: 5668)
- TextInputHost.exe (PID: 8012)
- EoAExperiences.exe (PID: 7472)
- StartMenuExperienceHost.exe (PID: 8928)
- tpmvscmgrsvr.exe (PID: 6016)
- SearchApp.exe (PID: 5156)
- perfmon.exe (PID: 2728)
- agentactivationruntimestarter.exe (PID: 10084)
- tpmvscmgrsvr.exe (PID: 9672)
- EoAExperiences.exe (PID: 6528)
- setup_wm.exe (PID: 8236)
- wmplayer.exe (PID: 1720)
The sample compiled with english language support
- tester24.exe (PID: 2148)
Create files in a temporary directory
- tester24.exe (PID: 2148)
- ClipUp.exe (PID: 5676)
- ddodiag.exe (PID: 4236)
- WSCollect.exe (PID: 8160)
- WFS.exe (PID: 7396)
- reg.exe (PID: 7700)
- reg.exe (PID: 7772)
- unregmp2.exe (PID: 11156)
Launching a file from a Registry key
- reg.exe (PID: 6900)
Reads the computer name
- tester24.exe (PID: 4172)
- tester24.exe (PID: 2148)
- SearchApp.exe (PID: 5668)
- TextInputHost.exe (PID: 8012)
- EoAExperiences.exe (PID: 7472)
- StartMenuExperienceHost.exe (PID: 2220)
- StartMenuExperienceHost.exe (PID: 8928)
- SearchApp.exe (PID: 5156)
- agentactivationruntimestarter.exe (PID: 10084)
- tpmvscmgrsvr.exe (PID: 9672)
- setup_wm.exe (PID: 8236)
- wmplayer.exe (PID: 1720)
- tpmvscmgrsvr.exe (PID: 6016)
Process checks computer location settings
- tester24.exe (PID: 4172)
- StartMenuExperienceHost.exe (PID: 2220)
- SearchApp.exe (PID: 5668)
- SearchApp.exe (PID: 5156)
- StartMenuExperienceHost.exe (PID: 8928)
- setup_wm.exe (PID: 8236)
- wmplayer.exe (PID: 1720)
Creates files in the program directory
- RMActivate_ssp_isv.exe (PID: 1472)
- FXSSVC.exe (PID: 5396)
- wermgr.exe (PID: 8428)
- mmc.exe (PID: 8360)
- DTUHandler.exe (PID: 5688)
- mmc.exe (PID: 10384)
- unregmp2.exe (PID: 8288)
- mmc.exe (PID: 8652)
Disables trace logs
- rasphone.exe (PID: 3652)
- FXSSVC.exe (PID: 5396)
- cmdl32.exe (PID: 8424)
- rasphone.exe (PID: 9988)
Checks transactions between databases Windows and Oracle
- dllhost.exe (PID: 3668)
- msdtc.exe (PID: 1488)
- mtstocom.exe (PID: 6172)
- UserAccountControlSettings.exe (PID: 504)
- mmc.exe (PID: 10384)
Reads security settings of Internet Explorer
- verifier.exe (PID: 7076)
- ComputerDefaults.exe (PID: 4088)
- FileHistory.exe (PID: 2292)
- certreq.exe (PID: 2756)
- LaunchTM.exe (PID: 7744)
- explorer.exe (PID: 7404)
- CompMgmtLauncher.exe (PID: 8380)
- mmc.exe (PID: 8360)
- mmc.exe (PID: 10120)
- CompMgmtLauncher.exe (PID: 6956)
- mmc.exe (PID: 10384)
- unregmp2.exe (PID: 11156)
- mmc.exe (PID: 8652)
Creates files or folders in the user directory
- RMActivate_isv.exe (PID: 4832)
- WerFault.exe (PID: 2296)
- WerFault.exe (PID: 9052)
- WerFault.exe (PID: 8568)
- explorer.exe (PID: 7404)
- mmc.exe (PID: 10120)
- WerFault.exe (PID: 10636)
- unregmp2.exe (PID: 8288)
Checks proxy server information
- SearchApp.exe (PID: 5668)
- WerFault.exe (PID: 8568)
- WerFault.exe (PID: 9052)
- SearchApp.exe (PID: 5156)
- explorer.exe (PID: 7404)
- mmc.exe (PID: 10120)
- WerFault.exe (PID: 2296)
- WerFault.exe (PID: 10636)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5668)
- SearchApp.exe (PID: 5156)
Reads the software policy settings
- SearchApp.exe (PID: 5668)
- WerFault.exe (PID: 2296)
- WerFault.exe (PID: 9052)
- WerFault.exe (PID: 8568)
- SearchApp.exe (PID: 5156)
- WerFault.exe (PID: 10636)
Reads Environment values
- SearchApp.exe (PID: 5668)
- SearchApp.exe (PID: 5156)
PyInstaller has been detected (YARA)
- tester24.exe (PID: 4172)
- tester24.exe (PID: 2148)
Encodes the UEFI Secure Boot certificates
- SecureBootEncodeUEFI.exe (PID: 9292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:22 08:58:14+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 174592 |
| InitializedDataSize: | 157184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd0d0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
632
Monitored processes
468
Malicious processes
6
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | "C:\Windows\System32\proquota.exe" | C:\Windows\System32\proquota.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ProQuota Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 480 | "C:\Windows\System32\UpgradeSubscription.exe" | C:\Windows\System32\UpgradeSubscription.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Upgrade to Subscription tool Exit code: 0 Version: 10.0.14393.0 (rs1_release.160715-1616) Modules
| |||||||||||||||
| 504 | "C:\Users\admin\Desktop\tester24.exe" | C:\Users\admin\Desktop\tester24.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RMActivate_ssp_isv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 504 | "C:\Windows\System32\UserAccountControlSettings.exe" | C:\Windows\System32\UserAccountControlSettings.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: UserAccountControlSettings Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | "C:\Windows\System32\wuauclt.exe" | C:\Windows\System32\wuauclt.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Update Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | C:\WINDOWS\system32\cmd.exe /c start | C:\Windows\System32\cmd.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | "C:\Windows\System32\secinit.exe" | C:\Windows\System32\secinit.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Security Init Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters ,1 ,True | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 984 | "C:\Windows\System32\TapiUnattend.exe" | C:\Windows\System32\TapiUnattend.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows(TM) Telephony Unattend Action Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
116 125
Read events
115 110
Write events
813
Delete events
202
Modification events
| (PID) Process: | (2368) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | WallpaperStyle |
Value: 0 | |||
| (PID) Process: | (1192) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: | |||
| (PID) Process: | (3480) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Colors |
| Operation: | write | Name: | Background |
Value: 0 0 0 | |||
| (PID) Process: | (4768) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (3668) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | TileWallpaper |
Value: 0 | |||
| (PID) Process: | (2464) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (4824) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop |
| Operation: | write | Name: | NoChangingWallPaper |
Value: 1 | |||
| (PID) Process: | (6900) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Tester24 |
Value: tester24.exe | |||
| (PID) Process: | (2216) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop |
| Operation: | write | Name: | NoChangingWallpaper |
Value: 1 | |||
| (PID) Process: | (6220) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | Wallpaper |
Value: | |||
Executable files
60
Suspicious files
80
Text files
54
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2148 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI21482\_ctypes.pyd | executable | |
MD5:429CB0177D5AB205F289D0CC830549FF | SHA256:6E804ED42CCA2EB401A896FE9542201D4D77DF22ACBD935A3C56DC68530DAE33 | |||
| 2148 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI21482\_bz2.pyd | executable | |
MD5:51CA0713F8FD5F142625A44DF7ED7100 | SHA256:8768315B1E0E81CCD0D96C3D6A863803F5DD1DE6AF849285C439D61ABD32B647 | |||
| 2148 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI21482\_decimal.pyd | executable | |
MD5:584652F877074FE71D7B1F8EEA1F849E | SHA256:E0F93185CD64F1DB3B9D1D20D620A691C5C453094B14D3B2BA2837F908F13304 | |||
| 2148 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI21482\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:9F746F4F7D845F063FEA3C37DCEBC27C | SHA256:88ACE577A9C51061CB7D1A36BABBBEFA48212FADC838FFDE98FDFFF60DE18386 | |||
| 2148 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI21482\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
| 2148 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI21482\_socket.pyd | executable | |
MD5:1AD8628499A107382153348A14A1DFC7 | SHA256:7A20FE96274F554CC527C65F42A8DE9CF0C201852BEDDDC12E44D9106BAB728F | |||
| 2148 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI21482\_hashlib.pyd | executable | |
MD5:692837EB1FCB73EF33A1474B18DFC7CD | SHA256:D674D53F7E2F906FBAF0D19AB871F9CFF53956D40B3CE003A2B4B44B549D4B92 | |||
| 2148 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI21482\_lzma.pyd | executable | |
MD5:0D549F688E0B2424B549AFCAC58D5FA7 | SHA256:80DF30ED0F2C532C07EA7FDC44836E40A8EBD9E7611365A1A26989147E1A4210 | |||
| 2148 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI21482\api-ms-win-core-kernel32-legacy-l1-1-1.dll | executable | |
MD5:0C1CC0A54D4B38885E1B250B40A34A84 | SHA256:A9B13A1CD1B8C19B0C6B4AFCD5BB0DD29C0E2288231AC9E6DB8510094CE68BA6 | |||
| 2148 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI21482\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:8F8EB9CB9E78E3A611BC8ACAEC4399CB | SHA256:1BD81DFD19204B44662510D9054852FB77C9F25C1088D647881C9B976CC16818 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
79
TCP/UDP connections
46
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6356 | RUXIMICS.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6356 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.201:443 | https://www.bing.com/rb/16/jnc,nj/-M-8YWX0KlEtdAHVrkTvKQHOghs.js?bu=Dicwe4sBkgGVAYgBgQGFAcABwwEwuAHGAQ&or=w | unknown | binary | 22.0 Kb | whitelisted |
— | — | GET | 200 | 2.16.241.205:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Init | unknown | html | 129 Kb | whitelisted |
— | — | POST | 204 | 2.16.241.218:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.205:443 | https://www.bing.com/rb/19/cir3,ortl,cc,nc/FgBbpIj0thGWZOh_xFnM9i4O7ek.css?bu=C8YL-ASFBpYM_wrpCt0IaWlpaQ&or=w | unknown | text | 19.8 Kb | whitelisted |
— | — | GET | 200 | 2.16.241.201:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | binary | 21.3 Kb | whitelisted |
— | — | GET | 200 | 2.16.241.218:443 | https://www.bing.com/manifest/threshold.appcache | unknown | text | 3.09 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6356 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6356 | RUXIMICS.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6356 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
win1910.ipv6.microsoft.com |
| whitelisted |
pnrpv2.ipv6.microsoft.com |
| whitelisted |
pnrpv21.ipv6.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Dism.exe | PID=8260 TID=8264 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=8260 TID=8264 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=8260 TID=8264 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
Dism.exe | PID=8260 TID=8264 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=8260 TID=8264 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=8260 TID=8264 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=8260 TID=8264 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=8260 TID=8264 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
Dism.exe | PID=8260 TID=8264 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|