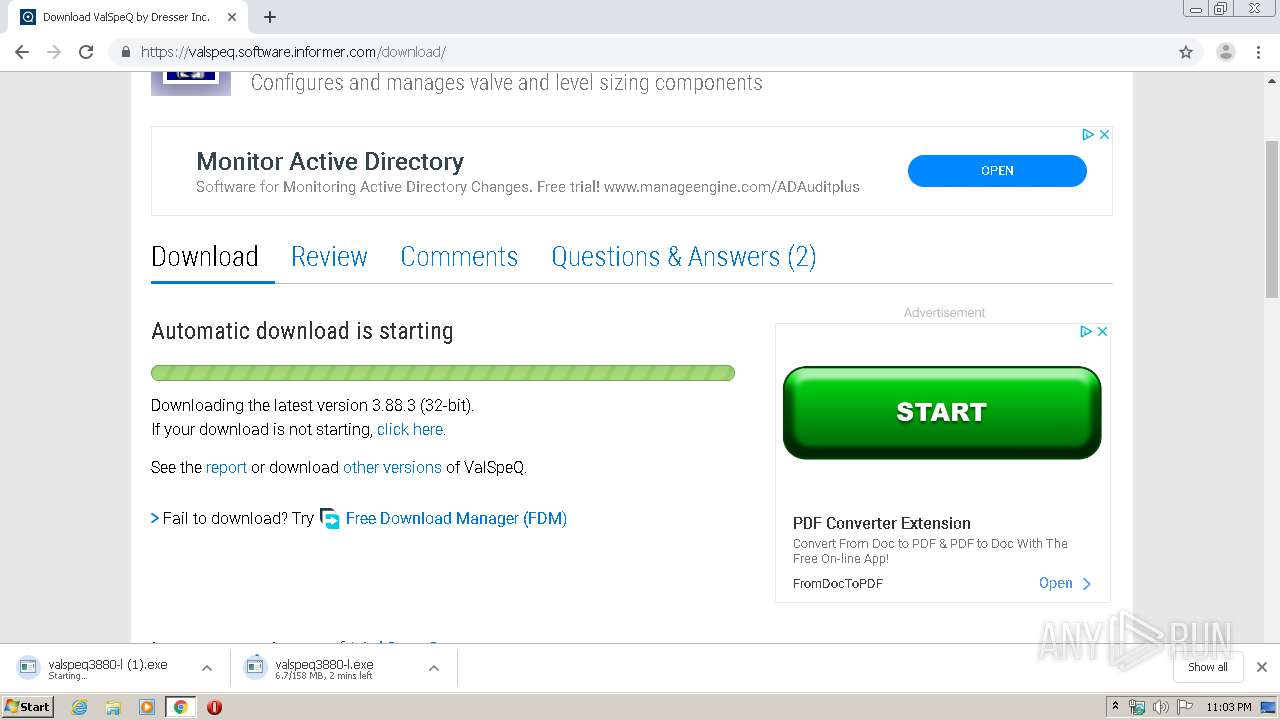
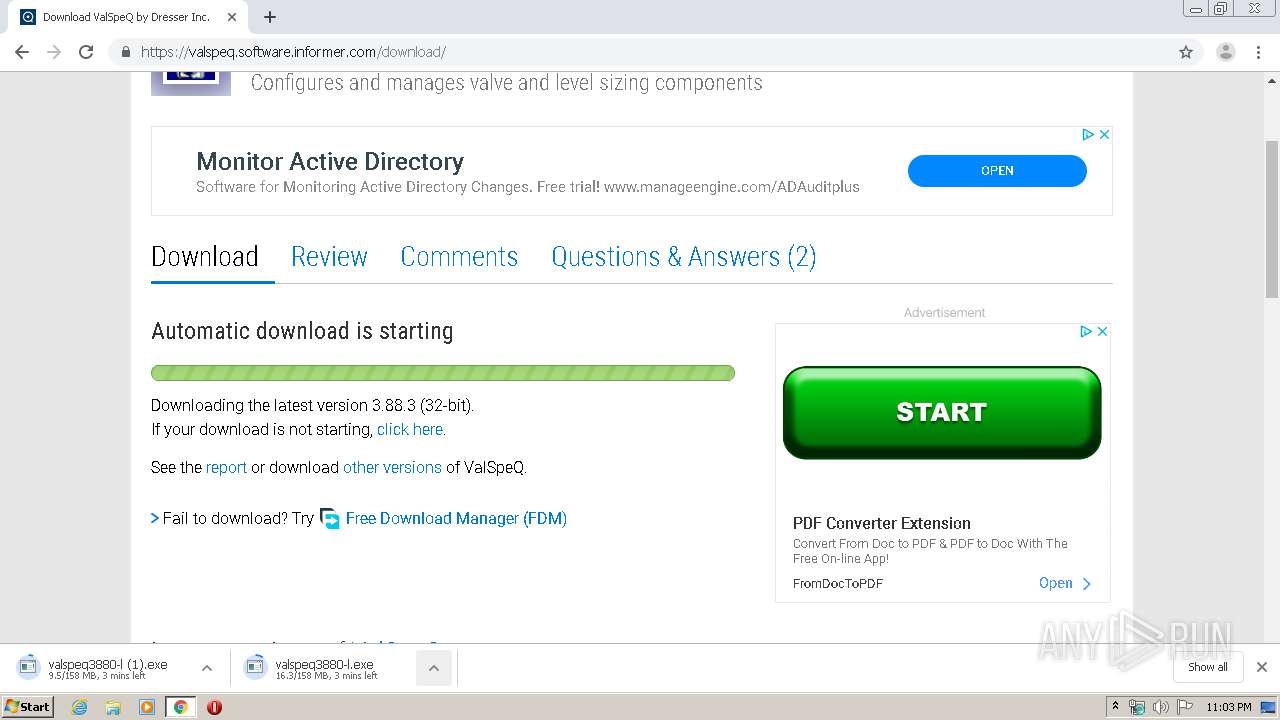
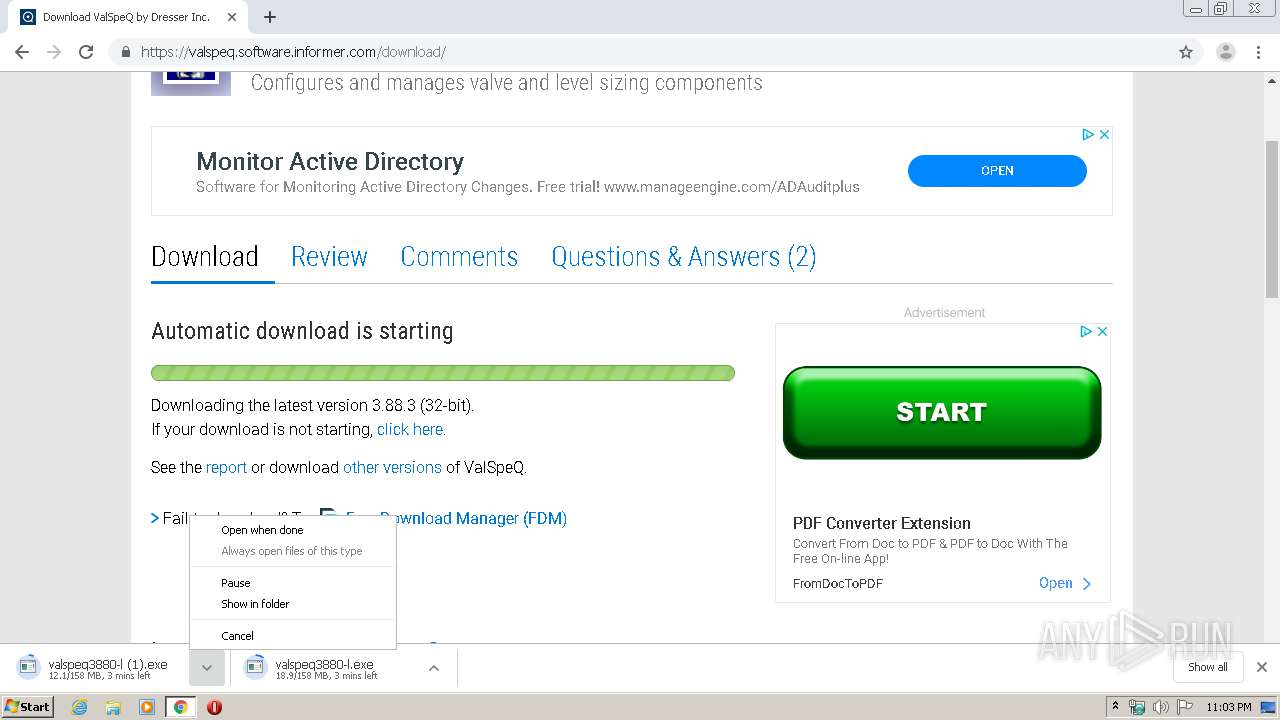
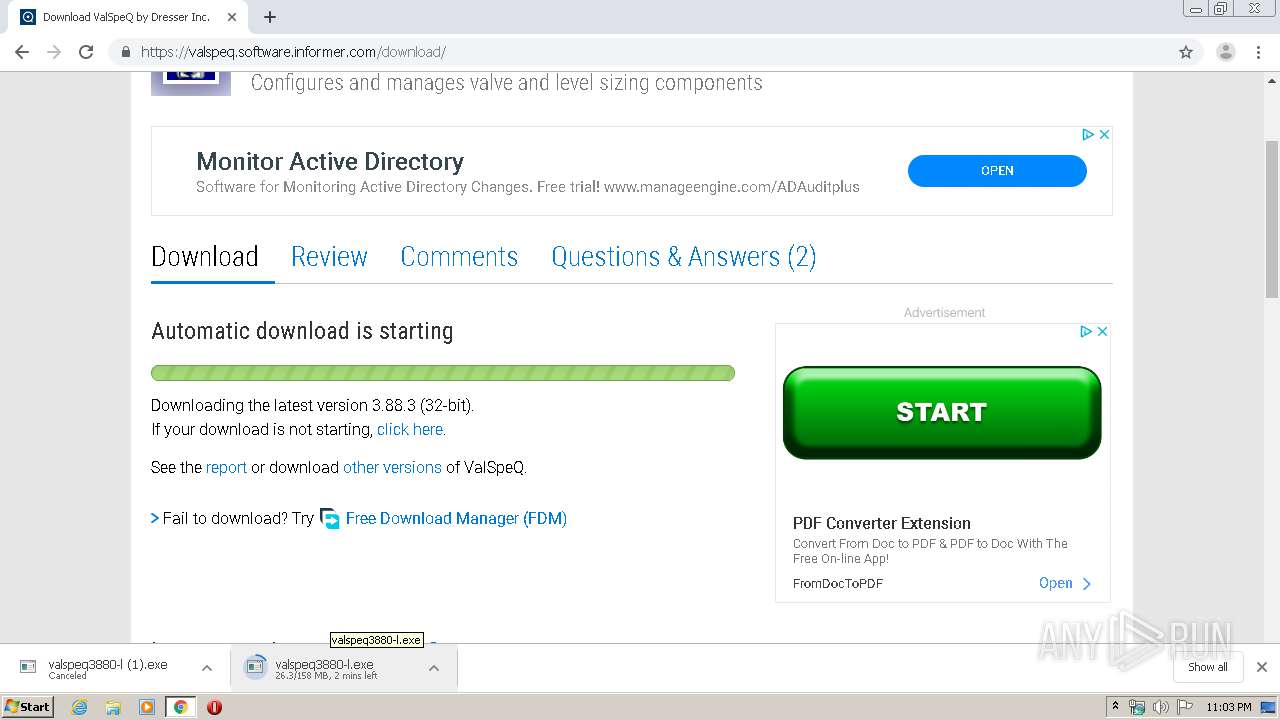
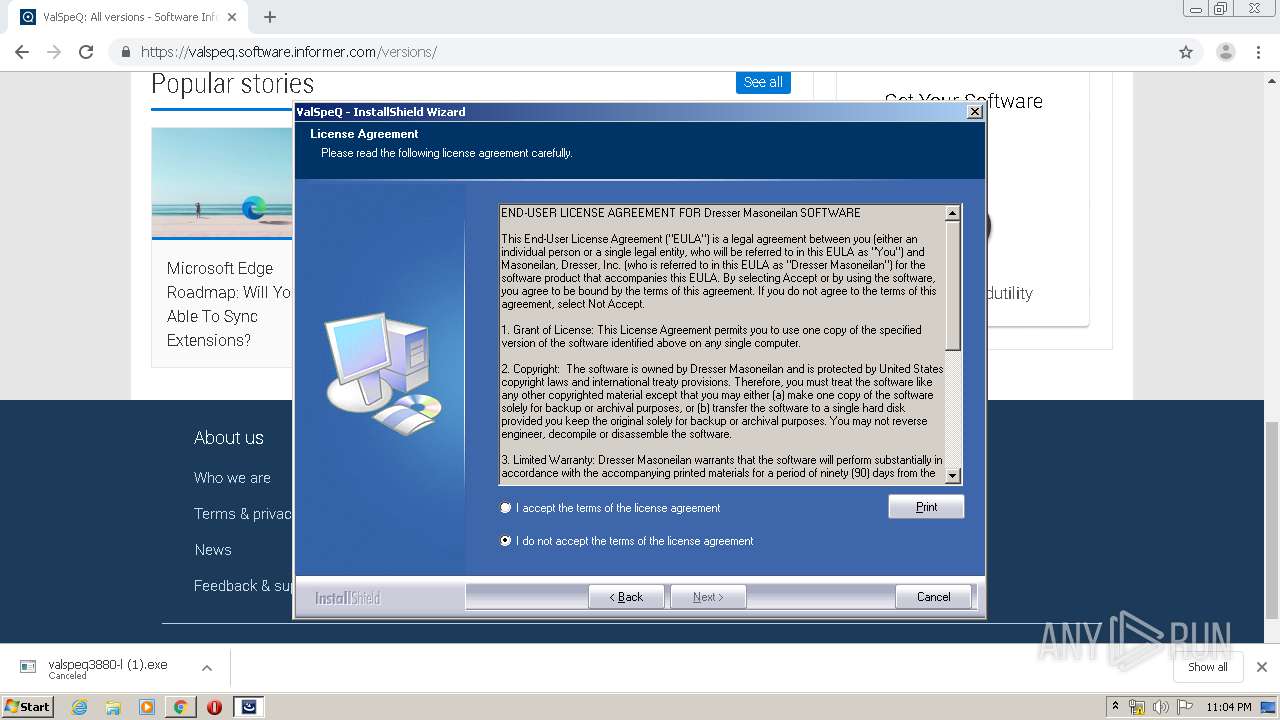
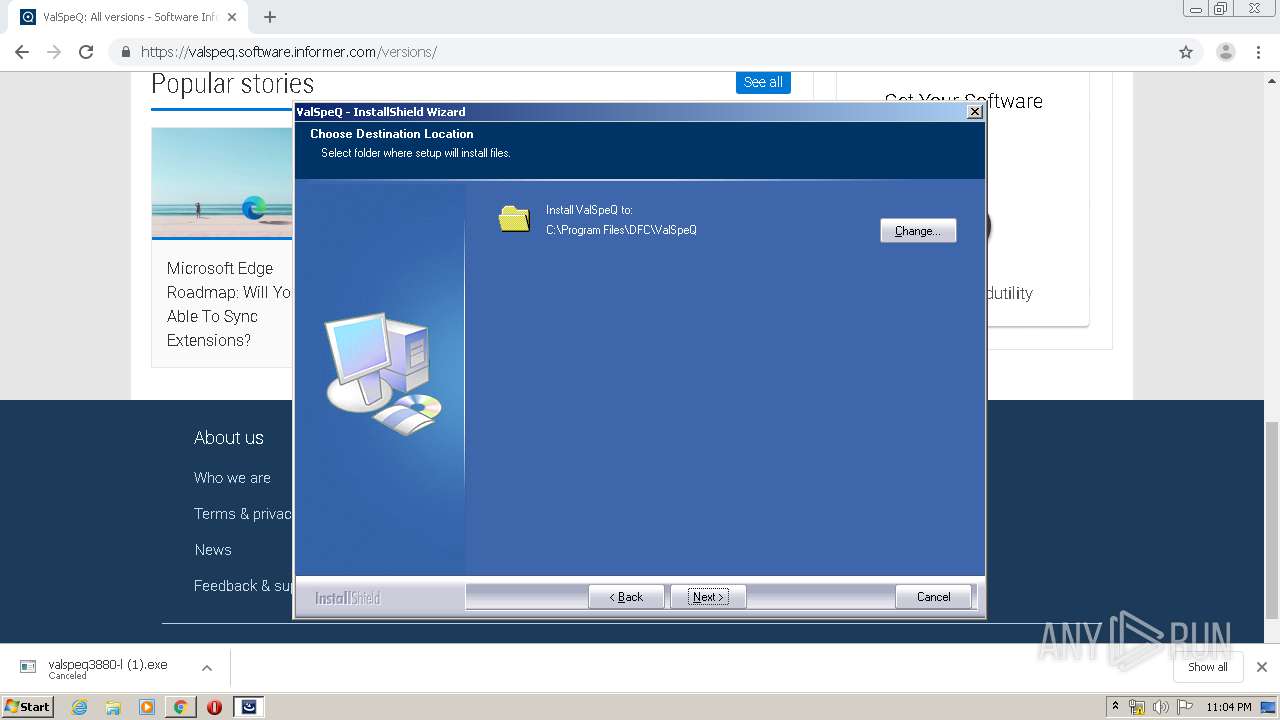
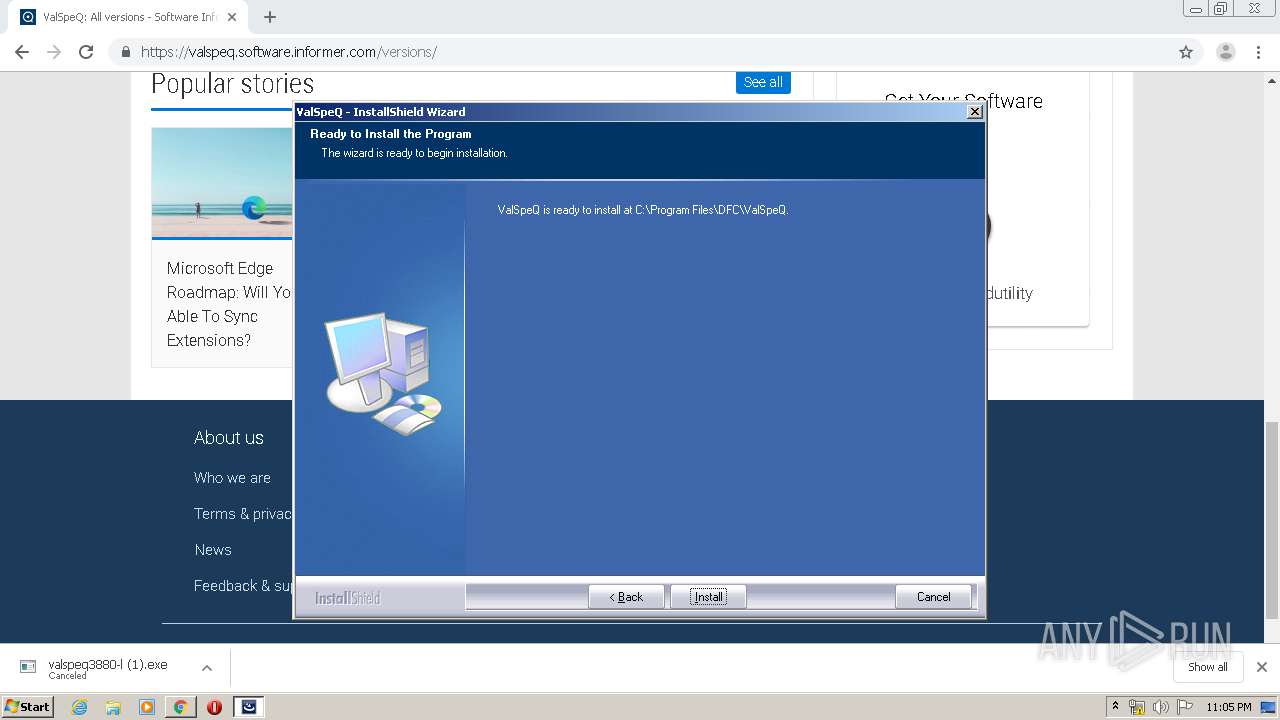
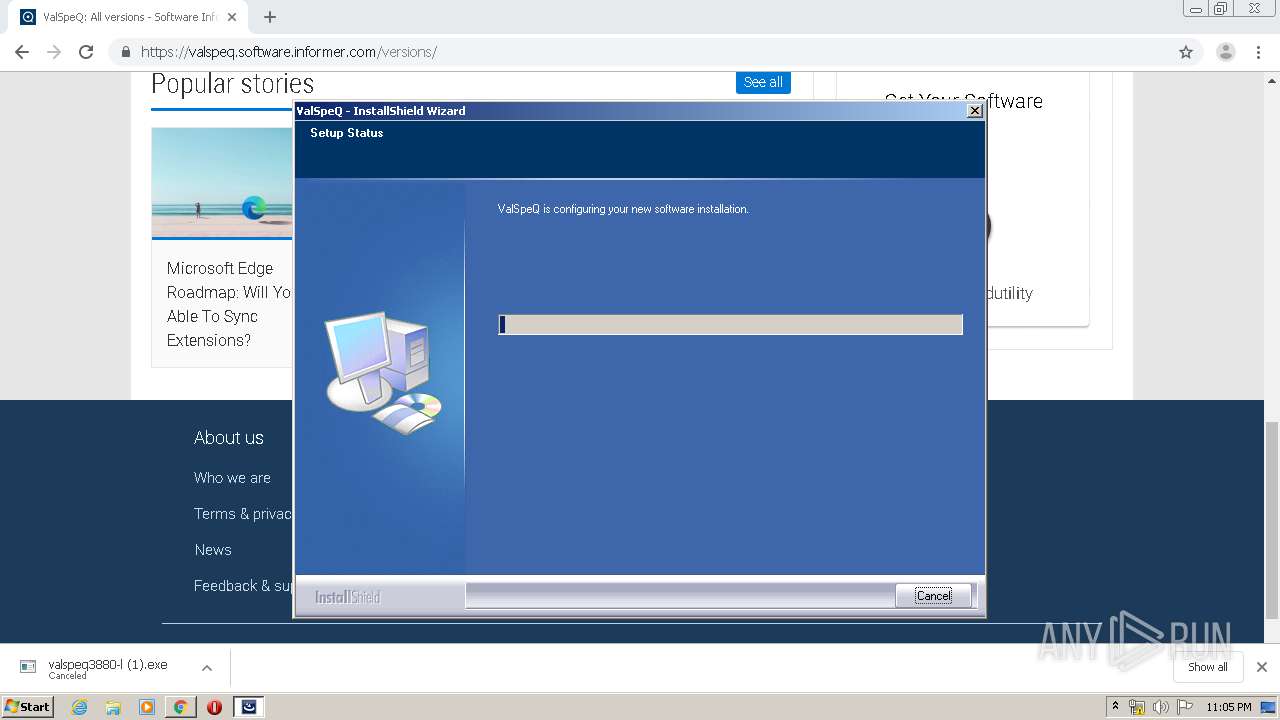
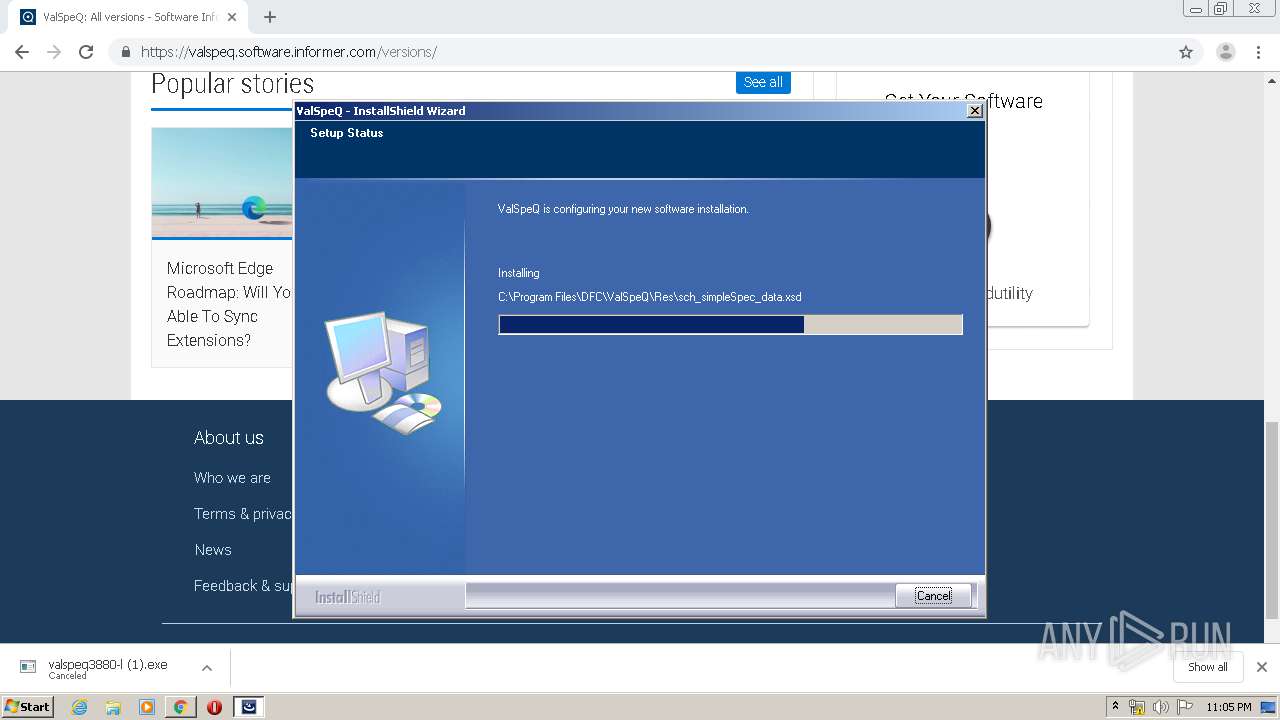
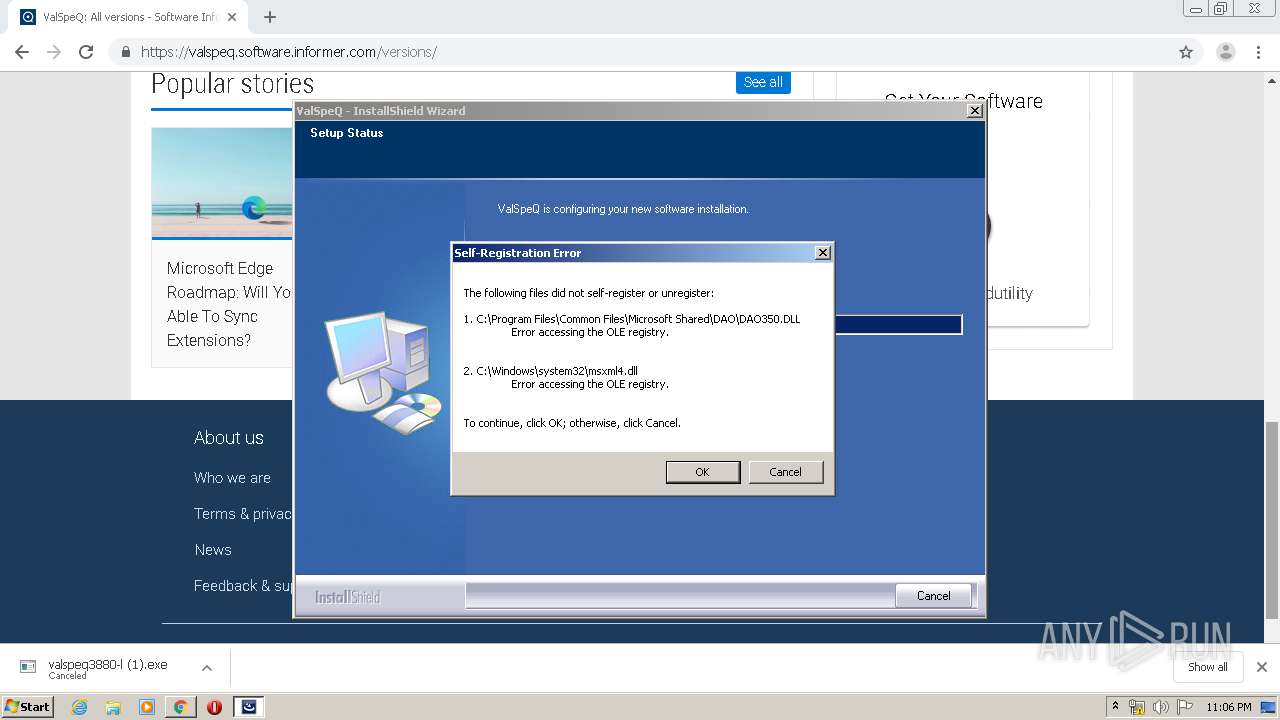
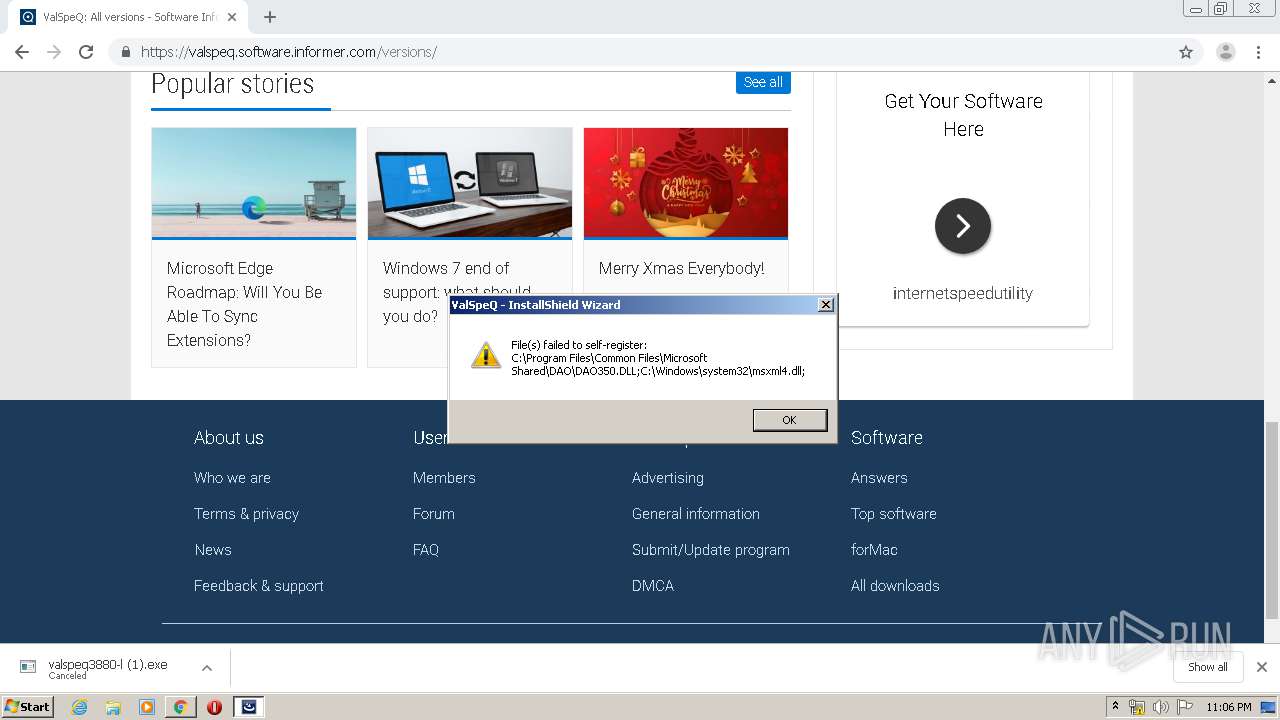
| URL: | https://valspeq.software.informer.com/3.8/ |
| Full analysis: | https://app.any.run/tasks/509976de-d321-43bd-9967-ce660c2dd5b1 |
| Verdict: | Malicious activity |
| Analysis date: | March 17, 2020, 23:02:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3778F2949AFDE261E6109BCD3E3BABB2 |
| SHA1: | 0E95B26BF846077D3344C18EC4C3439178927D54 |
| SHA256: | 94BDDA96840149A835339B049475652C00B1C6ED51D0181E14238363FEC8F77C |
| SSDEEP: | 3:N8+zULj4CdK:2Eu0CI |
MALICIOUS
Application was dropped or rewritten from another process
- valspeq3880-l.exe (PID: 3900)
- DotNetInstaller.exe (PID: 3352)
- DotNetInstaller.exe (PID: 3552)
- DotNetInstaller.exe (PID: 3284)
- DotNetInstaller.exe (PID: 3884)
- DotNetInstaller.exe (PID: 2732)
- DotNetInstaller.exe (PID: 3980)
- DotNetInstaller.exe (PID: 1780)
- DotNetInstaller.exe (PID: 3008)
- valspeq3880-l.exe (PID: 2812)
- DotNetInstaller.exe (PID: 2716)
- DotNetInstaller.exe (PID: 3900)
- DotNetInstaller.exe (PID: 2916)
- DotNetInstaller.exe (PID: 3216)
- DotNetInstaller.exe (PID: 1028)
- DotNetInstaller.exe (PID: 3560)
- DotNetInstaller.exe (PID: 3276)
- DotNetInstaller.exe (PID: 4036)
- DotNetInstaller.exe (PID: 2644)
- DotNetInstaller.exe (PID: 3816)
- DotNetInstaller.exe (PID: 3292)
- DotNetInstaller.exe (PID: 1900)
- ValSpeQ.exe (PID: 2748)
- Jet35sp3.exe (PID: 252)
Loads dropped or rewritten executable
- valspeq3880-l.exe (PID: 2812)
- DotNetInstaller.exe (PID: 3884)
- DotNetInstaller.exe (PID: 2716)
- DotNetInstaller.exe (PID: 2732)
- DotNetInstaller.exe (PID: 3284)
- DotNetInstaller.exe (PID: 3900)
- DotNetInstaller.exe (PID: 1780)
- DotNetInstaller.exe (PID: 4036)
- DotNetInstaller.exe (PID: 2916)
- DotNetInstaller.exe (PID: 3276)
- DotNetInstaller.exe (PID: 3292)
- MsiExec.exe (PID: 3728)
- MsiExec.exe (PID: 1228)
- MsiExec.exe (PID: 440)
- MsiExec.exe (PID: 180)
- MsiExec.exe (PID: 3012)
- MsiExec.exe (PID: 2780)
- MsiExec.exe (PID: 1136)
- MsiExec.exe (PID: 376)
- MsiExec.exe (PID: 3776)
- MsiExec.exe (PID: 1016)
- MsiExec.exe (PID: 3044)
- MsiExec.exe (PID: 3056)
- MsiExec.exe (PID: 3064)
- MsiExec.exe (PID: 3540)
- MsiExec.exe (PID: 4076)
- MsiExec.exe (PID: 3788)
- MsiExec.exe (PID: 3244)
- MsiExec.exe (PID: 1724)
- MsiExec.exe (PID: 1092)
- MsiExec.exe (PID: 3140)
- MsiExec.exe (PID: 1516)
- MsiExec.exe (PID: 1028)
- MsiExec.exe (PID: 3824)
- MsiExec.exe (PID: 2320)
- MsiExec.exe (PID: 2356)
- MsiExec.exe (PID: 3656)
- MsiExec.exe (PID: 1508)
- Jet35sp3.exe (PID: 252)
- ValSpeQ.exe (PID: 2748)
- MsiExec.exe (PID: 2376)
- MsiExec.exe (PID: 1676)
- DotNetInstaller.exe (PID: 3008)
Changes settings of System certificates
- DotNetInstaller.exe (PID: 2716)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2488)
- chrome.exe (PID: 1064)
- valspeq3880-l.exe (PID: 2812)
- msiexec.exe (PID: 3552)
- Jet35sp3.exe (PID: 252)
Reads Windows owner or organization settings
- valspeq3880-l.exe (PID: 2812)
Searches for installed software
- valspeq3880-l.exe (PID: 2812)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2488)
Reads the Windows organization settings
- valspeq3880-l.exe (PID: 2812)
Executed as Windows Service
- vssvc.exe (PID: 968)
Modifies the open verb of a shell class
- valspeq3880-l.exe (PID: 2812)
Creates COM task schedule object
- DotNetInstaller.exe (PID: 2716)
- msiexec.exe (PID: 3552)
- MsiExec.exe (PID: 3728)
- MsiExec.exe (PID: 440)
- MsiExec.exe (PID: 2780)
- MsiExec.exe (PID: 3012)
- MsiExec.exe (PID: 180)
- MsiExec.exe (PID: 1228)
- MsiExec.exe (PID: 376)
- MsiExec.exe (PID: 1136)
- MsiExec.exe (PID: 3776)
- MsiExec.exe (PID: 1016)
- MsiExec.exe (PID: 3056)
- MsiExec.exe (PID: 4076)
- MsiExec.exe (PID: 3064)
- MsiExec.exe (PID: 3540)
- MsiExec.exe (PID: 1028)
- MsiExec.exe (PID: 1724)
- MsiExec.exe (PID: 3140)
- MsiExec.exe (PID: 1516)
- MsiExec.exe (PID: 1092)
- MsiExec.exe (PID: 3788)
- MsiExec.exe (PID: 1676)
- MsiExec.exe (PID: 3824)
- MsiExec.exe (PID: 2320)
- MsiExec.exe (PID: 3656)
- MsiExec.exe (PID: 1508)
- MsiExec.exe (PID: 2356)
- valspeq3880-l.exe (PID: 2812)
- MsiExec.exe (PID: 3044)
- MsiExec.exe (PID: 2376)
- MsiExec.exe (PID: 3244)
Creates files in the program directory
- valspeq3880-l.exe (PID: 2812)
- ValSpeQ.exe (PID: 2748)
Creates files in the Windows directory
- valspeq3880-l.exe (PID: 2812)
- msiexec.exe (PID: 3552)
- Jet35sp3.exe (PID: 252)
Adds / modifies Windows certificates
- DotNetInstaller.exe (PID: 2716)
Removes files from Windows directory
- msiexec.exe (PID: 3552)
- Jet35sp3.exe (PID: 252)
Creates a software uninstall entry
- valspeq3880-l.exe (PID: 2812)
INFO
Reads the hosts file
- chrome.exe (PID: 2488)
- chrome.exe (PID: 1064)
Reads Internet Cache Settings
- chrome.exe (PID: 2488)
Low-level read access rights to disk partition
- vssvc.exe (PID: 968)
Application launched itself
- chrome.exe (PID: 2488)
- msiexec.exe (PID: 3552)
Reads settings of System Certificates
- chrome.exe (PID: 1064)
- DotNetInstaller.exe (PID: 2716)
- DotNetInstaller.exe (PID: 1780)
Starts application with an unusual extension
- msiexec.exe (PID: 3552)
Loads dropped or rewritten executable
- msiexec.exe (PID: 3552)
- MsiExec.exe (PID: 2788)
- MsiExec.exe (PID: 3640)
Dropped object may contain Bitcoin addresses
- valspeq3880-l.exe (PID: 2812)
- msiexec.exe (PID: 3552)
Creates files in the program directory
- MsiExec.exe (PID: 2788)
- msiexec.exe (PID: 3552)
Creates a software uninstall entry
- msiexec.exe (PID: 3552)
Manual execution by user
- ValSpeQ.exe (PID: 2748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
155
Monitored processes
91
Malicious processes
38
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | "C:\Windows\system32\MsiExec.exe" /Y "C:\Program Files\Business Objects\BusinessObjects Enterprise 12.0\win32_x86\exportmodeller.dll" | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 252 | C:\Users\admin\AppData\Local\Temp\{55999F80-4483-4584-BD54-1C20A53567AB}\{C6FB9F78-4CB8-4E8D-9A23-133F48A07C25}\Jet35sp3.exe | C:\Users\admin\AppData\Local\Temp\{55999F80-4483-4584-BD54-1C20A53567AB}\{C6FB9F78-4CB8-4E8D-9A23-133F48A07C25}\Jet35sp3.exe | valspeq3880-l.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 4.71.1015.0 Modules
| |||||||||||||||
| 376 | "C:\Windows\system32\MsiExec.exe" /Y "C:\Program Files\Business Objects\BusinessObjects Enterprise 12.0\win32_x86\datadefmodel.dll" | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 440 | "C:\Windows\system32\MsiExec.exe" /Y "C:\Program Files\Business Objects\BusinessObjects Enterprise 12.0\win32_x86\cubedefmodel.dll" | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 772 | "C:\Windows\Installer\MSI4F4B.tmp" | C:\Windows\Installer\MSI4F4B.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Business Objects Integrity Level: HIGH Description: CustActExe Exit code: 0 Version: 12.0.0.840 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,14134417760950761469,12088534520466632996,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2275226024184681919 --mojo-platform-channel-handle=4700 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,14134417760950761469,12088534520466632996,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15394538730901033042 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 968 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1016 | "C:\Windows\system32\MsiExec.exe" /Y "C:\Program Files\Business Objects\BusinessObjects Enterprise 12.0\win32_x86\prompt.dll" | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,14134417760950761469,12088534520466632996,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13157445781397770164 --mojo-platform-channel-handle=3496 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
16 503
Read events
3 982
Write events
12 398
Delete events
123
Modification events
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3924) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2488-13228959754653875 |
Value: 259 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2488-13228959754653875 |
Value: 259 | |||
Executable files
434
Suspicious files
118
Text files
1 320
Unknown types
147
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5E71570B-9B8.pma | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\7b8d1f37-4b08-4901-9380-8ae7d2f7d90a.tmp | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFa66c8d.TMP | text | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFa66c9d.TMP | text | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RFa66d1a.TMP | text | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFa66ea0.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
104
DNS requests
54
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1064 | chrome.exe | GET | 302 | 216.58.210.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 519 b | whitelisted |
1064 | chrome.exe | GET | 302 | 216.58.210.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 524 b | whitelisted |
1064 | chrome.exe | GET | 200 | 173.194.137.72:80 | http://r3---sn-aigzrn76.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=QJ&mip=85.203.46.135&mm=28&mn=sn-aigzrn76&ms=nvh&mt=1584486079&mv=m&mvi=2&pl=25&shardbypass=yes | US | crx | 293 Kb | whitelisted |
1064 | chrome.exe | GET | 200 | 173.194.135.106:80 | http://r5---sn-aigzrn7z.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=bs&mip=85.203.46.135&mm=28&mn=sn-aigzrn7z&ms=nvh&mt=1584486079&mv=m&mvi=4&pl=25&shardbypass=yes | US | crx | 862 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1064 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
1064 | chrome.exe | 100.25.93.238:443 | valspeq.software.informer.com | — | US | unknown |
1064 | chrome.exe | 172.217.16.130:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
1064 | chrome.exe | 172.217.18.14:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
1064 | chrome.exe | 216.58.210.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1064 | chrome.exe | 208.88.224.98:443 | i.informer.com | WZ Communications Inc. | US | unknown |
1064 | chrome.exe | 172.217.16.194:443 | adservice.google.co.uk | Google Inc. | US | whitelisted |
1064 | chrome.exe | 172.217.18.2:443 | www.googletagservices.com | Google Inc. | US | whitelisted |
1064 | chrome.exe | 208.94.233.126:443 | video.informer.com | WZ Communications Inc. | US | unknown |
1064 | chrome.exe | 74.117.179.70:443 | img.informer.com | WZ Communications Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
valspeq.software.informer.com |
| suspicious |
accounts.google.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
img.informer.com |
| whitelisted |
i.informer.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
art-u2.infcdn.net |
| suspicious |
hits.informer.com |
| unknown |
software.informer.com |
| whitelisted |