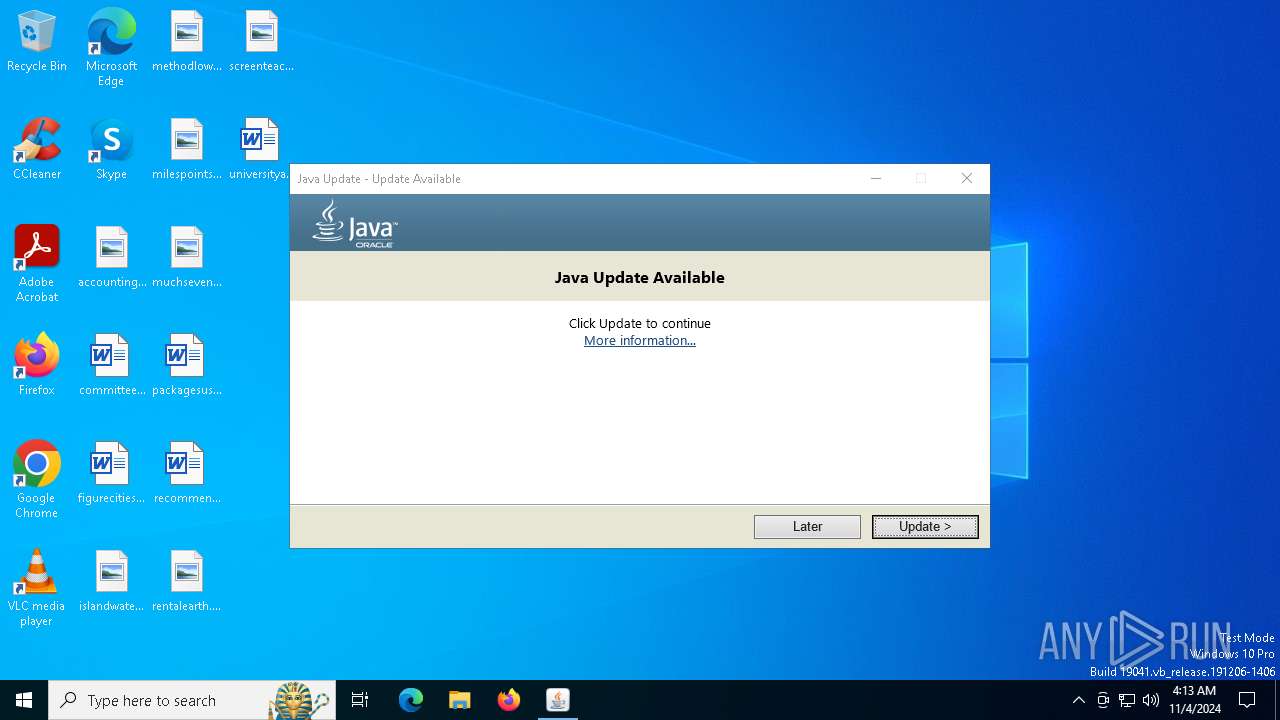
| File name: | ASYCUDAWorld_64.jnlp |
| Full analysis: | https://app.any.run/tasks/cd6f2cd5-34cd-43aa-bc9b-a07554129e0d |
| Verdict: | Malicious activity |
| Analysis date: | November 04, 2024, 04:13:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, ASCII text |
| MD5: | 46A06C29DF56390A9AD60E0C4A167446 |
| SHA1: | 481897504FE0FEADC0AE4E2A557739F18FE56991 |
| SHA256: | 94B25AF9B736D3C10DFCD79FF1560B5CD69FE94F549887FB0E4FB8E1C9BCB9C7 |
| SSDEEP: | 96:QMt52TDslrPCqvt0ybRPkd1zP/bRi/wlr8UsD5JVHRQwAOJru2SwULC/HwKxgIIJ:d2+8oCcep |
MALICIOUS
No malicious indicators.SUSPICIOUS
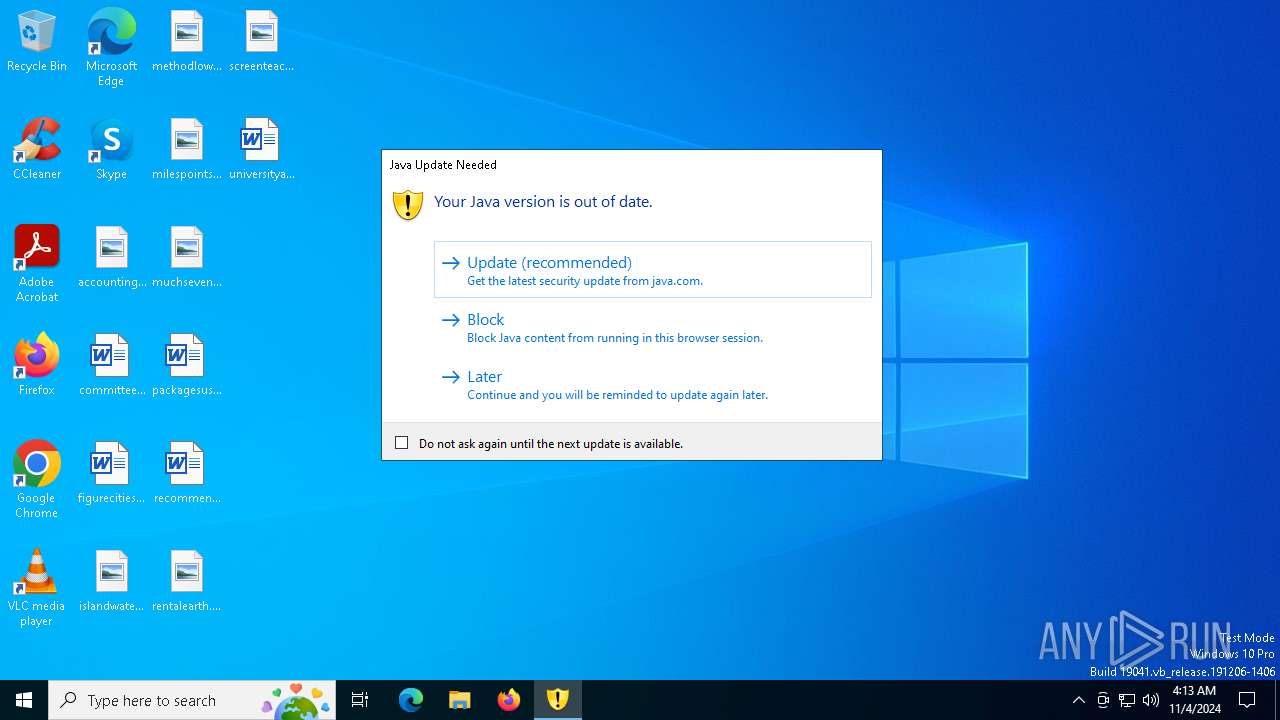
Checks for Java to be installed
- javaws.exe (PID: 6132)
- javaw.exe (PID: 6660)
- javaw.exe (PID: 1452)
- javaw.exe (PID: 1376)
- jucheck.exe (PID: 2724)
- jp2launcher.exe (PID: 7076)
Reads security settings of Internet Explorer
- jucheck.exe (PID: 2724)
Checks Windows Trust Settings
- jucheck.exe (PID: 2724)
INFO
Reads the computer name
- javaws.exe (PID: 6132)
- javaw.exe (PID: 1452)
- javaw.exe (PID: 6660)
- javaw.exe (PID: 1376)
- javaws.exe (PID: 7132)
- jucheck.exe (PID: 2724)
- jp2launcher.exe (PID: 7076)
Checks supported languages
- javaws.exe (PID: 6132)
- javaw.exe (PID: 6660)
- jp2launcher.exe (PID: 6436)
- javaw.exe (PID: 1452)
- javaw.exe (PID: 1376)
- jucheck.exe (PID: 2724)
- javaws.exe (PID: 7132)
- jp2launcher.exe (PID: 7076)
Create files in a temporary directory
- javaw.exe (PID: 6660)
- javaw.exe (PID: 1452)
- javaw.exe (PID: 1376)
- jp2launcher.exe (PID: 7076)
- jucheck.exe (PID: 2724)
Creates files in the program directory
- javaw.exe (PID: 1452)
Reads the machine GUID from the registry
- jucheck.exe (PID: 2724)
Checks proxy server information
- jucheck.exe (PID: 2724)
Reads the software policy settings
- jucheck.exe (PID: 2724)
Creates files or folders in the user directory
- jucheck.exe (PID: 2724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jnlp | | | Java Web Start application descriptor (88.3) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (11.6) |
EXIF
XMP
| JnlpSpec: | 1.0+ |
|---|---|
| JnlpCodebase: | https://202.124.161.212:8443/ |
| JnlpHref: | ASYCUDAWorld_64.jnlp |
| JnlpInformationTitle: | ASYCUDA World System |
| JnlpInformationVendor: | Sri Lanka Customs |
| JnlpInformationHomepageHref: | http://customs.gov.lk |
| JnlpInformationDescription: | ASYCUDA WORLD |
| JnlpInformationDescriptionKind: | short |
| JnlpInformationIconHref: | images/AW_image_install.jpg |
| JnlpInformationIconKind: | splash |
| JnlpSecurityAll-permissions: | - |
| JnlpResourcesPropertyName: | un.remotetartabinvocation |
| JnlpResourcesPropertyValue: | - |
| JnlpResourcesJ2seHref: | http://java.sun.com/products/autodl/j2se |
| JnlpResourcesJ2seInitial-heap-size: | 512m |
| JnlpResourcesJ2seMax-heap-size: | 5100m |
| JnlpResourcesJ2seVersion: | 1.6+ |
| JnlpResourcesJavafx-runtimeVersion: | 2.1+ |
| JnlpResourcesJavafx-runtimeHref: | http://javadl.sun.com/webapps/download/GetFile/javafx-latest/windows-i586/javafx2.jnlp |
| JnlpResourcesJarHref: | lib/asybarc.jar |
| JnlpResourcesJarMain: | - |
| JnlpApplication-descMain-class: | un.kernel.client.AWDesktopMain |
| JnlpApplication-descArgument: | https://202.124.161.212:8443/help/ |
Total processes
142
Monitored processes
10
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1376 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.suppression.11.271.2" "false" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1452 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.11.271.2" "update" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2724 | "C:\Program Files (x86)\Common Files\Java\Java Update\jucheck.exe" | C:\Program Files (x86)\Common Files\Java\Java Update\jucheck.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Update Checker Version: 2.8.271.9 Modules
| |||||||||||||||
| 4956 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6132 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" "C:\Users\admin\AppData\Local\Temp\ASYCUDAWorld_64.jnlp" | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | jp2launcher.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 1 Version: 11.271.2.09 Modules
| |||||||||||||||
| 6316 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6436 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -securejws C:\Users\admin\AppData\Local\Temp\ASYCUDAWorld_64.jnlp | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 6660 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.271.2" "1730693605" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 7076 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxwbHVnaW4uamFyAC1EamRrLmRpc2FibGVMYXN0VXNhZ2VUcmFja2luZz10cnVlAC1Eam5scHguanZtPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcYmluXGphdmF3LmV4ZQAtRGpubHB4LnZtYXJncz1MVVJxWkdzdVpHbHpZV0pzWlV4aGMzUlZjMkZuWlZSeVlXTnJhVzVuUFhSeWRXVUE= -ma LVNTVkJhc2VsaW5lVXBkYXRlAC1ub3RXZWJKYXZh | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 7132 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" -J-Djdk.disableLastUsageTracking=true -SSVBaselineUpdate | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | jucheck.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
Total events
6 730
Read events
6 626
Write events
80
Delete events
24
Modification events
| (PID) Process: | (1452) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.modified.timestamp |
Value: 1675955855080 | |||
| (PID) Process: | (1452) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.roaming.profile |
Value: false | |||
| (PID) Process: | (1452) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.version |
Value: 8 | |||
| (PID) Process: | (1452) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expired.version |
Value: 11.271.2 | |||
| (PID) Process: | (1452) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.browser.path |
Value: C:\Program Files\Internet Explorer\IEXPLORE.EXE | |||
| (PID) Process: | (1452) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1452) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expiration.decision.11.271.2 |
Value: update | |||
| (PID) Process: | (6660) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6660) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expiration.decision.11.271.2 |
Value: update | |||
| (PID) Process: | (6660) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.modified.timestamp |
Value: 1730693605507 | |||
Executable files
1
Suspicious files
4
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7076 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\blacklist.dynamic | text | |
MD5:B2C6EAE6382150192EA3912393747180 | SHA256:6C73C877B36D4ABD086CB691959B180513AC5ABC0C87FE9070D2D5426D3DBF71 | |||
| 2724 | jucheck.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:AB8BB3099BA5292B6AC759F820E027F6 | SHA256:A76531EB9179179CDAB6B22756A8F34077356B38C9B7F61216952369C4AA025C | |||
| 2724 | jucheck.exe | C:\Users\admin\AppData\Local\Temp\jusched.log | text | |
MD5:04F3F8F20FADAF3E37C578E334FC867A | SHA256:C35B686F7E6CADF12F4E0FD49751CCE94B40F294C816DAF50F00AB9704EA48C0 | |||
| 7076 | jp2launcher.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\83aa4cc77f591dfc2374580bbd95f6ba_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
| 7076 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\securitypack.jar | java | |
MD5:A66E19C05F3E0B24AC077A37C2B7589E | SHA256:9771364D53FA9B1BD14CEF7E48BE1F5DF23B11AAC9F5CB6763A4934B3190E126 | |||
| 7076 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\update.securitypack.timestamp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 2724 | jucheck.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:75FF70531FF40DB67379C0EC48F96100 | SHA256:37C12041D3226EF792E13C21CEFA71A3C8F5C9FC3927EC5C7D584D9724EAE043 | |||
| 1452 | javaw.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:7E5BF1C2603F607015942172FE8FAA1A | SHA256:A3FB88711C1309FA8B74FD437C2162D27A6E4110AAC2FA1234447BCA2DBBFC28 | |||
| 7076 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\baseline.versions | text | |
MD5:F989AC1096619951CAD21A1D0F03097F | SHA256:7093F98DDA691FAA746C514A00705268188163ABF865F6C4325902532CB3158C | |||
| 1452 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:94D86A4E3592578A4F239FA213AFD6B1 | SHA256:B2B79F08E1C383BFF8259238D52F184EF4EC5047849138D49951A670EE7321B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
39
DNS requests
20
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2364 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2724 | jucheck.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1744 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3644 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1744 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7076 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
7076 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2444 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4360 | SearchApp.exe | 104.126.37.162:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2364 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2364 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4360 | SearchApp.exe | 104.126.37.144:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
javadl-esd-secure.oracle.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7076 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
7076 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |