| File name: | sheep.exe |
| Full analysis: | https://app.any.run/tasks/5b530230-1eff-4916-a36c-75ee1d74b741 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2020, 05:14:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9FF13690CC4976DF6B7CFD41728A969F |
| SHA1: | 95C9651EA7D863FFEB22FF6CD0E99EE10268C832 |
| SHA256: | 9483157A5F62AA2132E20045B5D15A449E6240FF01BE1FF3FE3DA5F471C6E4C0 |
| SSDEEP: | 393216:cak/e3+wpPZouJg3rCa4Il82sObJazyJ8/Mv9+bnUrFnc6EkMdUUKhMqBMIOv7S:+uU6kDUKhMYxU7S |
MALICIOUS
Application was injected by another process
- explorer.exe (PID: 1784)
- ctfmon.exe (PID: 1816)
- dwm.exe (PID: 1648)
- taskeng.exe (PID: 1580)
- windanr.exe (PID: 2196)
Runs injected code in another process
- iexplore.exe (PID: 3040)
Application was dropped or rewritten from another process
- sheepmgr.exe (PID: 2356)
Actions looks like stealing of personal data
- explorer.exe (PID: 1784)
Changes the autorun value in the registry
- reg.exe (PID: 3992)
Writes to a start menu file
- iexplore.exe (PID: 2844)
SUSPICIOUS
Starts Internet Explorer
- sheepmgr.exe (PID: 2356)
Application launched itself
- Skype.exe (PID: 3572)
- Skype.exe (PID: 3376)
- Skype.exe (PID: 1468)
Reads CPU info
- Skype.exe (PID: 3572)
Modifies the open verb of a shell class
- Skype.exe (PID: 3572)
Executable content was dropped or overwritten
- sheep.exe (PID: 3436)
Creates files in the user directory
- Skype.exe (PID: 3572)
- Skype.exe (PID: 1468)
- Skype.exe (PID: 3376)
Uses REG.EXE to modify Windows registry
- Skype.exe (PID: 3572)
Creates files in the program directory
- iexplore.exe (PID: 2844)
INFO
Creates files in the user directory
- iexplore.exe (PID: 2844)
Reads the hosts file
- Skype.exe (PID: 3572)
Reads settings of System Certificates
- Skype.exe (PID: 3572)
Dropped object may contain Bitcoin addresses
- Skype.exe (PID: 3572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (21.4) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (2.3) |
| .exe | | | Generic Win/DOS Executable (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:11:15 22:25:30+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 12790272 |
| InitializedDataSize: | 4169728 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1031000 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.2.3.53610 |
| ProductVersionNumber: | 5.2.3.53610 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileVersion: | 5.2.3.15978858 |
| ProductVersion: | 5.2.3.15978858 |
| UnityVersion: | 5.2.3f1_f3d16a1fa2dd |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 15-Nov-2015 21:25:30 |
| Detected languages: |
|
| Debug artifacts: |
|
| FileVersion: | 5.2.3.15978858 |
| ProductVersion: | 5.2.3.15978858 |
| Unity Version: | 5.2.3f1_f3d16a1fa2dd |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000138 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 9 |
| Time date stamp: | 15-Nov-2015 21:25:30 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x01031000 | 0x00022000 | 0x00021C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.54632 |
.rdata | 0x00C34000 | 0x001D4E00 | 0x001D4E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.20707 |
.data | 0x00E09000 | 0x00115840 | 0x00056C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.05327 |
.trace | 0x00F1F000 | 0x00001D98 | 0x00001E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.28551 |
.data1 | 0x00F21000 | 0x00000040 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.436447 |
_RDATA | 0x00F22000 | 0x00000540 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.12448 |
.rsrc | 0x00F23000 | 0x0008A678 | 0x0008A800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.57812 |
.reloc | 0x00FAE000 | 0x00082954 | 0x00082A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.6185 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.37424 | 1409 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.61125 | 2440 | UNKNOWN | English - United States | RT_ICON |
3 | 4.11959 | 4264 | UNKNOWN | English - United States | RT_ICON |
4 | 4.05353 | 9640 | UNKNOWN | English - United States | RT_ICON |
5 | 3.76721 | 16936 | UNKNOWN | English - United States | RT_ICON |
6 | 3.73979 | 38056 | UNKNOWN | English - United States | RT_ICON |
7 | 3.57675 | 67624 | UNKNOWN | English - United States | RT_ICON |
8 | 3.58825 | 152104 | UNKNOWN | English - United States | RT_ICON |
9 | 2.99471 | 292 | UNKNOWN | English - United States | RT_DIALOG |
103 | 3.04448 | 132 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
DNSAPI.dll |
GDI32.dll |
HID.DLL |
IMM32.dll |
IPHLPAPI.DLL |
KERNEL32.dll |
MSACM32.dll |
OLEAUT32.dll |
OPENGL32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
??$Transfer@V?$StreamedBinaryRead@$00@@@AnimationEvent@@QAEXAAV?$StreamedBinaryRead@$00@@@Z | 1 | 0x00466A40 |
??$Transfer@V?$StreamedBinaryRead@$00@@@Behaviour@@QAEXAAV?$StreamedBinaryRead@$00@@@Z | 2 | 0x0012E6C0 |
??$Transfer@V?$StreamedBinaryRead@$00@@@Component@Unity@@QAEXAAV?$StreamedBinaryRead@$00@@@Z | 3 | 0x000109B0 |
??$Transfer@V?$StreamedBinaryRead@$00@@@GameObject@Unity@@QAEXAAV?$StreamedBinaryRead@$00@@@Z | 4 | 0x00011960 |
??$Transfer@V?$StreamedBinaryRead@$00@@@GlobalGameManager@@QAEXAAV?$StreamedBinaryRead@$00@@@Z | 5 | 0x0053DC20 |
??$Transfer@V?$StreamedBinaryRead@$00@@@LevelGameManager@@QAEXAAV?$StreamedBinaryRead@$00@@@Z | 6 | 0x0053DC20 |
??$Transfer@V?$StreamedBinaryRead@$00@@@NamedObject@@QAEXAAV?$StreamedBinaryRead@$00@@@Z | 7 | 0x00017380 |
??$Transfer@V?$StreamedBinaryRead@$00@@@Object@@IAEXAAV?$StreamedBinaryRead@$00@@@Z | 8 | 0x0025BEB0 |
??$Transfer@V?$StreamedBinaryRead@$00@@@Renderer@@QAEXAAV?$StreamedBinaryRead@$00@@@Z | 9 | 0x0011AA90 |
??$Transfer@V?$StreamedBinaryRead@$00@@@Terrain@@QAEXAAV?$StreamedBinaryRead@$00@@@Z | 10 | 0x004D0FB0 |
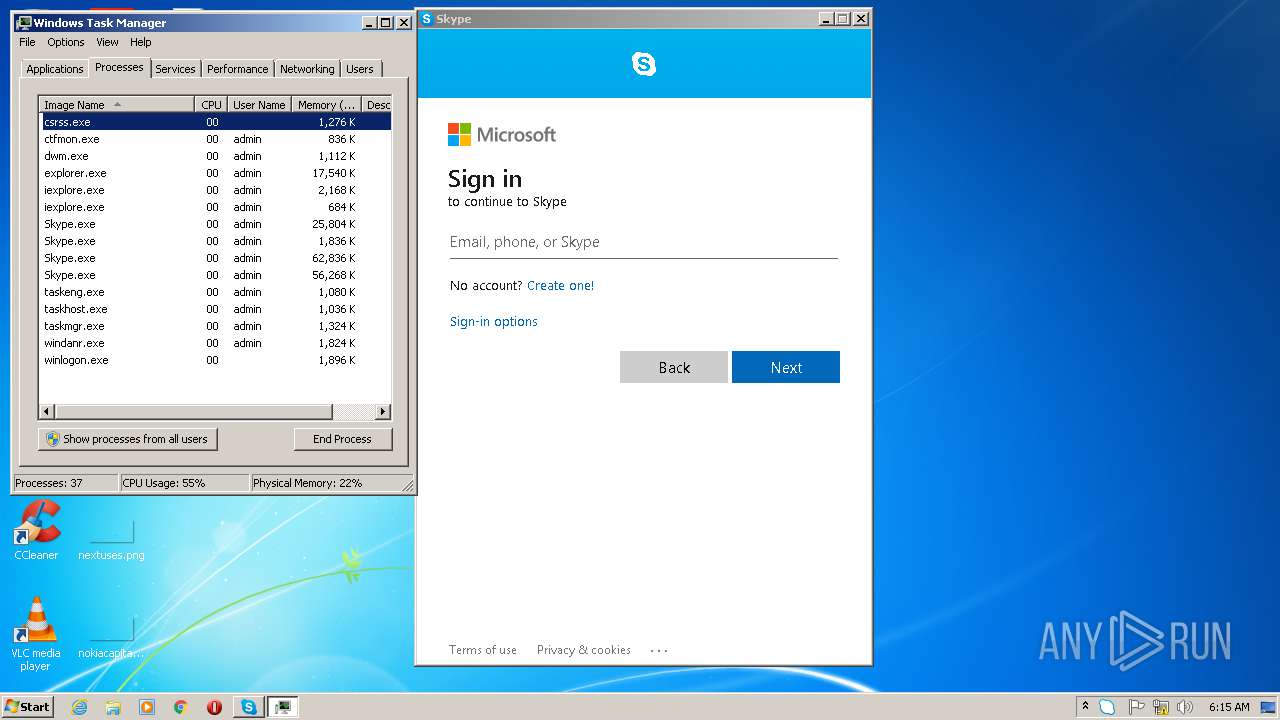
Total processes
50
Monitored processes
20
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 908 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --disable-databases --service-pipe-token=AA3DA4E4BF55C54FE082C390F79ADFFA --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\WebViewPreload.js" --guest-instance-id=1 --enable-blink-features --disable-blink-features --context-id=2 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=AA3DA4E4BF55C54FE082C390F79ADFFA --renderer-client-id=6 --mojo-platform-channel-handle=1604 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --service-pipe-token=2EF0EF8D1D5ACB411F206EBE5A8AD7D3 --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\Preload.js" --context-id=2 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=2EF0EF8D1D5ACB411F206EBE5A8AD7D3 --renderer-client-id=3 --mojo-platform-channel-handle=1604 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 1580 | taskeng.exe {D5FDA578-4A8E-4D92-89E9-C1DF61B7B0A2} | C:\Windows\System32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1648 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1784 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1816 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2196 | "windanr.exe" | C:\Windows\system32\windanr.exe | q.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2356 | C:\Users\admin\AppData\Local\Temp\sheepmgr.exe | C:\Users\admin\AppData\Local\Temp\sheepmgr.exe | — | sheep.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2440 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 2 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2484 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --disable-databases --service-pipe-token=365EC97EEE2A50EACD0C027A0BF36DF1 --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\WebViewPreload.js" --guest-instance-id=1 --enable-blink-features --disable-blink-features --context-id=1 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=365EC97EEE2A50EACD0C027A0BF36DF1 --renderer-client-id=7 --mojo-platform-channel-handle=2856 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
Total events
1 849
Read events
1 408
Write events
441
Delete events
0
Modification events
| (PID) Process: | (1784) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | P:\Hfref\nqzva\NccQngn\Ybpny\Grzc\furrc.rkr |
Value: 00000000000000000000000000000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (1784) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000004200000053000000C8ED25000B0000001A00000057BE0F007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000010000024E9ED017990C577B8006900000069000010000050E9ED01C4F6C4770000690000000000580269000002690064E9ED016C19C5770D00000000026900580269002CEBED0128EBED01000008009786217614E8ED0114EAED01D8E9ED0115E1C077C7670800FEFFFFFF8B8DC477108BC47701000000010000000000000004EAED01CCE9ED01E8E9ED012C8AC375010000000000000004EAED013F8AC375ED1805AB000000006CEFED0102000000FFFFFFFF0000000000000000000000000000E96FACE9ED01485F9B0050EEED01B514C5754D7B2BDFFEFFFFFF3F8AC375A36CC375A589C375651F05AB6CEFED0111000000483D3200403D32006CEFED017CEA0000C05704AB2CEAED018291D2767CEAED01EC430000FC5704AB40EAED01B69CD276F04311024C06000058EAED01603F110264EAED01789CD2763691D27611000000483D3200403D320000EBED01803F1102D0EA0000BC5704AB80EAED018291D276D0EAED0184EAED012795D27600000000EC431102ACEAED01CD94D276EC43110258EBED01603F1102E194D27600000000603F110258EBED01B4EAED010B0000001A00000057BE0F007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000010000024E9ED017990C577B8006900000069000010000050E9ED01C4F6C4770000690000000000580269000002690064E9ED016C19C5770D00000000026900580269002CEBED0128EBED01000008009786217614E8ED0114EAED01D8E9ED0115E1C077C7670800FEFFFFFF8B8DC477108BC47701000000010000000000000004EAED01CCE9ED01E8E9ED012C8AC375010000000000000004EAED013F8AC375ED1805AB000000006CEFED0102000000FFFFFFFF0000000000000000000000000000E96FACE9ED01485F9B0050EEED01B514C5754D7B2BDFFEFFFFFF3F8AC375A36CC375A589C375651F05AB6CEFED0111000000483D3200403D32006CEFED017CEA0000C05704AB2CEAED018291D2767CEAED01EC430000FC5704AB40EAED01B69CD276F04311024C06000058EAED01603F110264EAED01789CD2763691D27611000000483D3200403D320000EBED01803F1102D0EA0000BC5704AB80EAED018291D276D0EAED0184EAED012795D27600000000EC431102ACEAED01CD94D276EC43110258EBED01603F1102E194D27600000000603F110258EBED01B4EAED010B0000001A00000057BE0F007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000010000024E9ED017990C577B8006900000069000010000050E9ED01C4F6C4770000690000000000580269000002690064E9ED016C19C5770D00000000026900580269002CEBED0128EBED01000008009786217614E8ED0114EAED01D8E9ED0115E1C077C7670800FEFFFFFF8B8DC477108BC47701000000010000000000000004EAED01CCE9ED01E8E9ED012C8AC375010000000000000004EAED013F8AC375ED1805AB000000006CEFED0102000000FFFFFFFF0000000000000000000000000000E96FACE9ED01485F9B0050EEED01B514C5754D7B2BDFFEFFFFFF3F8AC375A36CC375A589C375651F05AB6CEFED0111000000483D3200403D32006CEFED017CEA0000C05704AB2CEAED018291D2767CEAED01EC430000FC5704AB40EAED01B69CD276F04311024C06000058EAED01603F110264EAED01789CD2763691D27611000000483D3200403D320000EBED01803F1102D0EA0000BC5704AB80EAED018291D276D0EAED0184EAED012795D27600000000EC431102ACEAED01CD94D276EC43110258EBED01603F1102E194D27600000000603F110258EBED01B4EAED01 | |||
| (PID) Process: | (1784) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1784) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\display.dll,-4 |
Value: S&creen resolution | |||
| (PID) Process: | (1784) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Windows Sidebar\sidebar.exe,-11100 |
Value: &Gadgets | |||
| (PID) Process: | (1784) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\themecpl.dll,-10 |
Value: Pe&rsonalize | |||
| (PID) Process: | (1784) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02 | |||
| (PID) Process: | (1784) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: FFFFFFFF | |||
| (PID) Process: | (1784) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | Mode |
Value: 1 | |||
| (PID) Process: | (1784) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | LogicalViewMode |
Value: 3 | |||
Executable files
1
Suspicious files
5
Text files
14
Unknown types
100
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\enbfqohg.exe | — | |
MD5:— | SHA256:— | |||
| 2844 | iexplore.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\LeiaMe.htm | html | |
MD5:— | SHA256:— | |||
| 2844 | iexplore.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\LeesMij.htm | html | |
MD5:— | SHA256:— | |||
| 2844 | iexplore.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Benioku.htm | html | |
MD5:— | SHA256:— | |||
| 2844 | iexplore.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\IrakHau.htm | html | |
MD5:— | SHA256:— | |||
| 2844 | iexplore.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Berime.htm | html | |
MD5:— | SHA256:— | |||
| 2844 | iexplore.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Liesmich.htm | html | |
MD5:— | SHA256:— | |||
| 2844 | iexplore.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Leggimi.htm | html | |
MD5:— | SHA256:— | |||
| 2844 | iexplore.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Lisezmoi.htm | html | |
MD5:— | SHA256:— | |||
| 2844 | iexplore.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Llegiu-me.htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
17
DNS requests
13
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3572 | Skype.exe | 216.58.212.138:443 | www.googleapis.com | Google Inc. | US | whitelisted |
2844 | iexplore.exe | 52.16.225.15:447 | tvrstrynyvwstrtve.com | Amazon.com, Inc. | IE | whitelisted |
3572 | Skype.exe | 40.90.22.192:443 | login.live.com | Microsoft Corporation | US | malicious |
3572 | Skype.exe | 2.18.233.81:443 | download.skype.com | Akamai International B.V. | — | whitelisted |
3572 | Skype.exe | 152.199.19.160:443 | bot-framework.azureedge.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3572 | Skype.exe | 13.107.42.23:443 | a.config.skype.com | Microsoft Corporation | US | suspicious |
3572 | Skype.exe | 52.114.133.60:443 | browser.pipe.aria.microsoft.com | Microsoft Corporation | US | suspicious |
3572 | Skype.exe | 52.233.180.130:443 | avatar.skype.com | Microsoft Corporation | NL | unknown |
3572 | Skype.exe | 192.229.221.185:443 | logincdn.msauth.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3572 | Skype.exe | 52.174.193.75:443 | get.skype.com | Microsoft Corporation | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| malicious |
supnewdmn.com |
| malicious |
get.skype.com |
| whitelisted |
a.config.skype.com |
| whitelisted |
download.skype.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
avatar.skype.com |
| whitelisted |
bot-framework.azureedge.net |
| whitelisted |
config.edge.skype.com |
| malicious |
tvrstrynyvwstrtve.com |
| malicious |
Threats
Process | Message |
|---|---|
Skype.exe | [2724:2672:0530/061459.170:VERBOSE1:crash_service_main.cc(78)] Session start. cmdline is [--reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1]
|
Skype.exe | [2724:2672:0530/061459.170:VERBOSE1:crash_service.cc(145)] window handle is 0004012E
|
Skype.exe | [2724:2672:0530/061459.170:VERBOSE1:crash_service.cc(304)] checkpoint is C:\Users\admin\AppData\Local\Temp\skype-preview Crashes\crash_checkpoint.txt
server is https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload
maximum 128 reports/day
reporter is electron-crash-service
|
Skype.exe | [2724:2412:0530/061459.170:VERBOSE1:crash_service.cc(333)] client start. pid = 3572
|
Skype.exe | [2724:2672:0530/061459.170:VERBOSE1:crash_service_main.cc(94)] Ready to process crash requests
|
Skype.exe | [2724:2672:0530/061459.170:VERBOSE1:crash_service.cc(300)] pipe name is \\.\pipe\skype-preview Crash Service
dumps at C:\Users\admin\AppData\Local\Temp\skype-preview Crashes
|
Skype.exe | [2724:2412:0530/061501.264:VERBOSE1:crash_service.cc(333)] client start. pid = 1468
|
Skype.exe | [3276:3284:0530/061501.453:VERBOSE1:crash_service_main.cc(78)] Session start. cmdline is [--reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1]
|
Skype.exe | [3276:3284:0530/061501.454:VERBOSE1:crash_service.cc(145)] window handle is 0001014C
|
Skype.exe | [3276:3284:0530/061501.455:VERBOSE1:crash_service.cc(304)] checkpoint is C:\Users\admin\AppData\Local\Temp\skype-preview Crashes\crash_checkpoint.txt
server is https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload
maximum 128 reports/day
reporter is electron-crash-service
|