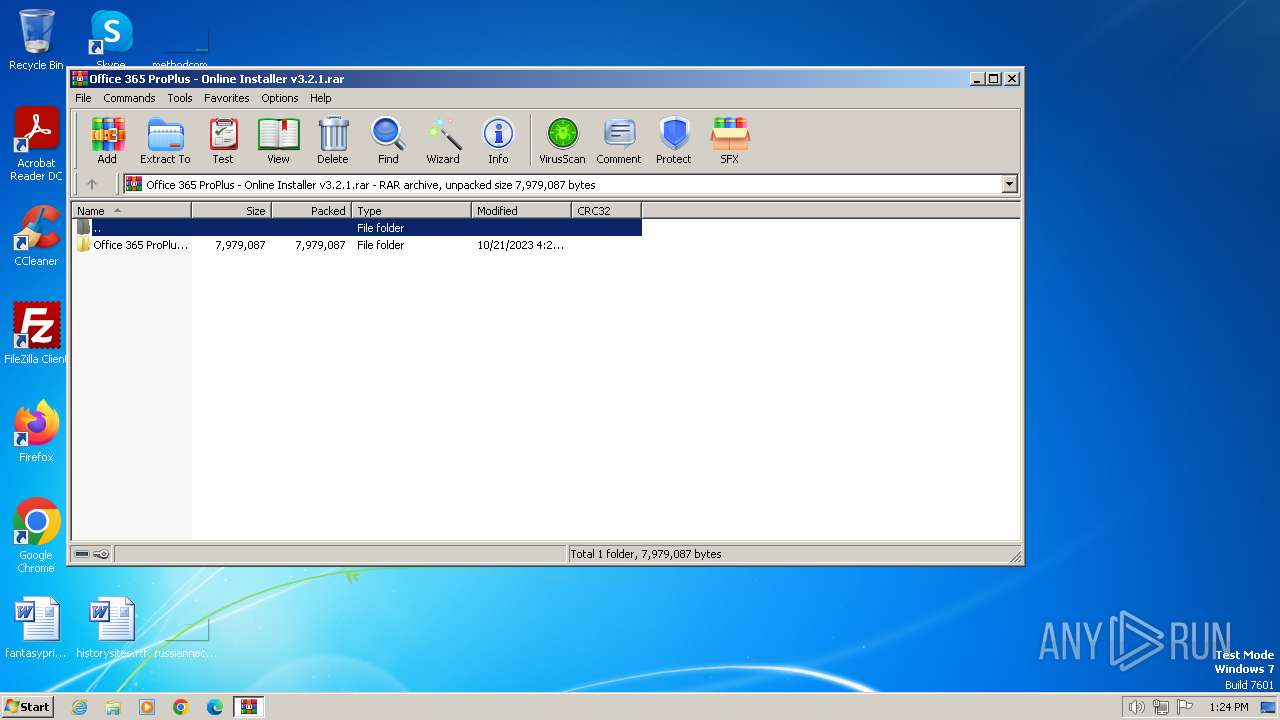
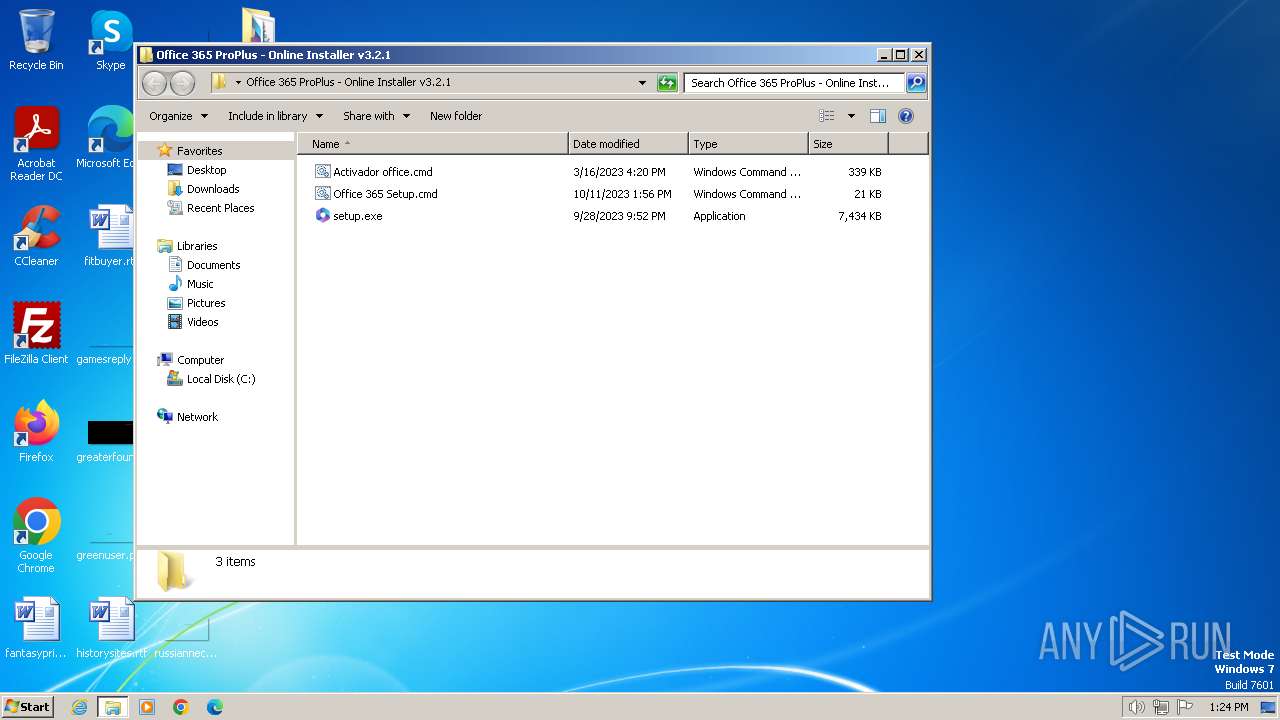
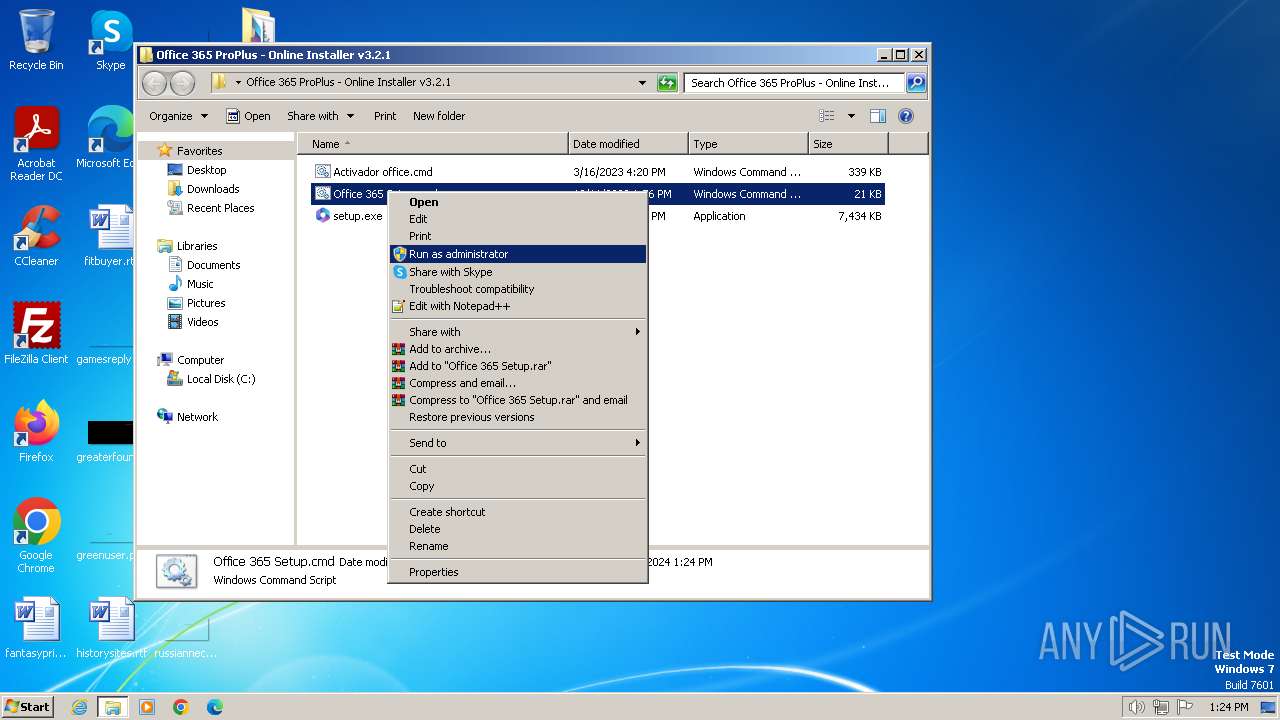
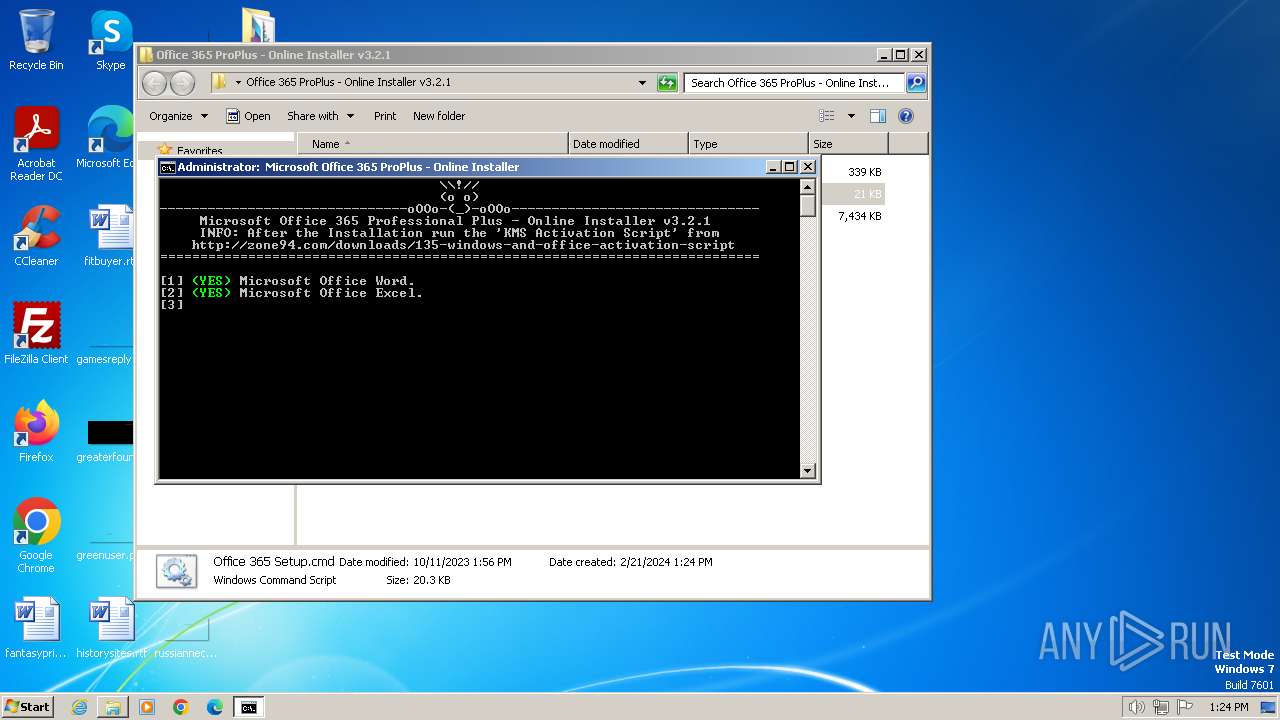
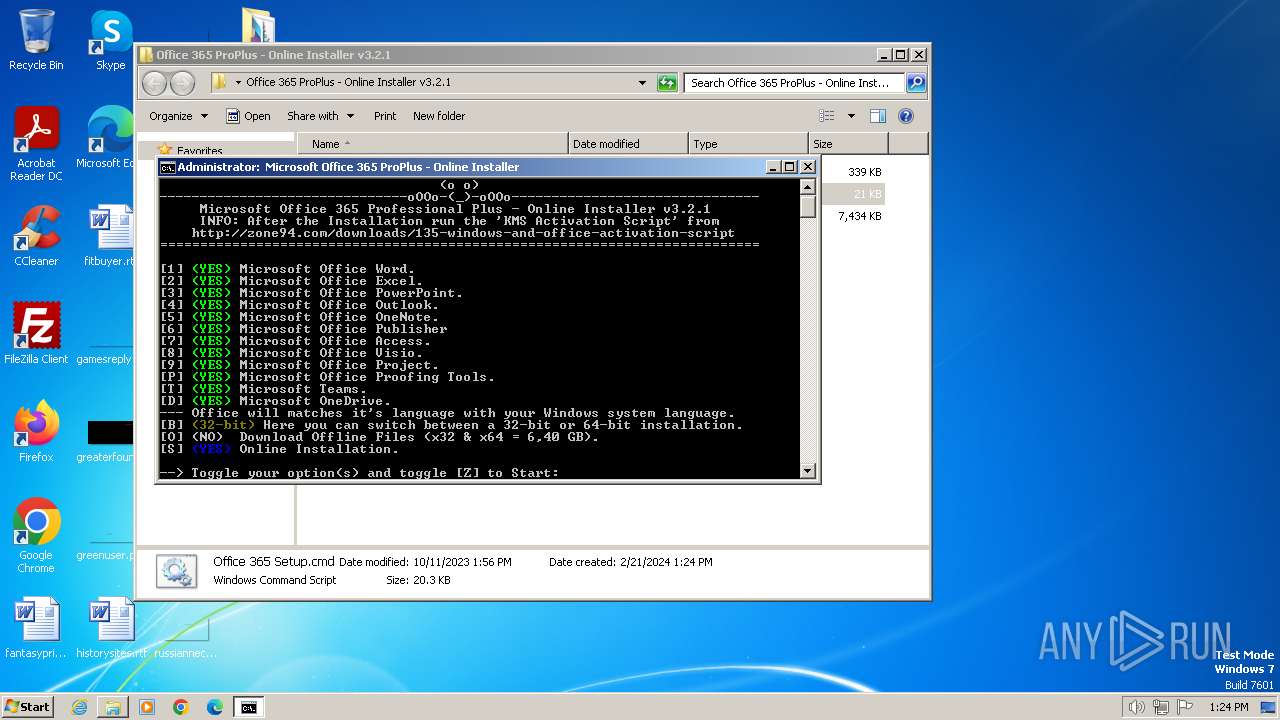
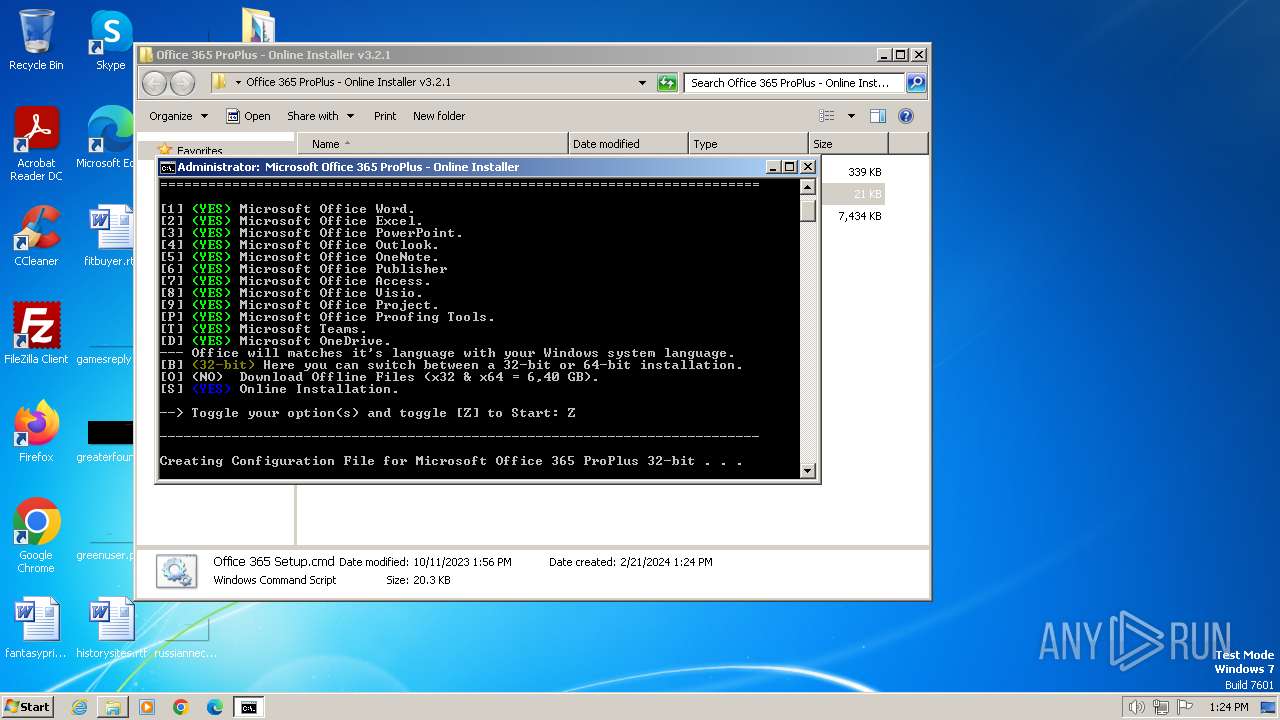
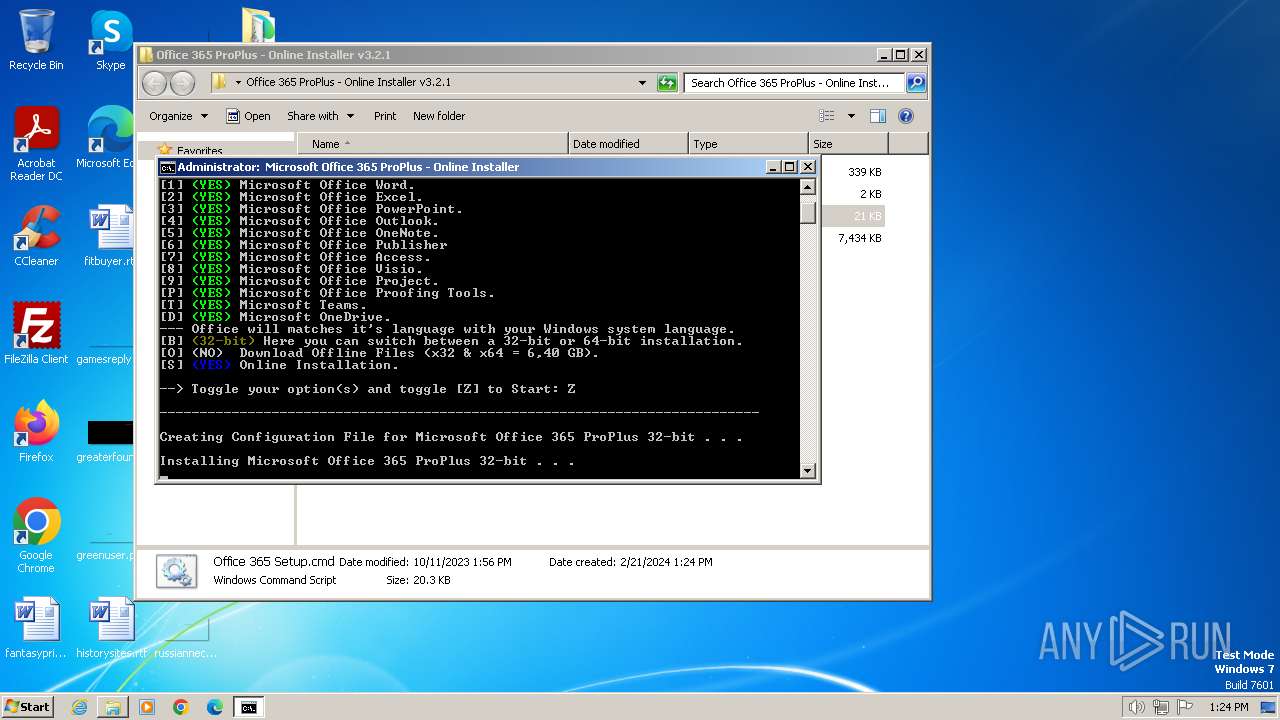
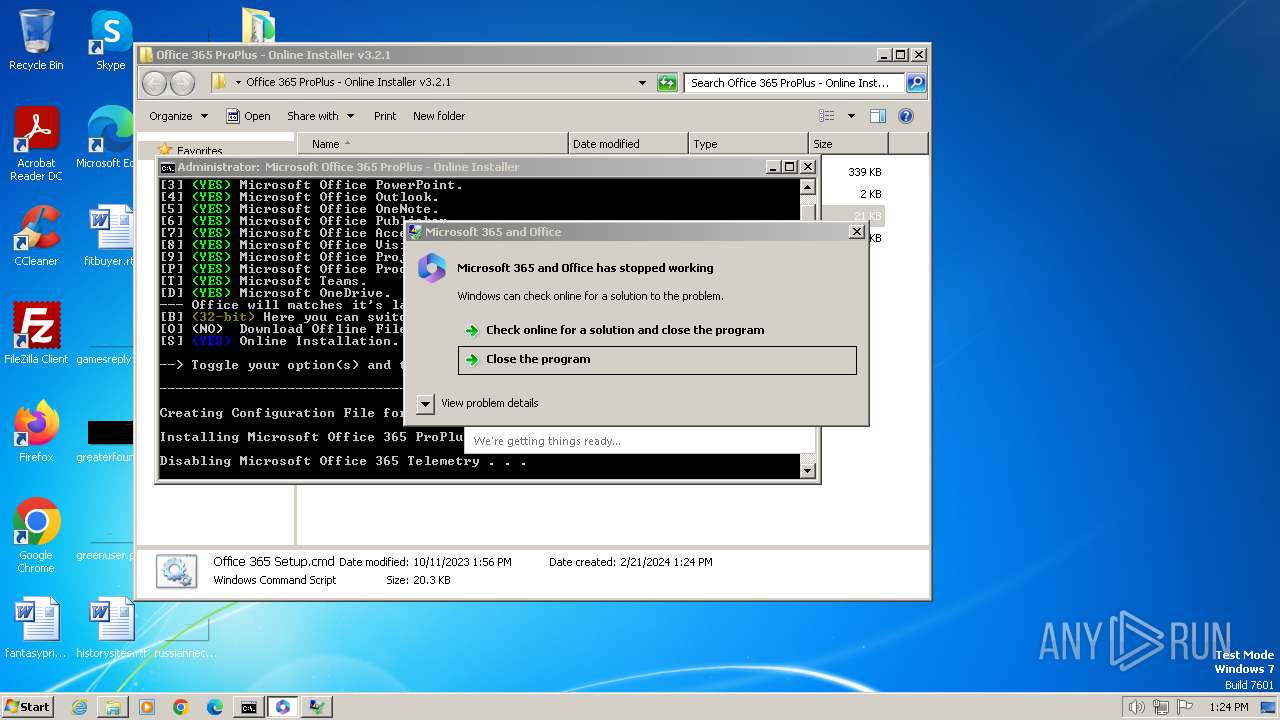
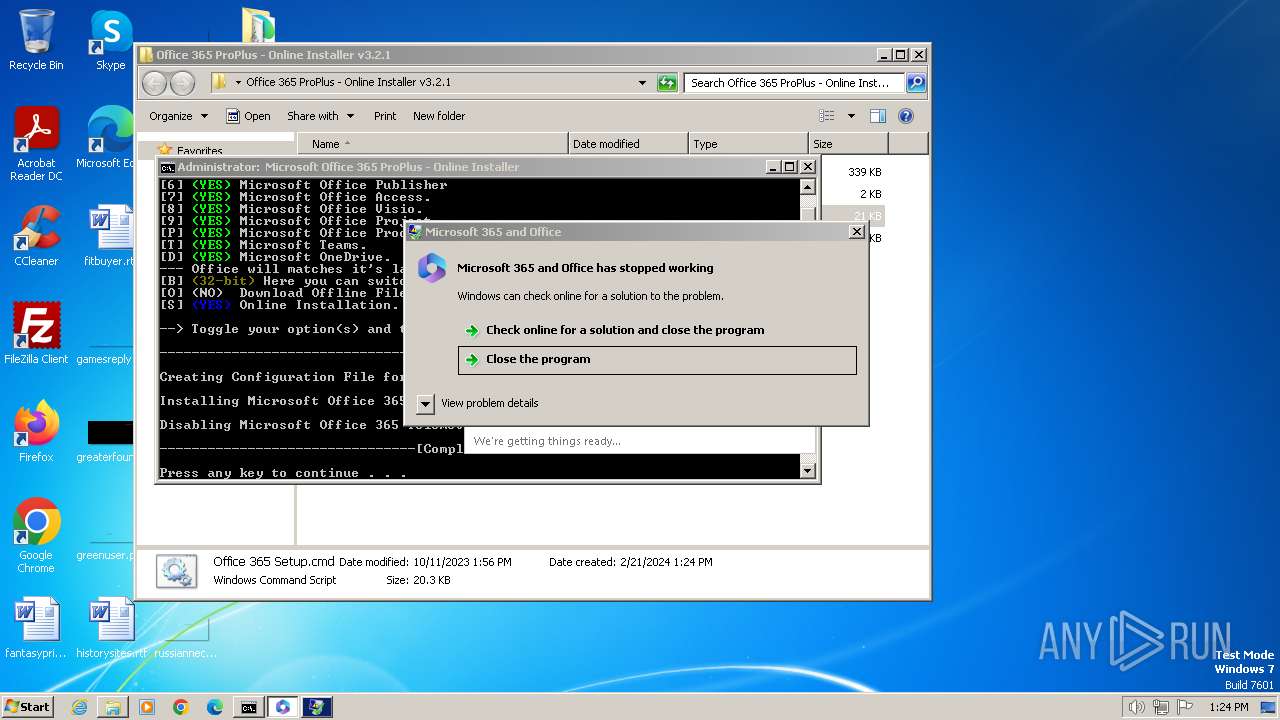
| File name: | Office 365 ProPlus - Online Installer v3.2.1.rar |
| Full analysis: | https://app.any.run/tasks/7ece6027-54f4-44d6-97a5-b6d650ec731a |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2024, 13:24:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1499EF40943FBC78E65B956F0F540F69 |
| SHA1: | 46439B684AA129A205B304D4829772AE5ADF77E7 |
| SHA256: | 947FD5718E9809622588285036E7132B6F27D831F70621E292813AE65C499BED |
| SSDEEP: | 98304:Q+Jvurmp6YKOHnslbosGM+kzO1vuvbWMf6g9HzolrpMyqfFkOeX3gs9dLeTfPiZF:ENNR8 |
MALICIOUS
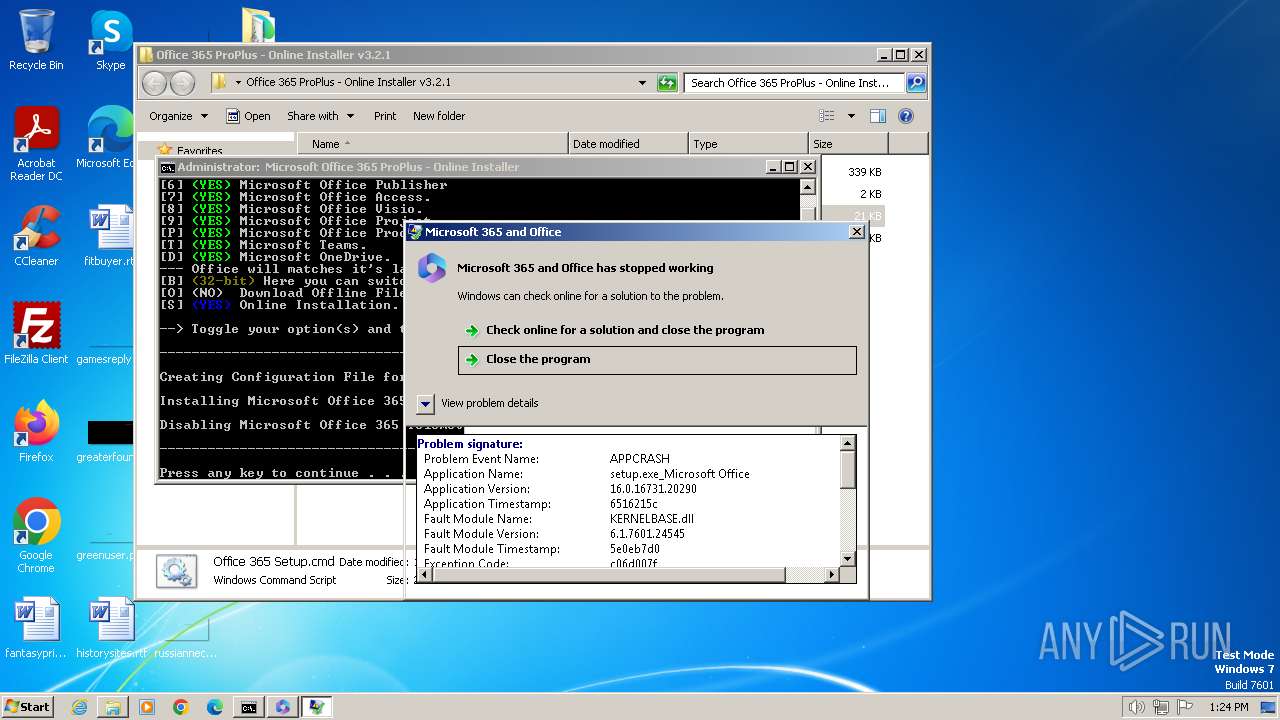
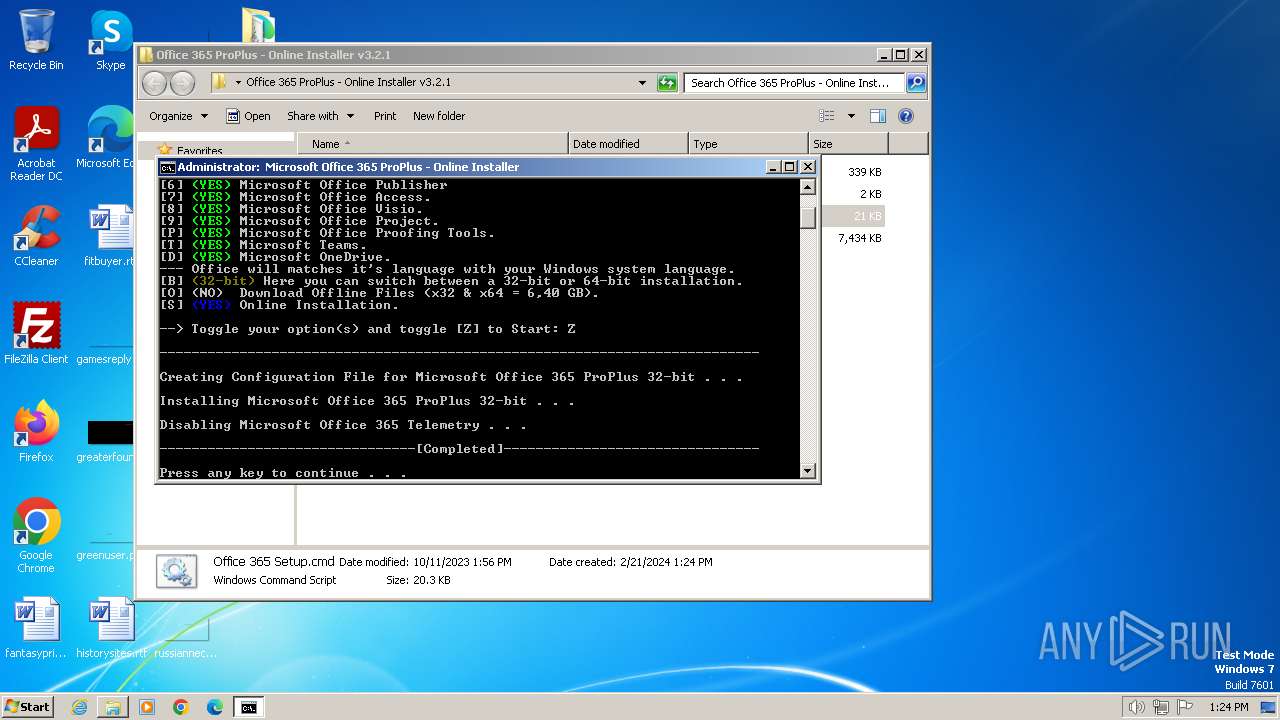
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1384)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1384)
Application launched itself
- cmd.exe (PID: 4008)
- cmd.exe (PID: 2292)
- cmd.exe (PID: 3276)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 2000)
- cmd.exe (PID: 2724)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 2592)
- cmd.exe (PID: 2804)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 1928)
- cmd.exe (PID: 3680)
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2668)
Starts application with an unusual extension
- cmd.exe (PID: 1040)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4008)
- cmd.exe (PID: 3276)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 2292)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 2000)
- cmd.exe (PID: 2804)
- cmd.exe (PID: 2592)
- cmd.exe (PID: 2724)
- cmd.exe (PID: 3680)
- cmd.exe (PID: 1928)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 2668)
- cmd.exe (PID: 3984)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1040)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1040)
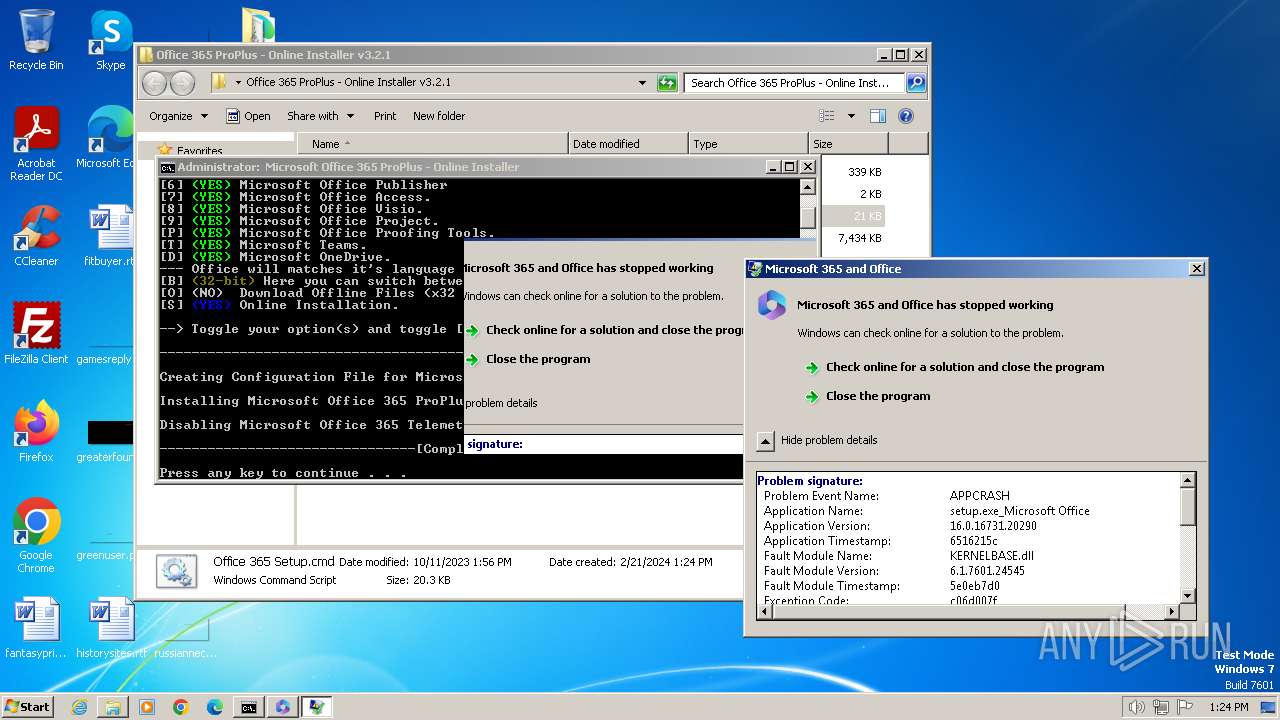
Starts a Microsoft application from unusual location
- setup.exe (PID: 2808)
Reads settings of System Certificates
- setup.exe (PID: 2808)
Reads security settings of Internet Explorer
- setup.exe (PID: 2808)
Reads the Internet Settings
- setup.exe (PID: 2808)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1040)
INFO
Checks supported languages
- chcp.com (PID: 3428)
- setup.exe (PID: 2808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1384)
Manual execution by a user
- cmd.exe (PID: 1040)
Process checks computer location settings
- setup.exe (PID: 2808)
Reads the machine GUID from the registry
- setup.exe (PID: 2808)
Reads Microsoft Office registry keys
- setup.exe (PID: 2808)
- reg.exe (PID: 3900)
Checks proxy server information
- setup.exe (PID: 2808)
Reads the software policy settings
- setup.exe (PID: 2808)
Reads the computer name
- setup.exe (PID: 2808)
Creates files or folders in the user directory
- setup.exe (PID: 2808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
114
Monitored processes
69
Malicious processes
2
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | C:\Windows\system32\cmd.exe /S /D /c" Echo PROMPT $H " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 448 | ping -n 3 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 480 | FindStr /l /i "(YES)" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | FindStr /l /i /b /p /a:0a /s /c:"_" ""(YES)"" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 712 | C:\Windows\system32\cmd.exe /S /D /c" Echo PROMPT $H " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 748 | "CMD" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 796 | "CMD" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 844 | "CMD" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 848 | C:\Windows\system32\cmd.exe /S /D /c" Echo PROMPT $H " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 984 | ping -n 3 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
10 184
Read events
10 084
Write events
91
Delete events
9
Modification events
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Office 365 ProPlus - Online Installer v3.2.1.rar | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1384 | WinRAR.exe | C:\Users\admin\Desktop\Office 365 ProPlus - Online Installer v3.2.1\Activador office.cmd | text | |
MD5:99AE4D160CE5C07CD5A88CFF6668C41C | SHA256:72D127C454C9426085CFD7D50DDFE81A96A6BD110B76DEB41A1246EB593FC2B2 | |||
| 1384 | WinRAR.exe | C:\Users\admin\Desktop\Office 365 ProPlus - Online Installer v3.2.1\setup.exe | executable | |
MD5:DB64720421A8002939227A173AB7A570 | SHA256:74B91E528ED9F80BF8A799B42045B8C9BB6758CDE2C5A6EFB2BDA387B3EC0071 | |||
| 1040 | cmd.exe | C:\Users\admin\AppData\Local\Temp\_(32-bit)\(32-bit) | binary | |
MD5:B14A7B8059D9C055954C92674CE60032 | SHA256:— | |||
| 2808 | setup.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\4542AFB8-B105-4AB8-8B56-6A963503C7FC | xml | |
MD5:0D0E891414F24EA84F694A7396BF21BE | SHA256:F561348717DA0B88EBB2AF9FEE7999A77FCBED8B22E89910E7EB18821F7996A2 | |||
| 1384 | WinRAR.exe | C:\Users\admin\Desktop\Office 365 ProPlus - Online Installer v3.2.1\Office 365 Setup.cmd | text | |
MD5:205430E5A831F37C417E2FD9CED824F1 | SHA256:5E431E9247A3F872B658B83E68335F2CC6A45EE3183813226697C74D56E4A8FC | |||
| 1040 | cmd.exe | C:\Users\admin\Desktop\Office 365 ProPlus - Online Installer v3.2.1\Office 365 Setup Config.xml | text | |
MD5:78F4E24C56550AB2621EE652849786E6 | SHA256:A77144AA552B42F5C843FEC95EDB9629E90DB2797897DA1DC27B67918D3D8AA6 | |||
| 1040 | cmd.exe | C:\Users\admin\AppData\Local\Temp\_(YES)\(YES) | binary | |
MD5:B14A7B8059D9C055954C92674CE60032 | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
13
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2808 | setup.exe | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
1360 | svchost.exe | 20.42.73.28:443 | vortex-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
vortex-win.data.microsoft.com |
| whitelisted |