| File name: | F.A.Q[2021.11.17_21-03].xlsb |
| Full analysis: | https://app.any.run/tasks/bb152a3c-ead3-413d-8259-18229c536efa |
| Verdict: | Malicious activity |
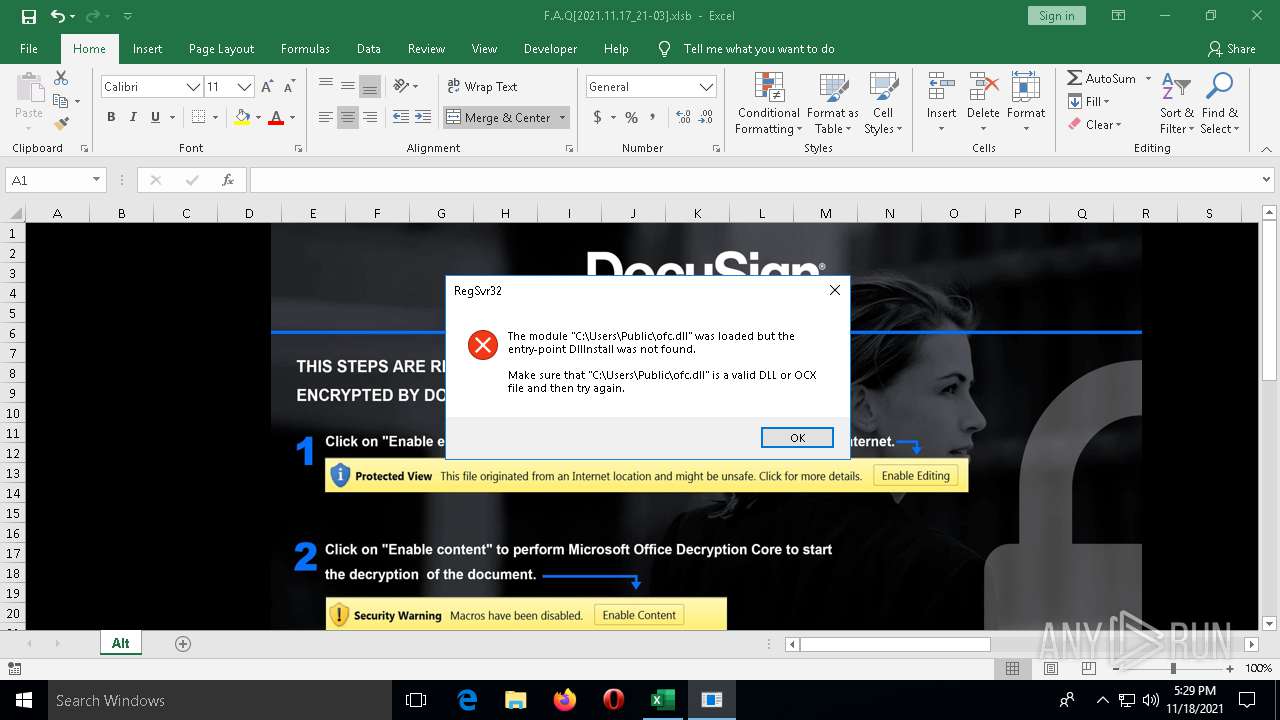
| Threats: | IcedID is a banking trojan-type malware which allows attackers to utilize it to steal banking credentials of the victims. IcedID aka BokBot mainly targets businesses and steals payment information, it also acts as a loader and can deliver another viruses or download additional modules. |
| Analysis date: | November 18, 2021, 17:28:41 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 33131357D897AA065D8220FD159733D4 |
| SHA1: | 7C5793AD1DCD2594C803C991F6CE0EF4A75E78D8 |
| SHA256: | 947A442E30A4A5BF3B19A691AE7198B3BBE2517BBF101E7820A16AF9F69287FE |
| SSDEEP: | 6144:5mMkBPtds3GmMXoJbhbjcY/l+Q0CXYfLkZQyf1m0ZwzTDar7AhntI9:gns3GmMXIBZ/8QqLkJmjarUhn+9 |
MALICIOUS
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 1224)
Registers / Runs the DLL via REGSVR32.EXE
- EXCEL.EXE (PID: 1224)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 5432)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 1224)
ICEDID was detected
- regsvr32.exe (PID: 5432)
SUSPICIOUS
Drops a file with a compile date too recent
- EXCEL.EXE (PID: 1224)
Reads the date of Windows installation
- EXCEL.EXE (PID: 1224)
Executed via COM
- rundll32.exe (PID: 5908)
INFO
Checks supported languages
- EXCEL.EXE (PID: 1224)
- regsvr32.exe (PID: 5432)
Reads the computer name
- EXCEL.EXE (PID: 1224)
- regsvr32.exe (PID: 5432)
Creates files in the user directory
- EXCEL.EXE (PID: 1224)
Reads Environment values
- EXCEL.EXE (PID: 1224)
Reads the software policy settings
- EXCEL.EXE (PID: 1224)
- regsvr32.exe (PID: 5432)
Reads settings of System Certificates
- EXCEL.EXE (PID: 1224)
- regsvr32.exe (PID: 5432)
Scans artifacts that could help determine the target
- EXCEL.EXE (PID: 1224)
Checks Windows Trust Settings
- EXCEL.EXE (PID: 1224)
Reads CPU info
- EXCEL.EXE (PID: 1224)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 1224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsx | | | Excel Microsoft Office Open XML Format document (61.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (31.5) |
| .zip | | | ZIP compressed archive (7.2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x49c13349 |
| ZipCompressedSize: | 441 |
| ZipUncompressedSize: | 1506 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | Андрей Елисеев |
|---|
XML
| LastModifiedBy: | Mishel Brown |
|---|---|
| CreateDate: | 2021:02:03 15:28:44Z |
| ModifyDate: | 2021:11:18 10:01:44Z |
| Application: | Microsoft Excel |
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: |
|
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16.03 |
Total processes
101
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1224 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Downloads\F.A.Q[2021.11.17_21-03].xlsb" | C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 5432 | regsvr32 -e -n -i:"Microsoft" C:\Users\Public\ofc.dll | C:\WINDOWS\SYSTEM32\regsvr32.exe | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5908 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {3eef301f-b596-4c0b-bd92-013beafce793} -Embedding | C:\WINDOWS\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 270
Read events
9 071
Write events
181
Delete events
18
Modification events
| (PID) Process: | (1224) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000284FFA2E01000000000000000500000000000000 | |||
| (PID) Process: | (1224) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\EXCEL\1224 |
| Operation: | write | Name: | 0 |
Value: 0B0E107A1A7528D719094895F87F41E9AACCD7230046FBFA94B39C94F7EB016A0410240044FA5D64A89E01008500A907556E6B6E6F776E00 | |||
| (PID) Process: | (1224) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (1224) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (1224) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (1224) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (1224) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (1224) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (1224) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (1224) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
2
Suspicious files
6
Text files
5
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1224 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\CloudFonts\FangSong\29400494812.ttf | — | |
MD5:— | SHA256:— | |||
| 1224 | EXCEL.EXE | C:\Users\Public\ofc.dll | executable | |
MD5:— | SHA256:— | |||
| 1224 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\F.A.Q[2021.11.17_21-03].xlsb.LNK | lnk | |
MD5:— | SHA256:— | |||
| 1224 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:— | SHA256:— | |||
| 1224 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\.ses | text | |
MD5:— | SHA256:— | |||
| 1224 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\CO4CFRDU\file1[1].cms | executable | |
MD5:— | SHA256:— | |||
| 1224 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\6F7A9592-DCBD-469F-BA51-BAF1DCD6830E | xml | |
MD5:— | SHA256:— | |||
| 1224 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Excel\~ar5E9E.xar | document | |
MD5:— | SHA256:— | |||
| 1224 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\CatalogCacheMetaData.xml | xml | |
MD5:— | SHA256:— | |||
| 1224 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\CloudFonts\Univers\27605362331.ttf | odttf | |
MD5:04A1E93A61F71DA4AA62F50C4FE5EDF3 | SHA256:7F5401A4CBE3B419DF381523E9EE6C75E0A553F4F7B566F1C5ACBEC936B4830E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
51
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1224 | EXCEL.EXE | GET | 304 | 20.54.89.106:443 | https://sls.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.16299.0/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.16299.98&MK=DELL&MD=DELL | US | — | — | whitelisted |
1224 | EXCEL.EXE | GET | 200 | 51.124.78.146:443 | https://settings-win.data.microsoft.com/settings/v2.0/WSD/WaaSAssessment?os=Windows&osVer=10.0.16299.431.amd64fre.rs3_release_svc_escrow.180502-&ring=Retail&sku=48&deviceClass=Windows.Desktop&locale=en-US&deviceId=BAD99146-31D3-4EC6-A1A4-BE76F32BA5D4&BranchReadinessLevel=CBB&ProcessorIdentifier=AMD64%20Family%206%20Model%2014%20Stepping%203&CurrentBranch=rs3_release_svc_escrow&OEMModel=DELL&FlightRing=Retail&AttrDataVer=43&InstallLanguage=en-US&OSUILocale=en-US&OEMModelBaseBoard=&FirmwareVersion=A.40&InstallationType=Client&FlightingBranchName=&ServicingBranch=CBB&OSSkuId=48&App=WaaSAssessment&InstallDate=1523361072&ProcessorManufacturer=AuthenticAMD&OEMName_Uncleaned=DELL&AppVer=10.0&OSArchitecture=AMD64&HonorWUfBDeferrals=1&UpdateManagementGroup=2&IsDeviceRetailDemo=0&HidOverGattReg=C%3A%5CWINDOWS%5CSystem32%5CDriverStore%5CFileRepository%5Chidbthle.inf_amd64_55f7f576bf549669%5CMicrosoft.Bluetooth.Profiles.HidOverGatt.dll&IsFlightingEnabled=0&DeferQualityUpdatePeriodInDays=0&TelemetryLevel=1&DefaultUserRegion=244&DeferFeatureUpdatePeriodInDays=30&OSVersion=10.0.16299.431&DeviceFamily=Windows.Desktop | GB | binary | 1.01 Kb | whitelisted |
1224 | EXCEL.EXE | GET | 200 | 162.241.224.176:443 | https://yfo.yag.mybluehost.me/wp-content/uploads/2020/08/file1.cms | US | executable | 375 Kb | malicious |
1224 | EXCEL.EXE | GET | 200 | 51.124.78.146:443 | https://settings-win.data.microsoft.com/settings/v2.0/WSD/WaaSAssessment?os=Windows&osVer=10.0.16299.431.amd64fre.rs3_release_svc_escrow.180502-&ring=Retail&sku=48&deviceClass=Windows.Desktop&locale=en-US&deviceId=BAD99146-31D3-4EC6-A1A4-BE76F32BA5D4&BranchReadinessLevel=CBB&ProcessorIdentifier=AMD64%20Family%206%20Model%2014%20Stepping%203&CurrentBranch=rs3_release_svc_escrow&OEMModel=DELL&FlightRing=Retail&AttrDataVer=43&InstallLanguage=en-US&OSUILocale=en-US&OEMModelBaseBoard=&FirmwareVersion=A.40&InstallationType=Client&FlightingBranchName=&ServicingBranch=CBB&OSSkuId=48&App=WaaSAssessment&InstallDate=1523361072&ProcessorManufacturer=AuthenticAMD&OEMName_Uncleaned=DELL&AppVer=10.0&OSArchitecture=AMD64&HonorWUfBDeferrals=1&UpdateManagementGroup=2&IsDeviceRetailDemo=0&HidOverGattReg=C%3A%5CWINDOWS%5CSystem32%5CDriverStore%5CFileRepository%5Chidbthle.inf_amd64_55f7f576bf549669%5CMicrosoft.Bluetooth.Profiles.HidOverGatt.dll&IsFlightingEnabled=0&DeferQualityUpdatePeriodInDays=0&TelemetryLevel=1&DefaultUserRegion=244&DeferFeatureUpdatePeriodInDays=30&OSVersion=10.0.16299.431&DeviceFamily=Windows.Desktop | GB | binary | 1.01 Kb | whitelisted |
1224 | EXCEL.EXE | GET | 200 | 51.124.78.146:443 | https://settings-win.data.microsoft.com/settings/v2.0/WSD/WaaSAssessment?os=Windows&osVer=10.0.16299.431.amd64fre.rs3_release_svc_escrow.180502-&ring=Retail&sku=48&deviceClass=Windows.Desktop&locale=en-US&deviceId=BAD99146-31D3-4EC6-A1A4-BE76F32BA5D4&BranchReadinessLevel=CBB&ProcessorIdentifier=AMD64%20Family%206%20Model%2014%20Stepping%203&CurrentBranch=rs3_release_svc_escrow&OEMModel=DELL&FlightRing=Retail&AttrDataVer=43&InstallLanguage=en-US&OSUILocale=en-US&OEMModelBaseBoard=&FirmwareVersion=A.40&InstallationType=Client&FlightingBranchName=&ServicingBranch=CBB&OSSkuId=48&App=WaaSAssessment&InstallDate=1523361072&ProcessorManufacturer=AuthenticAMD&OEMName_Uncleaned=DELL&AppVer=10.0&OSArchitecture=AMD64&HonorWUfBDeferrals=1&UpdateManagementGroup=2&IsDeviceRetailDemo=0&HidOverGattReg=C%3A%5CWINDOWS%5CSystem32%5CDriverStore%5CFileRepository%5Chidbthle.inf_amd64_55f7f576bf549669%5CMicrosoft.Bluetooth.Profiles.HidOverGatt.dll&IsFlightingEnabled=0&DeferQualityUpdatePeriodInDays=0&TelemetryLevel=1&DefaultUserRegion=244&DeferFeatureUpdatePeriodInDays=30&OSVersion=10.0.16299.431&DeviceFamily=Windows.Desktop | GB | binary | 1.01 Kb | whitelisted |
1224 | EXCEL.EXE | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v2/Office/excel/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=excel&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7b28751A7A-19D7-4809-95F8-7F41E9AACCD7%7d&LabMachine=false | US | text | 92.8 Kb | malicious |
1224 | EXCEL.EXE | GET | 200 | 51.124.78.146:443 | https://settings-win.data.microsoft.com/settings/v2.0/WSD/WaaSAssessment?os=Windows&osVer=10.0.16299.431.amd64fre.rs3_release_svc_escrow.180502-&ring=Retail&sku=48&deviceClass=Windows.Desktop&locale=en-US&deviceId=BAD99146-31D3-4EC6-A1A4-BE76F32BA5D4&BranchReadinessLevel=CBB&ProcessorIdentifier=AMD64%20Family%206%20Model%2014%20Stepping%203&CurrentBranch=rs3_release_svc_escrow&OEMModel=DELL&FlightRing=Retail&AttrDataVer=43&InstallLanguage=en-US&OSUILocale=en-US&OEMModelBaseBoard=&FirmwareVersion=A.40&InstallationType=Client&FlightingBranchName=&ServicingBranch=CBB&OSSkuId=48&App=WaaSAssessment&InstallDate=1523361072&ProcessorManufacturer=AuthenticAMD&OEMName_Uncleaned=DELL&AppVer=10.0&OSArchitecture=AMD64&HonorWUfBDeferrals=1&UpdateManagementGroup=2&IsDeviceRetailDemo=0&HidOverGattReg=C%3A%5CWINDOWS%5CSystem32%5CDriverStore%5CFileRepository%5Chidbthle.inf_amd64_55f7f576bf549669%5CMicrosoft.Bluetooth.Profiles.HidOverGatt.dll&IsFlightingEnabled=0&DeferQualityUpdatePeriodInDays=0&TelemetryLevel=1&DefaultUserRegion=244&DeferFeatureUpdatePeriodInDays=30&OSVersion=10.0.16299.431&DeviceFamily=Windows.Desktop | GB | binary | 1.01 Kb | whitelisted |
1224 | EXCEL.EXE | GET | 200 | 51.124.78.146:443 | https://settings-win.data.microsoft.com/settings/v2.0/wsd/muse?os=Windows&osVer=10.0.16299.431.amd64fre.rs3_release_svc_escrow.180502-1908&deviceId=bad99146-31d3-4ec6-a1a4-be76f32ba5d4&sampleId=95271487&deviceClass=Windows.Desktop&sku=48&locale=en-US&ring=Retail& | GB | binary | 682 b | whitelisted |
1224 | EXCEL.EXE | GET | 200 | 51.124.78.146:443 | https://settings-win.data.microsoft.com/settings/v2.0/WSD/WaaSAssessment?os=Windows&osVer=10.0.16299.431.amd64fre.rs3_release_svc_escrow.180502-&ring=Retail&sku=48&deviceClass=Windows.Desktop&locale=en-US&deviceId=BAD99146-31D3-4EC6-A1A4-BE76F32BA5D4&BranchReadinessLevel=CBB&ProcessorIdentifier=AMD64%20Family%206%20Model%2014%20Stepping%203&CurrentBranch=rs3_release_svc_escrow&OEMModel=DELL&FlightRing=Retail&AttrDataVer=43&InstallLanguage=en-US&OSUILocale=en-US&OEMModelBaseBoard=&FirmwareVersion=A.40&InstallationType=Client&FlightingBranchName=&ServicingBranch=CBB&OSSkuId=48&App=WaaSAssessment&InstallDate=1523361072&ProcessorManufacturer=AuthenticAMD&OEMName_Uncleaned=DELL&AppVer=10.0&OSArchitecture=AMD64&HonorWUfBDeferrals=1&UpdateManagementGroup=2&IsDeviceRetailDemo=0&HidOverGattReg=C%3A%5CWINDOWS%5CSystem32%5CDriverStore%5CFileRepository%5Chidbthle.inf_amd64_55f7f576bf549669%5CMicrosoft.Bluetooth.Profiles.HidOverGatt.dll&IsFlightingEnabled=0&DeferQualityUpdatePeriodInDays=0&TelemetryLevel=1&DefaultUserRegion=244&DeferFeatureUpdatePeriodInDays=30&OSVersion=10.0.16299.431&DeviceFamily=Windows.Desktop | GB | binary | 1.01 Kb | whitelisted |
5732 | sihclient.exe | GET | 200 | 2.21.143.74:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | der | 813 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5732 | sihclient.exe | 20.54.89.106:443 | — | — | US | whitelisted |
5732 | sihclient.exe | 92.123.194.162:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
1224 | EXCEL.EXE | 13.107.42.16:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
— | — | 20.54.89.106:443 | — | — | US | whitelisted |
1224 | EXCEL.EXE | 162.241.224.176:443 | yfo.yag.mybluehost.me | CyrusOne LLC | US | malicious |
628 | WaaSMedic.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | Microsoft Corporation | GB | whitelisted |
628 | WaaSMedic.exe | 20.73.194.208:443 | — | — | US | whitelisted |
1224 | EXCEL.EXE | 2.21.140.114:443 | fs.microsoft.com | Telia Company AB | — | suspicious |
2676 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | Microsoft Corporation | GB | whitelisted |
5432 | regsvr32.exe | 13.32.16.70:443 | aws.amazon.com | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| malicious |
yfo.yag.mybluehost.me |
| malicious |
settings-win.data.microsoft.com |
| whitelisted |
time.windows.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
insiderservice.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5432 | regsvr32.exe | A Network Trojan was detected | ET TROJAN Win32/IcedID Request Cookie |