| File name: | mRemoteNG.exe |
| Full analysis: | https://app.any.run/tasks/ff590e34-4668-47b9-84e4-9b2306aa4a31 |
| Verdict: | Malicious activity |
| Analysis date: | July 09, 2024, 14:31:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 232A562B71FB17C06BBE72C11181E7D4 |
| SHA1: | 4A8BA46820A4E36E77ECCEBF13B7FEDA833F5681 |
| SHA256: | 9476FE1896669163248747785FA053ACA7284949945ABD37C59DAE4184760D58 |
| SSDEEP: | 24576:VmzVqZ5uXyJ/MS0HNNIFb9SvEqyMOJlXcTJwTK6EjgjV:CgzbJ/MS0HNNIFb8vNyMOJlXcdwTZGyV |
MALICIOUS
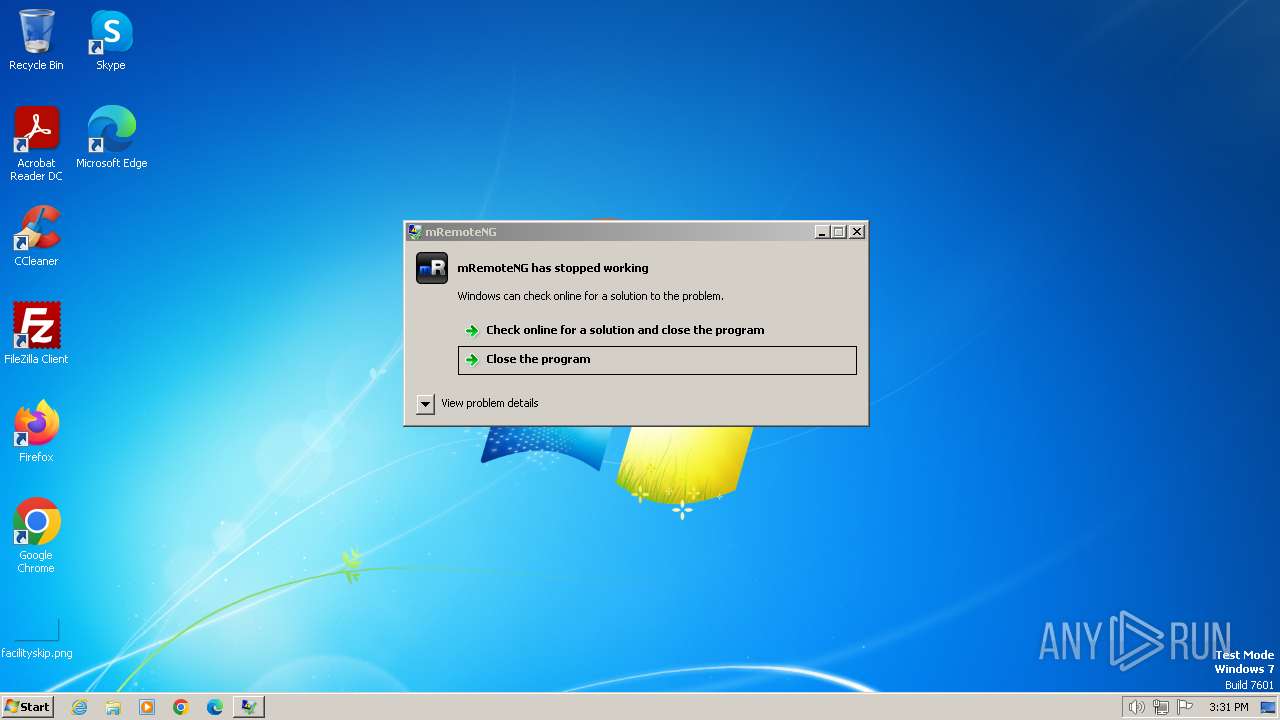
Drops the executable file immediately after the start
- mRemoteNG.exe (PID: 3344)
SUSPICIOUS
Reads security settings of Internet Explorer
- mRemoteNG.exe (PID: 3344)
Reads the Internet Settings
- mRemoteNG.exe (PID: 3344)
Checks Windows Trust Settings
- mRemoteNG.exe (PID: 3344)
Reads settings of System Certificates
- mRemoteNG.exe (PID: 3344)
INFO
Reads the computer name
- mRemoteNG.exe (PID: 3344)
Checks supported languages
- mRemoteNG.exe (PID: 3344)
Reads the machine GUID from the registry
- mRemoteNG.exe (PID: 3344)
Reads the software policy settings
- mRemoteNG.exe (PID: 3344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (49.4) |
|---|---|---|
| .scr | | | Windows screen saver (23.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (11.7) |
| .exe | | | Win32 Executable (generic) (8) |
| .exe | | | Generic Win/DOS Executable (3.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:04:12 13:42:21+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1485312 |
| InitializedDataSize: | 65024 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16c96e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.76.20.24669 |
| ProductVersionNumber: | 1.76.20.24669 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Multi-protocol remote connections manager |
| CompanyName: | - |
| FileDescription: | mRemoteNG |
| FileVersion: | 1.76.20.24669 |
| InternalName: | mRemoteNG.exe |
| LegalCopyright: | Copyright © 2019 mRemoteNG Dev Team; 2010-2013 Riley McArdle; 2007-2009 Felix Deimel |
| LegalTrademarks: | - |
| OriginalFileName: | mRemoteNG.exe |
| ProductName: | mRemoteNG |
| ProductVersion: | 1.76.20.24669 |
| AssemblyVersion: | 1.76.20.24669 |
Total processes
39
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3344 | "C:\Users\admin\AppData\Local\Temp\mRemoteNG.exe" | C:\Users\admin\AppData\Local\Temp\mRemoteNG.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: mRemoteNG Version: 1.76.20.24669 Modules
| |||||||||||||||
Total events
3 170
Read events
3 148
Write events
22
Delete events
0
Modification events
| (PID) Process: | (3344) mRemoteNG.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3344) mRemoteNG.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3344) mRemoteNG.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3344) mRemoteNG.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3344) mRemoteNG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
11
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3272 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1060 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
watson.microsoft.com |
| whitelisted |