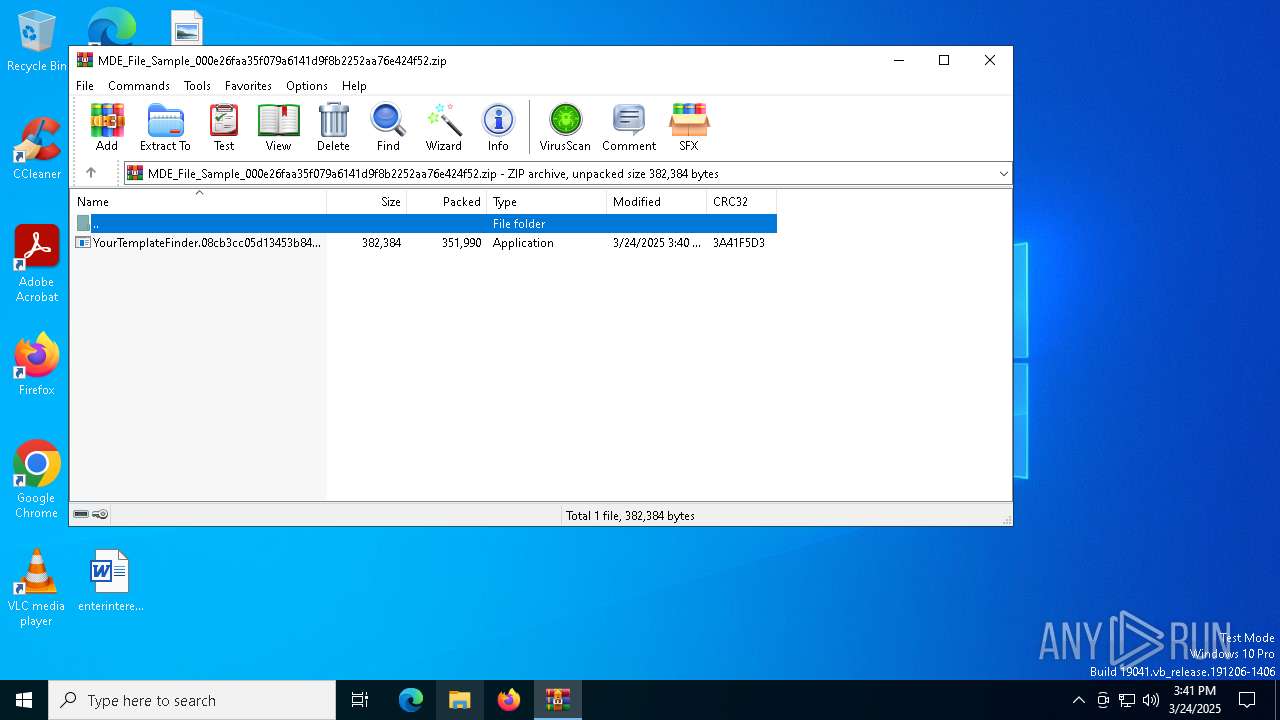
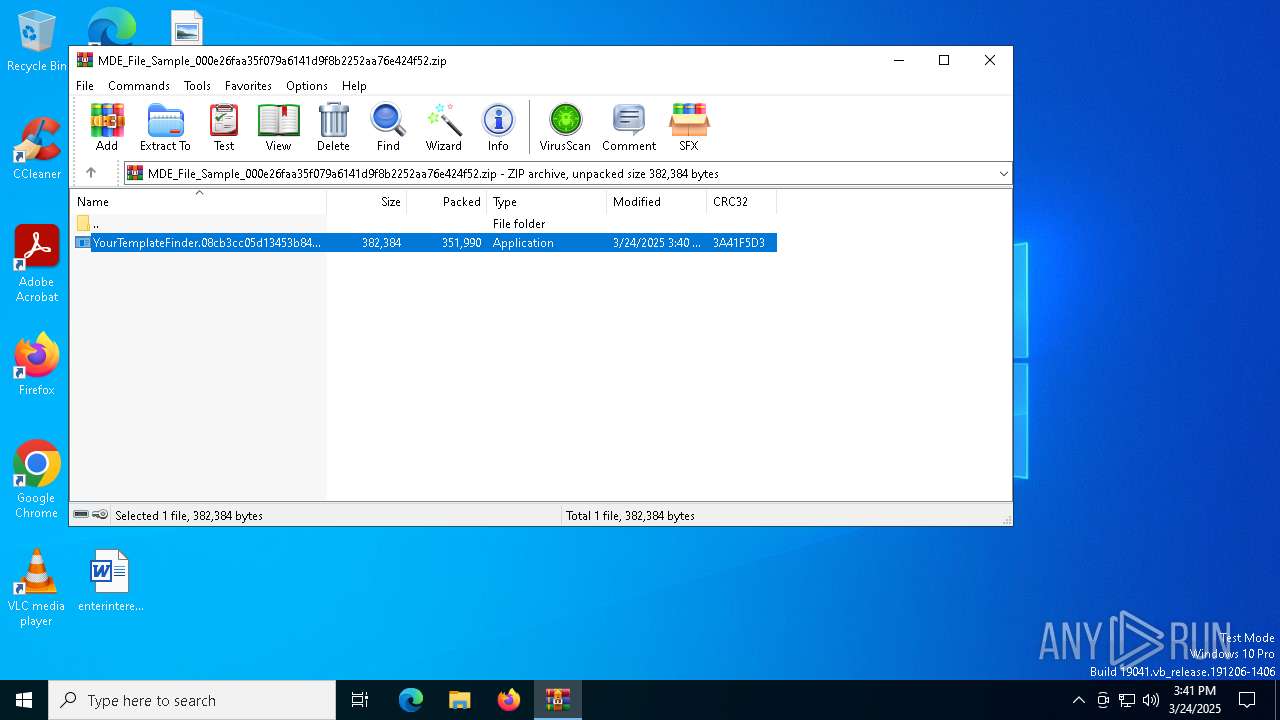
| File name: | MDE_File_Sample_000e26faa35f079a6141d9f8b2252aa76e424f52.zip |
| Full analysis: | https://app.any.run/tasks/daf7b802-29ea-4e54-a233-23e5b75cdf6d |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 15:41:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 2771F0037986334D29C19F5902C02F6A |
| SHA1: | AEEED2022788C952045284C11AF764523F1506AA |
| SHA256: | 944F5BCB29044ECA1DCB303AEFB92F2A5F2B05EC9E0A44F74E4438ABC683C6C0 |
| SSDEEP: | 12288:XISI2nc+csB34Ka0wWSiybJ/nUvehM8n8UJVbL:XISI2ntcAoKntSxJ/dC8n8UJVbL |
MALICIOUS
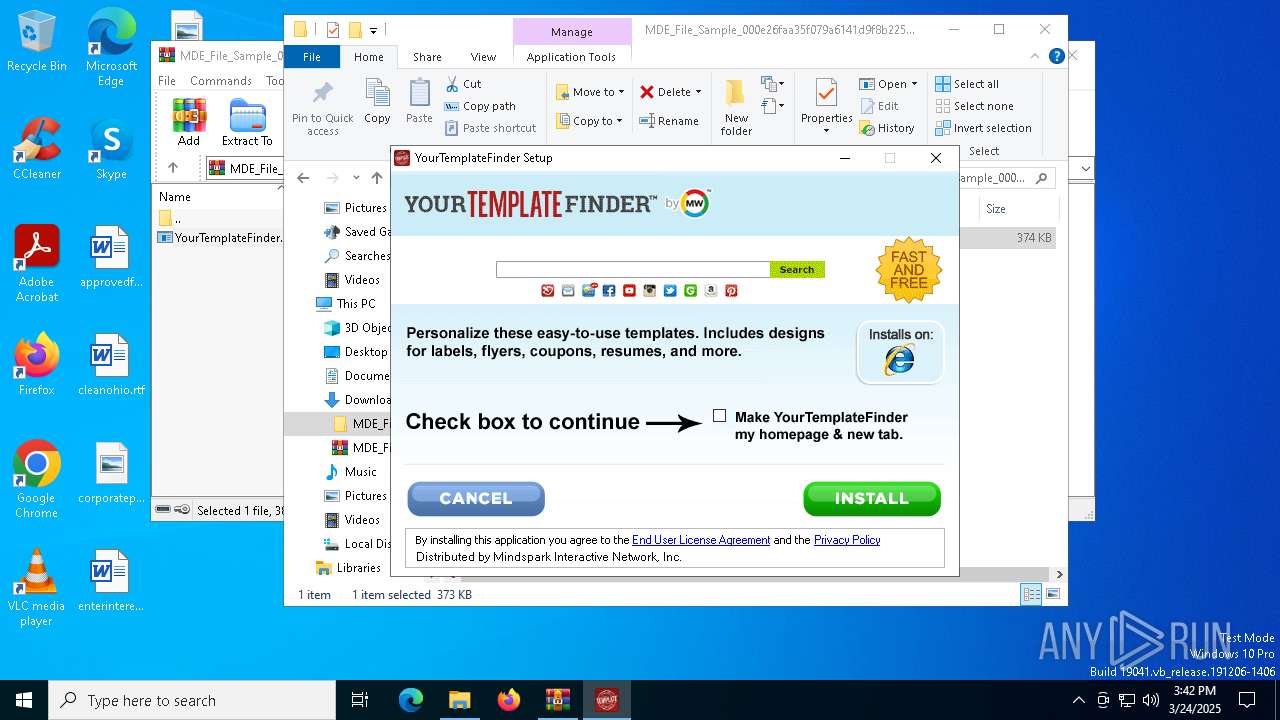
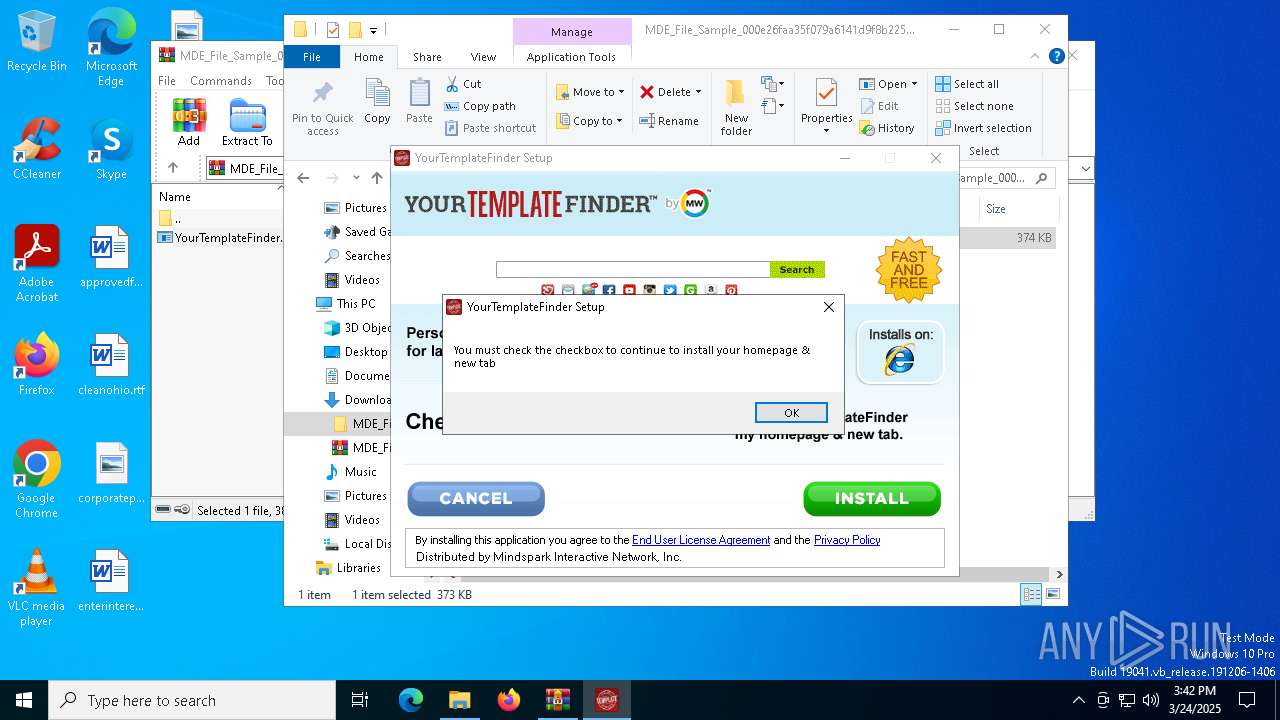
Executing a file with an untrusted certificate
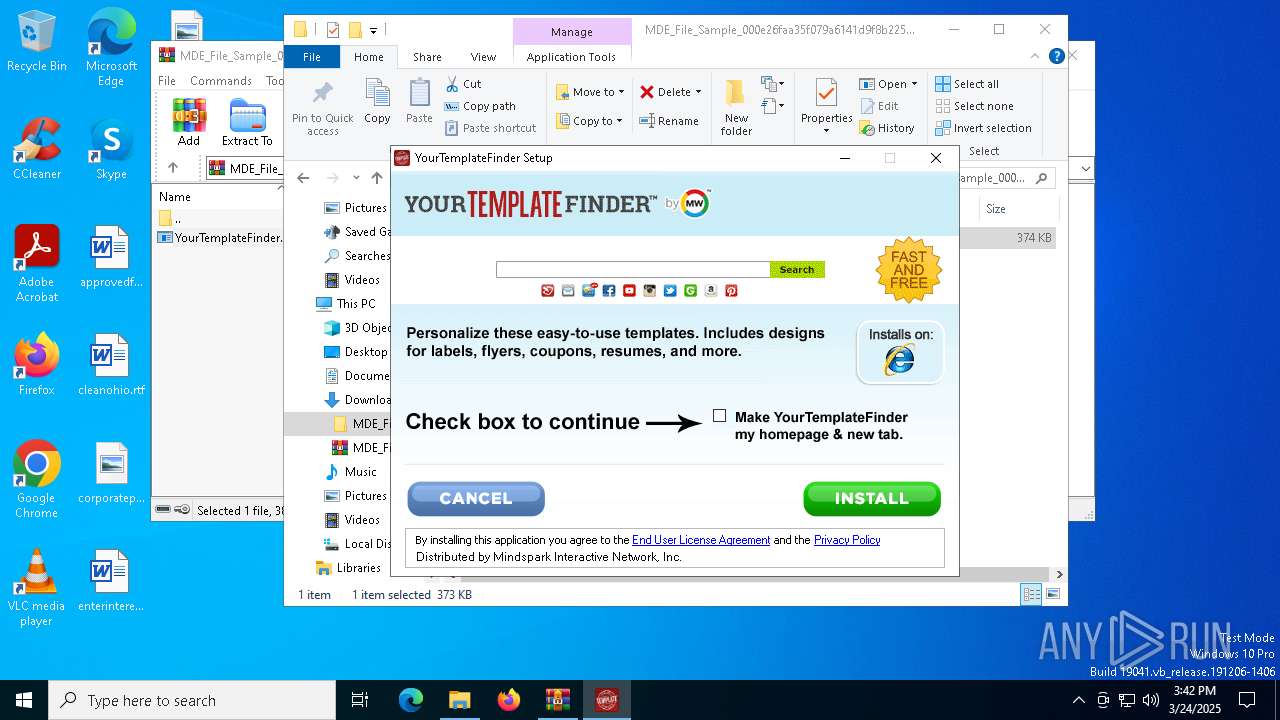
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
Executable content was dropped or overwritten
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
The process creates files with name similar to system file names
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
Reads security settings of Internet Explorer
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6404)
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6404)
Reads the software policy settings
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
Create files in a temporary directory
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
Manual execution by a user
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
Reads the machine GUID from the registry
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
Creates files or folders in the user directory
- YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe (PID: 3956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:24 15:40:44 |
| ZipCRC: | 0x3a41f5d3 |
| ZipCompressedSize: | 351990 |
| ZipUncompressedSize: | 382384 |
| ZipFileName: | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe |
Total processes
145
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
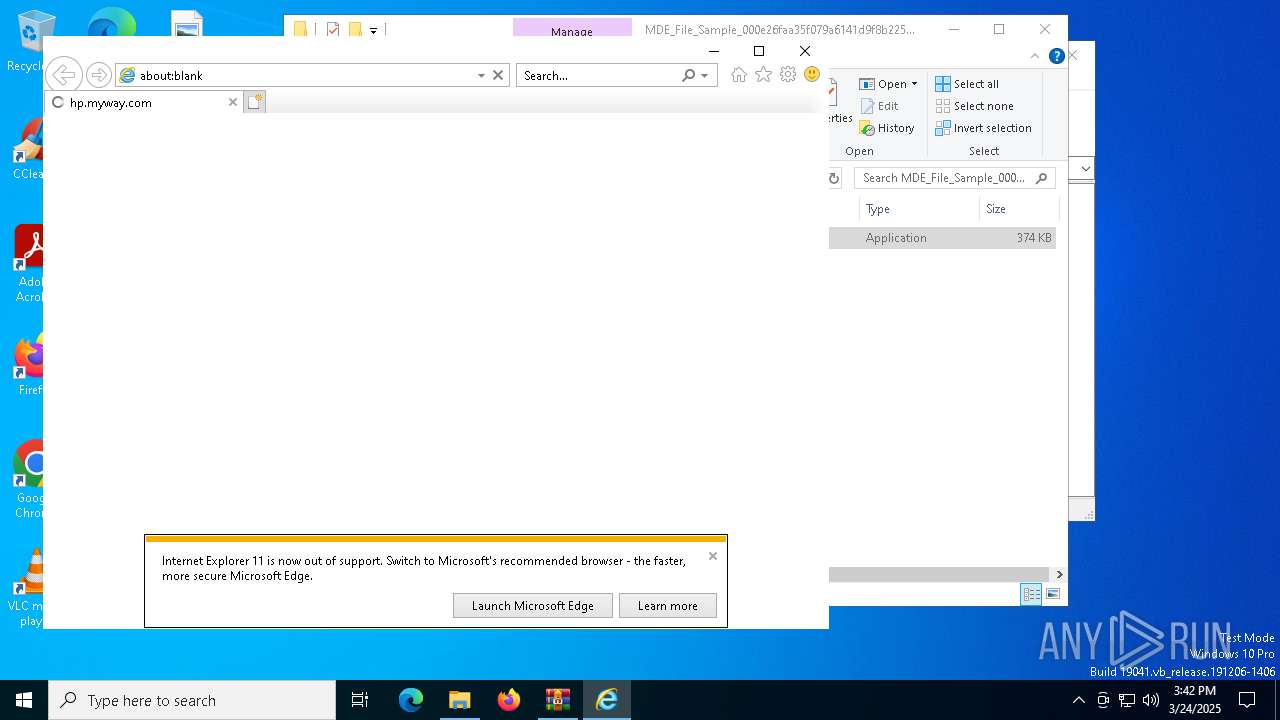
| 856 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:7148 CREDAT:9474 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
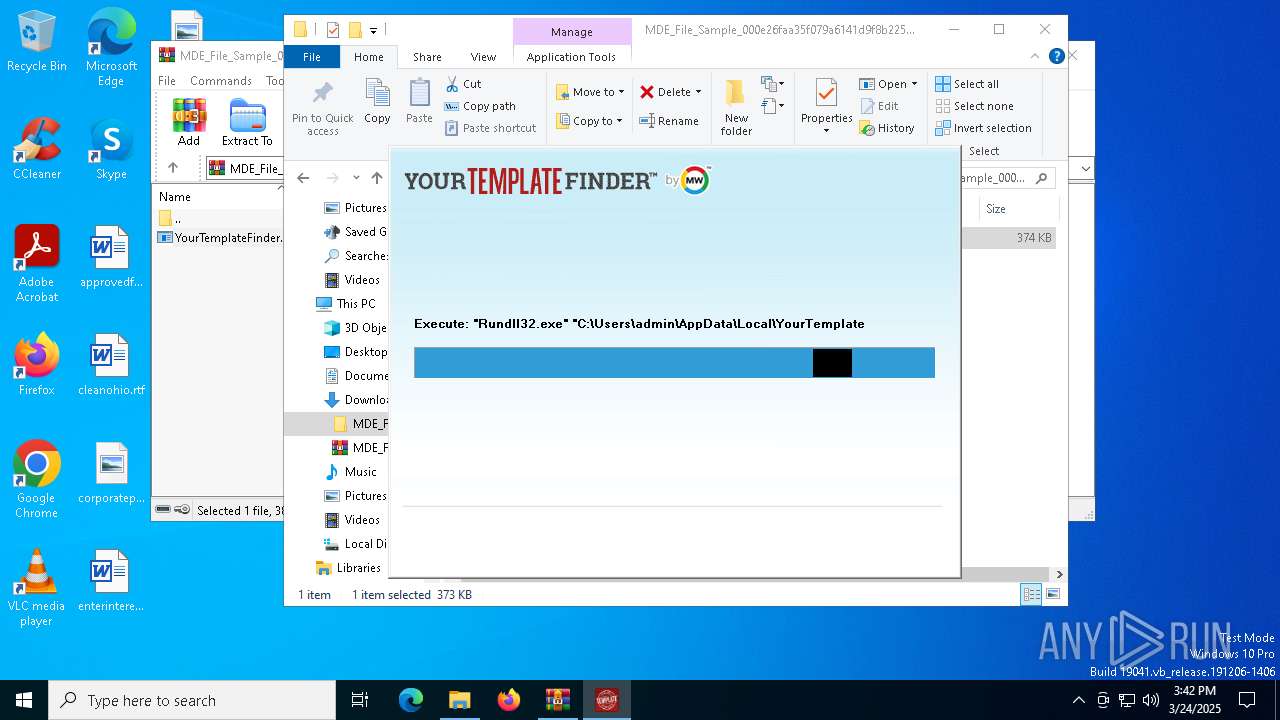
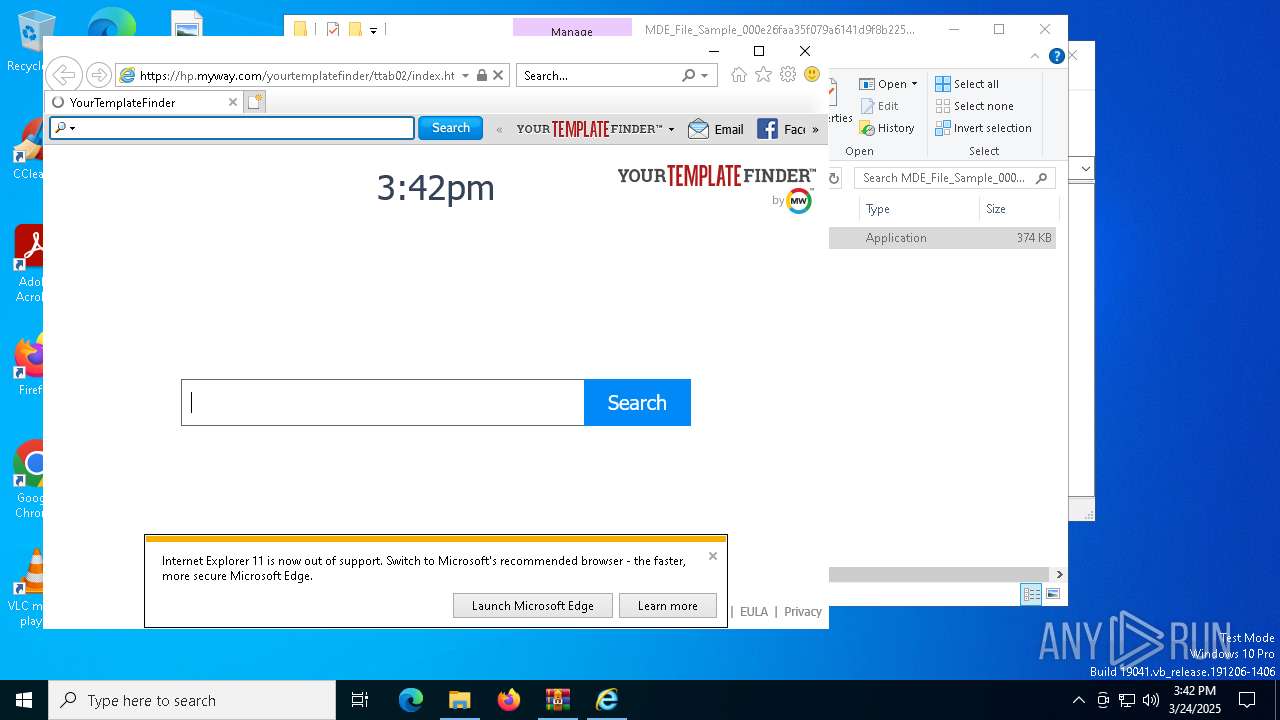
| 1040 | "Rundll32.exe" "C:\Users\admin\AppData\Local\YourTemplateFinderTooltab\TooltabExtension.dll",A -hp=https://hp.myway.com/yourtemplatefinder/ttab02/index.html -ua="(Windows NT 10.0; Win64; MSIE 11.3636; Build 19045; SP 0)" -ul=https://anx.mindspark.com/anx.gif?anxa=%251&anxe=%252&anxt=53540335-F284-4188-9E4B-EC685888CF80&anxtv=2.7.1.3000&anxp=^BNF^mni000^TTAB02&anxsi=&anxv=%253&anxd=2025-03-24&anxr=%254 -hu=SHOW | C:\Windows\SysWOW64\rundll32.exe | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1600 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:7148 CREDAT:791840 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2852 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3332 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3956 | "C:\Users\admin\Downloads\MDE_File_Sample_000e26faa35f079a6141d9f8b2252aa76e424f52\YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe" | C:\Users\admin\Downloads\MDE_File_Sample_000e26faa35f079a6141d9f8b2252aa76e424f52\YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | explorer.exe | ||||||||||||
User: admin Company: Mindspark Interactive Network, Inc. Integrity Level: MEDIUM Description: YourTemplateFinder Setup Exit code: 0 Version: 2.7.1.3000 Modules
| |||||||||||||||
| 4464 | "C:\Program Files (x86)\Internet Explorer\ielowutil.exe" -CLSID:{0002DF01-0000-0000-C000-000000000046} -Embedding | C:\Program Files (x86)\Internet Explorer\ielowutil.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Low-Mic Utility Tool Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4892 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6044 | C:\WINDOWS\system32\DllHost.exe /Processid:{49F171DD-B51A-40D3-9A6C-52D674CC729D} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 728
Read events
19 643
Write events
69
Delete events
16
Modification events
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\MDE_File_Sample_000e26faa35f079a6141d9f8b2252aa76e424f52.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
4
Suspicious files
44
Text files
34
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | C:\Users\admin\AppData\Local\Temp\nsh60AC.tmp\nsDialogs.dll | executable | |
MD5:B9A5A272154FC0DD652EF9C59C5D63A0 | SHA256:D84D810B8F8819F4A34D5E033B72951EADDA1BBB5ED0B8C76874B6C25001CAA9 | |||
| 3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | C:\Users\admin\AppData\Local\Temp\nsh60AC.tmp\System.dll | executable | |
MD5:7399323923E3946FE9140132AC388132 | SHA256:5A1C20A3E2E2EB182976977669F2C5D9F3104477E98F74D69D2434E79B92FDC3 | |||
| 6404 | WinRAR.exe | C:\Users\admin\Downloads\MDE_File_Sample_000e26faa35f079a6141d9f8b2252aa76e424f52\YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | executable | |
MD5:BE829601AD43250BAE1F680B783DB789 | SHA256:1EFA326B3C492AE187A89E11295882E3B8F059E0D7947E1846B93F8931246165 | |||
| 3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | C:\Users\admin\AppData\Local\Temp\nsh60AC.tmp\cancel_blue_1473358017200.bmp | image | |
MD5:C20F972BB1E321BCF007A11D1433496C | SHA256:DDEB1A235C5FBB989FADF287A627736894F62406C0258B2A8B73379ADA7A6775 | |||
| 3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | C:\Users\admin\AppData\Local\Temp\nsh60AC.tmp\YourTemplateFinder_msi_bg-copy_1501857870041.bmp | image | |
MD5:98E8AE48A448CEB300834709580DF9AF | SHA256:CD89FBA61ABCF16DBAF7B2D5BE655B2B3F950867B612BF72CE1913206E708E46 | |||
| 3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
| 3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | C:\Users\admin\AppData\Local\Temp\nsh60AC.tmp\YourTemplateFinder_msi_bg-copy_1501857885092.bmp | image | |
MD5:6B58A0A87B7ADE1F6533F201D7C10450 | SHA256:13D86CD66076216AF388C756E06504F3719C1B2C4A958C77CD4D5691A4532FA6 | |||
| 3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | C:\Users\admin\AppData\Local\YourTemplateFinderTooltab\TooltabExtension.dll | executable | |
MD5:767737F00455032D893A223B78621F2D | SHA256:E71ECA3BA443107880EA99520422489C4EFC238B846681B6E3A5D3C9E61071BF | |||
| 3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\49D317A8A486AEC11C0EDDC66260EF43 | binary | |
MD5:D106F02462B0290C7C38109099D114BB | SHA256:6320B12C1F2ABCB1C5CABD736AAFF03E20665470F9717E0368DD2A1D86CAAA3D | |||
| 3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:236F320C9BCA6B9977678910B10E8C7E | SHA256:88BFE2EB13006E2A716A048A15E0715C1681ABC5D81E657B66367AFE470E7182 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
84
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
1324 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/s/gts1d4/eQ2pKzFRzms/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEBrkojmzJx8VEEeg2WSex98%3D | unknown | — | — | whitelisted |
3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5072 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | GET | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgTTSt7lL2v29yQRdfENzOFX9A%3D%3D | unknown | — | — | whitelisted |
3956 | YourTemplateFinder.08cb3cc05d13453b84a2f610e5b495ba.exe | GET | 200 | 216.58.206.67:80 | http://crls.pki.goog/gts1d4/kA4WW9mzpzY.crl | unknown | — | — | whitelisted |
856 | iexplore.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBQbxmMY0ZtiFXXusCt0ac1S1Zoq4gQU9n4vvYCjSrJwW%2Bvfmh%2FY7cphgAcCEzMBYE%2B9jBRaxFEXbiQAAAFgT70%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5112 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5072 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |