| File name: | fat.exe |
| Full analysis: | https://app.any.run/tasks/de797838-671a-4d5e-81c9-abe379ad0822 |
| Verdict: | Malicious activity |
| Analysis date: | June 02, 2025, 20:44:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | D3C2519A4B1A0FCAA544ACC0811F5C1B |
| SHA1: | 338E88EC41BD6AF415397343A193E27E336DDD90 |
| SHA256: | 944A080711C209D86728FF347A9A6B017B89EFA59CA2F6B7FE9CCF511EC5FD6A |
| SSDEEP: | 196608:Z8owhBiCWMG+A7q/TIqd6ERJO9WxPHEB3hphGLSiJ:ZevWJzq/jUaPI4Sk |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- fat.exe (PID: 4400)
Process drops python dynamic module
- fat.exe (PID: 4400)
Executable content was dropped or overwritten
- fat.exe (PID: 4400)
Process drops legitimate windows executable
- fat.exe (PID: 4400)
Application launched itself
- fat.exe (PID: 4400)
Loads Python modules
- fat.exe (PID: 680)
Starts CMD.EXE for commands execution
- fat.exe (PID: 680)
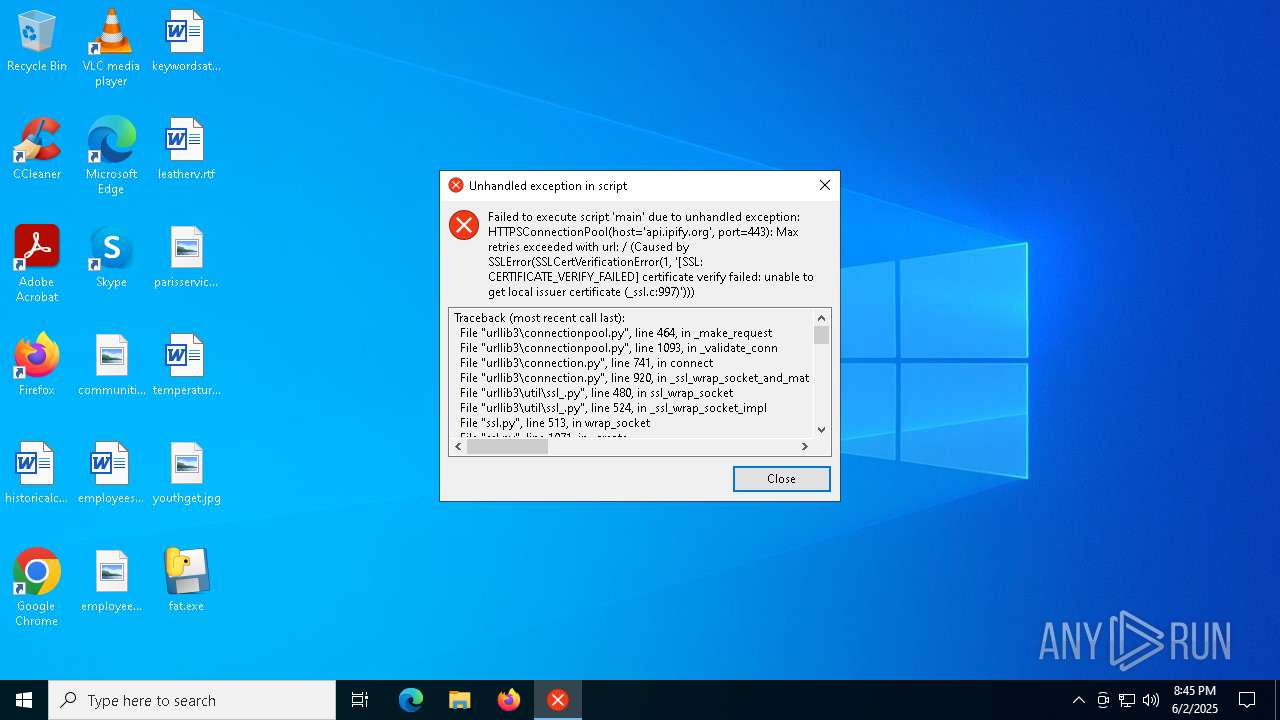
Checks for external IP
- fat.exe (PID: 680)
INFO
Checks supported languages
- fat.exe (PID: 4400)
- fat.exe (PID: 680)
Reads the computer name
- fat.exe (PID: 4400)
- fat.exe (PID: 680)
The sample compiled with english language support
- fat.exe (PID: 4400)
Create files in a temporary directory
- fat.exe (PID: 4400)
- fat.exe (PID: 680)
Reads the machine GUID from the registry
- fat.exe (PID: 680)
Checks operating system version
- fat.exe (PID: 680)
Checks proxy server information
- fat.exe (PID: 680)
- slui.exe (PID: 3268)
Reads the software policy settings
- slui.exe (PID: 3268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:01 23:37:27+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.32 |
| CodeSize: | 165888 |
| InitializedDataSize: | 154112 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xafa0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
125
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | "C:\Users\admin\Desktop\fat.exe" | C:\Users\admin\Desktop\fat.exe | fat.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4400 | "C:\Users\admin\Desktop\fat.exe" | C:\Users\admin\Desktop\fat.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 7812 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | fat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 649
Read events
6 649
Write events
0
Delete events
0
Modification events
Executable files
93
Suspicious files
2
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4400 | fat.exe | C:\Users\admin\AppData\Local\Temp\_MEI44002\Crypto\Cipher\_raw_arc2.pyd | executable | |
MD5:C541D432A2581F4822D69698D7EBF37C | SHA256:143D4D696F909E631FE4772D6490B4699CA9BCD8ADC4632516D7AE3AE5BFEFE3 | |||
| 4400 | fat.exe | C:\Users\admin\AppData\Local\Temp\_MEI44002\Crypto\Cipher\_raw_cast.pyd | executable | |
MD5:83E114861F490D23DE2B3CA29A536C28 | SHA256:23C0B7775AAE008895DCA6F0E0E261386053237926AD4C9A88835525ECB53498 | |||
| 4400 | fat.exe | C:\Users\admin\AppData\Local\Temp\_MEI44002\Crypto\Cipher\_Salsa20.pyd | executable | |
MD5:A5C4872EEE5DE17A38CC83E83B3527B9 | SHA256:E86C13FD9D8769FF430C02825CE490ACAC5BBA2D870F435D37220A2C9532C554 | |||
| 4400 | fat.exe | C:\Users\admin\AppData\Local\Temp\_MEI44002\Crypto\Cipher\_chacha20.pyd | executable | |
MD5:CF8FFD1342F25DC21DA26EFE0F9BFD5C | SHA256:06B6F6005B96FA3DDBFFA052CD11B9870101064225AE21258030A8B0C5A9495B | |||
| 4400 | fat.exe | C:\Users\admin\AppData\Local\Temp\_MEI44002\Crypto\Cipher\_pkcs1_decode.pyd | executable | |
MD5:AE49E0AA5BF01648AAFCF3A0B0BC0835 | SHA256:9EDD6673E3F45E194B970BCAF698CBE783223720A217B07BAB4A29B8D50B4DE6 | |||
| 4400 | fat.exe | C:\Users\admin\AppData\Local\Temp\_MEI44002\Crypto\Cipher\_raw_aesni.pyd | executable | |
MD5:51E9C6F28A53119EFA674605909E7E6B | SHA256:6A570EB6FE9611358D00E69091C3C7121906351355B61F835D729AD36506E019 | |||
| 4400 | fat.exe | C:\Users\admin\AppData\Local\Temp\_MEI44002\Crypto\Cipher\_raw_cfb.pyd | executable | |
MD5:8E5191B1A706217E6C2480161E8B6FF4 | SHA256:FADB475882E79793DF2D25D162B655D5DBBDE32458F33B04BF8A2F0980754106 | |||
| 4400 | fat.exe | C:\Users\admin\AppData\Local\Temp\_MEI44002\Crypto\Cipher\_raw_cbc.pyd | executable | |
MD5:B1A7FF8D600A4AFA51E63A294AAD3644 | SHA256:3176B78C6DC07BC119D0E59E23F3DEA732E606E876D36F9224C6D15D7A7B39A4 | |||
| 4400 | fat.exe | C:\Users\admin\AppData\Local\Temp\_MEI44002\Crypto\Cipher\_raw_blowfish.pyd | executable | |
MD5:A198952267D13A7B0360560F8FBF155B | SHA256:9CB5C5CF5D1677552B3A4CDBA1069F4D51C4D3F2F4D36E6EEFB72FC6B20AC178 | |||
| 4400 | fat.exe | C:\Users\admin\AppData\Local\Temp\_MEI44002\Crypto\Cipher\_raw_des.pyd | executable | |
MD5:D396715DE12BAD1416F4E3CCFB7FA6BD | SHA256:E0ABA48F05288315674C3667E3C883A1D2AF7813A58838B007C6CA6463D39471 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
21
DNS requests
7
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8172 | RUXIMICS.exe | GET | 200 | 2.18.121.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8172 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | — | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
8172 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
8172 | RUXIMICS.exe | 2.18.121.139:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
8172 | RUXIMICS.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
680 | fat.exe | 172.67.74.152:443 | api.ipify.org | CLOUDFLARENET | US | shared |
7676 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3268 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api.ipify.org |
| shared |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
680 | fat.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |