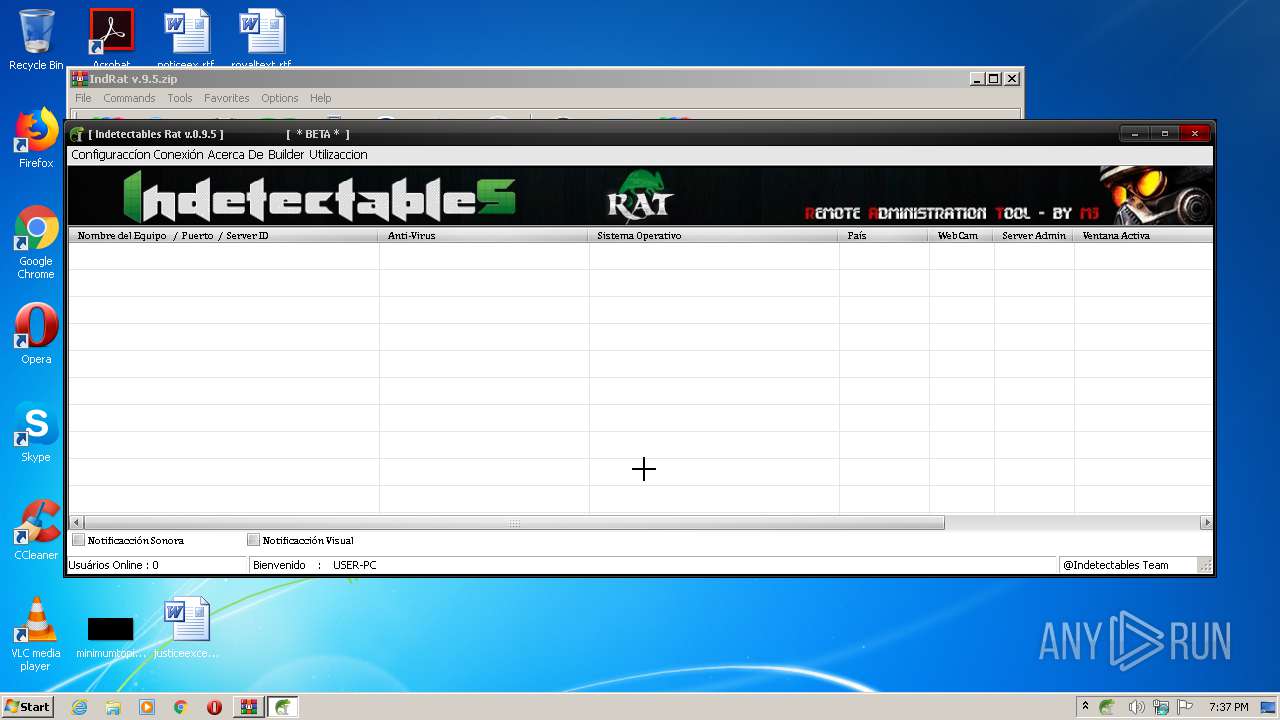
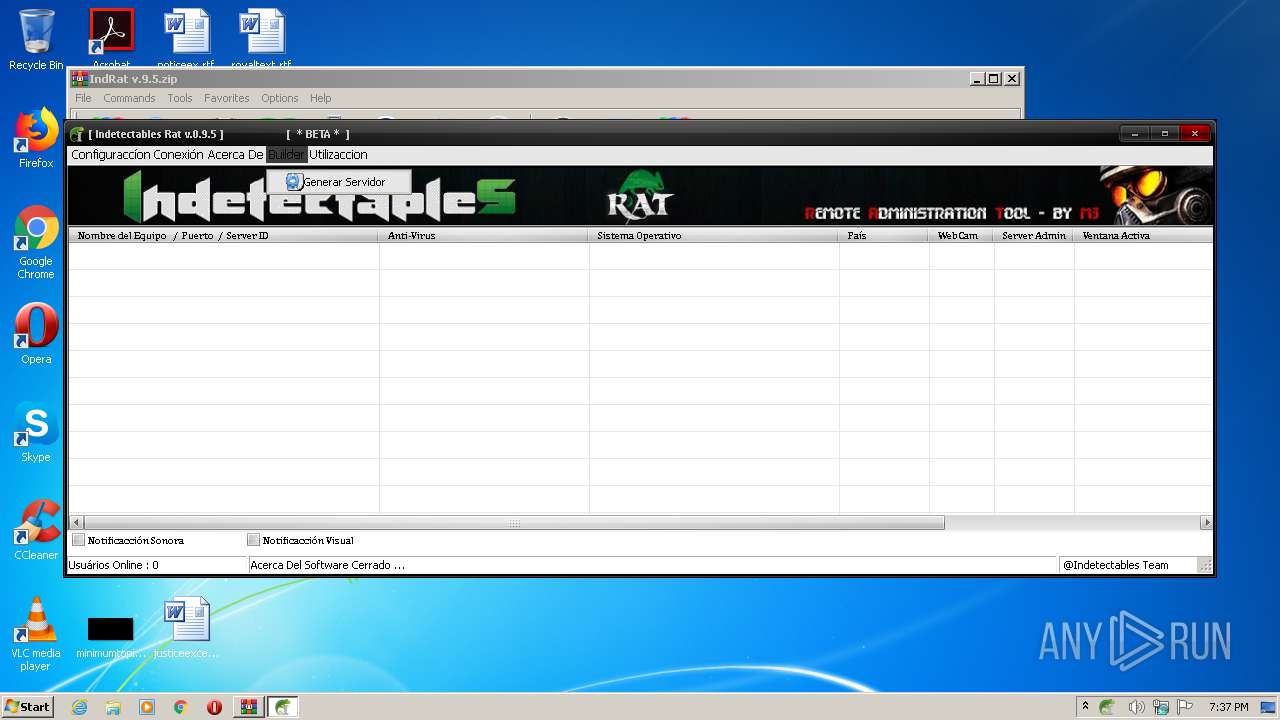
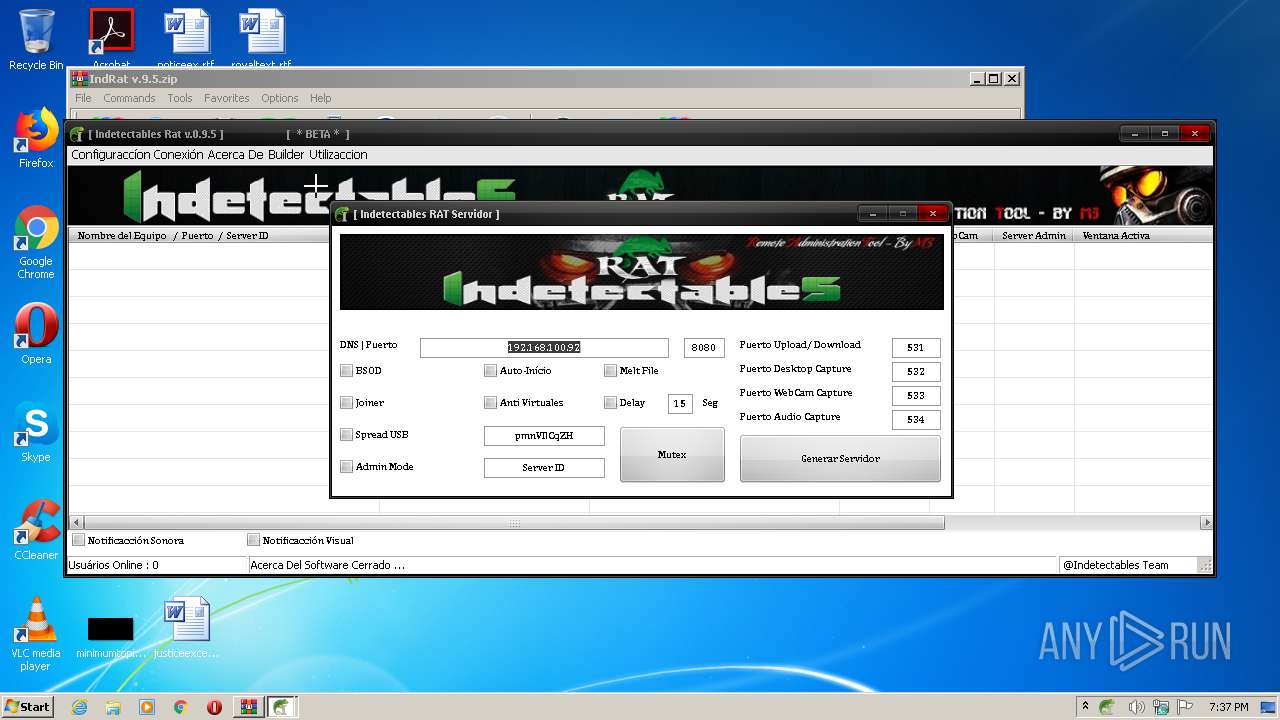
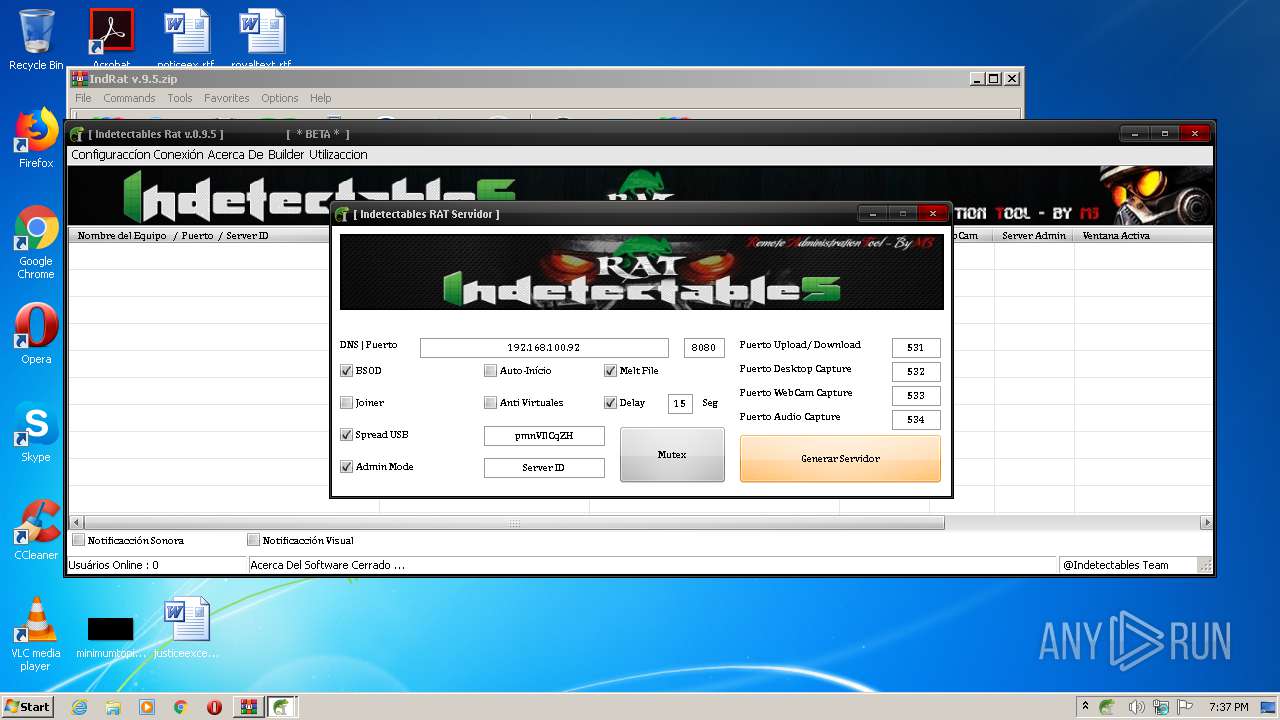
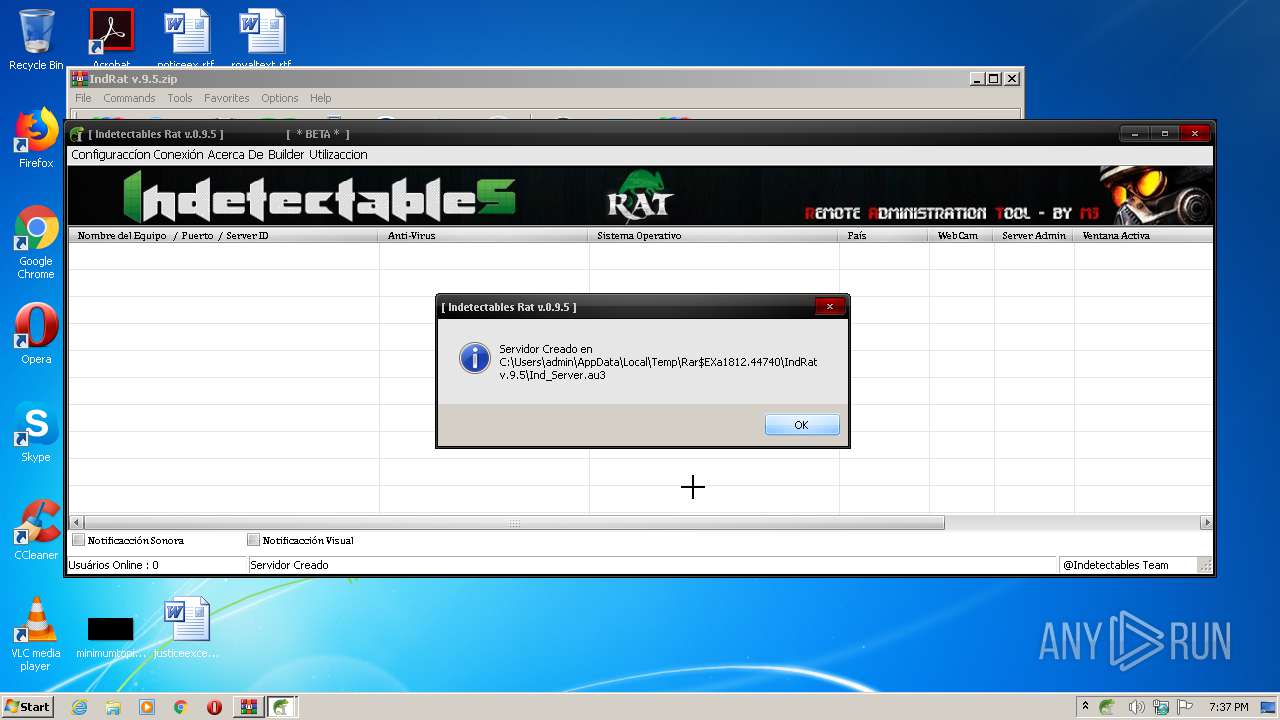
| File name: | IndRat v.9.5.zip |
| Full analysis: | https://app.any.run/tasks/65a3e695-2943-46d1-a7ff-b43befd91da6 |
| Verdict: | No threats detected |
| Analysis date: | June 16, 2020, 18:36:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 4D79420BA4144A480626CF508E3174CB |
| SHA1: | 3A76E8BC8744EB22FCBE98549287495D0498301C |
| SHA256: | 943DA1A8ABC518C28402B4B8E596D55A363A34CCCD3BDF24733AA0536B4379D8 |
| SSDEEP: | 393216:JRWZ3BeewrIT31qcynDoMUlrehlvebGKl2:vlewry1ynZUGKo |
MALICIOUS
Application was dropped or rewritten from another process
- IndRat.exe (PID: 2032)
Loads dropped or rewritten executable
- IndRat.exe (PID: 2032)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1812)
- IndRat.exe (PID: 2032)
Reads Internet Cache Settings
- IndRat.exe (PID: 2032)
Reads internet explorer settings
- IndRat.exe (PID: 2032)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 1812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (33.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2016:11:14 09:42:01 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | IndRat v.9.5/ |
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1812 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\IndRat v.9.5.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2032 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\IndRat.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\IndRat.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
Total events
526
Read events
506
Write events
20
Delete events
0
Modification events
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\IndRat v.9.5.zip | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
7
Suspicious files
0
Text files
470
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\Bandeiras\ag.png | image | |
MD5:1C0D859D89EA2FD426B5995629B48C02 | SHA256:DB673A779729744BD091322D388F31857B6E4B2F516C212317FB80BB6AE0660E | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\Bandeiras\ae.png | image | |
MD5:AA44839785B2EF1890987B6815791020 | SHA256:165A7FE36D6DABA17F36082CEBA573B107FF54293E8792C4FE2E186752210244 | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\Bandeiras\al.png | image | |
MD5:938F6D2AD6EB0754B4B1CE8D6EFE3D00 | SHA256:D3AD4F7C40CF88D3072EB158F6083053017D4B4F0537CFB8C0AAAD7CD79D768C | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\Bandeiras\ad.png | image | |
MD5:C22BA67A6B94164AD220C2064994ADD1 | SHA256:EEF9B90D0D988CC15B2AC5567852FACC7C0DE9B19A8C12BB96BDB7C64DD0D2C9 | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\Bandeiras\au.png | image | |
MD5:2A1384DE781BF1374F8A96710ED5CD70 | SHA256:5D7C2318950FD8490EEA8C6C488917E386407D4D0C29FF2B71D10F73A9169162 | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\Bandeiras\ar.png | image | |
MD5:073297D53D58B6EDFB99C3B9056529D3 | SHA256:4A0C6E510EA515CE0B11ACB1A5009A41BF883877ADA34D25F41137E8D18858FC | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\Bandeiras\bf.png | image | |
MD5:AB8408EA74F471C32297BE9559BED0CD | SHA256:C92AB1AFFBE2CA2E08EA5FBE92DA84956BDDDDD4AB7B17B2E36575DA9D20B8BB | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\Bandeiras\be.png | image | |
MD5:18E4B453844A360A88EB140660726BD9 | SHA256:10F1D7E798624369C1546581D64267580818D888771EE19853670805275C5841 | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\Bandeiras\bi.png | image | |
MD5:CE3075E5E79148FFBFAF9479CDA84540 | SHA256:851769A7CC050ED7181BB9046147761F424C3ED6A1C750877BE05707E241E934 | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.44740\IndRat v.9.5\Bandeiras\bg.png | image | |
MD5:01A706C970EED183313E65772ABF89B7 | SHA256:BC9901E980C8C2AD60C07C5BF7C69B2705C2602AFE5B7372B297F3F32B471CFE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report