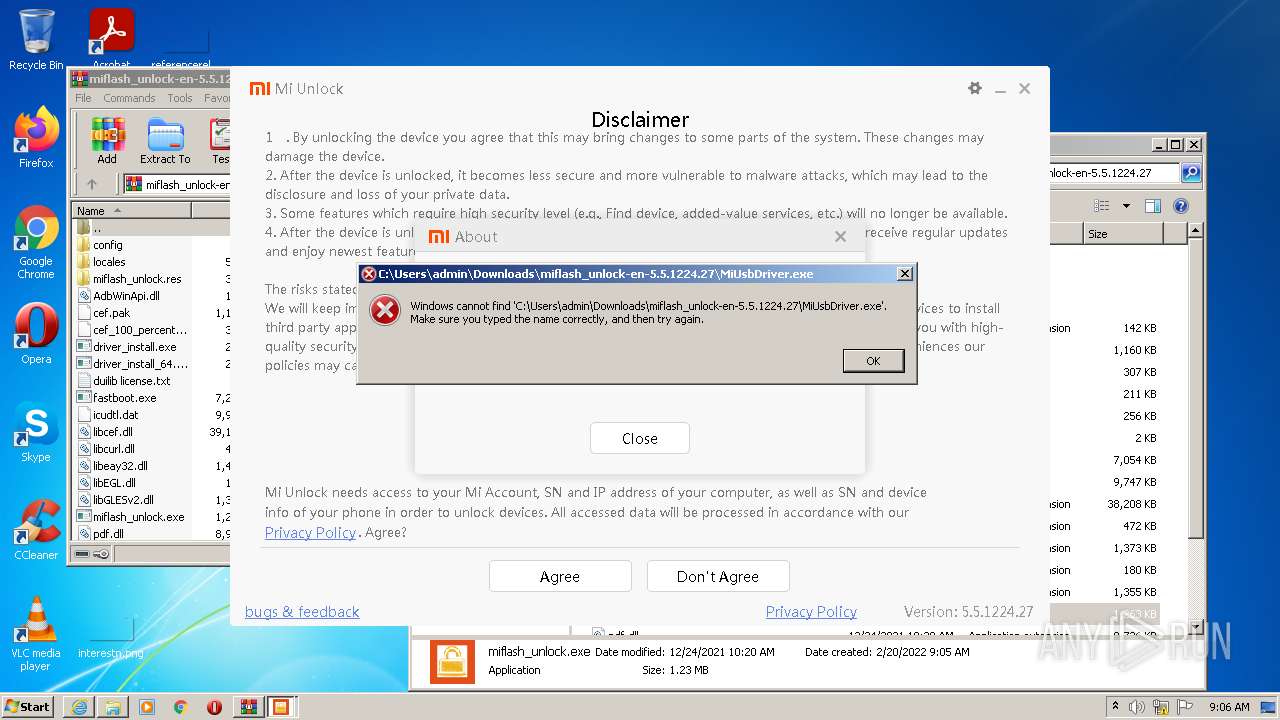
| URL: | http://miuirom.xiaomi.com/rom/u1106245679/5.5.1224.27/miflash_unlock-en-5.5.1224.27.zip |
| Full analysis: | https://app.any.run/tasks/5296e1ef-7a86-454c-9265-4cb61c3ab4e8 |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2022, 09:05:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B8136FEAC1EC5586FB79B727BEEB4BB3 |
| SHA1: | A82A7770C5898FB01A998E17E684323E53734880 |
| SHA256: | 943C5A53F526F72DA95A9A9340F7D7FCE0FBD3D6D5AF40435B8C54C4482C098D |
| SSDEEP: | 3:N1KTqXTLrKIdf2TbcKQkLUXBuKICK48QgXBuLc:CALKIdf2/cYLOY7SSYLc |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3512)
- miflash_unlock.exe (PID: 704)
- miflash_unlock.exe (PID: 3952)
- fastboot.exe (PID: 2140)
- fastboot.exe (PID: 404)
Application was dropped or rewritten from another process
- driver_install.exe (PID: 720)
- miflash_unlock.exe (PID: 704)
- miflash_unlock.exe (PID: 3952)
- fastboot.exe (PID: 2140)
- driver_install.exe (PID: 1032)
- fastboot.exe (PID: 404)
- driver_install.exe (PID: 3036)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3748)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 4052)
Reads the computer name
- WinRAR.exe (PID: 4052)
- miflash_unlock.exe (PID: 704)
- fastboot.exe (PID: 2140)
Checks supported languages
- WinRAR.exe (PID: 4052)
- miflash_unlock.exe (PID: 704)
- driver_install.exe (PID: 720)
- miflash_unlock.exe (PID: 3952)
- fastboot.exe (PID: 2140)
- driver_install.exe (PID: 3036)
- fastboot.exe (PID: 404)
- driver_install.exe (PID: 1032)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4052)
Reads CPU info
- miflash_unlock.exe (PID: 704)
- miflash_unlock.exe (PID: 3952)
Application launched itself
- miflash_unlock.exe (PID: 704)
Check for Java to be installed
- miflash_unlock.exe (PID: 704)
Creates files in the user directory
- miflash_unlock.exe (PID: 704)
INFO
Reads the computer name
- iexplore.exe (PID: 3172)
- iexplore.exe (PID: 3748)
- explorer.exe (PID: 1976)
Checks supported languages
- iexplore.exe (PID: 3172)
- explorer.exe (PID: 1976)
- iexplore.exe (PID: 3748)
Changes internet zones settings
- iexplore.exe (PID: 3172)
Application launched itself
- iexplore.exe (PID: 3172)
Reads the date of Windows installation
- iexplore.exe (PID: 3172)
Checks Windows Trust Settings
- iexplore.exe (PID: 3172)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3172)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 4052)
- iexplore.exe (PID: 3172)
Reads settings of System Certificates
- iexplore.exe (PID: 3172)
- miflash_unlock.exe (PID: 704)
Manual execution by user
- explorer.exe (PID: 1976)
- driver_install.exe (PID: 720)
- miflash_unlock.exe (PID: 704)
- driver_install.exe (PID: 3036)
- driver_install.exe (PID: 1032)
- fastboot.exe (PID: 404)
Creates files in the user directory
- iexplore.exe (PID: 3172)
Changes settings of System certificates
- iexplore.exe (PID: 3172)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3172)
Reads the hosts file
- miflash_unlock.exe (PID: 704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
12
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 404 | "C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\fastboot.exe" | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\fastboot.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 704 | "C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\miflash_unlock.exe" | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\miflash_unlock.exe | Explorer.EXE | ||||||||||||
User: admin Company: Xiaomi.Inc Integrity Level: MEDIUM Description: MIPhone unlock tool Exit code: 0 Version: 5.5.1224.27 Modules
| |||||||||||||||
| 720 | "C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\driver_install.exe" | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\driver_install.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 1032 | "C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\driver_install.exe" | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\driver_install.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 1976 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2140 | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\fastboot.exe devices | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\fastboot.exe | — | miflash_unlock.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3036 | "C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\driver_install.exe" | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\driver_install.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 3172 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://miuirom.xiaomi.com/rom/u1106245679/5.5.1224.27/miflash_unlock-en-5.5.1224.27.zip" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3512 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3748 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3172 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
17 967
Read events
17 828
Write events
137
Delete events
2
Modification events
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30942776 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 71856508 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30942777 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
14
Suspicious files
85
Text files
63
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3748 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\miflash_unlock-en-5.5.1224.27[1].zip | compressed | |
MD5:— | SHA256:— | |||
| 4052 | WinRAR.exe | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 4052 | WinRAR.exe | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27\libcef.dll | — | |
MD5:— | SHA256:— | |||
| 3172 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 3172 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3172 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:— | SHA256:— | |||
| 3512 | SearchProtocolHost.exe | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27.zip.0xufs69.partial | compressed | |
MD5:— | SHA256:— | |||
| 3172 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE1D91539FE86339F.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3172 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{300C334B-922C-11EC-BB61-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 3172 | iexplore.exe | C:\Users\admin\Downloads\miflash_unlock-en-5.5.1224.27.zip | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
37
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
704 | miflash_unlock.exe | GET | 302 | 161.117.86.249:80 | http://update.miui.com/updates/mi-updateV6.php?v=1.0.0.0&c=4.0&d=miflash_unlock-en&b=X | SG | — | — | unknown |
704 | miflash_unlock.exe | GET | 302 | 161.117.86.249:80 | http://update.miui.com/updates/mi-updateV6.php?v=1.0.0.0&c=4.0&d=miflash_unlock-en&b=X | SG | — | — | unknown |
3748 | iexplore.exe | GET | 200 | 92.123.101.139:80 | http://miuirom.xiaomi.com/rom/u1106245679/5.5.1224.27/miflash_unlock-en-5.5.1224.27.zip | unknown | compressed | 31.0 Mb | whitelisted |
704 | miflash_unlock.exe | GET | 200 | 161.117.86.249:80 | http://update.miui.com/updates/mi-update-mimanager.php?p=zVpbNXAnhBU%2F78QCGno7q3VCPMUnoENmgGyiryS%2F1%2B5a5InmEYSQGA5S%2B9lt6%2BuNsZUfsohYUSBa2BNdFifqJR81N1hRIHJrbGiPurYq3LBQ2XRCDhGYD6N%2F1MVrRgdTmq6m65x2Rg%2BG5OVFnrI9NNX78kWj%2BuhAQWFeqDBAFCG9QNnbzt%2FF7PEjT23wAl1klUf62SEBH34IcKFh8mmzCC7b5sjSvP4uAs4GiXsT%2Fmk%3D | SG | text | 1023 b | unknown |
3172 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
704 | miflash_unlock.exe | GET | 200 | 161.117.86.249:80 | http://update.miui.com/updates/mi-update-mimanager.php?p=zVpbNXAnhBU%2F78QCGno7q3VCPMUnoENmgGyiryS%2F1%2B5a5InmEYSQGA5S%2B9lt6%2BuNsZUfsohYUSBa2BNdFifqJR81N1hRIHJrbGiPurYq3LBQ2XRCDhGYD6N%2F1MVrRgdTmq6m65x2Rg%2BG5OVFnrI9NNX78kWj%2BuhAQWFeqDBAFCG9QNnbzt%2FF7PEjT23wAl1klUf62SEBH34IcKFh8mmzCC7b5sjSvP4uAs4GiXsT%2Fmk%3D | SG | text | 1023 b | unknown |
3172 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e2d778ed5b8838fa | US | compressed | 4.70 Kb | whitelisted |
3172 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3172 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d5a6dd4f3e8c7a9c | US | compressed | 4.70 Kb | whitelisted |
3172 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f3373b11fbd7af2e | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3748 | iexplore.exe | 92.123.101.139:80 | miuirom.xiaomi.com | Akamai International B.V. | — | unknown |
3172 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3172 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3172 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
704 | miflash_unlock.exe | 161.117.86.249:80 | update.miui.com | — | SG | unknown |
704 | miflash_unlock.exe | 20.47.97.75:443 | account.xiaomi.com | — | US | unknown |
704 | miflash_unlock.exe | 163.171.146.54:443 | ssl-cdn.static.browser.mi-img.com | — | US | unknown |
704 | miflash_unlock.exe | 79.133.177.230:443 | cdn.web-global.fds.api.mi-img.com | SOT LINE Limited Company | RU | malicious |
704 | miflash_unlock.exe | 2.16.186.32:443 | font.sec.miui.com | Akamai International B.V. | — | whitelisted |
704 | miflash_unlock.exe | 220.196.184.107:443 | cdn.cnbj1.fds.api.mi-img.com | — | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
miuirom.xiaomi.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
update.miui.com |
| unknown |
account.xiaomi.com |
| unknown |
cdn.web-global.fds.api.mi-img.com |
| malicious |
ssl-cdn.static.browser.mi-img.com |
| malicious |
font.sec.miui.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3748 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
Process | Message |
|---|---|
miflash_unlock.exe | DEBUG <09:06:03.975,T:2324> : miflash_unlock start
|
miflash_unlock.exe | [0220/090604:ERROR:gpu_info_collector_win.cc(147)] Could not read gaming score from assessment results.
|
miflash_unlock.exe | DEBUG <09:06:04.116,T:3756> : auto refresh device list
|
miflash_unlock.exe | [0220/090604:ERROR:renderer_main.cc(227)] Running without renderer sandbox
|
miflash_unlock.exe | INFO <09:06:04.194,T:3756> : fastboot devices
|
miflash_unlock.exe | INFO <09:06:05.359,T:3808> : new app version:5.5.1224.27 url:http://miuirom.xiaomi.com/rom/u1106245679/5.5.1224.27/miflash_unlock-en-5.5.1224.27.zip
|
miflash_unlock.exe | DEBUG <09:06:05.952,T:2324> : [200]End: https://account.xiaomi.com/fe/service/login?passive=true&json=false&_snsDefault=facebook&hidden=false&_locale=en_US&checkSafePhone=true&sid=unlockApi&qs=%253Fsid%253DunlockApi%2526json%253Dfalse%2526passive%253Dtrue%2526hidden%253Dfalse%2526_snsDefault%253Dfacebook%2526_locale%253Den_US%2526checkSafePhone%253Dtrue&callback=https%3A%2F%2Funlock.update.miui.com%2Fsts&_sign=lAfpKjMimkXF%2F2uEA47i664ZqJ8%3D&serviceParam=%7B%22checkSafePhone%22%3Atrue%2C%22checkSafeAddress%22%3Afalse%2C%22lsrp_score%22%3A0.0%7D&showActiveX=false&theme=&needTheme=false&bizDeviceType=
|
miflash_unlock.exe | INFO <09:06:08.604,T:2492> : new app version:5.5.1224.27 url:http://miuirom.xiaomi.com/rom/u1106245679/5.5.1224.27/miflash_unlock-en-5.5.1224.27.zip
|
miflash_unlock.exe | DEBUG <09:06:27.454,T:2324> : Close app after cef_close
|
miflash_unlock.exe | DEBUG <09:06:27.459,T:2324> : miflash_unlock exit
|