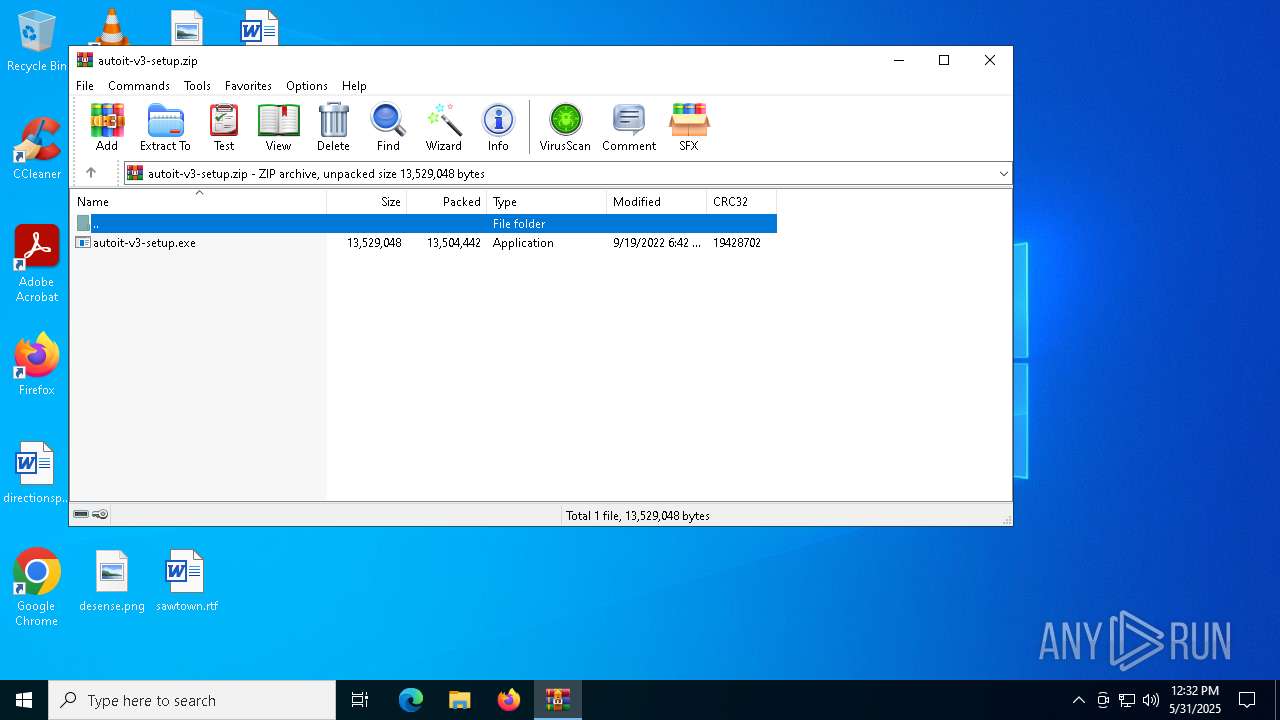
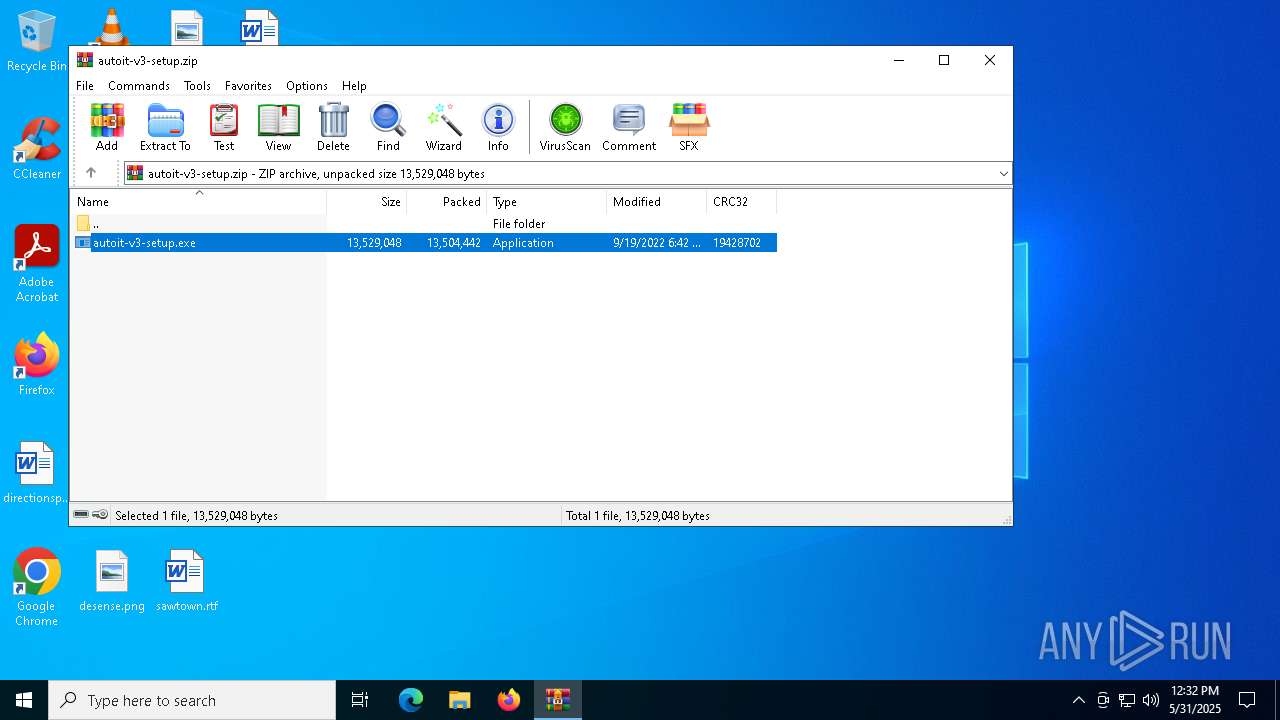
| File name: | autoit-v3-setup.zip |
| Full analysis: | https://app.any.run/tasks/ccc3da12-5c05-47c1-9995-9e7f4906de58 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2025, 12:32:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 0F544B1C2AE93A94146DA5C2855AE8F7 |
| SHA1: | B3857290A4469E2F03E1B7016FA6731502A201D6 |
| SHA256: | 942D85853686035F224B1D5B0DF6EECC61C5A91F8B9CD4217AC338E0C8096B0F |
| SSDEEP: | 393216:dYUgxlZL1imxuXY90bdgy0yZ2Hv5fNl4FQgLpcIXG1f:dYUgDZBNYWiIv14LLpHWJ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6992)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6992)
Malware-specific behavior (creating "System.dll" in Temp)
- autoit-v3-setup.exe (PID: 1188)
The process creates files with name similar to system file names
- autoit-v3-setup.exe (PID: 1188)
Executable content was dropped or overwritten
- autoit-v3-setup.exe (PID: 1188)
There is functionality for taking screenshot (YARA)
- autoit-v3-setup.exe (PID: 1188)
Creates/Modifies COM task schedule object
- autoit-v3-setup.exe (PID: 1188)
Creates a software uninstall entry
- autoit-v3-setup.exe (PID: 1188)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6992)
- autoit-v3-setup.exe (PID: 1188)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6992)
Checks supported languages
- autoit-v3-setup.exe (PID: 1188)
Reads the computer name
- autoit-v3-setup.exe (PID: 1188)
Create files in a temporary directory
- autoit-v3-setup.exe (PID: 1188)
Creates files in the program directory
- autoit-v3-setup.exe (PID: 1188)
The sample compiled with german language support
- autoit-v3-setup.exe (PID: 1188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:09:19 19:42:08 |
| ZipCRC: | 0x19428702 |
| ZipCompressedSize: | 13504442 |
| ZipUncompressedSize: | 13529048 |
| ZipFileName: | autoit-v3-setup.exe |
Total processes
125
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
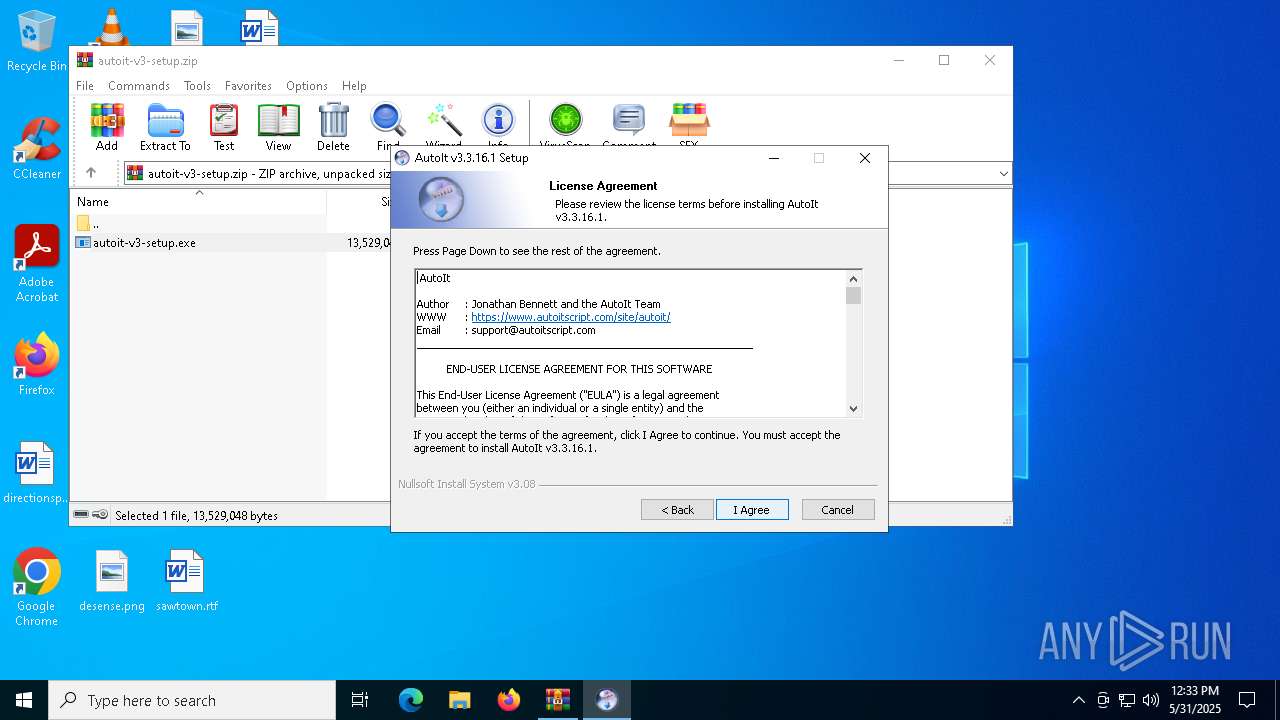
| 1188 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6992.8881\autoit-v3-setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6992.8881\autoit-v3-setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: HIGH Description: AutoIt v3 Setup Version: 3.3.16.1 Modules
| |||||||||||||||
| 5232 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6992.8881\autoit-v3-setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6992.8881\autoit-v3-setup.exe | — | WinRAR.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Setup Exit code: 3221226540 Version: 3.3.16.1 Modules
| |||||||||||||||
| 6992 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\autoit-v3-setup.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7924 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 862
Read events
1 829
Write events
33
Delete events
0
Modification events
| (PID) Process: | (6992) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6992) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6992) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6992) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\autoit-v3-setup.zip | |||
| (PID) Process: | (6992) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6992) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6992) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6992) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1188) autoit-v3-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.au3 |
| Operation: | write | Name: | PerceivedType |
Value: text | |||
| (PID) Process: | (1188) autoit-v3-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.au3\ShellNew |
| Operation: | write | Name: | FileName |
Value: Template.au3 | |||
Executable files
25
Suspicious files
37
Text files
994
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1188 | autoit-v3-setup.exe | C:\Program Files (x86)\AutoIt3\AutoIt.chm | — | |
MD5:— | SHA256:— | |||
| 1188 | autoit-v3-setup.exe | C:\Users\admin\AppData\Local\Temp\nsa33CC.tmp\ioPreviousVersion.ini | text | |
MD5:8C032D104411DA01E43D8E8B9AD88EB4 | SHA256:659CAD01FE631A96E0856C44D4114E12AC0E5402F863C2B1213A87D375C26F59 | |||
| 6992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6992.8881\autoit-v3-setup.exe | executable | |
MD5:A65B5DF1A846FB0BB7AD4B2DA19BBBCD | SHA256:19F91EE8A2ACF408D69BE07E1C4A99992213E565B9C8BB6D5C52F59F79707DA3 | |||
| 1188 | autoit-v3-setup.exe | C:\Users\admin\AppData\Local\Temp\nsa33CC.tmp\ioSpecial.ini | text | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 1188 | autoit-v3-setup.exe | C:\Users\admin\AppData\Local\Temp\nsa33CC.tmp\InstallOptions.dll | executable | |
MD5:ECE25721125D55AA26CDFE019C871476 | SHA256:C7FEF6457989D97FECC0616A69947927DA9D8C493F7905DC8475C748F044F3CF | |||
| 1188 | autoit-v3-setup.exe | C:\Program Files (x86)\AutoIt3\Au3Info.exe | executable | |
MD5:B6E281BF0E2C2F182F1537BC5148FAA9 | SHA256:5238261F80D3683101D2EF2242D92C3719A92A63C45A211C7973B831DD318F36 | |||
| 1188 | autoit-v3-setup.exe | C:\Users\admin\AppData\Local\Temp\nsa33CC.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 1188 | autoit-v3-setup.exe | C:\Program Files (x86)\AutoIt3\AutoIt3_x64.exe | executable | |
MD5:8FA52F316C393496F272357191DB6DEB | SHA256:92C6531A09180FAE8B2AAE7384B4CEA9986762F0C271B35DA09B4D0E733F9F45 | |||
| 1188 | autoit-v3-setup.exe | C:\Users\admin\AppData\Local\Temp\nsa33CC.tmp\UserInfo.dll | executable | |
MD5:2F69AFA9D17A5245EC9B5BB03D56F63C | SHA256:E54989D2B83E7282D0BEC56B098635146AAB5D5A283F1F89486816851EF885A0 | |||
| 1188 | autoit-v3-setup.exe | C:\Users\admin\AppData\Local\Temp\nsa33CC.tmp\ioDefaultOpen.ini | text | |
MD5:8C032D104411DA01E43D8E8B9AD88EB4 | SHA256:659CAD01FE631A96E0856C44D4114E12AC0E5402F863C2B1213A87D375C26F59 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
17
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.17.251.116:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.251.116:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7572 | svchost.exe | GET | 200 | 2.17.251.116:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.21.189.233:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7572 | svchost.exe | GET | 200 | 2.21.189.233:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.21.189.233:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.17.251.116:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
7572 | svchost.exe | 2.17.251.116:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.17.251.116:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
7572 | svchost.exe | 2.21.189.233:80 | www.microsoft.com | Akamai International B.V. | GB | whitelisted |
— | — | 2.21.189.233:80 | www.microsoft.com | Akamai International B.V. | GB | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.21.189.233:80 | www.microsoft.com | Akamai International B.V. | GB | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |