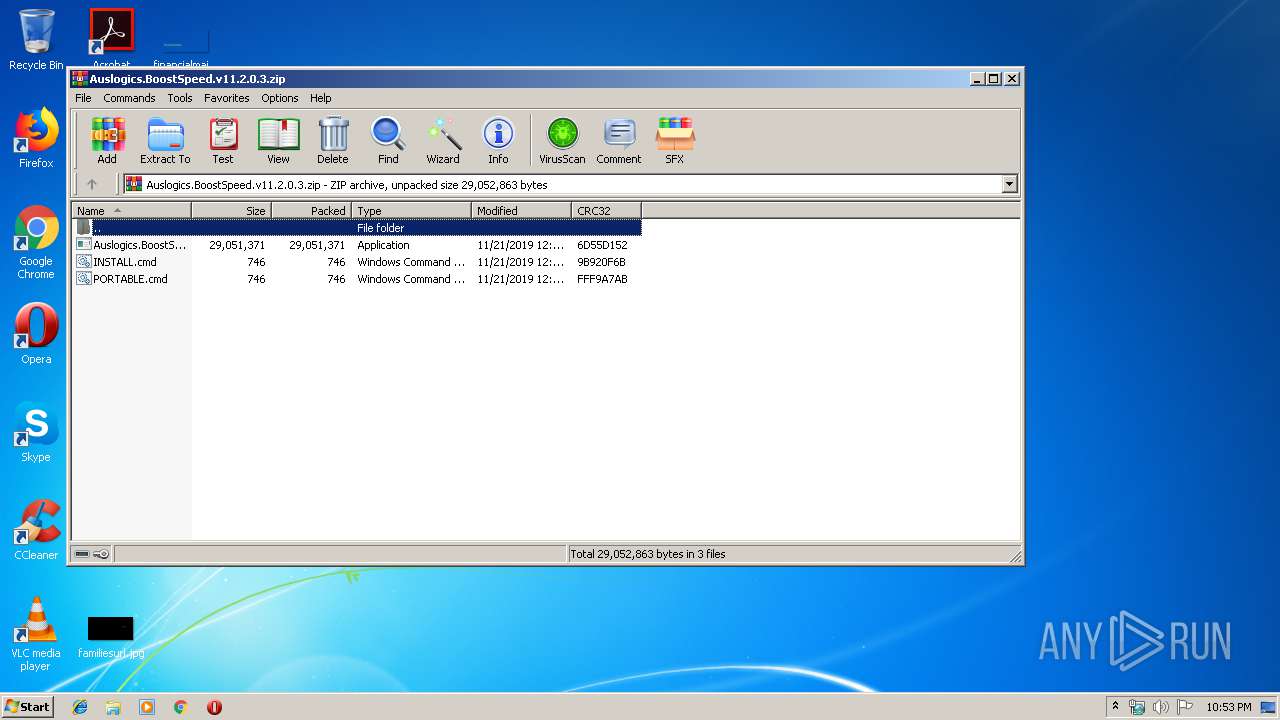
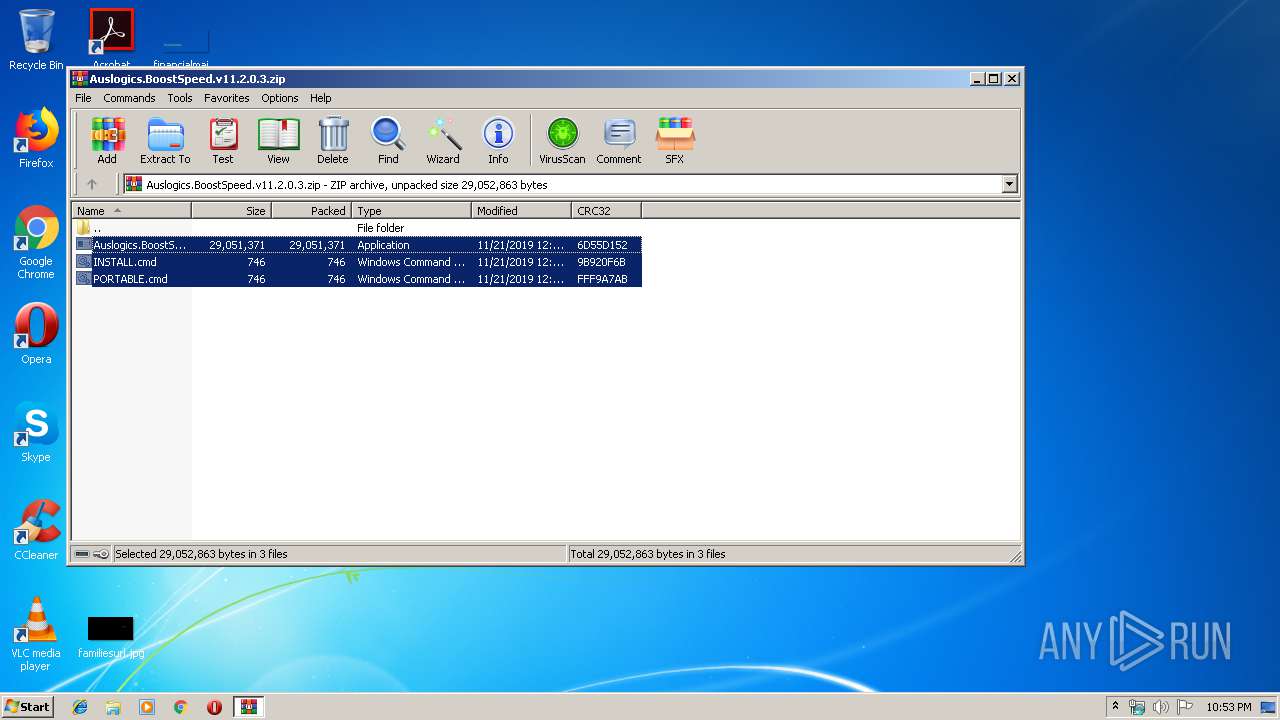
| File name: | Auslogics.BoostSpeed.v11.2.0.3.zip |
| Full analysis: | https://app.any.run/tasks/6c30f914-5cd2-4c14-a2cc-c7313004e418 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2019, 22:52:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 1978408F4E6443D8D7B5D8FD3C92B0C9 |
| SHA1: | ADEF60584FC0417E49A989B08FD27B8C78304520 |
| SHA256: | 9429123F5DDE587D189CE92656793ADEC9A2808064896FA75F41286A848FAC87 |
| SSDEEP: | 393216:25oqBMgQBFAfnNiBeXyl886wi91H4YoQmDKQj7X/ROp8e6aVY/Nbo5XvkEw4UW:OowNivdRi9x4NQqLRM8e3cU5XsE7 |
MALICIOUS
Application was dropped or rewritten from another process
- Auslogics.BoostSpeed.v11.2.0.3.exe (PID: 3852)
- Auslogics.BoostSpeed.v11.2.0.3.exe (PID: 2232)
- ns28AF.tmp (PID: 2208)
- ns2BBD.tmp (PID: 2084)
- Auslogics.BoostSpeed.v11.2.0.3.exe (PID: 1812)
- AusLogicsBoostSpeed11Portable.exe (PID: 992)
- AusLogicsBoostSpeed11Portable.exe (PID: 3616)
- taballtools.exe (PID: 1856)
- Integrator.exe (PID: 2400)
- tabcarecenter.exe (PID: 1936)
- tabcleanup.exe (PID: 2888)
- tabdashboard.exe (PID: 3384)
- tabprotect.exe (PID: 3396)
- tabmaintain.exe (PID: 2256)
- taboneclickscanner.exe (PID: 3848)
- taboptimize.exe (PID: 2420)
- tabreports.exe (PID: 2412)
- DeepDiskCleaner.exe (PID: 964)
- DeepDiskCleaner.exe (PID: 3692)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3468)
- Auslogics.BoostSpeed.v11.2.0.3.exe (PID: 3852)
- AusLogicsBoostSpeed11Portable.exe (PID: 3616)
- tabmaintain.exe (PID: 2256)
- Integrator.exe (PID: 2400)
- tabdashboard.exe (PID: 3384)
- taboneclickscanner.exe (PID: 3848)
- tabcleanup.exe (PID: 2888)
- taboptimize.exe (PID: 2420)
- tabprotect.exe (PID: 3396)
- taballtools.exe (PID: 1856)
- tabreports.exe (PID: 2412)
- tabcarecenter.exe (PID: 1936)
- DllHost.exe (PID: 4088)
- DeepDiskCleaner.exe (PID: 964)
- DeepDiskCleaner.exe (PID: 3692)
Loads the Task Scheduler COM API
- Integrator.exe (PID: 2400)
- tabdashboard.exe (PID: 3384)
- taboptimize.exe (PID: 2420)
Actions looks like stealing of personal data
- tabprotect.exe (PID: 3396)
SUSPICIOUS
Starts application with an unusual extension
- Auslogics.BoostSpeed.v11.2.0.3.exe (PID: 3852)
Uses NETSH.EXE for network configuration
- ns28AF.tmp (PID: 2208)
Creates COM task schedule object
- AusLogicsBoostSpeed11Portable.exe (PID: 3616)
Executable content was dropped or overwritten
- AusLogicsBoostSpeed11Portable.exe (PID: 3616)
- Auslogics.BoostSpeed.v11.2.0.3.exe (PID: 3852)
Reads the machine GUID from the registry
- Integrator.exe (PID: 2400)
- tabdashboard.exe (PID: 3384)
- taboneclickscanner.exe (PID: 3848)
- tabcleanup.exe (PID: 2888)
- tabreports.exe (PID: 2412)
- taballtools.exe (PID: 1856)
- taboptimize.exe (PID: 2420)
- tabmaintain.exe (PID: 2256)
- tabprotect.exe (PID: 3396)
- tabcarecenter.exe (PID: 1936)
- DeepDiskCleaner.exe (PID: 964)
- DeepDiskCleaner.exe (PID: 3692)
Reads Windows Product ID
- Integrator.exe (PID: 2400)
- tabdashboard.exe (PID: 3384)
- taboneclickscanner.exe (PID: 3848)
- tabcleanup.exe (PID: 2888)
- tabreports.exe (PID: 2412)
- taballtools.exe (PID: 1856)
- taboptimize.exe (PID: 2420)
- tabmaintain.exe (PID: 2256)
- tabprotect.exe (PID: 3396)
- tabcarecenter.exe (PID: 1936)
- DeepDiskCleaner.exe (PID: 964)
- DeepDiskCleaner.exe (PID: 3692)
Low-level read access rights to disk partition
- Integrator.exe (PID: 2400)
- tabcleanup.exe (PID: 2888)
- taboptimize.exe (PID: 2420)
- tabmaintain.exe (PID: 2256)
- tabdashboard.exe (PID: 3384)
- DeepDiskCleaner.exe (PID: 964)
Executed via COM
- DllHost.exe (PID: 4088)
Reads Internet Cache Settings
- Integrator.exe (PID: 2400)
Creates files in the program directory
- Integrator.exe (PID: 2400)
- tabcarecenter.exe (PID: 1936)
- taboptimize.exe (PID: 2420)
- tabprotect.exe (PID: 3396)
Reads the BIOS version
- tabcarecenter.exe (PID: 1936)
- tabdashboard.exe (PID: 3384)
- taboptimize.exe (PID: 2420)
- Integrator.exe (PID: 2400)
- tabprotect.exe (PID: 3396)
Searches for installed software
- taboptimize.exe (PID: 2420)
- tabmaintain.exe (PID: 2256)
- DeepDiskCleaner.exe (PID: 964)
- taboneclickscanner.exe (PID: 3848)
- Integrator.exe (PID: 2400)
INFO
Manual execution by user
- cmd.exe (PID: 2768)
- AusLogicsBoostSpeed11Portable.exe (PID: 3616)
- AusLogicsBoostSpeed11Portable.exe (PID: 992)
Reads the hosts file
- Auslogics.BoostSpeed.v11.2.0.3.exe (PID: 3852)
Dropped object may contain Bitcoin addresses
- Auslogics.BoostSpeed.v11.2.0.3.exe (PID: 3852)
Reads Microsoft Office registry keys
- taboneclickscanner.exe (PID: 3848)
- taboptimize.exe (PID: 2420)
- tabmaintain.exe (PID: 2256)
- Integrator.exe (PID: 2400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:11:21 15:19:21 |
| ZipCRC: | 0x6d55d152 |
| ZipCompressedSize: | 29051371 |
| ZipUncompressedSize: | 29051371 |
| ZipFileName: | Auslogics.BoostSpeed.v11.2.0.3.exe |
Total processes
76
Monitored processes
26
Malicious processes
15
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | "C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\DeepDiskCleaner.exe" | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\DeepDiskCleaner.exe | — | taballtools.exe | |||||||||||
User: admin Company: Auslogics Integrity Level: HIGH Description: Deep Disk Cleaner Exit code: 0 Version: 11.2.0.3 Modules
| |||||||||||||||
| 992 | "C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\AusLogicsBoostSpeed11Portable.exe" | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\AusLogicsBoostSpeed11Portable.exe | — | explorer.exe | |||||||||||
User: admin Company: CWER.ws/portable Integrity Level: MEDIUM Description: AusLogics BoostSpeed 11 Portable Exit code: 3221226540 Version: 2019.06.02.0 Modules
| |||||||||||||||
| 1812 | "C:\Users\admin\Desktop\Auslogics.BoostSpeed.v11.2.0.3.exe" /S /P | C:\Users\admin\Desktop\Auslogics.BoostSpeed.v11.2.0.3.exe | — | cmd.exe | |||||||||||
User: admin Company: Auslogics Software Pty Ltd. Integrity Level: MEDIUM Description: Auslogics BoostSpeed v11.2.0.3 Exit code: 3221226540 Version: 11.2.0.3 Modules
| |||||||||||||||
| 1856 | "C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\taballtools.exe" | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\taballtools.exe | — | Integrator.exe | |||||||||||
User: admin Company: Auslogics Integrity Level: HIGH Description: AllTools Exit code: 0 Version: 11.2.0.3 Modules
| |||||||||||||||
| 1936 | "C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\tabcarecenter.exe" | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\tabcarecenter.exe | Integrator.exe | ||||||||||||
User: admin Company: Auslogics Integrity Level: HIGH Description: Care Center Exit code: 0 Version: 11.2.0.3 Modules
| |||||||||||||||
| 2084 | "C:\Users\admin\AppData\Local\Temp\nso289E.tmp\ns2BBD.tmp" route.exe delete 95.141.193.133 | C:\Users\admin\AppData\Local\Temp\nso289E.tmp\ns2BBD.tmp | — | Auslogics.BoostSpeed.v11.2.0.3.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\AppData\Local\Temp\nso289E.tmp\ns28AF.tmp" netsh.exe advfirewall firewall delete rule name="all" remoteip=95.141.193.133 | C:\Users\admin\AppData\Local\Temp\nso289E.tmp\ns28AF.tmp | — | Auslogics.BoostSpeed.v11.2.0.3.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2232 | "C:\Users\admin\Desktop\Auslogics.BoostSpeed.v11.2.0.3.exe" /S /P | C:\Users\admin\Desktop\Auslogics.BoostSpeed.v11.2.0.3.exe | — | cmd.exe | |||||||||||
User: admin Company: Auslogics Software Pty Ltd. Integrity Level: MEDIUM Description: Auslogics BoostSpeed v11.2.0.3 Exit code: 3221226540 Version: 11.2.0.3 Modules
| |||||||||||||||
| 2256 | "C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\tabmaintain.exe" | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\tabmaintain.exe | — | Integrator.exe | |||||||||||
User: admin Company: Auslogics Integrity Level: HIGH Description: Maintain Exit code: 0 Version: 11.2.0.3 Modules
| |||||||||||||||
| 2400 | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\Integrator.exe | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\Integrator.exe | AusLogicsBoostSpeed11Portable.exe | ||||||||||||
User: admin Company: Auslogics Integrity Level: HIGH Description: BoostSpeed Exit code: 0 Version: 11.2.0.3 Modules
| |||||||||||||||
Total events
18 967
Read events
18 496
Write events
438
Delete events
33
Modification events
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Auslogics.BoostSpeed.v11.2.0.3.zip | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6003 |
Value: Windows Command Script | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
108
Suspicious files
8
Text files
5
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
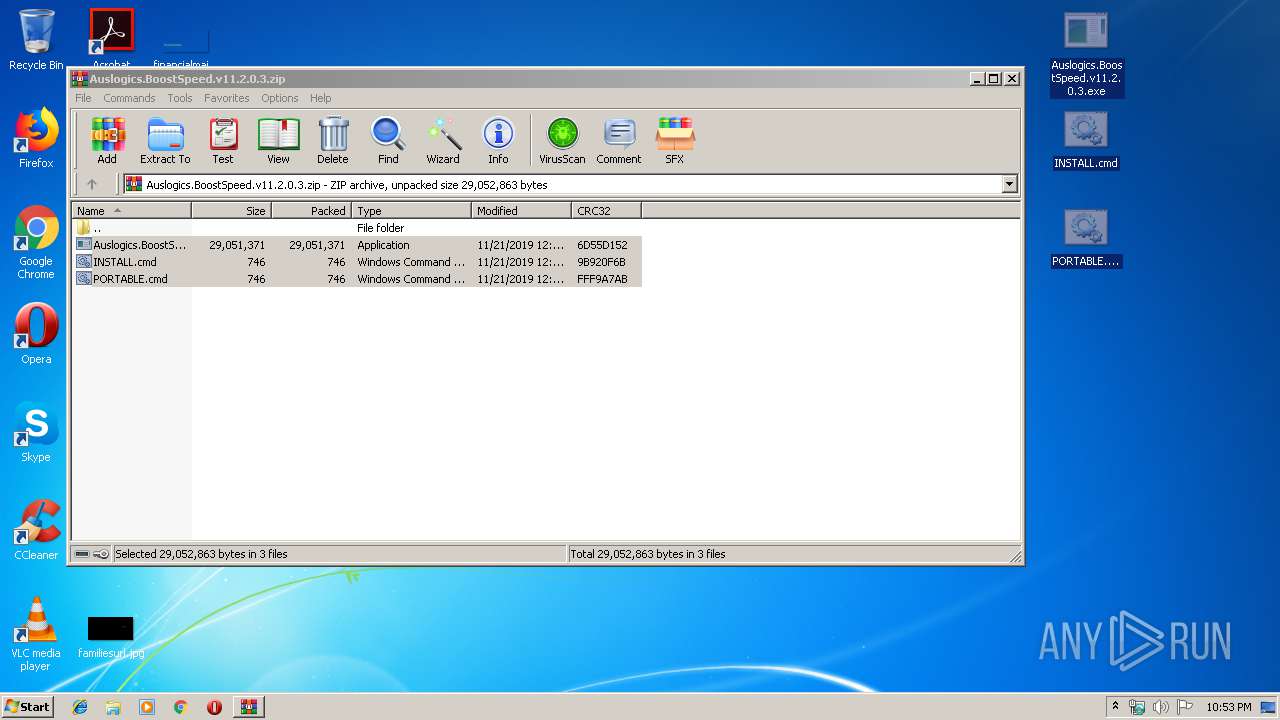
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21212\Auslogics.BoostSpeed.v11.2.0.3.exe | — | |
MD5:— | SHA256:— | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21212\INSTALL.cmd | — | |
MD5:— | SHA256:— | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21212\PORTABLE.cmd | — | |
MD5:— | SHA256:— | |||
| 3852 | Auslogics.BoostSpeed.v11.2.0.3.exe | C:\Users\admin\AppData\Local\Temp\nso289E.tmp\ns2BBD.tmp | — | |
MD5:— | SHA256:— | |||
| 3852 | Auslogics.BoostSpeed.v11.2.0.3.exe | C:\Users\admin\AppData\Local\Temp\nso289E.tmp\nsExec.dll | executable | |
MD5:132E6153717A7F9710DCEA4536F364CD | SHA256:D29AFCE2588D8DD7BB94C00CA91CAC0E85B80FFA6B221F5FFCB83A2497228EB2 | |||
| 3852 | Auslogics.BoostSpeed.v11.2.0.3.exe | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\BrowserPluginsHelper.Agent.x32.dll | executable | |
MD5:— | SHA256:— | |||
| 3852 | Auslogics.BoostSpeed.v11.2.0.3.exe | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\AdvisorHelper.dll | executable | |
MD5:— | SHA256:— | |||
| 3852 | Auslogics.BoostSpeed.v11.2.0.3.exe | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\BrowserPluginsHelper.Agent.x64.dll | executable | |
MD5:— | SHA256:— | |||
| 3852 | Auslogics.BoostSpeed.v11.2.0.3.exe | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\CFAHelper.dll | executable | |
MD5:— | SHA256:— | |||
| 3852 | Auslogics.BoostSpeed.v11.2.0.3.exe | C:\Users\admin\Desktop\AuslogicsBoostSpeedPortable\App\BoostSpeed\BrowserProtectionHelper.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
18
DNS requests
12
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 13.35.254.41:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
— | — | GET | 200 | 13.35.254.89:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEA4vBMJJxPg6SKCVbxEbKkA%3D | US | der | 471 b | whitelisted |
— | — | GET | 200 | 52.222.149.158:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
— | — | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.4 Kb | whitelisted |
1080 | svchost.exe | GET | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/GTSGIAG3/MEkwRzBFMEMwQTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCCC7Rp3EQG0zo | US | binary | 5 b | whitelisted |
— | — | GET | 200 | 143.204.208.108:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
— | — | GET | 200 | 143.204.208.196:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2400 | Integrator.exe | HEAD | 200 | 45.33.8.241:80 | http://ads.auslogics.com/uploads/50af3d5413855c55b7843c2659c42f65.png | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2400 | Integrator.exe | 52.201.171.253:443 | abs.aslgics.com | Amazon.com, Inc. | US | unknown |
— | — | 205.185.216.10:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
— | — | 13.35.254.41:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
— | — | 143.204.208.108:80 | ocsp.rootca1.amazontrust.com | — | US | whitelisted |
— | — | 13.35.254.89:80 | ocsp.sca1b.amazontrust.com | — | US | whitelisted |
2400 | Integrator.exe | 45.33.8.241:443 | ads.auslogics.com | Linode, LLC | US | malicious |
1936 | tabcarecenter.exe | 45.33.8.241:443 | ads.auslogics.com | Linode, LLC | US | malicious |
2400 | Integrator.exe | 45.33.8.241:80 | ads.auslogics.com | Linode, LLC | US | malicious |
3384 | tabdashboard.exe | 45.33.8.241:443 | ads.auslogics.com | Linode, LLC | US | malicious |
1080 | svchost.exe | 172.217.22.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
abs.aslgics.com |
| unknown |
x.ss2.us |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
ads.auslogics.com |
| whitelisted |
www.auslogics.com |
| whitelisted |
qa.auslogics.com |
| malicious |
Threats
5 ETPRO signatures available at the full report