| File name: | wait.exe |
| Full analysis: | https://app.any.run/tasks/a0a785f7-0aeb-4e05-bf91-bc5ab7896c6a |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2019, 12:07:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 1118A05976B0EBC02D238D0F841C6109 |
| SHA1: | 5820AC680D03E1D2083BEEAA6105D9A0C27E3C56 |
| SHA256: | 94248E593E0480BA8119262CDBD2B4496741BBAD414F79304572395DDE0F1B81 |
| SSDEEP: | 6144:vOLN1J6J0G46rSpZrawZWjfprZ9vP+h7LbrwM8uBGF1DfsBqUfei2rOJkGlVep4K:vY1qNsLrQdZyLrwM0BEAQ2rzFda6r5/d |
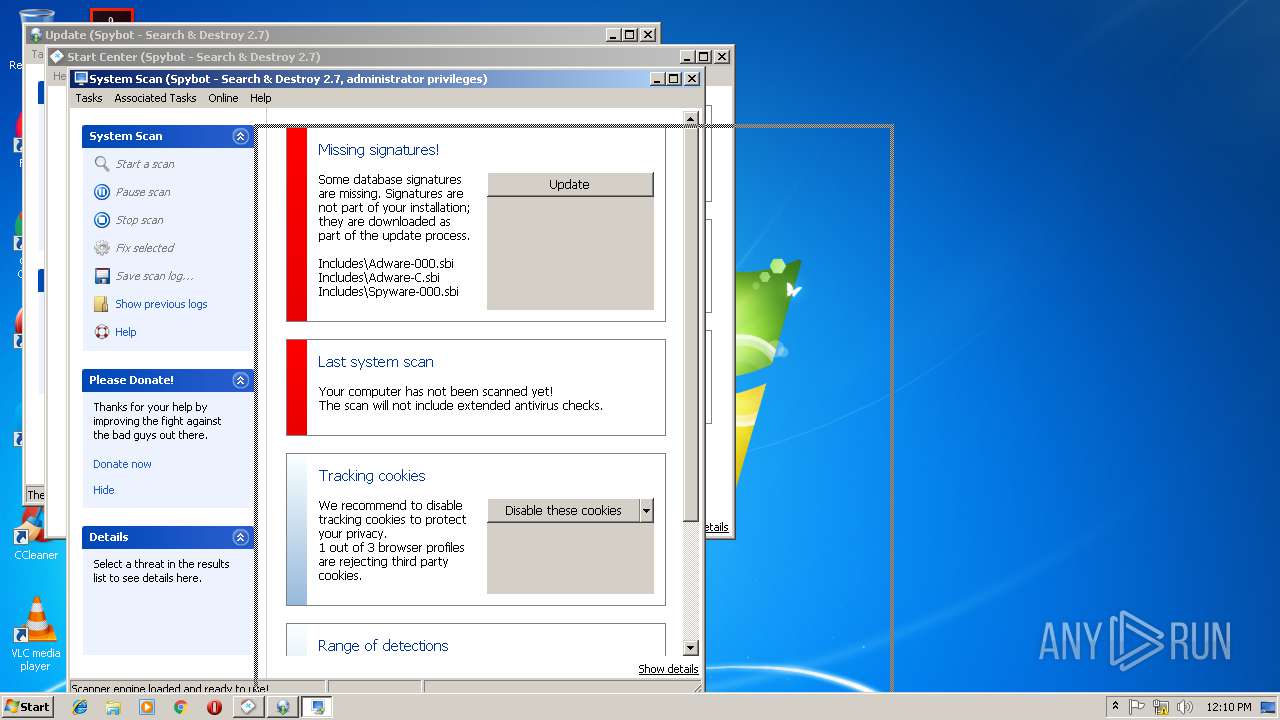
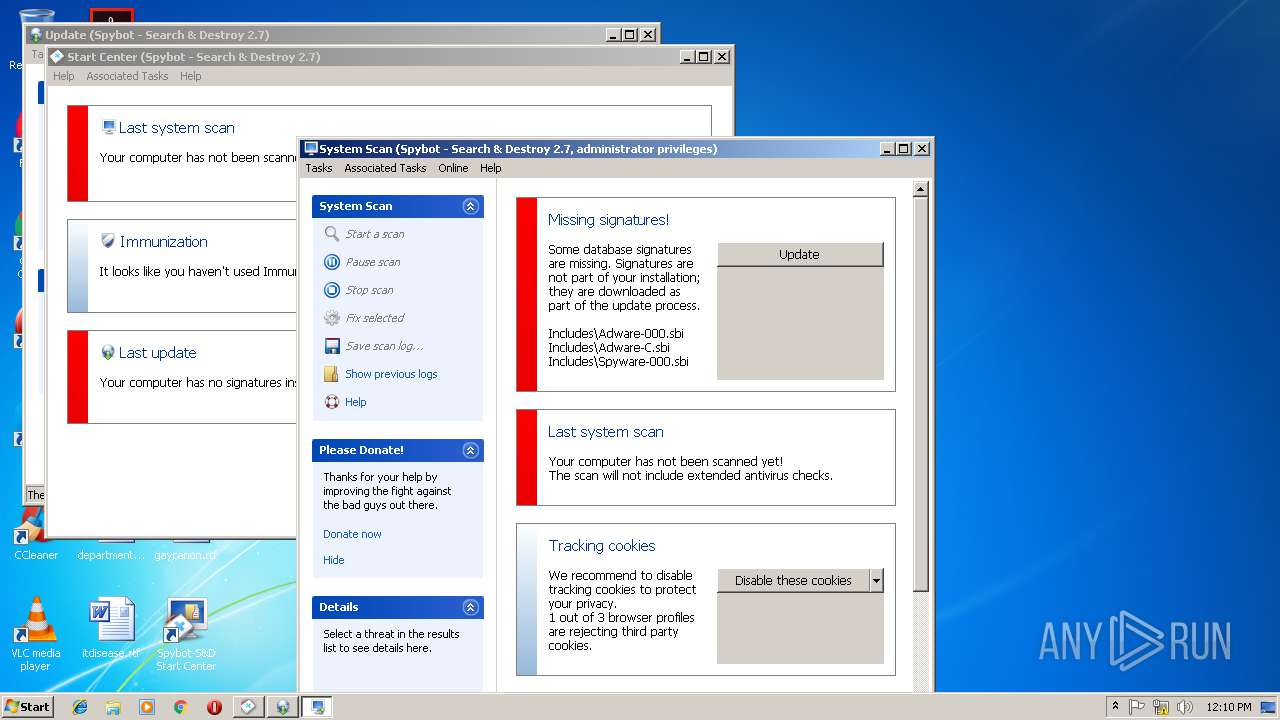
MALICIOUS
Changes the autorun value in the registry
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
Application was dropped or rewritten from another process
- SDTray.exe (PID: 3416)
- SDFSSvc.exe (PID: 2188)
- SDUpdSvc.exe (PID: 3844)
- SDUpdate.exe (PID: 2116)
- SDWelcome.exe (PID: 2860)
- SDUpdate.exe (PID: 2672)
- SDScan.exe (PID: 2888)
- SDScan.exe (PID: 1996)
- SDImmunize.exe (PID: 2740)
- SDImmunize.exe (PID: 1604)
- SDUpdate.exe (PID: 3420)
- spybotsd2-install-license-installer.exe (PID: 792)
- spybotsd2-install-license-installer.tmp (PID: 3332)
- spybotsd2-SDLicense-websitev3.tmp (PID: 3200)
- spybotsd2-SDLicense-websitev3.exe (PID: 3128)
Loads dropped or rewritten executable
- SDTray.exe (PID: 3416)
- SDFSSvc.exe (PID: 2188)
- SDUpdSvc.exe (PID: 3844)
- SDUpdate.exe (PID: 2116)
- SDWelcome.exe (PID: 2860)
- SDUpdate.exe (PID: 2672)
- SDScan.exe (PID: 1996)
- SDImmunize.exe (PID: 1604)
- SDUpdate.exe (PID: 3420)
Actions looks like stealing of personal data
- SDTray.exe (PID: 3416)
- SDUpdSvc.exe (PID: 3844)
- SDUpdate.exe (PID: 2116)
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
- SDWelcome.exe (PID: 2860)
- SDUpdate.exe (PID: 2672)
- SDFSSvc.exe (PID: 2188)
- SDUpdate.exe (PID: 3420)
- SDScan.exe (PID: 1996)
- SDImmunize.exe (PID: 1604)
Loads the Task Scheduler DLL interface
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
Loads the Task Scheduler COM API
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
SUSPICIOUS
Executable content was dropped or overwritten
- spybotsd-2.7.64.0[1].exe (PID: 2488)
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
- spybotsd-2.7.64.0[1].exe (PID: 2664)
- spybotsd2-install-license-installer.exe (PID: 792)
- SDUpdSvc.exe (PID: 3844)
- spybotsd2-install-license-installer.tmp (PID: 3332)
- spybotsd2-SDLicense-websitev3.exe (PID: 3128)
- spybotsd2-SDLicense-websitev3.tmp (PID: 3200)
Reads the Windows organization settings
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
- spybotsd2-install-license-installer.tmp (PID: 3332)
- spybotsd2-SDLicense-websitev3.tmp (PID: 3200)
Reads Windows owner or organization settings
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
- spybotsd2-install-license-installer.tmp (PID: 3332)
- spybotsd2-SDLicense-websitev3.tmp (PID: 3200)
Creates COM task schedule object
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
Creates executable files which already exist in Windows
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
Creates files in the Windows directory
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
- SDFSSvc.exe (PID: 2188)
- SDUpdate.exe (PID: 2116)
- SDUpdSvc.exe (PID: 3844)
- spybotsd2-install-license-installer.exe (PID: 792)
- spybotsd2-SDLicense-websitev3.exe (PID: 3128)
Modifies the open verb of a shell class
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
- spybotsd2-install-license-installer.tmp (PID: 3332)
Creates or modifies windows services
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
- SDTray.exe (PID: 3416)
- SDFSSvc.exe (PID: 2188)
- SDUpdSvc.exe (PID: 3844)
Reads Environment values
- SDTray.exe (PID: 3416)
- SDFSSvc.exe (PID: 2188)
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
- SDUpdate.exe (PID: 2116)
- SDUpdate.exe (PID: 2672)
- SDWelcome.exe (PID: 2860)
- SDScan.exe (PID: 1996)
- SDImmunize.exe (PID: 1604)
- SDUpdate.exe (PID: 3420)
- SDUpdSvc.exe (PID: 3844)
Creates files in the program directory
- SDTray.exe (PID: 3416)
- SDFSSvc.exe (PID: 2188)
- SDUpdSvc.exe (PID: 3844)
- SDImmunize.exe (PID: 1604)
- SDUpdate.exe (PID: 3420)
- spybotsd2-install-license-installer.tmp (PID: 3332)
- spybotsd2-SDLicense-websitev3.tmp (PID: 3200)
Removes files from Windows directory
- SDFSSvc.exe (PID: 2188)
- SDUpdate.exe (PID: 2116)
- SDUpdSvc.exe (PID: 3844)
- spybotsd2-install-license-installer.tmp (PID: 3332)
- spybotsd2-install-license-installer.exe (PID: 792)
- spybotsd2-SDLicense-websitev3.tmp (PID: 3200)
- spybotsd2-SDLicense-websitev3.exe (PID: 3128)
Creates files in the user directory
- SDWelcome.exe (PID: 2860)
- SDUpdate.exe (PID: 2672)
- SDScan.exe (PID: 1996)
- SDImmunize.exe (PID: 1604)
- SDUpdate.exe (PID: 3420)
Reads the cookies of Mozilla Firefox
- SDImmunize.exe (PID: 1604)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3992)
- iexplore.exe (PID: 2872)
Reads internet explorer settings
- iexplore.exe (PID: 3992)
Changes internet zones settings
- iexplore.exe (PID: 2872)
Application was dropped or rewritten from another process
- spybotsd-2.7.64.0[1].tmp (PID: 904)
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
Application launched itself
- iexplore.exe (PID: 2872)
Creates a software uninstall entry
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
Loads dropped or rewritten executable
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
Creates files in the program directory
- spybotsd-2.7.64.0[1].tmp (PID: 3336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (25.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (22.8) |
| .exe | | | UPX compressed Win32 Executable (22.3) |
| .exe | | | Win32 EXE Yoda's Crypter (21.9) |
| .exe | | | Win32 Executable (generic) (3.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:05:28 19:39:42+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 8192 |
| InitializedDataSize: | 16384 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2196 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | - |
| ProductVersion: | - |
| Comment: | - |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 28-May-2013 17:39:42 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | - |
| zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz: | - |
| FileDescription: | - |
| zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz: | - |
| FileVersion: | 1.0.0.0 |
| zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz: | - |
| InternalName: | - |
| zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz: | - |
| LegalCopyright: | - |
| zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz: | - |
| LegalTrademarks: | - |
| OriginalFilename: | - |
| zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz: | - |
| ProductName: | - |
| ProductVersion: | - |
| Comment: | - |
| zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 28-May-2013 17:39:42 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000012EC | 0x00002000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 4.24172 |
.rdata | 0x00003000 | 0x0000096A | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.66782 |
.data | 0x00004000 | 0x00000290 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.0578391 |
.rsrc | 0x00005000 | 0x000010A0 | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.43 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 1.8011 | 2868 | UNKNOWN | English - United States | RT_VERSION |
2 | 2.00385 | 296 | UNKNOWN | English - United States | RT_ICON |
PERLEXE | 2.37086 | 34 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
KERNEL32.dll |
MSVCRT.dll |
USER32.dll |
Total processes
67
Monitored processes
23
Malicious processes
19
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 792 | "C:\Program Files\Spybot - Search & Destroy 2\spybotsd2-install-license-installer.exe" /silent /verysilent /norestart | C:\Program Files\Spybot - Search & Destroy 2\spybotsd2-install-license-installer.exe | SDUpdSvc.exe | ||||||||||||
User: SYSTEM Company: Safer-Networking Ltd. Integrity Level: SYSTEM Description: License installer update for Spybot - Search & Destroy Exit code: 0 Version: 2.7.65.0 Modules
| |||||||||||||||
| 904 | "C:\Users\admin\AppData\Local\Temp\is-4VR1N.tmp\spybotsd-2.7.64.0[1].tmp" /SL5="$60188,69389626,206848,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\spybotsd-2.7.64.0[1].exe" | C:\Users\admin\AppData\Local\Temp\is-4VR1N.tmp\spybotsd-2.7.64.0[1].tmp | — | spybotsd-2.7.64.0[1].exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1604 | "C:\Program Files\Spybot - Search & Destroy 2\SDImmunize.exe" /check | C:\Program Files\Spybot - Search & Destroy 2\SDImmunize.exe | SDWelcome.exe | ||||||||||||
User: admin Company: Safer-Networking Ltd. Integrity Level: HIGH Description: Pro-active browser protection Exit code: 0 Version: 2.7.64.133 Modules
| |||||||||||||||
| 1996 | "C:\Program Files\Spybot - Search & Destroy 2\SDScan.exe" /scan | C:\Program Files\Spybot - Search & Destroy 2\SDScan.exe | SDWelcome.exe | ||||||||||||
User: admin Company: Safer-Networking Ltd. Integrity Level: HIGH Description: Malware Scanner Exit code: 0 Version: 2.7.64.191 Modules
| |||||||||||||||
| 2116 | "C:\Program Files\Spybot - Search & Destroy 2\SDUpdate.exe" /autoupdate /silent /autoclose /background | C:\Program Files\Spybot - Search & Destroy 2\SDUpdate.exe | taskeng.exe | ||||||||||||
User: SYSTEM Company: Safer-Networking Ltd. Integrity Level: SYSTEM Description: Update Exit code: 0 Version: 2.7.64.98 Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Spybot - Search & Destroy 2\SDFSSvc.exe" | C:\Program Files\Spybot - Search & Destroy 2\SDFSSvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Safer-Networking Ltd. Integrity Level: SYSTEM Description: Spybot-S&D 2 Scanner Service Exit code: 0 Version: 2.7.64.219 Modules
| |||||||||||||||
| 2488 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\spybotsd-2.7.64.0[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\spybotsd-2.7.64.0[1].exe | iexplore.exe | ||||||||||||
User: admin Company: Safer-Networking Ltd. Integrity Level: MEDIUM Description: Spybot - Search & Destroy Exit code: 0 Version: 2.7.64.0 Modules
| |||||||||||||||
| 2652 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2664 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\spybotsd-2.7.64.0[1].exe" /SPAWNWND=$2024A /NOTIFYWND=$60188 | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\spybotsd-2.7.64.0[1].exe | spybotsd-2.7.64.0[1].tmp | ||||||||||||
User: admin Company: Safer-Networking Ltd. Integrity Level: HIGH Description: Spybot - Search & Destroy Exit code: 0 Version: 2.7.64.0 Modules
| |||||||||||||||
| 2672 | "C:\Program Files\Spybot - Search & Destroy 2\SDUpdate.exe" /autoupdate | C:\Program Files\Spybot - Search & Destroy 2\SDUpdate.exe | spybotsd-2.7.64.0[1].tmp | ||||||||||||
User: admin Company: Safer-Networking Ltd. Integrity Level: MEDIUM Description: Update Exit code: 0 Version: 2.7.64.98 Modules
| |||||||||||||||
Total events
4 572
Read events
3 640
Write events
910
Delete events
22
Modification events
| (PID) Process: | (2872) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2872) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2872) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2872) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2872) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2872) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2872) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {76579359-1F07-11E9-91D7-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2872) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2872) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2872) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070100030017000C00070021000402 | |||
Executable files
96
Suspicious files
191
Text files
1 620
Unknown types
253
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3120 | wait.exe | C:\Users\admin\AppData\Local\Temp\p2xtmp-3120\p2x5163.dll | — | |
MD5:— | SHA256:— | |||
| 2872 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2872 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3992 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\spybotsd-2.7.64.0[1].exe | — | |
MD5:— | SHA256:— | |||
| 2872 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\spybotsd-2.7.64.0[1].exe | — | |
MD5:— | SHA256:— | |||
| 2872 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF9348599F5E92D544.TMP | — | |
MD5:— | SHA256:— | |||
| 2872 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{4BBB6F4B-AC5C-11E8-969E-5254004AAD11}.dat | — | |
MD5:— | SHA256:— | |||
| 2872 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFD562CDCF4A7C2BF9.TMP | — | |
MD5:— | SHA256:— | |||
| 2872 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{7657935A-1F07-11E9-91D7-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 2872 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0B7C9024AF962403.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
143
TCP/UDP connections
161
DNS requests
15
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2188 | SDFSSvc.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSFDxAmS5JEAmWxO0Ue9OdQ9z7zPAQUFQASKxOYspkH7R7for5XDStnAs0CEAMBmgI6%2F1ixa9bV6uYX8GY%3D | US | der | 471 b | whitelisted |
2188 | SDFSSvc.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | US | der | 471 b | whitelisted |
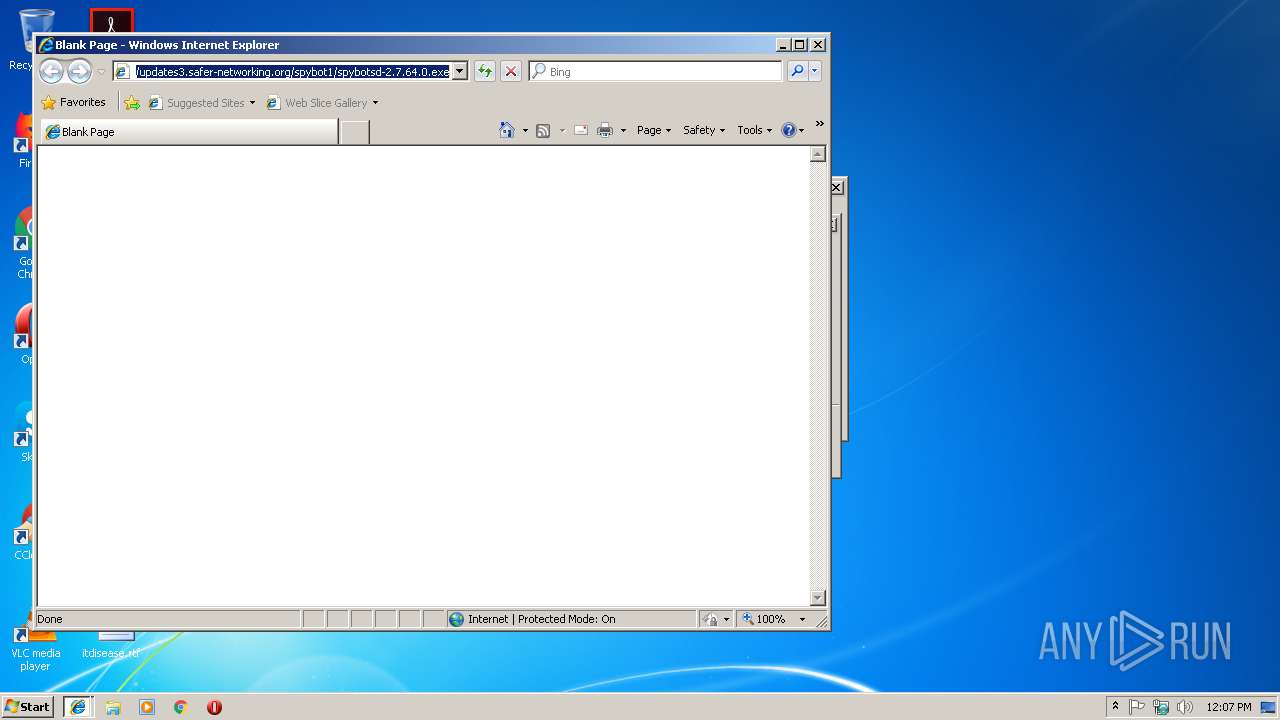
3420 | SDUpdate.exe | GET | 200 | 5.196.84.219:80 | http://updates3.safer-networking.org/spybotsd2.uid | FR | binary | 16.3 Kb | suspicious |
3416 | SDTray.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEAs%2F0y45skewnIBAVx1q0vM%3D | US | der | 471 b | whitelisted |
3416 | SDTray.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSFDxAmS5JEAmWxO0Ue9OdQ9z7zPAQUFQASKxOYspkH7R7for5XDStnAs0CEAMBmgI6%2F1ixa9bV6uYX8GY%3D | US | der | 471 b | whitelisted |
3416 | SDTray.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAb9%2BQOWA63qAArrPye7uhs%3D | US | der | 471 b | whitelisted |
3416 | SDTray.exe | GET | 200 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 55.2 Kb | whitelisted |
2188 | SDFSSvc.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAb9%2BQOWA63qAArrPye7uhs%3D | US | der | 471 b | whitelisted |
3844 | SDUpdSvc.exe | GET | 200 | 163.172.168.58:80 | http://updates2.safer-networking.org/spybotsd2.uid | FR | binary | 16.3 Kb | suspicious |
2188 | SDFSSvc.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEAs%2F0y45skewnIBAVx1q0vM%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2872 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3992 | iexplore.exe | 5.196.84.219:443 | updates3.safer-networking.org | OVH SAS | FR | unknown |
3336 | spybotsd-2.7.64.0[1].tmp | 167.114.117.64:80 | www.safer-networking.org | OVH SAS | CA | unknown |
3416 | SDTray.exe | 2.16.186.81:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3416 | SDTray.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2188 | SDFSSvc.exe | 205.185.216.10:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2188 | SDFSSvc.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3844 | SDUpdSvc.exe | 163.172.168.58:80 | updates2.safer-networking.org | Online S.a.s. | FR | suspicious |
3844 | SDUpdSvc.exe | 50.21.178.242:80 | sbsd-dl-us.com | 1&1 Internet SE | US | suspicious |
3844 | SDUpdSvc.exe | 5.196.84.219:80 | updates3.safer-networking.org | OVH SAS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
updates3.safer-networking.org |
| suspicious |
www.safer-networking.org |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
updates2.safer-networking.org |
| suspicious |
filehorse.sbsd-updates.eu |
| malicious |
sbsd-dl-us.com |
| whitelisted |
sbsd-dl-uk.com |
| suspicious |
sbsd-dl-eu.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3336 | spybotsd-2.7.64.0[1].tmp | Misc activity | SUSPICIOUS [PTsecurity] HTTP GET method with POST body (RFC7231) |
3844 | SDUpdSvc.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
Process | Message |
|---|---|
SDTray.exe | C:\Program Files\Spybot - Search & Destroy 2\SDLicense.dll: GetCodeSignatureIssuerPE: -1 |
SDTray.exe | TMemoryMappedFileBase: Handle created, |
SDTray.exe | TMemoryMappedFileBase: Handle created, |
SDTray.exe | TMemoryMappedFileBase: Handle created, |
SDTray.exe | TMemoryMappedFileBase: Handle created, |
SDFSSvc.exe | C:\Program Files\Spybot - Search & Destroy 2\SDLicense.dll: GetCodeSignatureIssuerPE: -1 |
SDFSSvc.exe | sbsdWebTestLists.AddListFromFile: missing file Includes\GoodBanks.sbs |
SDFSSvc.exe | sbsdWebTestLists.AddListFromFile: missing file Includes\GoodBankScripts.sbs |
SDFSSvc.exe | TSDScannerService.ServiceCreate.1 |
SDFSSvc.exe | TMemoryMappedFileBase: Handle created, |