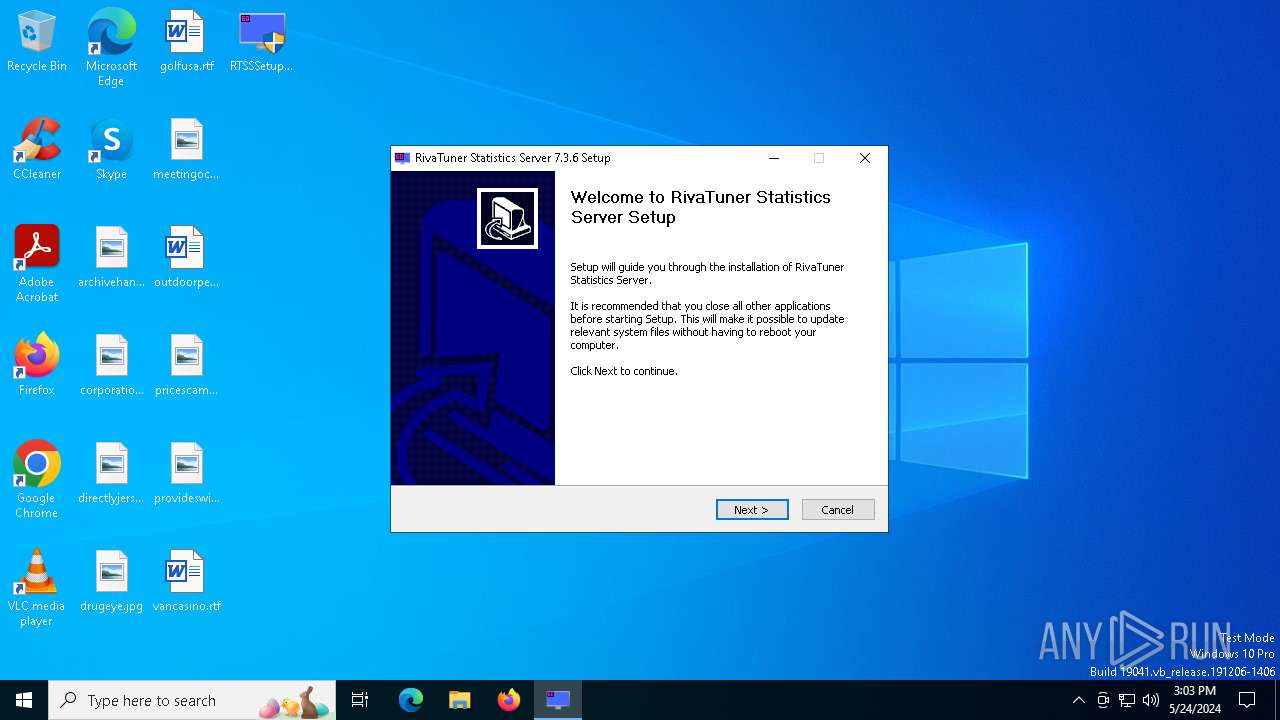
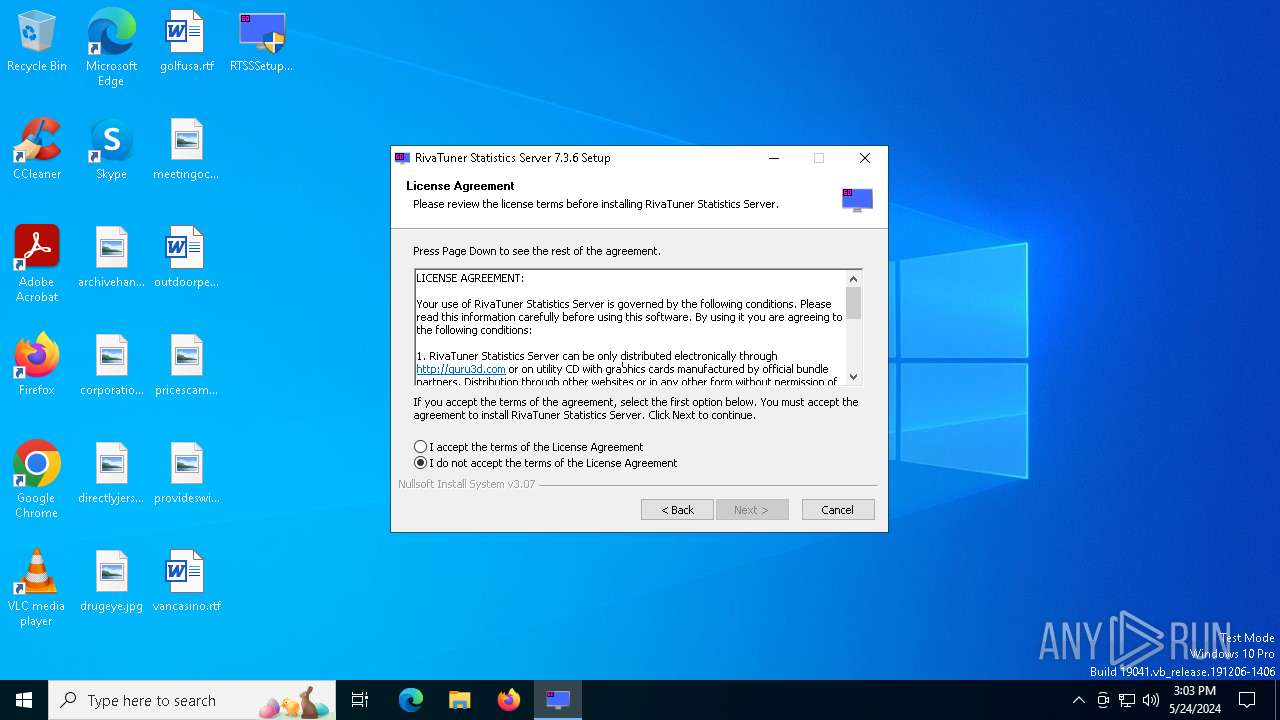
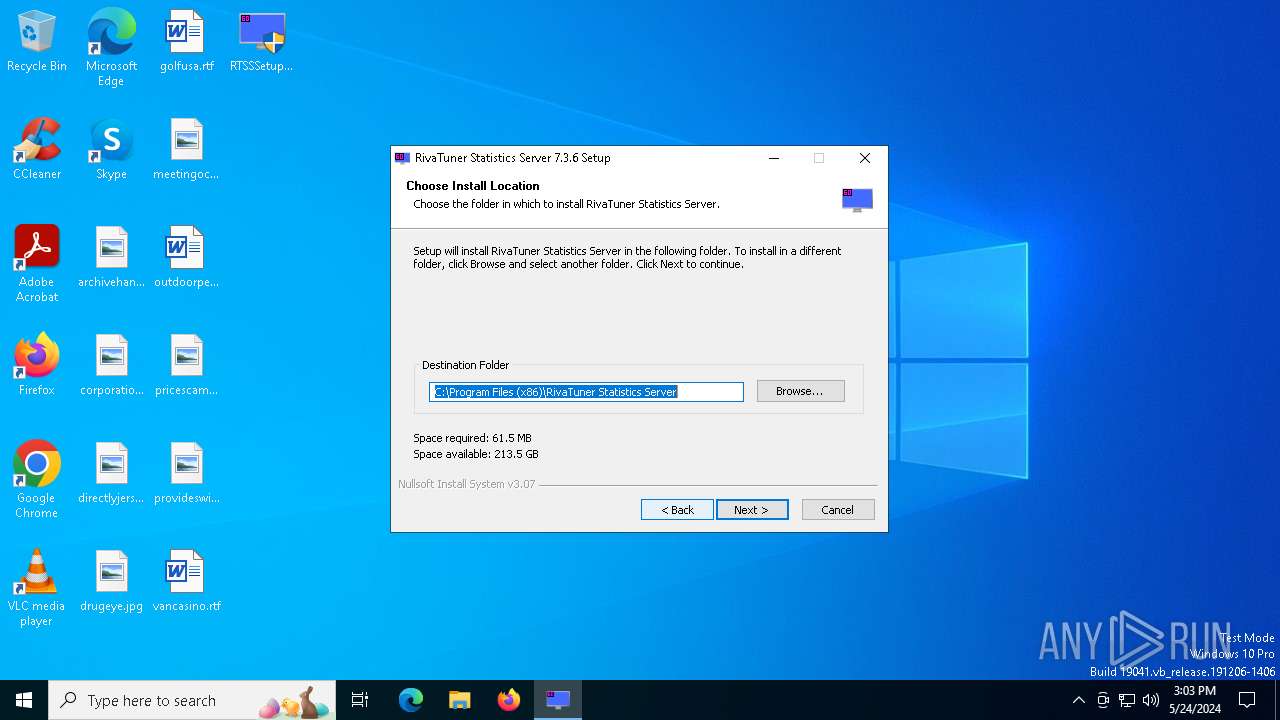
| File name: | RTSSSetup736.exe |
| Full analysis: | https://app.any.run/tasks/805a886d-f29b-4225-98c6-ca301b6bacfa |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2024, 15:03:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | F57C07115788603CF14320F2632F6668 |
| SHA1: | 28F8643EC2CCCAA623F045912453FC299A48F141 |
| SHA256: | 941CC44F629086310DBA8C9E96AB55994F230EEF6917A2E70EC6C9B698154D88 |
| SSDEEP: | 98304:9a8z5zI+ri6siIs6aThHszwCAlJMMoCApaEL14/zT3kGCbOmhjLuCT8g9Ng6x+hz:das/IhMIYDrwtWKe5QKmvEJAXAuSN |
MALICIOUS
Actions looks like stealing of personal data
- RTSSSetup736.exe (PID: 4936)
Drops the executable file immediately after the start
- RTSSSetup736.exe (PID: 4936)
- VCRedistWebSetup.exe (PID: 2800)
Creates a writable file in the system directory
- RTSSSetup736.exe (PID: 4936)
SUSPICIOUS
Executable content was dropped or overwritten
- RTSSSetup736.exe (PID: 4936)
Malware-specific behavior (creating "System.dll" in Temp)
- RTSSSetup736.exe (PID: 4936)
Creates a software uninstall entry
- RTSSSetup736.exe (PID: 4936)
Reads security settings of Internet Explorer
- RTSSSetup736.exe (PID: 4936)
- VCRedistWebSetup.exe (PID: 2800)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 5536)
- RTSSSetup736.exe (PID: 4936)
Reads the date of Windows installation
- RTSSSetup736.exe (PID: 4936)
Process drops legitimate windows executable
- RTSSSetup736.exe (PID: 4936)
- VCRedistWebSetup.exe (PID: 2800)
The process creates files with name similar to system file names
- RTSSSetup736.exe (PID: 4936)
Drops a system driver (possible attempt to evade defenses)
- RTSSSetup736.exe (PID: 4936)
Checks Windows Trust Settings
- VCRedistWebSetup.exe (PID: 2800)
Process requests binary or script from the Internet
- VCRedistWebSetup.exe (PID: 2800)
INFO
Reads the computer name
- RTSSSetup736.exe (PID: 4936)
- VCRedistWebSetup.exe (PID: 2800)
Create files in a temporary directory
- RTSSSetup736.exe (PID: 4936)
Checks supported languages
- RTSSSetup736.exe (PID: 4936)
- VCRedistWebSetup.exe (PID: 2800)
Process checks computer location settings
- RTSSSetup736.exe (PID: 4936)
Creates files in the program directory
- RTSSSetup736.exe (PID: 4936)
- VCRedistWebSetup.exe (PID: 2800)
Manual execution by a user
- mspaint.exe (PID: 3244)
- mspaint.exe (PID: 3692)
Creates files or folders in the user directory
- RTSSSetup736.exe (PID: 4936)
Reads the software policy settings
- VCRedistWebSetup.exe (PID: 2800)
Checks proxy server information
- VCRedistWebSetup.exe (PID: 2800)
Reads the machine GUID from the registry
- VCRedistWebSetup.exe (PID: 2800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:07:24 22:17:55+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x348f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
125
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2800 | "C:\Program Files (x86)\RivaTuner Statistics Server\Redist\VCRedistWebSetup.exe" /I /Q 2022 | C:\Program Files (x86)\RivaTuner Statistics Server\Redist\VCRedistWebSetup.exe | RTSSSetup736.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Microsoft Visual C++ redistributable web setup Version: 1.0.0.0 Modules
| |||||||||||||||
| 3244 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\pricescame.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3692 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\drugeye.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3724 | "C:\Windows\System32\rundll32.exe" LockedList64.dll,GetSystemModulesCount64 0x000B01D8 | C:\Windows\System32\rundll32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4936 | "C:\Users\admin\Desktop\RTSSSetup736.exe" | C:\Users\admin\Desktop\RTSSSetup736.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 5536 | "C:\Windows\System32\rundll32.exe" LockedList64.dll,GetSystemModulesCount64 0x000B01D8 | C:\Windows\SysWOW64\rundll32.exe | — | RTSSSetup736.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5776 | "C:\Users\admin\Desktop\RTSSSetup736.exe" | C:\Users\admin\Desktop\RTSSSetup736.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5824 | "C:\Windows\System32\rundll32.exe" LockedList64.dll,EnumSystemProcesses64 0x000C01D8 1 1 | C:\Windows\System32\rundll32.exe | — | RTSSSetup736.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 732
Read events
7 642
Write events
88
Delete events
2
Modification events
| (PID) Process: | (4936) RTSSSetup736.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4936) RTSSSetup736.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4936) RTSSSetup736.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4936) RTSSSetup736.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4936) RTSSSetup736.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RTSS |
| Operation: | write | Name: | Publisher |
Value: Unwinder | |||
| (PID) Process: | (4936) RTSSSetup736.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RTSS |
| Operation: | write | Name: | DisplayName |
Value: RivaTuner Statistics Server 7.3.6 | |||
| (PID) Process: | (4936) RTSSSetup736.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RTSS |
| Operation: | write | Name: | DisplayVersion |
Value: 7.3.6 | |||
| (PID) Process: | (4936) RTSSSetup736.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RTSS |
| Operation: | write | Name: | DisplayIcon |
Value: "C:\Program Files (x86)\RivaTuner Statistics Server\uninstall.exe" | |||
| (PID) Process: | (4936) RTSSSetup736.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RTSS |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\RivaTuner Statistics Server\uninstall.exe" | |||
| (PID) Process: | (3244) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | WindowPlacement |
Value: 2C00000000000000010000000000000000000000FFFFFFFFFFFFFFFF7F000000470000007F04000087020000 | |||
Executable files
70
Suspicious files
18
Text files
1 738
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4936 | RTSSSetup736.exe | C:\Users\admin\AppData\Local\Temp\nsf42B4.tmp\nsDialogs.dll | executable | |
MD5:CA5BB0EE2B698869C41C087C9854487C | SHA256:C719697D5CED17D97BBC48662327339CCEC7E03F6552AA1D5C248F6FA5F16324 | |||
| 4936 | RTSSSetup736.exe | C:\Program Files (x86)\RivaTuner Statistics Server\DesktopOverlayHostLoader.exe | executable | |
MD5:D9FF9504DA8B627B720FE8F62F3BD24D | SHA256:57DFCE7A5CFE97578A45B35731A327E88B22FEE0DBC4EC0B4DC1E919CC94E12F | |||
| 4936 | RTSSSetup736.exe | C:\Users\admin\AppData\Local\Temp\nsf42B4.tmp\LockedList.dll | executable | |
MD5:84C93011C323095555FCFCBEBAB4DF83 | SHA256:CF1B3D307918E11F4C90888EF65F9CAD0302EABF7235187EAAD5764646874340 | |||
| 4936 | RTSSSetup736.exe | C:\Users\admin\AppData\Local\Temp\nsf42B4.tmp\LangDLL.dll | executable | |
MD5:08DE81A4584F5201086F57A7A93ED83B | SHA256:4883CD4231744BE2DCA4433EF62824B7957A3C16BE54F8526270402D9413EBE6 | |||
| 4936 | RTSSSetup736.exe | C:\Program Files (x86)\RivaTuner Statistics Server\EncoderServer64.exe | executable | |
MD5:813F7094987655E2C6846EB1188AB420 | SHA256:F1BA5943A9010E879DBF832CB6741DAE3FC92E19F657CE69335AD904FDBDEAE4 | |||
| 4936 | RTSSSetup736.exe | C:\Users\admin\AppData\Local\Temp\nsf42B4.tmp\LockedList64.dll | executable | |
MD5:F982F688C44A109382504BE756E54A28 | SHA256:FBE4C84D389B32D3646991F0F59C987D5052ECC0ECBAA4DA2BBEBD922FD3762C | |||
| 4936 | RTSSSetup736.exe | C:\Program Files (x86)\RivaTuner Statistics Server\DesktopOverlayHost.exe | executable | |
MD5:7057CAB5E1D3D38D3D5A1F8F2F0CD7EF | SHA256:D594B3870D81FFDCBDA2CB630061CAC915D239E921B4AF7BF19C4FCB26FFCECA | |||
| 4936 | RTSSSetup736.exe | C:\Users\admin\AppData\Local\Temp\nsf42B4.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 4936 | RTSSSetup736.exe | C:\Users\admin\AppData\Local\Temp\nsf42B4.tmp\System.dll | executable | |
MD5:6E55A6E7C3FDBD244042EB15CB1EC739 | SHA256:ACF90AB6F4EDC687E94AAF604D05E16E6CFB5E35873783B50C66F307A35C6506 | |||
| 4936 | RTSSSetup736.exe | C:\Program Files (x86)\RivaTuner Statistics Server\libmfxsw32.dll | executable | |
MD5:6980F97A2A92DCE04C5CCE88028BD160 | SHA256:39AA5129F3E61473DE411A3E286A8AB2A410436923BBAA9320610DE30EE1DF5F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
25
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5952 | svchost.exe | GET | 200 | 2.16.164.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | 200 | 2.16.164.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5952 | svchost.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2800 | VCRedistWebSetup.exe | GET | 301 | 52.170.7.25:443 | https://aka.ms/vs/17/release/vc_redist.x86.exe | unknown | — | — | unknown |
2800 | VCRedistWebSetup.exe | GET | 301 | 52.170.7.25:443 | https://aka.ms/vs/17/release/vc_redist.x86.exe | unknown | — | — | unknown |
— | — | POST | 204 | 23.73.138.97:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
2800 | VCRedistWebSetup.exe | GET | 200 | 68.232.34.200:443 | https://download.visualstudio.microsoft.com/download/pr/9c69db26-cda4-472d-bdae-f2b87f4a0177/A32DD41EAAB0C5E1EAA78BE3C0BB73B48593DE8D97A7510B97DE3FD993538600/VC_redist.x86.exe | unknown | executable | 13.2 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4856 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5952 | svchost.exe | 2.16.164.114:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
— | — | 2.16.164.114:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5140 | MoUsoCoreWorker.exe | 2.16.164.114:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5952 | svchost.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
— | — | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
aka.ms |
| whitelisted |
download.visualstudio.microsoft.com |
| whitelisted |