| download: | /Information/f6UKALOfa0GZmo |
| Full analysis: | https://app.any.run/tasks/abc3efee-b1a6-49ff-929f-82bfaee61076 |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2025, 13:07:10 |
| OS: | Ubuntu 22.04.2 |
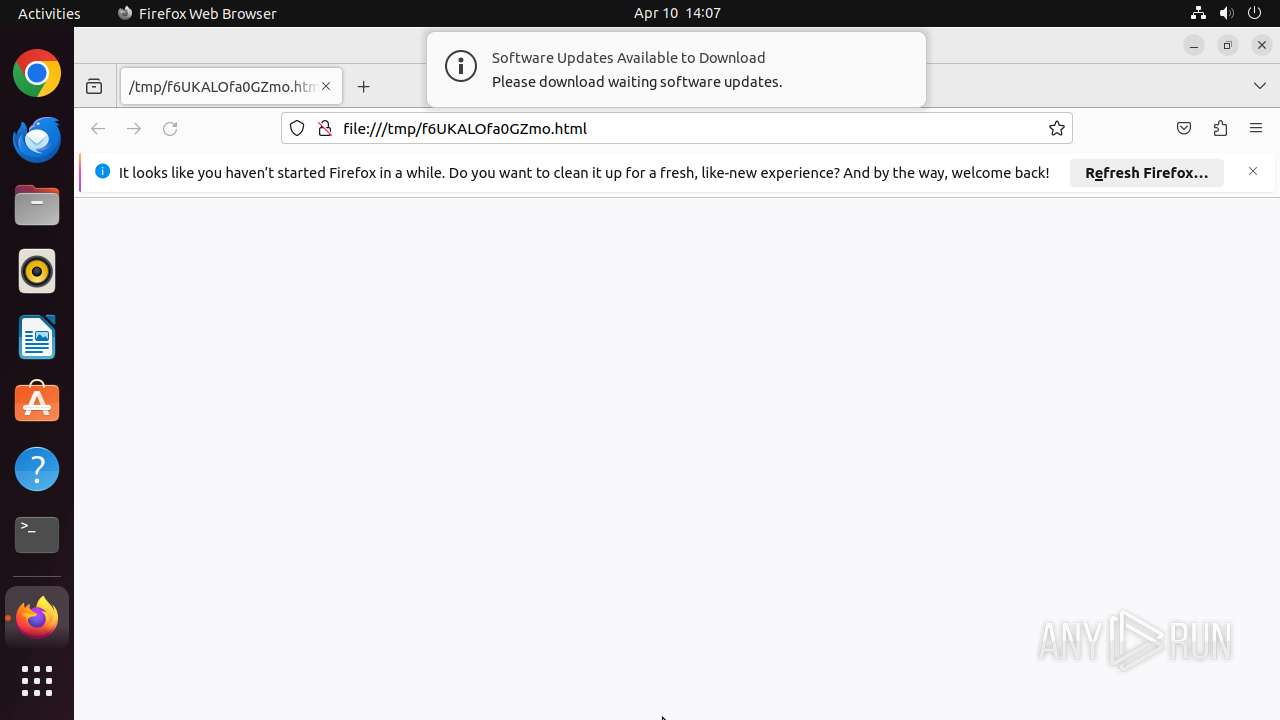
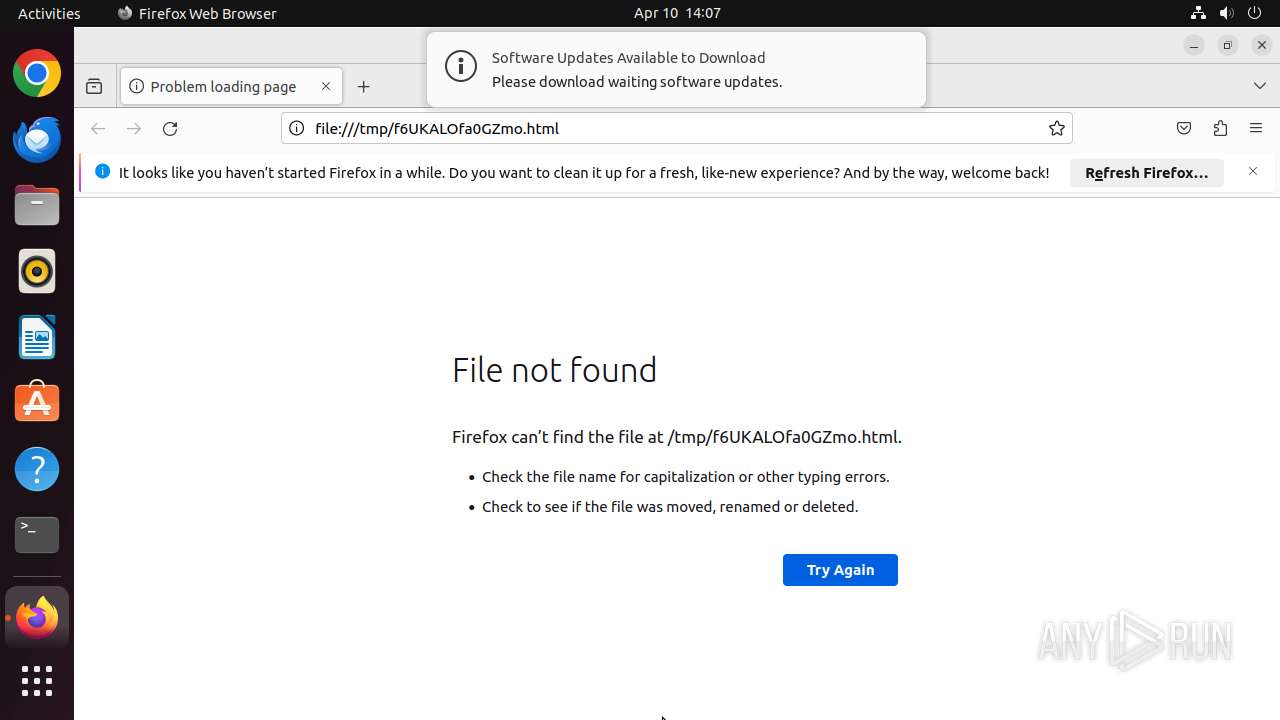
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines (302) |
| MD5: | 6B728DEFD4AC27F89D785A5AB8BF8853 |
| SHA1: | 16748A5A9414EAFA7C272DE07B7F924044426408 |
| SHA256: | 93FD8FD8AA0031E24F376285601C09DFFE7A0E177B80FBAFC4EDBAB2579AC4B8 |
| SSDEEP: | 96:05pkSO7mi0iOaGqT5PqUJVtsKdddatUdddRdddskxdddOTucxCx:0dami0iOafyQMOyPCx |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes commands using command-line interpreter
- sudo (PID: 40662)
- firefox (PID: 40663)
Check the Environment Variables Related to System Identification (os-release)
- snapctl (PID: 40714)
- snapctl (PID: 40758)
- firefox (PID: 40663)
- snapctl (PID: 40753)
- snapctl (PID: 40720)
Reads passwd file
- dumpe2fs (PID: 40694)
- dumpe2fs (PID: 40687)
INFO
Creates file in the temporary folder
- firefox (PID: 40663)
Checks timezone
- dumpe2fs (PID: 40687)
- dumpe2fs (PID: 40694)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| HTTPEquivXUACompatible: | IE=edge |
|---|---|
| Viewport: | width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no |
| CacheControl: | no-store, no-cache, must-revalidate |
| Pragma: | no-cache |
| Expires: | - |
| Robots: | noindex, nofollow |
| GoogleBot: | noindex, nofollow |
| Title: | File Link Information - BiteBlob |
Total processes
393
Monitored processes
173
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 40661 | /bin/sh -c "DISPLAY=:0 sudo -iu user firefox /tmp/f6UKALOfa0GZmo\.html " | /usr/bin/dash | — | any-guest-agent |
User: user Integrity Level: UNKNOWN | ||||
| 40662 | sudo -iu user firefox /tmp/f6UKALOfa0GZmo.html | /usr/bin/sudo | — | dash |
User: root Integrity Level: UNKNOWN | ||||
| 40663 | /snap/firefox/3358/usr/lib/firefox/firefox /tmp/f6UKALOfa0GZmo.html | /snap/firefox/3358/usr/lib/firefox/firefox | sudo | |
User: user Integrity Level: UNKNOWN | ||||
| 40664 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40678 | /snap/snapd/20290/usr/lib/snapd/snap-seccomp version-info | /snap/snapd/20290/usr/lib/snapd/snap-seccomp | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40686 | /snap/snapd/20290/usr/lib/snapd/snap-confine --base core22 snap.firefox.firefox /usr/lib/snapd/snap-exec firefox /tmp/f6UKALOfa0GZmo.html | /snap/snapd/20290/usr/lib/snapd/snap-confine | — | firefox |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40687 | dumpe2fs -h /dev/sda3 | /usr/sbin/dumpe2fs | — | udisksd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40688 | snap-update-ns --from-snap-confine firefox | /snap/snapd/20290/usr/lib/snapd/snap-update-ns | — | firefox |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40694 | dumpe2fs -h /dev/sda3 | /usr/sbin/dumpe2fs | — | udisksd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40695 | snap-update-ns --from-snap-confine --user-mounts firefox | /snap/snapd/20290/usr/lib/snapd/snap-update-ns | — | firefox |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
50
DNS requests
94
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
40663 | firefox | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
40663 | firefox | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
40663 | firefox | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
40663 | firefox | POST | 200 | 184.24.77.77:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
40663 | firefox | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
40663 | firefox | POST | 200 | 184.24.77.71:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
40663 | firefox | POST | 200 | 184.24.77.77:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
40663 | firefox | POST | 200 | 184.24.77.77:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
40663 | firefox | POST | 200 | 184.24.77.77:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 91.189.91.98:80 | — | Canonical Group Limited | US | unknown |
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 207.211.211.26:443 | odrs.gnome.org | — | US | whitelisted |
512 | snapd | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
40663 | firefox | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
40663 | firefox | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
40663 | firefox | 142.250.186.67:80 | o.pki.goog | GOOGLE | US | whitelisted |
40663 | firefox | 184.24.77.77:80 | r10.o.lencr.org | Akamai International B.V. | DE | whitelisted |
40663 | firefox | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
40663 | firefox | 172.217.23.106:443 | safebrowsing.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
connectivity-check.ubuntu.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
api.snapcraft.io |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
mc.prod.ads.prod.webservices.mozgcp.net |
| whitelisted |