| File name: | cve-2025-21298-poc.rtf |
| Full analysis: | https://app.any.run/tasks/92694ddd-4b55-42f1-8b2b-de2b3124dae0 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 09:42:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1 |
| MD5: | 9D68678AEEE52684BBE3C983222B1DA3 |
| SHA1: | BA3AE643E20A26ACA550B6888D9107E5D434959C |
| SHA256: | 93EF57B81021BE174E33B5B48C1AED525D2785C3607AEB540508BB3713690179 |
| SSDEEP: | 3:gOVAGaI6vUvuvX+xReRQGJ/ecPBEmrd3V8CLRBgTfVdVDVfVdVwFt3dXVBYv:9AFQfxR4F/jExCL40Yv |
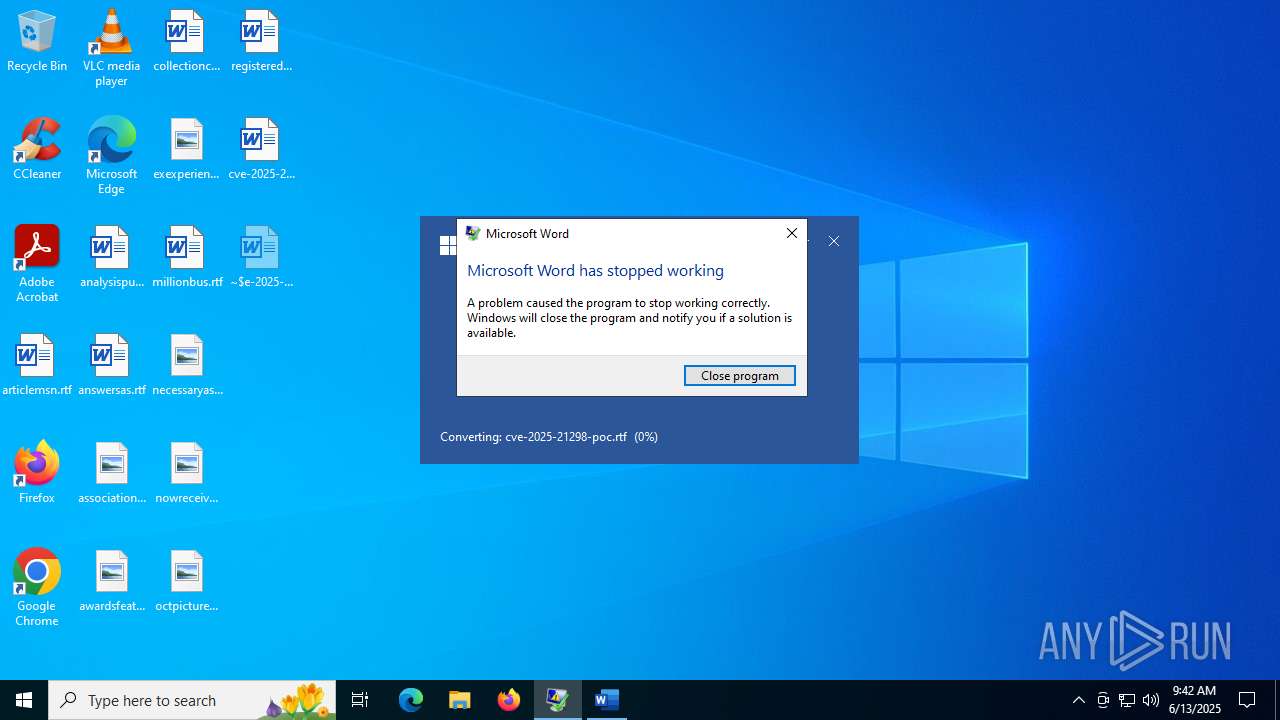
MALICIOUS
Unusual execution from MS Office
- WINWORD.EXE (PID: 6584)
SUSPICIOUS
No suspicious indicators.INFO
Creates files in the program directory
- DWWIN.EXE (PID: 5612)
Creates files or folders in the user directory
- DWWIN.EXE (PID: 5612)
Checks proxy server information
- DWWIN.EXE (PID: 5612)
Reads the software policy settings
- DWWIN.EXE (PID: 5612)
Reads Microsoft Office registry keys
- DWWIN.EXE (PID: 5612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
143
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5612 | C:\WINDOWS\system32\dwwin.exe -x -s 3928 | C:\Windows\System32\DWWIN.EXE | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Error Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6148 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6584 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\cve-2025-21298-poc.rtf /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 4 Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
7 705
Read events
7 493
Write events
206
Delete events
6
Modification events
| (PID) Process: | (6584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\6584 |
| Operation: | write | Name: | 0 |
Value: 0B0E10A4EE386FDBA9A84D920BB0AFDB42A69B230046B2C7B591F788F7ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B833D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
0
Suspicious files
5
Text files
5
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5612 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_WINWORD.EXE_32afa92cd6dc5a41387953d68edafb73db78ecf_00000000_7f5122e6-23a9-4c4f-849c-18cc21fea3df\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6584 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:0DFB11135DB799A9E05A7B3A83F8A94B | SHA256:5B79EFC60F01ED61560D2C1D2641FDB52684A21477F8299304CD02024D507DD1 | |||
| 5612 | DWWIN.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:5B63C0144C61100C949E65C9B4C7B790 | SHA256:51E7A9D4403161514027724D012C19E4717FD92CC87B31049944A37B40228B8E | |||
| 6584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{E3312FCC-445D-4077-AE63-178C07FED2F0}.tmp | smt | |
MD5:830FBF83999E052538EAF156AB6ECB17 | SHA256:D5098A2CEAE815DB29CD53C76F85240C95DC4D2E3FEDDD71D628617064C29869 | |||
| 5612 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6002.tmp.WERInternalMetadata.xml | xml | |
MD5:5D48CE001A8CF3FB40ECB20D86DE13AD | SHA256:0A7709D681FF2A63FD6319B8DF39518CA864A2C7454068C7CFCBF66629AC2F87 | |||
| 5612 | DWWIN.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:7F4F9C0E9B9115DDF6AA9827CBAC491E | SHA256:7CC09246502DE1FB3289FFEDB3822A20ED17E87D7F6CD457F2E901B678D8AE0D | |||
| 5612 | DWWIN.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:63F6E6C284C9563323E3000B6063D0E8 | SHA256:D90A935E89DAD9B9826A8C3B4E79E7C16D8DE3DED60611D05226FDB38646EC7E | |||
| 6584 | WINWORD.EXE | C:\Users\admin\Desktop\~$e-2025-21298-poc.rtf | pgc | |
MD5:4639FB133CB9F723E83C9ED452D2F5E8 | SHA256:E5544670D3A66E7B319327D30808CD2F9A3D1A94DAB153AD0D19496FE7013D44 | |||
| 6584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:F6B360DE2061DA5E200466FC50A36DC4 | SHA256:2D843D0AFE24EAA35DE35819D327B1847EE503690C52944F4F3C195A39BD7245 | |||
| 6584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:AD13EC57D771C1C80715E3B74B9ECE36 | SHA256:8584F65E46D83BCC52F0D791BCE0D3C5FCE82FDE966C3303CD2F8741D96A129E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5612 | DWWIN.EXE | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5612 | DWWIN.EXE | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2288 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5564 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5564 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6876 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6584 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
6584 | WINWORD.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6584 | WINWORD.EXE | 2.16.168.101:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
5612 | DWWIN.EXE | 20.189.173.22:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5612 | DWWIN.EXE | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |