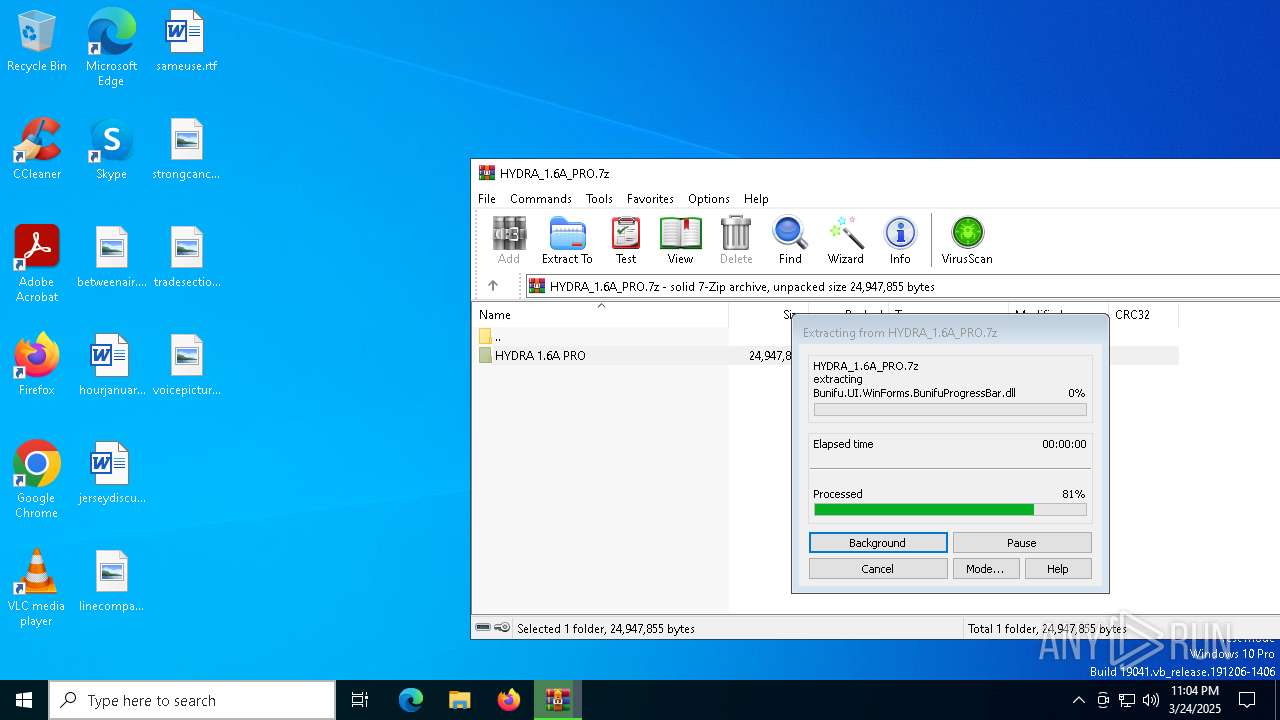
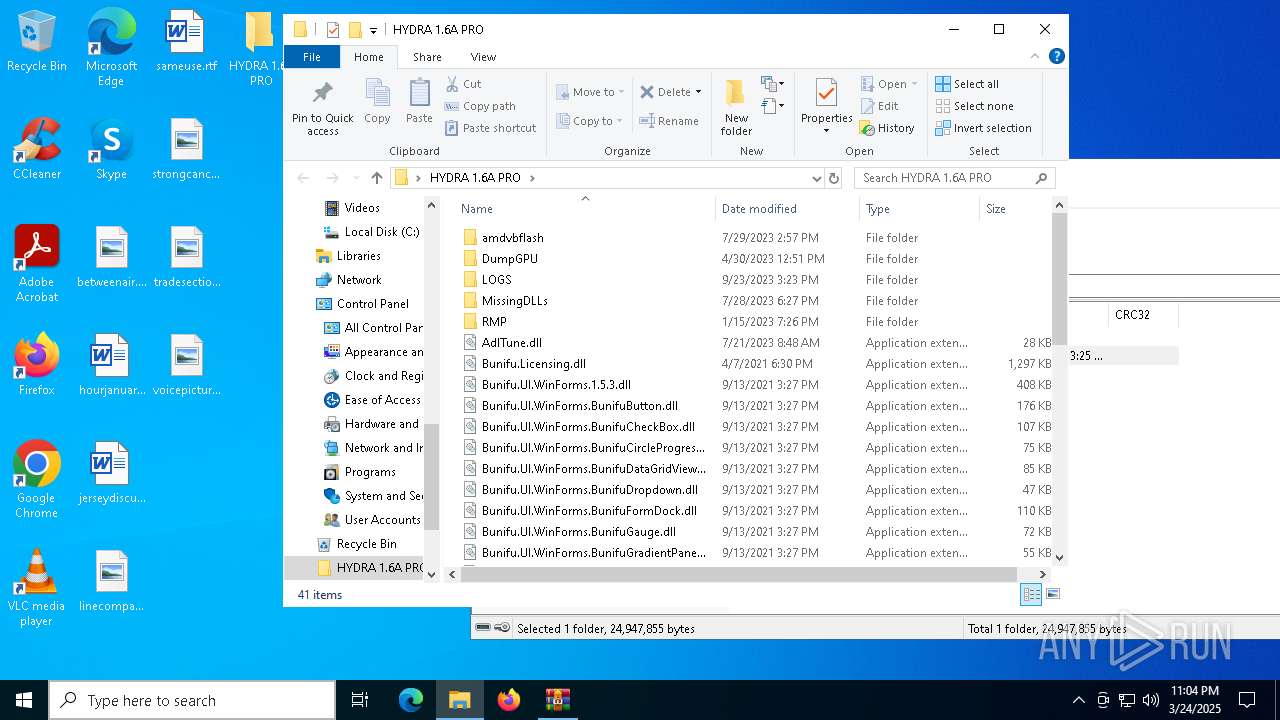
| File name: | HYDRA_1.6A_PRO.7z |
| Full analysis: | https://app.any.run/tasks/cf3dac80-bf6c-48bd-9f99-6687e3f52743 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 23:04:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 6D47A14B502E9960EEDA11FF5DF353F0 |
| SHA1: | 67EA63E09CE107188046D4C05E58540DF50CE3AA |
| SHA256: | 93D658F8A71BFC7E0F550D333856098D879FD46806F7D129177D07A0AB5C8939 |
| SSDEEP: | 98304:3L86LrScbzPLAjqgPc6fQFXB3NTopjETVxsUmz/31qYfv1k2CzpL3lcV8c1LII0f:r2ILBK1ONqBUFBF |
MALICIOUS
Vulnerable driver has been detected
- WinRAR.exe (PID: 7720)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 7720)
- HYDRA.exe (PID: 7352)
Creates files in the driver directory
- HYDRA.exe (PID: 7352)
Executable content was dropped or overwritten
- HYDRA.exe (PID: 7352)
Starts CMD.EXE for commands execution
- HYDRA.exe (PID: 7352)
Executes as Windows Service
- WmiApSrv.exe (PID: 7048)
The process checks if it is being run in the virtual environment
- HYDRA.exe (PID: 7352)
Uses powercfg.exe to modify the power settings
- HYDRA.exe (PID: 7352)
INFO
Manual execution by a user
- HYDRA.exe (PID: 1616)
- HYDRA.exe (PID: 7352)
- HYDRA.exe (PID: 4812)
- HYDRA.exe (PID: 7708)
- HYDRA.exe (PID: 7912)
- HYDRA.exe (PID: 8024)
- HYDRA.exe (PID: 5756)
- HYDRA.exe (PID: 8136)
- HYDRA.exe (PID: 8084)
- HYDRA.exe (PID: 7452)
- HYDRA.exe (PID: 632)
- HYDRA.exe (PID: 6808)
- HYDRA.exe (PID: 7316)
- HYDRA.exe (PID: 2564)
- HYDRA.exe (PID: 7528)
The sample compiled with english language support
- WinRAR.exe (PID: 7720)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7720)
The sample compiled with japanese language support
- WinRAR.exe (PID: 7720)
Checks supported languages
- HYDRA.exe (PID: 7352)
- HYDRA.exe (PID: 7912)
- HYDRA.exe (PID: 8084)
- HYDRA.exe (PID: 5756)
- HYDRA.exe (PID: 7452)
- HYDRA.exe (PID: 7708)
Reads the computer name
- HYDRA.exe (PID: 7352)
- HYDRA.exe (PID: 7708)
- HYDRA.exe (PID: 7912)
- HYDRA.exe (PID: 5756)
- HYDRA.exe (PID: 7528)
Reads the machine GUID from the registry
- HYDRA.exe (PID: 7352)
Reads the time zone
- HYDRA.exe (PID: 7352)
Reads CPU info
- HYDRA.exe (PID: 7352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2023:09:23 15:25:43+00:00 |
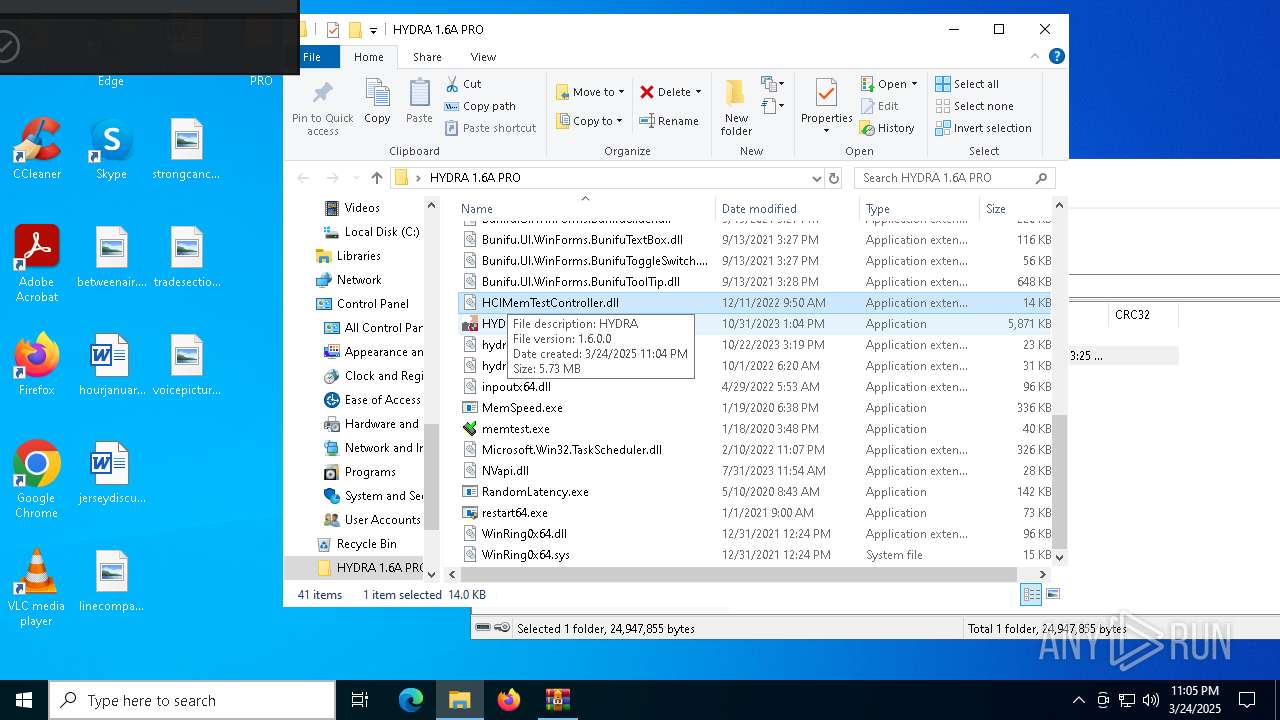
| ArchivedFileName: | HYDRA 1.6A PRO |
Total processes
196
Monitored processes
60
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "powercfg.exe" /setacvalueindex c206b735-d3a0-4474-9777-b69a09e63c7c 54533251-82be-4824-96c1-47b60b740d00 40fbefc7-2e9d-4d25-a185-0cfd8574bac6 0x00000000 | C:\Windows\System32\powercfg.exe | — | HYDRA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Users\admin\Desktop\HYDRA 1.6A PRO\HYDRA.exe" | C:\Users\admin\Desktop\HYDRA 1.6A PRO\HYDRA.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: HYDRA Exit code: 3221226540 Version: 1.6.0.0 Modules
| |||||||||||||||
| 864 | "powercfg.exe" /l | C:\Windows\System32\powercfg.exe | — | HYDRA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "powercfg.exe" /setacvalueindex c206b735-d3a0-4474-9777-b69a09e63c7c 54533251-82be-4824-96c1-47b60b740d00 3b04d4fd-1cc7-4f23-ab1c-d1337819c4bb 0x00000000 | C:\Windows\System32\powercfg.exe | — | HYDRA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "C:\Users\admin\Desktop\HYDRA 1.6A PRO\HYDRA.exe" | C:\Users\admin\Desktop\HYDRA 1.6A PRO\HYDRA.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: HYDRA Exit code: 3221226540 Version: 1.6.0.0 Modules
| |||||||||||||||
| 1628 | "powercfg.exe" /restoredefaultschemes | C:\Windows\System32\powercfg.exe | — | HYDRA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2564 | "C:\Users\admin\Desktop\HYDRA 1.6A PRO\HYDRA.exe" | C:\Users\admin\Desktop\HYDRA 1.6A PRO\HYDRA.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: HYDRA Exit code: 3221226540 Version: 1.6.0.0 Modules
| |||||||||||||||
Total events
6 983
Read events
6 615
Write events
199
Delete events
169
Modification events
| (PID) Process: | (7720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HYDRA_1.6A_PRO.7z | |||
| (PID) Process: | (7720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7528) lodctr.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\usbhub\Performance |
| Operation: | write | Name: | Last Counter |
Value: 2266 | |||
| (PID) Process: | (7528) lodctr.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\usbhub\Performance |
| Operation: | write | Name: | Last Help |
Value: 2267 | |||
Executable files
42
Suspicious files
3
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7720.28173\HYDRA 1.6A PRO\amdvbflash\AMDVBFLASH_User_Guide_NDA.pdf | ||
MD5:F4A483489567D6B10B6A2A884205DA5D | SHA256:A2463E61CE763447111A7EF97C6ED424E1921C5CA4F75F827E078238F23FAB93 | |||
| 7720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7720.28173\HYDRA 1.6A PRO\Bunifu.UI.WinForms.BunifuDropdown.dll | executable | |
MD5:C715CBDEE4B7E42294BEA2A949626D41 | SHA256:41199AFA13D2967121028FBEA947397EB86505DD3C42E4BBFB002FAB04FE46A6 | |||
| 7720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7720.28173\HYDRA 1.6A PRO\Bunifu.UI.WinForms.BunifuCircleProgress.dll | executable | |
MD5:69BECCB5C9E400CA1434932D094D137A | SHA256:1351825949D8D0AA65AF08D527214C4C316BBEB9B87027DBB965F7C8D07C3FE8 | |||
| 7720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7720.28173\HYDRA 1.6A PRO\Bunifu.UI.WinForms.BunifuGauge.dll | executable | |
MD5:67A0FDEFFA7A25ACE3510A3DBB6FBF98 | SHA256:149BAF3988895FDC6D777C75DC2DB5A8A2163C58410F99F04A5B845963BB8BE2 | |||
| 7720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7720.28173\HYDRA 1.6A PRO\Bunifu.UI.WinForms.BunifuFormDock.dll | executable | |
MD5:E650EA1FB5E93378801E29EA63448E6B | SHA256:89A51E8E994FE35D1EDB0DEE4F5E87CCECD5ECC8973D21F055D0A549372C001D | |||
| 7720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7720.28173\HYDRA 1.6A PRO\Bunifu.UI.WinForms.BunifuImageButton.dll | executable | |
MD5:AC51E7EF8F6C6C7C702DA1B1C866AAAC | SHA256:AE2A9616382326BA3D6926E47F1851F9B13B6CE8F5F5DE77D27CB81E7AC1067A | |||
| 7720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7720.28173\HYDRA 1.6A PRO\amdvbflash\amdvbflash.exe | executable | |
MD5:313ED2279DF1AF019A0CCD06B4507277 | SHA256:CB04893E48312E2AA23436D21DD3CAACF8FEC2339373EEF3F3875B7C359B1A3C | |||
| 7720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7720.28173\HYDRA 1.6A PRO\Bunifu.UI.WinForms.BunifuDataGridView.dll | executable | |
MD5:C895E9BAD25D4A9D97EC1DB436F7071E | SHA256:5CE993B88CB8C5B5FA453F4CFA237EDF298F5E15CDE42D6895664FC1ED6E3D37 | |||
| 7720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7720.28173\HYDRA 1.6A PRO\AdlTune.dll | executable | |
MD5:886BA5044E7FDE070981A33AF6EB637D | SHA256:C01E542AFB95E999B309AD1B8B0324D2F2A1462D6049154C6747F9270998BC24 | |||
| 7720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7720.28173\HYDRA 1.6A PRO\Bunifu.UI.WinForms.BunifuPages.dll | executable | |
MD5:AFDCD61A8A6AF3E24C8A078C6A061A9E | SHA256:D1F9D7B6AA3D385DEEAEBDA2F52D58C1F82618E98C1D354762EF0D7B922AFB76 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7868 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4400 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4400 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4024 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
7868 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |