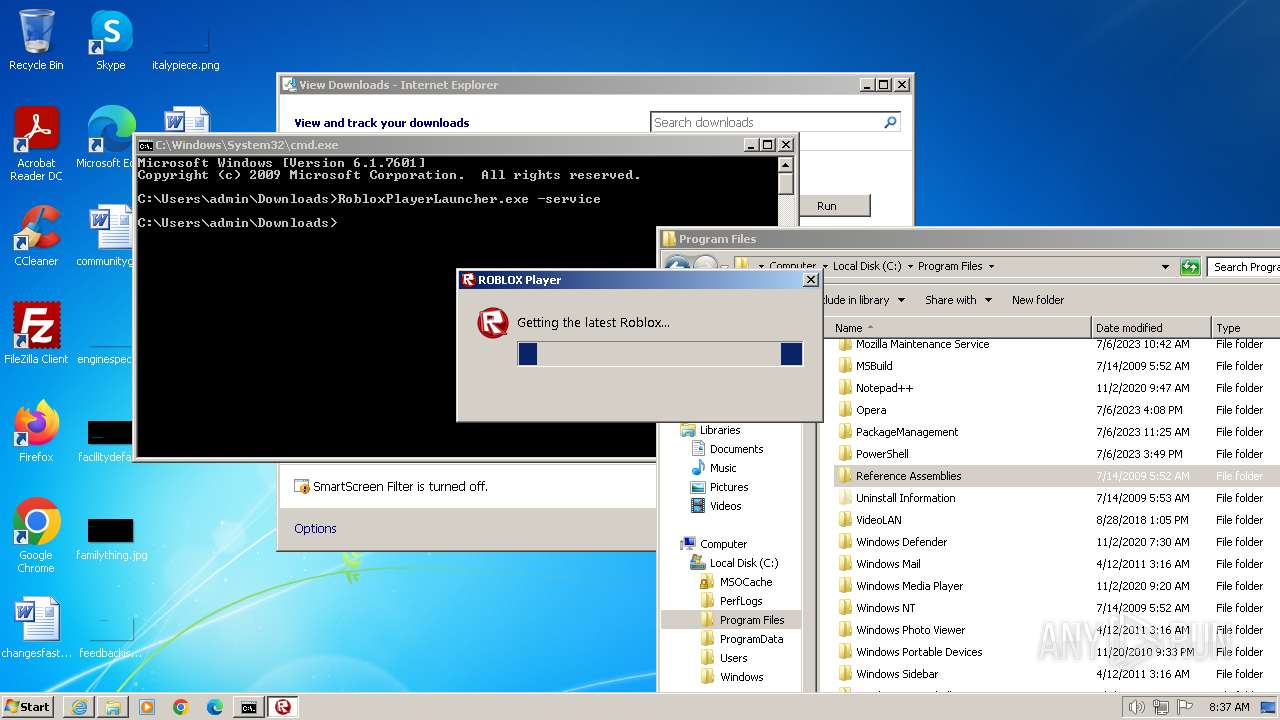
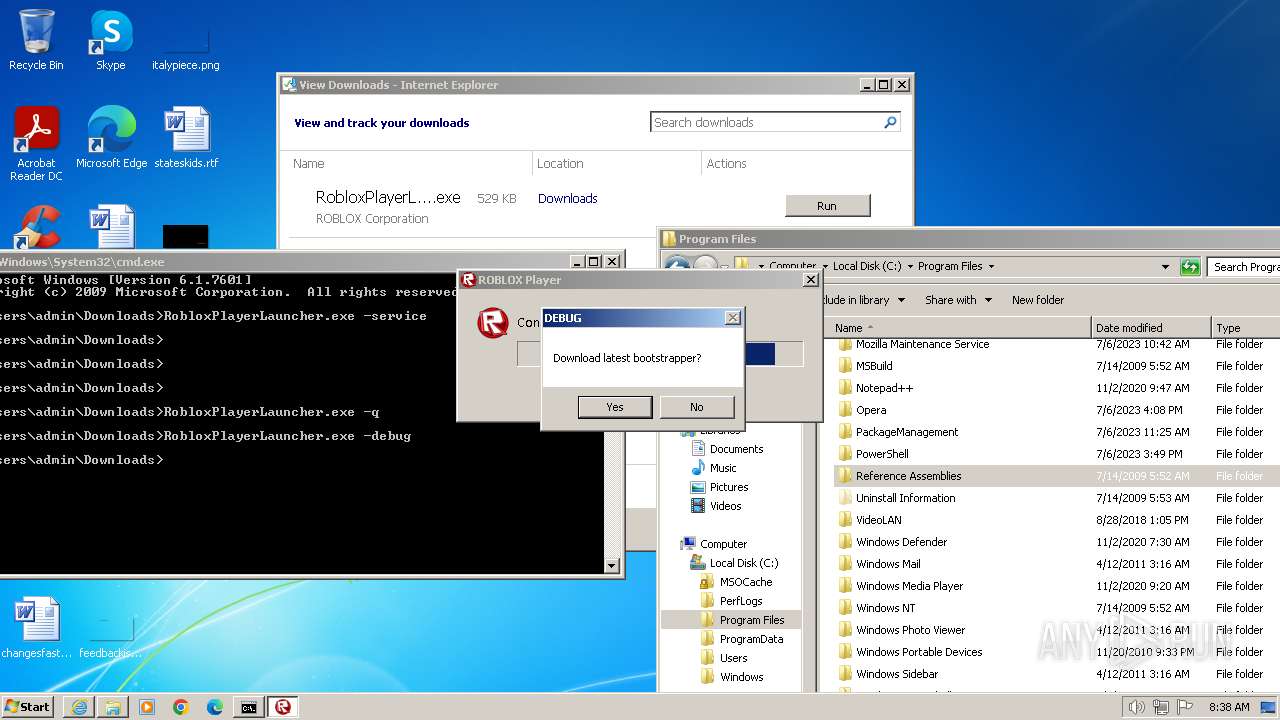
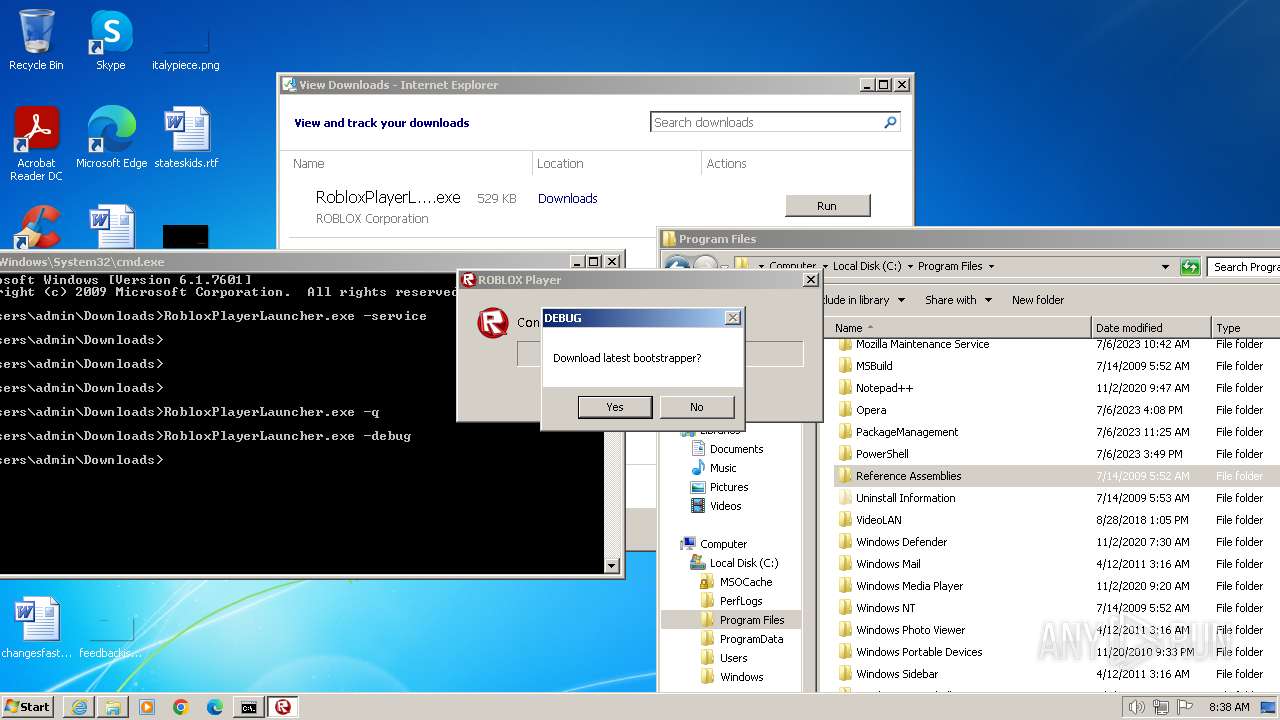
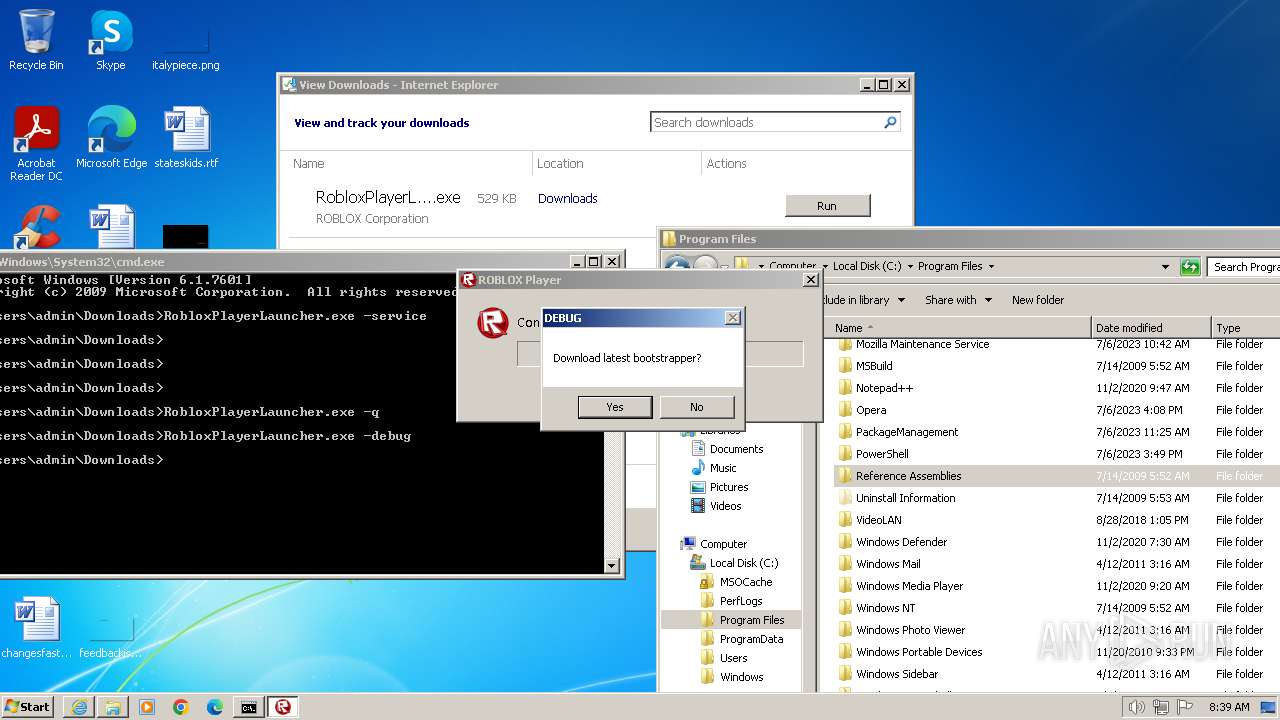
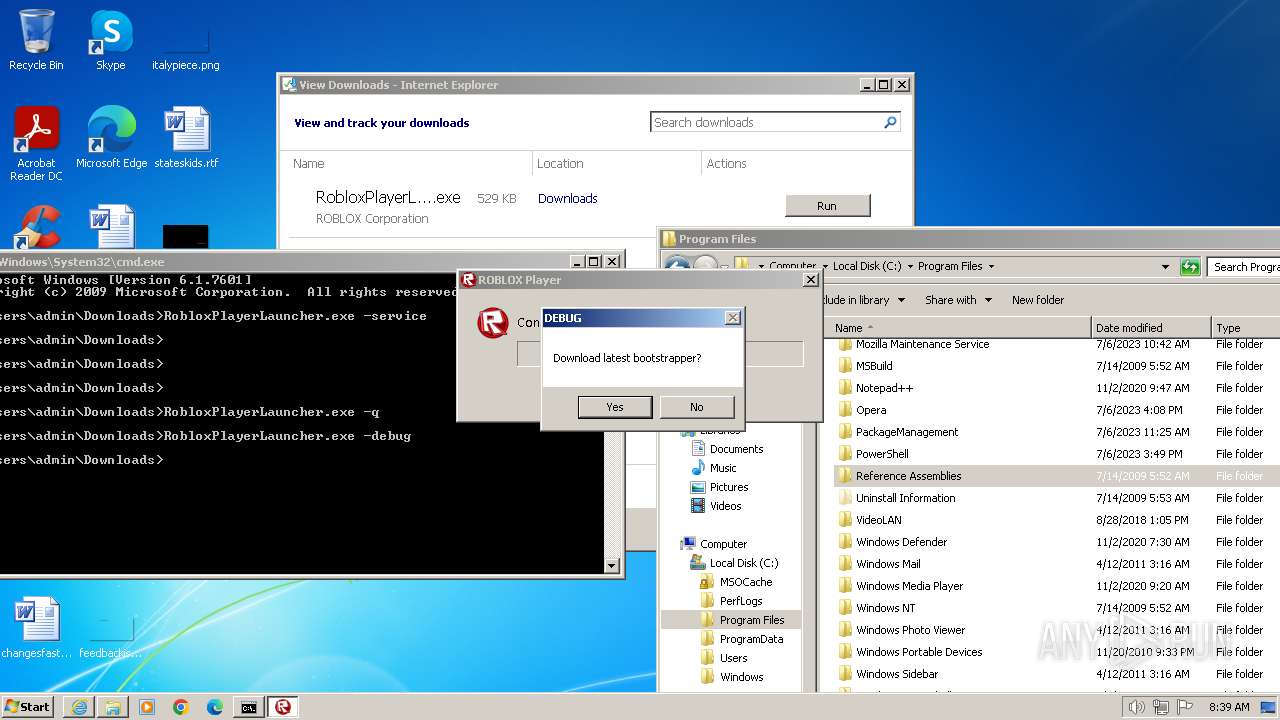
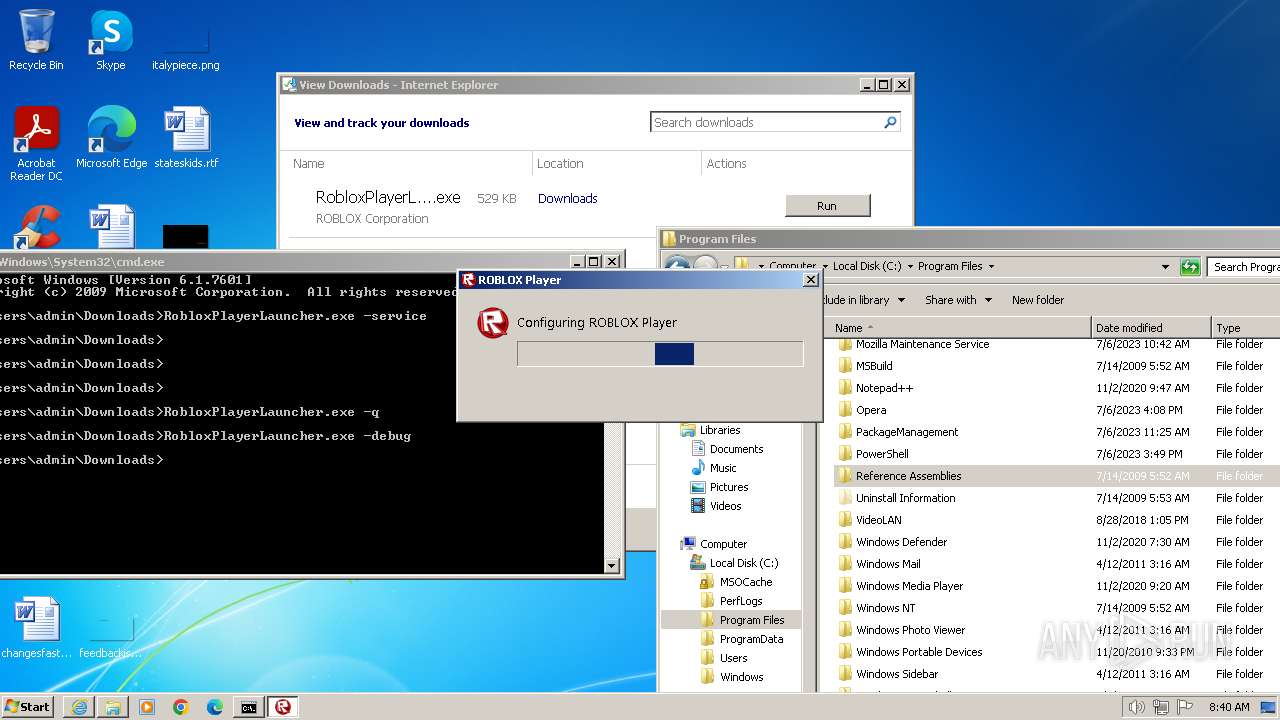
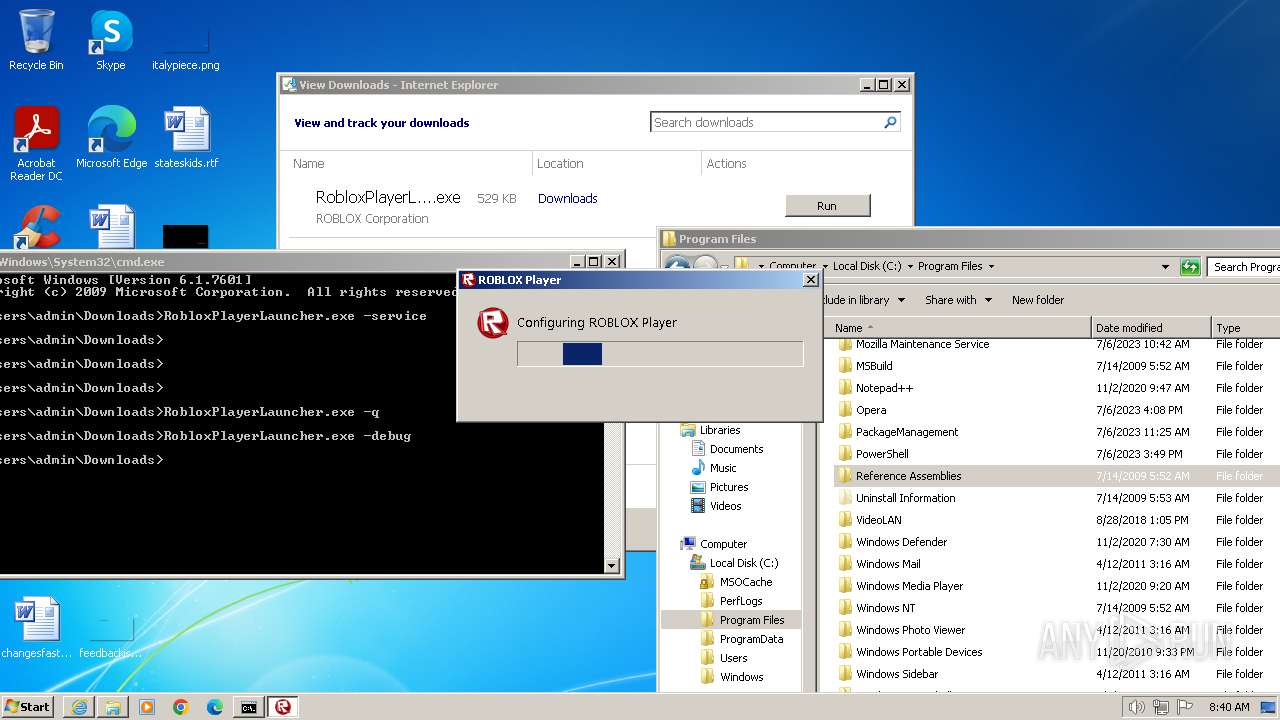
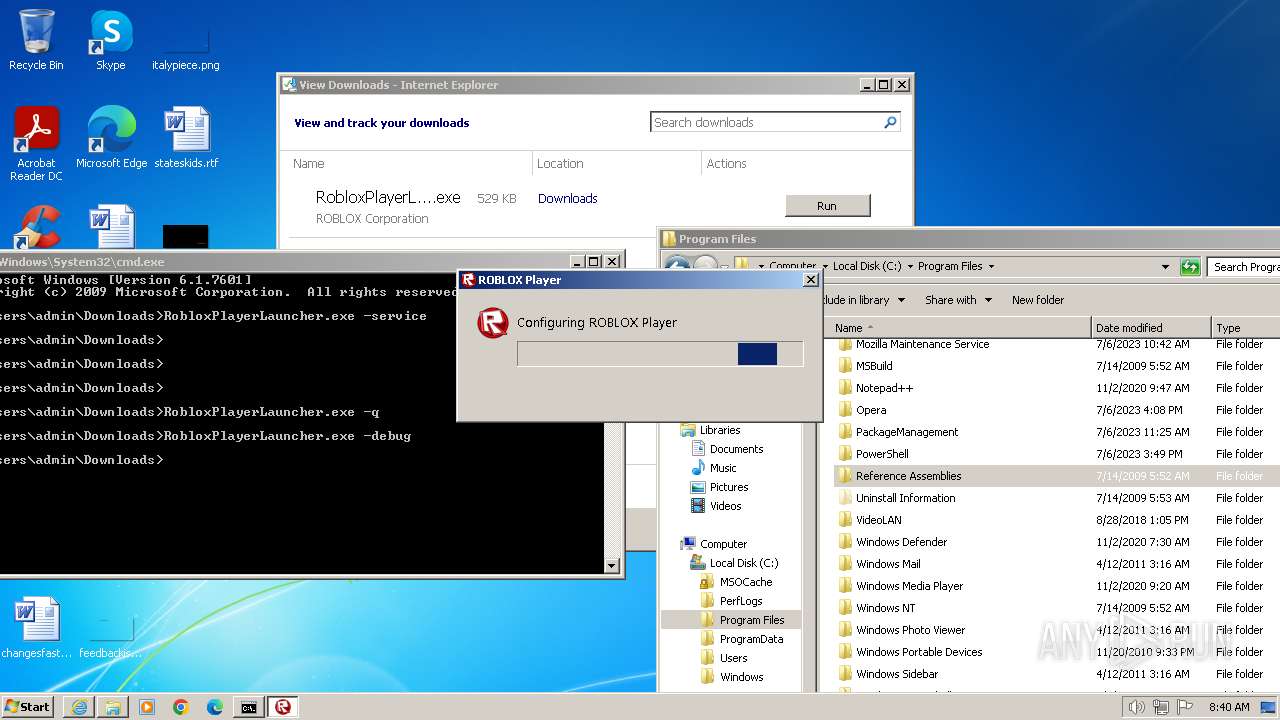
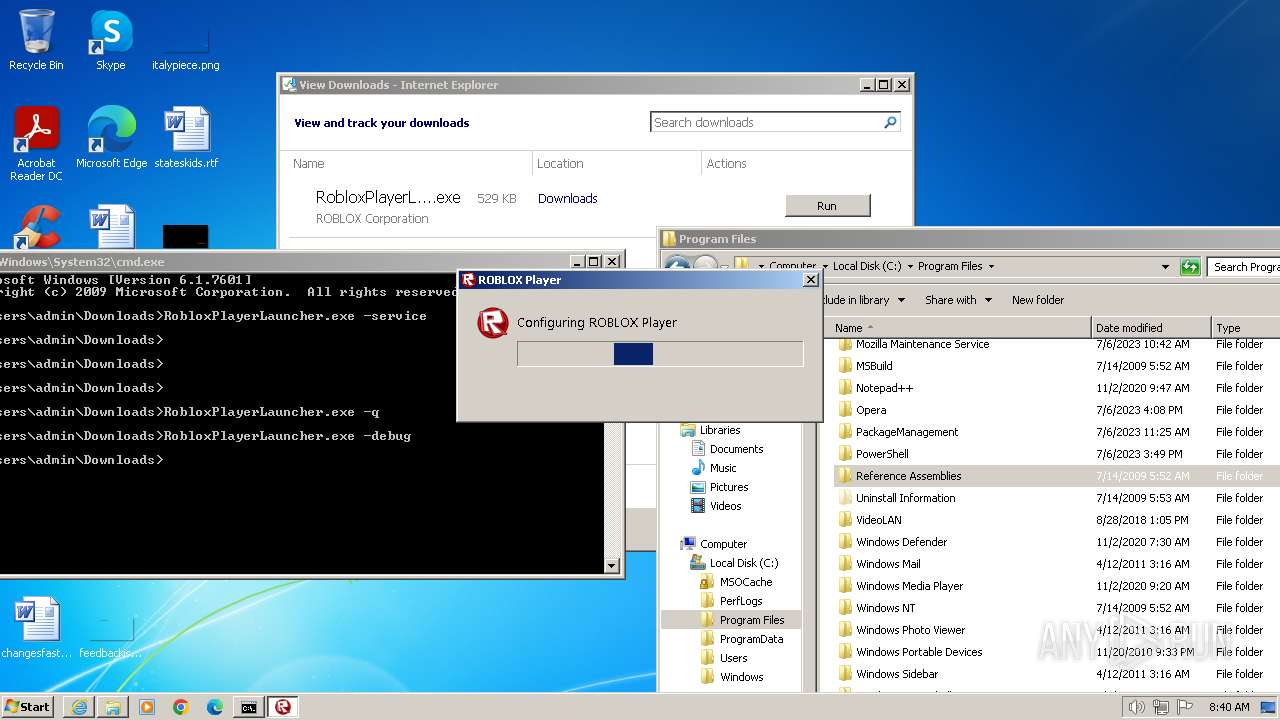
| URL: | https://s3.amazonaws.com/setup.gametest2.robloxlabs.com/version-c779580ecbd9426c-Roblox.exe |
| Full analysis: | https://app.any.run/tasks/fd144b68-3077-41b3-bf1e-683254ace3ba |
| Verdict: | Malicious activity |
| Analysis date: | April 02, 2024, 07:35:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 458428824895102C9AFCD25B8C53A5AC |
| SHA1: | 0E9B047C691E41C36D4B1DBEDDEA1EF1ACC3F2A7 |
| SHA256: | 93CFA4688A97858378AE7C87F6850621040C6B54A338D2C6395B1BC9B536B5B5 |
| SSDEEP: | 3:N8H7WtWARuTAWFcJbTIFAGhcdGMOHmn:2H90uMIczdGMv |
MALICIOUS
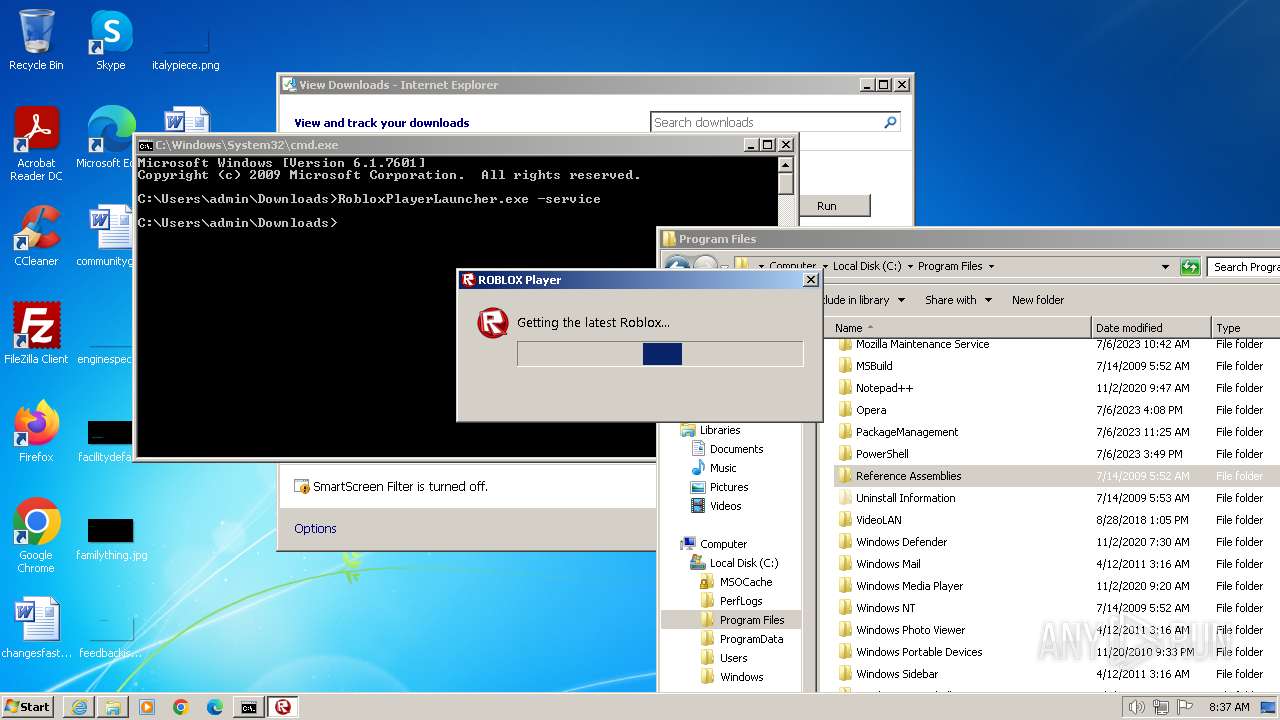
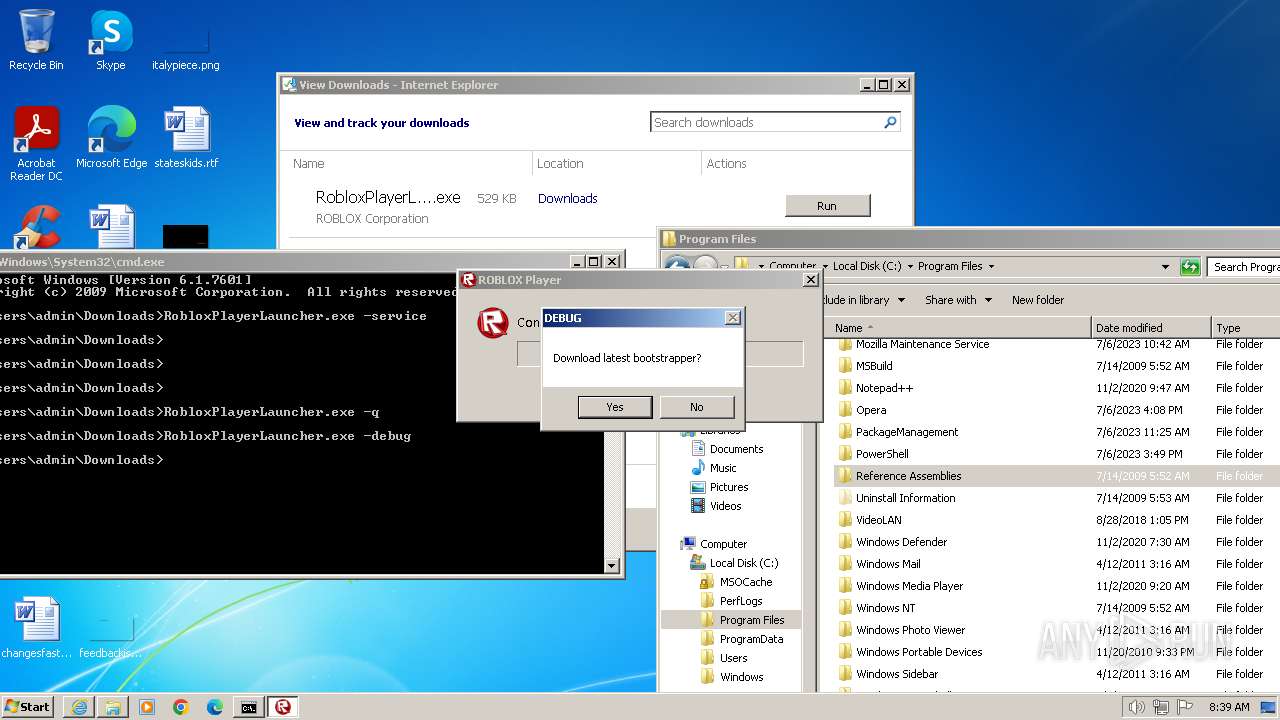
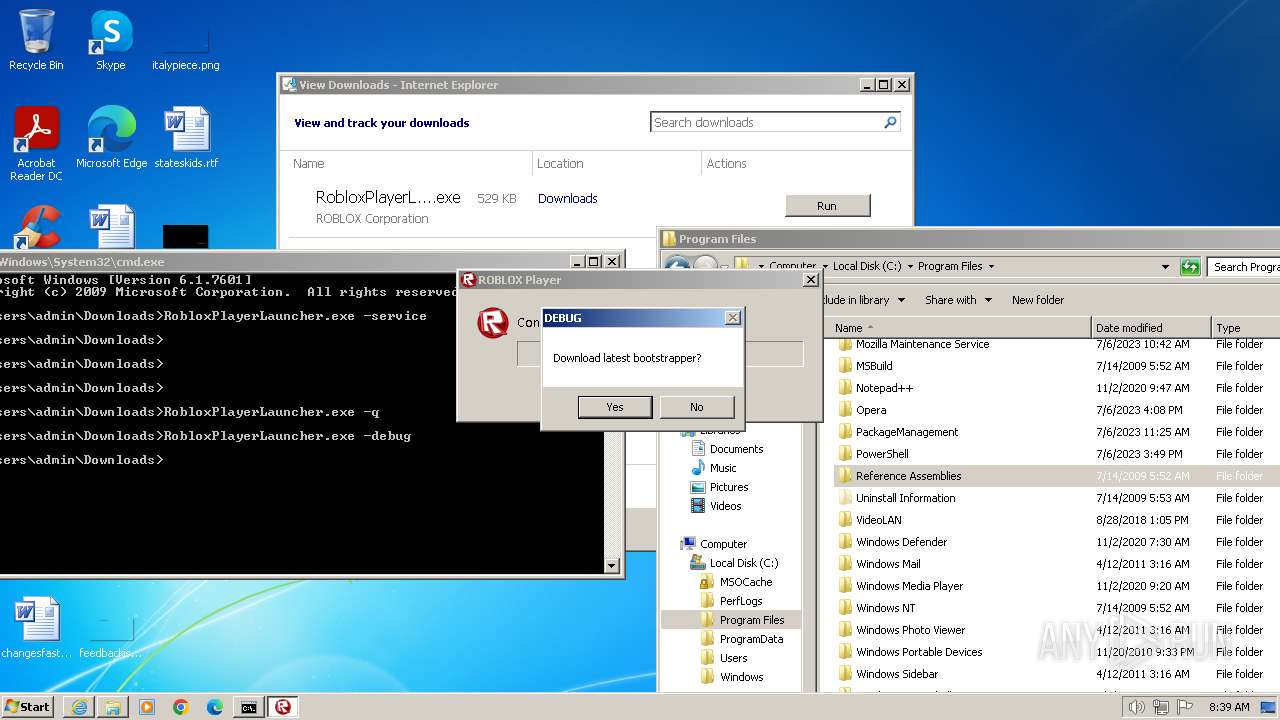
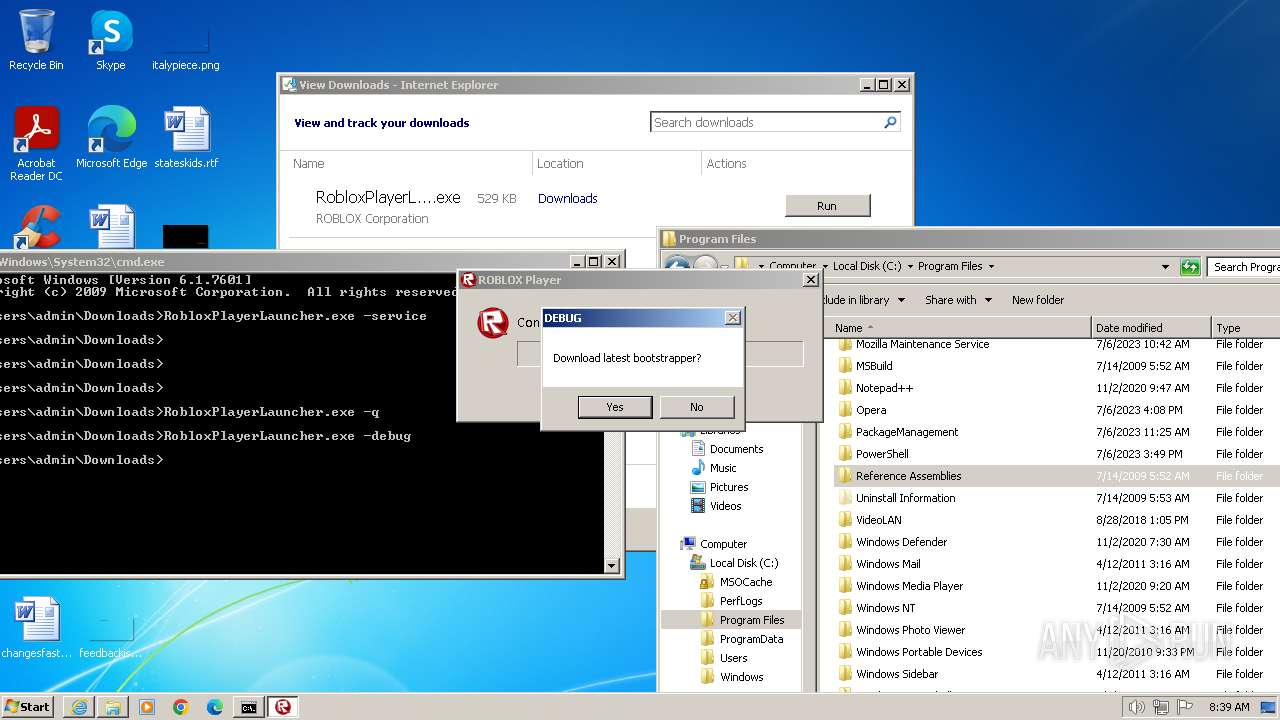
Drops the executable file immediately after the start
- RobloxPlayerLauncher.exe (PID: 1264)
SUSPICIOUS
Reads the Internet Settings
- RobloxPlayerLauncher.exe (PID: 2112)
- RobloxPlayerLauncher.exe (PID: 1124)
- RobloxPlayerLauncher.exe (PID: 1264)
Reads security settings of Internet Explorer
- RobloxPlayerLauncher.exe (PID: 2112)
- RobloxPlayerLauncher.exe (PID: 1124)
- RobloxPlayerLauncher.exe (PID: 1264)
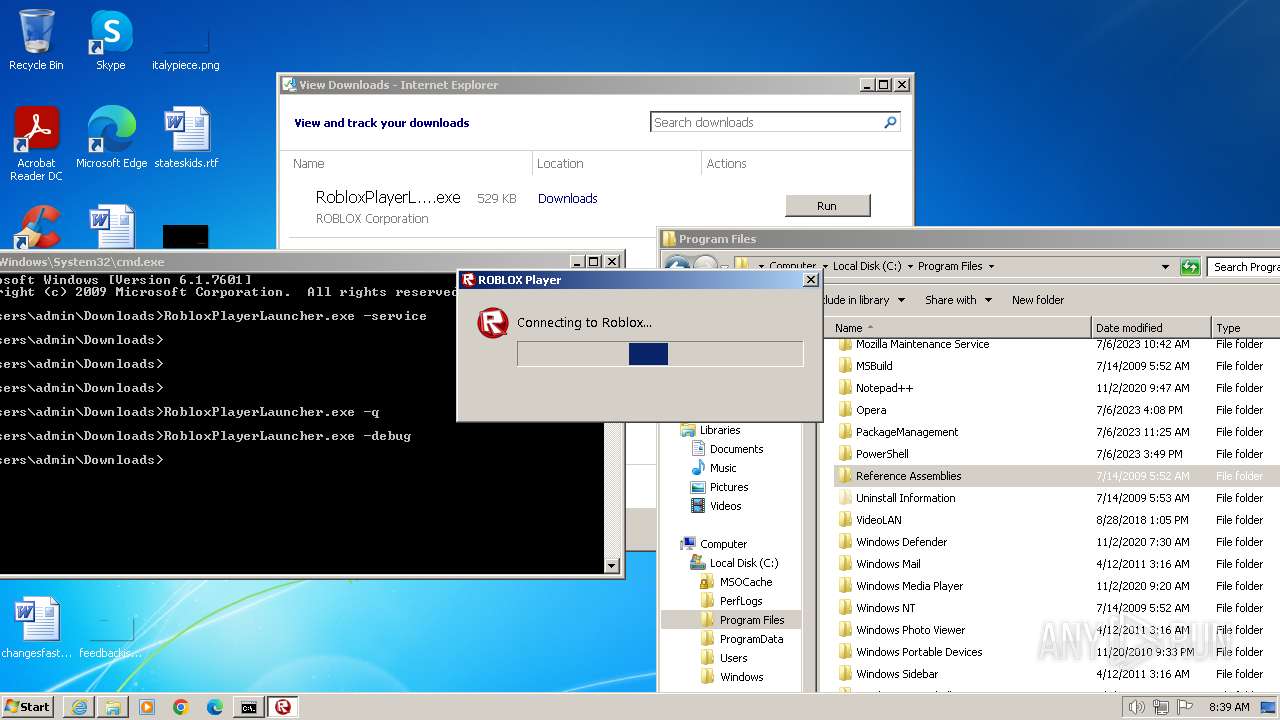
Process requests binary or script from the Internet
- RobloxPlayerLauncher.exe (PID: 2112)
INFO
Application launched itself
- iexplore.exe (PID: 3956)
Reads the computer name
- wmpnscfg.exe (PID: 1308)
- RobloxPlayerLauncher.exe (PID: 2112)
- RobloxPlayerLauncher.exe (PID: 1124)
- RobloxPlayerLauncher.exe (PID: 1264)
Checks supported languages
- wmpnscfg.exe (PID: 1308)
- RobloxPlayerLauncher.exe (PID: 2112)
- RobloxPlayerLauncher.exe (PID: 1124)
- RobloxPlayerLauncher.exe (PID: 1264)
Manual execution by a user
- explorer.exe (PID: 2372)
- wmpnscfg.exe (PID: 1308)
- cmd.exe (PID: 2504)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3964)
- iexplore.exe (PID: 3956)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3956)
The process uses the downloaded file
- iexplore.exe (PID: 3956)
Checks proxy server information
- RobloxPlayerLauncher.exe (PID: 2112)
- RobloxPlayerLauncher.exe (PID: 1264)
- RobloxPlayerLauncher.exe (PID: 1124)
Reads the machine GUID from the registry
- RobloxPlayerLauncher.exe (PID: 2112)
- RobloxPlayerLauncher.exe (PID: 1264)
- RobloxPlayerLauncher.exe (PID: 1124)
Create files in a temporary directory
- RobloxPlayerLauncher.exe (PID: 2112)
- RobloxPlayerLauncher.exe (PID: 1264)
- RobloxPlayerLauncher.exe (PID: 1124)
Creates files or folders in the user directory
- RobloxPlayerLauncher.exe (PID: 1264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
8
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1124 | RobloxPlayerLauncher.exe -q | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe | cmd.exe | ||||||||||||
User: admin Company: ROBLOX Corporation Integrity Level: MEDIUM Description: Roblox Exit code: 0 Version: 1, 6, 0, 492 Modules
| |||||||||||||||
| 1264 | RobloxPlayerLauncher.exe -debug | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe | cmd.exe | ||||||||||||
User: admin Company: ROBLOX Corporation Integrity Level: MEDIUM Description: Roblox Version: 1, 6, 0, 492 Modules
| |||||||||||||||
| 1308 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2112 | RobloxPlayerLauncher.exe -service | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe | cmd.exe | ||||||||||||
User: admin Company: ROBLOX Corporation Integrity Level: MEDIUM Description: Roblox Version: 1, 6, 0, 492 Modules
| |||||||||||||||
| 2372 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2504 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3956 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://s3.amazonaws.com/setup.gametest2.robloxlabs.com/version-c779580ecbd9426c-Roblox.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3964 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3956 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 829
Read events
19 583
Write events
195
Delete events
51
Modification events
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31098064 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31098064 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
3
Suspicious files
9
Text files
16
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D03E46CD585BBE111C712E6577BC5F07_5C7AA733A26CC779AF88EBB5B7FEEFA4 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D03E46CD585BBE111C712E6577BC5F07_5C7AA733A26CC779AF88EBB5B7FEEFA4 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\RobloxPlayerLauncher[1].exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
46
DNS requests
25
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3964 | iexplore.exe | GET | 304 | 23.32.238.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?92967c53a8c0ec29 | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 304 | 23.32.238.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?36ca310eb28aaa33 | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 200 | 108.138.2.107:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m01.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBShdVEFnSEQ0gG5CBtzM48cPMe9XwQUgbgOY4qJEhjl%2Bjs7UJWf5uWQE4UCEAqFHNMUTb3%2B%2FNnQWmcy9Rg%3D | unknown | — | — | unknown |
3956 | iexplore.exe | GET | 304 | 23.32.238.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3ffc3fbc5b315e52 | unknown | — | — | unknown |
3956 | iexplore.exe | GET | 304 | 23.32.238.225:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?719f0b64dcb4a601 | unknown | — | — | unknown |
3956 | iexplore.exe | GET | 304 | 23.32.238.217:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?31055eca6ea3b32e | unknown | — | — | unknown |
3956 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3964 | iexplore.exe | 54.231.229.208:443 | s3.amazonaws.com | AMAZON-02 | US | unknown |
3964 | iexplore.exe | 23.32.238.240:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3964 | iexplore.exe | 23.32.238.235:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3964 | iexplore.exe | 108.138.2.107:80 | o.ss2.us | AMAZON-02 | US | whitelisted |
3964 | iexplore.exe | 18.66.142.79:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | unknown |
3964 | iexplore.exe | 18.245.65.219:80 | ocsp.r2m01.amazontrust.com | — | US | unknown |
3956 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s3.amazonaws.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m01.amazontrust.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ephemeralcounters.api.gametest2.robloxlabs.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
— | — | Potentially Bad Traffic | ET POLICY Executable served from Amazon S3 |
— | — | Misc activity | ET INFO EXE - Served Inline HTTP |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6 ETPRO signatures available at the full report