| File name: | NDI 6 Runtime.exe |
| Full analysis: | https://app.any.run/tasks/1f6d32df-6450-4dcb-8fd8-b636af5056a3 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2025, 18:49:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 55A486CFB4E8E5F319EDA8FBAF38AE7A |
| SHA1: | A142A05554B07277B46BFB280D9D26DC2886DC67 |
| SHA256: | 93BAED79F27203C61A090093BD4A1BAFBB606C6A8E768D9DEA650AD23B7BDF71 |
| SSDEEP: | 98304:k+QqZ8fUCdg3mKSiNH7R+9cJH7wgFZ8wmTPQeLbmQfx1DRqUmCATz05CJswNDd/B:n87ZAWHmfGPOOt7xSAENp+5Qgq |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- NDI 6 Runtime.tmp (PID: 4708)
Changes the autorun value in the registry
- netsh.exe (PID: 5160)
SUSPICIOUS
Executable content was dropped or overwritten
- NDI 6 Runtime.exe (PID: 6136)
- NDI 6 Runtime.tmp (PID: 4708)
- NDI 6 Runtime.exe (PID: 7152)
Reads security settings of Internet Explorer
- NDI 6 Runtime.tmp (PID: 6016)
Reads the Windows owner or organization settings
- NDI 6 Runtime.tmp (PID: 4708)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 6560)
- regsvr32.exe (PID: 6472)
Starts CMD.EXE for commands execution
- NDI 6 Runtime.tmp (PID: 4708)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 6752)
- cmd.exe (PID: 4544)
INFO
Create files in a temporary directory
- NDI 6 Runtime.exe (PID: 6136)
- NDI 6 Runtime.exe (PID: 7152)
Checks supported languages
- NDI 6 Runtime.exe (PID: 7152)
- NDI 6 Runtime.tmp (PID: 4708)
- _setup64.tmp (PID: 6452)
- NDI 6 Runtime.exe (PID: 6136)
- NDI 6 Runtime.tmp (PID: 6016)
Process checks computer location settings
- NDI 6 Runtime.tmp (PID: 6016)
Reads the computer name
- NDI 6 Runtime.tmp (PID: 6016)
- NDI 6 Runtime.tmp (PID: 4708)
Creates files in the program directory
- NDI 6 Runtime.tmp (PID: 4708)
The sample compiled with english language support
- NDI 6 Runtime.tmp (PID: 4708)
Creates a software uninstall entry
- NDI 6 Runtime.tmp (PID: 4708)
Disables trace logs
- netsh.exe (PID: 3680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:15 09:48:30+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 290304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.1.0 |
| ProductVersionNumber: | 6.0.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
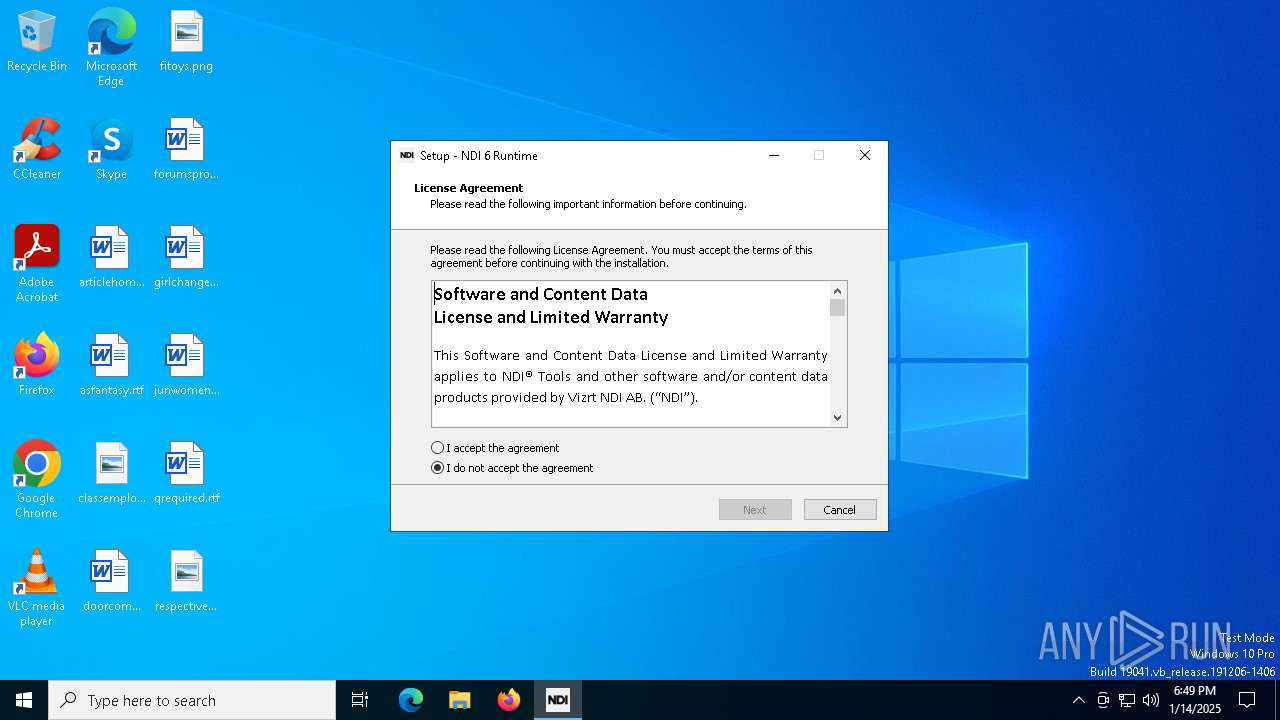
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | NDI |
| FileDescription: | NDI 6 Runtime Setup |
| FileVersion: | 6.0.1.0 |
| LegalCopyright: | Copyright © 2023-2024 Vizrt NDI AB. All rights reserved. |
| OriginalFileName: | |
| ProductName: | NDI 6 Runtime |
| ProductVersion: | 6.0.1.0 |
Total processes
132
Monitored processes
14
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3680 | netsh int tcp reset | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3692 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4544 | "cmd" /c netsh int tcp reset | C:\Windows\System32\cmd.exe | — | NDI 6 Runtime.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4708 | "C:\Users\admin\AppData\Local\Temp\is-H9AD9.tmp\NDI 6 Runtime.tmp" /SL5="$5035E,8988195,1032704,C:\Users\admin\AppData\Local\Temp\NDI 6 Runtime.exe" /SPAWNWND=$602C6 /NOTIFYWND=$602B0 | C:\Users\admin\AppData\Local\Temp\is-H9AD9.tmp\NDI 6 Runtime.tmp | NDI 6 Runtime.exe | ||||||||||||
User: admin Company: NDI Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 5160 | netsh winsock reset | C:\Windows\System32\netsh.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | _setup64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6016 | "C:\Users\admin\AppData\Local\Temp\is-SO3UF.tmp\NDI 6 Runtime.tmp" /SL5="$602B0,8988195,1032704,C:\Users\admin\AppData\Local\Temp\NDI 6 Runtime.exe" | C:\Users\admin\AppData\Local\Temp\is-SO3UF.tmp\NDI 6 Runtime.tmp | — | NDI 6 Runtime.exe | |||||||||||
User: admin Company: NDI Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6136 | "C:\Users\admin\AppData\Local\Temp\NDI 6 Runtime.exe" /SPAWNWND=$602C6 /NOTIFYWND=$602B0 | C:\Users\admin\AppData\Local\Temp\NDI 6 Runtime.exe | NDI 6 Runtime.tmp | ||||||||||||
User: admin Company: NDI Integrity Level: HIGH Description: NDI 6 Runtime Setup Exit code: 0 Version: 6.0.1.0 Modules
| |||||||||||||||
| 6452 | helper 105 0x4A0 | C:\Users\admin\AppData\Local\Temp\is-EM9J9.tmp\_isetup\_setup64.tmp | — | NDI 6 Runtime.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 347
Read events
1 872
Write events
352
Delete events
123
Modification events
| (PID) Process: | (4708) NDI 6 Runtime.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\NewTek\InstallVersion\{{71AFF296-ED43-4166-8301-4649285EE712} |
| Operation: | write | Name: | upgrade_version |
Value: 240506 | |||
| (PID) Process: | (4708) NDI 6 Runtime.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\NewTek\InstallVersion\NdiRedistributable |
| Operation: | write | Name: | upgrade_version |
Value: 240506 | |||
| (PID) Process: | (6472) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\NDI |
| Operation: | write | Name: | Source Filter |
Value: {90F86EFC-87CF-4097-9FCE-0C11D573FF8F} | |||
| (PID) Process: | (6472) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Multimedia\WMPlayer\Schemes\NDI |
| Operation: | write | Name: | Runtime |
Value: 1 | |||
| (PID) Process: | (6472) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{90F86EFC-87CF-4097-9FCE-0C11D573FF8F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (6472) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{083863F1-70DE-11D0-BD40-00A0C911CE86}\Instance\{90F86EFC-87CF-4097-9FCE-0C11D573FF8F} |
| Operation: | write | Name: | FilterData |
Value: 02000000000020000100000000000000307069330800000000000000010000000000000000000000307479330000000038000000480000007669647300001000800000AA00389B7100000000000000000000000000000000 | |||
| (PID) Process: | (4708) NDI 6 Runtime.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{71AFF296-ED43-4166-8301-4649285EE712}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.1.2 | |||
| (PID) Process: | (4708) NDI 6 Runtime.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{71AFF296-ED43-4166-8301-4649285EE712}_is1 |
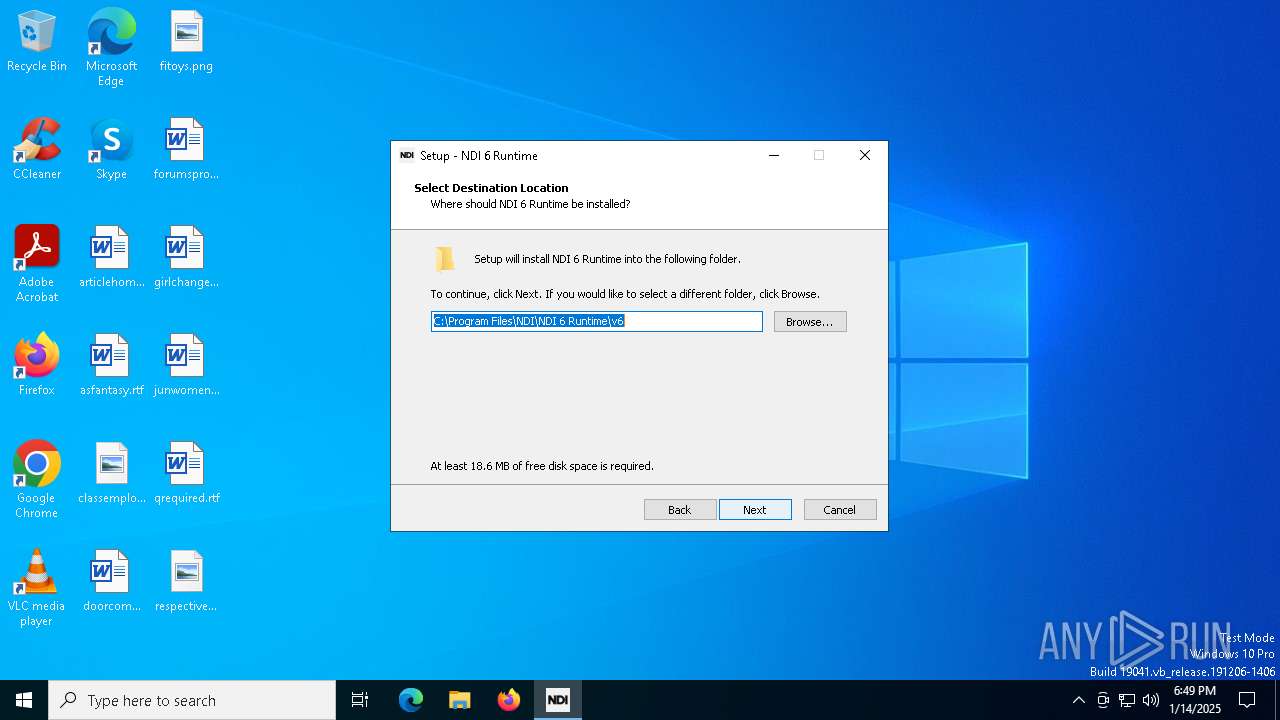
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\NDI\NDI 6 Runtime\v6 | |||
| (PID) Process: | (4708) NDI 6 Runtime.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{71AFF296-ED43-4166-8301-4649285EE712}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\NDI\NDI 6 Runtime\v6\ | |||
| (PID) Process: | (4708) NDI 6 Runtime.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{71AFF296-ED43-4166-8301-4649285EE712}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: NDI 6 Runtime | |||
Executable files
16
Suspicious files
3
Text files
2
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4708 | NDI 6 Runtime.tmp | C:\Program Files\NDI\NDI 6 Runtime\v6\is-3SB67.tmp | — | |
MD5:— | SHA256:— | |||
| 4708 | NDI 6 Runtime.tmp | C:\Program Files\NDI\NDI 6 Runtime\v6\Processing.NDI.Lib.DirectShow.x64.dll | — | |
MD5:— | SHA256:— | |||
| 6136 | NDI 6 Runtime.exe | C:\Users\admin\AppData\Local\Temp\is-H9AD9.tmp\NDI 6 Runtime.tmp | executable | |
MD5:D4C61EA627BFA5BC38594E23C52D6561 | SHA256:9CEBAD2847D1F392587C418F878BD49DEA3E5ED35989474591F8F2BF80ABBCF5 | |||
| 7152 | NDI 6 Runtime.exe | C:\Users\admin\AppData\Local\Temp\is-SO3UF.tmp\NDI 6 Runtime.tmp | executable | |
MD5:D4C61EA627BFA5BC38594E23C52D6561 | SHA256:9CEBAD2847D1F392587C418F878BD49DEA3E5ED35989474591F8F2BF80ABBCF5 | |||
| 4708 | NDI 6 Runtime.tmp | C:\Users\admin\AppData\Local\Temp\is-EM9J9.tmp\idp.dll | executable | |
MD5:0630DC4DB009852DF6EF39CB1C8A936C | SHA256:3B0EC63CEC63BB6AE7C206793D5714BE341C316D9F966832391A0981C2E420C1 | |||
| 4708 | NDI 6 Runtime.tmp | C:\Program Files\NDI\NDI 6 Runtime\v6\NDI License Agreement.pdf | ||
MD5:4E6122996F10BDCD31D77501B0F57192 | SHA256:E66417CAB004B5B68433F5139E10FEC18BB6B8779E7C4020B6B8E4182215C443 | |||
| 4708 | NDI 6 Runtime.tmp | C:\Program Files\NDI\NDI 6 Runtime\v6\is-KIEUR.tmp | executable | |
MD5:AE773F5539797D6937A93B269648787F | SHA256:C24FE5F7739A0A7C6C673FD83D14CA623DB15F3612C41FBCC878E55693A5A12E | |||
| 4708 | NDI 6 Runtime.tmp | C:\Users\admin\AppData\Local\Temp\is-EM9J9.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4708 | NDI 6 Runtime.tmp | C:\Program Files\NDI\NDI 6 Runtime\v6\unins000.exe | executable | |
MD5:AE773F5539797D6937A93B269648787F | SHA256:C24FE5F7739A0A7C6C673FD83D14CA623DB15F3612C41FBCC878E55693A5A12E | |||
| 4708 | NDI 6 Runtime.tmp | C:\Program Files\NDI\NDI 6 Runtime\v6\NDI Information.url | url | |
MD5:8F9095160A7EBCA3FB512962BDD45F7D | SHA256:D609C58A98B55E16B7867F31D79D2F05CBA0A65BEB0B5576F8FEA31FCB609DDB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
32
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
836 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
836 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6648 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |