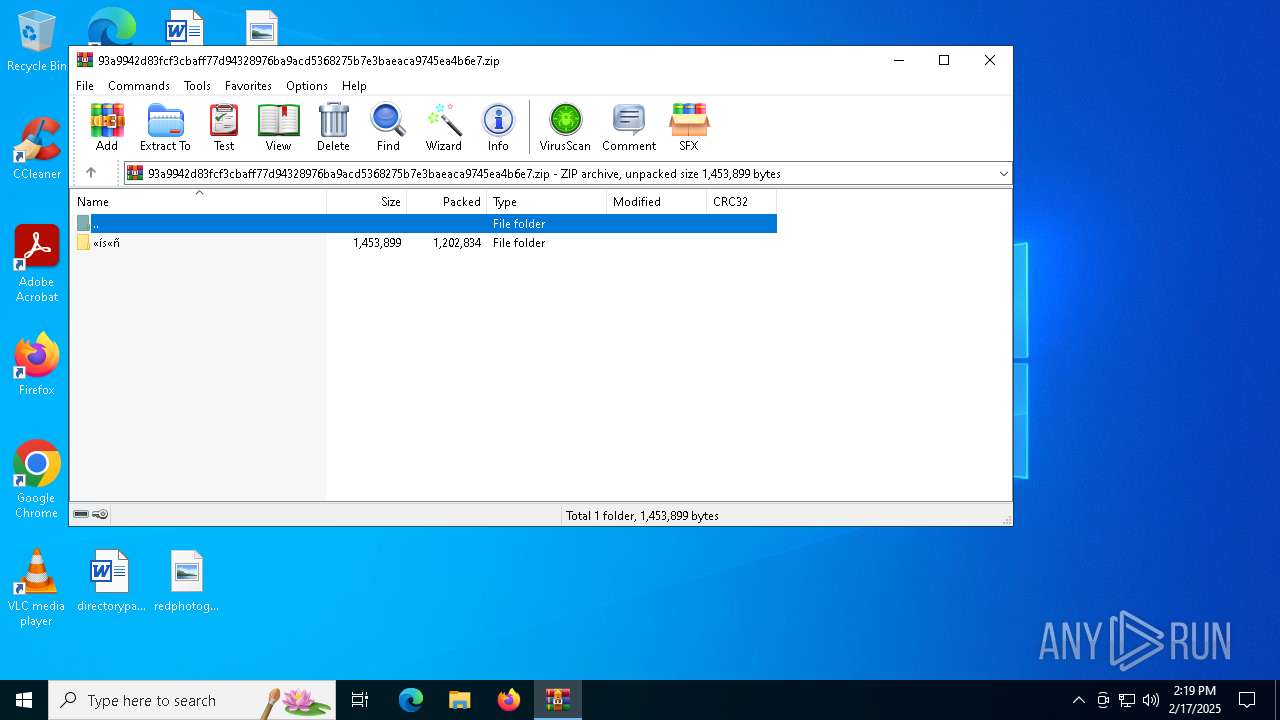
| File name: | 93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7 |
| Full analysis: | https://app.any.run/tasks/952dac1c-3bd3-4e76-8c5c-f84248a87b5a |
| Verdict: | Malicious activity |
| Analysis date: | February 17, 2025, 14:19:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 1B11867E6C2C94A121B90F448FF89949 |
| SHA1: | 2A99BE04FF50278100CE15C608BFB7D7D862CAF1 |
| SHA256: | 93A9942D83FCF3CBAFF77D94328976BA9ACD5368275B7E3BAEACA9745EA4B6E7 |
| SSDEEP: | 49152:rktSlAf4zkaHhpza1Fz5N08XG6mF7lxel8eeWnMYssnJNfJ9idJn5nN4v914j322:rk0Sf4zkaBpza1FtNTXG68il8LhYssJ4 |
MALICIOUS
Detects Cygwin installation
- WinRAR.exe (PID: 3816)
Starts NET.EXE for service management
- net.exe (PID: 6872)
- cmd.exe (PID: 6788)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3816)
- powershell.exe (PID: 2060)
- powershell.exe (PID: 6536)
- cmd.exe (PID: 6264)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3816)
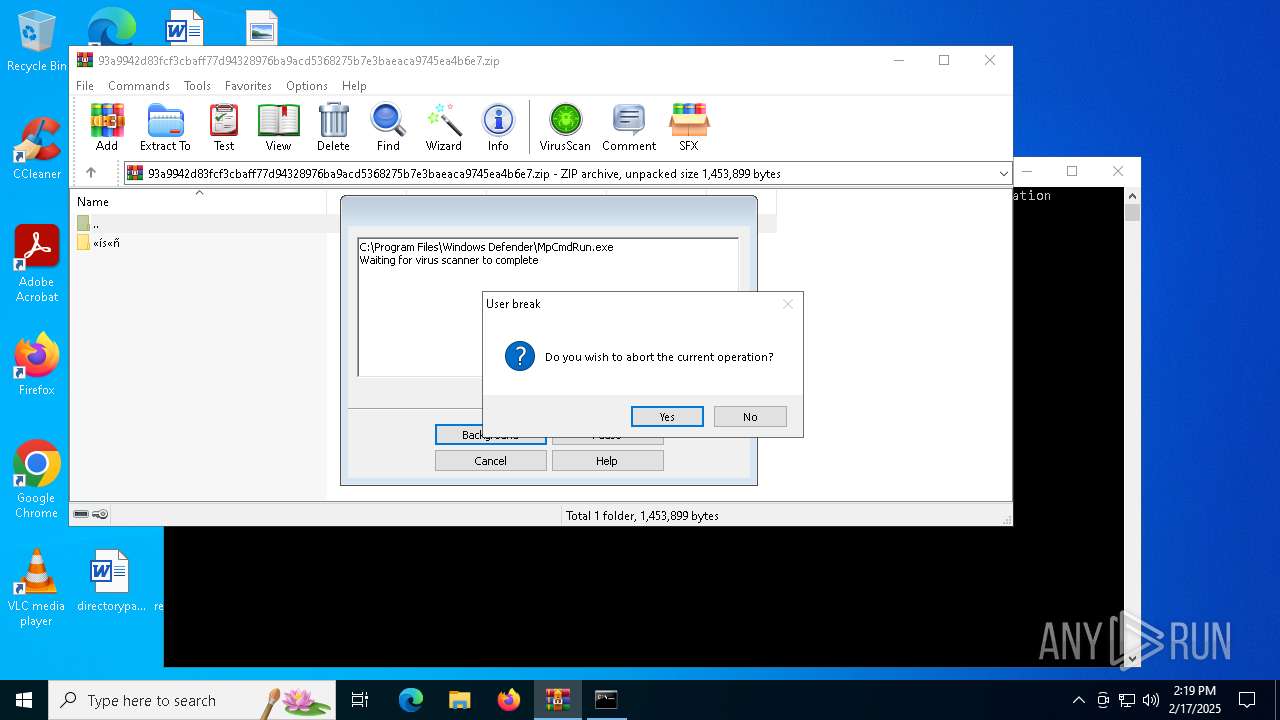
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 3816)
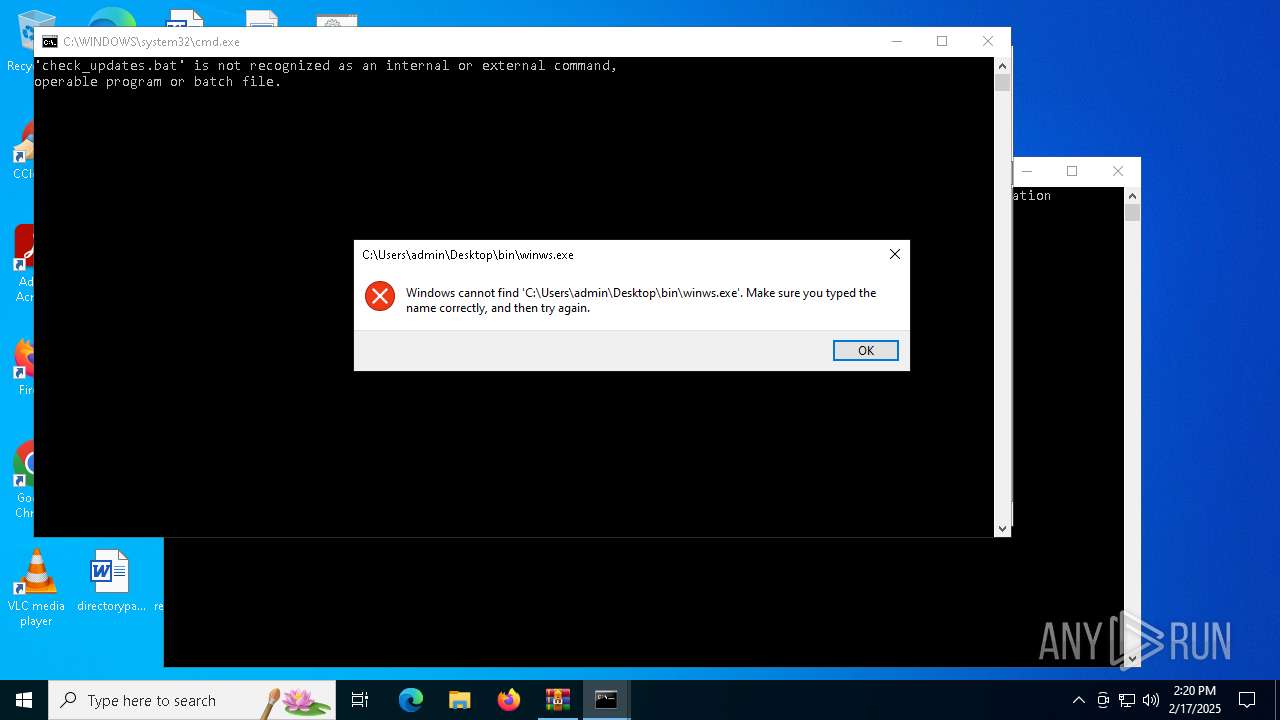
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3816)
- powershell.exe (PID: 2060)
- powershell.exe (PID: 6536)
Starts application with an unusual extension
- cmd.exe (PID: 4328)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 3220)
- cmd.exe (PID: 3420)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 1016)
- cmd.exe (PID: 5752)
- cmd.exe (PID: 6156)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 6464)
- cmd.exe (PID: 6788)
Starts process via Powershell
- powershell.exe (PID: 2060)
- powershell.exe (PID: 6536)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1348)
- cmd.exe (PID: 6352)
- cmd.exe (PID: 6612)
- cmd.exe (PID: 6464)
Application launched itself
- cmd.exe (PID: 6264)
Hides command output
- cmd.exe (PID: 6612)
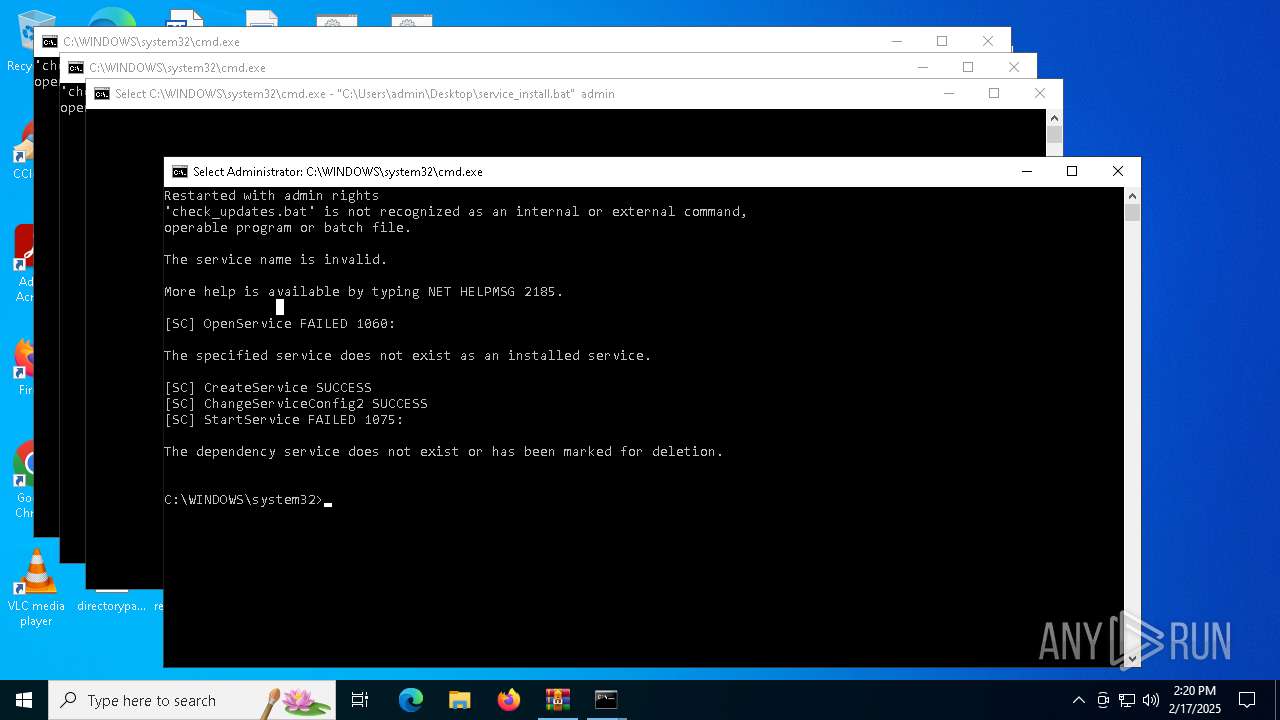
Windows service management via SC.EXE
- sc.exe (PID: 6956)
- sc.exe (PID: 6996)
- sc.exe (PID: 7016)
Creates a new Windows service
- sc.exe (PID: 6976)
Starts SC.EXE for service management
- cmd.exe (PID: 6788)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 3816)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3816)
Create files in a temporary directory
- MpCmdRun.exe (PID: 1016)
Checks supported languages
- MpCmdRun.exe (PID: 1016)
- chcp.com (PID: 4132)
- chcp.com (PID: 6016)
- chcp.com (PID: 2072)
- chcp.com (PID: 4952)
- chcp.com (PID: 4536)
- chcp.com (PID: 5628)
- chcp.com (PID: 4504)
- chcp.com (PID: 6328)
- chcp.com (PID: 5788)
- chcp.com (PID: 6232)
- chcp.com (PID: 6852)
- chcp.com (PID: 6516)
Manual execution by a user
- cmd.exe (PID: 4328)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 3220)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 3420)
- cmd.exe (PID: 1016)
- cmd.exe (PID: 5752)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 6464)
Reads the computer name
- MpCmdRun.exe (PID: 1016)
Changes the display of characters in the console
- cmd.exe (PID: 4328)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 3220)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 3420)
- cmd.exe (PID: 1016)
- cmd.exe (PID: 5752)
- cmd.exe (PID: 6156)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 6464)
- cmd.exe (PID: 6788)
Checks proxy server information
- powershell.exe (PID: 6628)
Disables trace logs
- powershell.exe (PID: 6628)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:11:07 15:00:14 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | ??室/bin/ |
Total processes
172
Monitored processes
52
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
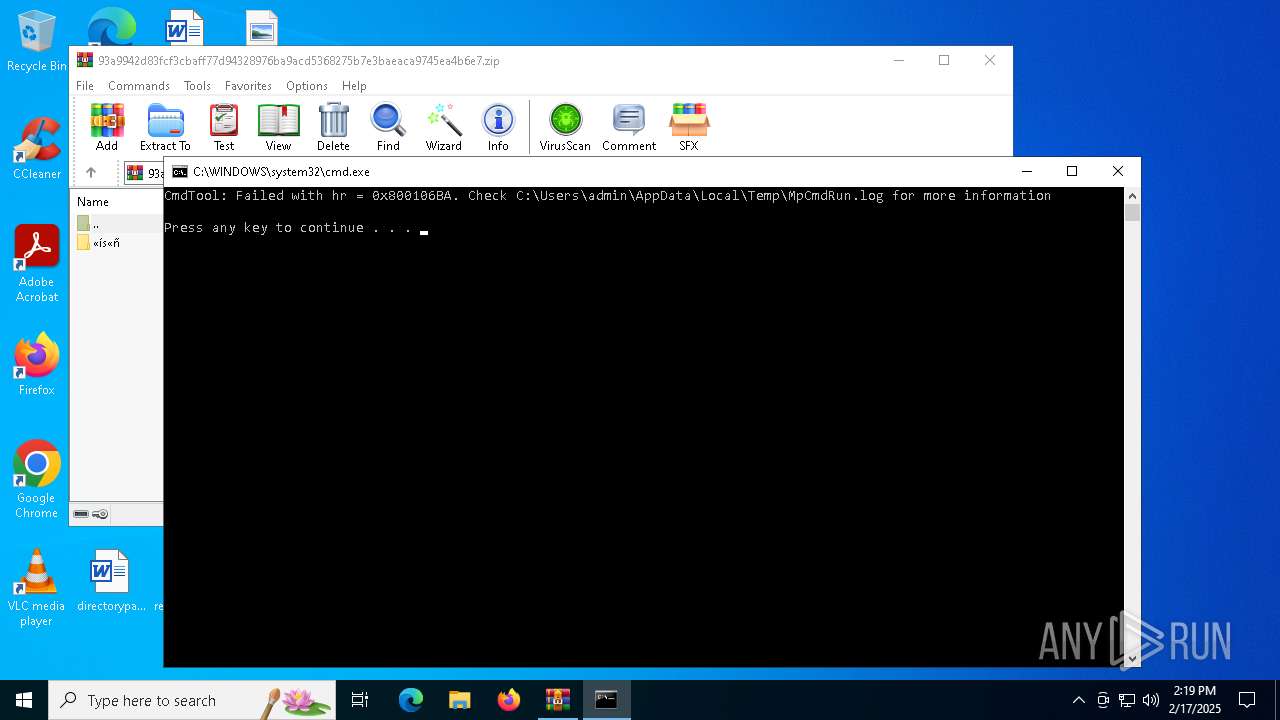
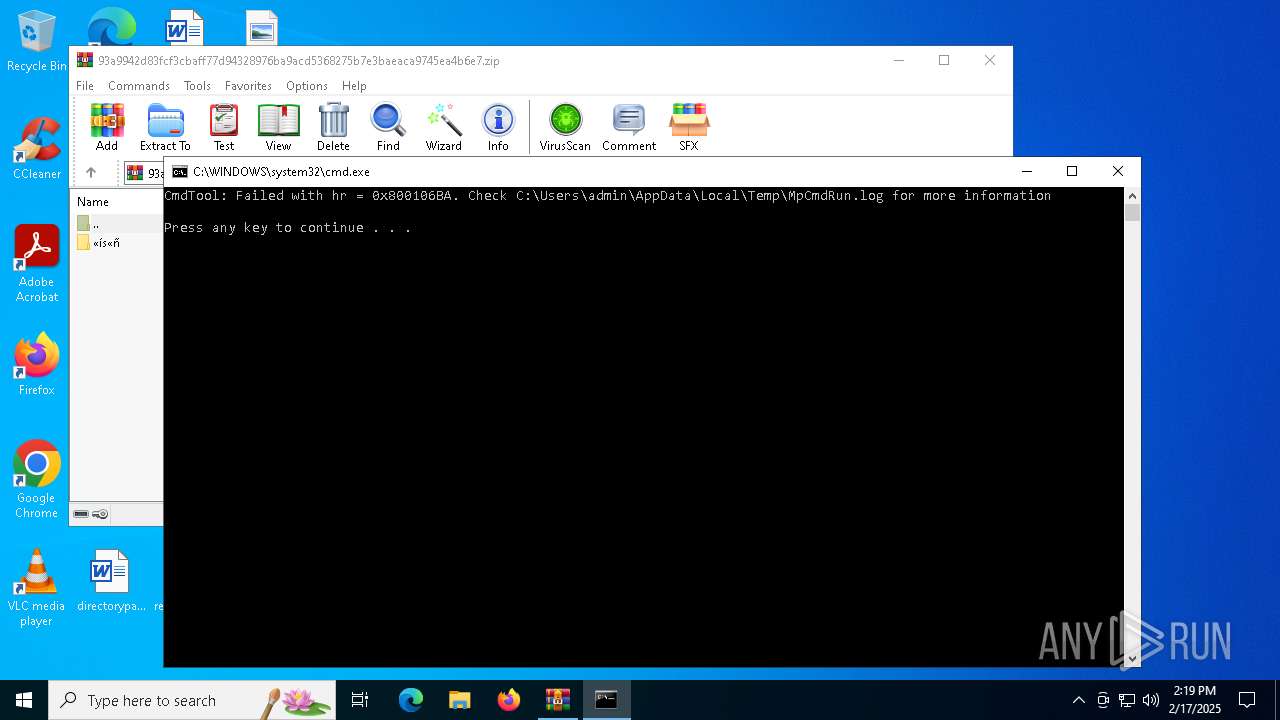
| 1016 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
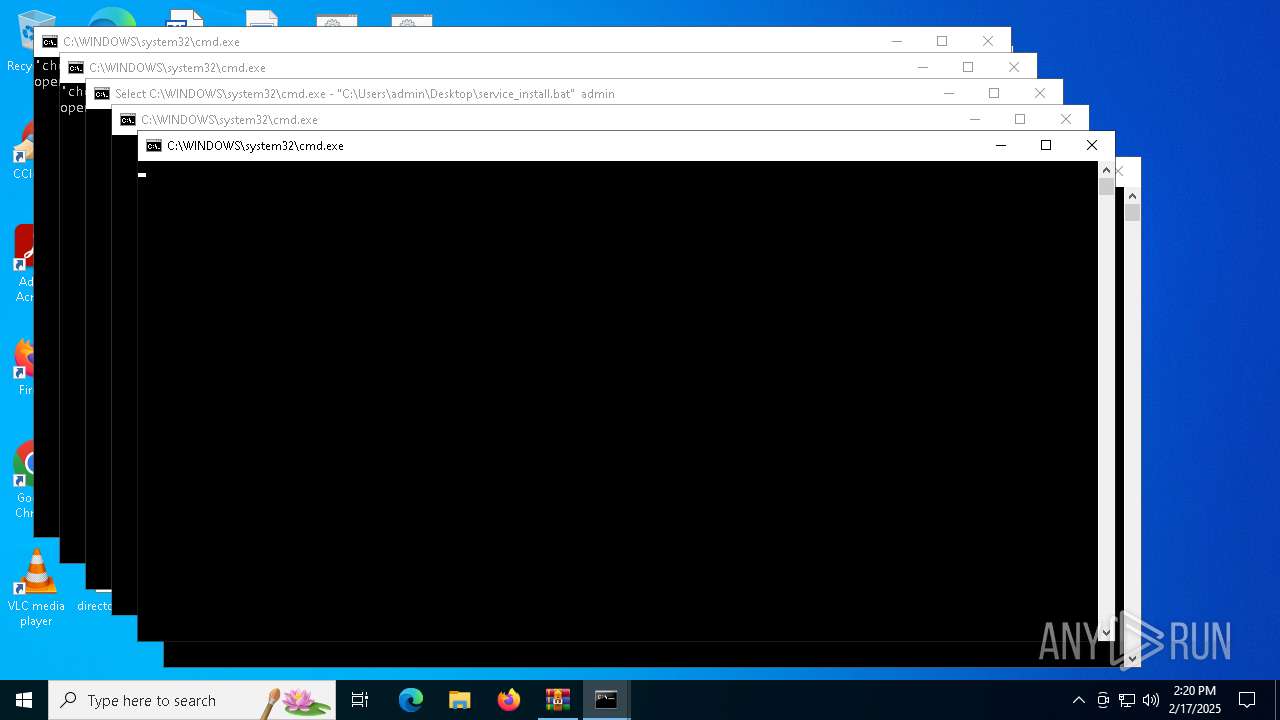
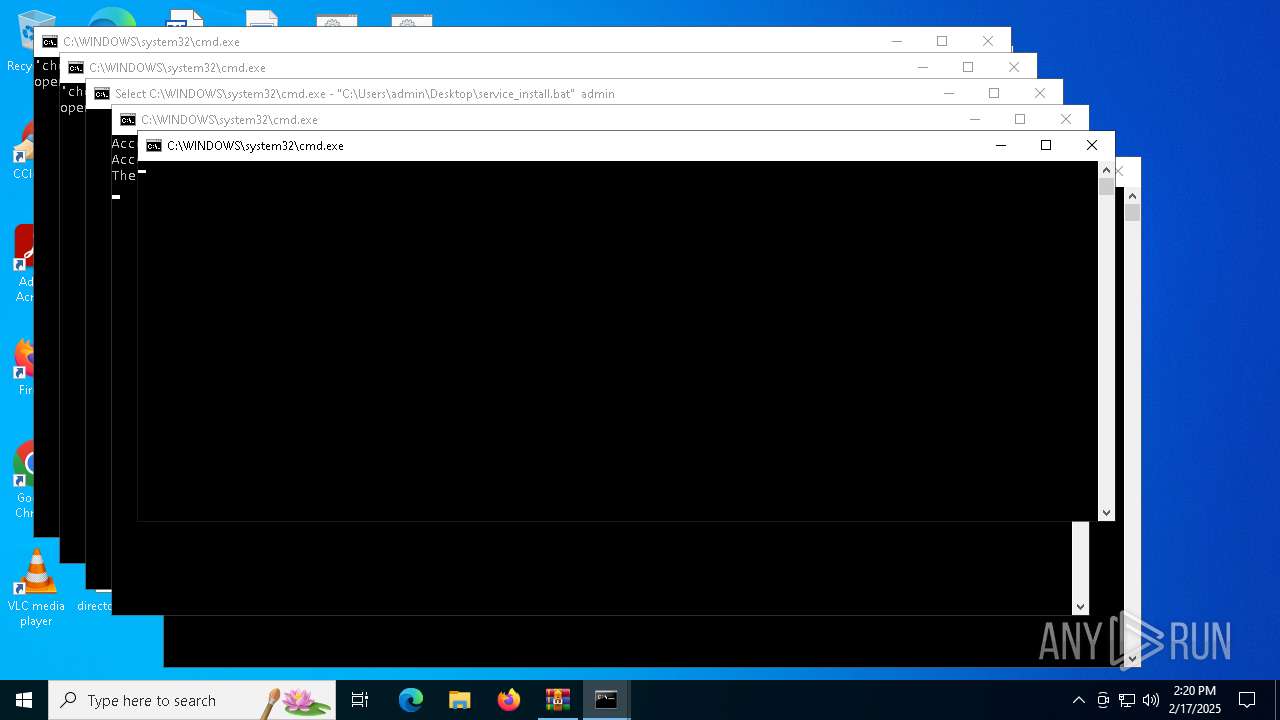
| 1016 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\discord.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
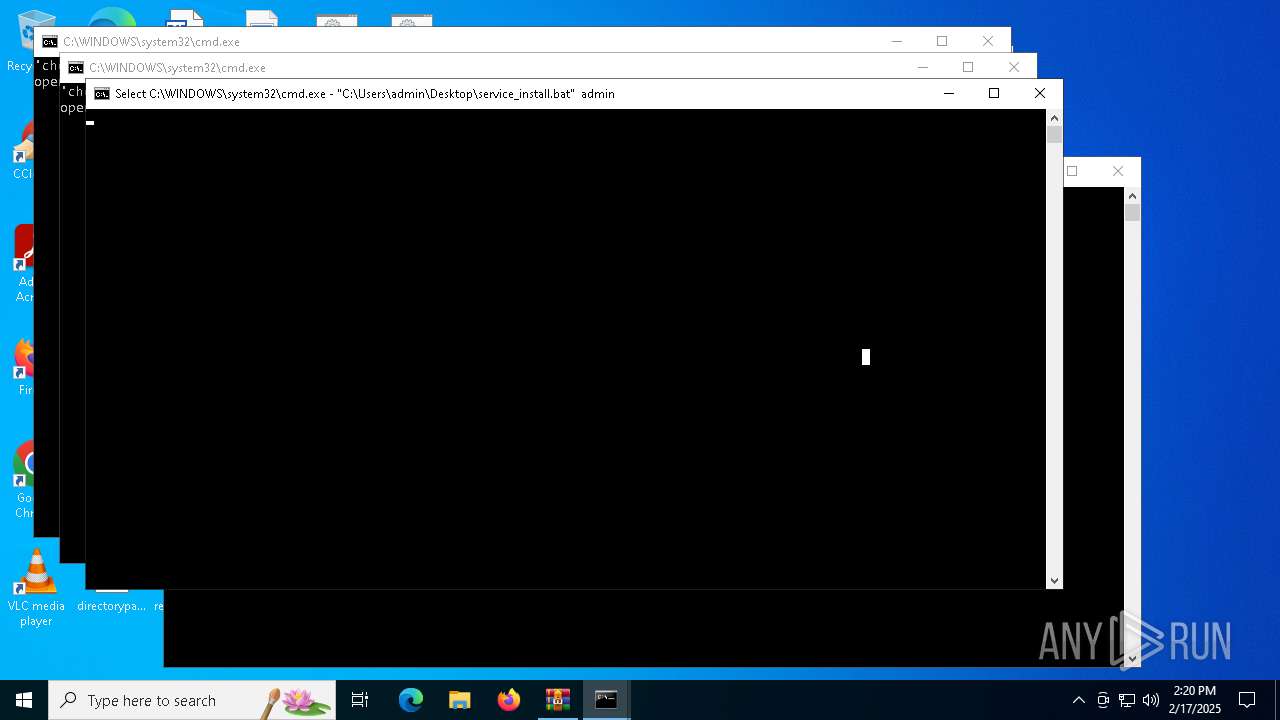
| 1348 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\service_install.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2060 | powershell -Command "Start-Process 'cmd.exe' -ArgumentList '/k \"\"C:\Users\admin\Desktop\service_install.bat\" admin\"' -Verb RunAs" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2072 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3220 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\general (ALT2).bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3420 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\general (2).bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\general (ALT3).bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3532 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 964
Read events
19 955
Write events
9
Delete events
0
Modification events
| (PID) Process: | (3816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip | |||
| (PID) Process: | (3816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
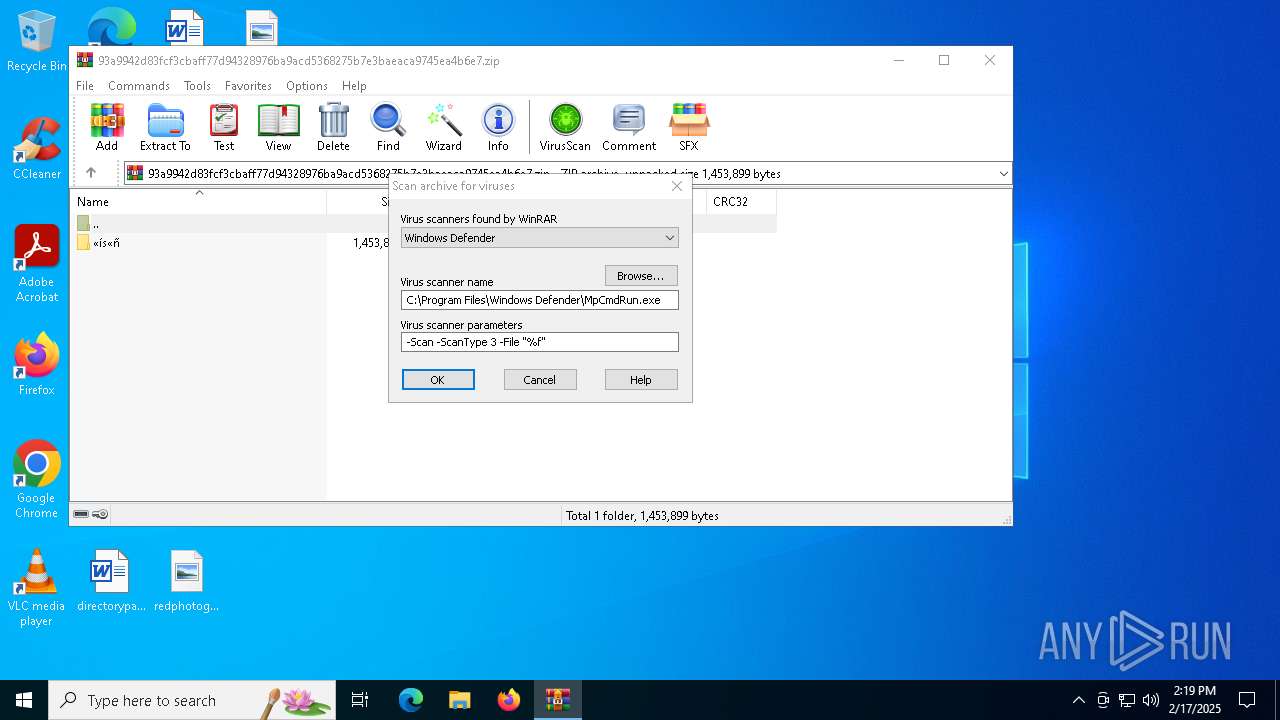
| (PID) Process: | (3816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
4
Suspicious files
4
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
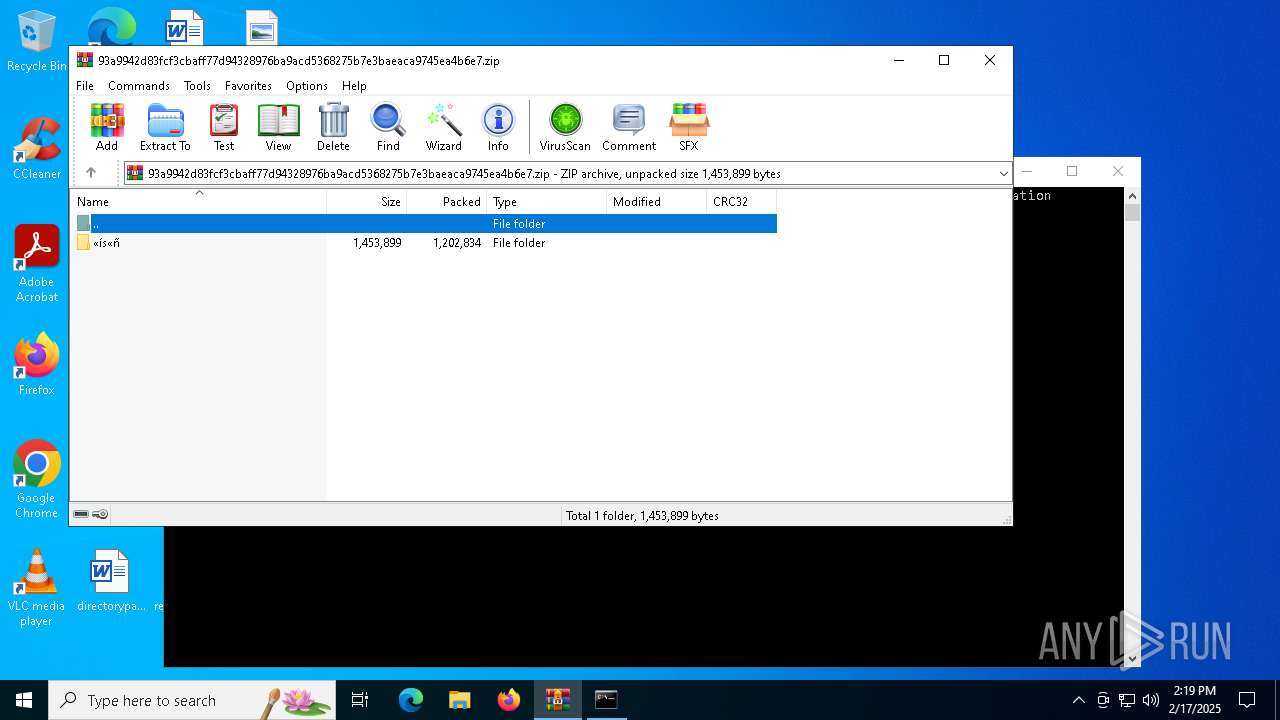
| 3816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip\«ís«ñ\bin\tls_clienthello_www_google_com.bin | binary | |
MD5:7AB7AD857C5B8794FBDF1091B494DC94 | SHA256:E5938780152169F720383F80EABB309E9477369B83B5EC40CC137C397F862CDE | |||
| 3816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip\«ís«ñ\bin\quic_initial_www_google_com.bin | binary | |
MD5:312526D39958D89B1F8AB67789AB985F | SHA256:F4589C57749F956BB30538197A521D7005F8B0A8723B4707E72405E51DDAC50A | |||
| 3816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip\«ís«ñ\bin\WinDivert64.sys | executable | |
MD5:89ED5BE7EA83C01D0DE33D3519944AA5 | SHA256:8DA085332782708D8767BCACE5327A6EC7283C17CFB85E40B03CD2323A90DDC2 | |||
| 3816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip\«ís«ñ\bin\cygwin1.dll | executable | |
MD5:C50B50303FAE4AFE7248307339A00D13 | SHA256:712C39A069541AFA69CFCBE01B422BD67B4201EEE7E94CC1327D4ED8B4FA2167 | |||
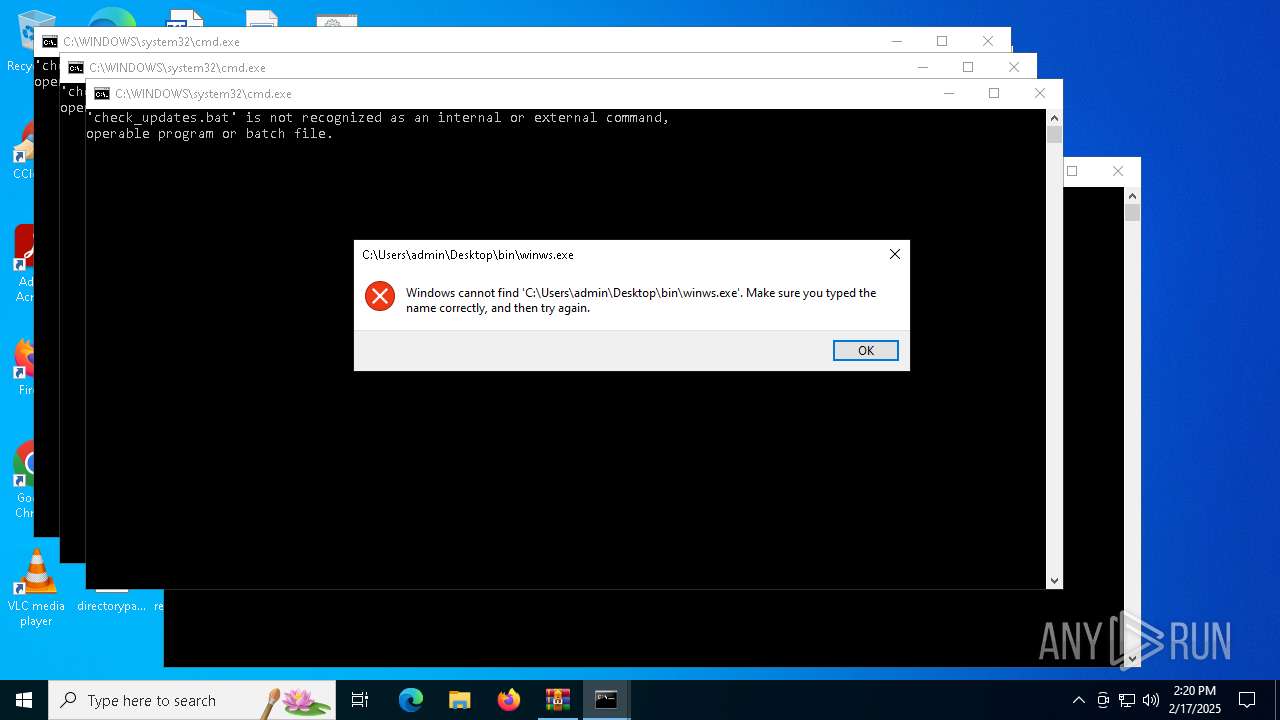
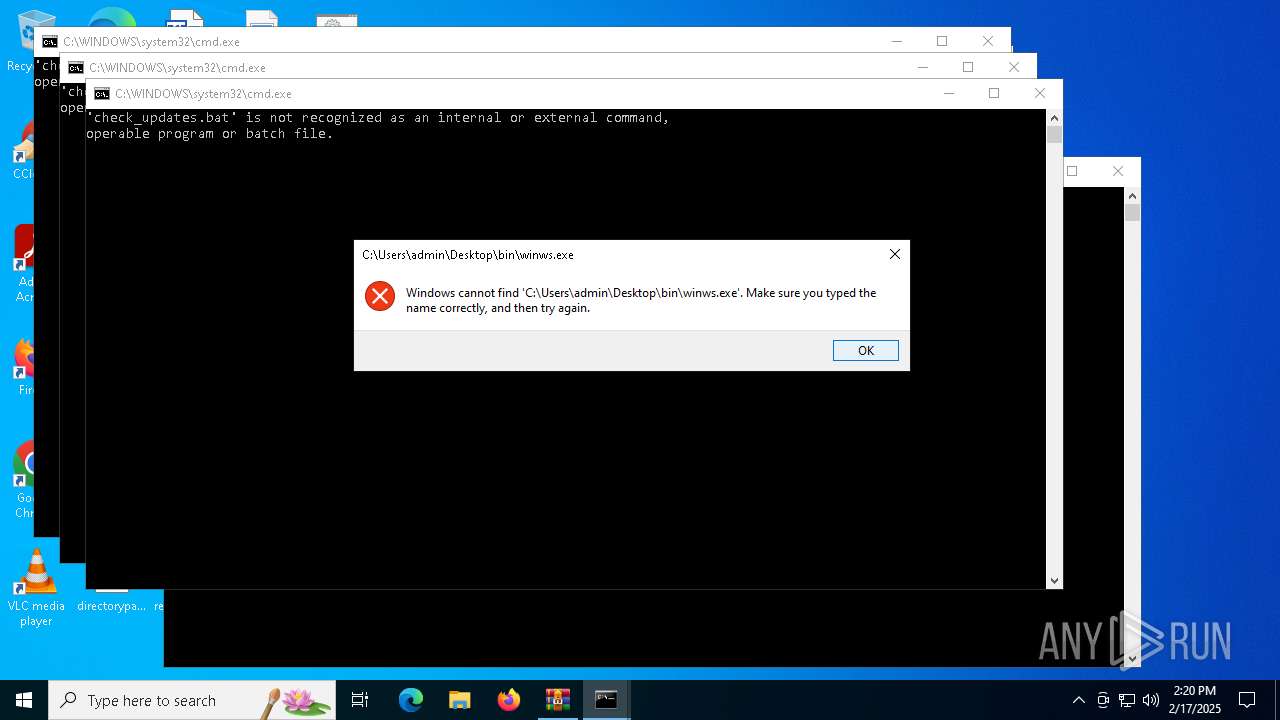
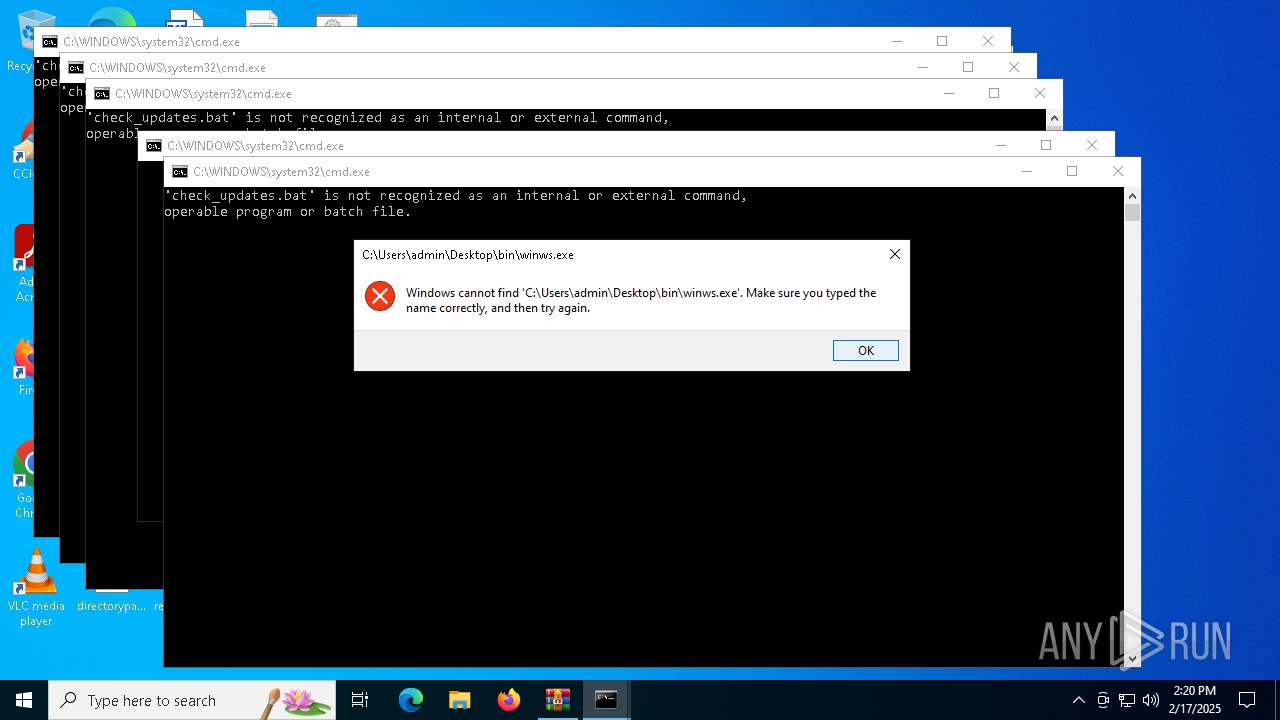
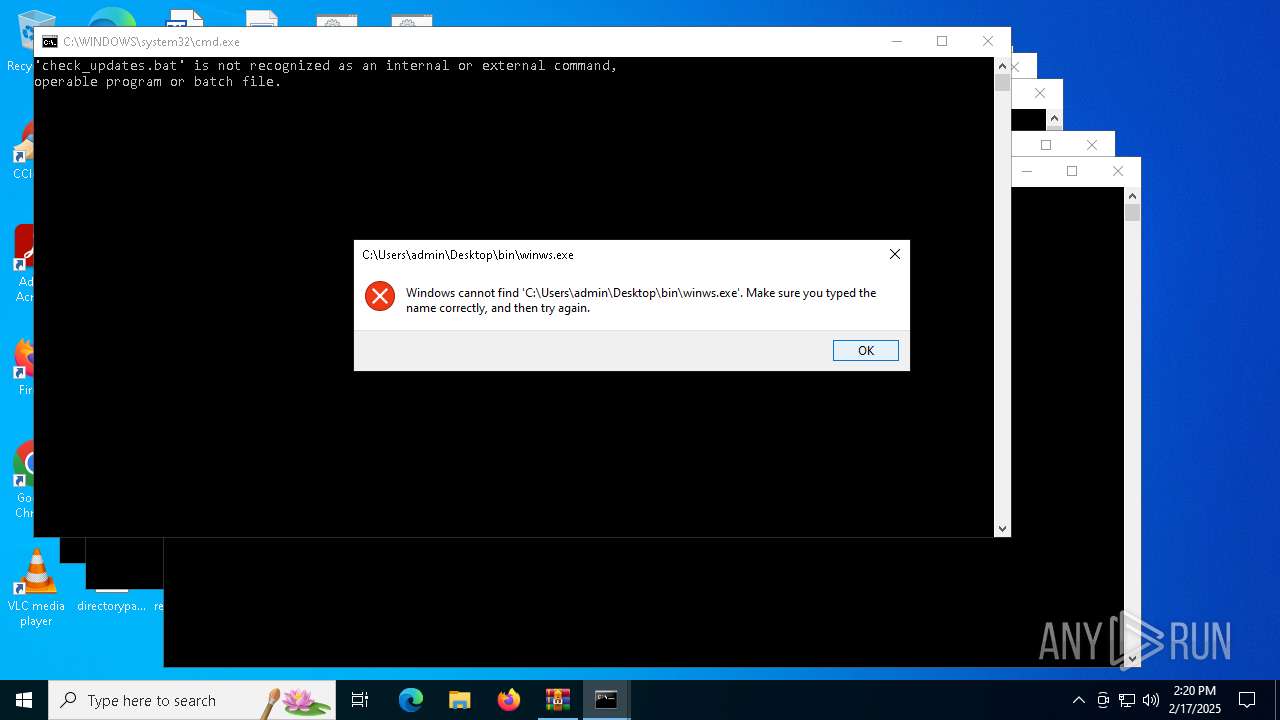
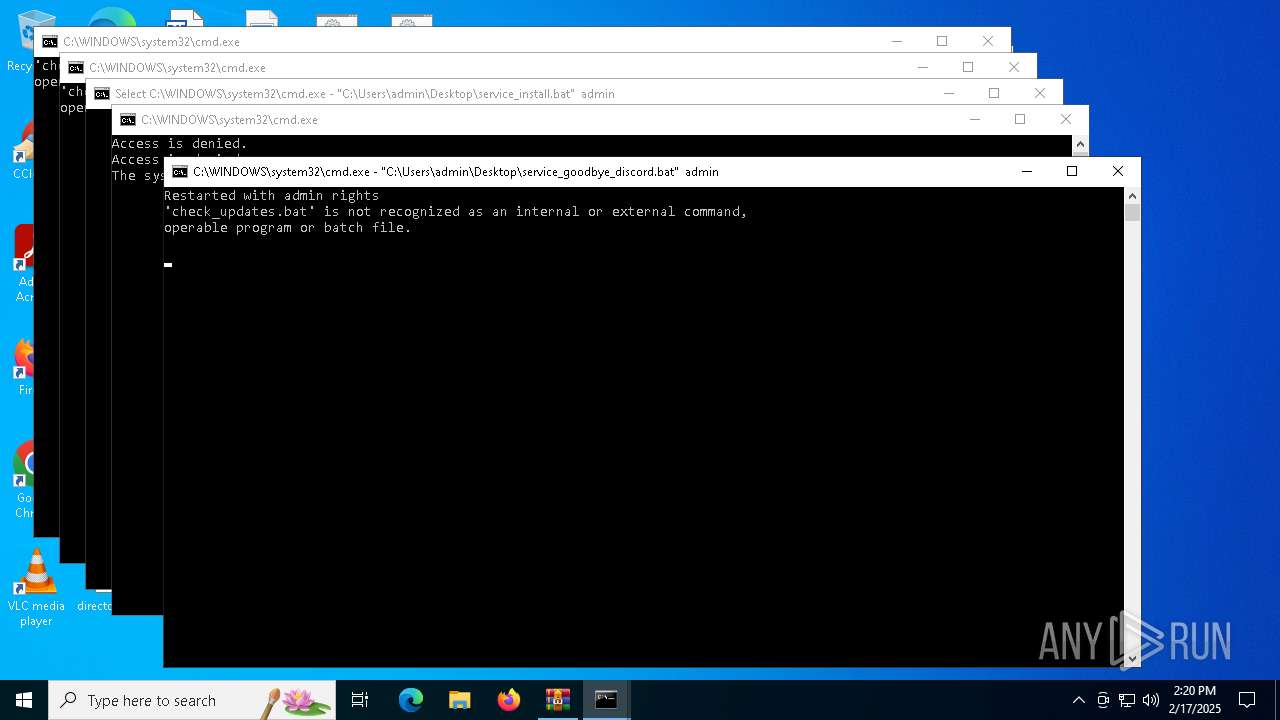
| 3816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip\«ís«ñ\check_updates.bat | text | |
MD5:C0AF479B986A7E2095929A68136CD97C | SHA256:438ADFB9F66429E1B6B0474FE0CDBD397098D58C4B80FF2C74237C6F9B99DF23 | |||
| 3816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip\«ís«ñ\bin\WinDivert.dll | executable | |
MD5:B2014D33EE645112D5DC16FE9D9FCBFF | SHA256:C1E060EE19444A259B2162F8AF0F3FE8C4428A1C6F694DCE20DE194AC8D7D9A2 | |||
| 3816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip\«ís«ñ\general (ALT).bat | text | |
MD5:F2DFDB0EC74378D6DEFC004BCFCEE491 | SHA256:ADFA52BEACE1FF288D2CC20D6814E8EB04FAE5A9256B600C402F91AB94AF5886 | |||
| 3816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip\«ís«ñ\bin\winws.exe | executable | |
MD5:444FE359CA183016B93D8BFE398D5103 | SHA256:0453FCE6906402181DBFF7E09B32181EB1C08BB002BE89849E8992B832F43B89 | |||
| 3816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip\«ís«ñ\general (ALT2).bat | text | |
MD5:4B24D1B6ACA069DFFB4A55C003AD89CF | SHA256:16113CF48D720D27BEFBCDDCF26C890515D5586967A0B536838D2C8F5D42974F | |||
| 3816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3816.29832\93a9942d83fcf3cbaff77d94328976ba9acd5368275b7e3baeaca9745ea4b6e7.zip\«ís«ñ\general (îâÆæ2).bat | text | |
MD5:68A787EE43D189566AF3FD05DB25BCE6 | SHA256:011332D582BF344B0543E8EC972C2C3A2A6B09A8D2052BC04CED067BEB16DBC9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
8
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.17:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5392 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | — | 140.82.121.3:443 | https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/refs/heads/main/.service/version.txt | unknown | — | — | unknown |
5392 | svchost.exe | GET | 200 | 2.16.164.17:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.19.96.90:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5392 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.17:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5392 | svchost.exe | 2.16.164.17:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5392 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |