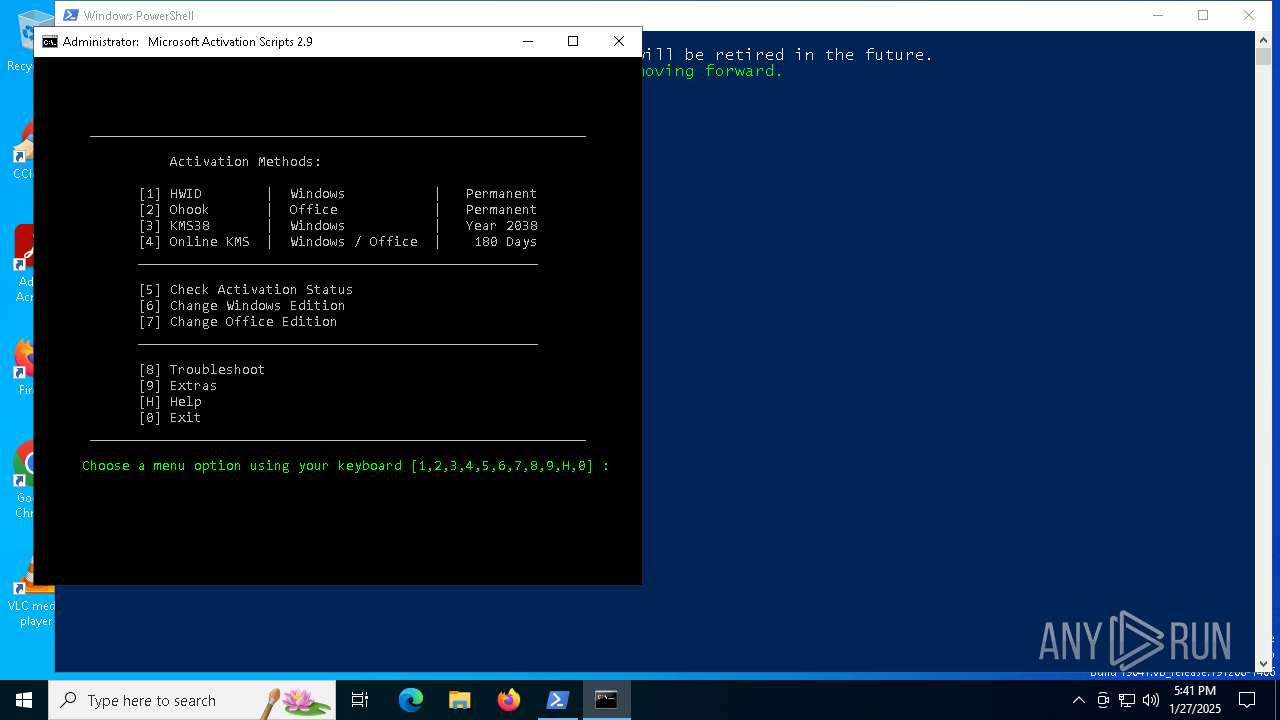
| File name: | Massgrave.ps1 |
| Full analysis: | https://app.any.run/tasks/1dfcf203-8e12-4f23-96d4-4fd3ab848f86 |
| Verdict: | Malicious activity |
| Analysis date: | January 27, 2025, 17:40:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 9D6BE2013F159CEC15AA16AC63A3DFD0 |
| SHA1: | 5249BC02AAD18CEA0876EB3FA568177B311800D4 |
| SHA256: | 93A790E0A65D0A47A7988E81F069C4C7044802C50848735DCAF0F6B0EF921DCD |
| SSDEEP: | 3:WIuC0KP:WIuC0U |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 4576)
SUSPICIOUS
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4576)
- powershell.exe (PID: 5920)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 2324)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 4576)
- powershell.exe (PID: 5920)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 2324)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 4576)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 4576)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 4576)
- cmd.exe (PID: 1344)
- cmd.exe (PID: 2312)
- powershell.exe (PID: 4716)
- cmd.exe (PID: 1856)
- cmd.exe (PID: 5112)
- powershell.exe (PID: 1296)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 5728)
Executing commands from ".cmd" file
- powershell.exe (PID: 4576)
- cmd.exe (PID: 1344)
- powershell.exe (PID: 4716)
- cmd.exe (PID: 1856)
- powershell.exe (PID: 1296)
- cmd.exe (PID: 1348)
Windows service management via SC.EXE
- sc.exe (PID: 6012)
- sc.exe (PID: 4840)
- sc.exe (PID: 4624)
Starts SC.EXE for service management
- cmd.exe (PID: 1344)
- cmd.exe (PID: 1856)
- cmd.exe (PID: 1348)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1344)
- cmd.exe (PID: 1856)
- cmd.exe (PID: 1348)
Application launched itself
- cmd.exe (PID: 2312)
- cmd.exe (PID: 1344)
- cmd.exe (PID: 5112)
- cmd.exe (PID: 1856)
- cmd.exe (PID: 5728)
- cmd.exe (PID: 1348)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 5200)
- cmd.exe (PID: 2600)
- cmd.exe (PID: 3540)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5200)
- cmd.exe (PID: 1344)
- cmd.exe (PID: 2600)
- cmd.exe (PID: 1856)
- cmd.exe (PID: 3540)
- cmd.exe (PID: 1348)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 5200)
- cmd.exe (PID: 2600)
- cmd.exe (PID: 3540)
INFO
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 4576)
- powershell.exe (PID: 5920)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 2324)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 4576)
- powershell.exe (PID: 5920)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 2324)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4576)
- powershell.exe (PID: 5920)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 2324)
Checks proxy server information
- powershell.exe (PID: 4576)
Disables trace logs
- powershell.exe (PID: 4576)
Checks operating system version
- cmd.exe (PID: 1344)
- cmd.exe (PID: 1856)
- cmd.exe (PID: 1348)
Starts MODE.COM to configure console settings
- mode.com (PID: 5764)
Checks supported languages
- mode.com (PID: 5764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
195
Monitored processes
82
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | fltmc | C:\Windows\System32\fltMC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Filter Manager Control Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 244 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo prompt $E " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 520 | reg query "HKCU\Console" /v ForceV2 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | find /i "ARM64" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | find /i "ARM64" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | powershell.exe "$t=[AppDomain]::CurrentDomain.DefineDynamicAssembly(4, 1).DefineDynamicModule(2, $False).DefineType(0); $t.DefinePInvokeMethod('GetStdHandle', 'kernel32.dll', 22, 1, [IntPtr], @([Int32]), 1, 3).SetImplementationFlags(128); $t.DefinePInvokeMethod('SetConsoleMode', 'kernel32.dll', 22, 1, [Boolean], @([IntPtr], [Int32]), 1, 3).SetImplementationFlags(128); $k=$t.CreateType(); $b=$k::SetConsoleMode($k::GetStdHandle(-10), 0x0080); & cmd.exe '/c' '"""C:\Users\admin\AppData\Local\Temp\MAS_9d61b4f1-9852-42e7-b3a1-4a24c9a876fe.cmd""" -el -el -qedit'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | "C:\WINDOWS\system32\cmd.exe" /c ""C:\Users\admin\AppData\Local\Temp\MAS_9d61b4f1-9852-42e7-b3a1-4a24c9a876fe.cmd" " | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | "C:\WINDOWS\System32\cmd.exe" /c ""C:\Users\admin\AppData\Local\Temp\MAS_9d61b4f1-9852-42e7-b3a1-4a24c9a876fe.cmd" -el -el -qedit" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 531
Read events
35 531
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
4
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4576 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sxekvnl1.203.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5920 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mdlotmn0.3ow.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4576 | powershell.exe | C:\Users\admin\AppData\Local\Temp\MAS_9d61b4f1-9852-42e7-b3a1-4a24c9a876fe.cmd | text | |
MD5:0169BC1FC358A3BB6054B59B6AF53FA6 | SHA256:B35D90AAEE60E961F00497033808396B55A00894BC985AEF6ED79EB1C6FD7E44 | |||
| 4576 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:69B8F4C4AA43BBC3E1357A362B56F9B4 | SHA256:13908F494A72E71E7737D5DF69270A2613D5CBEEAA270A51622E50E9B0161064 | |||
| 4840 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_u4ksutil.pqi.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5920 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:6287FF2315E27CC3BC4C5948644516C7 | SHA256:39CA788D4785D5DBA22111B985F01D2AAFDEDB7897EF90F3DD4954307D75A25C | |||
| 3732 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pbntqlr1.x1s.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4716 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_atcpo3ay.mwz.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3732 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_thobao4i.hzw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4576 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SKYHGJ32ZT3EKDZ0W9UC.temp | binary | |
MD5:69B8F4C4AA43BBC3E1357A362B56F9B4 | SHA256:13908F494A72E71E7737D5DF69270A2613D5CBEEAA270A51622E50E9B0161064 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.254.19:443 | https://dev.azure.com/massgrave/Microsoft-Activation-Scripts/_apis/git/repositories/Microsoft-Activation-Scripts/items?path=/MAS/All-In-One-Version-KL/MAS_AIO.cmd&versionType=Commit&version=37ec96504a2983a5801c43e975ab78c8f9315d2a | unknown | — | — | unknown |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 301 | 172.67.201.171:443 | https://massgrave.dev/get | unknown | text | 23 b | unknown |
— | — | GET | 200 | 104.21.22.3:443 | https://massgrave.dev/get.ps1 | unknown | text | 4.04 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4576 | powershell.exe | 104.21.22.3:443 | massgrave.dev | CLOUDFLARENET | — | unknown |
3976 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4576 | powershell.exe | 13.107.42.20:443 | dev.azure.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
massgrave.dev |
| unknown |
dev.azure.com |
| whitelisted |
updatecheck.massgrave.dev |
| unknown |
self.events.data.microsoft.com |
| whitelisted |