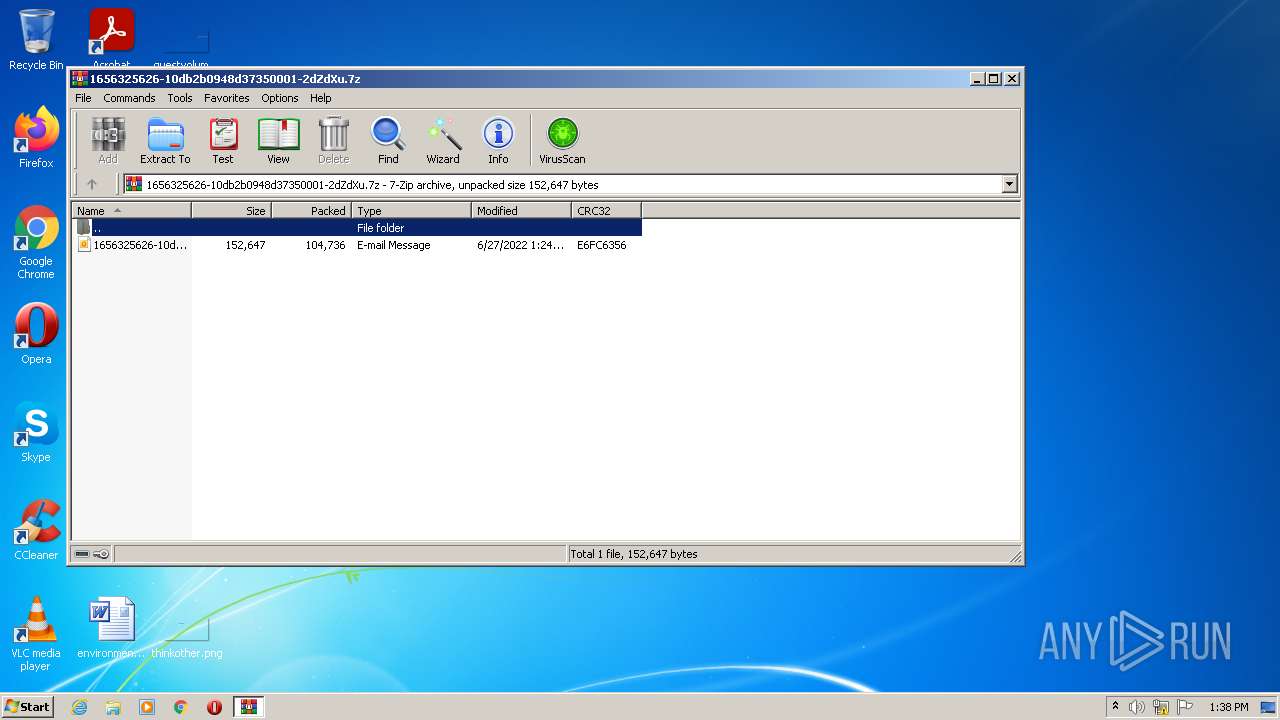
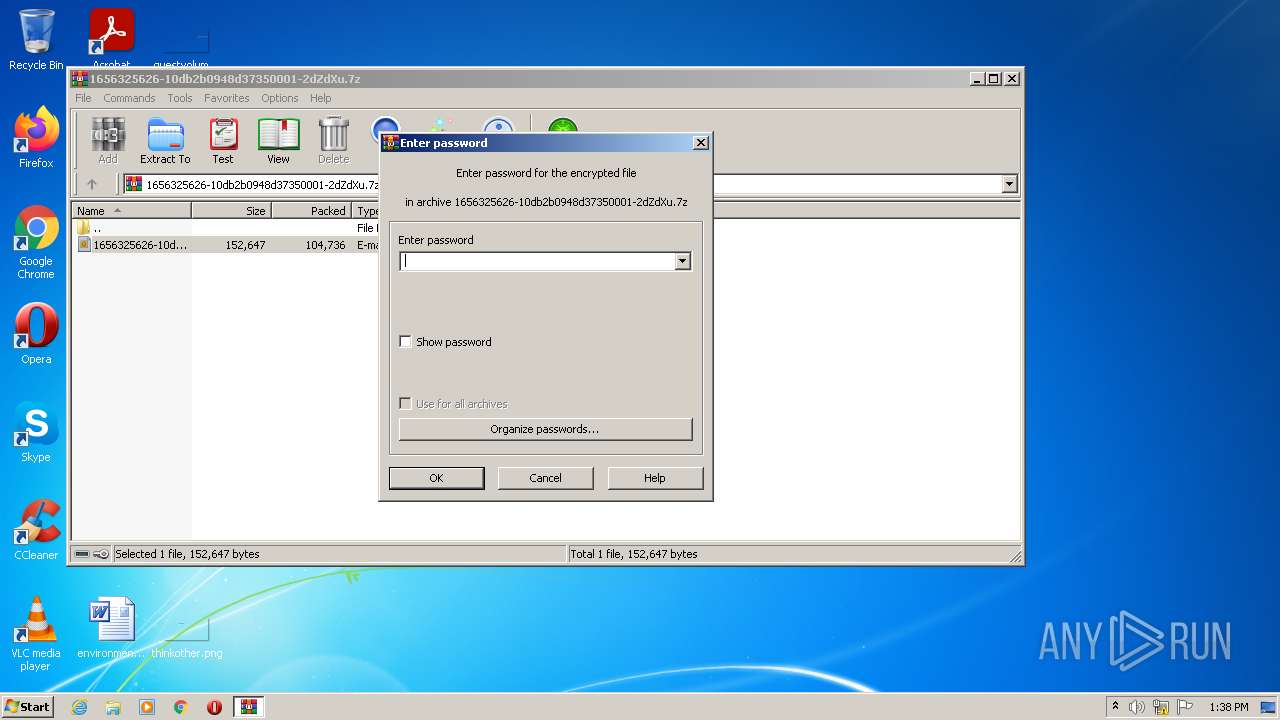
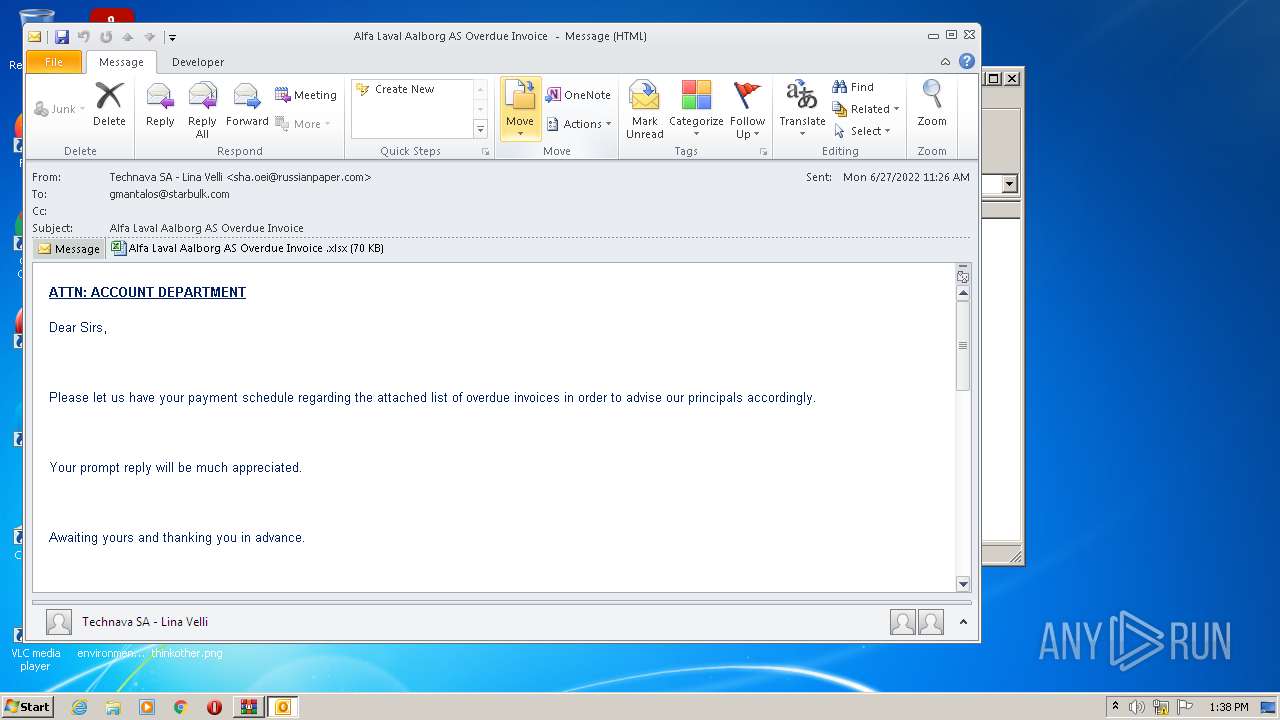
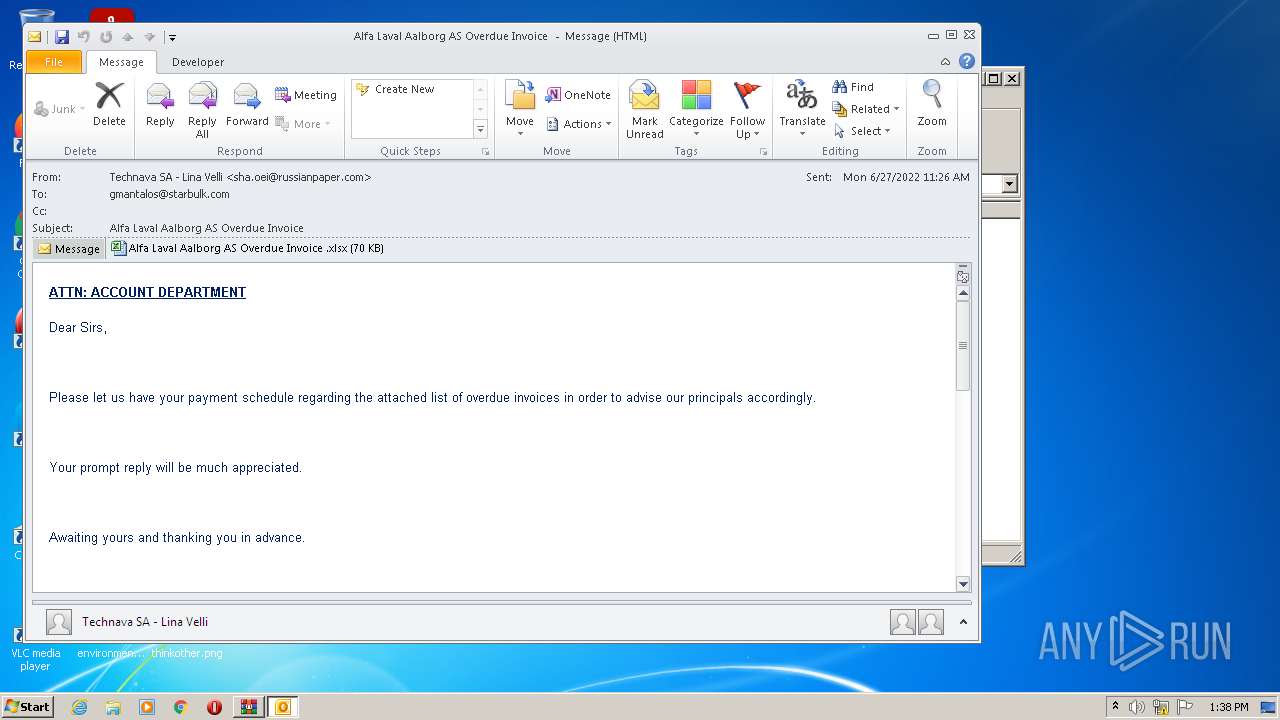
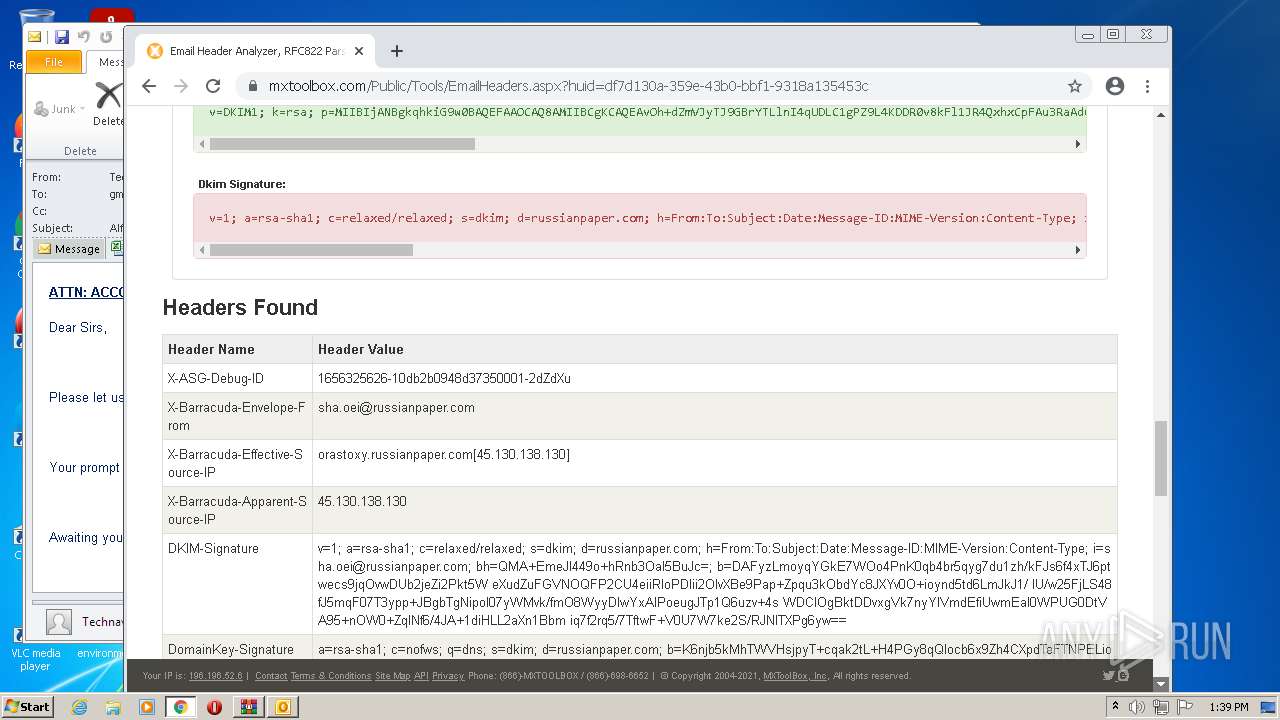
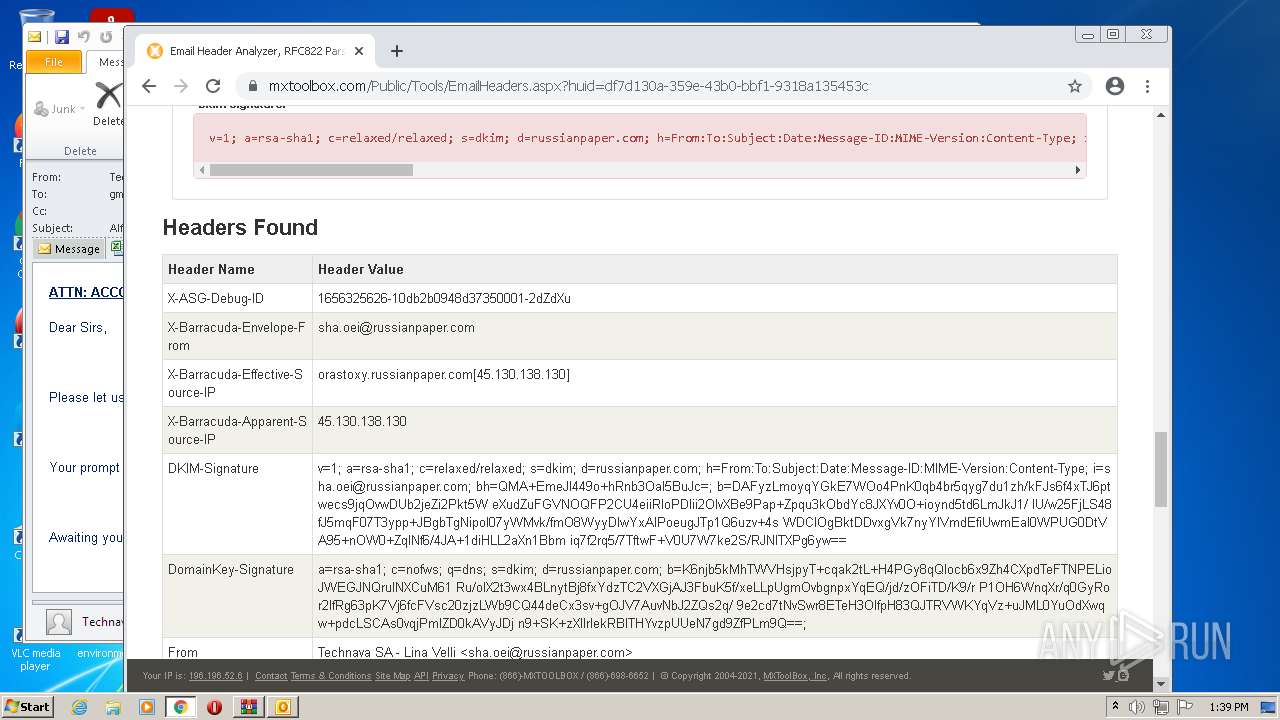
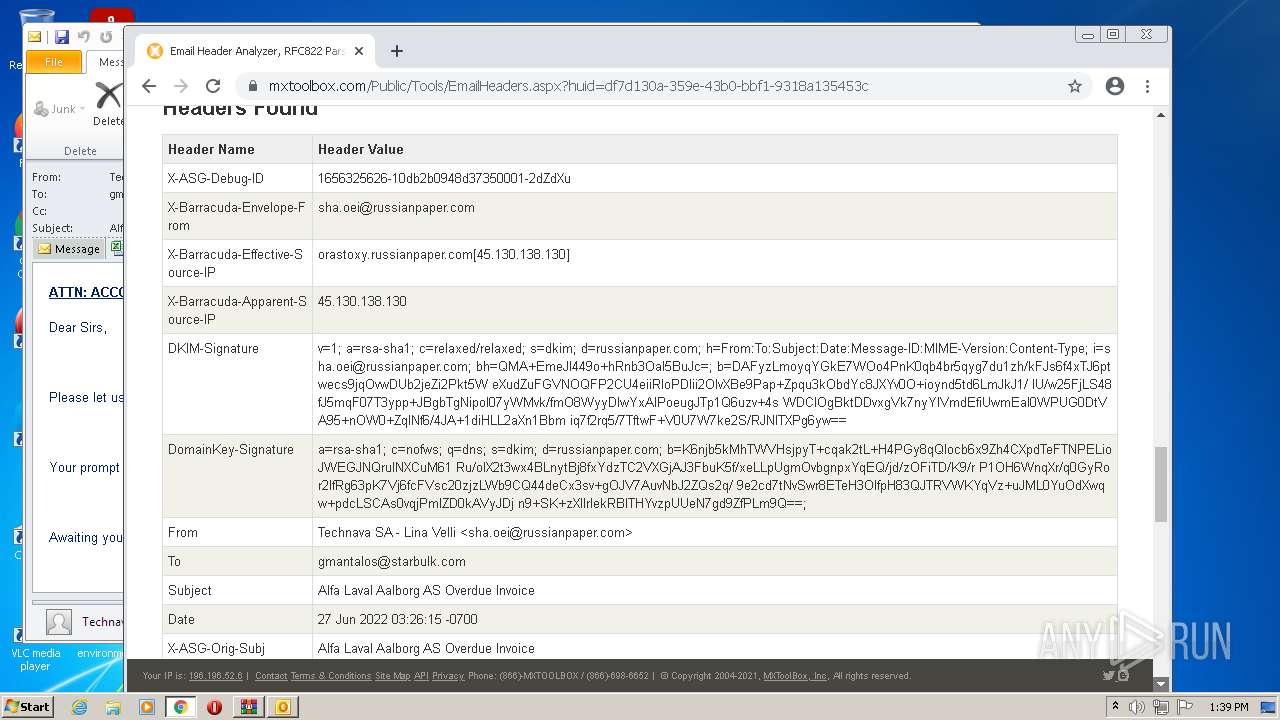
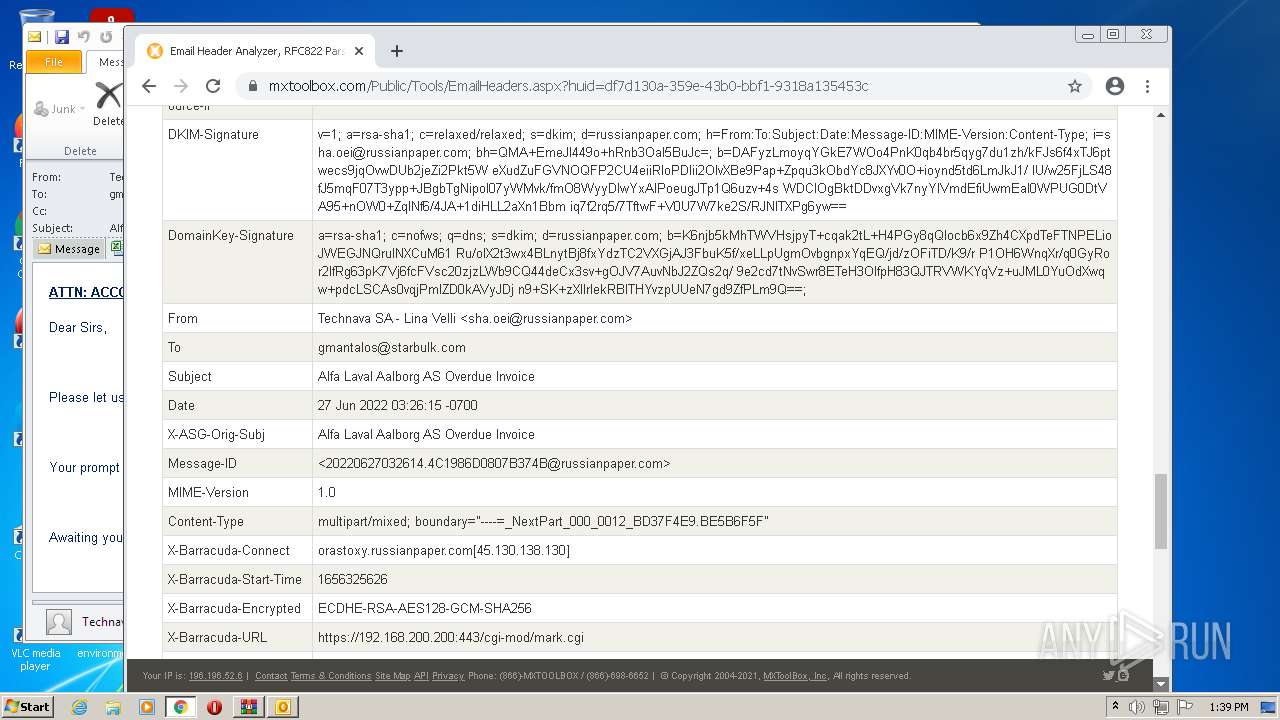
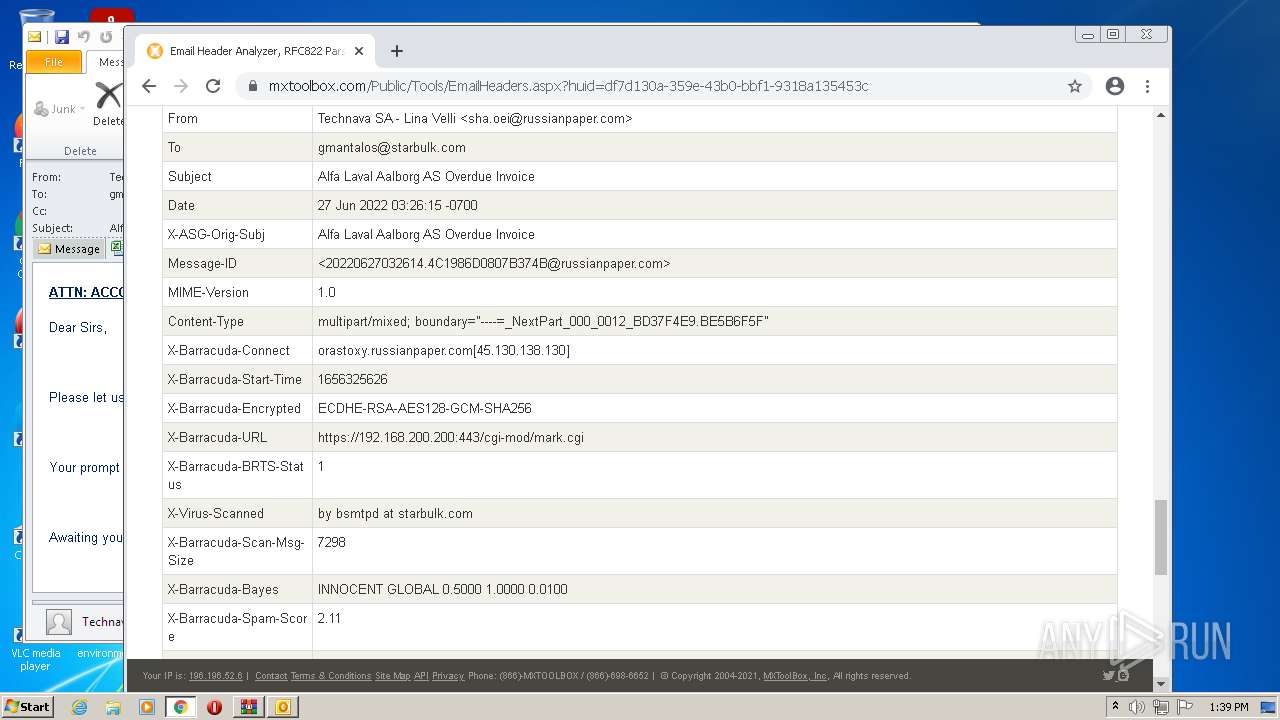
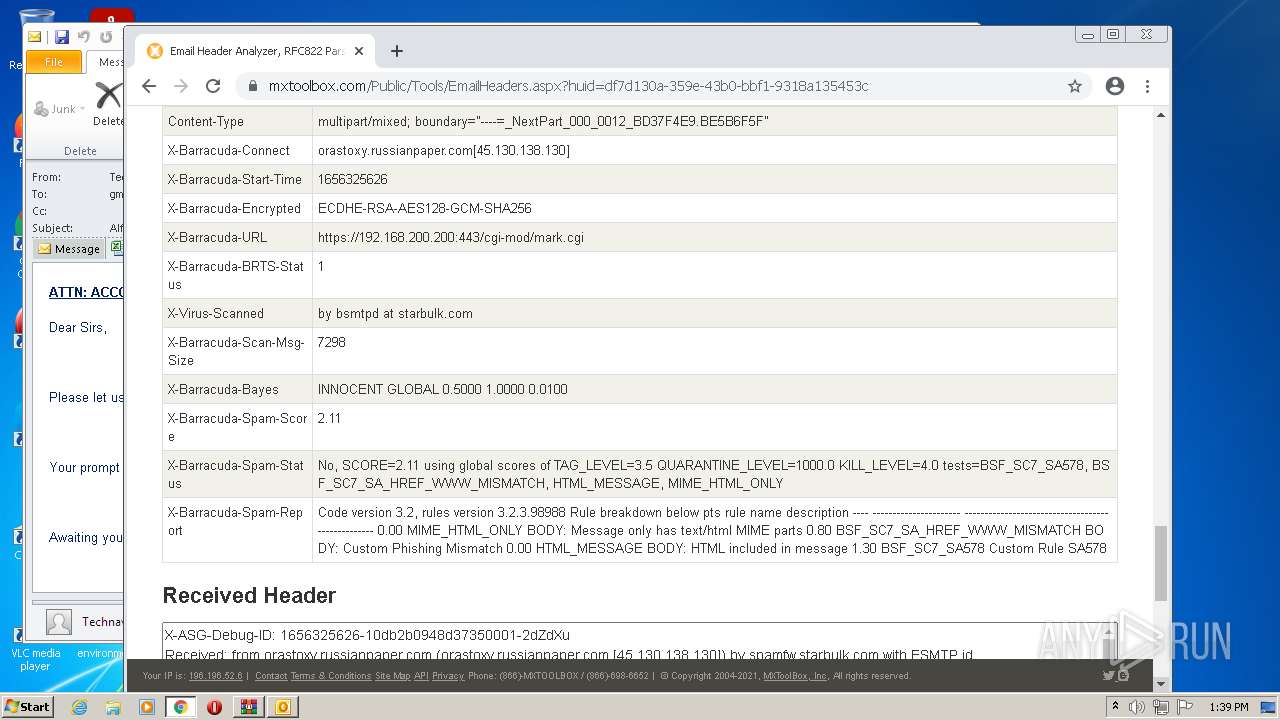
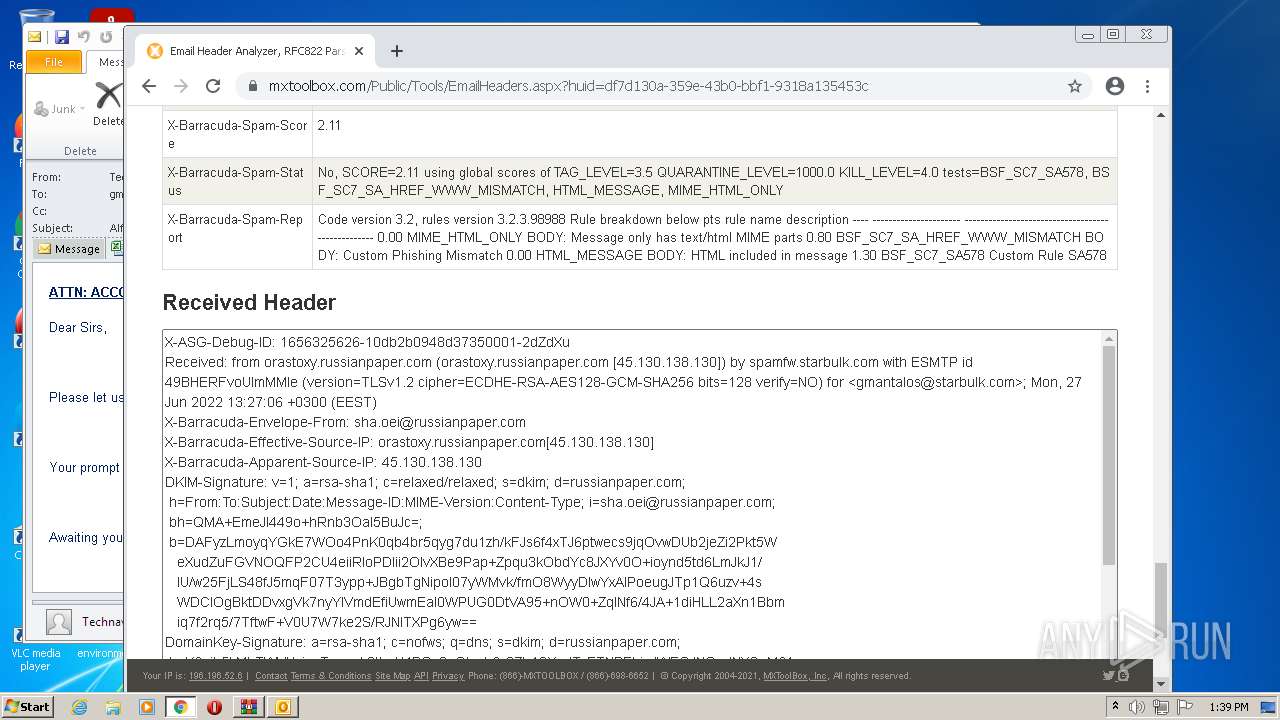
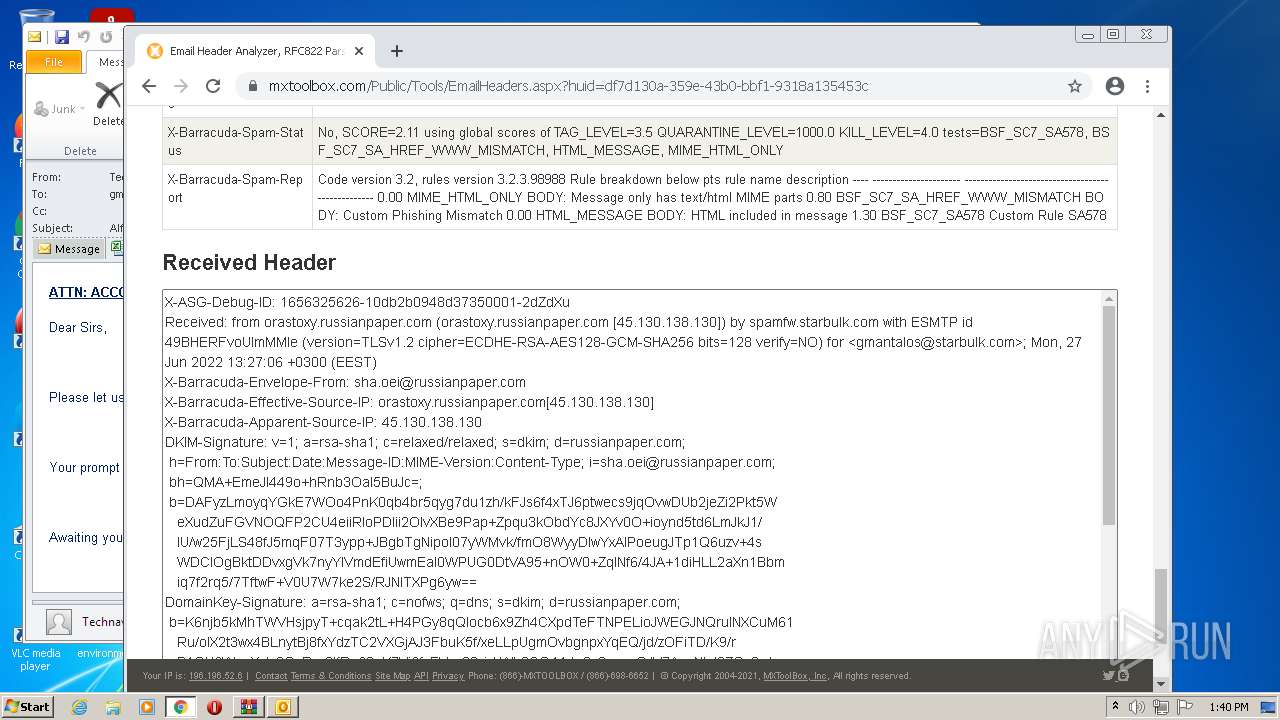
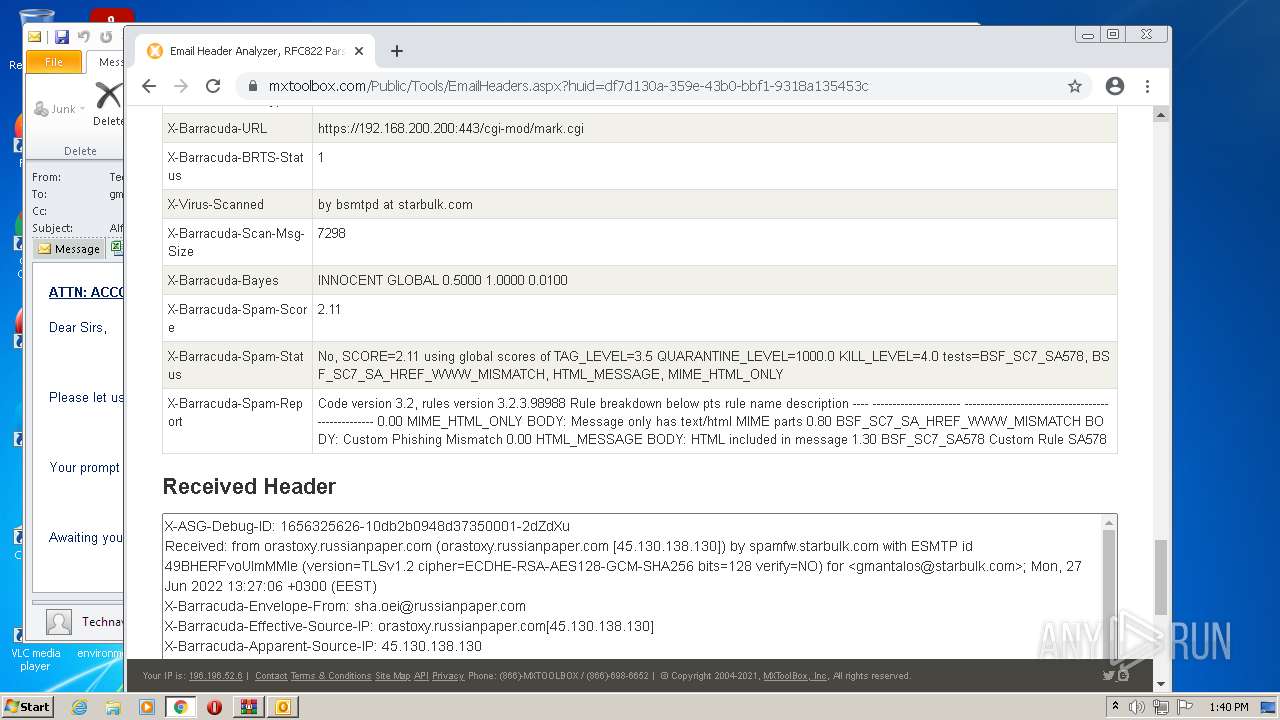
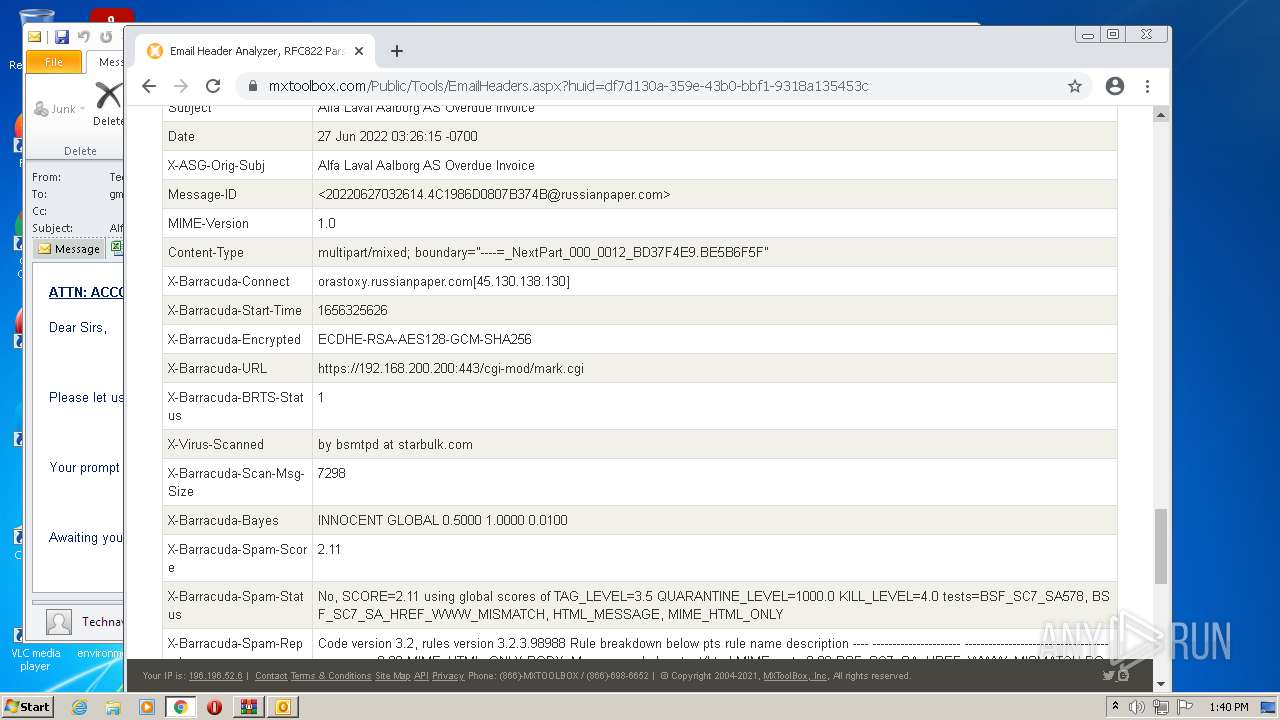
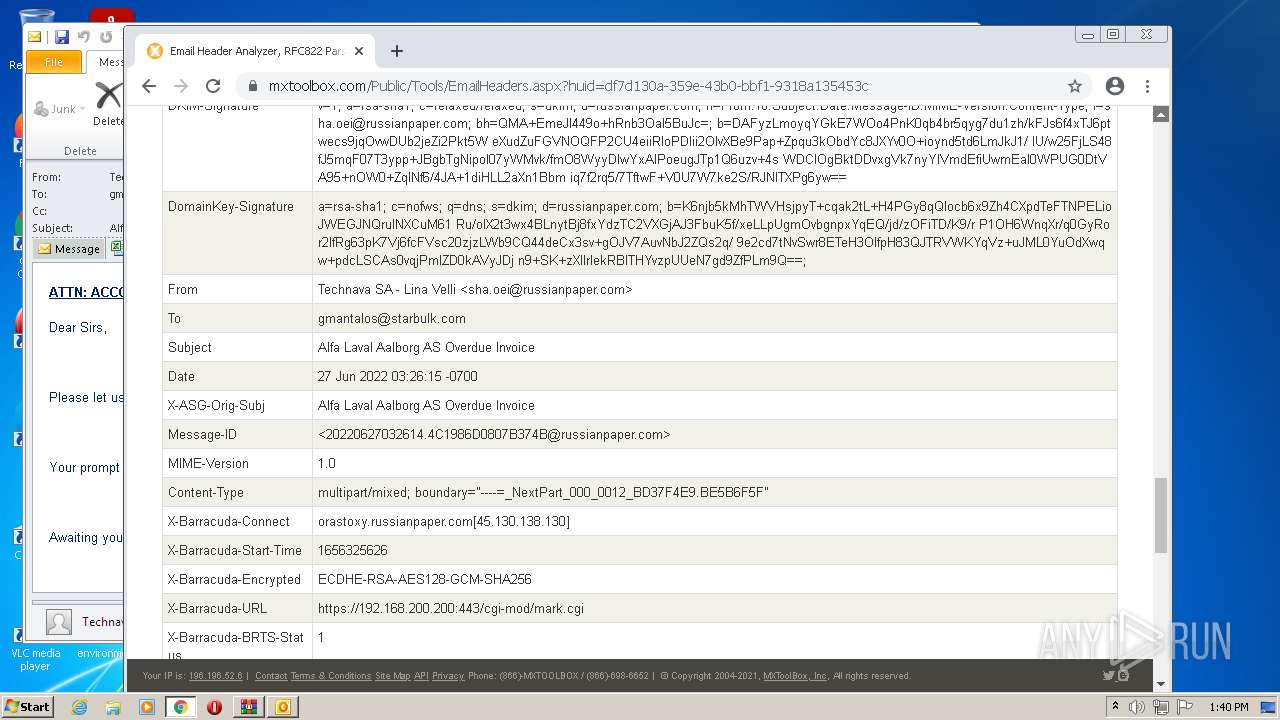
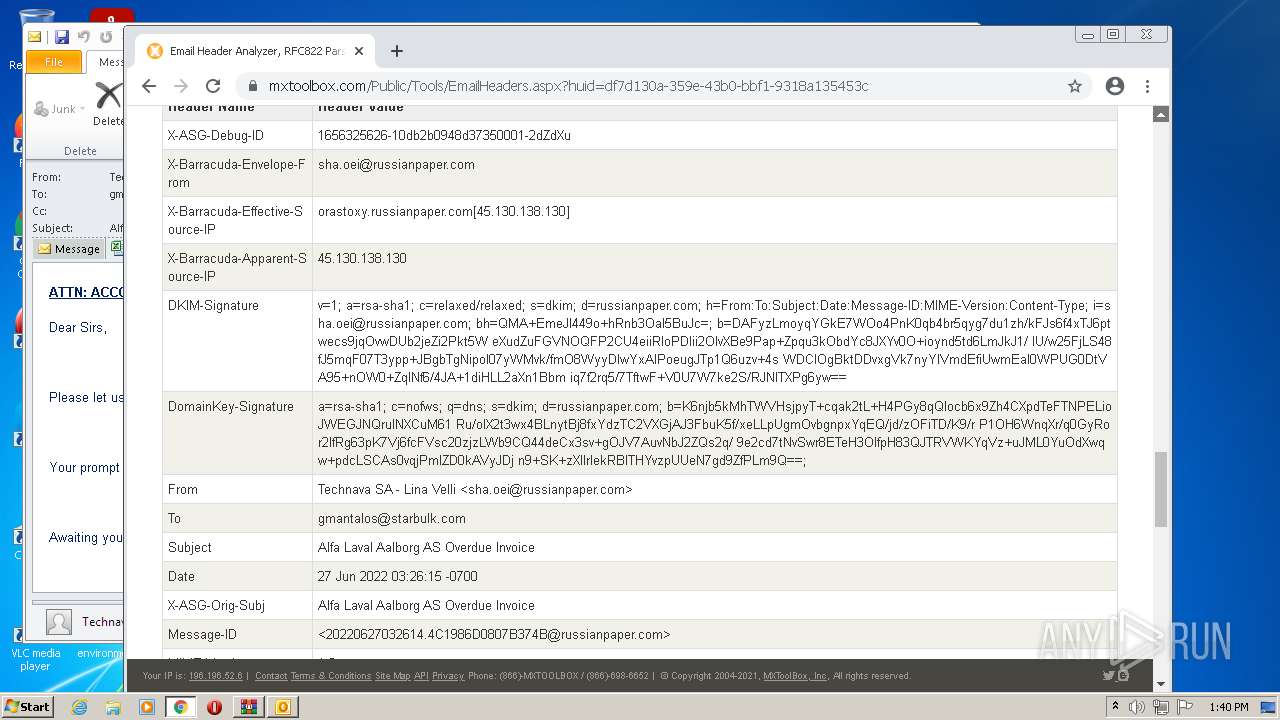
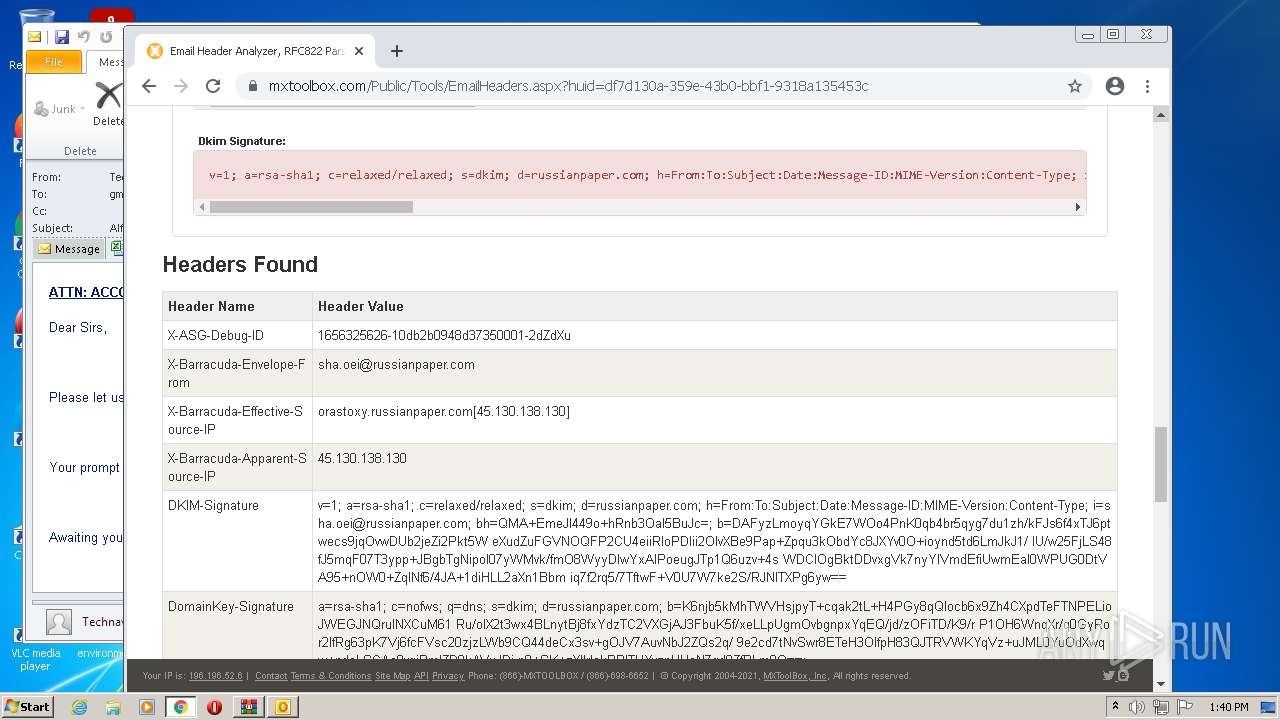
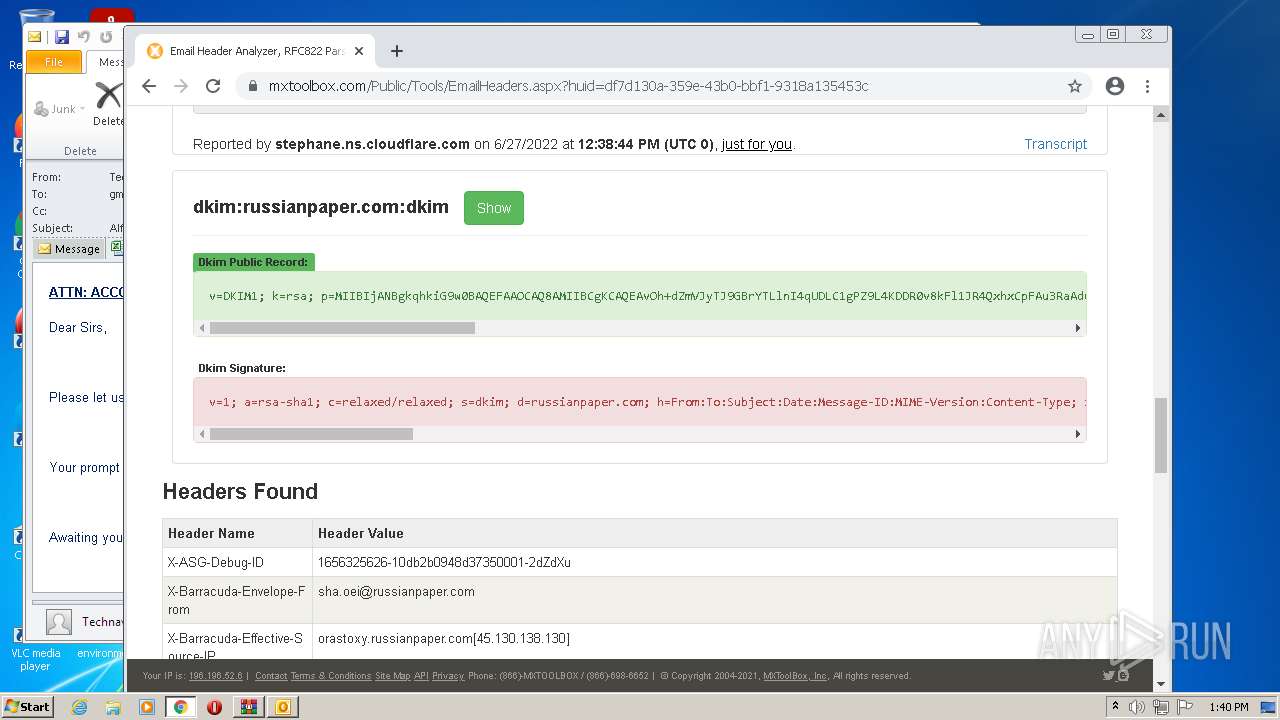
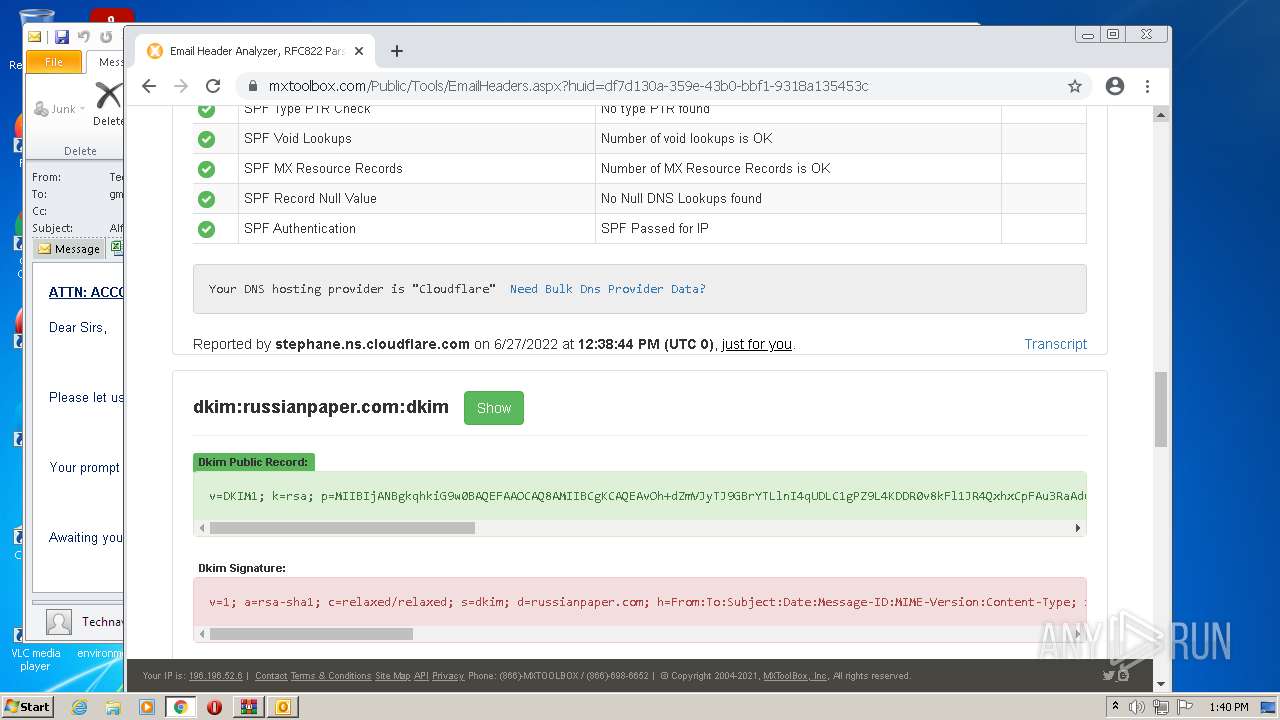
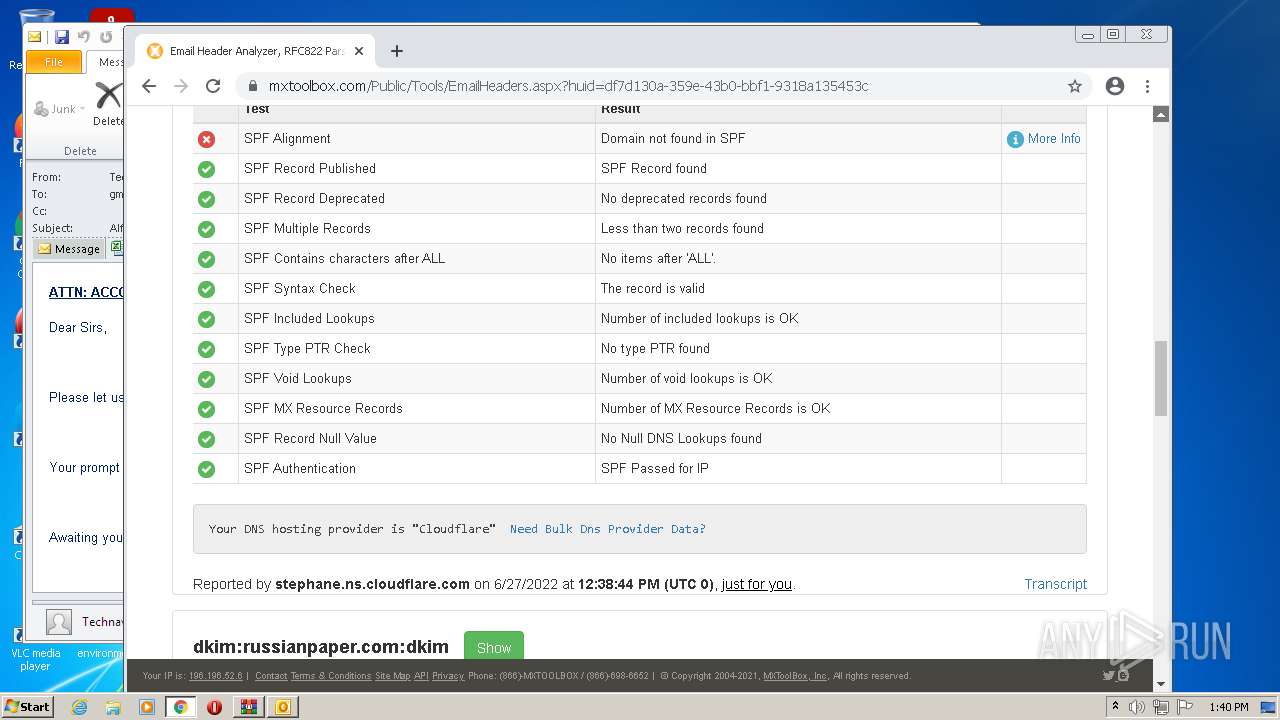
| File name: | 1656325626-10db2b0948d37350001-2dZdXu.7z |
| Full analysis: | https://app.any.run/tasks/914fcb62-c173-402c-ade8-1d26acc3bc73 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 12:38:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | F6FAE40BB2B2188BF28D81BC95EDCDB8 |
| SHA1: | DD9531DC2A4A3AB6A9CF962B0793D71319053D0C |
| SHA256: | 93856318C1F8B1E6898561228FEF7D6404CFB54682E1285BA3E6B6EFCD5F1866 |
| SSDEEP: | 3072:NPsW1WahVpuMtqwtn6Ri7oBDg+vHEQdYj37:JVAahVvgMeisvHEgYj37 |
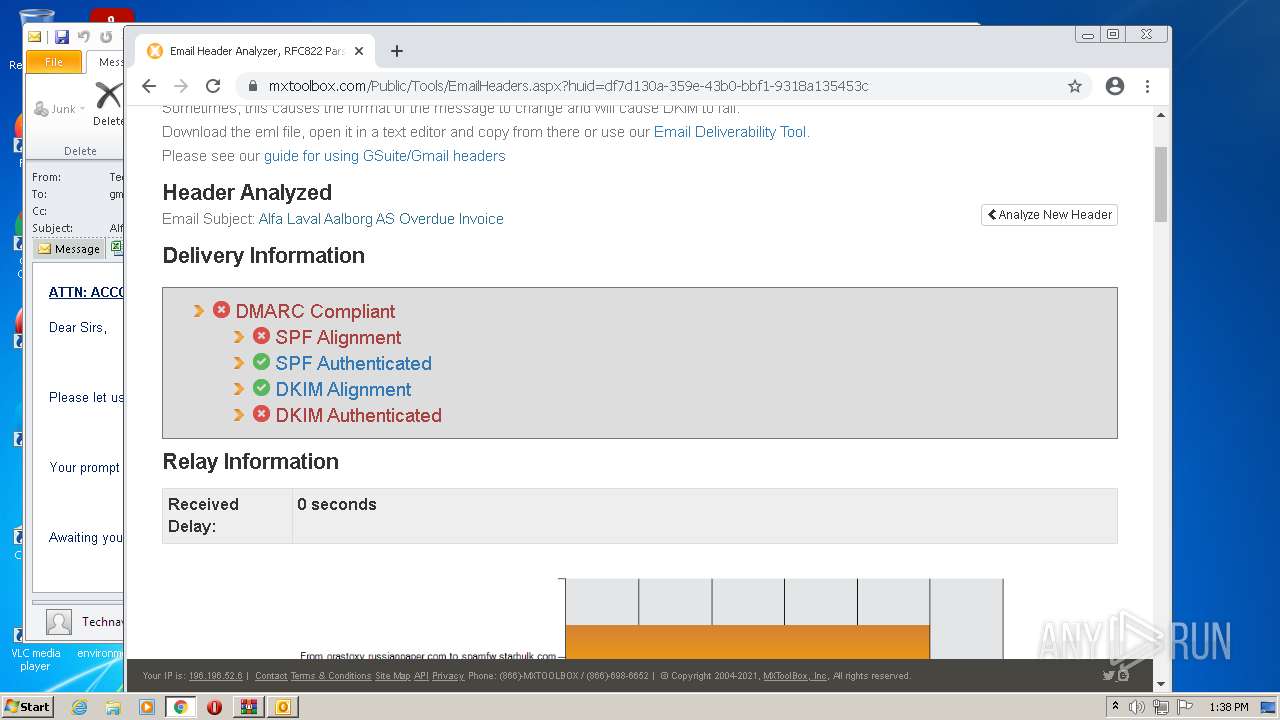
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2944)
- OUTLOOK.EXE (PID: 2776)
Reads the computer name
- WinRAR.exe (PID: 2944)
- OUTLOOK.EXE (PID: 2776)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 2944)
Searches for installed software
- OUTLOOK.EXE (PID: 2776)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2776)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2112)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2944)
Checks supported languages
- chrome.exe (PID: 2112)
- chrome.exe (PID: 2728)
- chrome.exe (PID: 3168)
- chrome.exe (PID: 3004)
- chrome.exe (PID: 3604)
- chrome.exe (PID: 3548)
- chrome.exe (PID: 3728)
- chrome.exe (PID: 2820)
- chrome.exe (PID: 3540)
- chrome.exe (PID: 2292)
- chrome.exe (PID: 3244)
- chrome.exe (PID: 3696)
- chrome.exe (PID: 2204)
- chrome.exe (PID: 3320)
- chrome.exe (PID: 4028)
- chrome.exe (PID: 3336)
- chrome.exe (PID: 1016)
- chrome.exe (PID: 2188)
- chrome.exe (PID: 1928)
- chrome.exe (PID: 2160)
- chrome.exe (PID: 3492)
- chrome.exe (PID: 996)
- chrome.exe (PID: 3340)
- chrome.exe (PID: 1828)
- chrome.exe (PID: 1768)
Reads the hosts file
- chrome.exe (PID: 2112)
- chrome.exe (PID: 3168)
Manual execution by user
- chrome.exe (PID: 2112)
Reads the computer name
- chrome.exe (PID: 2112)
- chrome.exe (PID: 3168)
- chrome.exe (PID: 2728)
- chrome.exe (PID: 3540)
- chrome.exe (PID: 3336)
- chrome.exe (PID: 2160)
- chrome.exe (PID: 3492)
- chrome.exe (PID: 1828)
Application launched itself
- chrome.exe (PID: 2112)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2776)
Reads settings of System Certificates
- chrome.exe (PID: 3168)
Reads the date of Windows installation
- chrome.exe (PID: 3492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
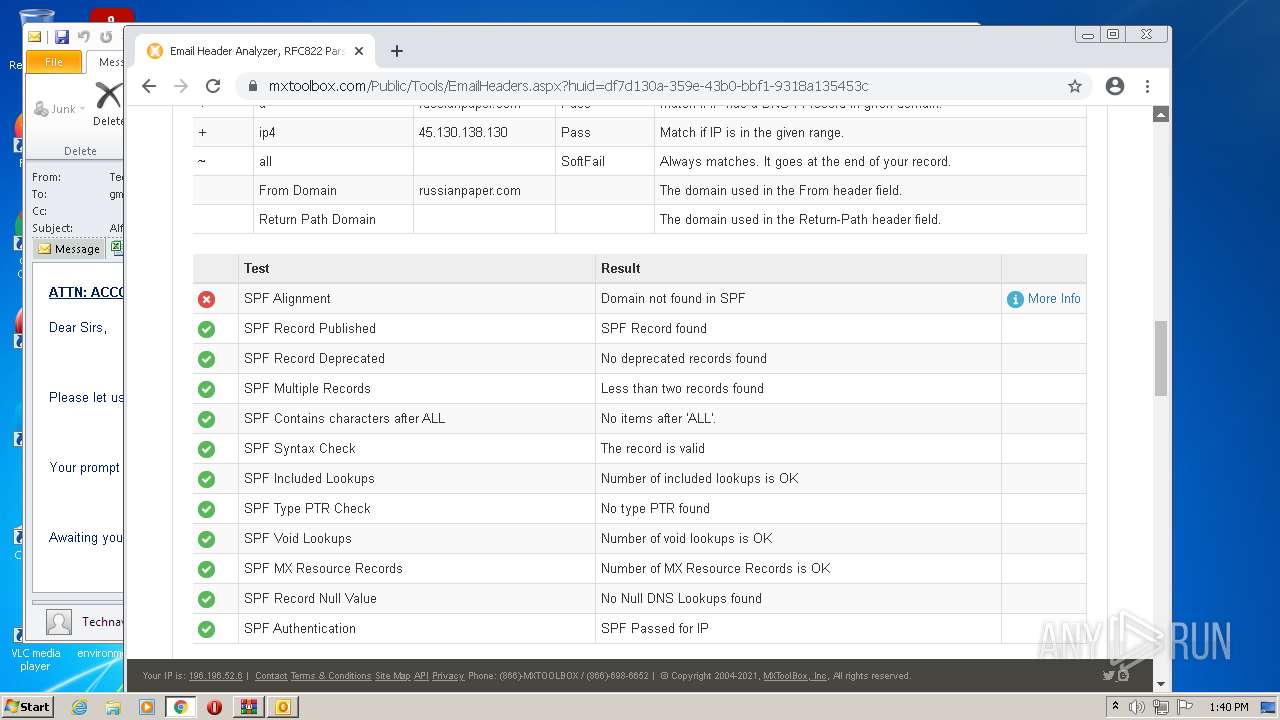
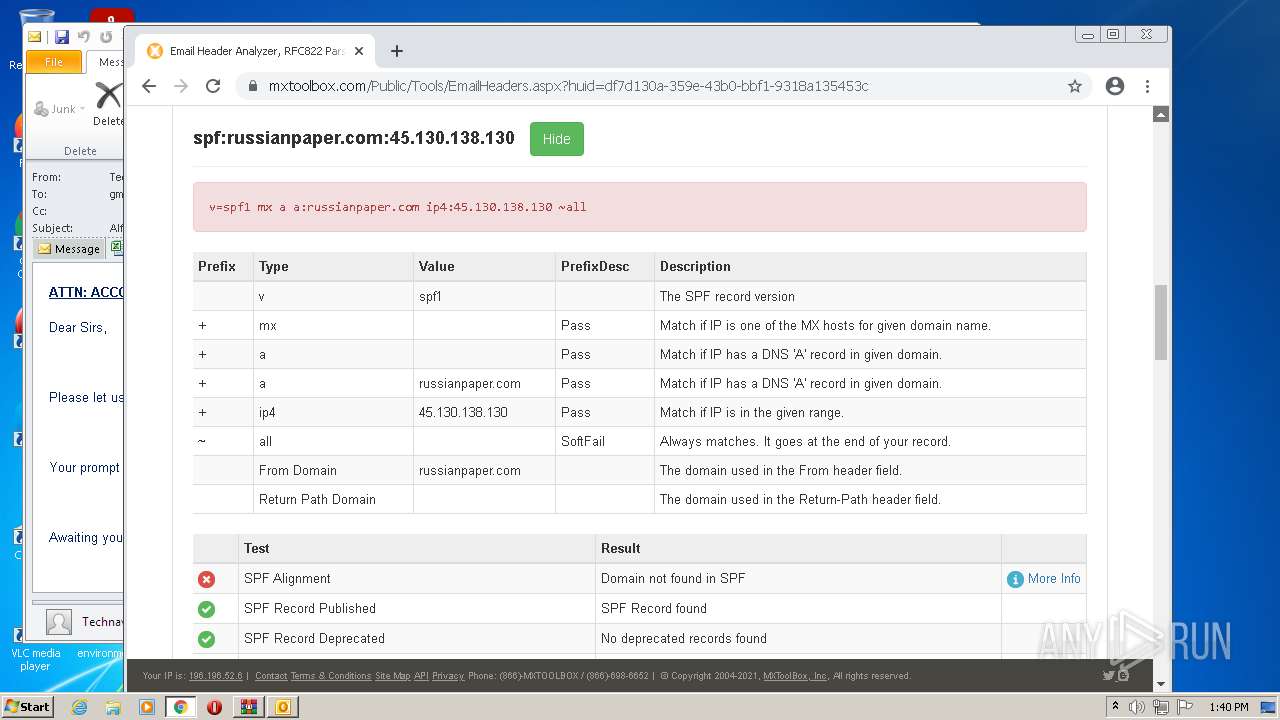
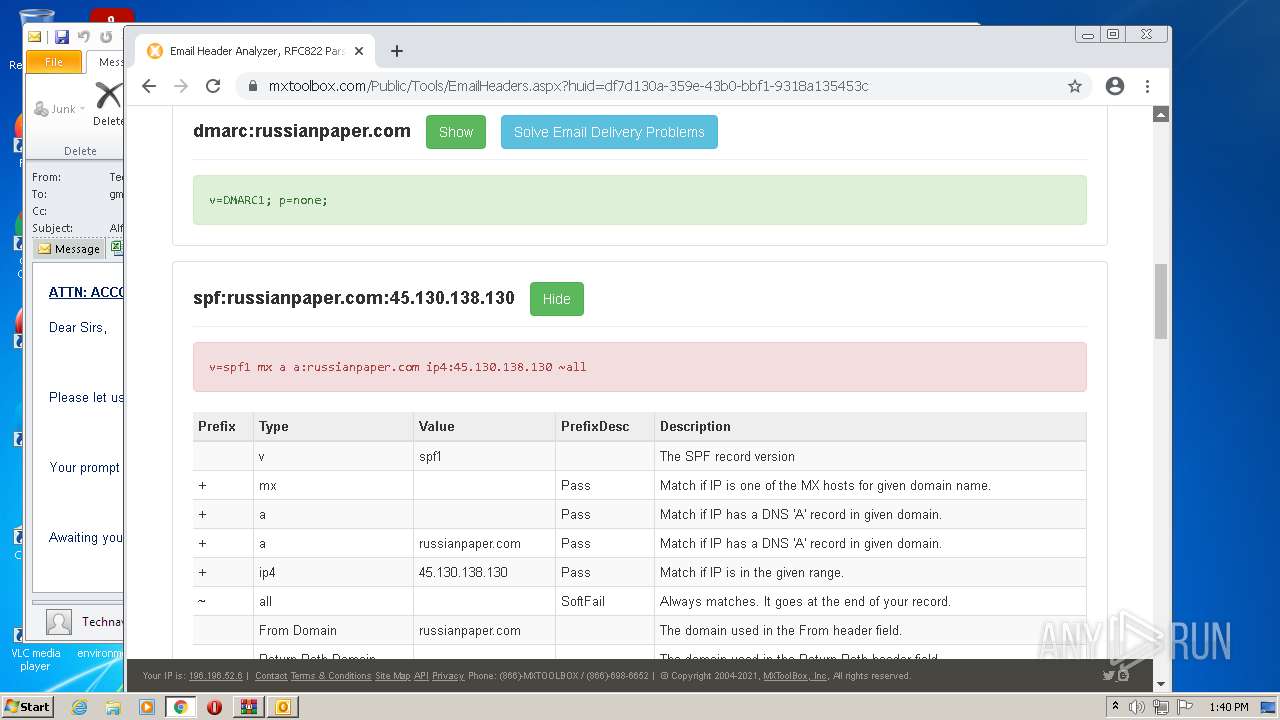
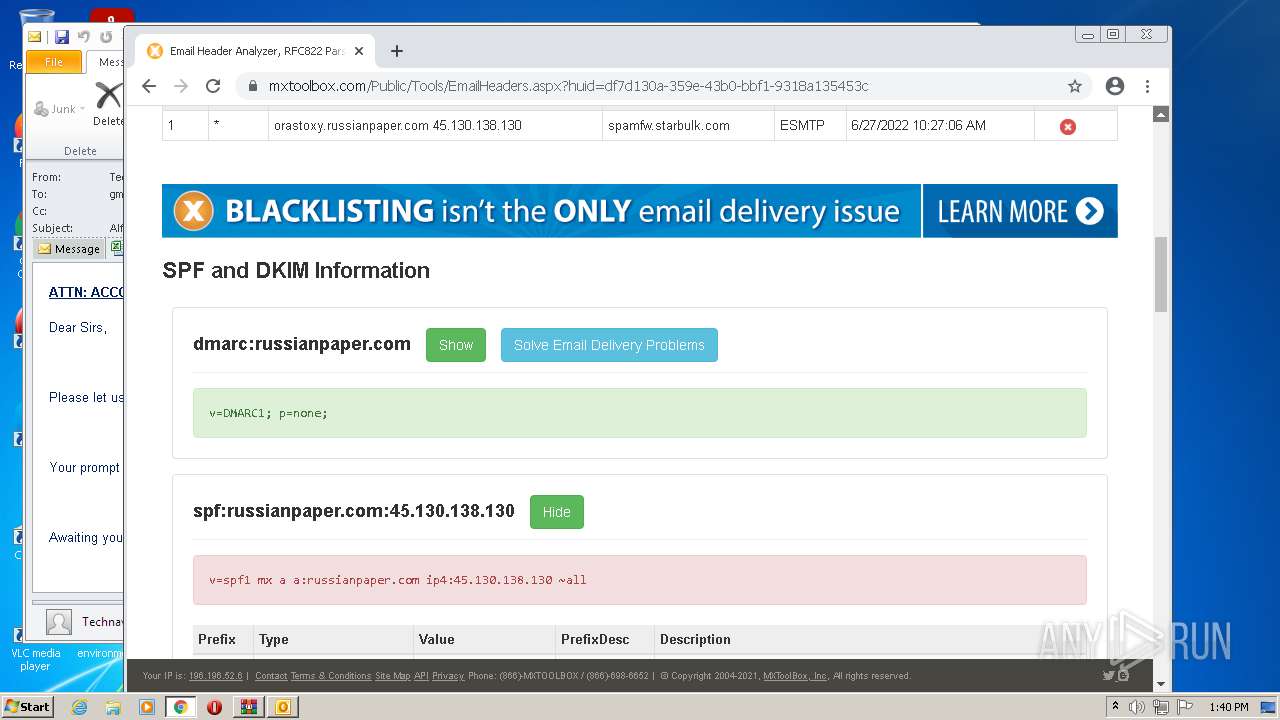
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
65
Monitored processes
27
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1072,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2796 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1072,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3420 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1072,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2628 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1072,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3884 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1072,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2924 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2112 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2160 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1072,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3856 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1072,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3404 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1072,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3604 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1072,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2964 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
17 145
Read events
16 410
Write events
708
Delete events
27
Modification events
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1656325626-10db2b0948d37350001-2dZdXu.7z | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
165
Text files
135
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2776 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR6A45.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2776 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2112 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-62B9A4BE-840.pma | — | |
MD5:— | SHA256:— | |||
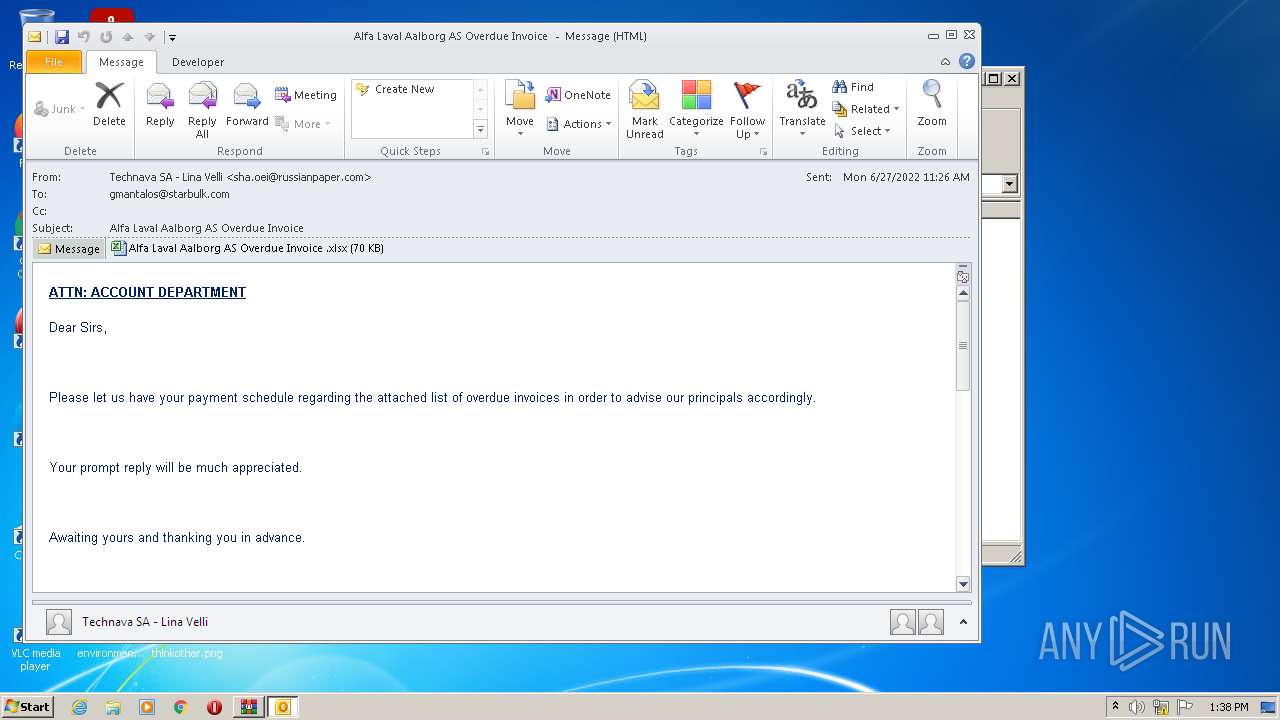
| 2944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2944.14457\1656325626-10db2b0948d37350001-2dZdXu.eml | html | |
MD5:— | SHA256:— | |||
| 2776 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\C13BC488.dat | image | |
MD5:— | SHA256:— | |||
| 2776 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2776 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2776 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{65188434-416E-4C03-A5B8-767B7E9711E1}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 2776 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_4301C19CA1991C4F8A2DF2A7DE7E6BF1.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 2776 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
81
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2776 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
— | — | HEAD | 302 | 142.251.37.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
— | — | HEAD | 200 | 173.194.150.220:80 | http://r6---sn-5goeen7r.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3?cms_redirect=yes&mh=VX&mip=196.196.52.6&mm=28&mn=sn-5goeen7r&ms=nvh&mt=1656333151&mv=m&mvi=6&pl=24&rmhost=r3---sn-5goeen7r.gvt1.com&shardbypass=sd&smhost=r1---sn-5goeenez.gvt1.com | US | — | — | whitelisted |
— | — | GET | 302 | 142.251.37.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | html | 610 b | whitelisted |
— | — | GET | 302 | 142.251.37.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | html | 610 b | whitelisted |
3168 | chrome.exe | GET | 302 | 172.217.18.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 591 b | whitelisted |
— | — | GET | 302 | 142.251.37.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | html | 610 b | whitelisted |
— | — | GET | 302 | 142.251.37.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | html | 610 b | whitelisted |
— | — | GET | 302 | 142.251.37.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | html | 610 b | whitelisted |
3168 | chrome.exe | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d67ae17bff976f8d | US | compressed | 60.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3168 | chrome.exe | 142.250.186.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2776 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3168 | chrome.exe | 142.250.184.238:443 | clients2.google.com | Google Inc. | US | whitelisted |
3168 | chrome.exe | 142.250.185.225:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
3168 | chrome.exe | 142.250.186.164:443 | www.google.com | Google Inc. | US | whitelisted |
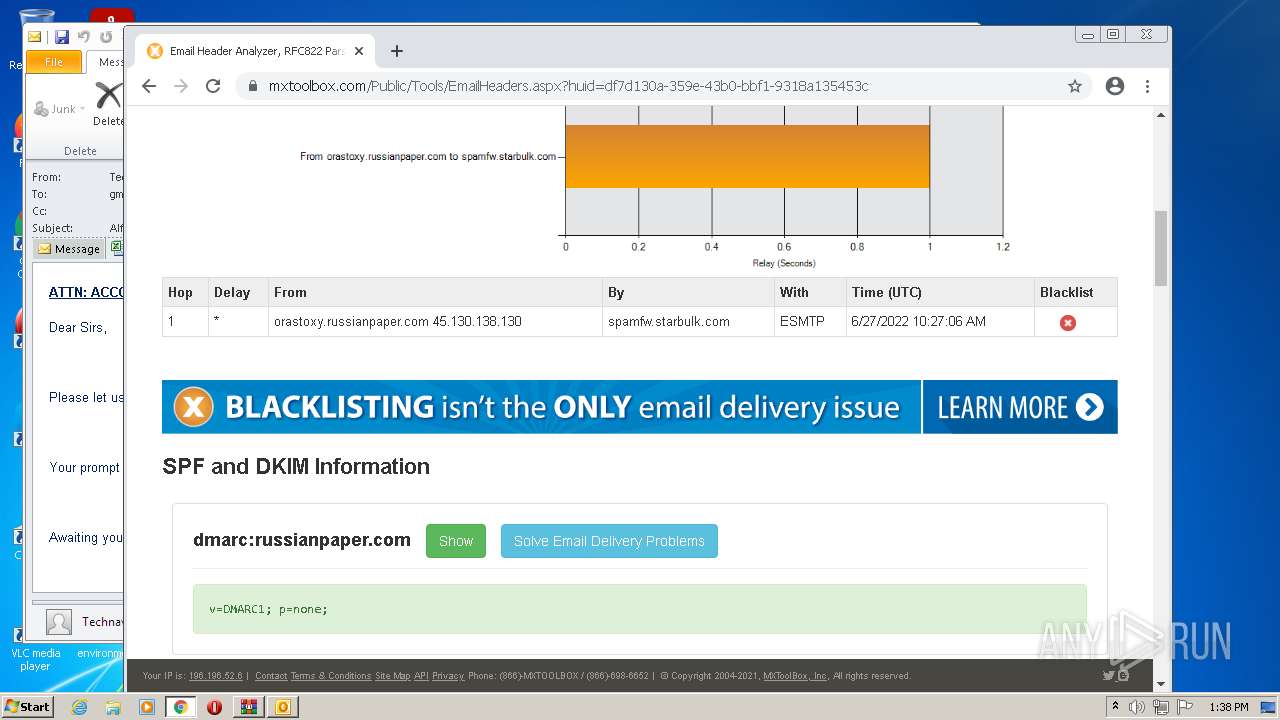
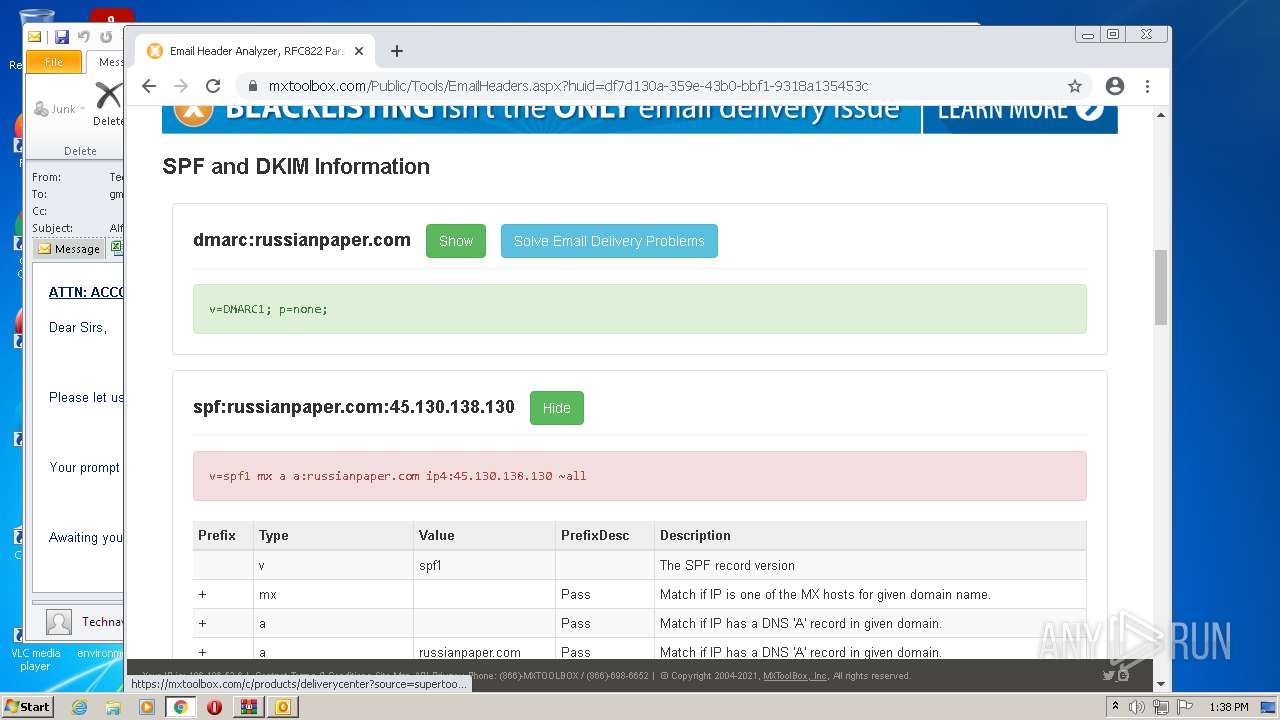
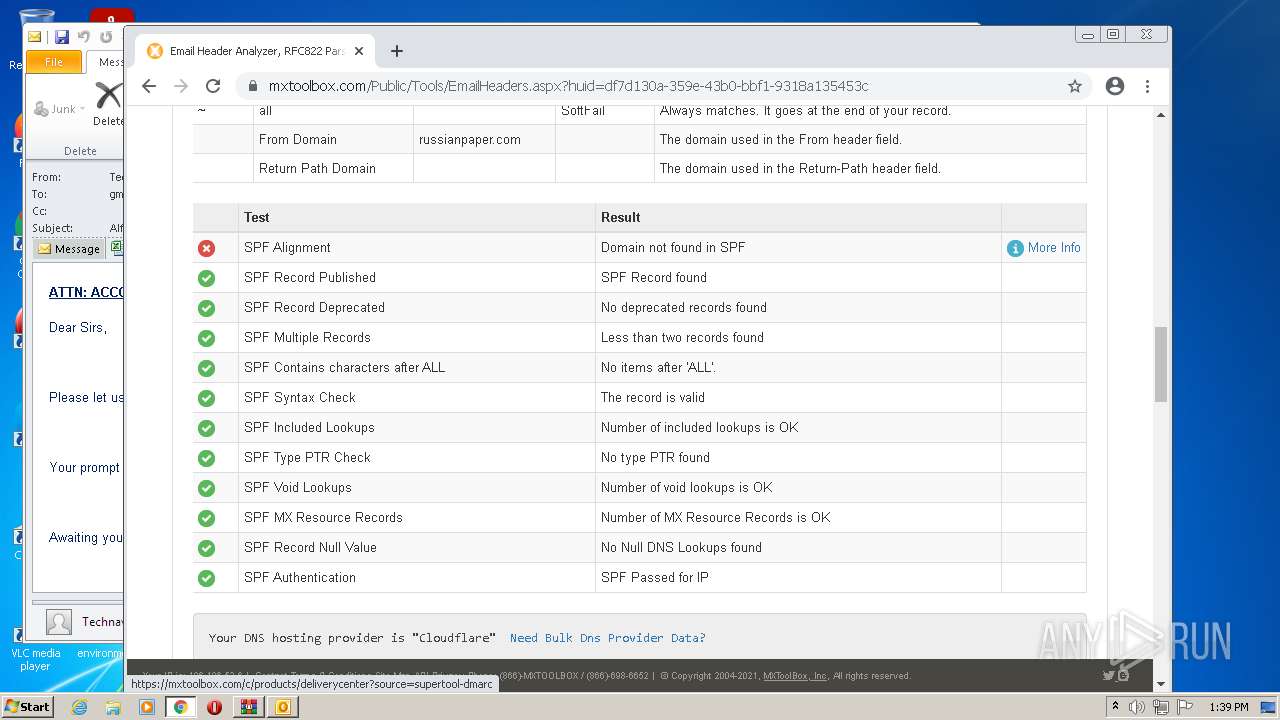
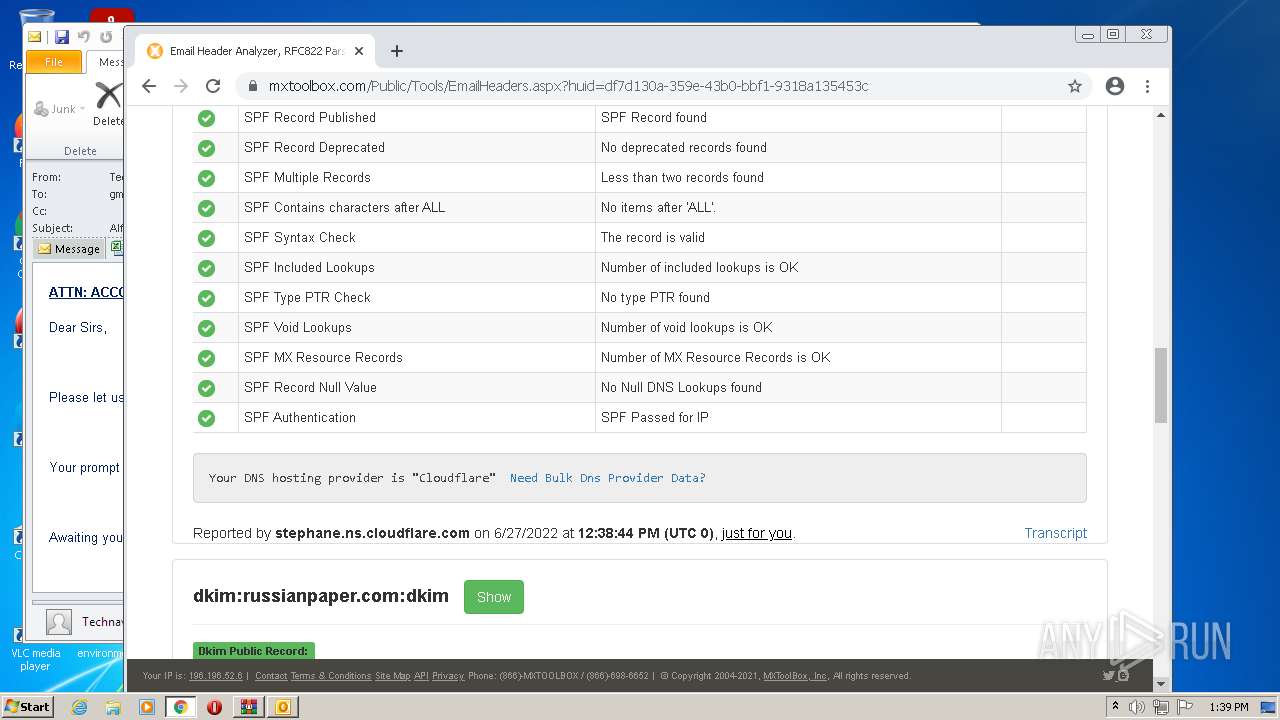
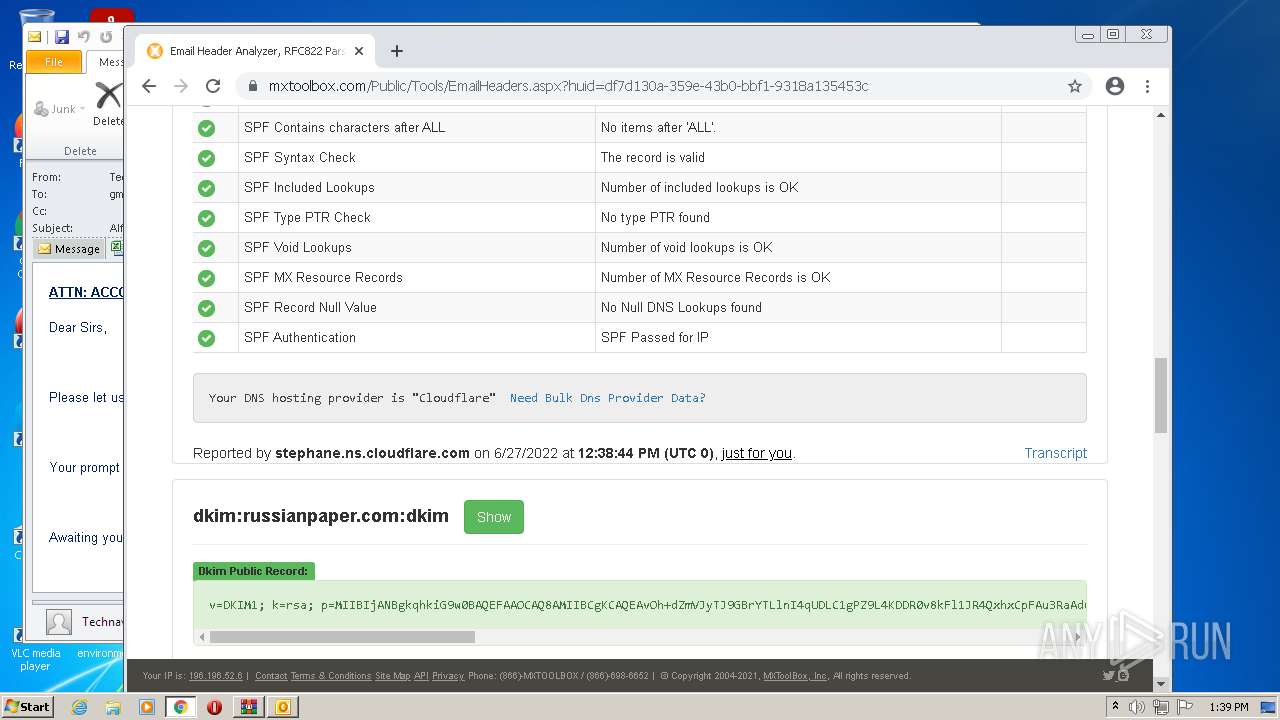
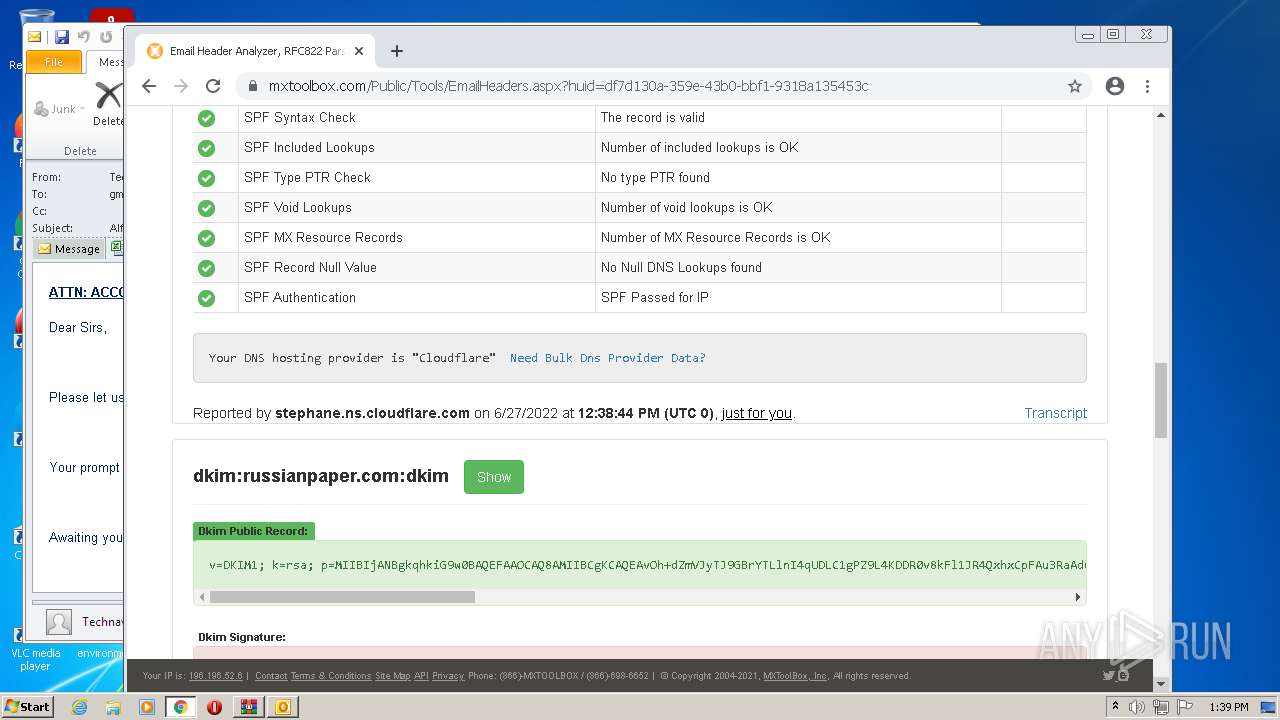
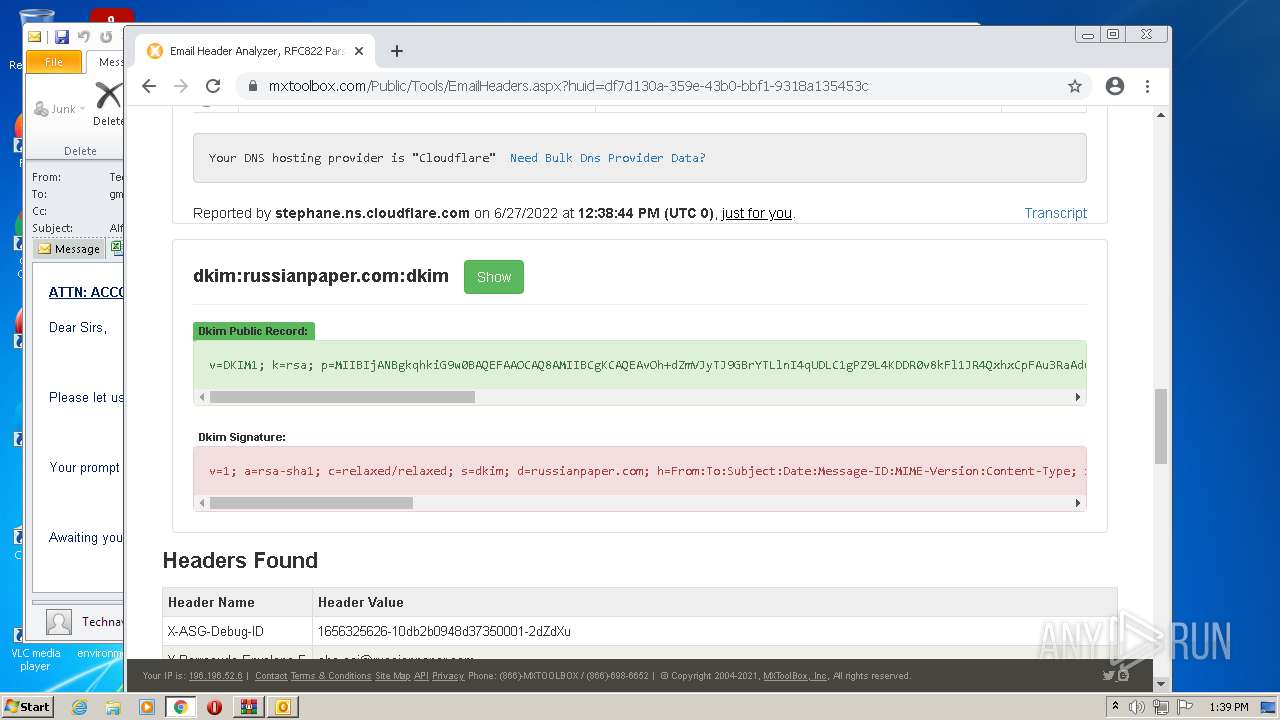
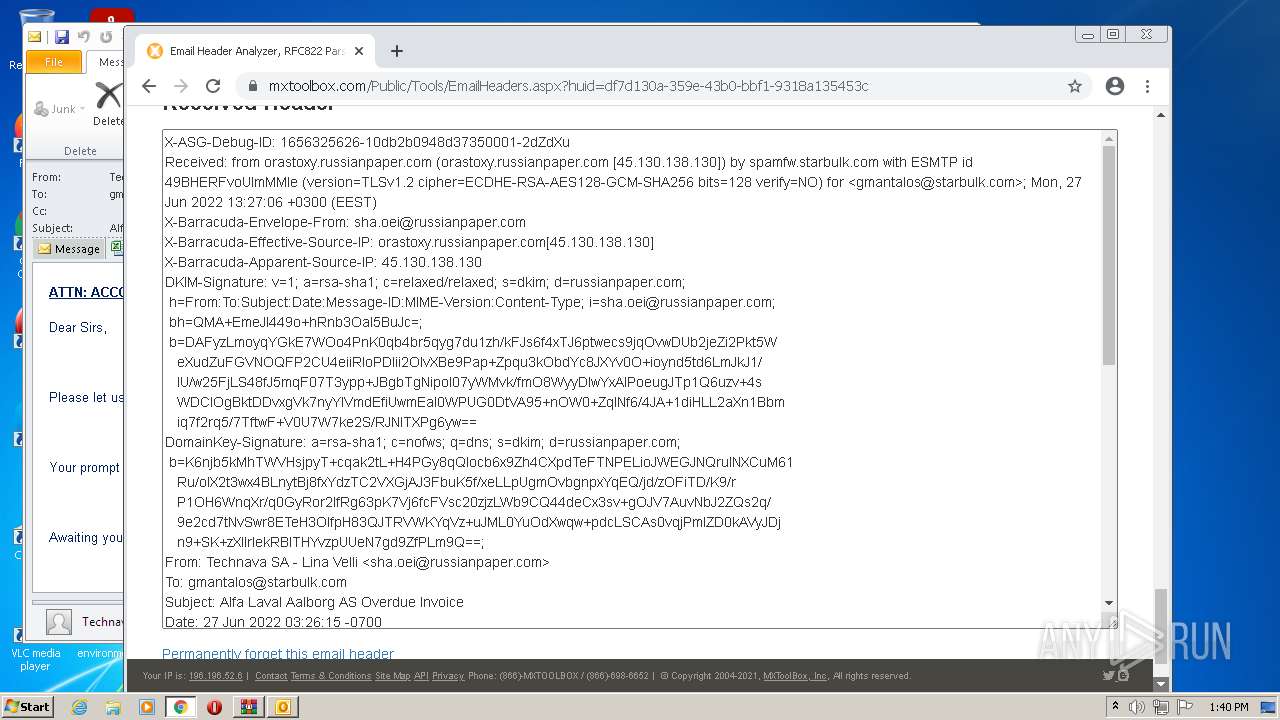
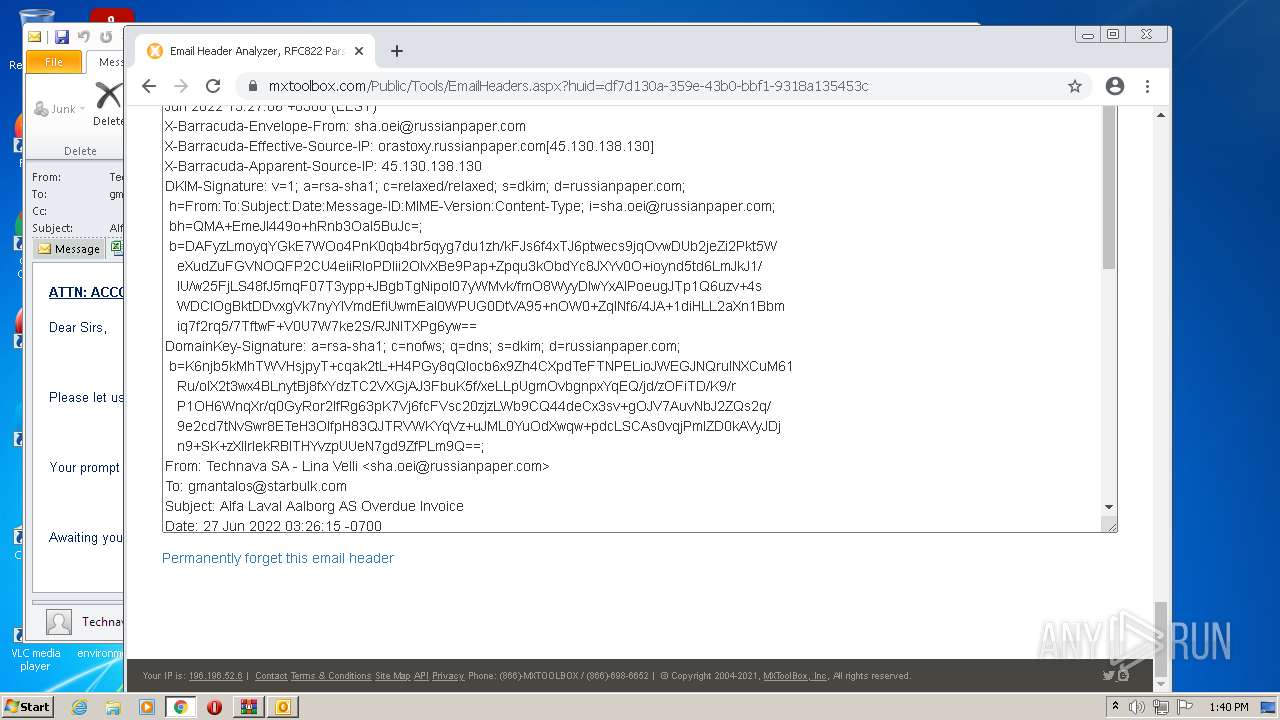
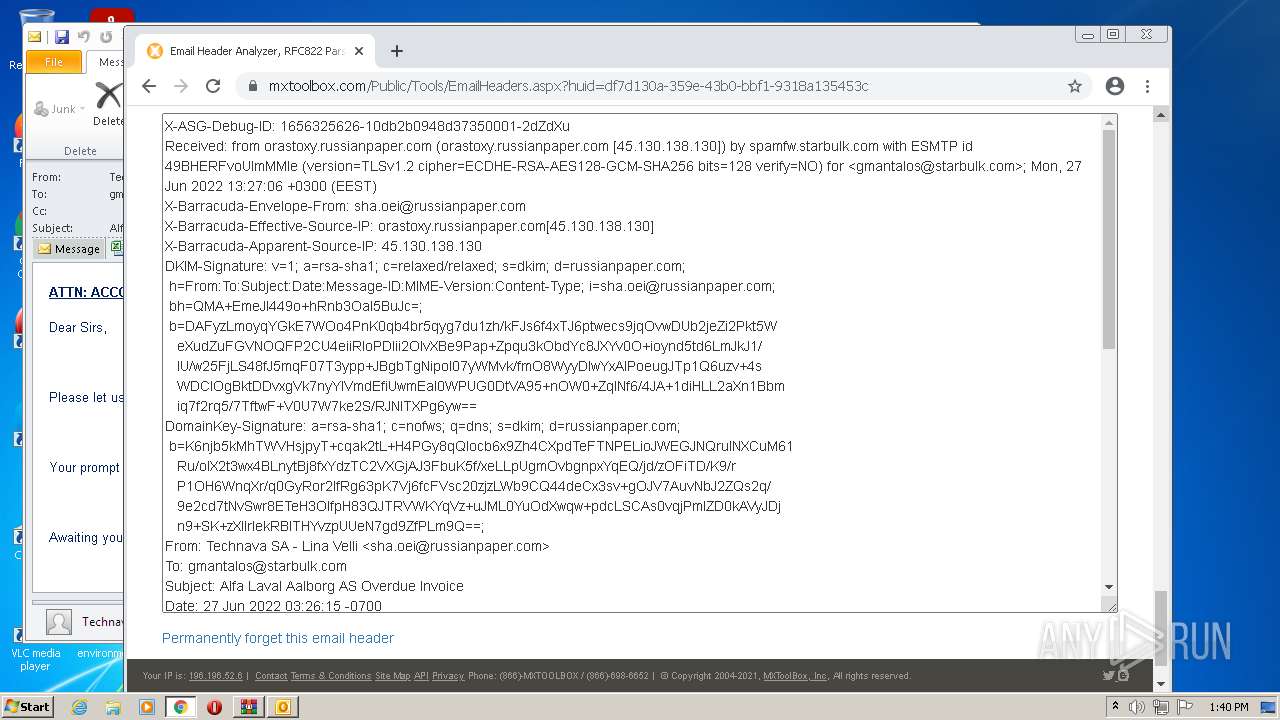
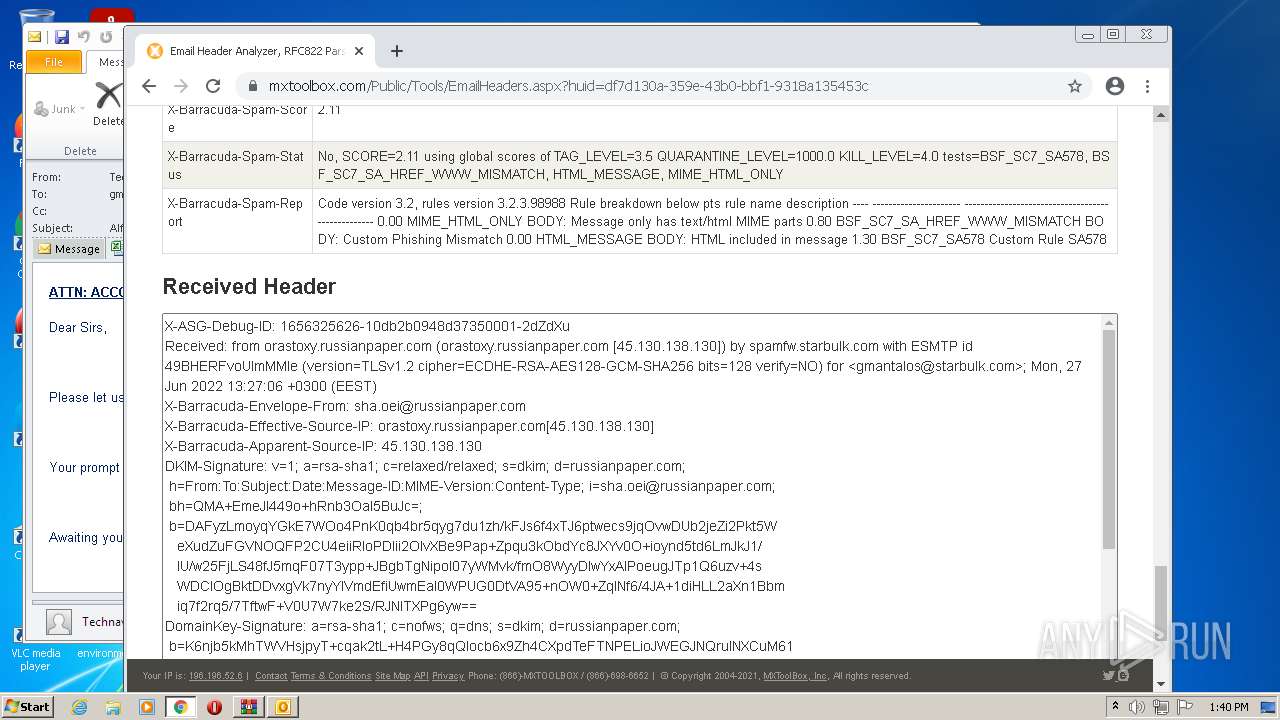
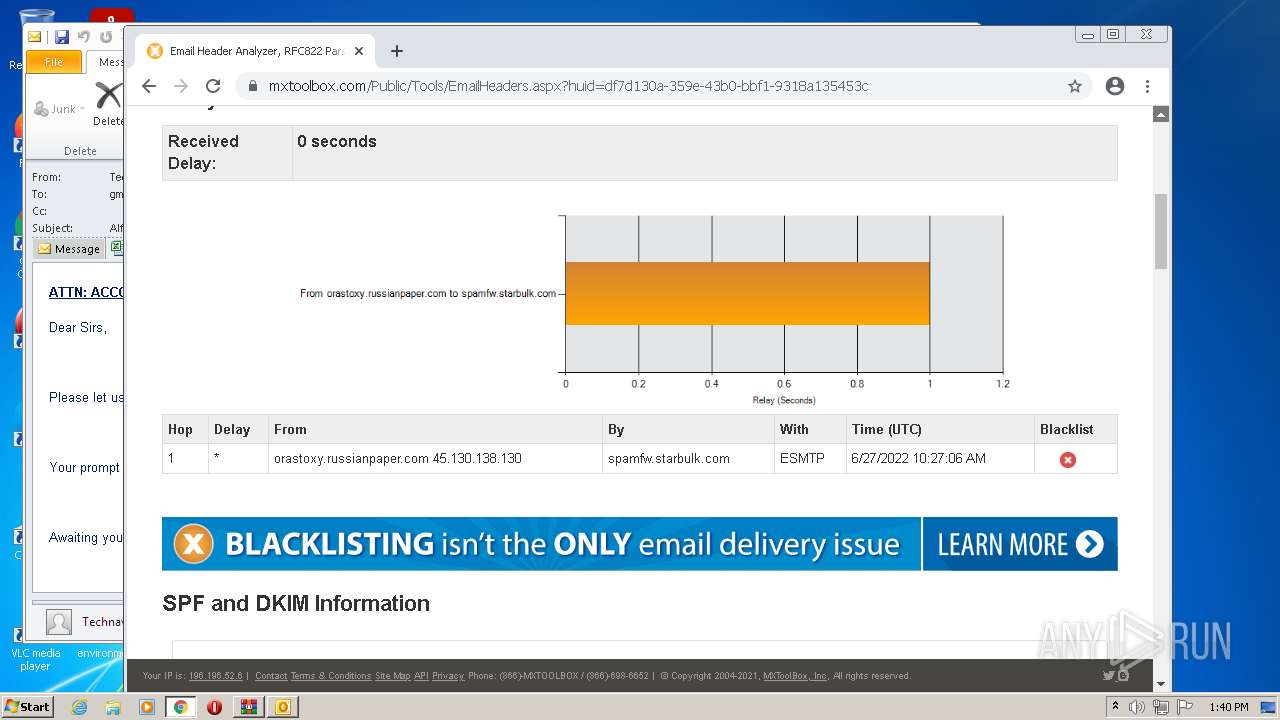
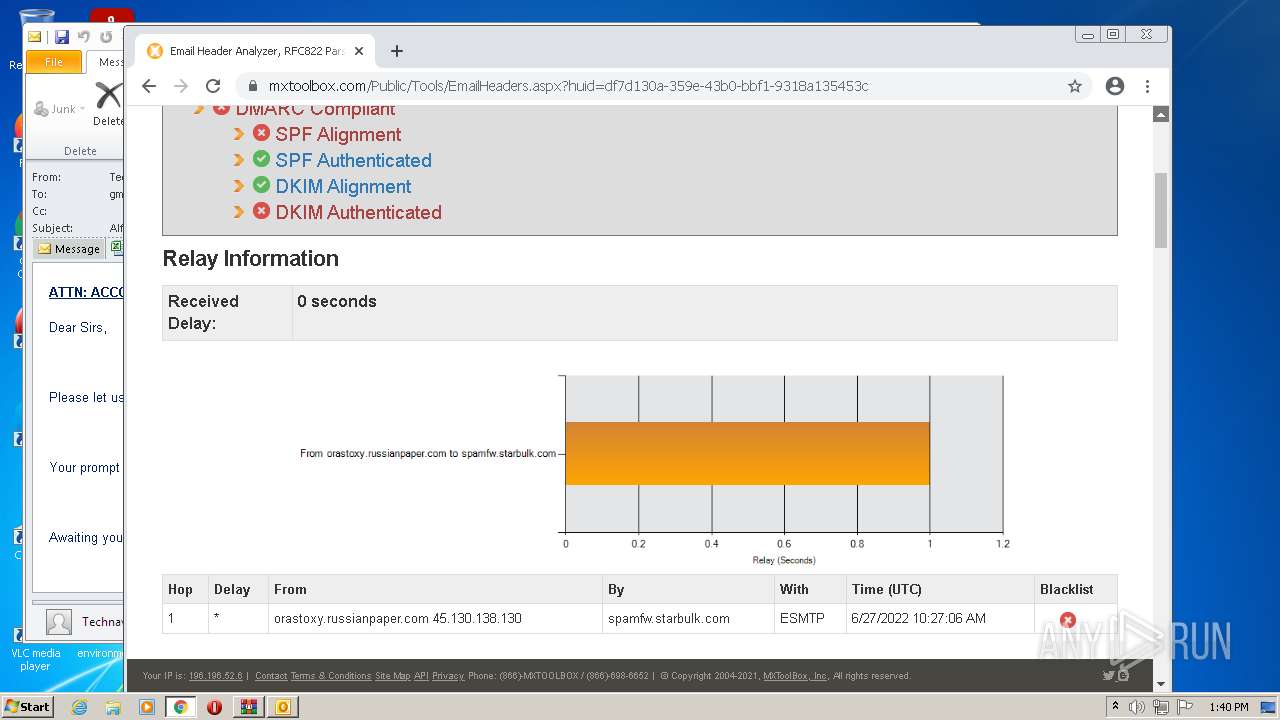
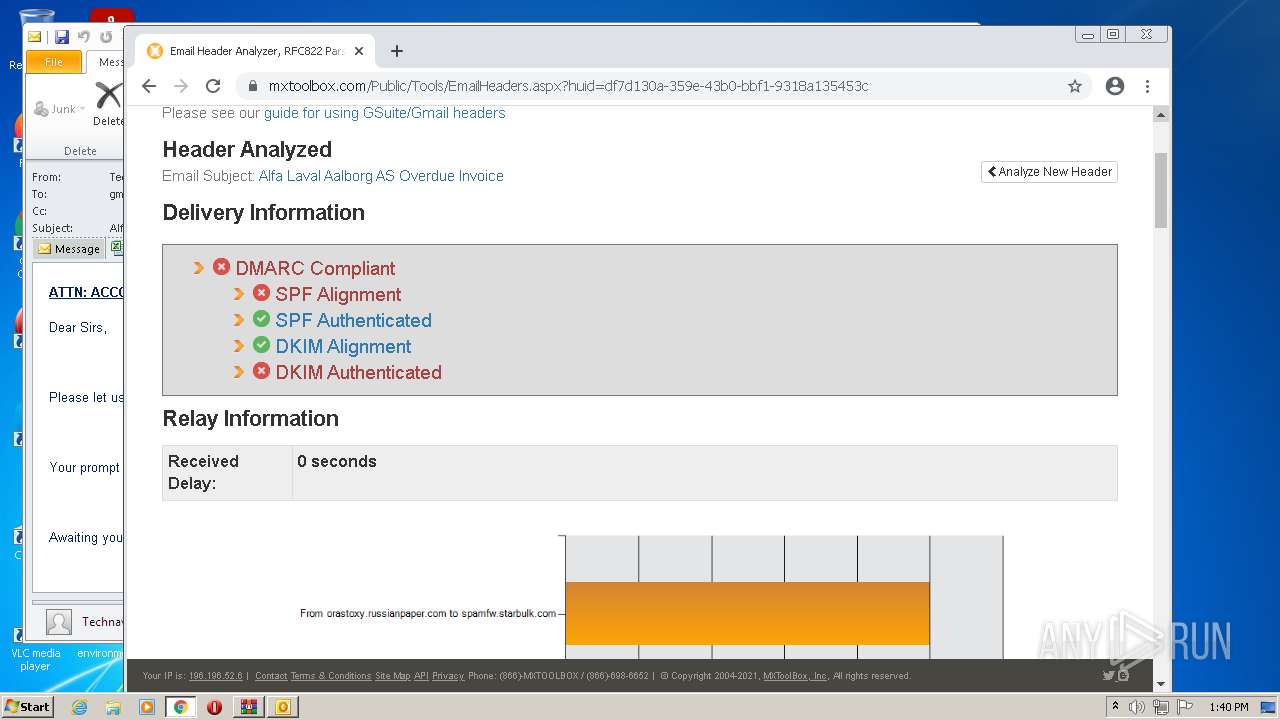
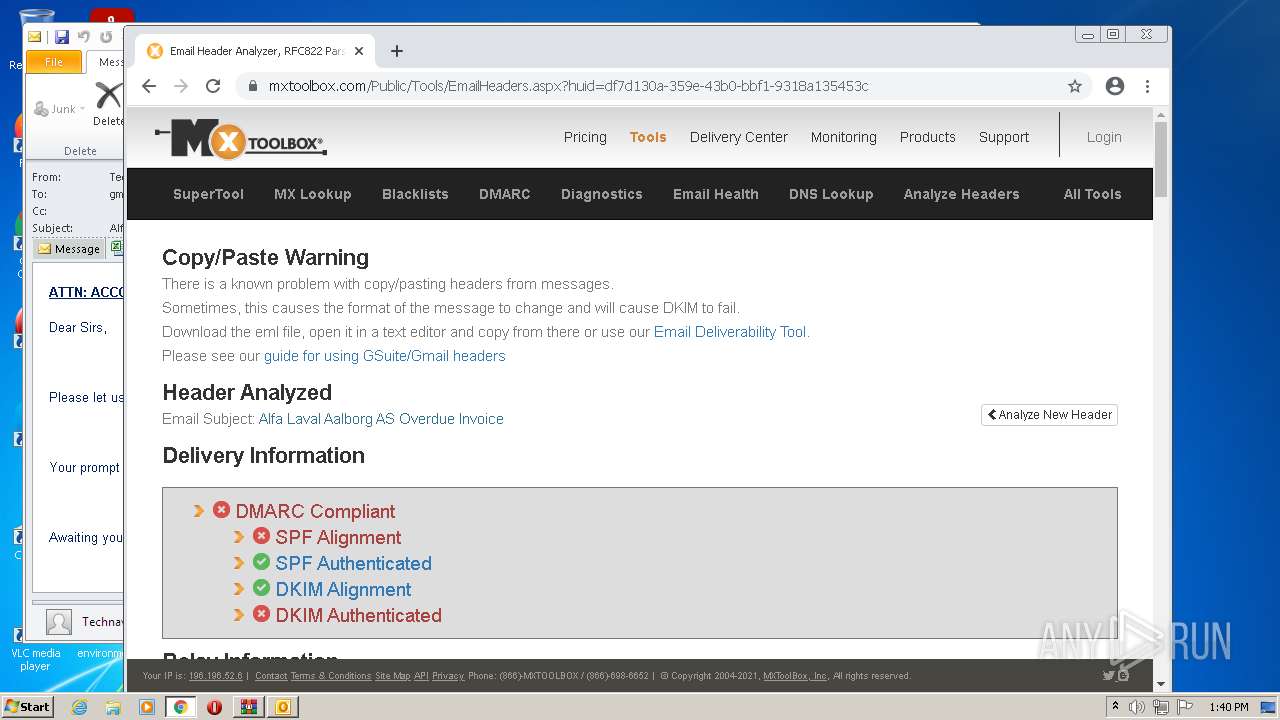
— | — | 18.66.248.66:80 | mxtoolbox.com | Massachusetts Institute of Technology | US | suspicious |
3168 | chrome.exe | 18.66.248.66:443 | mxtoolbox.com | Massachusetts Institute of Technology | US | suspicious |
3168 | chrome.exe | 34.96.102.137:443 | dev.visualwebsiteoptimizer.com | — | US | suspicious |
3168 | chrome.exe | 108.157.4.106:443 | images.mxtoolbox.com | — | US | unknown |
3168 | chrome.exe | 142.250.185.110:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
lh5.googleusercontent.com |
| whitelisted |
mxtoolbox.com |
| whitelisted |
dev.visualwebsiteoptimizer.com |
| whitelisted |
images.mxtoolbox.com |
| shared |