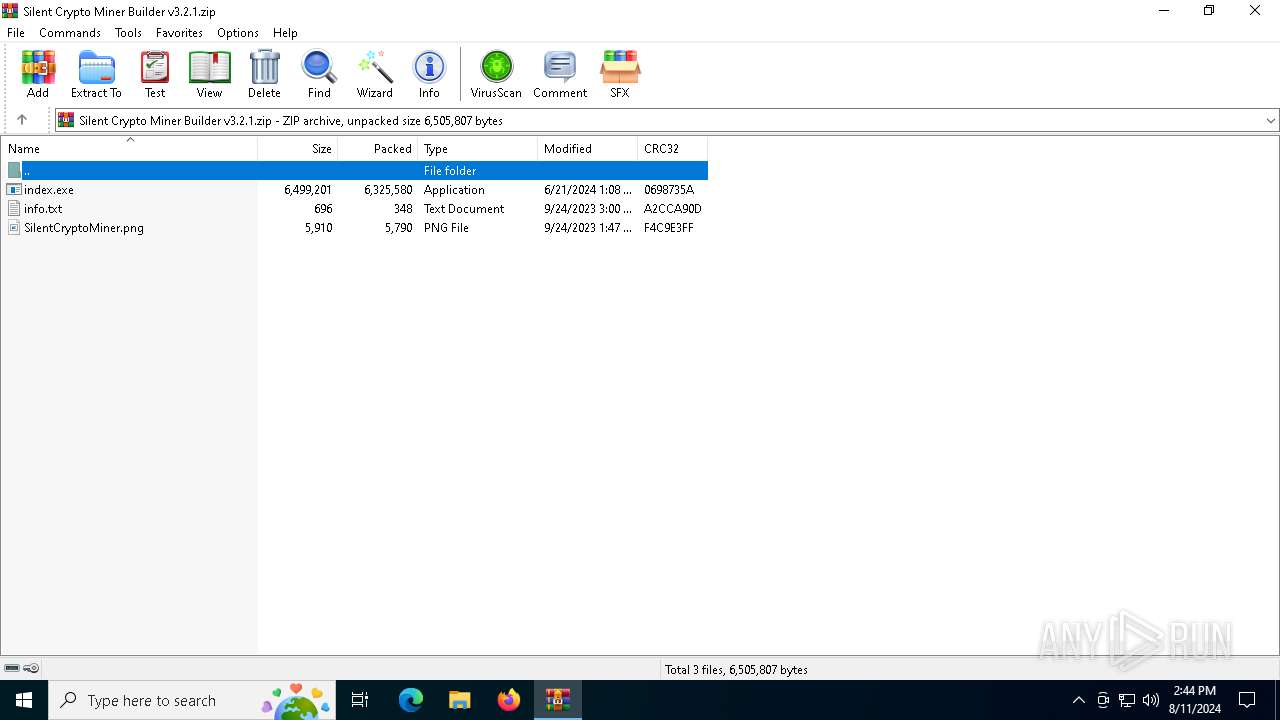
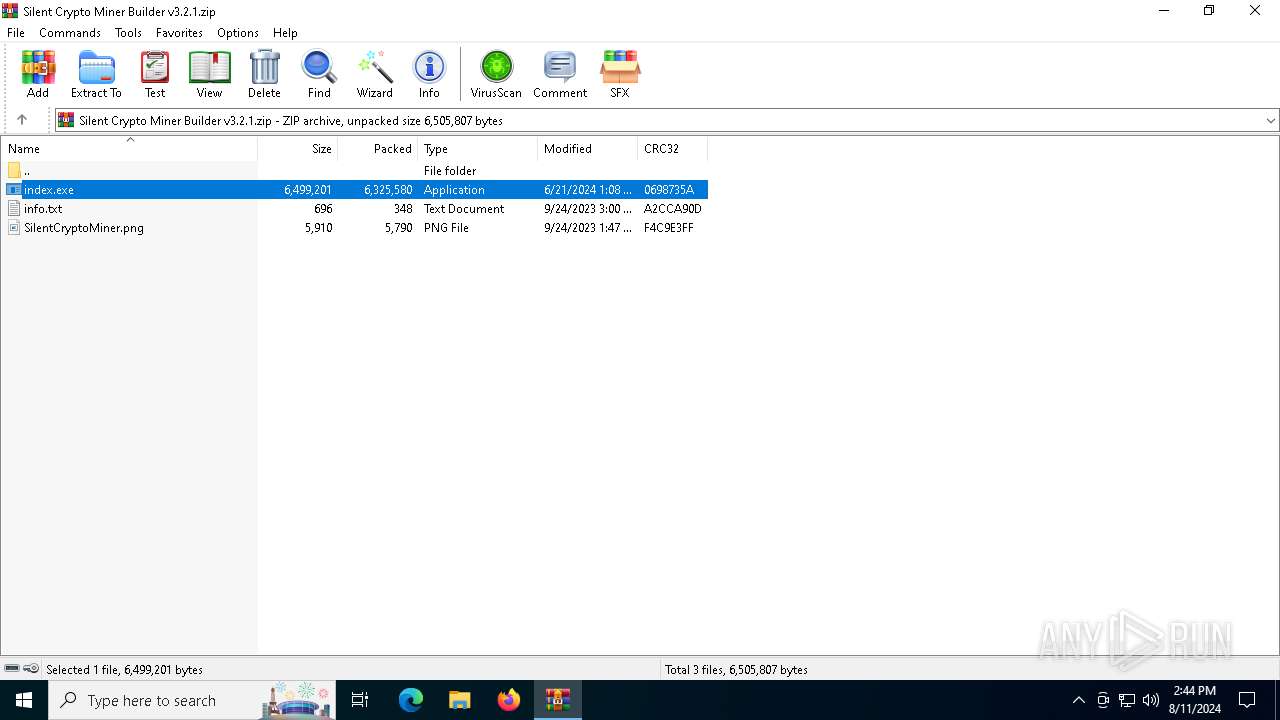
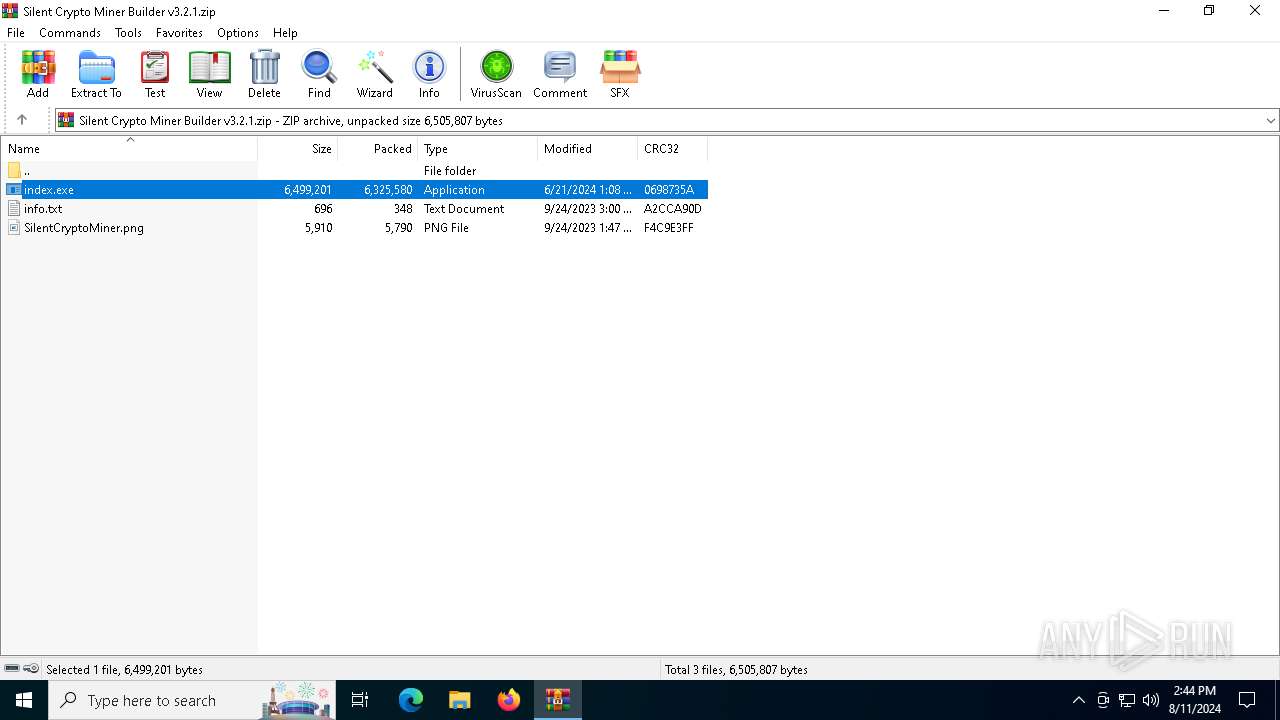
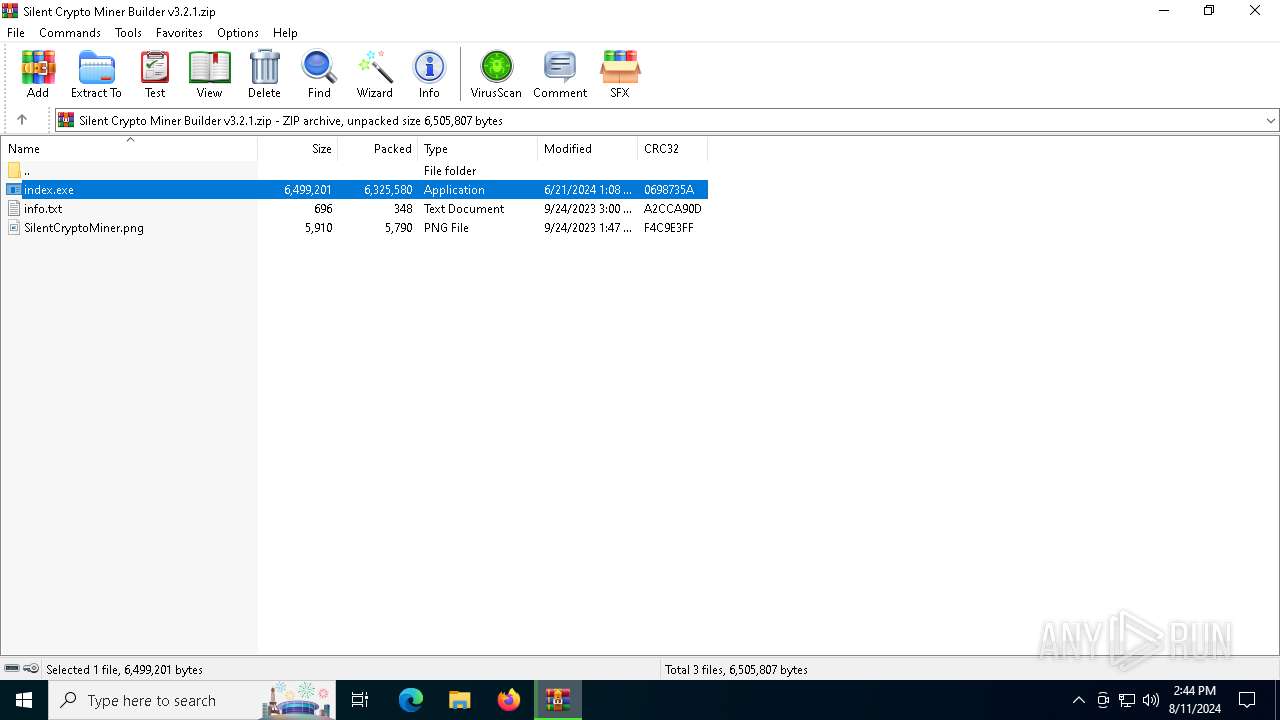
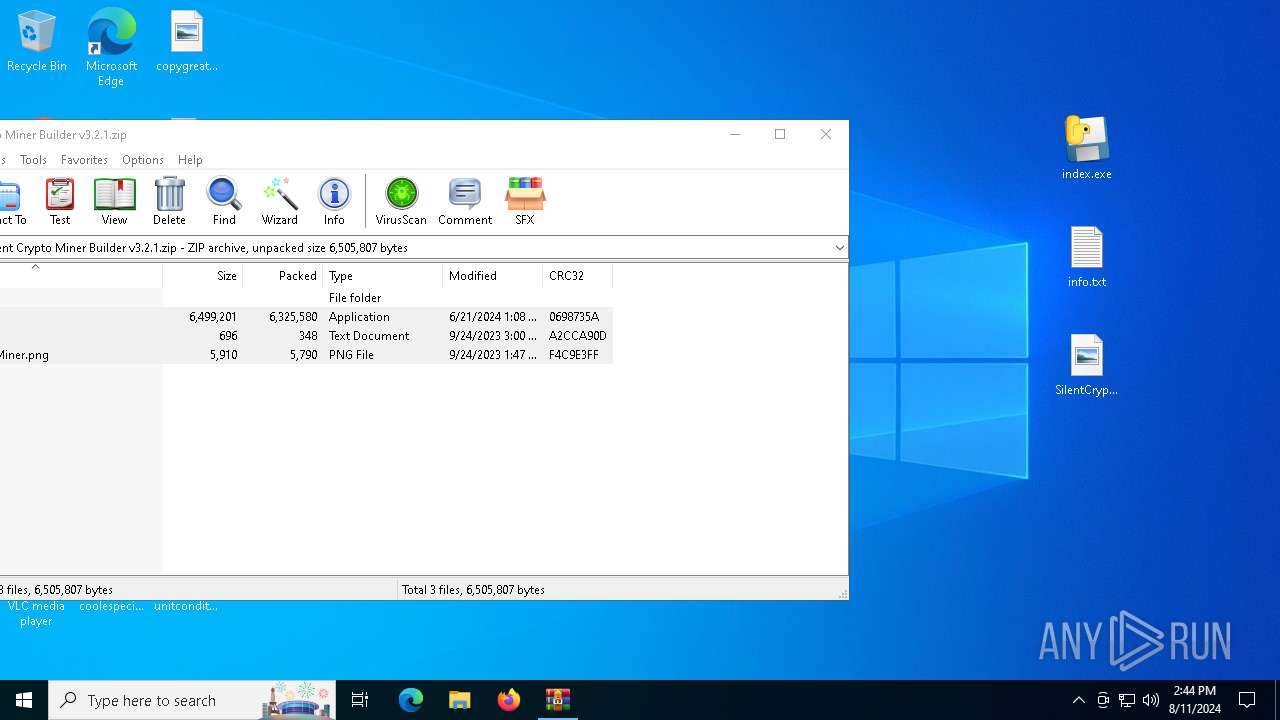
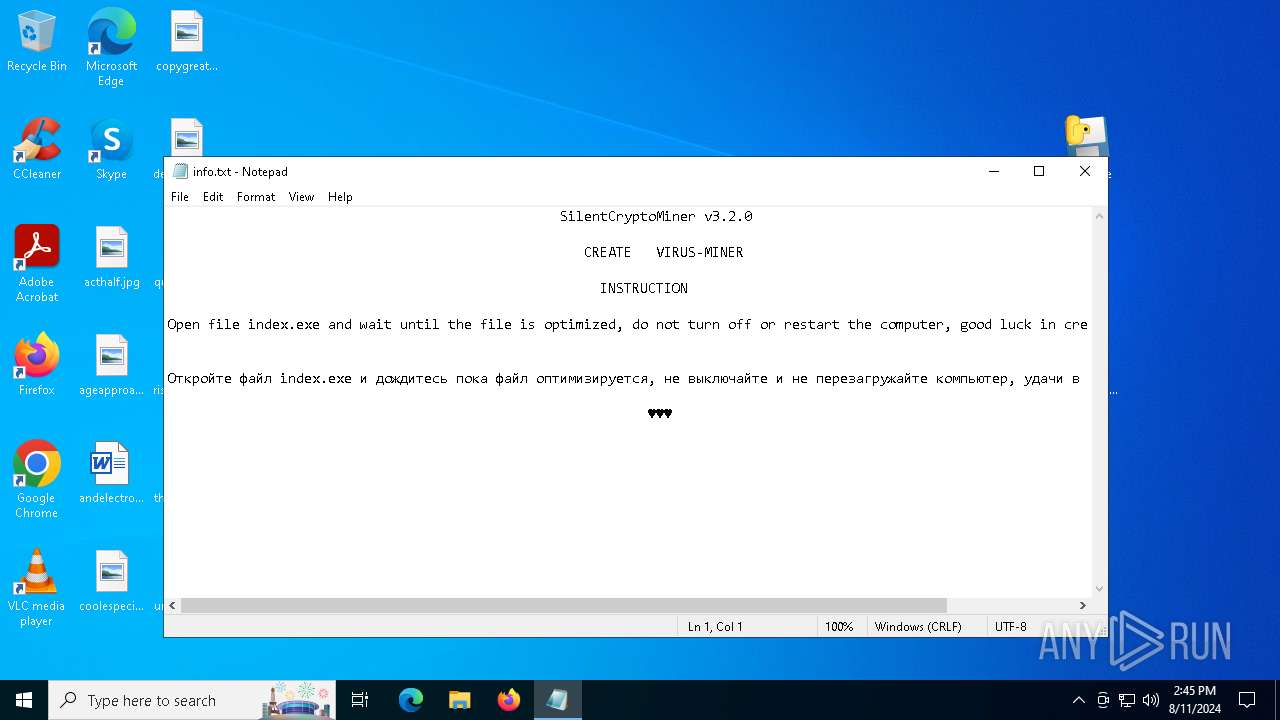
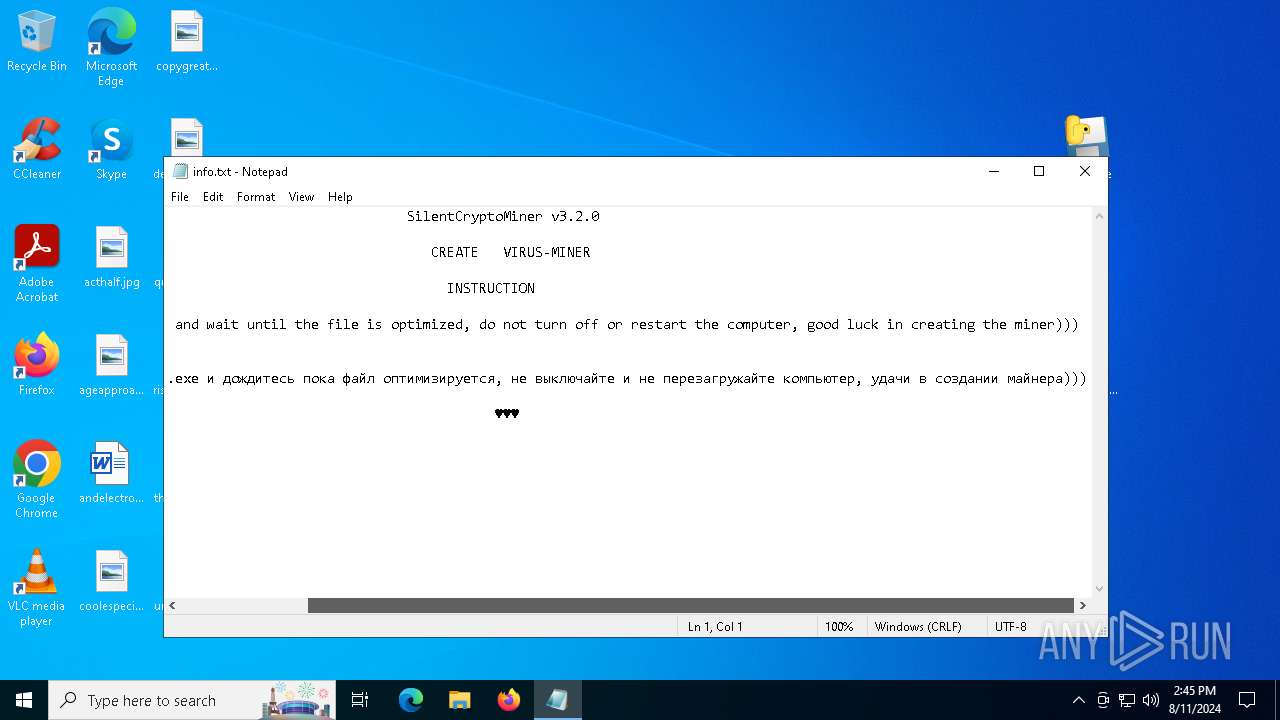
| File name: | Silent Crypto Miner Builder v3.2.1.zip |
| Full analysis: | https://app.any.run/tasks/cb3793d1-c8dc-48de-aa1f-d460e63246a9 |
| Verdict: | Malicious activity |
| Analysis date: | August 11, 2024, 14:43:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 885523DD16A5B4E4B9B2CB5DC65F585B |
| SHA1: | 735BF7649747703C7180260E41742353711F79CA |
| SHA256: | 935A951302E7D7F90234307ACAA2554519D6F9277FC5CFC177658A24C54DE3FE |
| SSDEEP: | 98304:QS6VBfqIbpFwJ5K5uhdaSyCiPJW6gt1TPFf+x04j5ra6xQNlQRRlU9U+zMtzl9Sf:+vsGtuZSu6Rgl5ec |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- index.exe (PID: 6716)
- index.exe (PID: 30672)
- WinRAR.exe (PID: 6484)
Application launched itself
- index.exe (PID: 6716)
- index.exe (PID: 30672)
The process drops C-runtime libraries
- index.exe (PID: 6716)
- index.exe (PID: 30672)
Process drops python dynamic module
- index.exe (PID: 6716)
- index.exe (PID: 30672)
Loads Python modules
- index.exe (PID: 6736)
- index.exe (PID: 31220)
Executable content was dropped or overwritten
- index.exe (PID: 6716)
- index.exe (PID: 30672)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6484)
Process drops legitimate windows executable
- index.exe (PID: 6716)
- index.exe (PID: 30672)
INFO
Reads the computer name
- index.exe (PID: 6716)
- index.exe (PID: 30672)
- index.exe (PID: 6736)
- index.exe (PID: 31220)
- TextInputHost.exe (PID: 10288)
Checks supported languages
- index.exe (PID: 6716)
- index.exe (PID: 6736)
- index.exe (PID: 30672)
- index.exe (PID: 31220)
- TextInputHost.exe (PID: 10288)
Create files in a temporary directory
- index.exe (PID: 6716)
- index.exe (PID: 30672)
Checks proxy server information
- index.exe (PID: 6736)
- index.exe (PID: 31220)
Reads the machine GUID from the registry
- index.exe (PID: 6736)
- index.exe (PID: 31220)
PyInstaller has been detected (YARA)
- index.exe (PID: 6716)
- index.exe (PID: 6736)
- index.exe (PID: 30672)
- index.exe (PID: 31220)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6484)
Manual execution by a user
- notepad.exe (PID: 33156)
- mspaint.exe (PID: 55612)
Reads security settings of Internet Explorer
- notepad.exe (PID: 33156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:21 15:08:06 |
| ZipCRC: | 0x0698735a |
| ZipCompressedSize: | 6325580 |
| ZipUncompressedSize: | 6499201 |
| ZipFileName: | index.exe |
Total processes
147
Monitored processes
8
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6484 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Silent Crypto Miner Builder v3.2.1.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6716 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.25899\index.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.25899\index.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6736 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.25899\index.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.25899\index.exe | index.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 10288 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 30672 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.30010\index.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.30010\index.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 31220 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.30010\index.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.30010\index.exe | index.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 33156 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\info.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 55612 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\ageapproach.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
Total events
300 590
Read events
300 563
Write events
27
Delete events
0
Modification events
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Silent Crypto Miner Builder v3.2.1.zip | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
33
Suspicious files
2
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.25899\SilentCryptoMiner.png | image | |
MD5:80526EFFB67A81E226DC4A7059974251 | SHA256:5C32ABC1CB82680D1EF9411B38899F0817CADFC3AB9BAC1689DDA0B38D075750 | |||
| 6484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.25899\info.txt | text | |
MD5:4995967B0A8B71399CA8447E2F40E62F | SHA256:B06A59221EFD41366FD422EE8432BC5ECC48216B2440BAED7097D5C9DEB6DFFC | |||
| 6716 | index.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\_bz2.pyd | executable | |
MD5:E877E39CC3C42ED1F5461E2D5E62FC0F | SHA256:4B1D29F19ADAF856727FA4A1F50EEE0A86C893038DFBA2E52F26C11AB5B3672F | |||
| 6716 | index.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\_decimal.pyd | executable | |
MD5:95F1BE8C2D46AA4B5AD13F4FBB228C31 | SHA256:F7864B8B37715A87F4F11D5CBFEFD5F1489399E064F7662FA0E0D7C5DF59D5E4 | |||
| 6716 | index.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\_lzma.pyd | executable | |
MD5:80DA699F55CA8ED4DF2D154F17A08583 | SHA256:2E3FD65C4E02C99A61344CE59E09EC7FDE74C671DB5F82A891732E1140910F20 | |||
| 6716 | index.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\_ssl.pyd | executable | |
MD5:CF2F95ECF1A72F8670177C081EEDEB04 | SHA256:BA6025AB22D8E6C5AD53C66DC919F219A542E87540502905609B33DC0A8DDDD8 | |||
| 6484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6484.25899\index.exe | executable | |
MD5:8A35DDE5AB743A95A11CDE36627184E5 | SHA256:3DFD229B92521BBA1B1F546E259AD3129B939142BE21A60F5BEB79F452F768EA | |||
| 6716 | index.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\libssl-1_1.dll | executable | |
MD5:BD857F444EBBF147A8FCD1215EFE79FC | SHA256:B7C0E42C1A60A2A062B899C8D4EBD0C50EF956177BA21785CE07C517C143AEAF | |||
| 6716 | index.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\VCRUNTIME140.dll | executable | |
MD5:A87575E7CF8967E481241F13940EE4F7 | SHA256:DED5ADAA94341E6C62AEA03845762591666381DCA30EB7C17261DD154121B83E | |||
| 6716 | index.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\select.pyd | executable | |
MD5:589F030C0BAA8C47F7F8082A92B834F5 | SHA256:B9EF1709ED4CD0FD72E4C4BA9B7702CB79D1619C11554EA06277F3DAC21BD010 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
18 367
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4292 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
18200 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
18144 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1164 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5588 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6736 | index.exe | 37.230.118.111:443 | riadagestan.ru | JSC IOT | RU | unknown |
31220 | index.exe | 37.230.118.111:443 | riadagestan.ru | JSC IOT | RU | unknown |
5336 | SearchApp.exe | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
riadagestan.ru |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |