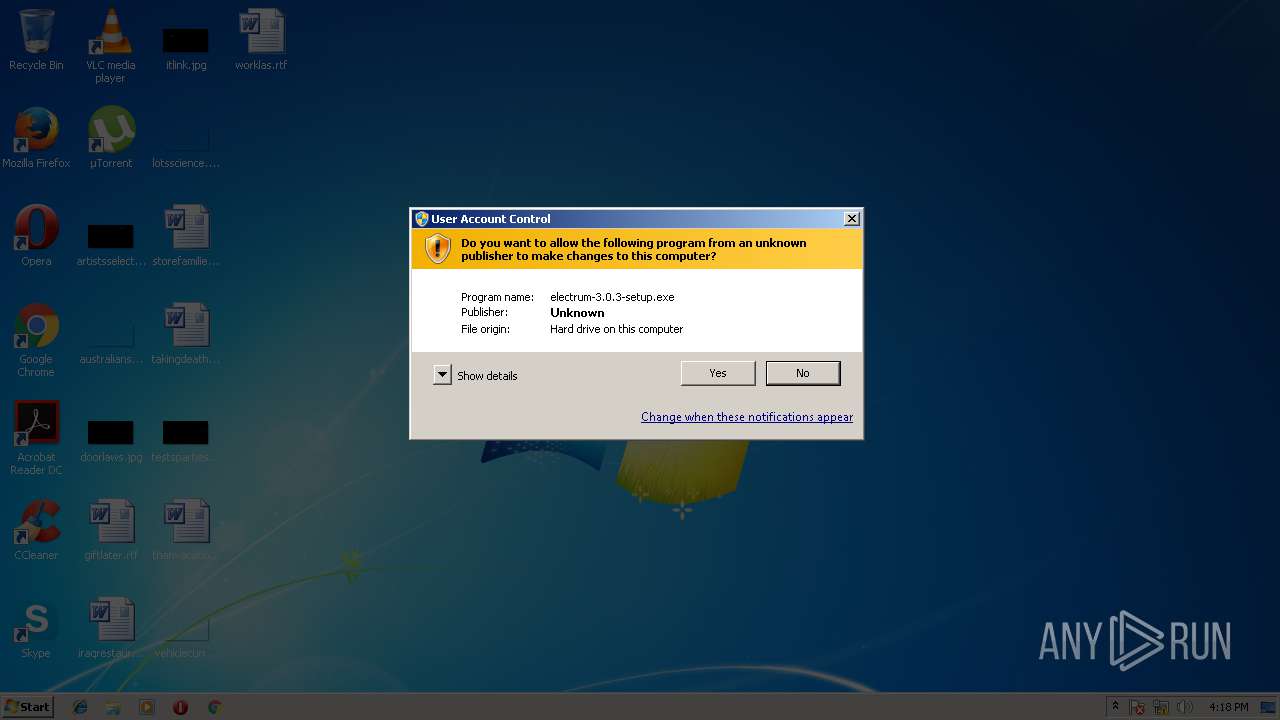
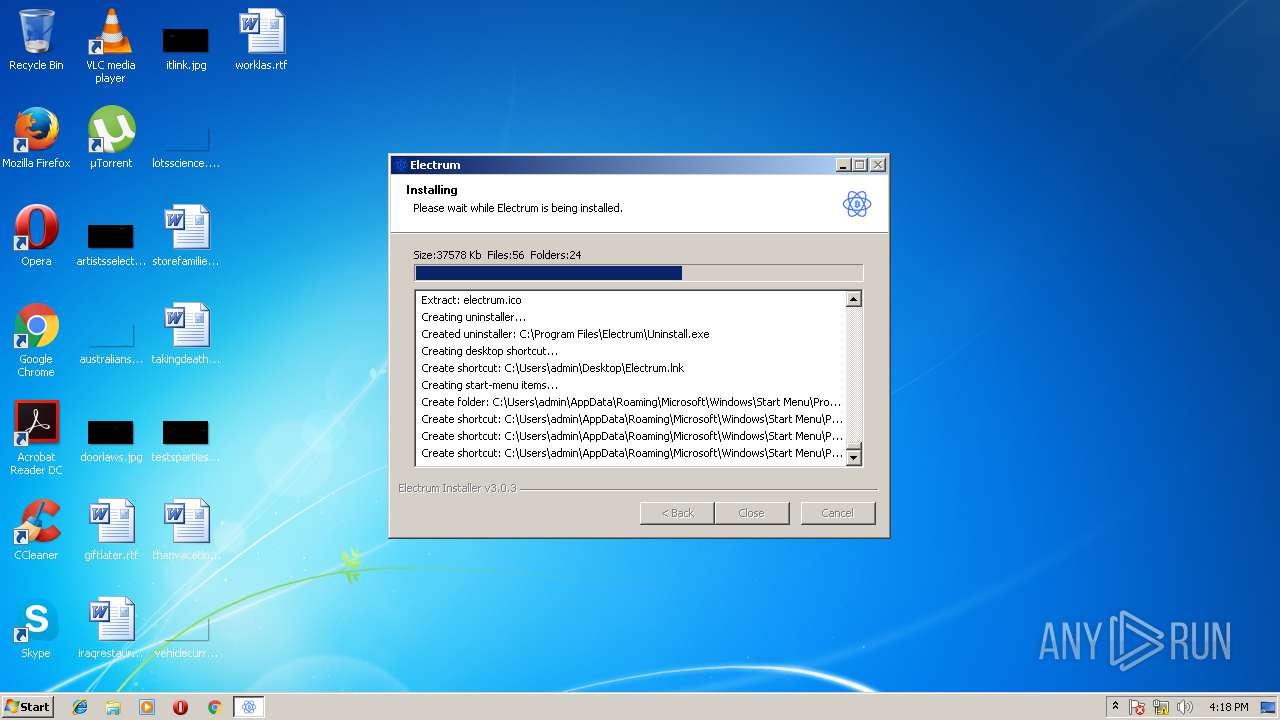
| File name: | electrum-3.0.3-setup.exe |
| Full analysis: | https://app.any.run/tasks/a016b502-21d2-4894-9b5a-13a04485d5a0 |
| Verdict: | Malicious activity |
| Analysis date: | March 09, 2018, 16:17:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | AF109EE40F0D0EB30F1E088D0F98D381 |
| SHA1: | C89556006A35672E294005165389D7B3332D76BC |
| SHA256: | 9349E27BF9F315F4F4CC0EEB90A28D78AD1A0A37F3BCBA1F604078A554DC088C |
| SSDEEP: | 393216:WnM/2+58eodEASCJ8I5XfJsK4iPLQifq8:WP+merwJ75PJPPLQi3 |
MALICIOUS
Application loaded dropped or rewritten executable
- electrum-3.0.3.exe (PID: 2536)
- electrum-3.0.3-setup.exe (PID: 120)
Application was dropped or rewritten from another process
- electrum-3.0.3.exe (PID: 2536)
SUSPICIOUS
Creates a software uninstall entry
- electrum-3.0.3-setup.exe (PID: 120)
Modifies the open verb of a shell class
- electrum-3.0.3-setup.exe (PID: 120)
Creates files in the user directory
- electrum-3.0.3.exe (PID: 2536)
- electrum-3.0.3-setup.exe (PID: 120)
Creates files in the program directory
- electrum-3.0.3-setup.exe (PID: 120)
INFO
Reads settings of System Certificates
- electrum-3.0.3.exe (PID: 2536)
Loads rich edit control libraries
- electrum-3.0.3-setup.exe (PID: 120)
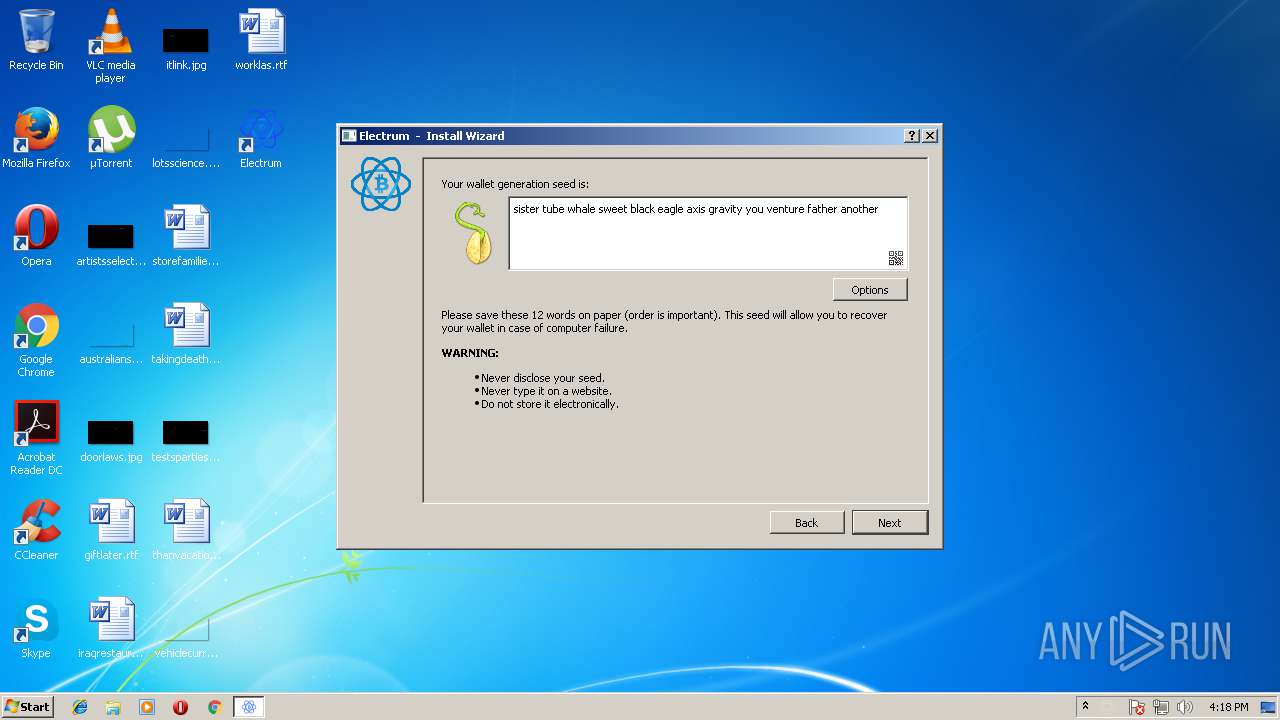
Dropped object may contain Bitcoin addresses
- electrum-3.0.3-setup.exe (PID: 120)
Dropped object may contain URL's
- electrum-3.0.3-setup.exe (PID: 120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:08:01 02:33:55+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25088 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x330d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | The installer for Electrum |
| CompanyName: | Electrum |
| FileDescription: | Electrum Installer |
| FileVersion: | 3.0.3 |
| InternalName: | Electrum Installer |
| LegalCopyright: | 2013-2016 Electrum Technologies GmbH |
| LegalTrademarks: | Electrum is a trademark of Electrum Technologies GmbH |
| OriginalFileName: | Electrum.exe |
| ProductName: | Electrum Installer |
| ProductVersion: | 3.0.3 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Aug-2017 00:33:55 |
| Detected languages: |
|
| Comments: | The installer for Electrum |
| CompanyName: | Electrum |
| FileDescription: | Electrum Installer |
| FileVersion: | 3.0.3 |
| InternalName: | Electrum Installer |
| LegalCopyright: | 2013-2016 Electrum Technologies GmbH |
| LegalTrademarks: | Electrum is a trademark of Electrum Technologies GmbH |
| OriginalFilename: | Electrum.exe |
| ProductName: | Electrum Installer |
| ProductVersion: | 3.0.3 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 01-Aug-2017 00:33:55 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000603C | 0x00006200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.39362 |
.rdata | 0x00008000 | 0x00001248 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.04426 |
.data | 0x0000A000 | 0x0001A838 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.22313 |
.ndata | 0x00025000 | 0x0000F000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00034000 | 0x0000DB58 | 0x0000DC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.07474 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.2901 | 1072 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.20642 | 9640 | UNKNOWN | English - United States | RT_ICON |
3 | 3.52336 | 4264 | UNKNOWN | English - United States | RT_ICON |
4 | 2.80722 | 3752 | UNKNOWN | English - United States | RT_ICON |
5 | 2.47831 | 2216 | UNKNOWN | English - United States | RT_ICON |
6 | 2.66811 | 1640 | UNKNOWN | English - United States | RT_ICON |
7 | 1.15935 | 1384 | UNKNOWN | English - United States | RT_ICON |
8 | 4.17452 | 1128 | UNKNOWN | English - United States | RT_ICON |
9 | 2.65167 | 744 | UNKNOWN | English - United States | RT_ICON |
10 | 1.734 | 296 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
38
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\AppData\Local\Temp\electrum-3.0.3-setup.exe" | C:\Users\admin\AppData\Local\Temp\electrum-3.0.3-setup.exe | explorer.exe | ||||||||||||
User: admin Company: Electrum Integrity Level: HIGH Description: Electrum Installer Exit code: 0 Version: 3.0.3 Modules
| |||||||||||||||
| 2536 | "C:\Program Files\Electrum\electrum-3.0.3.exe" | C:\Program Files\Electrum\electrum-3.0.3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3428 | "C:\Users\admin\AppData\Local\Temp\electrum-3.0.3-setup.exe" | C:\Users\admin\AppData\Local\Temp\electrum-3.0.3-setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Electrum Integrity Level: MEDIUM Description: Electrum Installer Exit code: 3221226540 Version: 3.0.3 Modules
| |||||||||||||||
Total events
988
Read events
929
Write events
58
Delete events
1
Modification events
| (PID) Process: | (120) electrum-3.0.3-setup.exe | Key: | HKEY_CURRENT_USER\Software\Electrum |
| Operation: | write | Name: | |
Value: C:\Program Files\Electrum | |||
| (PID) Process: | (120) electrum-3.0.3-setup.exe | Key: | HKEY_CLASSES_ROOT\bitcoin |
| Operation: | write | Name: | |
Value: URL:bitcoin Protocol | |||
| (PID) Process: | (120) electrum-3.0.3-setup.exe | Key: | HKEY_CLASSES_ROOT\bitcoin |
| Operation: | write | Name: | URL Protocol |
Value: | |||
| (PID) Process: | (120) electrum-3.0.3-setup.exe | Key: | HKEY_CLASSES_ROOT\bitcoin |
| Operation: | write | Name: | DefaultIcon |
Value: "C:\Program Files\Electrum\electrum.ico, 0" | |||
| (PID) Process: | (120) electrum-3.0.3-setup.exe | Key: | HKEY_CLASSES_ROOT\bitcoin\shell\open\command |
| Operation: | write | Name: | |
Value: "C:\Program Files\Electrum\electrum-3.0.3.exe" "%1" | |||
| (PID) Process: | (120) electrum-3.0.3-setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\Electrum |
| Operation: | write | Name: | DisplayName |
Value: Electrum | |||
| (PID) Process: | (120) electrum-3.0.3-setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\Electrum |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\Electrum\Uninstall.exe | |||
| (PID) Process: | (120) electrum-3.0.3-setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\Electrum |
| Operation: | write | Name: | DisplayVersion |
Value: 3.0.3 | |||
| (PID) Process: | (120) electrum-3.0.3-setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\Electrum |
| Operation: | write | Name: | URLInfoAbout |
Value: https://github.com/spesmilo/electrum | |||
| (PID) Process: | (120) electrum-3.0.3-setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\Electrum |
| Operation: | write | Name: | Publisher |
Value: Electrum Technologies GmbH | |||
Executable files
76
Suspicious files
1
Text files
102
Unknown types
38
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 120 | electrum-3.0.3-setup.exe | C:\Program Files\Electrum\PyQt5.QtPrintSupport.pyd | executable | |
MD5:5238C21D91D72C2E238BDAE92814D96E | SHA256:98A037CF5DEF169AE4882D4FBB8E2874643A32F1D9532C562708081143F07D42 | |||
| 120 | electrum-3.0.3-setup.exe | C:\Program Files\Electrum\PyQt5.Qt.pyd | executable | |
MD5:944380C3198C31872DAD761AF5026FE5 | SHA256:6AA65D830905E596332B3187A67C7D61E9CDEF0542FE6D6689CA351174AA4B57 | |||
| 120 | electrum-3.0.3-setup.exe | C:\Users\admin\AppData\Local\Temp\nsoF1A2.tmp\UserInfo.dll | executable | |
MD5:C051C86F6FA84AC87EFB0CF3961950A1 | SHA256:D0949B4C0640EE6A80DB5A7F6D93FC631ED194DE197D79BF080EC1752C6F1166 | |||
| 120 | electrum-3.0.3-setup.exe | C:\Program Files\Electrum\_bz2.pyd | executable | |
MD5:BA168455CE3546714C74BCB8539F155E | SHA256:4066CC9E43ED93EF1D60D46B33BA92E4BD1F0D5506A112C69FF7E692D718A60F | |||
| 120 | electrum-3.0.3-setup.exe | C:\Program Files\Electrum\_socket.pyd | executable | |
MD5:E4C88A3E847BFA4FB85239152773C214 | SHA256:4C9866C39726EA4C18E1BD08E6F6E306837B14F27AD300154C4CF5005E9BA239 | |||
| 120 | electrum-3.0.3-setup.exe | C:\Program Files\Electrum\VCRUNTIME140.dll | executable | |
MD5:8E65E033799EB9FD46BC5C184E7D1B85 | SHA256:BE38A38E22128AF9A529AF33D1F02DD24B2A344D29175939E229CF3A280673E4 | |||
| 120 | electrum-3.0.3-setup.exe | C:\Program Files\Electrum\PyQt5.QtGui.pyd | executable | |
MD5:8F6A5BF441DDBC784D2D44ED54163DFE | SHA256:1E13D049D986BEC3112843395393561E604DF1C9BDB069479006736CA421488C | |||
| 120 | electrum-3.0.3-setup.exe | C:\Program Files\Electrum\Qt5PrintSupport.dll | executable | |
MD5:47E1E09882F094EF77D6A472EA538703 | SHA256:57472B8587A55678230164CF631793B062C861618F43056D2FD902457DC44B84 | |||
| 120 | electrum-3.0.3-setup.exe | C:\Program Files\Electrum\_decimal.pyd | executable | |
MD5:6A9669E2F5DA15C9EF2644954B944A2A | SHA256:455AC18CDAEFB3A243E628AA83B07FFE96E179B564636418C6C313B1D329CE45 | |||
| 120 | electrum-3.0.3-setup.exe | C:\Program Files\Electrum\_lzma.pyd | executable | |
MD5:8528784C860B6D18E554E73E3C2EFA62 | SHA256:2B0AE3EE2AAFB749D06CD2A5159A3E33EC9FEEAD10EF1A90980270B932F84FDE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
18
DNS requests
9
Threats
4
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 217.233.84.167:50002 | ndnd.selfhost.eu | Deutsche Telekom AG | DE | unknown |
— | — | 144.217.204.104:50002 | electrum.cutie.ga | OVH SAS | CA | unknown |
— | — | 216.189.151.199:50002 | node1.volatilevictory.com | HostUS | US | unknown |
— | — | 45.77.138.212:50002 | songbird.bauerj.eu | — | US | unknown |
— | — | 37.59.46.112:50002 | electrum.vom-stausee.de | OVH SAS | FR | unknown |
— | — | 51.15.77.78:50002 | VPS.hsmiths.com | Online S.a.s. | FR | unknown |
— | — | 178.32.88.133:50002 | helicarrier.bauerj.eu | OVH SAS | FR | unknown |
— | — | 78.46.103.75:443 | headers.electrum.org | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ndnd.selfhost.eu |
| malicious |
electrum.cutie.ga |
| malicious |
node1.volatilevictory.com |
| unknown |
songbird.bauerj.eu |
| unknown |
electrum.vom-stausee.de |
| whitelisted |
s5.noip.pl |
| unknown |
VPS.hsmiths.com |
| unknown |
helicarrier.bauerj.eu |
| unknown |
headers.electrum.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ga Domain |
— | — | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
— | — | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
— | — | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
Process | Message |
|---|---|
electrum-3.0.3.exe | QWindowsNativeFileDialogBase::onSelectionChange () 0
|