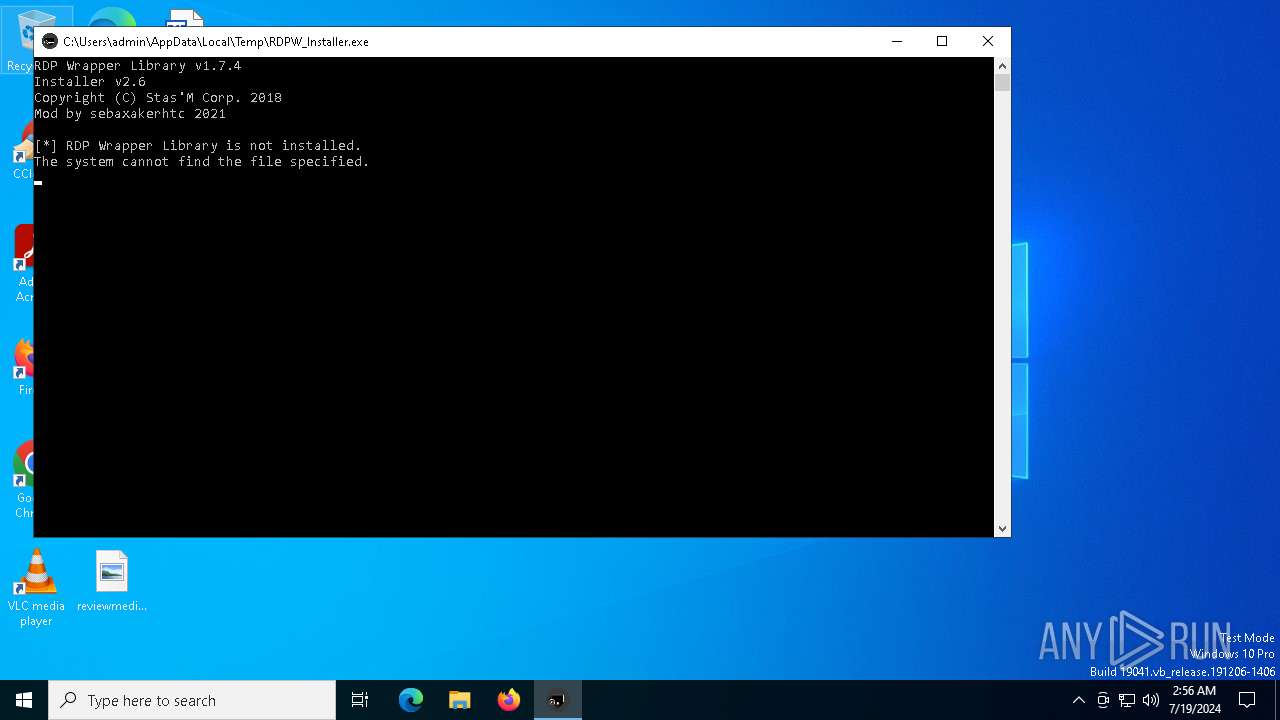
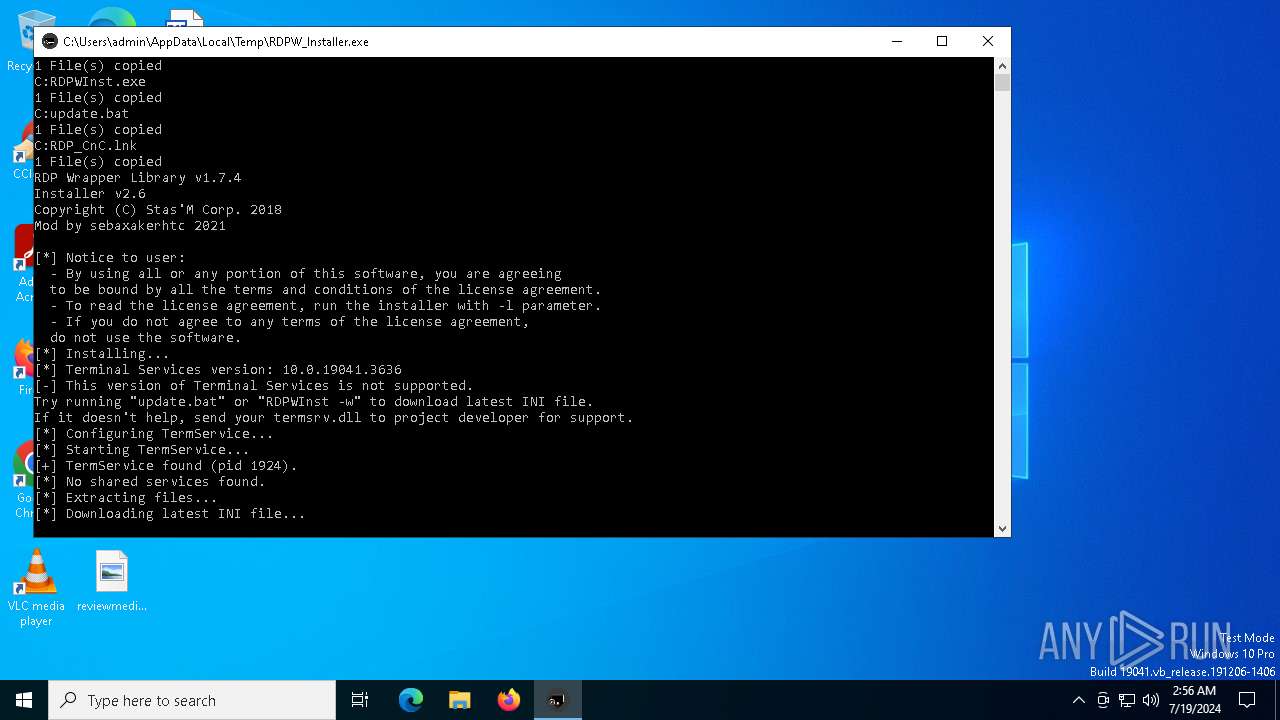
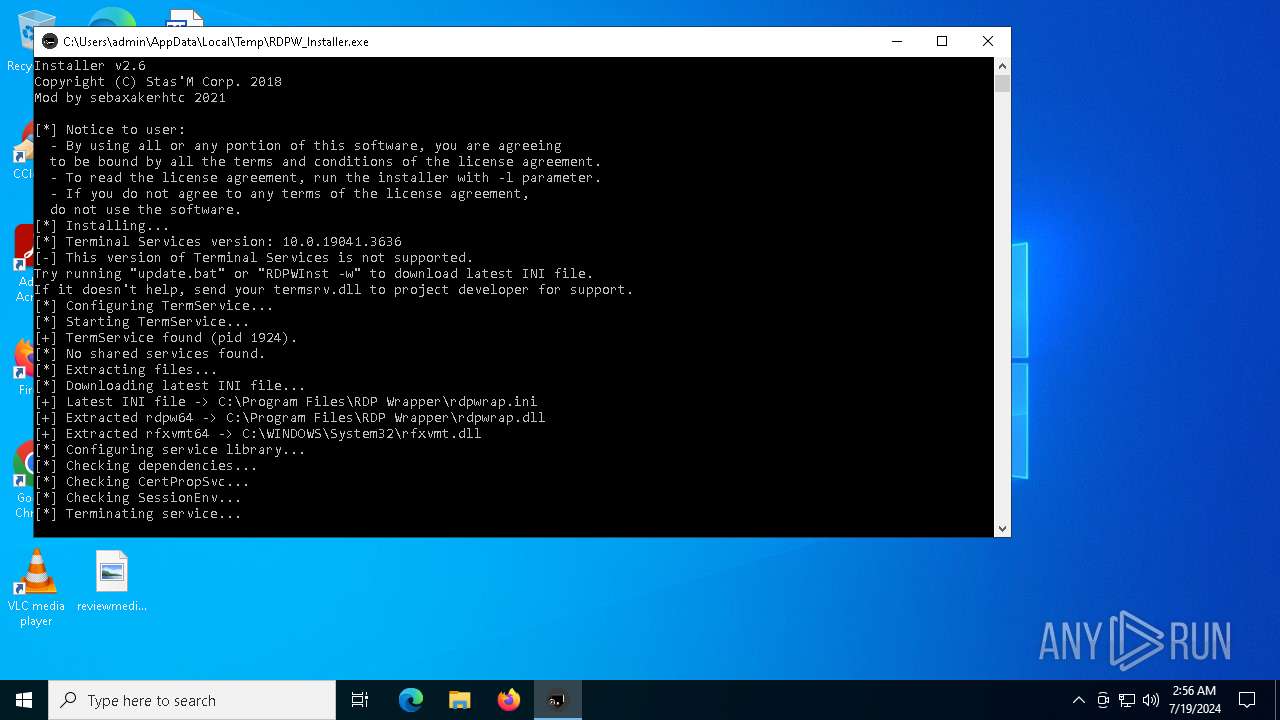
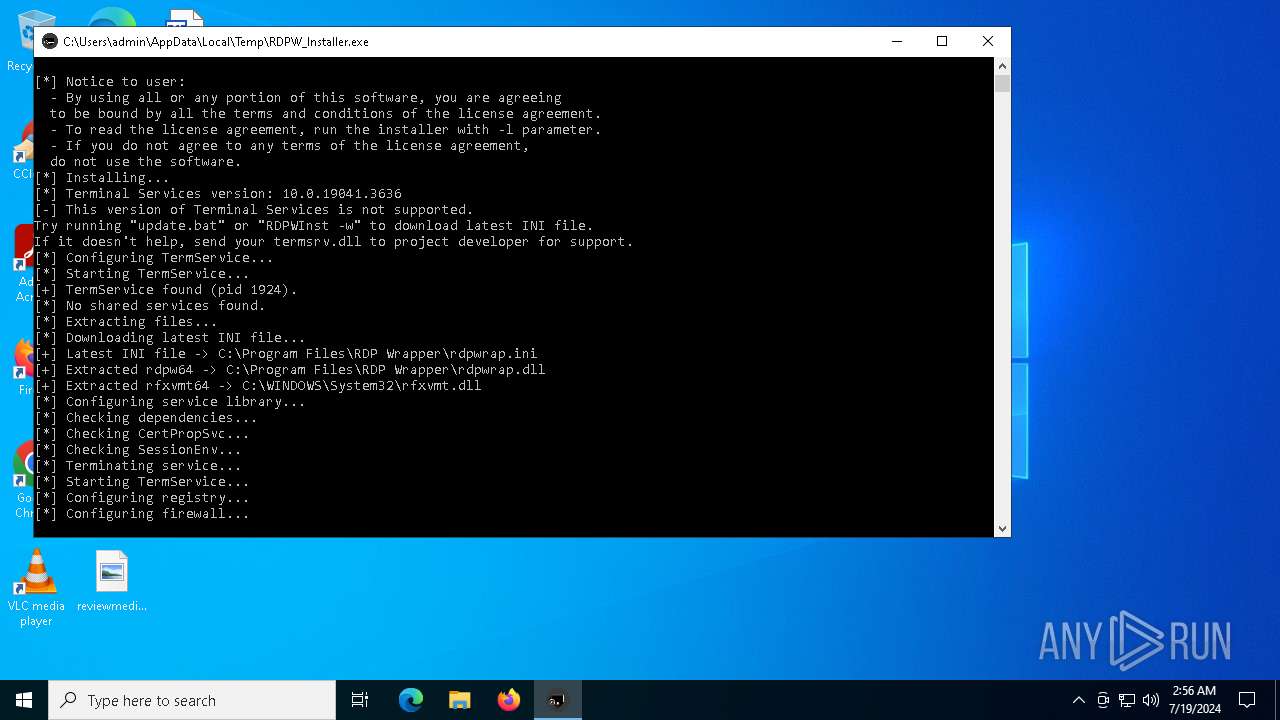
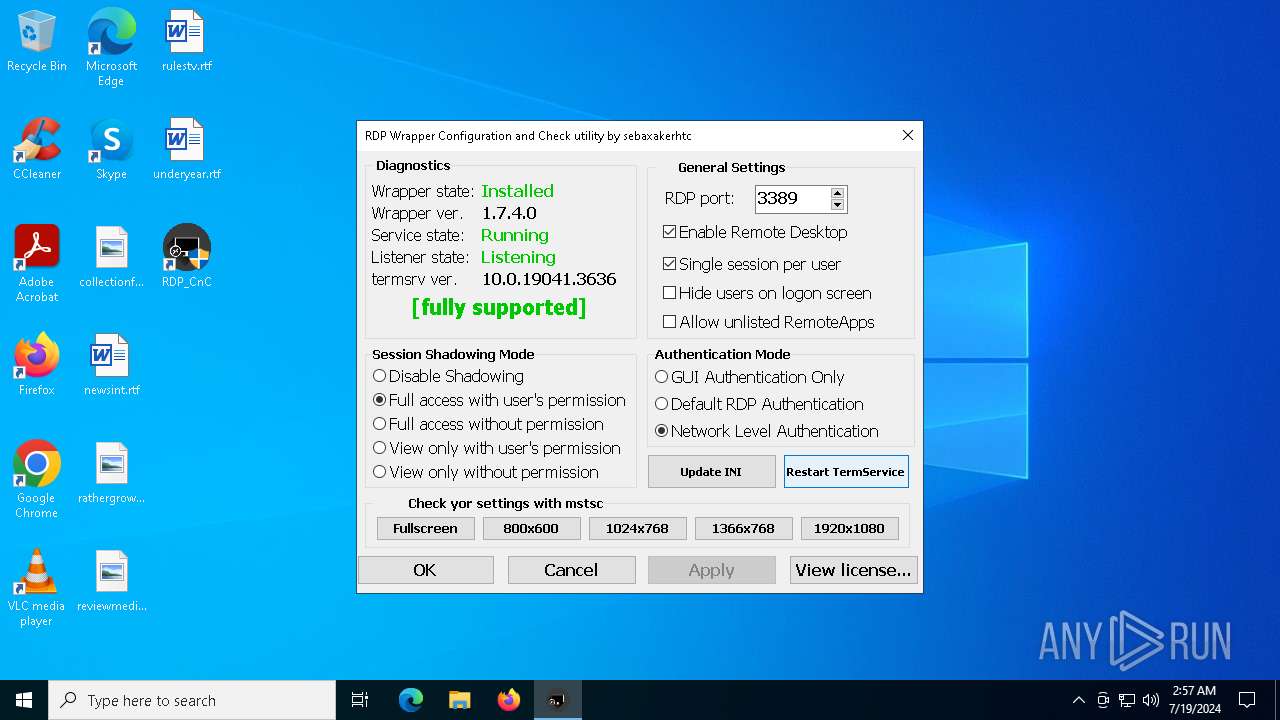
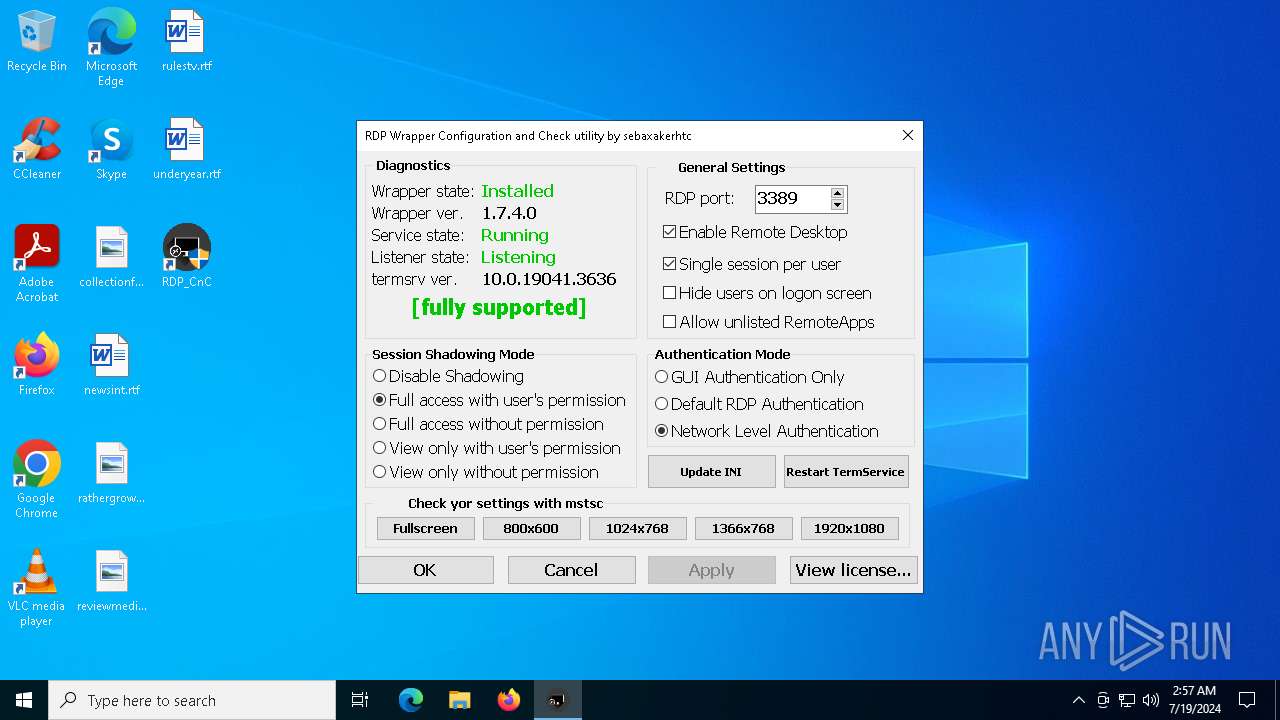
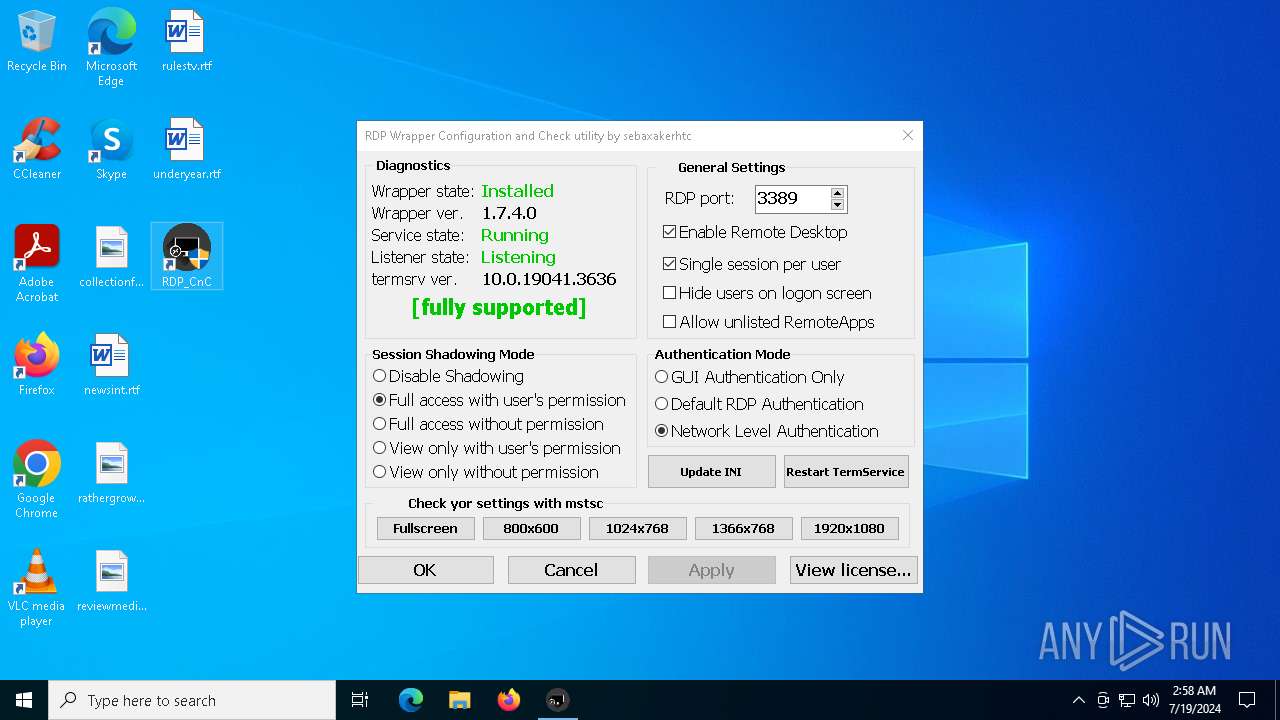
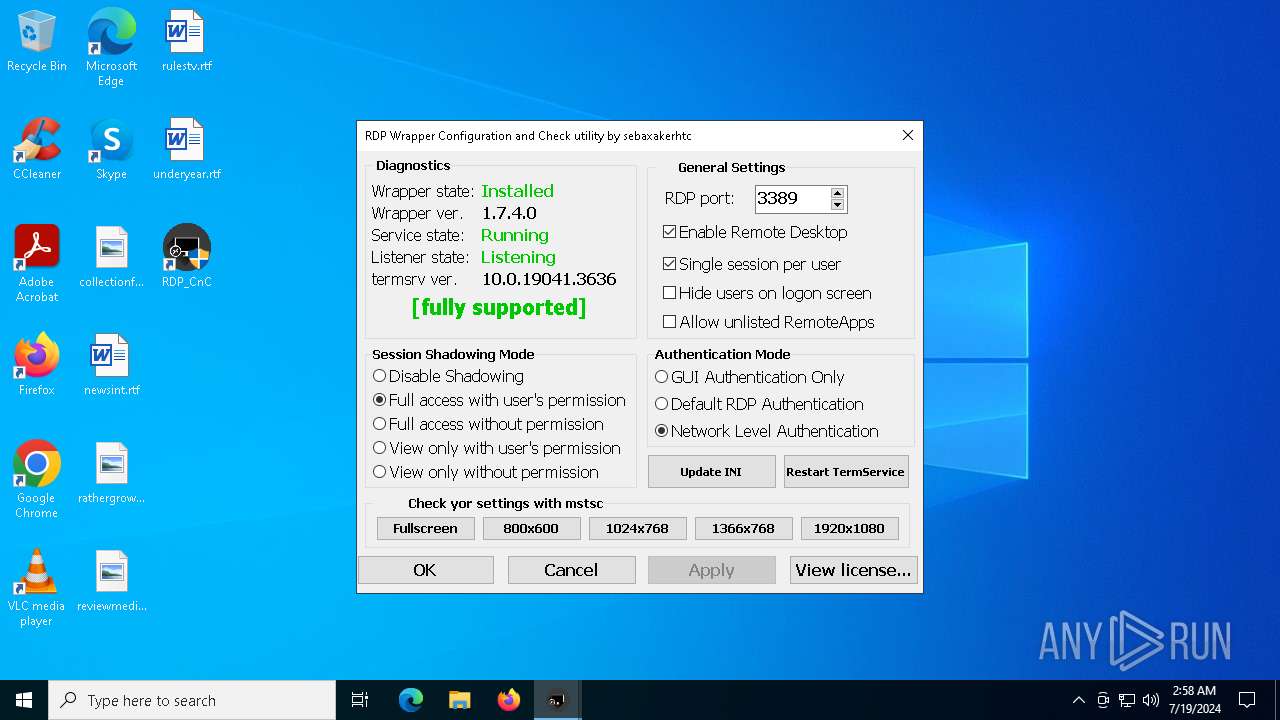
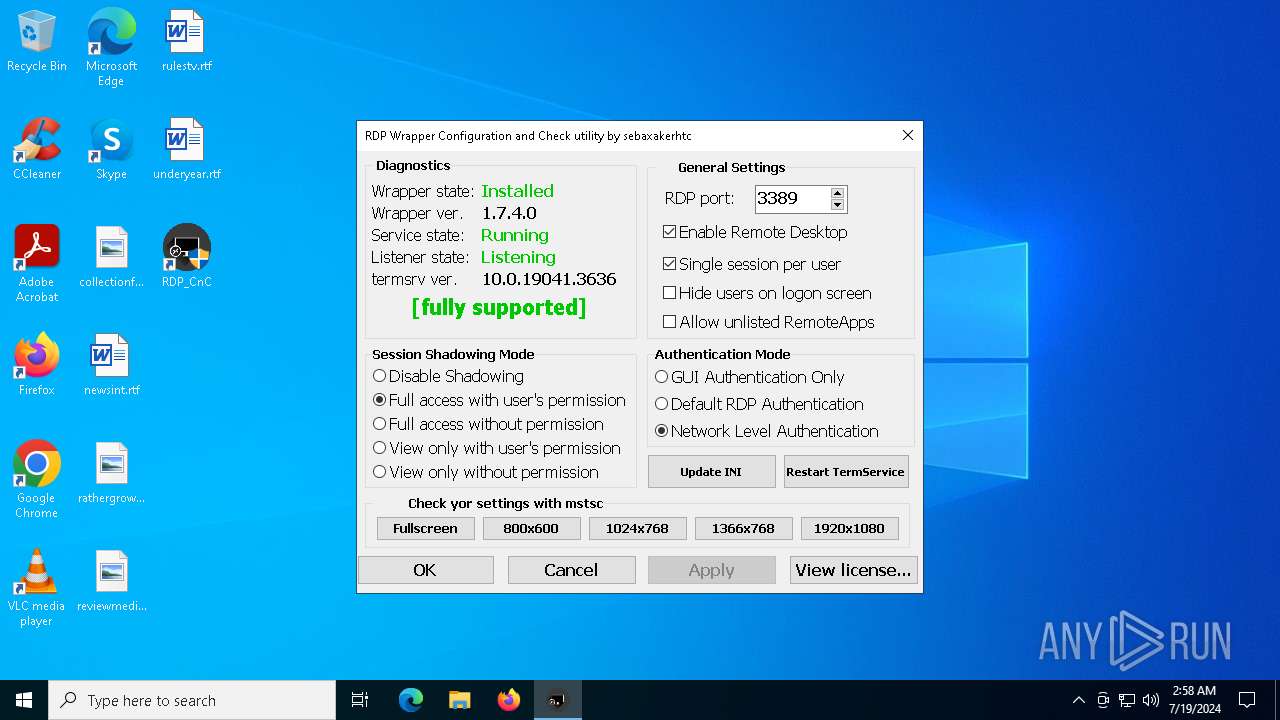
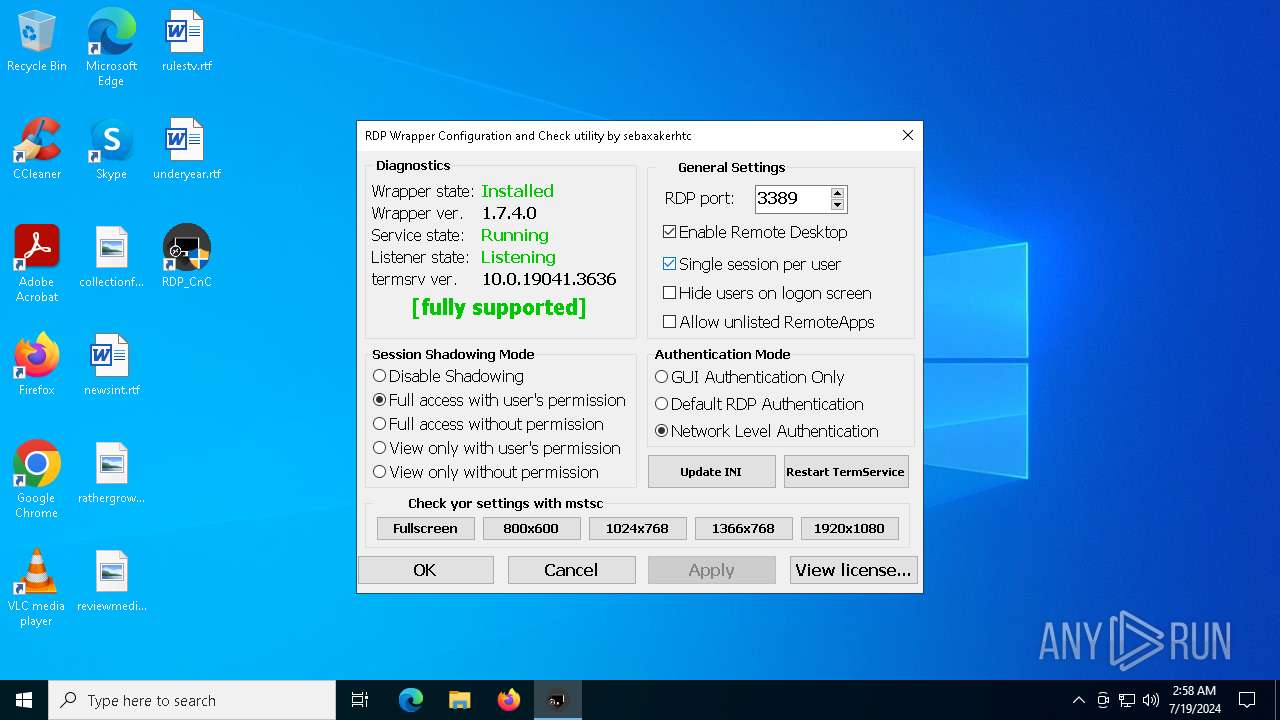
| File name: | RDPW_Installer.exe |
| Full analysis: | https://app.any.run/tasks/1bc31274-f77e-4427-a83c-fca538c9c89a |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2024, 02:56:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 6EBEA4D46302623D47827CD82E0AA4B3 |
| SHA1: | 51C8D2AF8A8F00DA1EAB9CE34A9F9505115295DE |
| SHA256: | 932BCF6C68E34FB99FFAFB5AE62A1473FE761D961034CB5630DC3A9BA9155CCB |
| SSDEEP: | 98304:7qsLZ475+bairV071rc9Va1aCGxQtM0eerjgJikszsmjsV4dt3uOn2boyB3G1JS/:uTQki |
MALICIOUS
Drops the executable file immediately after the start
- RDPW_Installer.exe (PID: 7996)
- RDPWInst.exe (PID: 2104)
Creates or modifies Windows services
- RDPWInst.exe (PID: 2104)
Creates a writable file in the system directory
- RDPWInst.exe (PID: 2104)
- LGPO.exe (PID: 5464)
Changes the Windows auto-update feature
- LGPO.exe (PID: 5464)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3964)
Starts NET.EXE for service management
- net.exe (PID: 6032)
- net.exe (PID: 3624)
- RDP_CnC.exe (PID: 4288)
SUSPICIOUS
Process drops legitimate windows executable
- RDPW_Installer.exe (PID: 7996)
- RDPWInst.exe (PID: 2104)
Executable content was dropped or overwritten
- RDPW_Installer.exe (PID: 7996)
- xcopy.exe (PID: 3776)
- xcopy.exe (PID: 7452)
- RDPWInst.exe (PID: 2104)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3964)
Executing commands from a ".bat" file
- RDPW_Installer.exe (PID: 7996)
Starts CMD.EXE for commands execution
- RDPW_Installer.exe (PID: 7996)
- cmd.exe (PID: 3964)
Process copies executable file
- cmd.exe (PID: 3964)
Reads security settings of Internet Explorer
- RDPWInst.exe (PID: 2104)
- RDPWInst.exe (PID: 7864)
- RDP_CnC.exe (PID: 5748)
- RDP_CnC.exe (PID: 4288)
Checks Windows Trust Settings
- RDPWInst.exe (PID: 2104)
- RDPWInst.exe (PID: 7864)
Uses NETSH.EXE to add a firewall rule or allowed programs
- RDPWInst.exe (PID: 2104)
Starts a Microsoft application from unusual location
- LGPO.exe (PID: 5464)
Application launched itself
- RDP_CnC.exe (PID: 5748)
- cmd.exe (PID: 3964)
- RDP_CnC.exe (PID: 4288)
Reads the date of Windows installation
- RDP_CnC.exe (PID: 5748)
- RDP_CnC.exe (PID: 4288)
INFO
Checks supported languages
- RDPWInst.exe (PID: 7868)
- RDPW_Installer.exe (PID: 7996)
- RDPWInst.exe (PID: 2104)
- LGPO.exe (PID: 5464)
- RDP_CnC.exe (PID: 5748)
- RDPWInst.exe (PID: 7864)
- RDP_CnC.exe (PID: 4288)
- RDP_CnC.exe (PID: 4808)
- RDP_CnC.exe (PID: 7912)
- RDP_CnC.exe (PID: 5108)
Creates files in the program directory
- xcopy.exe (PID: 3776)
- xcopy.exe (PID: 7452)
- xcopy.exe (PID: 7576)
- RDPWInst.exe (PID: 2104)
Create files in a temporary directory
- RDPW_Installer.exe (PID: 7996)
Drops the executable file immediately after the start
- xcopy.exe (PID: 3776)
- xcopy.exe (PID: 7452)
Checks proxy server information
- RDPWInst.exe (PID: 2104)
- RDPWInst.exe (PID: 7864)
Reads the computer name
- RDPWInst.exe (PID: 2104)
- LGPO.exe (PID: 5464)
- RDPWInst.exe (PID: 7864)
- RDP_CnC.exe (PID: 5748)
- RDP_CnC.exe (PID: 4288)
- RDP_CnC.exe (PID: 7912)
- RDP_CnC.exe (PID: 4808)
- RDP_CnC.exe (PID: 5108)
Reads the machine GUID from the registry
- RDPWInst.exe (PID: 2104)
- RDPWInst.exe (PID: 7864)
Reads the software policy settings
- RDPWInst.exe (PID: 2104)
- RDPWInst.exe (PID: 7864)
Creates files or folders in the user directory
- RDPWInst.exe (PID: 2104)
- RDPWInst.exe (PID: 7864)
Process checks computer location settings
- RDP_CnC.exe (PID: 5748)
- RDP_CnC.exe (PID: 4288)
Manual execution by a user
- RDP_CnC.exe (PID: 4808)
- RDP_CnC.exe (PID: 3128)
- RDP_CnC.exe (PID: 5108)
- RDP_CnC.exe (PID: 5164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:01 20:18:05+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 70144 |
| InitializedDataSize: | 2472960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.8.9.9 |
| ProductVersionNumber: | 1.8.9.9 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 1.8.9.9 |
| ProductVersion: | 1.8.9.9 |
| ProductName: | RDPW_Installer |
| OriginalFileName: | RDPW_Installer |
| InternalName: | RDPW_Installer |
| CompanyName: | sebaxakerhtc |
Total processes
169
Monitored processes
32
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1284 | xcopy "RDP_CnC.lnk" "C:\Users\admin\Desktop\" /s /I /y | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
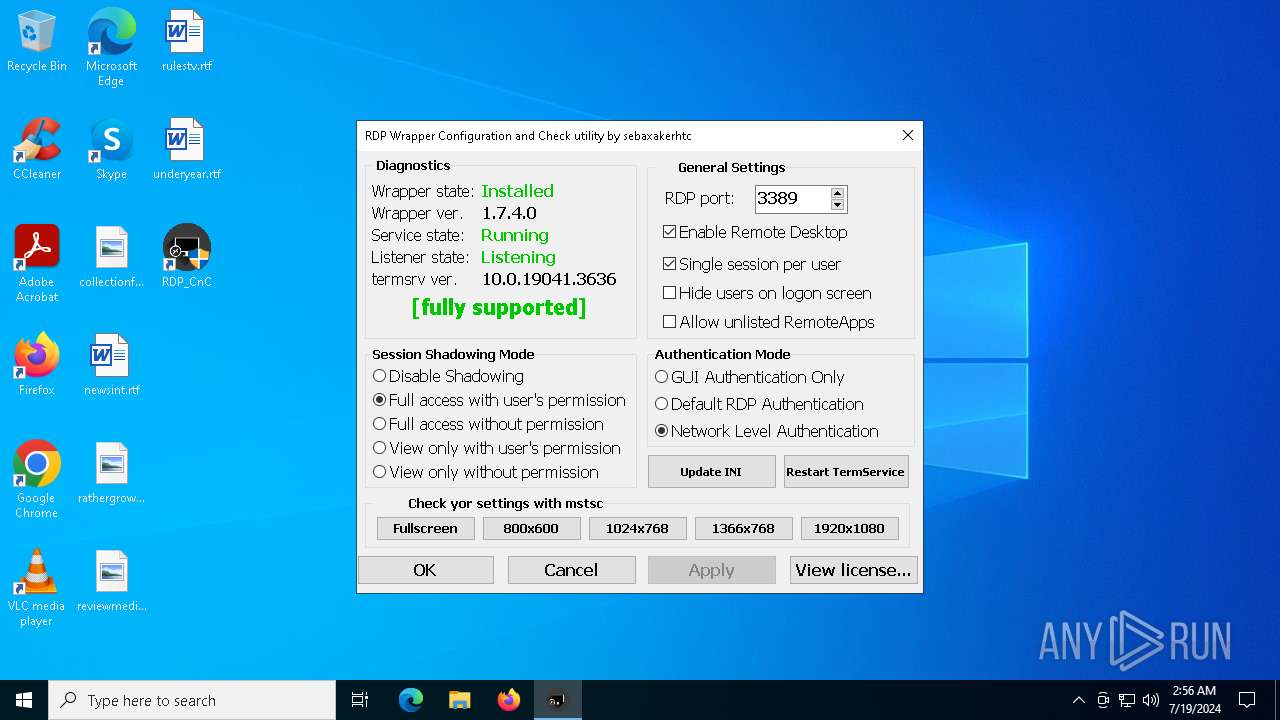
| 2104 | "C:\Program Files\RDP Wrapper\RDPWInst" -i -o | C:\Program Files\RDP Wrapper\RDPWInst.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2436 | SCHTASKS /CREATE /SC ONSTART /DELAY 0002:00 /TN "RDPWUpdater" /TR "'C:\Program Files\RDP Wrapper\RDPWInst.exe' -w" /RL HIGHEST /RU SYSTEM /NP /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3128 | "C:\Program Files\RDP Wrapper\RDP_CnC.exe" | C:\Program Files\RDP Wrapper\RDP_CnC.exe | — | explorer.exe | |||||||||||
User: admin Company: Thanks to Stas'M Corp for this project Integrity Level: MEDIUM Description: RDP Wrapper Configuration and Check utility by sebaxakerhtc Exit code: 3221226540 Version: 1.8.9.9 Modules
| |||||||||||||||
| 3152 | C:\WINDOWS\system32\net1 start termservice /y | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3624 | net start termservice /y | C:\Windows\System32\net.exe | — | RDP_CnC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3776 | xcopy "RDP_CnC.exe" "C:\Program Files\RDP Wrapper\" /s /I /y | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3964 | "C:\WINDOWS\sysnative\cmd" /c "C:\Users\admin\AppData\Local\Temp\9614.tmp\9615.tmp\9616.bat C:\Users\admin\AppData\Local\Temp\RDPW_Installer.exe" | C:\Windows\System32\cmd.exe | — | RDPW_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4288 | "C:\Program Files\RDP Wrapper\RDP_CnC.exe" | C:\Program Files\RDP Wrapper\RDP_CnC.exe | — | RDP_CnC.exe | |||||||||||
User: admin Company: Thanks to Stas'M Corp for this project Integrity Level: HIGH Description: RDP Wrapper Configuration and Check utility by sebaxakerhtc Exit code: 0 Version: 1.8.9.9 Modules
| |||||||||||||||
| 4808 | "C:\Program Files\RDP Wrapper\RDP_CnC.exe" | C:\Program Files\RDP Wrapper\RDP_CnC.exe | explorer.exe | ||||||||||||
User: admin Company: Thanks to Stas'M Corp for this project Integrity Level: HIGH Description: RDP Wrapper Configuration and Check utility by sebaxakerhtc Exit code: 0 Version: 1.8.9.9 Modules
| |||||||||||||||
Total events
8 329
Read events
8 234
Write events
68
Delete events
27
Modification events
| (PID) Process: | (2104) RDPWInst.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2104) RDPWInst.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2104) RDPWInst.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2104) RDPWInst.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2104) RDPWInst.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2104) RDPWInst.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2104) RDPWInst.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2104) RDPWInst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\TermService\Parameters |
| Operation: | write | Name: | ServiceDll |
Value: %ProgramFiles%\RDP Wrapper\rdpwrap.dll | |||
| (PID) Process: | (2104) RDPWInst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Terminal Server |
| Operation: | write | Name: | fDenyTSConnections |
Value: 0 | |||
| (PID) Process: | (2104) RDPWInst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Terminal Server\Licensing Core |
| Operation: | write | Name: | EnableConcurrentSessions |
Value: 1 | |||
Executable files
7
Suspicious files
10
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3776 | xcopy.exe | C:\Program Files\RDP Wrapper\RDP_CnC.exe | executable | |
MD5:08ED5177C4AA58AECB690243A7C60513 | SHA256:5552C5AB33A144F420F1F1855392BD216C31385B4470B807F65017B310490C0E | |||
| 7996 | RDPW_Installer.exe | C:\Users\admin\AppData\Local\Temp\9614.tmp\RDP_CnC.lnk | lnk | |
MD5:BF5E6E967E6DF74051E971D62EE9D282 | SHA256:83F134B45E9E28ABD1E4A773F48C0303BC5F8B8B22F7FC12EE4FCB4011A7733D | |||
| 7996 | RDPW_Installer.exe | C:\Users\admin\AppData\Local\Temp\9614.tmp\9615.tmp\9616.bat | text | |
MD5:1C04DB7C0404D977651E89247B449FB5 | SHA256:BF7F1043F7D151E06440C07AA91BD2C7048657515C12A0AF8DEA2BECFE6802BD | |||
| 2104 | RDPWInst.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\rdpwrap[1].ini | binary | |
MD5:1E1B8C8EFE19C79C87F0915827F45600 | SHA256:F076E8795486788FFBD13B42837E5A9AE2E6C3FAD70B0BE70855278F10A07F56 | |||
| 5464 | LGPO.exe | C:\WINDOWS\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:288EAC8E2EFBF03198E866E3FD34BC09 | SHA256:59F0A1F65C2249FDE4D9C14EF9C7F46995EDF0A26976B577AAD6D9122B54A9B1 | |||
| 2104 | RDPWInst.exe | C:\Program Files\RDP Wrapper\rdpwrap.ini | binary | |
MD5:1E1B8C8EFE19C79C87F0915827F45600 | SHA256:F076E8795486788FFBD13B42837E5A9AE2E6C3FAD70B0BE70855278F10A07F56 | |||
| 2104 | RDPWInst.exe | C:\WINDOWS\System32\rfxvmt.dll | executable | |
MD5:E3E4492E2C871F65B5CEA8F1A14164E2 | SHA256:32FF81BE7818FA7140817FA0BC856975AE9FCB324A081D0E0560D7B5B87EFB30 | |||
| 5464 | LGPO.exe | C:\WINDOWS\SysWOW64\GroupPolicy\gpt.ini | text | |
MD5:39DFFC602ED934569F26BE44EC645814 | SHA256:B57A88E5B1ACF3A784BE88B87FA3EE1F0991CB7C1C66DA423F3595FFC6E0C5C2 | |||
| 7996 | RDPW_Installer.exe | C:\Users\admin\AppData\Local\Temp\9614.tmp\RDPWInst.exe | executable | |
MD5:980D56AE0A529BA108D9194FB056F285 | SHA256:D8B3001C86A1433524F1239C2A14A11D67009BBA44DC3C686F295BCC0FACC5A1 | |||
| 7996 | RDPW_Installer.exe | C:\Users\admin\AppData\Local\Temp\9614.tmp\RDP_CnC.exe | executable | |
MD5:08ED5177C4AA58AECB690243A7C60513 | SHA256:5552C5AB33A144F420F1F1855392BD216C31385B4470B807F65017B310490C0E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
32
DNS requests
12
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | RDPWInst.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7484 | backgroundTaskHost.exe | 20.103.156.88:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4716 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
7856 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2760 | svchost.exe | 40.115.3.253:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7484 | backgroundTaskHost.exe | 20.223.36.55:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2104 | RDPWInst.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2104 | RDPWInst.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1032 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
arc.msn.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |