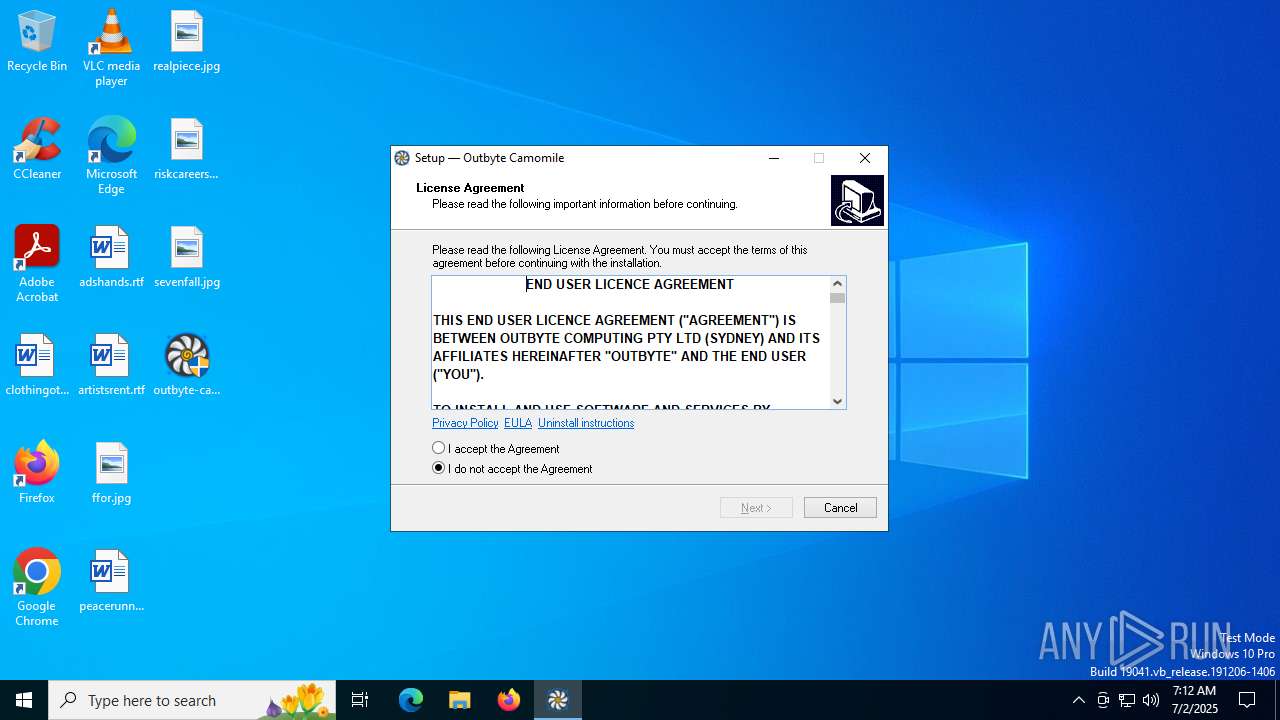
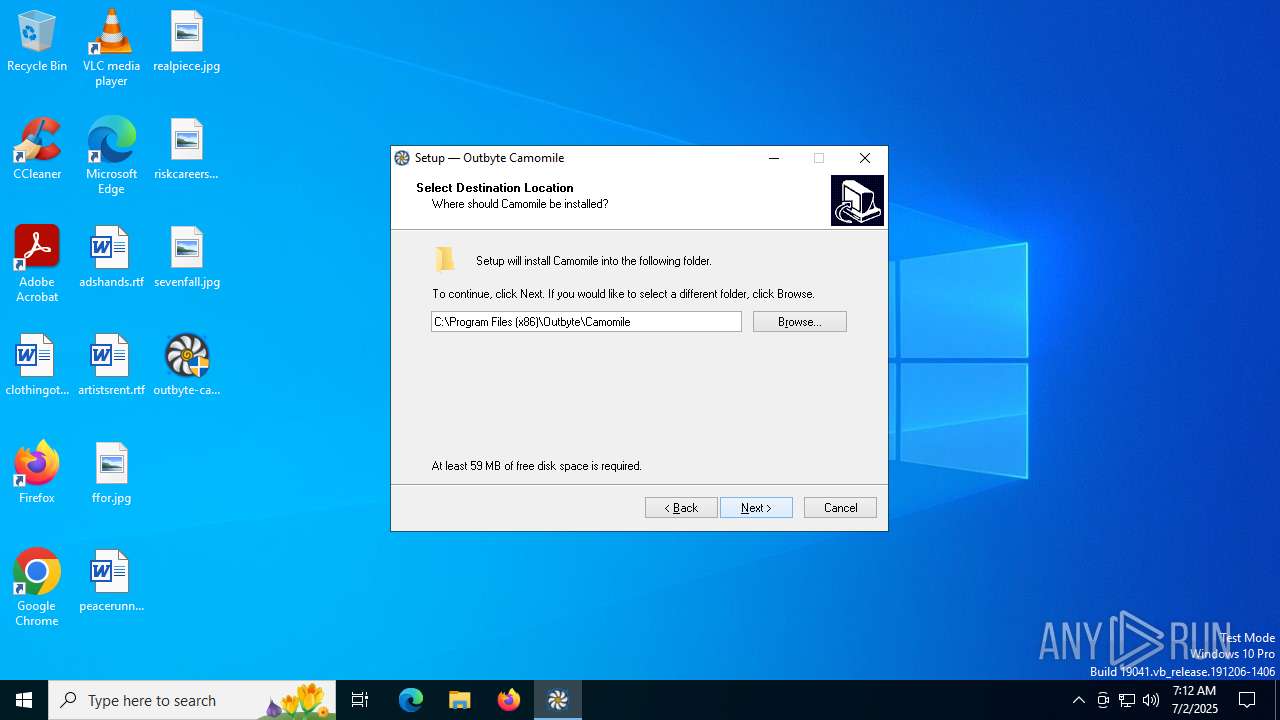
| File name: | outbyte-camomile-setup.exe |
| Full analysis: | https://app.any.run/tasks/6ed1ba02-5c21-4e43-baec-025ac79ed3f8 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2025, 07:11:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | 6C5A79BE4C0A57AB14A35E8C8861A5F6 |
| SHA1: | 4BB3C7C78E2AC01635D67C17D2DC64DAB9ABAF28 |
| SHA256: | 93249EF2AEF8560D16CAB4813460A5D67E70C7553531BDB496EF572495A674C0 |
| SSDEEP: | 98304:KEfoHtB3t+w8k53ArgJazUMqdra/+QidooeAS+O5gHga6W7lTpdKEEm1e+m/ARVP:iQ2Xv/PHlR8toIrjJqOxmsYDFvt |
MALICIOUS
Executing a file with an untrusted certificate
- Installer.exe (PID: 2668)
SUSPICIOUS
Process drops SQLite DLL files
- outbyte-camomile-setup.exe (PID: 6472)
Reads security settings of Internet Explorer
- outbyte-camomile-setup.exe (PID: 6472)
- Installer.exe (PID: 2668)
Executable content was dropped or overwritten
- outbyte-camomile-setup.exe (PID: 6472)
- Installer.exe (PID: 2668)
Reads the BIOS version
- Installer.exe (PID: 2668)
Reads the Windows owner or organization settings
- Installer.exe (PID: 2668)
There is functionality for taking screenshot (YARA)
- Installer.exe (PID: 2668)
There is functionality for communication over UDP network (YARA)
- Installer.exe (PID: 2668)
INFO
Process checks computer location settings
- outbyte-camomile-setup.exe (PID: 6472)
- Installer.exe (PID: 2668)
Checks supported languages
- outbyte-camomile-setup.exe (PID: 6472)
- Installer.exe (PID: 2668)
Reads Environment values
- outbyte-camomile-setup.exe (PID: 6472)
- Installer.exe (PID: 2668)
The sample compiled with english language support
- outbyte-camomile-setup.exe (PID: 6472)
Create files in a temporary directory
- outbyte-camomile-setup.exe (PID: 6472)
- Installer.exe (PID: 2668)
Reads the computer name
- outbyte-camomile-setup.exe (PID: 6472)
- Installer.exe (PID: 2668)
Checks proxy server information
- outbyte-camomile-setup.exe (PID: 6472)
- Installer.exe (PID: 2668)
- slui.exe (PID: 6364)
Reads the machine GUID from the registry
- Installer.exe (PID: 2668)
Creates files or folders in the user directory
- Installer.exe (PID: 2668)
Reads the software policy settings
- Installer.exe (PID: 2668)
- slui.exe (PID: 6364)
Creates files in the program directory
- Installer.exe (PID: 2668)
Compiled with Borland Delphi (YARA)
- Installer.exe (PID: 2668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (79.7) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (8.6) |
| .exe | | | Win16/32 Executable Delphi generic (3.9) |
| .exe | | | Generic Win/DOS Executable (3.8) |
| .exe | | | DOS Executable Generic (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:14 14:08:20+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 144384 |
| InitializedDataSize: | 414208 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x24530 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.5.1.42923 |
| ProductVersionNumber: | 1.5.1.42923 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Camomile |
| CompanyName: | Outbyte |
| FileDescription: | Outbyte Camomile Installation File |
| FileVersion: | 1.5.1.42923 |
| LegalCopyright: | Copyright © 2016-2025 Outbyte Computing Pty Ltd |
| OriginalFileName: | Outbyte-camomile-setup.exe |
| ProductName: | Camomile |
| ProductVersion: | 1.x |
Total processes
133
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2668 | "C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\Installer.exe" /spid:6472 /splha:37724992 | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\Installer.exe | outbyte-camomile-setup.exe | ||||||||||||
User: admin Company: Outbyte Integrity Level: HIGH Description: Installer Version: 1.5.1.42923 Modules
| |||||||||||||||
| 5920 | "C:\Users\admin\Desktop\outbyte-camomile-setup.exe" | C:\Users\admin\Desktop\outbyte-camomile-setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Outbyte Integrity Level: MEDIUM Description: Outbyte Camomile Installation File Exit code: 3221226540 Version: 1.5.1.42923 Modules
| |||||||||||||||
| 6364 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6472 | "C:\Users\admin\Desktop\outbyte-camomile-setup.exe" | C:\Users\admin\Desktop\outbyte-camomile-setup.exe | explorer.exe | ||||||||||||
User: admin Company: Outbyte Integrity Level: HIGH Description: Outbyte Camomile Installation File Version: 1.5.1.42923 Modules
| |||||||||||||||
Total events
7 859
Read events
7 838
Write events
21
Delete events
0
Modification events
| (PID) Process: | (6472) outbyte-camomile-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | General.CustomClientId |
Value: 1036007967.299999247683 | |||
| (PID) Process: | (6472) outbyte-camomile-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | General.URLClientId |
Value: 1036007967.299999247683 | |||
| (PID) Process: | (6472) outbyte-camomile-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6472) outbyte-camomile-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6472) outbyte-camomile-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2668) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | General.TrackingIV.CID |
Value: 1460652058.1751440323 | |||
| (PID) Process: | (2668) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | General.TrackingIV.SID |
Value: RLlKmaSeez | |||
| (PID) Process: | (2668) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | Application.GAIV.FunnelDate |
Value: 77DDF9990962E640 | |||
| (PID) Process: | (2668) Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2668) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{6D484312-2A78-96B5-2103-981509CE347B}\Version |
| Operation: | write | Name: | Assembly |
Value: BE994333A9628BBEEC0B5B013C8229BBBE994333A9628BBEEC0B5B013C8229BB88AD8CBB5ED3F66B83A8A2CDF194269C890BB34AEBD806E41A50D3BD9C0B4765219909F09E75DEC0927FF4E8152284CD219909F09E75DEC0927FF4E8152284CD59B5414605BAE21E9735786EB516D3F8DE1283C2AFF9BF99D33ED2740C86BBD2F8157495FE950FA4A01046BB55F00DAD0F20AA1B1ADFE602954529934D03147D | |||
Executable files
14
Suspicious files
6
Text files
2
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6472 | outbyte-camomile-setup.exe | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\InstallerUtils.dll | executable | |
MD5:77854A0914DC89E41FEAE61761BE46C4 | SHA256:D20623730B883A451D449F99C9F9D57D229D73409DD84FA354E956D09664A043 | |||
| 6472 | outbyte-camomile-setup.exe | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\Lang\enu.lng | binary | |
MD5:B2BBAFE2B07F5CA653A4BC18B1741671 | SHA256:4383DFD855B566B82BA7C7FE079AB33FF918925A24F27BC5BA23450EFA0180E5 | |||
| 6472 | outbyte-camomile-setup.exe | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\Lang\esp.lng | binary | |
MD5:76C97AC1E76E42A815A273E01E8569FF | SHA256:591A15494C18B2F07A07E03A0520546ABCFFC4801B5D1646B79871EF58C9984E | |||
| 6472 | outbyte-camomile-setup.exe | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\GoogleAnalyticsHelperIV.dll | executable | |
MD5:4823223D90BD0BF92E770CE461374DE7 | SHA256:3B3C94366EA9D7C51994EB9DF7332965579BB998896EFD338621721B5BF21774 | |||
| 6472 | outbyte-camomile-setup.exe | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\Installer.exe | odttf | |
MD5:176EE1EA7C3FB193D8CE7CE560C24672 | SHA256:1A98506EA1C14F57DAA1825B1EEC43B19D1AC4A837DD9CEC12569D5EF743A65A | |||
| 6472 | outbyte-camomile-setup.exe | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\rtl250.bpl | executable | |
MD5:CBE607A419C5D416B85DD1304314EB73 | SHA256:E0BF4264BEA7CC76A66794DB362F11A4925DD2EF12436D7C7D9F5AEC33110C3A | |||
| 6472 | outbyte-camomile-setup.exe | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\SetupHelper.dll | executable | |
MD5:1B838687DF9C790313A34965DFABB4ED | SHA256:BDF0309AD012F4680EBA3DA0604ACA715726D02D1EEF3554BE732408AAA5DD14 | |||
| 6472 | outbyte-camomile-setup.exe | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\AxComponentsRTL.bpl | executable | |
MD5:5FF9E72FAB73E5B3025A240FA5C5A3D6 | SHA256:DB14544E9DF668A8F13C06EFCDDDF943B5F48749B765CDFDD8D8FE27BAED68FC | |||
| 6472 | outbyte-camomile-setup.exe | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\OxComponentsRTL.bpl | executable | |
MD5:57A1F050387C985162057FAC99F746E1 | SHA256:A5859582037A8A9F137FE4FFB25D672552BA19DA5F1084A102ED416BC7FBABE0 | |||
| 6472 | outbyte-camomile-setup.exe | C:\Users\admin\AppData\Local\Temp\is-15331663.tmp\vclie250.bpl | executable | |
MD5:16548A508AA0248E73BAD315D5E60256 | SHA256:666165E5542D7FAC8C0906C4BFE69C8C65CD8AE50843E11A1DA1522545B4B7E2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
41
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2668 | Installer.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.68:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
2668 | Installer.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 45.33.97.245:443 | https://outbyte.com/tools/userdata/?product=camomile | unknown | binary | 13 b | unknown |
2668 | Installer.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAwfypkv9EfKYa1bFvWpvwk%3D | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.68:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
outbyte.com |
| unknown |
www.google-analytics.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |