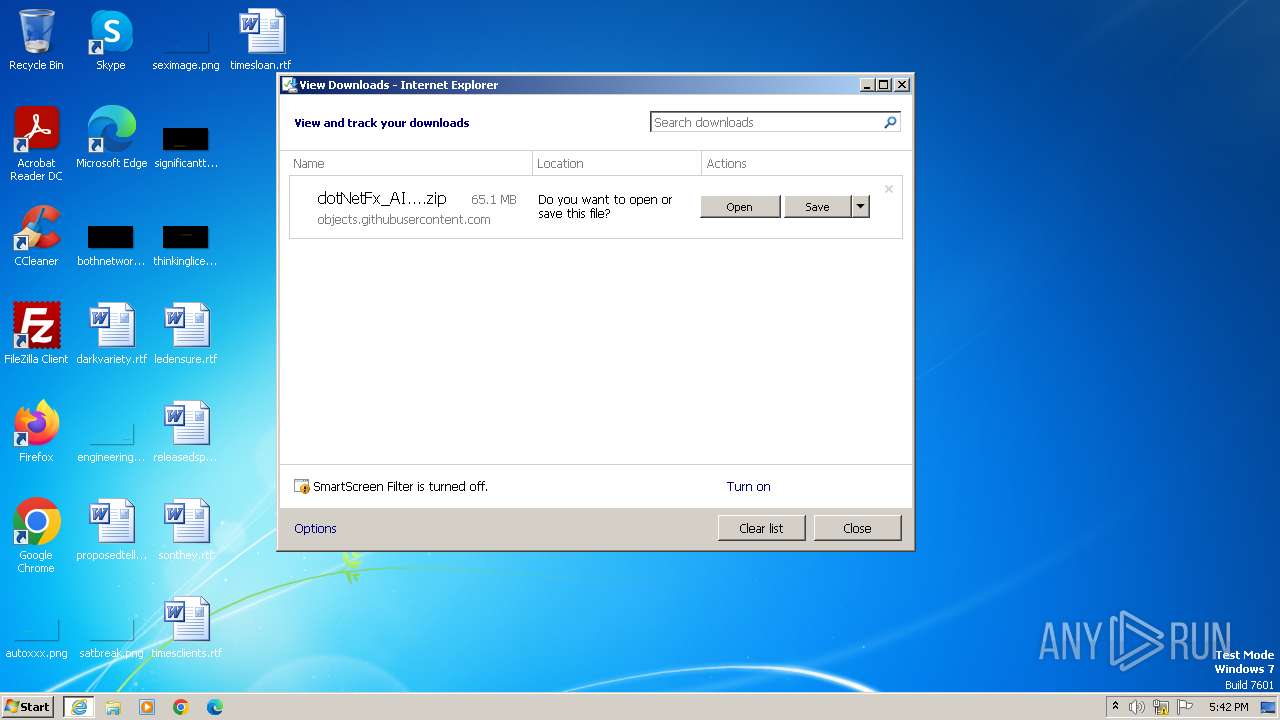
| URL: | https://github.com/abbodi1406/dotNetXP/releases/download/22.06.20/dotNetFx_AIO_x86_20220620.zip |
| Full analysis: | https://app.any.run/tasks/9ec23957-0838-46ac-a1b1-d1f7a76581d7 |
| Verdict: | Malicious activity |
| Analysis date: | November 18, 2023, 17:42:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | 33495C77DD2519EBE7E2949CD6C7232957358A0A |
| SHA256: | 931E4FB8A5956B7C45219BB1230F916437B0D9807B004599C7A1D1A8CA92B3C7 |
| SSDEEP: | 3:N8tEd0nHIVGBKRrA2AOrkCXh9rGDZYVn:2uionSnOr4iVn |
MALICIOUS
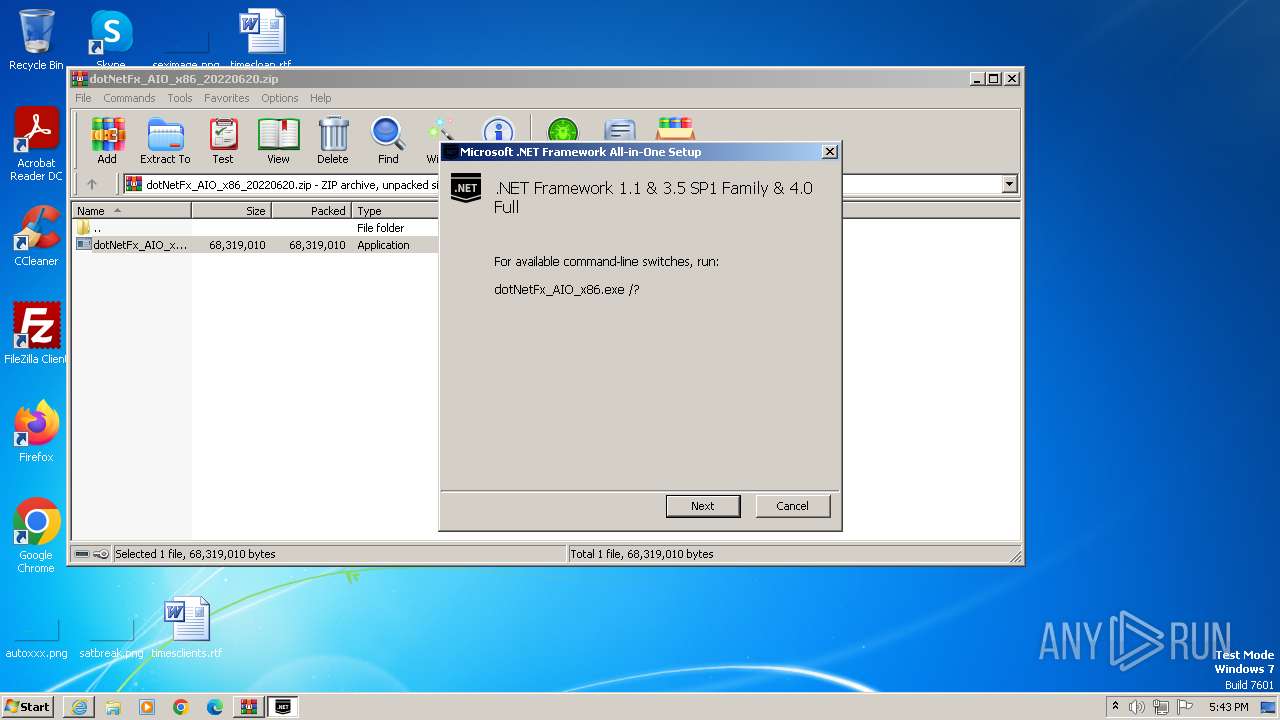
Drops the executable file immediately after the start
- dotNetFx_AIO_x86.exe (PID: 3892)
SUSPICIOUS
Process drops legitimate windows executable
- dotNetFx_AIO_x86.exe (PID: 3892)
The process creates files with name similar to system file names
- dotNetFx_AIO_x86.exe (PID: 3892)
The process drops C-runtime libraries
- dotNetFx_AIO_x86.exe (PID: 3892)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3844)
Application launched itself
- iexplore.exe (PID: 3196)
Checks supported languages
- wmpnscfg.exe (PID: 3844)
- dotNetFx_AIO_x86.exe (PID: 3892)
Reads the computer name
- wmpnscfg.exe (PID: 3844)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3844)
The process uses the downloaded file
- WinRAR.exe (PID: 3912)
- iexplore.exe (PID: 3196)
Create files in a temporary directory
- dotNetFx_AIO_x86.exe (PID: 3892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2896 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3196 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3196 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/abbodi1406/dotNetXP/releases/download/22.06.20/dotNetFx_AIO_x86_20220620.zip" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3844 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
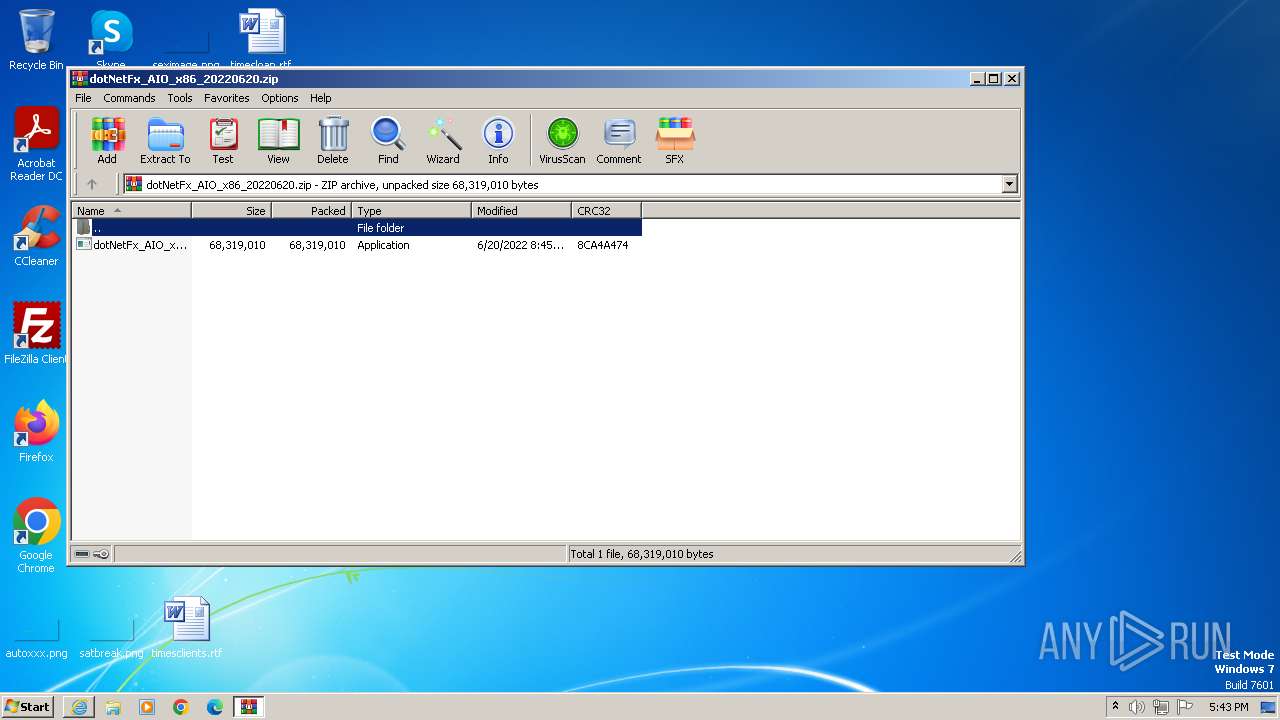
| 3892 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3912.36819\dotNetFx_AIO_x86.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3912.36819\dotNetFx_AIO_x86.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 1.1, 2.0, 3.0, 3.5, 4.0 Setup Exit code: 0 Version: 4.0.30320.0 Modules
| |||||||||||||||
| 3912 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\dotNetFx_AIO_x86_20220620.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3984 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3912.36819\dotNetFx_AIO_x86.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3912.36819\dotNetFx_AIO_x86.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 1.1, 2.0, 3.0, 3.5, 4.0 Setup Exit code: 3221226540 Version: 4.0.30320.0 Modules
| |||||||||||||||
Total events
18 968
Read events
18 881
Write events
83
Delete events
4
Modification events
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
380
Suspicious files
22
Text files
306
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\dotNetFx_AIO_x86_20220620.zip.bomsftj.partial | — | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\dotNetFx_AIO_x86_20220620.zip | — | |
MD5:— | SHA256:— | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3912.36819\dotNetFx_AIO_x86.exe | — | |
MD5:— | SHA256:— | |||
| 3892 | dotNetFx_AIO_x86.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\DNF11\netfx.msi | — | |
MD5:— | SHA256:— | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\verE757.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:96ABFAD53E91249F5AB3C43ACA7E678D | SHA256:1CE3A8B2D0467B4C8DBBABA58C0F4A961B90D979A7DD8637110517ED247661C3 | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:574181BA9BD81C92B22104851F824B77 | SHA256:E80B9F20237109A0D61D426BD306768E23D3A18C45EADE435BA23AFE92404662 | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:041B81AF7828E922F01011FC21499C34 | SHA256:93293DBC5D9AF8CE47266C856B17E5C6BEBC7782A16872D61BCC734A13645C2A | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:C21F31B4953EA9676FD18817117D6600 | SHA256:B359BAAE19D5568491A098D6C266F750C6DC527E0955CD9A230BF0621C70846D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
15
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2896 | iexplore.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b4811d0122f48a02 | unknown | compressed | 4.66 Kb | unknown |
2896 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | binary | 471 b | unknown |
2896 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | unknown | binary | 312 b | unknown |
2896 | iexplore.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e50ae344da5aee8a | unknown | compressed | 4.66 Kb | unknown |
3196 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2896 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2896 | iexplore.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2896 | iexplore.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2896 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2896 | iexplore.exe | 185.199.109.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3196 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3196 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |