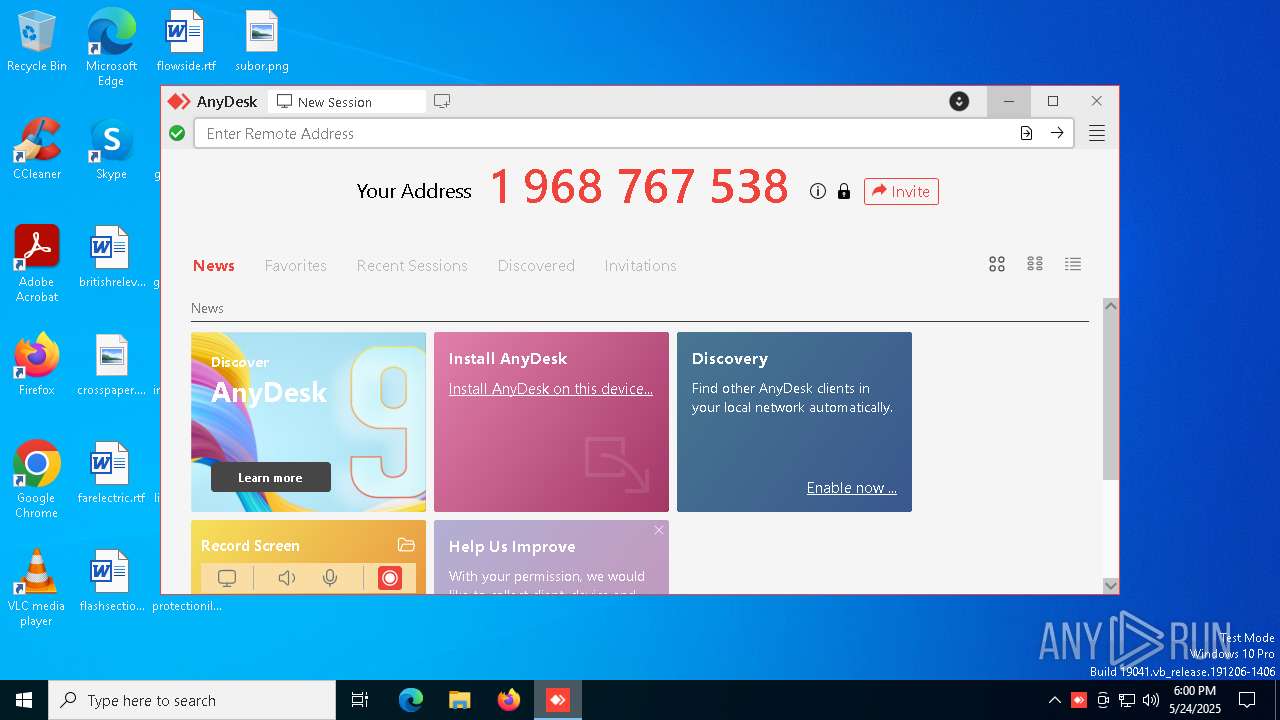
| File name: | AnyDesk.exe |
| Full analysis: | https://app.any.run/tasks/10e1c966-1624-4334-9d1e-90eb6af6460b |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 18:00:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 2B9C5F6F01A7A06BEEB533967A6E23EF |
| SHA1: | F8D4D4ACD87C6F5D9EA538850E7A7D53E2624BCA |
| SHA256: | 9303B671778422754BCF8FC97CD99F9F19173473FF515A6956BC61BC1DE84389 |
| SSDEEP: | 98304:fhUANy0hTFQ1tPyVbvPNgyQLocbud2pEQAcl6WSZFWjK/bZ8ROJeEvSt0ZAGR7VI:577oH6Ft7u8PS |
MALICIOUS
No malicious indicators.SUSPICIOUS
ANYDESK mutex has been found
- AnyDesk.exe (PID: 4696)
- AnyDesk.exe (PID: 5380)
- AnyDesk.exe (PID: 7036)
ANYDESK has been found
- AnyDesk.exe (PID: 4696)
Application launched itself
- AnyDesk.exe (PID: 4696)
INFO
Reads the computer name
- AnyDesk.exe (PID: 4696)
- AnyDesk.exe (PID: 7036)
- AnyDesk.exe (PID: 5380)
Checks supported languages
- AnyDesk.exe (PID: 4696)
- AnyDesk.exe (PID: 7036)
- AnyDesk.exe (PID: 5380)
The sample compiled with english language support
- AnyDesk.exe (PID: 4696)
Creates files or folders in the user directory
- AnyDesk.exe (PID: 4696)
- AnyDesk.exe (PID: 7036)
- AnyDesk.exe (PID: 5380)
Process checks whether UAC notifications are on
- AnyDesk.exe (PID: 4696)
Reads the machine GUID from the registry
- AnyDesk.exe (PID: 7036)
- AnyDesk.exe (PID: 4696)
Reads CPU info
- AnyDesk.exe (PID: 5380)
Checks proxy server information
- AnyDesk.exe (PID: 5380)
Manual execution by a user
- WINWORD.EXE (PID: 5392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:12 11:31:03+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 10752 |
| InitializedDataSize: | 7743488 |
| UninitializedDataSize: | 28073984 |
| EntryPoint: | 0x3653 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.5.4.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | AnyDesk Software GmbH |
| FileDescription: | AnyDesk |
| FileVersion: | 9.5.4 |
| ProductName: | AnyDesk |
| ProductVersion: | 9.5 |
| LegalCopyright: | (C) 2025 AnyDesk Software GmbH |
Total processes
137
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4696 | "C:\Users\admin\AppData\Local\Temp\AnyDesk.exe" | C:\Users\admin\AppData\Local\Temp\AnyDesk.exe | — | explorer.exe | |||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 0 Version: 9.5.4 Modules
| |||||||||||||||
| 5380 | "C:\Users\admin\AppData\Local\Temp\AnyDesk.exe" --local-control | C:\Users\admin\AppData\Local\Temp\AnyDesk.exe | — | AnyDesk.exe | |||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 0 Version: 9.5.4 Modules
| |||||||||||||||
| 5392 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\licenseprint.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6156 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "BB1CF9D6-84AD-4E58-99C7-85EB8238B977" "7ECD2A3C-150D-49BD-A715-CEE7DA687897" "5392" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 6652 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7036 | "C:\Users\admin\AppData\Local\Temp\AnyDesk.exe" --local-service | C:\Users\admin\AppData\Local\Temp\AnyDesk.exe | AnyDesk.exe | ||||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 0 Version: 9.5.4 Modules
| |||||||||||||||
Total events
14 754
Read events
14 402
Write events
332
Delete events
20
Modification events
| (PID) Process: | (5392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (5392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\5392 |
| Operation: | write | Name: | 0 |
Value: 0B0E10FDDD24BCD7E4064AA3BA470D464322FA230046B2F187A7DD9AF3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511902AD2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (5392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (5392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (5392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (5392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (5392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (5392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (5392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
33
Suspicious files
137
Text files
196
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4696 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\system.conf~RF10aad8.TMP | — | |
MD5:— | SHA256:— | |||
| 4696 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\user.conf~RF10aae8.TMP | — | |
MD5:— | SHA256:— | |||
| 4696 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\user.conf~RF10ab84.TMP | — | |
MD5:— | SHA256:— | |||
| 4696 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\user.conf~RF10abf1.TMP | — | |
MD5:— | SHA256:— | |||
| 4696 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\user.conf~RF10ac20.TMP | — | |
MD5:— | SHA256:— | |||
| 4696 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\user.conf~RF10ad59.TMP | — | |
MD5:— | SHA256:— | |||
| 4696 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\user.conf~RF10ad68.TMP | — | |
MD5:— | SHA256:— | |||
| 7036 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\system.conf~RF10b7c9.TMP | — | |
MD5:— | SHA256:— | |||
| 5380 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\user.conf~RF10b865.TMP | — | |
MD5:— | SHA256:— | |||
| 5380 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\user.conf~RF10b874.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
61
DNS requests
30
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5392 | WINWORD.EXE | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
5392 | WINWORD.EXE | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5392 | WINWORD.EXE | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
5392 | WINWORD.EXE | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
5392 | WINWORD.EXE | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5392 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5744 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5796 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7036 | AnyDesk.exe | 57.128.101.74:443 | boot.net.anydesk.com | OVH SAS | FR | whitelisted |
7036 | AnyDesk.exe | 195.181.174.176:443 | relay-7fe0f546.net.anydesk.com | Datacamp Limited | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
boot.net.anydesk.com |
| whitelisted |
relay-7fe0f546.net.anydesk.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET REMOTE_ACCESS Anydesk Relay Domain (net .anydesk .com) in DNS Lookup |
2196 | svchost.exe | Misc activity | ET REMOTE_ACCESS Anydesk Domain (boot .net .anydesk .com) in DNS Lookup |
2196 | svchost.exe | Misc activity | ET REMOTE_ACCESS Anydesk Relay Domain (net .anydesk .com) in DNS Lookup |