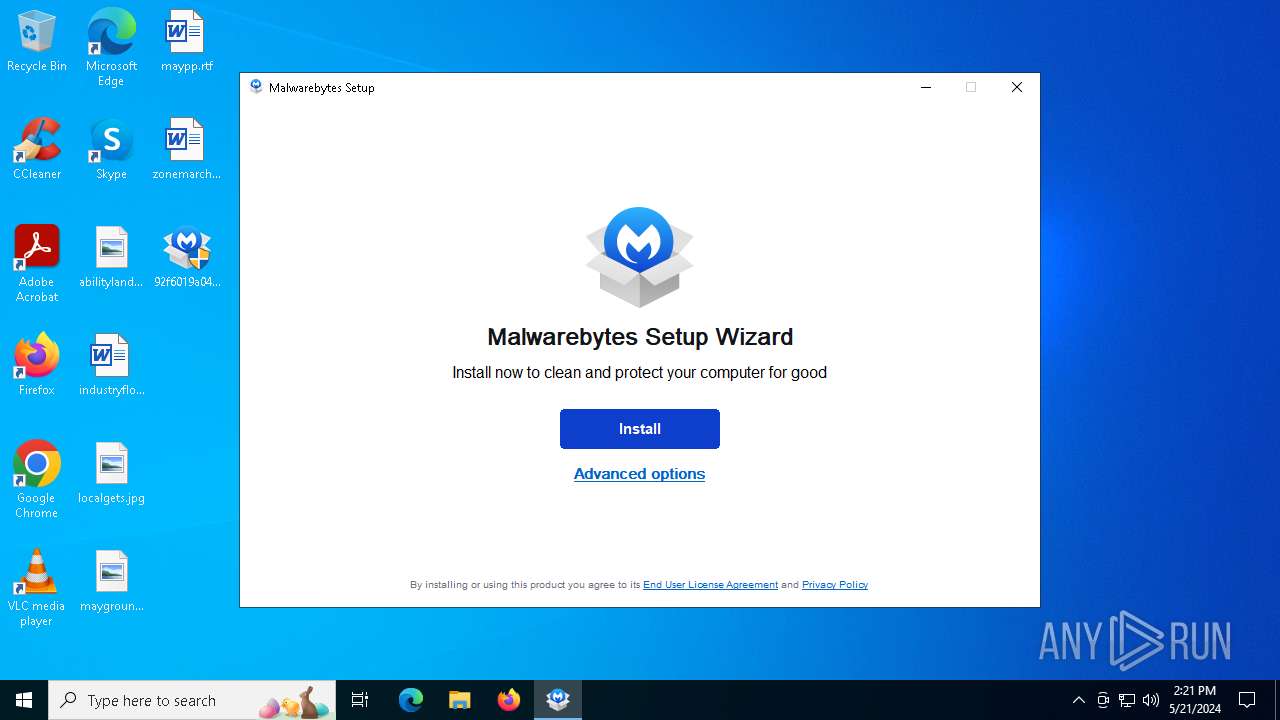
| File name: | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe |
| Full analysis: | https://app.any.run/tasks/60018138-a4f6-4b36-b00f-a6b26c2c56d2 |
| Verdict: | Malicious activity |
| Threats: | DarkGate is a loader, which possesses extensive functionality, ranging from keylogging to crypto mining. Written in Delphi, this malware is known for the use of AutoIT scripts in its infection process. Thanks to this malicious software’s versatile architecture, it is widely used by established threat actors. |
| Analysis date: | May 21, 2024, 14:20:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0B8BC95983C20FE0A4D6DA5D0D02BBF0 |
| SHA1: | F0F1F39F581E64F48D857455E827E4AB99E176DD |
| SHA256: | 92F6019A04B29F6CD676706E49A554E0885FF2FCD8C19734A33633395CBB888E |
| SSDEEP: | 98304:6Wn8nBa4ZfPM5t0X1N9i22IT1PD2222222721vFdGBeQN0aFvGSSRkrlcfABLqI9:pX+fX |
MALICIOUS
Creates a writable file in the system directory
- armsvc.exe (PID: 4284)
- msdtc.exe (PID: 6828)
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
Drops the executable file immediately after the start
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
- armsvc.exe (PID: 4284)
Actions looks like stealing of personal data
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
- armsvc.exe (PID: 4284)
- alg.exe (PID: 5860)
- SearchIndexer.exe (PID: 7568)
Connects to the CnC server
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
SUSPICIOUS
Executes as Windows Service
- armsvc.exe (PID: 4284)
- FlashPlayerUpdateService.exe (PID: 712)
- alg.exe (PID: 5860)
- MicrosoftEdgeUpdate.exe (PID: 3104)
- DiagnosticsHub.StandardCollector.Service.exe (PID: 5092)
- AppVClient.exe (PID: 4216)
- FXSSVC.exe (PID: 4216)
- GameInputSvc.exe (PID: 6252)
- GoogleUpdate.exe (PID: 6464)
- maintenanceservice.exe (PID: 6748)
- msdtc.exe (PID: 6828)
- perfhost.exe (PID: 7100)
- MicrosoftEdgeUpdate.exe (PID: 7132)
- PSEXESVC.exe (PID: 6244)
- PerceptionSimulationService.exe (PID: 7032)
- Locator.exe (PID: 6284)
- SensorDataService.exe (PID: 6520)
- snmptrap.exe (PID: 6796)
- ssh-agent.exe (PID: 6552)
- Spectrum.exe (PID: 6972)
- GoogleUpdate.exe (PID: 8108)
- TieringEngineService.exe (PID: 7200)
- vds.exe (PID: 7332)
- AgentService.exe (PID: 7296)
- wbengine.exe (PID: 7428)
- VSSVC.exe (PID: 7364)
- WmiApSrv.exe (PID: 7480)
Searches for installed software
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
Reads the BIOS version
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
Application launched itself
- MicrosoftEdgeUpdate.exe (PID: 3104)
- MicrosoftEdgeUpdate.exe (PID: 4484)
- GameInputSvc.exe (PID: 6252)
- GoogleUpdate.exe (PID: 6464)
- GoogleUpdate.exe (PID: 6580)
- MicrosoftEdgeUpdate.exe (PID: 7132)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 5536)
- MicrosoftEdgeUpdate.exe (PID: 5076)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6348)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6260)
Process drops legitimate windows executable
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
- armsvc.exe (PID: 4284)
Executable content was dropped or overwritten
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
- armsvc.exe (PID: 4284)
Creates files in the driver directory
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
Contacting a server suspected of hosting an CnC
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
INFO
Reads the computer name
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
- armsvc.exe (PID: 4284)
- FlashPlayerUpdateService.exe (PID: 712)
- MicrosoftEdgeUpdate.exe (PID: 3104)
- MicrosoftEdgeUpdate.exe (PID: 4484)
- MicrosoftEdgeUpdate.exe (PID: 5076)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 5536)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6260)
- MicrosoftEdgeUpdate.exe (PID: 6428)
- GoogleUpdate.exe (PID: 6580)
- elevation_service.exe (PID: 6376)
- GoogleUpdate.exe (PID: 6464)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6348)
- elevation_service.exe (PID: 6644)
- GoogleUpdate.exe (PID: 6668)
- GoogleCrashHandler.exe (PID: 6708)
- maintenanceservice.exe (PID: 6748)
- GoogleCrashHandler64.exe (PID: 6768)
- GoogleUpdate.exe (PID: 6848)
- MicrosoftEdgeUpdate.exe (PID: 7132)
- PSEXESVC.exe (PID: 6244)
- MicrosoftEdgeUpdate.exe (PID: 5744)
- ssh-agent.exe (PID: 6552)
- GoogleUpdate.exe (PID: 8108)
Create files in a temporary directory
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
Checks supported languages
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
- armsvc.exe (PID: 4284)
- FlashPlayerUpdateService.exe (PID: 712)
- MicrosoftEdgeUpdate.exe (PID: 3104)
- MicrosoftEdgeUpdate.exe (PID: 4484)
- MicrosoftEdgeUpdate.exe (PID: 5076)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 5536)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6260)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6348)
- MicrosoftEdgeUpdate.exe (PID: 6428)
- elevation_service.exe (PID: 6376)
- GoogleUpdate.exe (PID: 6464)
- GoogleUpdate.exe (PID: 6580)
- elevation_service.exe (PID: 6644)
- GoogleUpdate.exe (PID: 6668)
- GoogleCrashHandler.exe (PID: 6708)
- maintenanceservice.exe (PID: 6748)
- GoogleCrashHandler64.exe (PID: 6768)
- GoogleUpdate.exe (PID: 6848)
- MicrosoftEdgeUpdate.exe (PID: 7132)
- PSEXESVC.exe (PID: 6244)
- MicrosoftEdgeUpdate.exe (PID: 5744)
- ssh-agent.exe (PID: 6552)
- GoogleUpdate.exe (PID: 8108)
Creates files or folders in the user directory
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
- GoogleUpdate.exe (PID: 6668)
Reads the machine GUID from the registry
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
- GoogleUpdate.exe (PID: 6668)
- GoogleUpdate.exe (PID: 8108)
Reads the software policy settings
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
- GameInputSvc.exe (PID: 6308)
- GoogleUpdate.exe (PID: 6668)
- MicrosoftEdgeUpdate.exe (PID: 5744)
- MicrosoftEdgeUpdate.exe (PID: 7132)
- GoogleUpdate.exe (PID: 8108)
Creates files in the program directory
- FXSSVC.exe (PID: 4216)
- GoogleUpdate.exe (PID: 6464)
- GoogleUpdate.exe (PID: 6580)
- GoogleUpdate.exe (PID: 6668)
- maintenanceservice.exe (PID: 6748)
- GoogleUpdate.exe (PID: 6848)
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
- SearchIndexer.exe (PID: 7568)
- GoogleUpdate.exe (PID: 8108)
Executes as Windows Service
- elevation_service.exe (PID: 6376)
- elevation_service.exe (PID: 6644)
- SearchIndexer.exe (PID: 7568)
Checks proxy server information
- 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe (PID: 6112)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 5744)
Checks transactions between databases Windows and Oracle
- msdtc.exe (PID: 6828)
Reads the time zone
- TieringEngineService.exe (PID: 7200)
Reads security settings of Internet Explorer
- SearchProtocolHost.exe (PID: 7852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:04:22 21:17:20+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 750080 |
| InitializedDataSize: | 1796608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6ee6e |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.1.4.89 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Malwarebytes |
| FileDescription: | Malwarebytes Setup |
| FileVersion: | 5.1.4.89 |
| LegalCopyright: | Copyright (C) 2017 - 2024 Malwarebytes, Inc. All rights reserved. |
| InternalName: | MBSetup.exe |
| OriginalFileName: | MBSetup.exe |
| ProductName: | Malwarebytes |
Total processes
171
Monitored processes
49
Malicious processes
3
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | C:\WINDOWS\SysWOW64\Macromed\Flash\FlashPlayerUpdateService.exe | C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerUpdateService.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Adobe Integrity Level: SYSTEM Description: Adobe® Flash® Player Update Service 32.0 r0 Exit code: 0 Version: 32,0,0,465 Modules
| |||||||||||||||
| 3104 | "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /svc | C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.147.37 Modules
| |||||||||||||||
| 3872 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 4216 | C:\WINDOWS\system32\AppVClient.exe | C:\Windows\System32\AppVClient.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Application Virtualization Client Service Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4216 | C:\WINDOWS\system32\fxssvc.exe | C:\Windows\System32\FXSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Fax Service Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4284 | "C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\armsvc.exe" | C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\armsvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Adobe Inc. Integrity Level: SYSTEM Description: Acrobat Update Service Version: 1.824.460.1042 Modules
| |||||||||||||||
| 4288 | "C:\Users\admin\Desktop\92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe" | C:\Users\admin\Desktop\92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | — | explorer.exe | |||||||||||
User: admin Company: Malwarebytes Integrity Level: MEDIUM Description: Malwarebytes Setup Exit code: 3221226540 Version: 5.1.4.89 Modules
| |||||||||||||||
| 4484 | "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /c | C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Edge Update Version: 1.3.147.37 Modules
| |||||||||||||||
| 5076 | "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /regserver | C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.147.37 Modules
| |||||||||||||||
| 5092 | C:\WINDOWS\system32\DiagSvcs\DiagnosticsHub.StandardCollector.Service.exe | C:\Windows\System32\DiagSvcs\DiagnosticsHub.StandardCollector.Service.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft (R) Diagnostics Hub Standard Collector Version: 11.00.19041.3930 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
41 799
Read events
35 632
Write events
6 076
Delete events
91
Modification events
| (PID) Process: | (6112) 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Malwarebytes |
| Operation: | write | Name: | id |
Value: 6f3fa464972e46499969ace0bd5733fc | |||
| (PID) Process: | (6112) 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Malwarebytes |
| Operation: | write | Name: | id |
Value: 6f3fa464972e46499969ace0bd5733fc | |||
| (PID) Process: | (4284) armsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Adobe\Adobe ARM\1.0\ARM |
| Operation: | write | Name: | iLastSvcSuccess |
Value: 1132250 | |||
| (PID) Process: | (3104) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\UsageStats\Daily\Integers |
| Operation: | write | Name: | omaha_version |
Value: 1100B90003000100 | |||
| (PID) Process: | (3104) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\UsageStats\Daily\Booleans |
| Operation: | write | Name: | is_system_install |
Value: 01000000 | |||
| (PID) Process: | (3104) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\UsageStats\Daily\Counts |
| Operation: | write | Name: | goopdate_main |
Value: 1500000000000000 | |||
| (PID) Process: | (3104) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\UsageStats\Daily\Counts |
| Operation: | write | Name: | goopdate_constructor |
Value: 1500000000000000 | |||
| (PID) Process: | (3104) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\UsageStats\Daily\Integers |
| Operation: | write | Name: | windows_major_version |
Value: 0A00000000000000 | |||
| (PID) Process: | (4484) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | InstallTime |
Value: | |||
| (PID) Process: | (4484) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientState\{F3017226-FE2A-4295-8BDF-00C3A9A7E4C5} |
| Operation: | write | Name: | InstallTime |
Value: | |||
Executable files
149
Suspicious files
4
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | C:\WINDOWS\SysWOW64\Macromed\Flash\FlashPlayerUpdateService.exe | executable | |
MD5:226E16E60BFA65098DABA2FCC09F889C | SHA256:E99D65605F7AE171F25066D86588CC0E52AF116EDFCC268CCC2DB74F95486208 | |||
| 6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | C:\WINDOWS\System32\GameInputSvc.exe | executable | |
MD5:F54B5D48868E1BF14ADAE8E0961B0D15 | SHA256:3809136DFA3228B82F753A010C144B1C8A3FF573643FB8E4239CD5FB21377502 | |||
| 6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | executable | |
MD5:06E88025AE1C4ED0302F58B5819ECF16 | SHA256:3656CA54A4E017E345E8E72283B0A4F09D9BE7300F8F138B44A0F087BF3BD0C7 | |||
| 6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\elevation_service.exe | executable | |
MD5:9FAF2F8E3BB93459538D7BED2A26D8BA | SHA256:86CE4A6A3E3C718C36CBA4A1150C197B04144087097131A03997644426B1F8FF | |||
| 6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | C:\Program Files\Google\Chrome\Application\122.0.6261.70\elevation_service.exe | executable | |
MD5:BEE89FB69AA27DE9B94175E47A0B9FAC | SHA256:CB7DBF800EA9CCB6D037EFA8476B3A11A8968C03167F6DDD3EDF13817118215A | |||
| 6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | C:\WINDOWS\system32\AppVClient.exe | executable | |
MD5:035ED1A978C55505916448212DD941AE | SHA256:E366F0BB327A7DCA10C1643903D560BDD431C4371697026F0F33FF6A63E8D4E4 | |||
| 6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | C:\Users\admin\AppData\Roaming\26b799fa89ba8c8f.bin | binary | |
MD5:5F9A48CE19855B619ABF06A0CDF84AFD | SHA256:6E737B809FCA61C6D05800A611B588563B0A50B7600F7BEF122EF1887818012E | |||
| 6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | C:\WINDOWS\System32\alg.exe | executable | |
MD5:AF4622B6ABA246A90C1F92F73E0E3FDA | SHA256:D1E2D4BB04B5B2DD352895BEBDAA3A93F425300E40DD0F48D936456A04D3372A | |||
| 6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | C:\WINDOWS\system32\fxssvc.exe | executable | |
MD5:92BA8C844DB140332E4C09543CEF3203 | SHA256:A989158172490B845D22948608D796694984D035C288C546CF0AEB7BB9B69AFF | |||
| 4284 | armsvc.exe | C:\WINDOWS\SysWOW64\config\systemprofile\AppData\Roaming\26b799fa89ba8c8f.bin | binary | |
MD5:16CC18F042CAC2064F8C140EF7678EB5 | SHA256:0AC8DB01D9DE6C8BC3DE4391C1F7F054EB3976D98AF8813CD73288FC7103DD91 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
194
TCP/UDP connections
65
DNS requests
33
Threats
34
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | POST | 200 | 35.91.124.102:80 | http://pywolwnvd.biz/tswjewijdfokpvf | unknown | — | — | unknown |
6668 | GoogleUpdate.exe | GET | 204 | 142.250.185.206:443 | https://clients2.google.com/service/check2?crx3=true&appid=%7B430FD4D0-B729-4F61-AA34-91526481799D%7D&appversion=1.3.36.372&applang=&machine=1&version=1.3.36.372&userid=&osversion=10.0&servicepack= | unknown | — | — | unknown |
4284 | armsvc.exe | POST | 200 | 35.91.124.102:80 | http://pywolwnvd.biz/tswjewijdfokpvf | unknown | — | — | unknown |
6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | POST | — | 18.141.10.107:80 | http://ssbzmoy.biz/fkgftkhhaqorgr | unknown | — | — | unknown |
4284 | armsvc.exe | POST | 200 | 18.141.10.107:80 | http://ssbzmoy.biz/oa | unknown | — | — | unknown |
4428 | RUXIMICS.exe | GET | 200 | 92.123.77.26:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4284 | armsvc.exe | POST | 200 | 54.244.188.177:80 | http://cvgrf.biz/ebanaqrokjquwa | unknown | — | — | unknown |
4428 | RUXIMICS.exe | GET | 200 | 95.100.245.144:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4284 | armsvc.exe | POST | — | 54.157.24.8:80 | http://przvgke.biz/yvd | unknown | — | — | unknown |
6816 | svchost.exe | HEAD | 204 | 142.250.185.206:443 | https://clients2.google.com/service/check2?crx3=true&appid=%7B430FD4D0-B729-4F61-AA34-91526481799D%7D&appversion=1.3.36.372&applang=&machine=1&version=1.3.36.372&userid=&osversion=10.0&servicepack= | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5228 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4428 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5140 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | 54.203.47.28:443 | api2.amplitude.com | AMAZON-02 | US | unknown |
6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | 35.91.124.102:80 | pywolwnvd.biz | AMAZON-02 | US | unknown |
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4284 | armsvc.exe | 35.91.124.102:80 | pywolwnvd.biz | AMAZON-02 | US | unknown |
6668 | GoogleUpdate.exe | 142.250.185.206:443 | clients2.google.com | GOOGLE | US | whitelisted |
6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | 18.141.10.107:80 | ssbzmoy.biz | AMAZON-02 | SG | unknown |
4284 | armsvc.exe | 18.141.10.107:80 | ssbzmoy.biz | AMAZON-02 | SG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
api2.amplitude.com |
| whitelisted |
pywolwnvd.biz |
| unknown |
clients2.google.com |
| whitelisted |
ssbzmoy.biz |
| unknown |
config.edge.skype.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
msedge.api.cdp.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
cvgrf.biz |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2184 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2184 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2184 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value Snkz |
6112 | 92f6019a04b29f6cd676706e49a554e0885ff2fcd8c19734a33633395cbb888e.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value btst |
4284 | armsvc.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value Snkz |
4284 | armsvc.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value btst |
2184 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2184 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value Snkz |
3 ETPRO signatures available at the full report