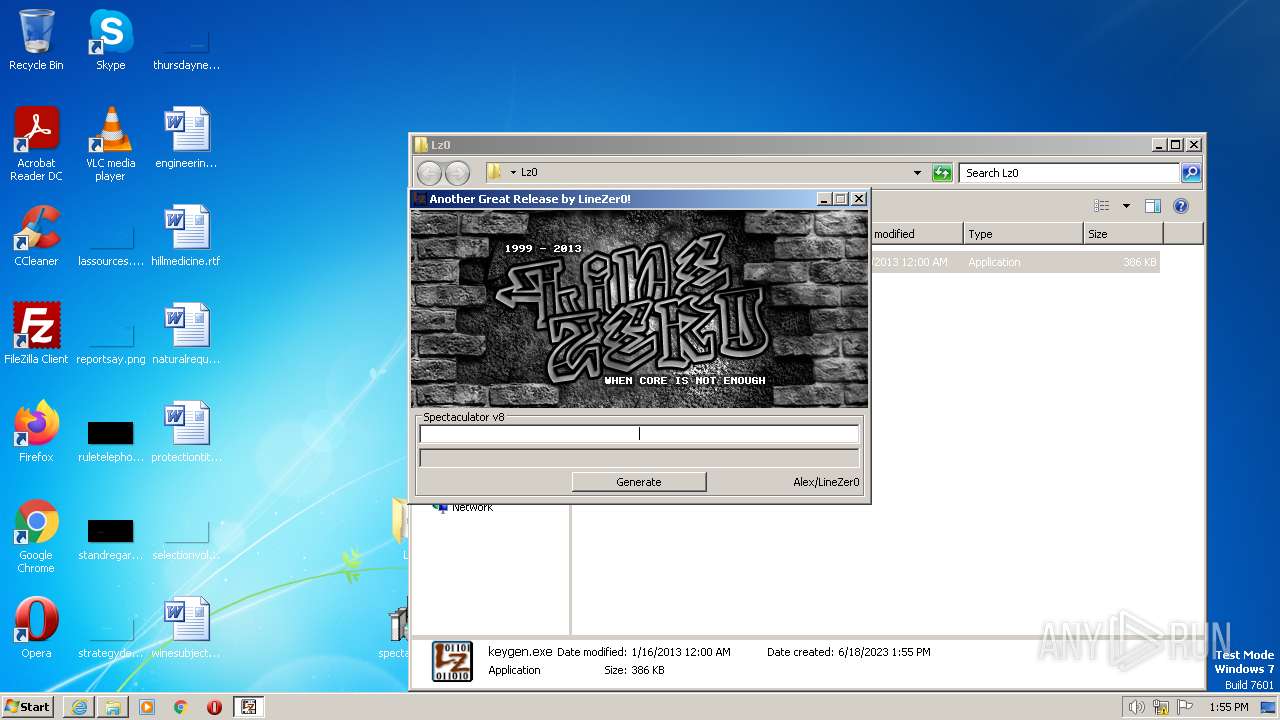
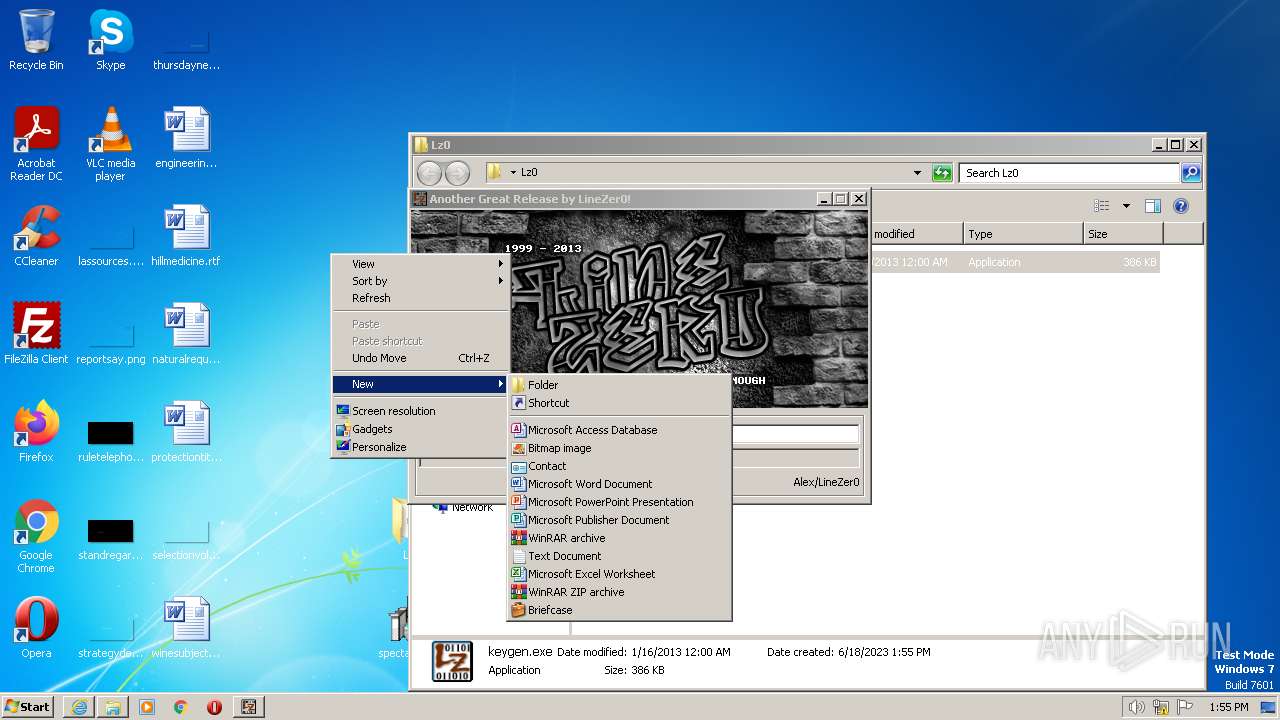
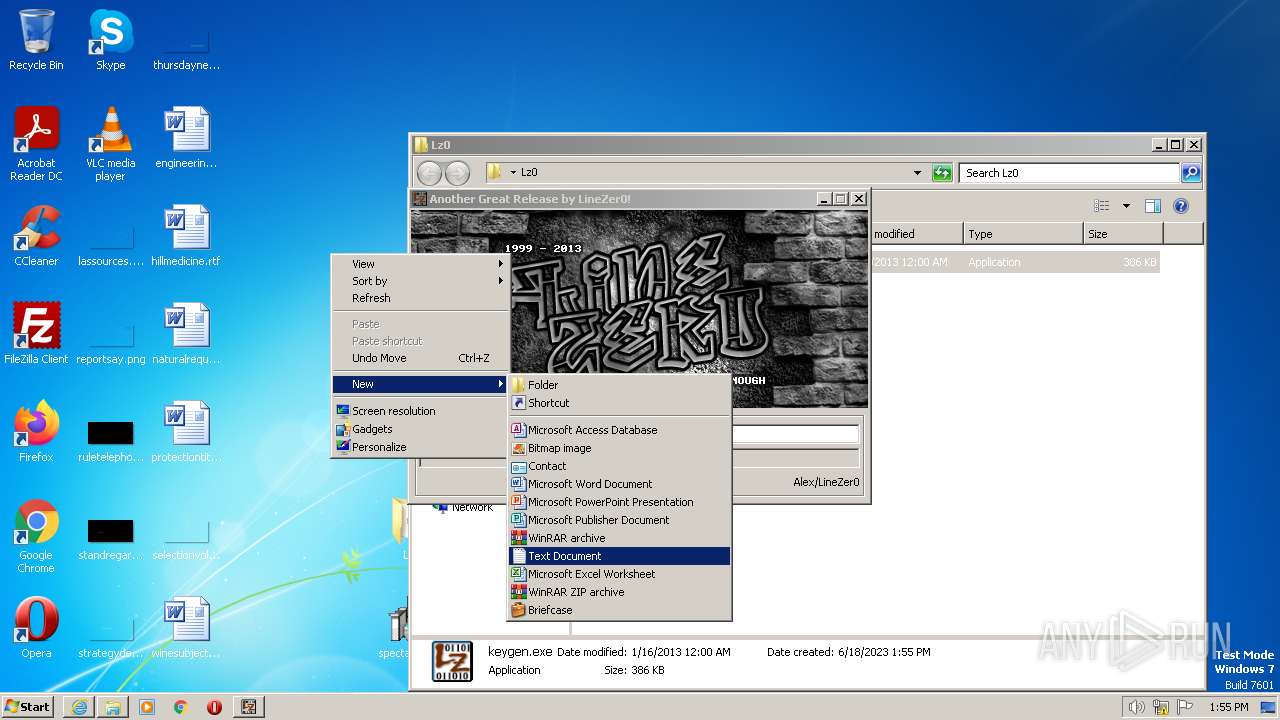
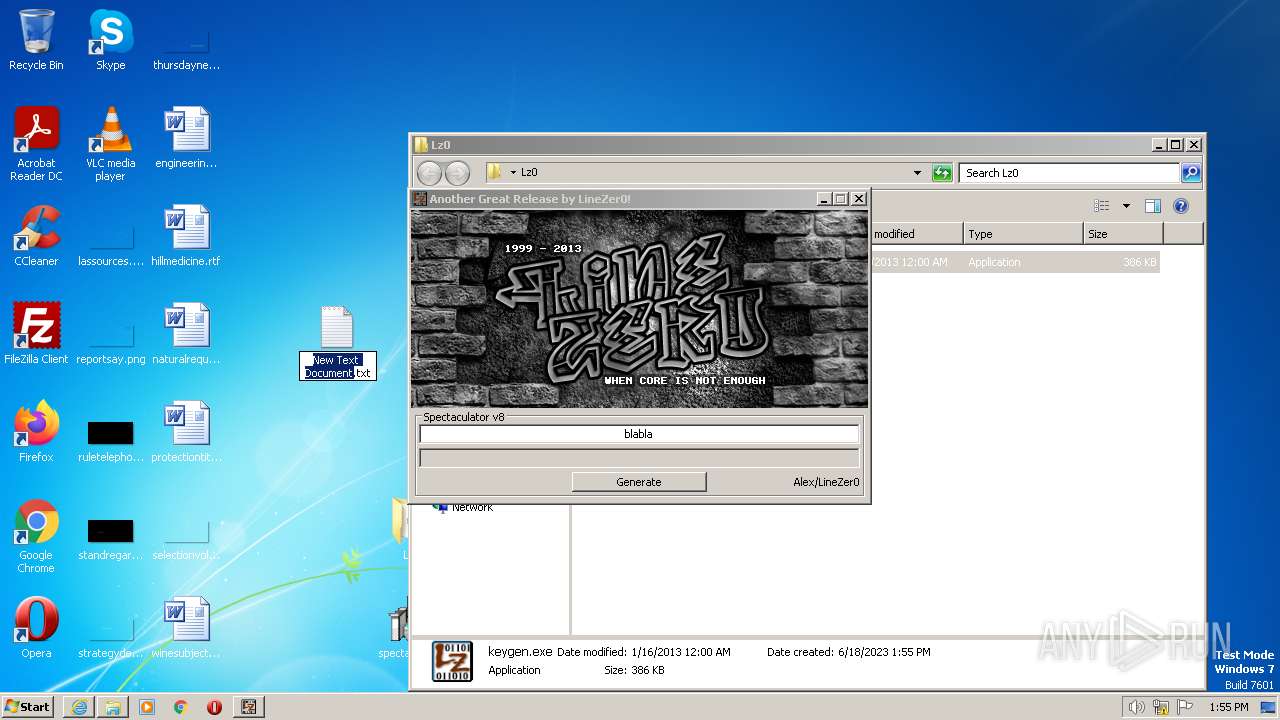
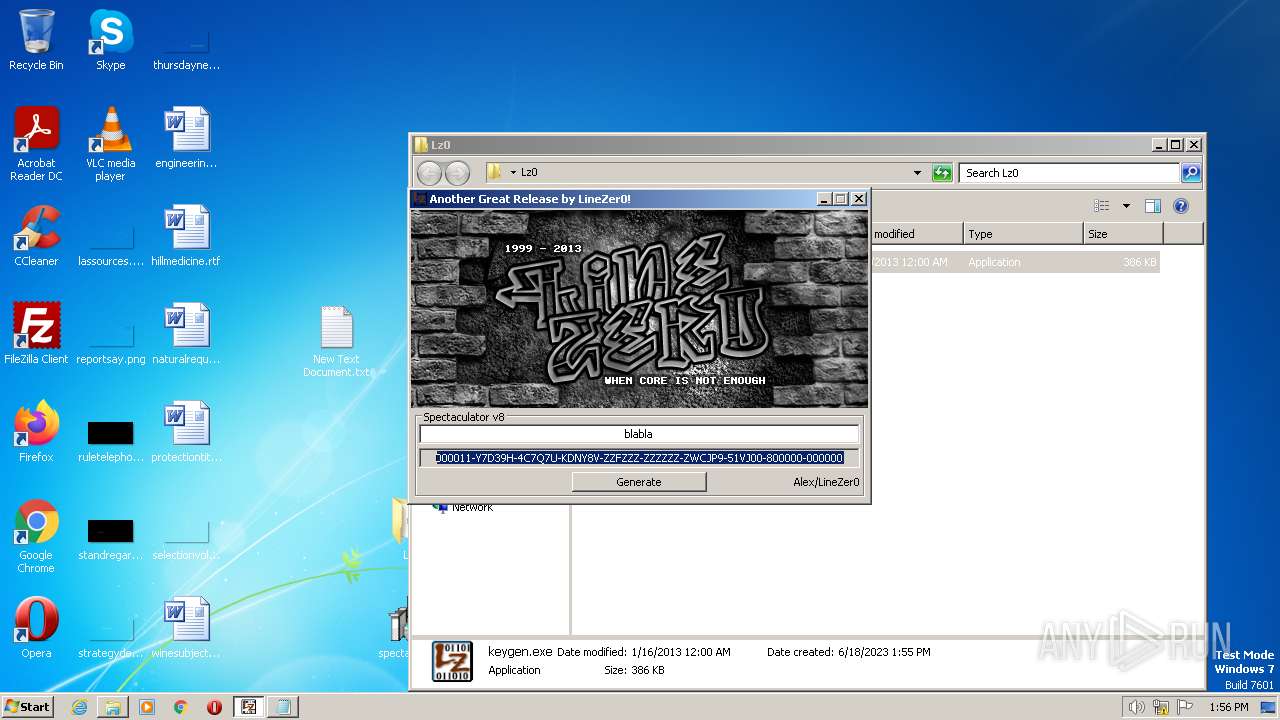
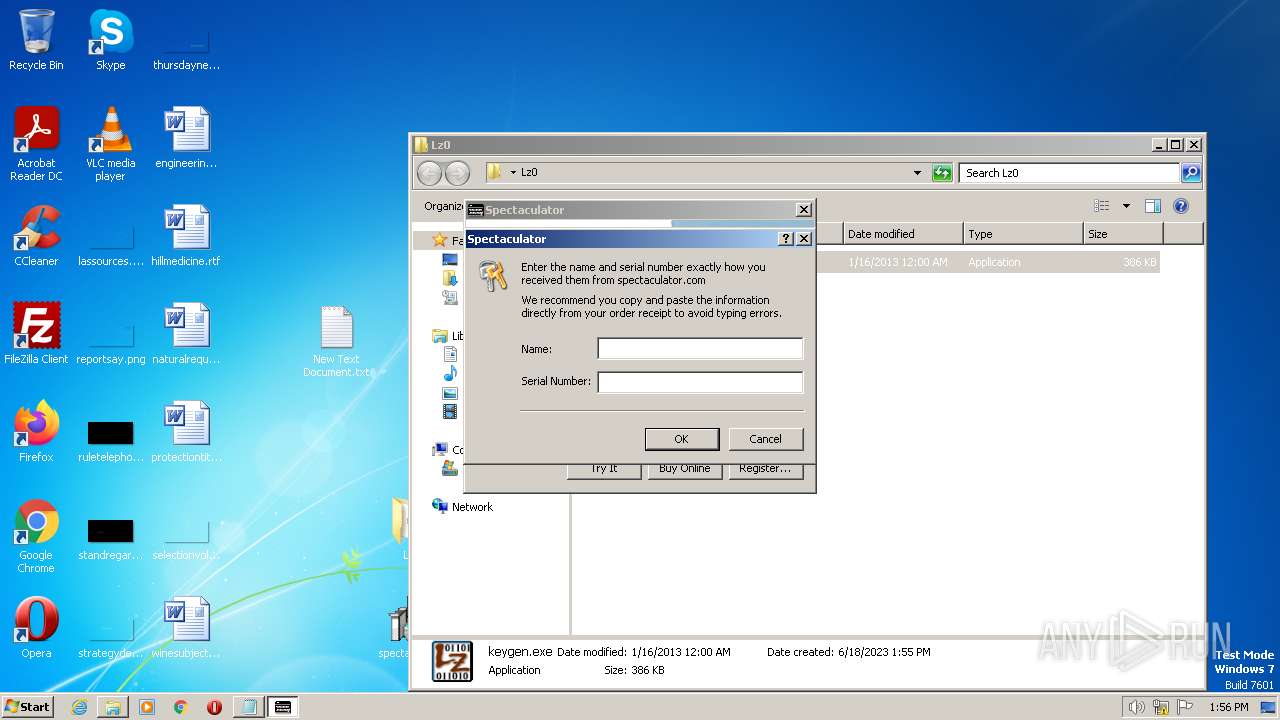
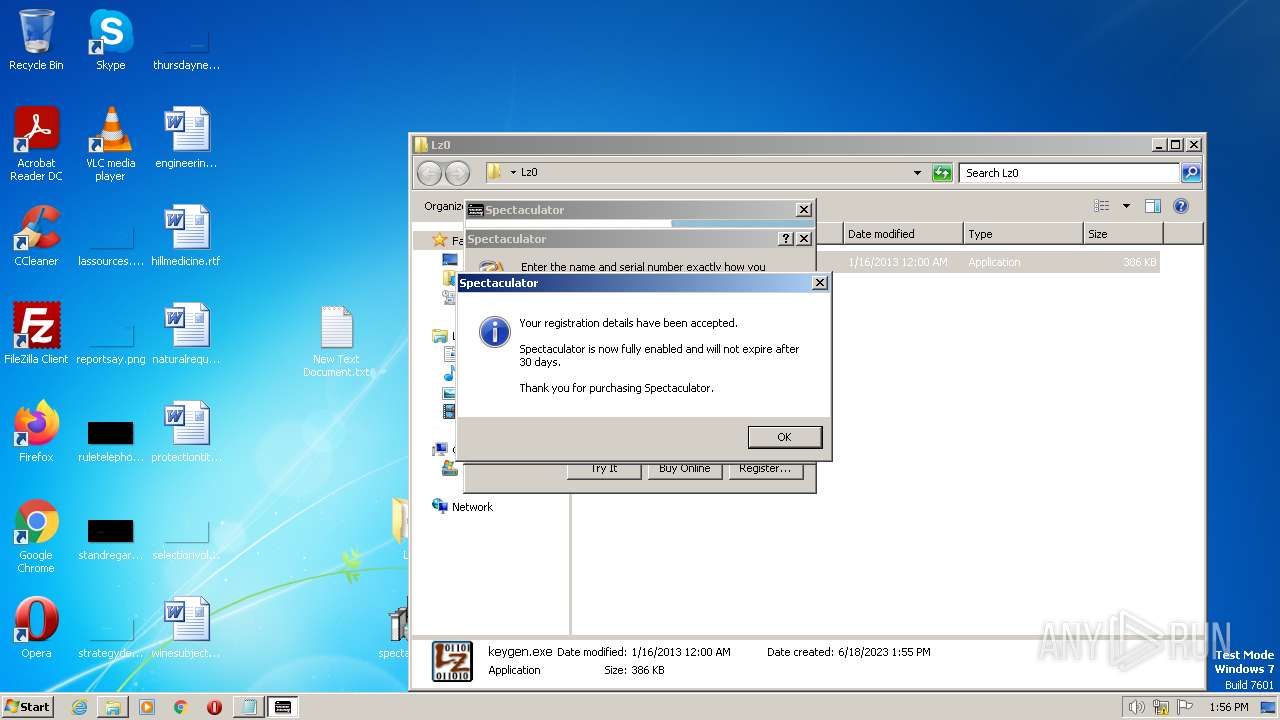
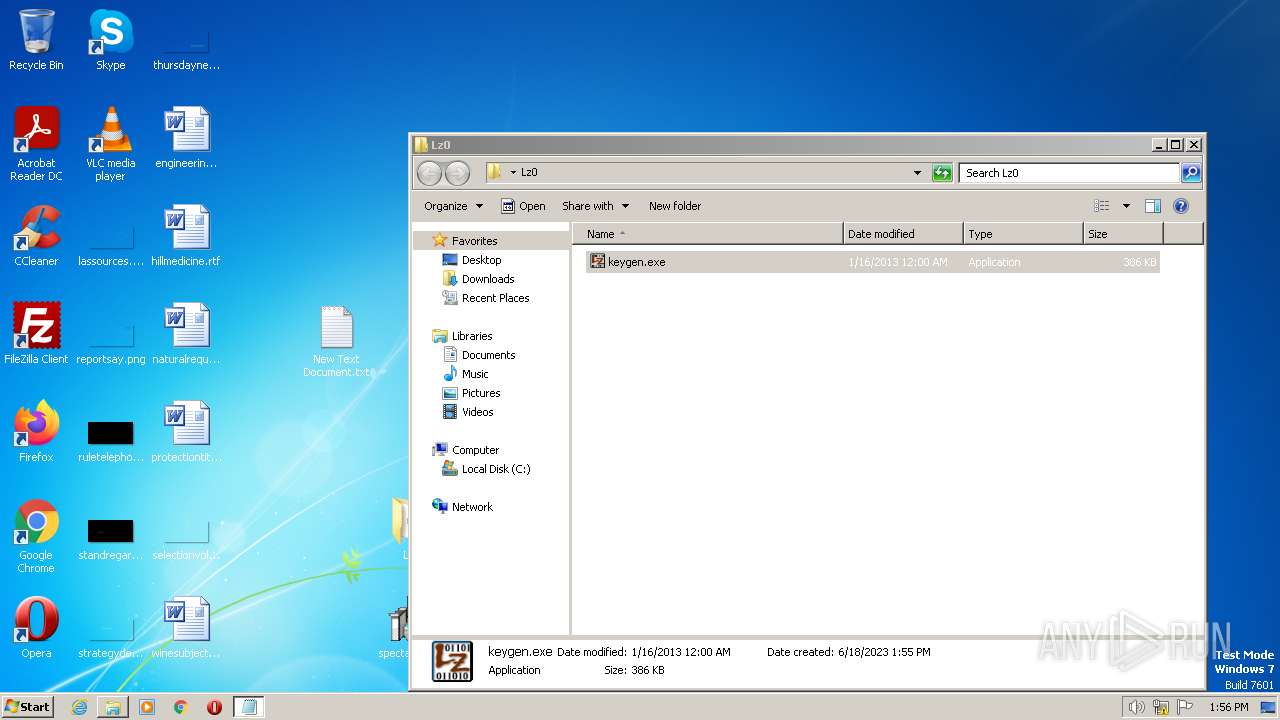
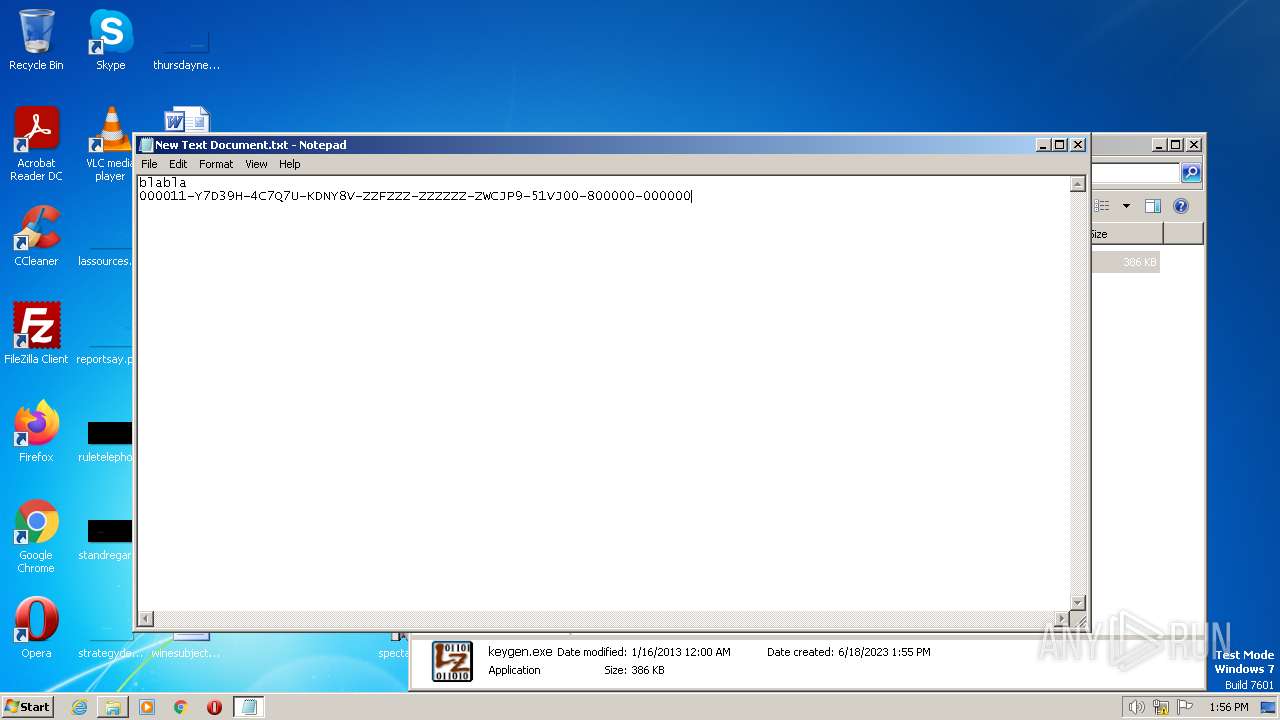
| File name: | Spectaculator.v8.0.Incl.Keygen-Lz0.rar |
| Full analysis: | https://app.any.run/tasks/fdbc003c-eb1d-4dcd-a7d9-e9f3e2c80521 |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2023, 12:54:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v2.0, os: Unix |
| MD5: | 2F117C1B5A4C04A2A707573A0D0010F1 |
| SHA1: | 87781B3561EA0DA3E22480DDFE173F89851C5147 |
| SHA256: | 92F0F5409B547C57CB0EE65DC4D7A18EB1D868ED7673C35F821FD9889C5739C4 |
| SSDEEP: | 98304:lr4Iq5UC/RO+7QFA87AGBbtiGRBKPTKqnmzEM:NUn/RP7WAyhbtiGR6WqnfM |
MALICIOUS
Loads dropped or rewritten executable
- msiexec.exe (PID: 3068)
- msiexec.exe (PID: 2288)
- Spectaculator.exe (PID: 2816)
- Spectaculator.exe (PID: 2180)
- Spectaculator.exe (PID: 1912)
Application was dropped or rewritten from another process
- SpecStub.exe (PID: 1252)
- keygen.exe (PID: 3968)
- Spectaculator.exe (PID: 3400)
- Spectaculator.exe (PID: 2816)
- Spectaculator.exe (PID: 2180)
- Spectaculator.exe (PID: 3468)
- SpecStub.exe (PID: 2076)
- Spectaculator.exe (PID: 1912)
- Spectaculator.exe (PID: 3016)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2544)
- WinRAR.exe (PID: 2796)
- Spectaculator.exe (PID: 3016)
- Spectaculator.exe (PID: 2816)
- Spectaculator.exe (PID: 3400)
- Spectaculator.exe (PID: 3468)
Checks Windows Trust Settings
- msiexec.exe (PID: 2504)
Executes as Windows Service
- VSSVC.exe (PID: 3784)
Detected use of alternative data streams (AltDS)
- msiexec.exe (PID: 2288)
- Spectaculator.exe (PID: 2816)
- Spectaculator.exe (PID: 2180)
- Spectaculator.exe (PID: 1912)
Reads the BIOS version
- msiexec.exe (PID: 2288)
- Spectaculator.exe (PID: 2816)
- Spectaculator.exe (PID: 2180)
- Spectaculator.exe (PID: 1912)
INFO
Checks supported languages
- msiexec.exe (PID: 2504)
- msiexec.exe (PID: 3068)
- msiexec.exe (PID: 2288)
- keygen.exe (PID: 3968)
- Spectaculator.exe (PID: 3016)
- Spectaculator.exe (PID: 2816)
- Spectaculator.exe (PID: 3400)
- Spectaculator.exe (PID: 2180)
- SpecStub.exe (PID: 2076)
- Spectaculator.exe (PID: 1912)
- Spectaculator.exe (PID: 3468)
- SpecStub.exe (PID: 1252)
The process checks LSA protection
- msiexec.exe (PID: 2504)
- msiexec.exe (PID: 3068)
- msiexec.exe (PID: 2388)
- VSSVC.exe (PID: 3784)
- msiexec.exe (PID: 2288)
- Spectaculator.exe (PID: 2180)
- Spectaculator.exe (PID: 1912)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2504)
- msiexec.exe (PID: 3068)
- msiexec.exe (PID: 2288)
- Spectaculator.exe (PID: 2180)
- Spectaculator.exe (PID: 1912)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3820)
- msiexec.exe (PID: 2388)
- msiexec.exe (PID: 2504)
Manual execution by a user
- msiexec.exe (PID: 2388)
- keygen.exe (PID: 3968)
- notepad.exe (PID: 2736)
- SpecStub.exe (PID: 2076)
- chrome.exe (PID: 1040)
- SpecStub.exe (PID: 1252)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2388)
Reads the computer name
- msiexec.exe (PID: 2504)
- msiexec.exe (PID: 3068)
- msiexec.exe (PID: 2288)
- keygen.exe (PID: 3968)
- Spectaculator.exe (PID: 2816)
- Spectaculator.exe (PID: 2180)
- Spectaculator.exe (PID: 1912)
Application launched itself
- msiexec.exe (PID: 2504)
- chrome.exe (PID: 1040)
Create files in a temporary directory
- msiexec.exe (PID: 2504)
Creates files in the program directory
- Spectaculator.exe (PID: 2816)
Creates files or folders in the user directory
- Spectaculator.exe (PID: 2180)
- Spectaculator.exe (PID: 1912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| ArchivedFileName: | Spectaculator.v8.0.Incl.Keygen-Lz0\linezer0.nfo |
|---|---|
| PackingMethod: | Stored |
| ModifyDate: | 2013:01:19 07:57:48 |
| OperatingSystem: | Unix |
| UncompressedSize: | 24814 |
| CompressedSize: | 24884 |
Total processes
101
Monitored processes
58
Malicious processes
12
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=880,1923266466735472522,8398665086163468587,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=532 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=880,1923266466735472522,8398665086163468587,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1124 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=880,1923266466735472522,8398665086163468587,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3584 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=880,1923266466735472522,8398665086163468587,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=28 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2708 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=880,1923266466735472522,8398665086163468587,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2976 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1252 | "C:\Program Files\Spectaculator\SpecStub.exe" | C:\Program Files\Spectaculator\SpecStub.exe | — | explorer.exe | |||||||||||
User: admin Company: spectaculator.com Integrity Level: MEDIUM Description: Spectaculator ZX Spectrum Emulator Exit code: 0 Version: 8.0.0.3092 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=880,1923266466735472522,8398665086163468587,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3556 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=880,1923266466735472522,8398665086163468587,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3584 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=880,1923266466735472522,8398665086163468587,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3352 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
28 404
Read events
28 083
Write events
301
Delete events
20
Modification events
| (PID) Process: | (2544) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
40
Suspicious files
173
Text files
138
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3820 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3820.38743\spectaculator80.msi | — | |
MD5:— | SHA256:— | |||
| 2504 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2504 | msiexec.exe | C:\Windows\Installer\11e471.msi | — | |
MD5:— | SHA256:— | |||
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2796.38345\linezer0.rar | compressed | |
MD5:7A82FD663A45234926B4B3EC238A288D | SHA256:D556085CEE22AF01692BE7F187FDFE3404F765800BE4BB5838E55858AF9959EB | |||
| 2504 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:B4403FEEA3B08FADAE36E690D207154D | SHA256:DED789BCF0960B62A62BDDCCDE45DCF2B337D1C5F1622F9DDF426E3B8330E727 | |||
| 3820 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3820.38743\Lz0\keygen.exe | executable | |
MD5:A207C5D5DDF65B0A19D666DD89EA30D3 | SHA256:492A9C4531CD85F8F490C7E6B8E52AB529E6F3E2F257D52E5824BAF0D8BCD211 | |||
| 2544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2544.38212\lzqdcsu1.zip | compressed | |
MD5:E2CFAA0E20CB9ADF0809F2EEDD7290EB | SHA256:07EF6BF27F85FA192DECA16D18819070742B6E682C770D219E7A4D5B784BB76B | |||
| 2504 | msiexec.exe | C:\Program Files\Spectaculator\drivers\Debugger.dll | executable | |
MD5:465021D3498398771C4BB66A5A2AFFD8 | SHA256:F3360EEFF1A53075CA0C4F94A67A329CB819964718DF40896BF73E8C18385CD6 | |||
| 2504 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFAAFF81566E1FECBB.TMP | gmc | |
MD5:9B125C8B7242E6372E11C19581A488CA | SHA256:DA99DA8E46CAC01DC82BDFBCCC1B7B36366EA4BBCC14C9AD6712B24D75656D4D | |||
| 2504 | msiexec.exe | C:\Program Files\Spectaculator\drivers\audiorec.dll | executable | |
MD5:A3E54882C70C105BFF39A61A4CC59FE5 | SHA256:6B7A3960F0A23C5543BED7EF025CEFF45E1FF6B2E820A80095A6D133B21B81CD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
52
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2428 | chrome.exe | GET | 301 | 188.114.97.3:80 | http://sharedrop.io/ | US | — | — | malicious |
2428 | chrome.exe | GET | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | — | — | whitelisted |
852 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvODJiQUFYYVJaZ0k5di1hUFlXS1prX2xDZw/1.0.0.13_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | binary | 2.81 Kb | whitelisted |
2428 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | binary | 471 b | whitelisted |
2428 | chrome.exe | GET | 200 | 67.27.158.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5ff400915d9e9fd4 | US | compressed | 4.70 Kb | whitelisted |
852 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/cxpsjblnoxgjoqggdsbvujtof4_58/khaoiebndkojlmppeemjhbpbandiljpe_58_win_advr4ucepztwtigvw3fduftsvbeq.crx3 | US | crx | 5.46 Kb | whitelisted |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/YGkwa4MXjfWSuERyWQYP_A_4/aapLKTSZ439A-0g3nqJr3Q | US | binary | 3.84 Kb | whitelisted |
852 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/YGkwa4MXjfWSuERyWQYP_A_4/aapLKTSZ439A-0g3nqJr3Q | US | crx | 3.72 Kb | whitelisted |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvODJiQUFYYVJaZ0k5di1hUFlXS1prX2xDZw/1.0.0.13_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjg0QUFYSnN4MFUtaEQwNDZqVGRkVkFmZw/1.0.6.0_aemomkdncapdnfajjbbcbdebjljbpmpj.crx | US | binary | 3.84 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1040 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2428 | chrome.exe | 216.58.212.141:443 | accounts.google.com | GOOGLE | US | whitelisted |
568 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2428 | chrome.exe | 172.217.16.129:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
2428 | chrome.exe | 142.250.186.68:443 | www.google.com | GOOGLE | US | whitelisted |
2428 | chrome.exe | 142.250.185.234:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
2428 | chrome.exe | 142.250.186.99:443 | www.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
msiexec.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
msiexec.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Spectaculator.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Spectaculator.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Spectaculator.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Spectaculator.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Spectaculator.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Spectaculator.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |