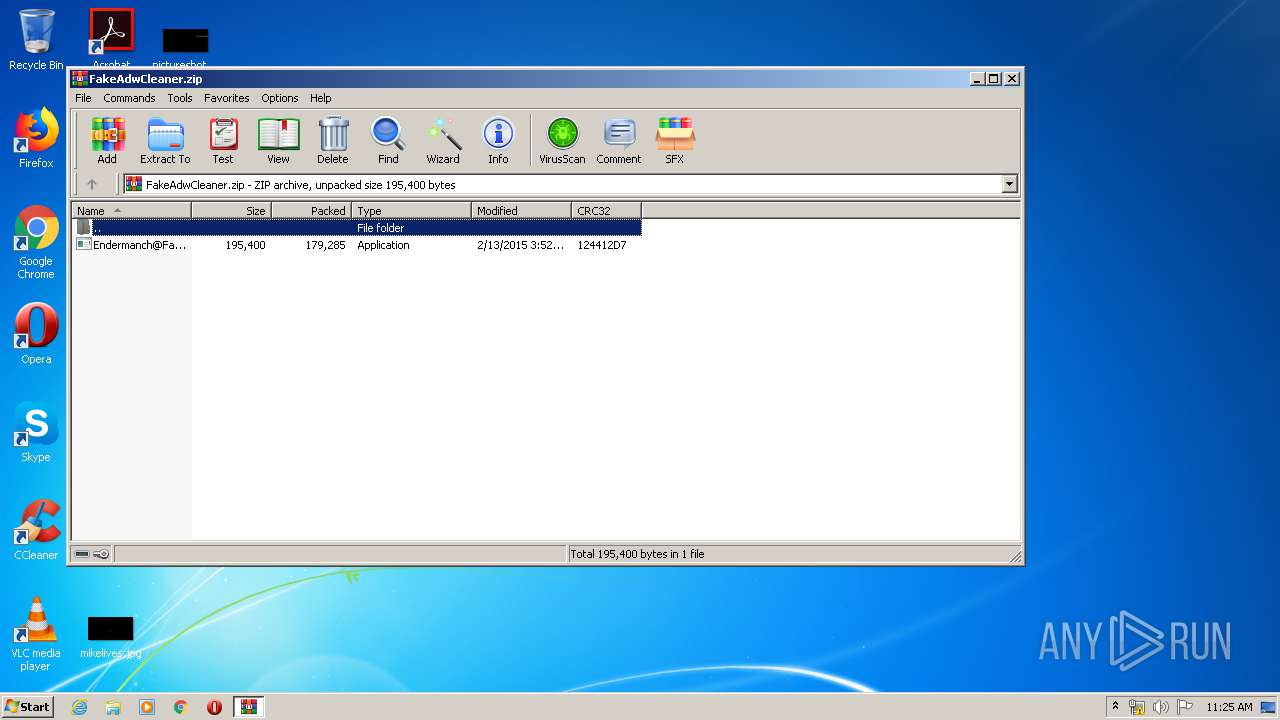
| File name: | FakeAdwCleaner.zip |
| Full analysis: | https://app.any.run/tasks/d2c2a4b6-287d-4b20-9fed-09fa6623adf1 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2020, 10:24:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 6D8C9D01BA5C32AEDC734087CC3D0B1B |
| SHA1: | F7E58E5EDD203ABC2364922B11B6641D3EE9ADD5 |
| SHA256: | 92E885D1763E4BA1ABC92BEE9B08CA7A2AE358BDA5FE98B31A8E217327982BF7 |
| SSDEEP: | 3072:5oVnkybquxcF6U/aVHOBuv7j4/rIUUT4iI5mflT9xuUqywFdiZS3e:5oV5bZxIsV4l/kz4iFh98UqywKw3e |
MALICIOUS
Application was dropped or rewritten from another process
- 6AdwCleaner.exe (PID: 2728)
- Endermanch@FakeAdwCleaner.exe (PID: 4072)
Changes the autorun value in the registry
- 6AdwCleaner.exe (PID: 2728)
Connects to CnC server
- 6AdwCleaner.exe (PID: 2728)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1396)
- Endermanch@FakeAdwCleaner.exe (PID: 4072)
INFO
Manual execution by user
- Endermanch@FakeAdwCleaner.exe (PID: 4072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2015:02:13 18:52:06 |
| ZipCRC: | 0x124412d7 |
| ZipCompressedSize: | 179285 |
| ZipUncompressedSize: | 195400 |
| ZipFileName: | Endermanch@FakeAdwCleaner.exe |
Total processes
39
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1396 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\FakeAdwCleaner.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2728 | "C:\Users\admin\AppData\Local\6AdwCleaner.exe" | C:\Users\admin\AppData\Local\6AdwCleaner.exe | Endermanch@FakeAdwCleaner.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AdwareBooC Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4072 | "C:\Users\admin\Desktop\Endermanch@FakeAdwCleaner.exe" | C:\Users\admin\Desktop\Endermanch@FakeAdwCleaner.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
868
Read events
810
Write events
58
Delete events
0
Modification events
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\FakeAdwCleaner.zip | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1396.13848\Endermanch@FakeAdwCleaner.exe | executable | |
MD5:248AADD395FFA7FFB1670392A9398454 | SHA256:51290129CCCCA38C6E3B4444D0DFB8D848C8F3FC2E5291FC0D219FD642530ADC | |||
| 4072 | Endermanch@FakeAdwCleaner.exe | C:\Users\admin\AppData\Local\6AdwCleaner.exe | executable | |
MD5:87E4959FEFEC297EBBF42DE79B5C88F6 | SHA256:4F0033E811FE2497B38F0D45DF958829D01933EBE7D331079EEFC8E38FBEAA61 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2728 | 6AdwCleaner.exe | GET | 403 | 104.247.81.133:80 | http://www.vikingwebscanner.com/scripts/new_install.php?owner=6AdwCleaner | CA | html | 146 b | malicious |
2728 | 6AdwCleaner.exe | GET | 403 | 104.247.81.133:80 | http://www.vikingwebscanner.com/scripts/status.php?action=scan&id=0 | CA | html | 146 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2728 | 6AdwCleaner.exe | 104.247.81.133:80 | www.vikingwebscanner.com | Team Internet AG | CA | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.vikingwebscanner.com |
| malicious |
Threats
1 ETPRO signatures available at the full report