| URL: | https://www.iptvsmarters.com/download/?download=windows_app |
| Full analysis: | https://app.any.run/tasks/624c30d4-209c-416c-8b9e-abd1d936cd97 |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2024, 21:29:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 60D12BFEC5EECE1EC2C8B3446938A9A7 |
| SHA1: | E1E16B2A767834D06C1362FADFC45E457F9C4239 |
| SHA256: | 92C706A1CD68A308078A33EE2BE30D0F967E94BADACA47FC41FB2CBFDC307DC9 |
| SSDEEP: | 3:N8DSLuHMGGBKLa0FSP:2OLSNubP |
MALICIOUS
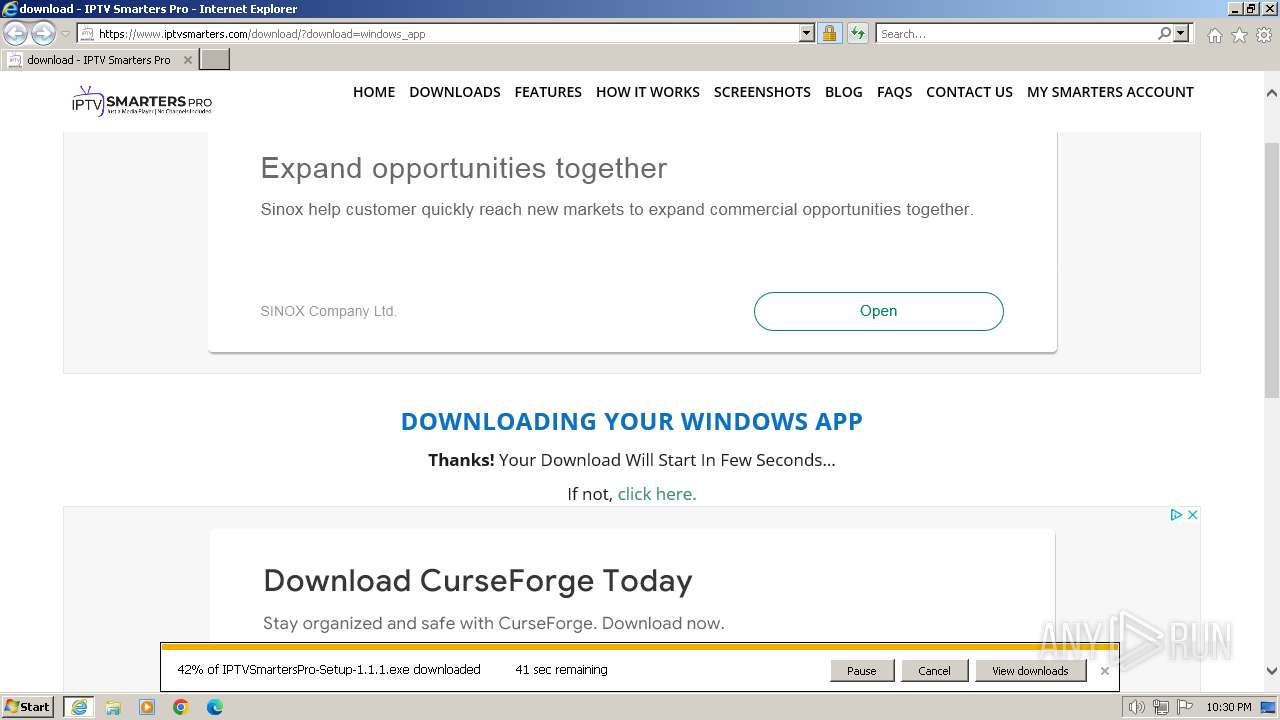
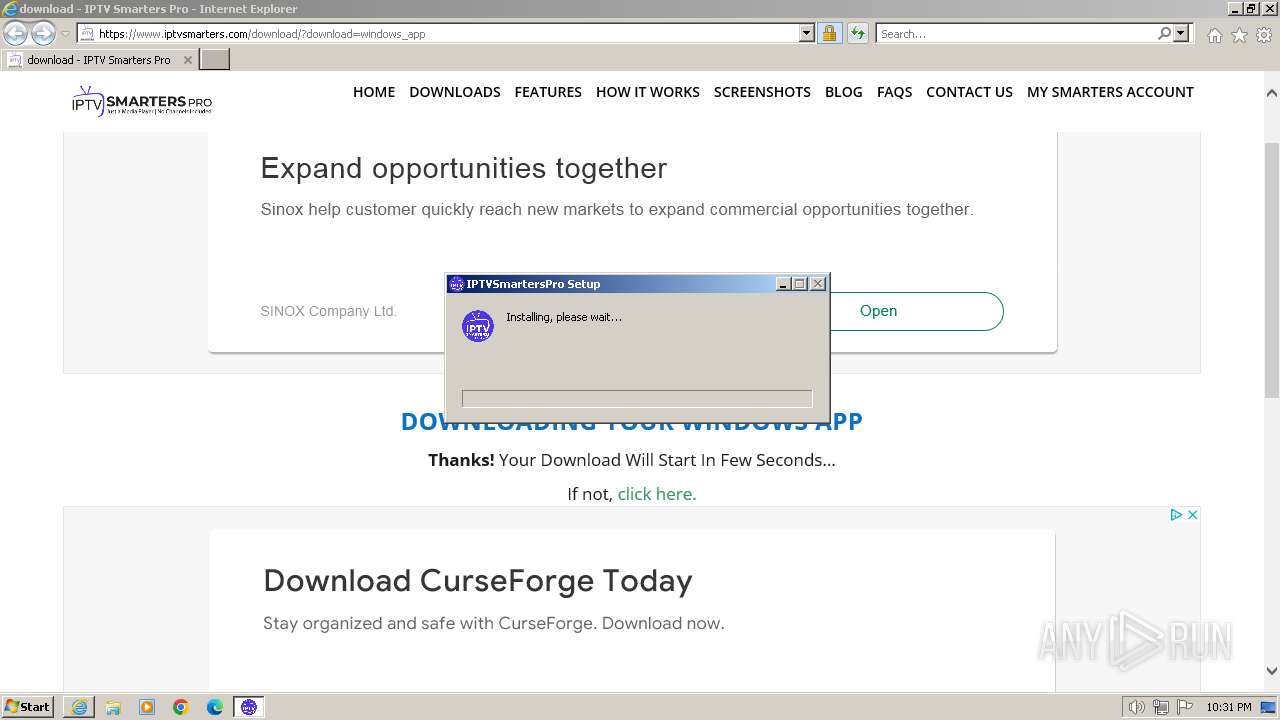
Drops the executable file immediately after the start
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
SUSPICIOUS
The process creates files with name similar to system file names
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
Executable content was dropped or overwritten
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
Drops 7-zip archiver for unpacking
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
Process drops legitimate windows executable
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
Creates a software uninstall entry
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
Node.exe was dropped
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
Malware-specific behavior (creating "System.dll" in Temp)
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
Reads the Internet Settings
- IPTVSmartersPro.exe (PID: 2196)
Application launched itself
- IPTVSmartersPro.exe (PID: 2196)
Reads settings of System Certificates
- IPTVSmartersPro.exe (PID: 2196)
INFO
Executable content was dropped or overwritten
- iexplore.exe (PID: 3432)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3344)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3432)
Reads the computer name
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
- IPTVSmartersPro.exe (PID: 2276)
- IPTVSmartersPro.exe (PID: 2196)
The process uses the downloaded file
- iexplore.exe (PID: 3344)
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
Creates files or folders in the user directory
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
- IPTVSmartersPro.exe (PID: 2196)
Checks supported languages
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
- IPTVSmartersPro.exe (PID: 2196)
- IPTVSmartersPro.exe (PID: 2276)
Create files in a temporary directory
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
- IPTVSmartersPro.exe (PID: 2196)
Manual execution by a user
- IPTVSmartersPro.exe (PID: 2196)
Application launched itself
- iexplore.exe (PID: 3344)
Reads the machine GUID from the registry
- IPTVSmartersPro-Setup-1.1.1.exe (PID: 1808)
- IPTVSmartersPro.exe (PID: 2196)
Reads the software policy settings
- IPTVSmartersPro.exe (PID: 2196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
46
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1808 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\IPTVSmartersPro-Setup-1.1.1.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\IPTVSmartersPro-Setup-1.1.1.exe | iexplore.exe | ||||||||||||
User: admin Company: WHMCS Smarters Integrity Level: MEDIUM Description: IPTV Smarters Pro is a Live IPTV player for end-users that provides the facility to watch Live TV, VOD, Series. Exit code: 0 Version: 1.1.1 Modules
| |||||||||||||||
| 2196 | "C:\Users\admin\AppData\Local\Programs\IPTVSmartersPro\IPTVSmartersPro.exe" | C:\Users\admin\AppData\Local\Programs\IPTVSmartersPro\IPTVSmartersPro.exe | explorer.exe | ||||||||||||
User: admin Company: WHMCS Smarters Integrity Level: MEDIUM Description: IPTVSmartersPro Version: 1.1.1 Modules
| |||||||||||||||
| 2276 | "C:\Users\admin\AppData\Local\Programs\IPTVSmartersPro\IPTVSmartersPro.exe" --type=renderer --no-sandbox --primordial-pipe-token=9A11AA70F0392C55618E8FE941B98503 --lang=en-US --node-integration=true --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --content-image-texture-target=3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553 --video-image-texture-target=3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --mojo-channel-token=DD103CF4EF8093C55371A62648A647D9 --mojo-application-channel-token=9A11AA70F0392C55618E8FE941B98503 --channel="2196.0.692127903\1293488761" --mojo-platform-channel-handle=1220 /prefetch:1 | C:\Users\admin\AppData\Local\Programs\IPTVSmartersPro\IPTVSmartersPro.exe | — | IPTVSmartersPro.exe | |||||||||||
User: admin Company: WHMCS Smarters Integrity Level: MEDIUM Description: IPTVSmartersPro Version: 1.1.1 Modules
| |||||||||||||||
| 3344 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.iptvsmarters.com/download/?download=windows_app" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3432 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3344 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
29 265
Read events
29 100
Write events
135
Delete events
30
Modification events
| (PID) Process: | (3344) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3344) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3344) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31115078 | |||
| (PID) Process: | (3344) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3344) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31115078 | |||
| (PID) Process: | (3344) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3344) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3344) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3344) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3344) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
305
Suspicious files
137
Text files
67
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | der | |
MD5:1BFE0A81DB078EA084FF82FE545176FE | SHA256:5BA8817F13EEE00E75158BAD93076AB474A068C6B52686579E0F728FDA68499F | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\pum-site-styles[1].css | text | |
MD5:A02739222C307D2A1E72B1BC03B23F7B | SHA256:01BE912D997E052C244977442E64F7506A8CE6E8A0E67A3E24CADFD82DAF1C69 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\style.min[1].css | text | |
MD5:51A8390B47AA0582CF2D9C96C5ADDEE2 | SHA256:98CECF88A23542FA047CE46EEDB650B5C5128761ED4386C0977B847094DDFA20 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\light-box-styles[1].css | text | |
MD5:E38FE315F4B525E15C61CA5E9DCB839E | SHA256:C629444A1FD6F94E1E747DCE6FC67382E33B134E93A876B699CF2937DCAACCC8 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\swiper.min[1].css | text | |
MD5:61F38C0476F40331B3B05798FA1EE59E | SHA256:14641486871FC6955F0FA3938125C4562E808719E2D40F6632BCD438F6B02760 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\logo-white-300x111[1].png | image | |
MD5:BDBA752BB65CED8665F64F2BEEE3E599 | SHA256:C4A411EE47CDABB0A6D66AD121DA7AC4750B1C936052916F42253FDF0438F236 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:2365869258DF7A66A2121B802CA4AFD9 | SHA256:D6B1932822BBD72A8E78C771717D992142348F67D625A42393719FEFBE59B0ED | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\choices.min[1].css | text | |
MD5:88E49A1CA77DAC27CBFB2C929F76A8FA | SHA256:8CBF449A12FFCB4E90C14CFE5028D9965AF5FFAAEDB6BCD287CF527CA617848C | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\play[1].png | image | |
MD5:F78C11263F75E19F8E8D1F99AAD491AF | SHA256:674D79637D6E2B8C602E21A4B16D4E4A88AE26355E732B65C4DD3DE20712263E | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:259C738D60E36A31F6368F22C257C76D | SHA256:EDE66C9BF6D2CE2C44F07AD61D63D1DA7DD6B313F003D9790C22C7931B958D25 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
67
DNS requests
32
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3432 | iexplore.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e11ed310cb05c77e | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e7395a10ad170b70 | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQD5h8yP4fv97BLq9sYqcTVS | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCehKugGJdgWBAhc1EB8hIz | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEAIE94ivqY0gCWDtim5%2Ffhw%3D | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCDR9vuwevMnRDMxC1byWoK | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3432 | iexplore.exe | 104.26.5.2:443 | — | CLOUDFLARENET | US | unknown |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3432 | iexplore.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3432 | iexplore.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3432 | iexplore.exe | 142.250.185.67:80 | c.pki.goog | GOOGLE | US | whitelisted |
3432 | iexplore.exe | 142.250.185.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
c.pki.goog |
| unknown |
fonts.googleapis.com |
| whitelisted |
cdn.ampproject.org |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
o.pki.goog |
| unknown |
fonts.gstatic.com |
| whitelisted |
region1.analytics.google.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | IPTVSmartersPro.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Adware |