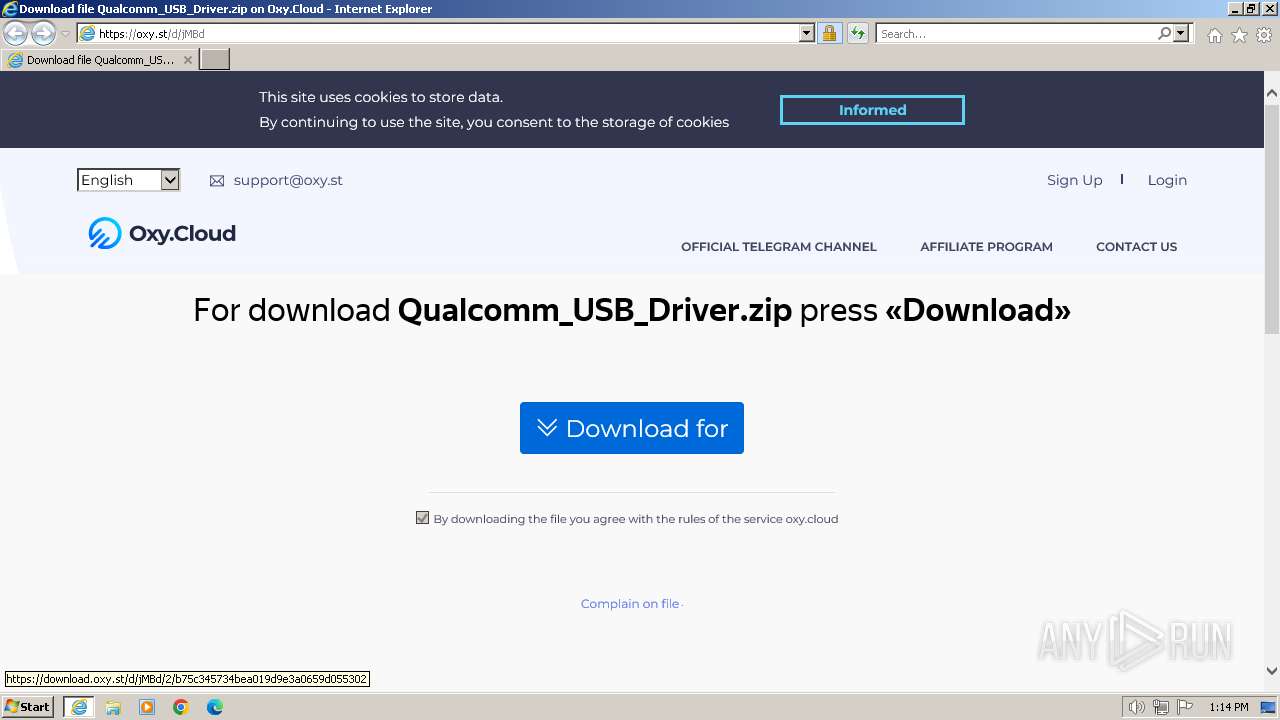
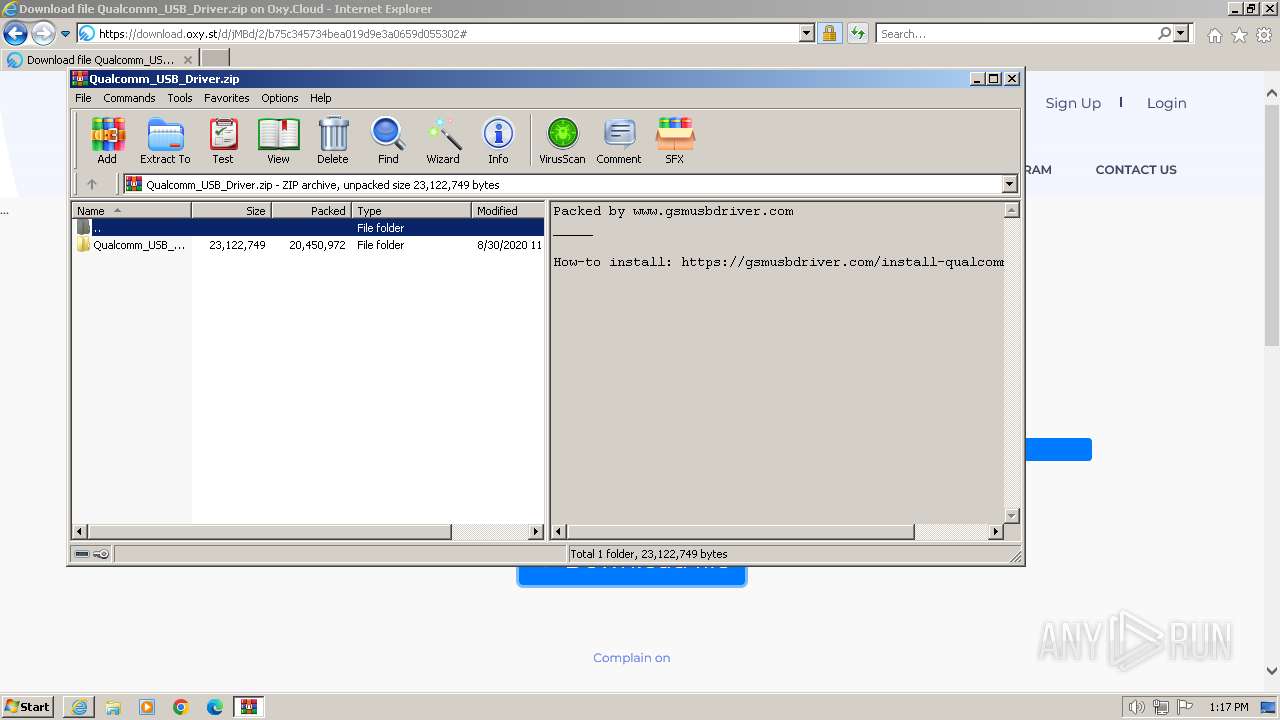
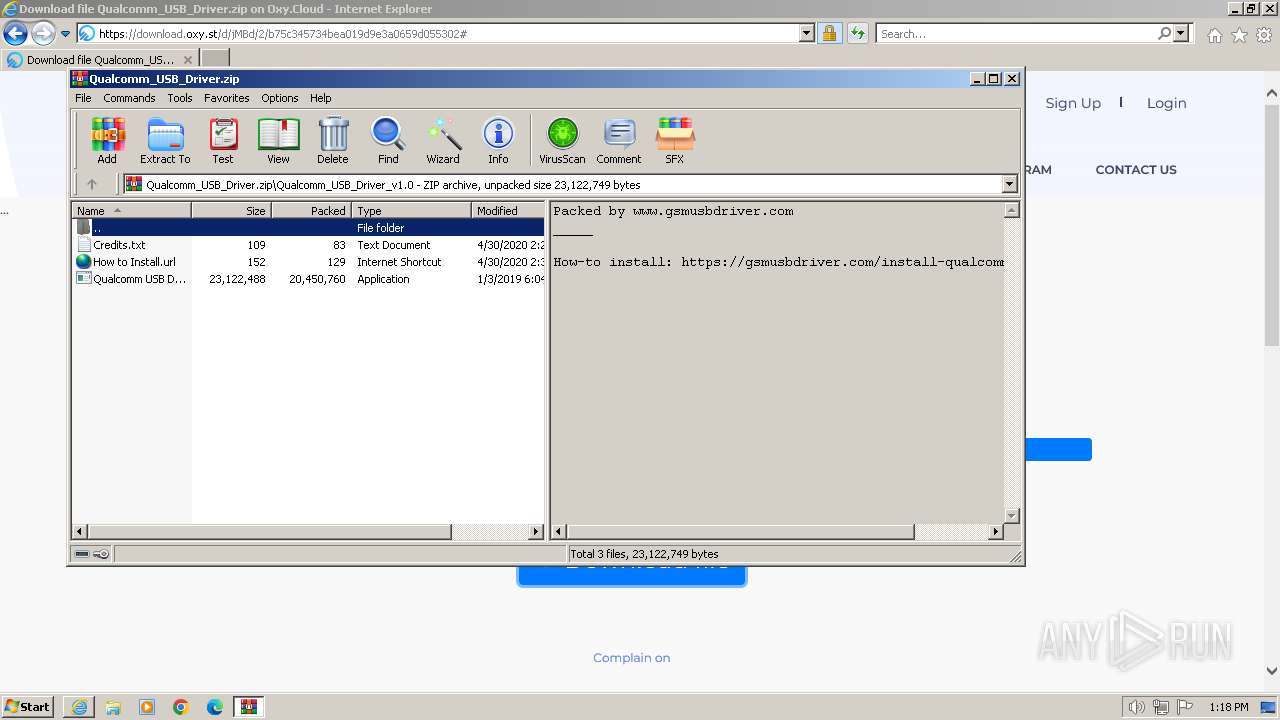
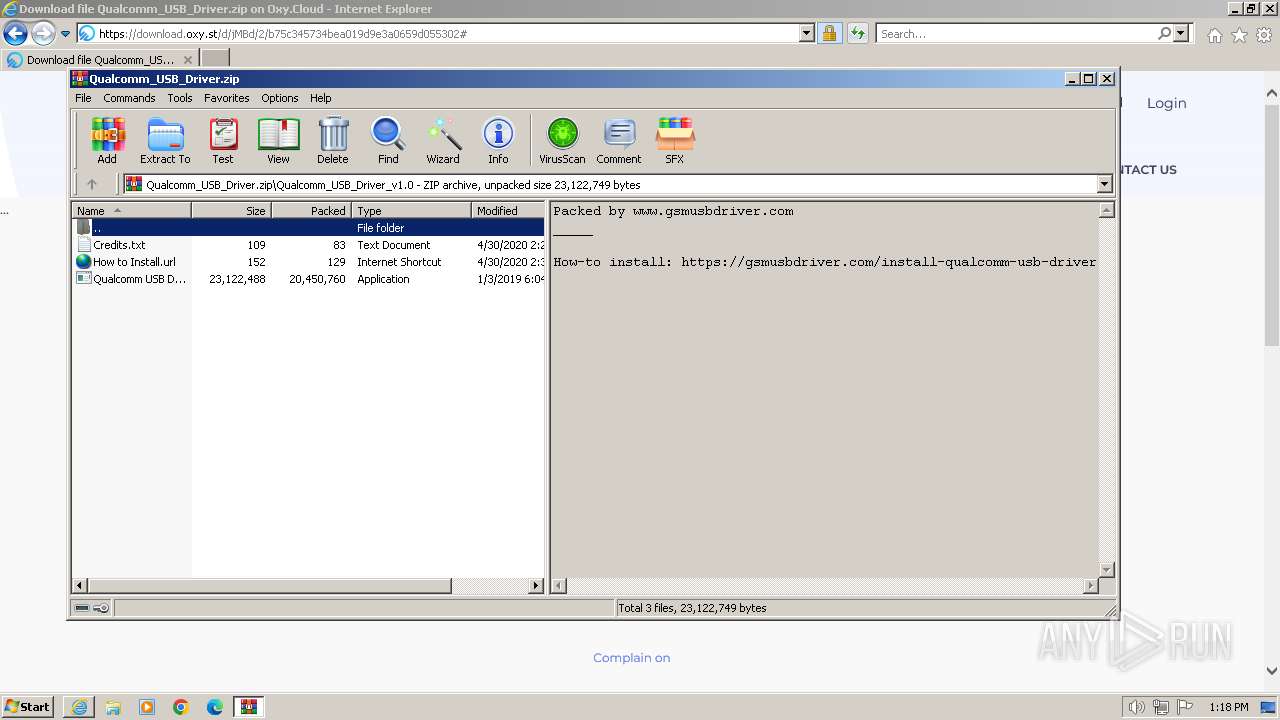
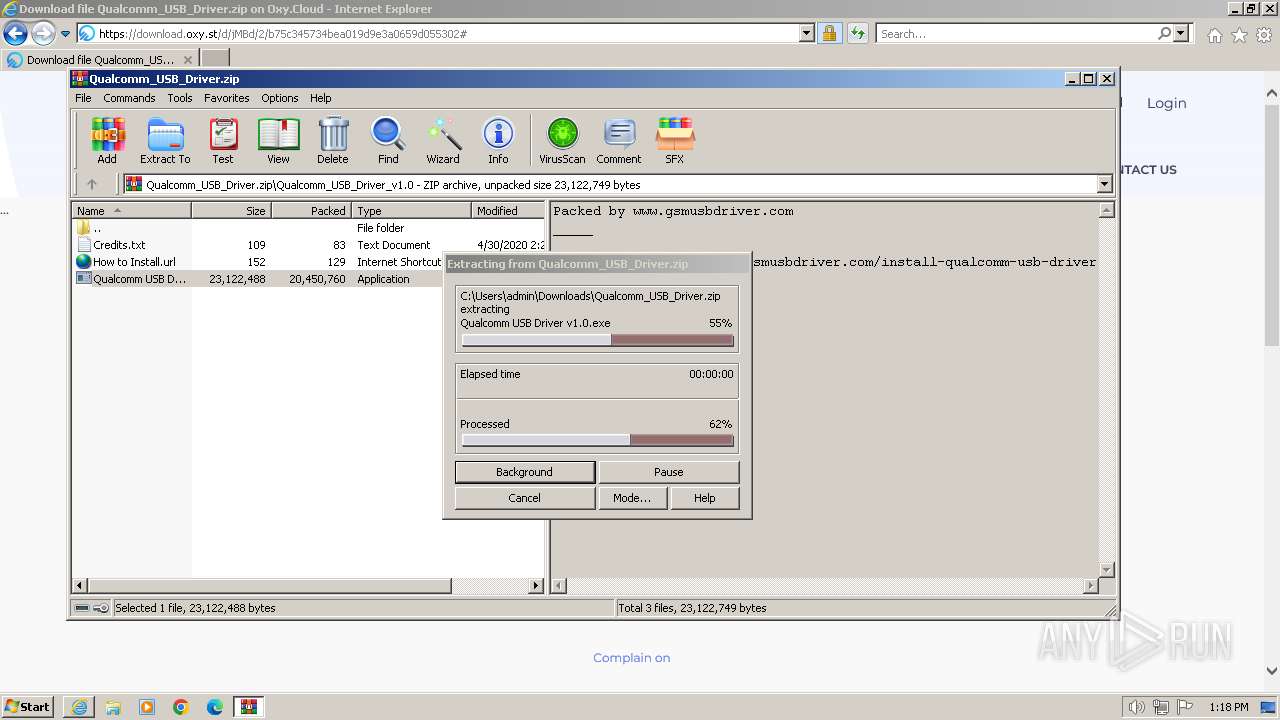
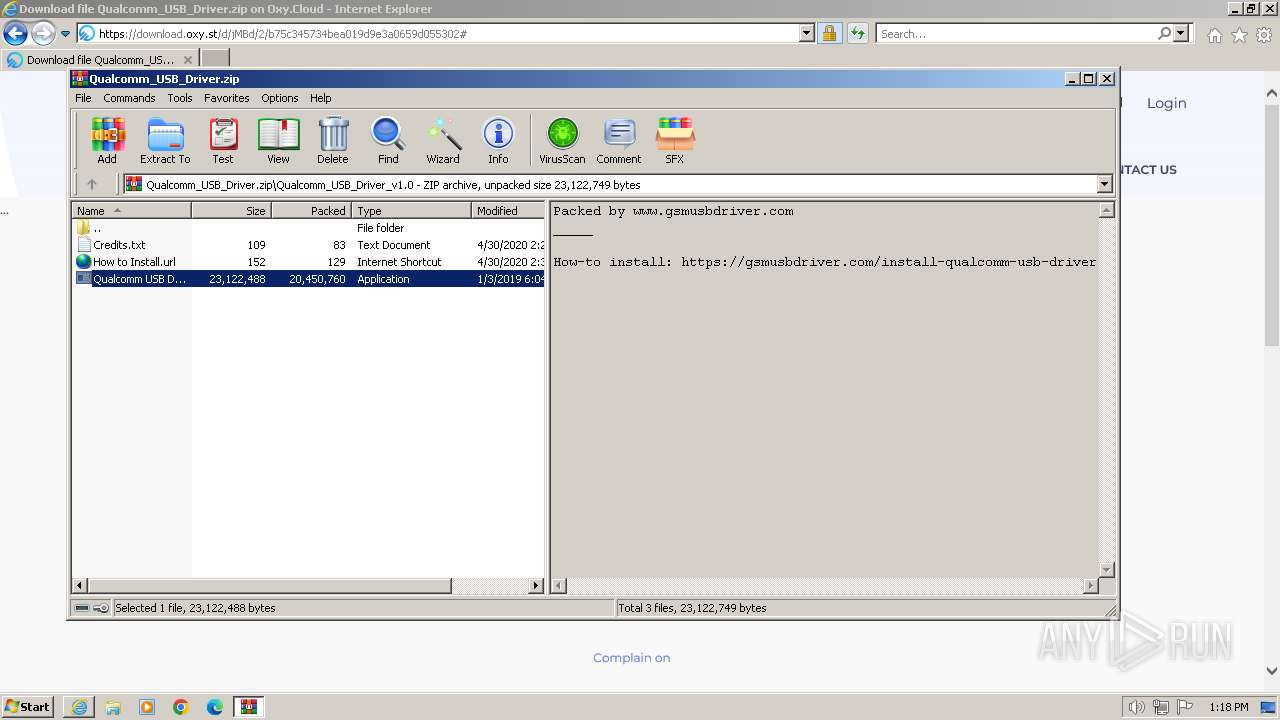
| URL: | https://oxy.st/d/jMBd |
| Full analysis: | https://app.any.run/tasks/942f4971-e883-4da3-a201-c7b506b59acb |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2024, 13:14:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C1938501651615A6A7487D8755F15AC3 |
| SHA1: | F343F43B4FA025A6B0F5C93A2EB9BCD396A0F547 |
| SHA256: | 92C5B6427BD992779BE20A1CD571F706B4E5B3D43C39B85320E8B64422FFDFFB |
| SSDEEP: | 3:N8U2xB:2U2xB |
MALICIOUS
Creates a writable file in the system directory
- drvinst.exe (PID: 2228)
- drvinst.exe (PID: 3968)
- drvinst.exe (PID: 2036)
- drvinst.exe (PID: 2924)
- drvinst.exe (PID: 4028)
Drops the executable file immediately after the start
- drvinst.exe (PID: 2228)
- drvinst.exe (PID: 3968)
- drvinst.exe (PID: 2036)
- drvinst.exe (PID: 2924)
- drvinst.exe (PID: 4028)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1584)
Executes as Windows Service
- VSSVC.exe (PID: 896)
- qcmtusvc.exe (PID: 3588)
Creates files in the driver directory
- drvinst.exe (PID: 2228)
- drvinst.exe (PID: 3968)
- drvinst.exe (PID: 2036)
- drvinst.exe (PID: 2924)
- drvinst.exe (PID: 4028)
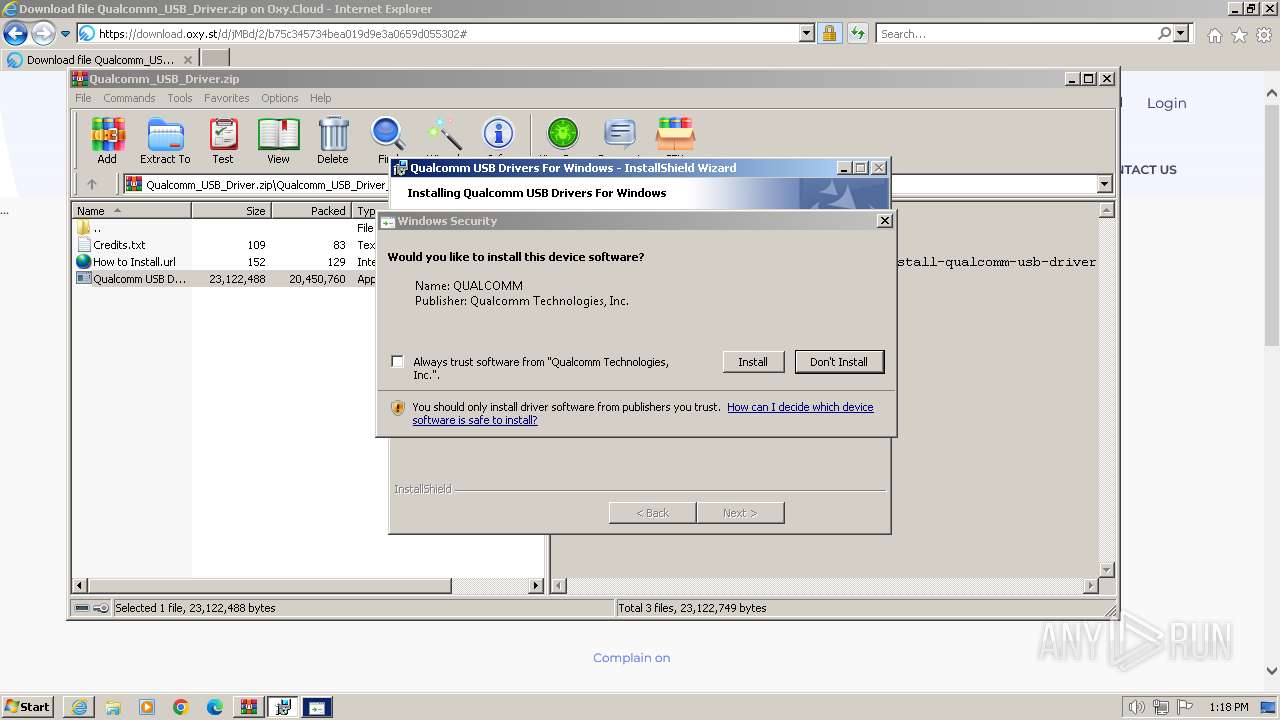
Checks Windows Trust Settings
- drvinst.exe (PID: 2228)
- drvinst.exe (PID: 3968)
- drvinst.exe (PID: 2036)
- drvinst.exe (PID: 2924)
- drvinst.exe (PID: 4028)
Executable content was dropped or overwritten
- drvinst.exe (PID: 2228)
- drvinst.exe (PID: 3968)
- drvinst.exe (PID: 2036)
- drvinst.exe (PID: 2924)
- drvinst.exe (PID: 4028)
Drops a system driver (possible attempt to evade defenses)
- drvinst.exe (PID: 2228)
- drvinst.exe (PID: 3968)
- drvinst.exe (PID: 2036)
- drvinst.exe (PID: 2924)
- drvinst.exe (PID: 4028)
Process drops legitimate windows executable
- drvinst.exe (PID: 4028)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 1584)
- iexplore.exe (PID: 2124)
Application launched itself
- iexplore.exe (PID: 2124)
- chrome.exe (PID: 3652)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4064)
- WinRAR.exe (PID: 1584)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2124)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1584)
- msiexec.exe (PID: 4064)
Create files in a temporary directory
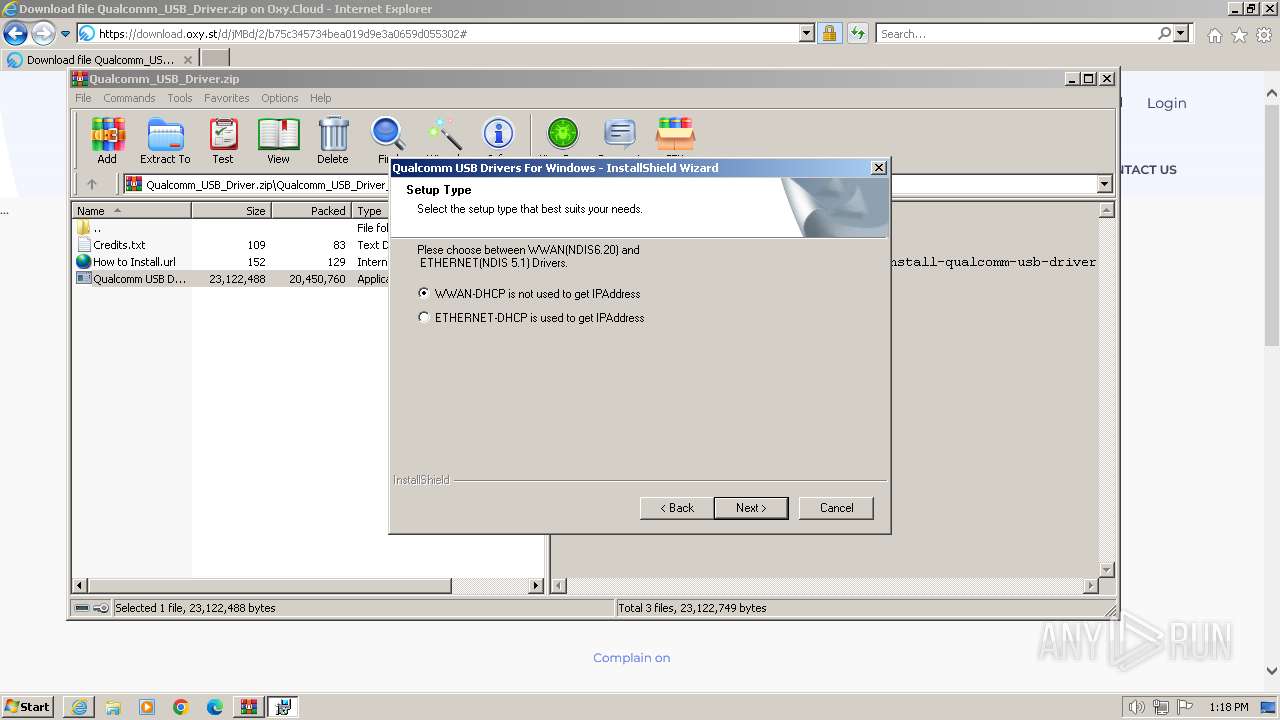
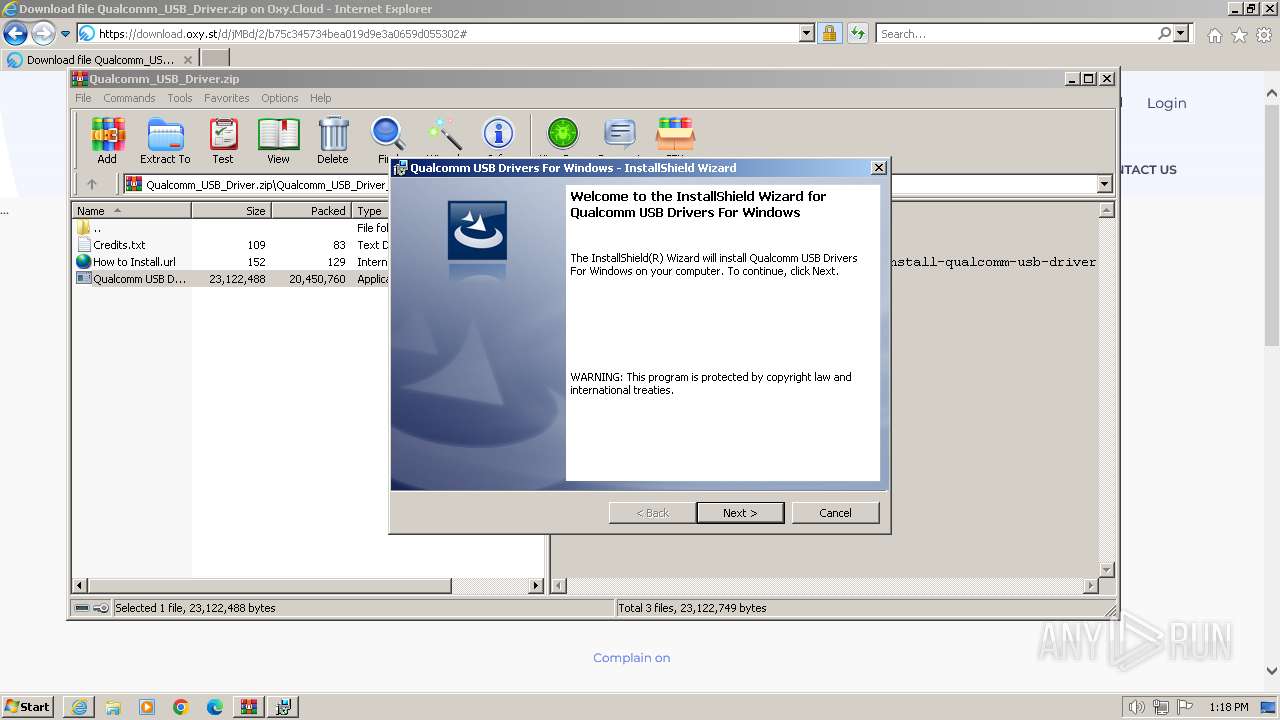
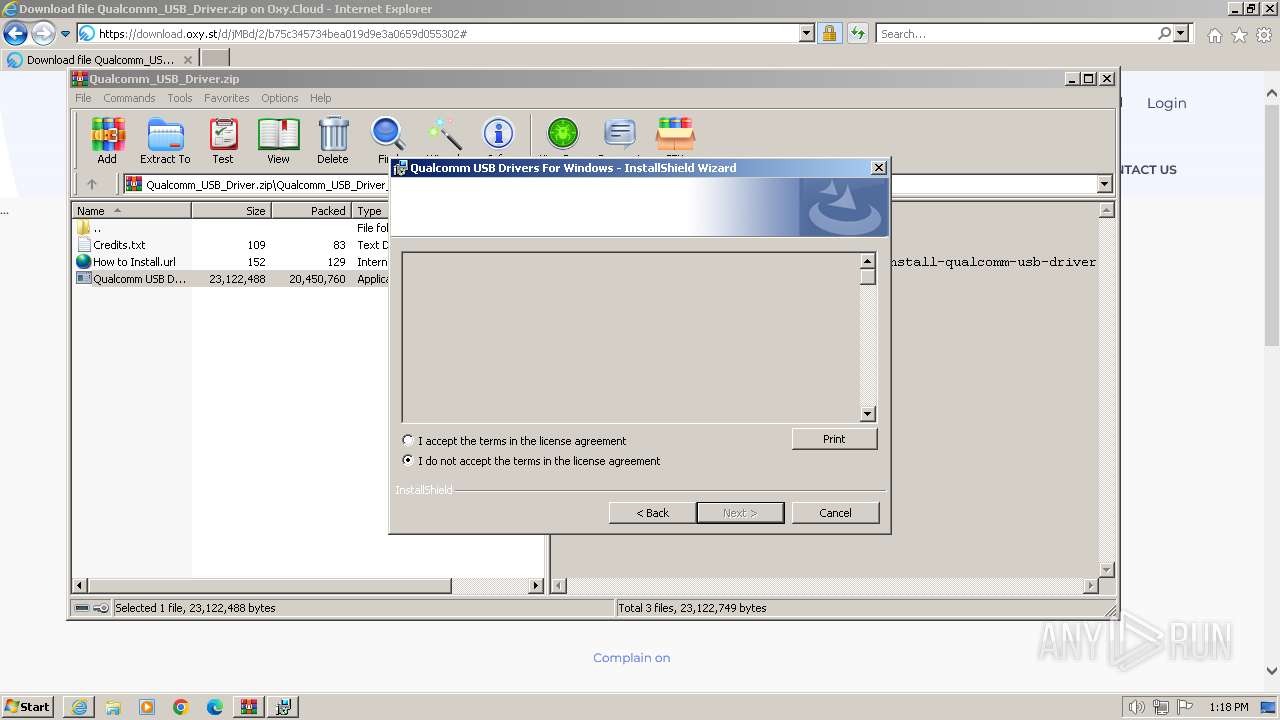
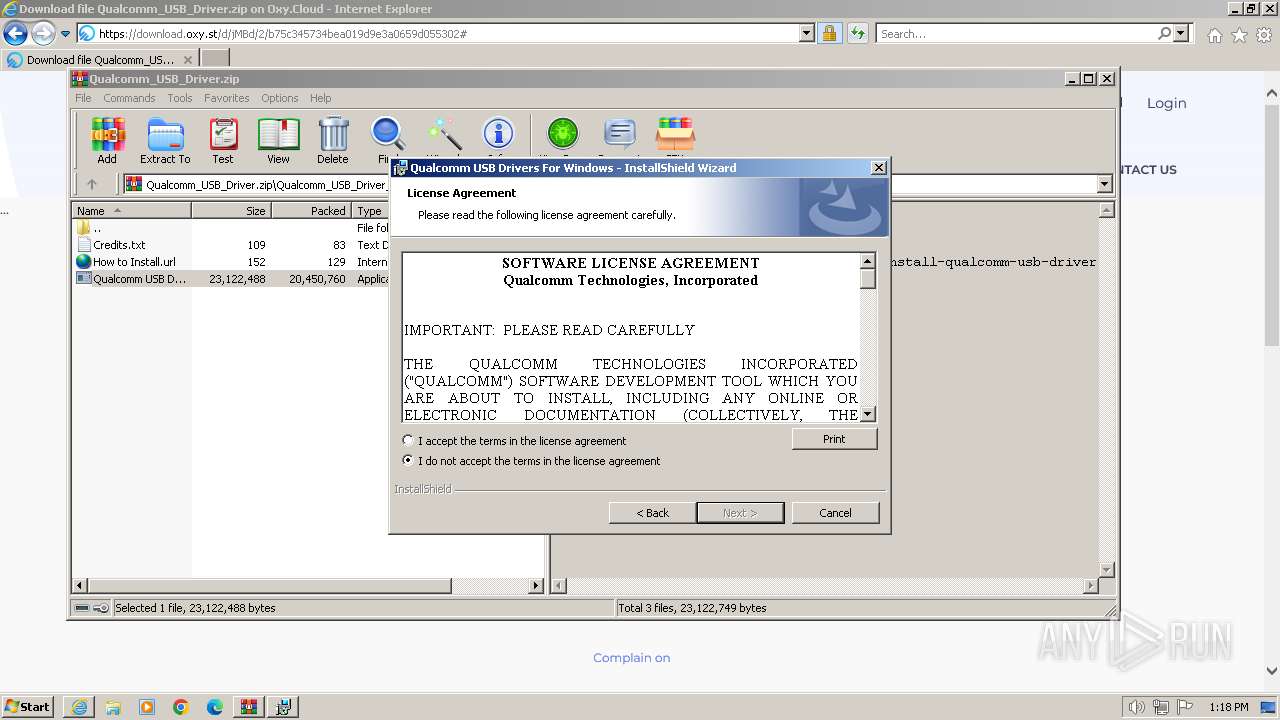
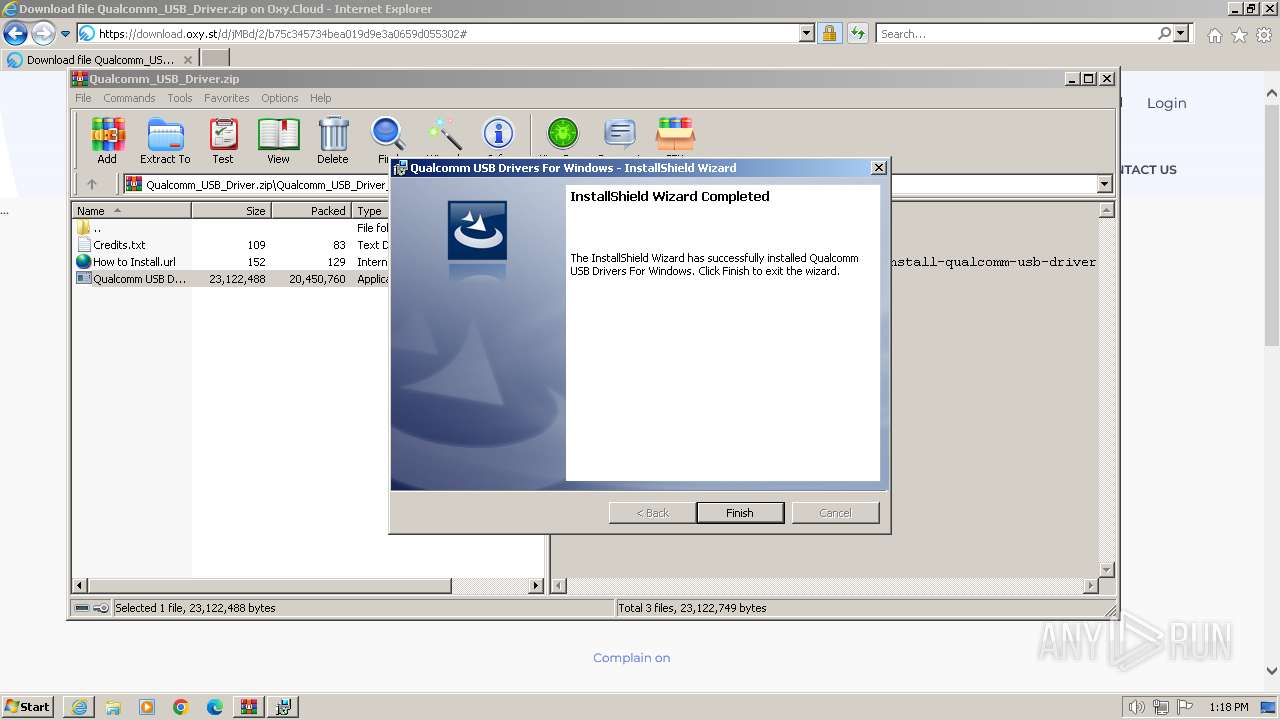
- Qualcomm USB Driver v1.0.exe (PID: 2956)
Reads the computer name
- qcmtusvc.exe (PID: 3588)
- drvinst.exe (PID: 2228)
- drvinst.exe (PID: 3968)
- drvinst.exe (PID: 2036)
- drvinst.exe (PID: 2924)
- drvinst.exe (PID: 4028)
Checks supported languages
- Qualcomm USB Driver v1.0.exe (PID: 2956)
- drvinst.exe (PID: 2228)
- qcmtusvc.exe (PID: 3588)
- drvinst.exe (PID: 3968)
- drvinst.exe (PID: 2036)
- drvinst.exe (PID: 2924)
- drvinst.exe (PID: 4028)
Reads the machine GUID from the registry
- drvinst.exe (PID: 2228)
- drvinst.exe (PID: 3968)
- drvinst.exe (PID: 2036)
- drvinst.exe (PID: 2924)
- drvinst.exe (PID: 4028)
Reads the software policy settings
- drvinst.exe (PID: 2228)
- drvinst.exe (PID: 3968)
- drvinst.exe (PID: 2036)
- drvinst.exe (PID: 2924)
- drvinst.exe (PID: 4028)
- rundll32.exe (PID: 3904)
Adds/modifies Windows certificates
- drvinst.exe (PID: 4028)
Manual execution by a user
- chrome.exe (PID: 3652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
74
Monitored processes
29
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3516 --field-trial-handle=1152,i,4272174307022128852,11482854374713885220,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 552 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1584.27305\Qualcomm_USB_Driver_v1.0\Qualcomm USB Driver v1.0.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1584.27305\Qualcomm_USB_Driver_v1.0\Qualcomm USB Driver v1.0.exe | — | WinRAR.exe | |||||||||||
User: admin Company: QUALCOMM, Inc. Integrity Level: MEDIUM Description: QUALCOMM Setup Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2188 --field-trial-handle=1152,i,4272174307022128852,11482854374713885220,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3788 --field-trial-handle=1152,i,4272174307022128852,11482854374713885220,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 896 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1324 --field-trial-handle=1152,i,4272174307022128852,11482854374713885220,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Qualcomm_USB_Driver.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1520 --field-trial-handle=1152,i,4272174307022128852,11482854374713885220,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2036 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{0c3bf575-4546-504b-d4e3-172be6159e20}\qcmdm.inf" "0" "6a46e0ea3" "000005D0" "WinSta0\Default" "000005D8" "208" "C:\Program Files\QUALCOMM Incorporated\Qualcomm USB Drivers For Windows\DriverPackage\Qualcomm\fre\Windows7" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://oxy.st/d/jMBd" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
58 621
Read events
58 163
Write events
408
Delete events
50
Modification events
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31096301 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31096301 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
14
Suspicious files
115
Text files
109
Unknown types
44
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:A5AD26873A9A1C112FCA3F893DDD7BDF | SHA256:6B5A0A3DE712A14414CF8BCBE6437071ADA416397482612467E64960D97D8B8A | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\jMBd[1].htm | html | |
MD5:A0B0DC4DBEB749A1947AEC325DF80347 | SHA256:46655D35BDF7E3C3BB2C8573415954648280DDD9ED66126AED930033149DD8EC | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\cookie[1].css | text | |
MD5:A53EB58F04DB28B561E3CF6F2327C28D | SHA256:67DD147575B0963981F0A47878165F9048269FD8C90F632A28EECCE73B5D9AE6 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\cloud[1].css | text | |
MD5:526B65035FF31BD7147BE9E785A768AC | SHA256:8996A1606A4793B1A05580FF47567F4467C2D16BBE7CBCB049DC849E0105DA86 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:08C43362198BACE5706065208AFAD847 | SHA256:BE7A1AC2F335A4E3374A2E8F38CB8C85EE9EA8A2497A041D7B434EE1F7EF3EF7 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:2A0958B4CDE3578AECB5E6D6D5351E1C | SHA256:1C33ABFAE534FE8D204D0AB674F74DC2C81979A67C9FE13804FCBA878EA45684 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F876A388676EDF0683AB04E769CC171E | binary | |
MD5:757C5F2763EDD4BE302E0E8BB29A4DED | SHA256:B1FE34B035D7656F1DEAE78F62E6CC0F28288092E9AD722BB4865ED3FF1C7B19 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D36115BBD10B95EBF21BE9298860721C | der | |
MD5:F660B910388A42C6B03CD66E12F66577 | SHA256:8FA9A1F3C5D6F6DC7262956E4B88340AB619D32BE59E34E51C46B57B1CE24E84 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\62RRP814.txt | text | |
MD5:2E1ACD27F7305182200F387ACC190BC6 | SHA256:2D26121A195B921585A3CD22D73C06B2D4E7F3F95C0C5A022C4DDF2206583158 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
79
DNS requests
43
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2856 | iexplore.exe | GET | 304 | 23.216.77.79:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?36ca310eb28aaa33 | unknown | — | — | unknown |
2856 | iexplore.exe | GET | 304 | 23.216.77.79:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b150b552b216e1f4 | unknown | — | — | unknown |
2856 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
2856 | iexplore.exe | GET | 200 | 184.24.77.79:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPNFZx9oh6DivqFnefD9sv1YQ%3D%3D | unknown | binary | 503 b | unknown |
2856 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2856 | iexplore.exe | GET | 200 | 184.24.77.79:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQzk3Nv4%2FgtDDklF1jBZfqE%2FA%3D%3D | unknown | binary | 503 b | unknown |
2856 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
2856 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEH1NQqkrQx1%2BZFPnwZqNWHc%3D | unknown | binary | 1.41 Kb | unknown |
2856 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/alphasslcasha256g4/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSPdwLcDiHQXlVfp8h37hrpMerTggQUT8usqMLvq92Db2u%2Fzpg9XFgldhUCDHMpyMx9IikDqs0mIw%3D%3D | unknown | binary | 1.40 Kb | unknown |
2856 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2856 | iexplore.exe | 185.178.208.137:443 | oxy.st | Ddos-guard Ltd | RU | unknown |
2856 | iexplore.exe | 23.216.77.79:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2856 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
2856 | iexplore.exe | 184.24.77.79:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
2856 | iexplore.exe | 216.58.206.74:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
2856 | iexplore.exe | 88.208.46.222:443 | smatr.net | DataWeb Global Group B.V. | NL | unknown |
2856 | iexplore.exe | 23.35.228.23:443 | contextual.media.net | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
oxy.st |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
contextual.media.net |
| shared |
fonts.googleapis.com |
| whitelisted |
ads.themoneytizer.com |
| whitelisted |
smatr.net |
| unknown |
cdn.adlook.me |
| unknown |
ocsp.pki.goog |
| whitelisted |
Threats
Process | Message |
|---|---|
qcmtusvc.exe | MTU instance running...
|
qcmtusvc.exe | Starting: Qualcomm MTU Service
|
qcmtusvc.exe | Startup event signaled: 0
|
qcmtusvc.exe | Start MTU device monitor thread
|
qcmtusvc.exe | Qualcomm MTU Service running in service mode.
|
qcmtusvc.exe | DevMon_THREAD_REG_CHANGE
|
qcmtusvc.exe | DevMon_WAIT_TIMEOUT: scanning system...
|
qcmtusvc.exe | Scanned system, 0 total adapters
|
qcmtusvc.exe | Scanned system, 0 total adapters
|
qcmtusvc.exe | DevMon_WAIT_TIMEOUT: scanning system...
|