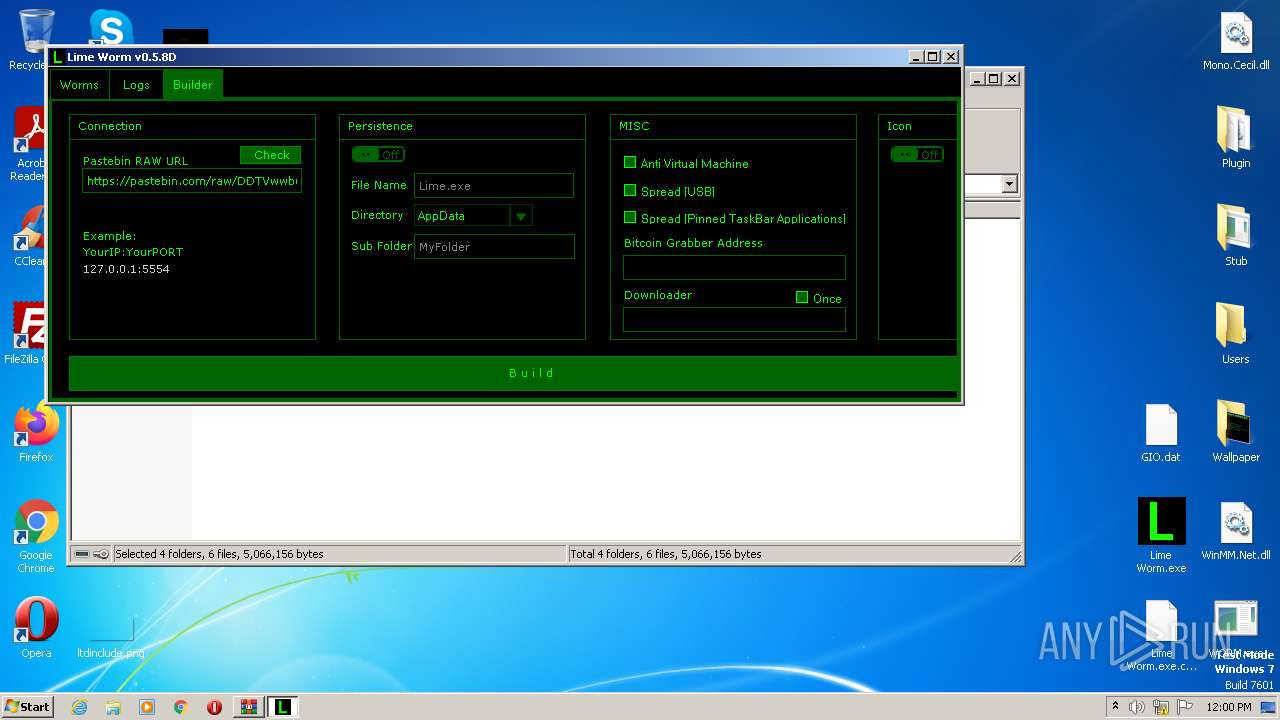
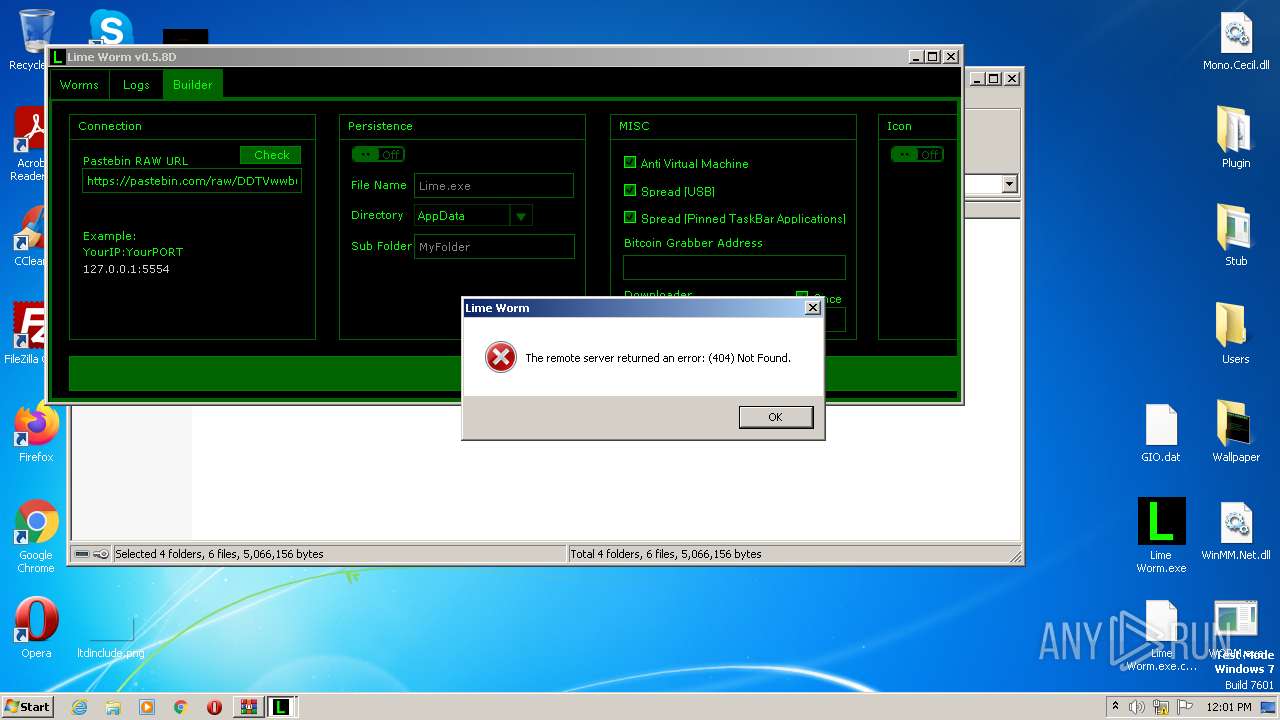
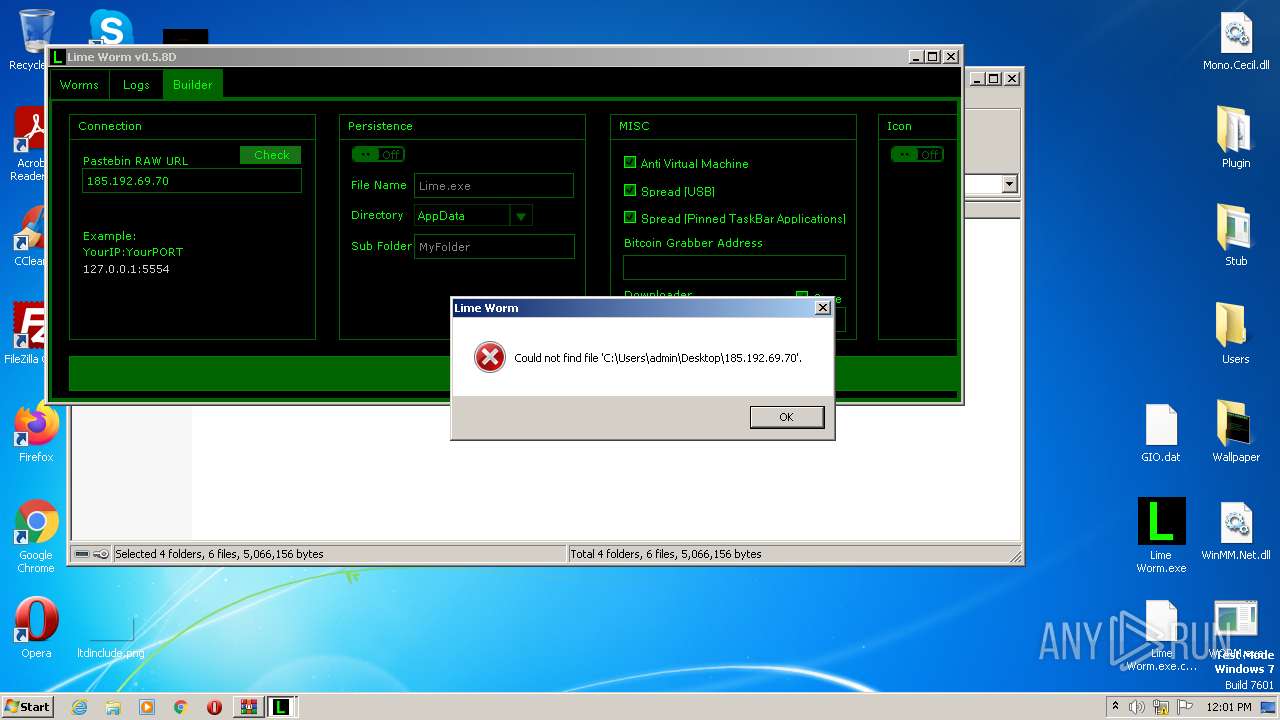
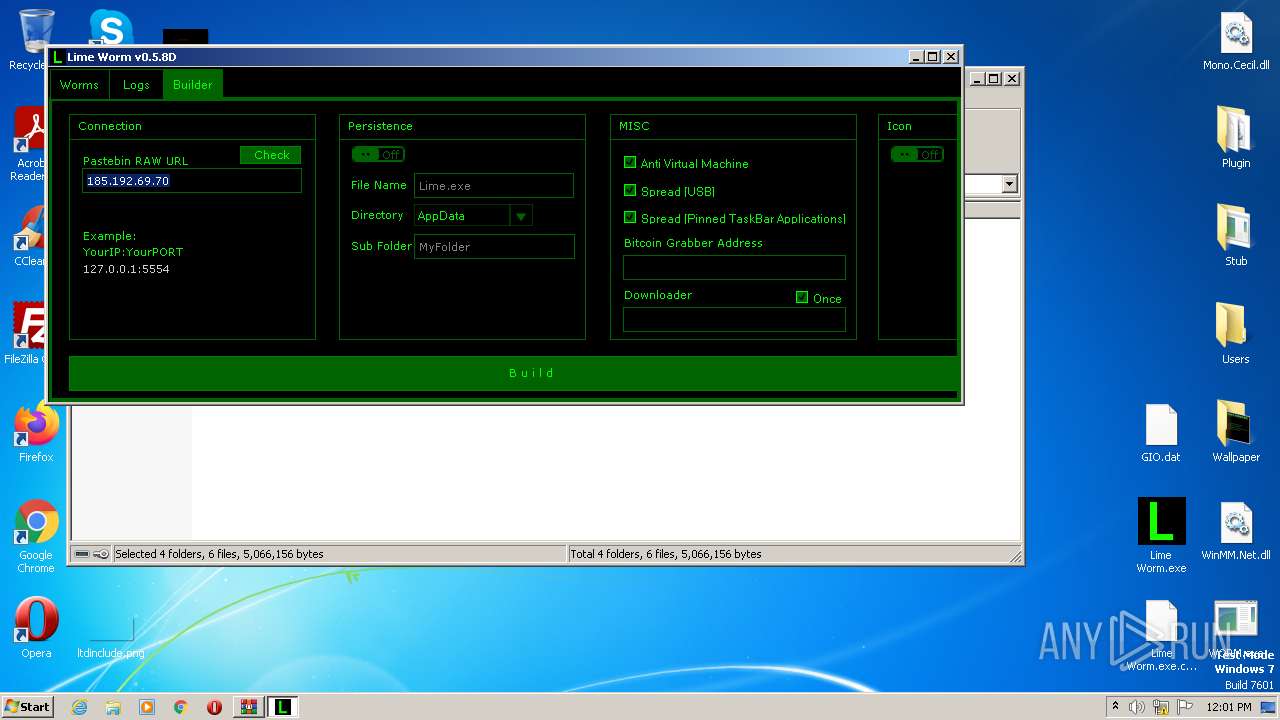
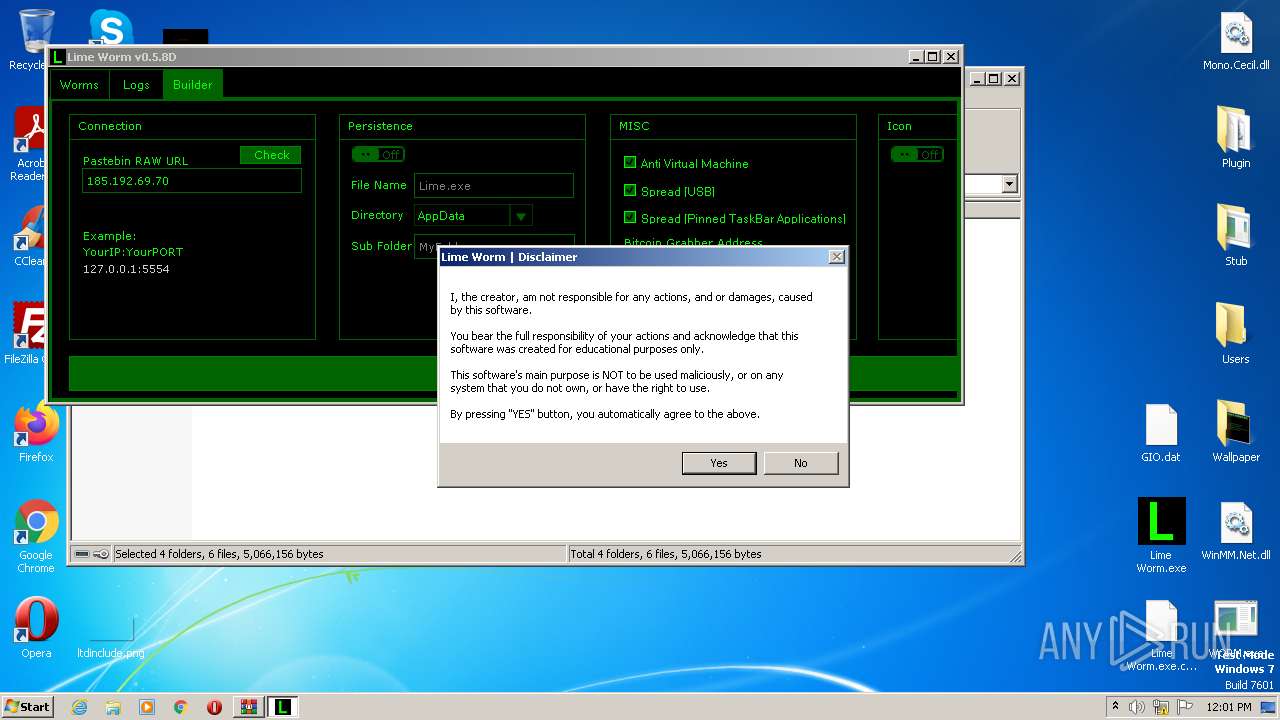
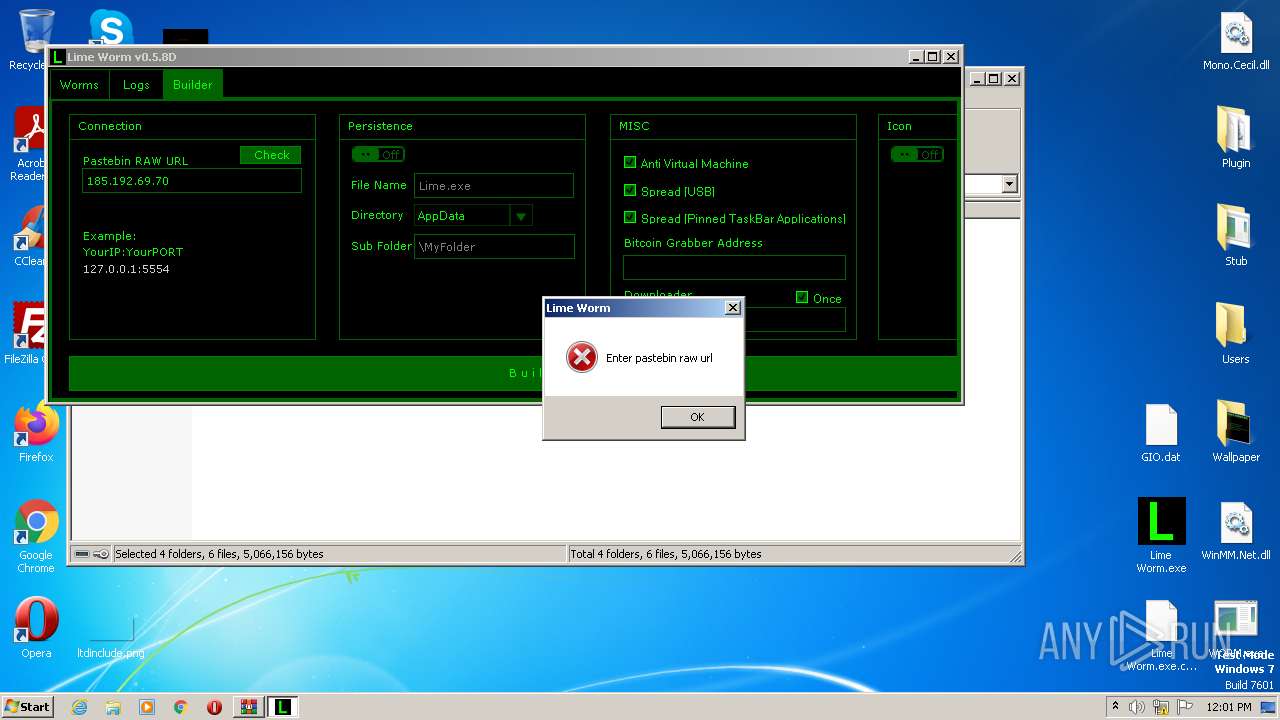
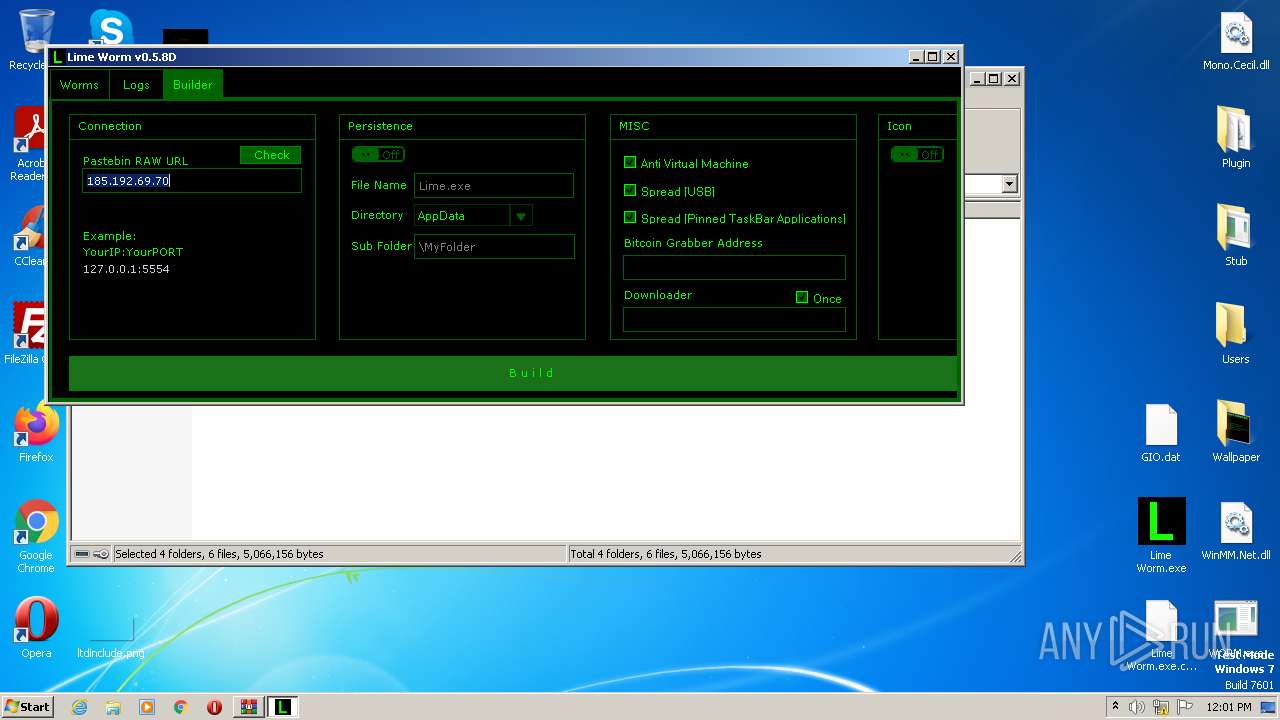
| File name: | Lime-Worm-0.5.8D.zip |
| Full analysis: | https://app.any.run/tasks/cefa3bc4-772f-432b-bfb4-d070dfb809c5 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2023, 10:58:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 791CA6D7C86AE0A0825DCA8BE235813F |
| SHA1: | 6A79D95BCCB2F00E2A2D0DE0D0E5670BB106598A |
| SHA256: | 92C569FD895C2F1FEE9C19C85690F7BB1D2D76B6179DBB005973DFF9F2C37F1A |
| SSDEEP: | 49152:0DxDQv//EARFphh1YPaU3VFccPI/feHkKd1gmG1ASj73fy:21A//EARFdrU3g+dgmGj7Py |
MALICIOUS
The DLL Hijacking
- SearchProtocolHost.exe (PID: 2452)
Loads dropped or rewritten executable
- Lime Worm.exe (PID: 2064)
- Lime Worm.exe (PID: 1956)
Application was dropped or rewritten from another process
- Lime Worm.exe (PID: 1956)
- Lime Worm.exe (PID: 2064)
REVENGERAT detected by memory dumps
- Lime Worm.exe (PID: 2064)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- Lime Worm.exe (PID: 1956)
- Lime Worm.exe (PID: 2064)
INFO
Reads the computer name
- Lime Worm.exe (PID: 1956)
- Lime Worm.exe (PID: 2064)
Reads the machine GUID from the registry
- Lime Worm.exe (PID: 2064)
- Lime Worm.exe (PID: 1956)
The process checks LSA protection
- Lime Worm.exe (PID: 2064)
- Lime Worm.exe (PID: 1956)
Reads Environment values
- Lime Worm.exe (PID: 1956)
- Lime Worm.exe (PID: 2064)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4060)
Checks supported languages
- Lime Worm.exe (PID: 1956)
- Lime Worm.exe (PID: 2064)
Creates files in the program directory
- Lime Worm.exe (PID: 1956)
Manual execution by a user
- Lime Worm.exe (PID: 1956)
- Lime Worm.exe (PID: 2064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
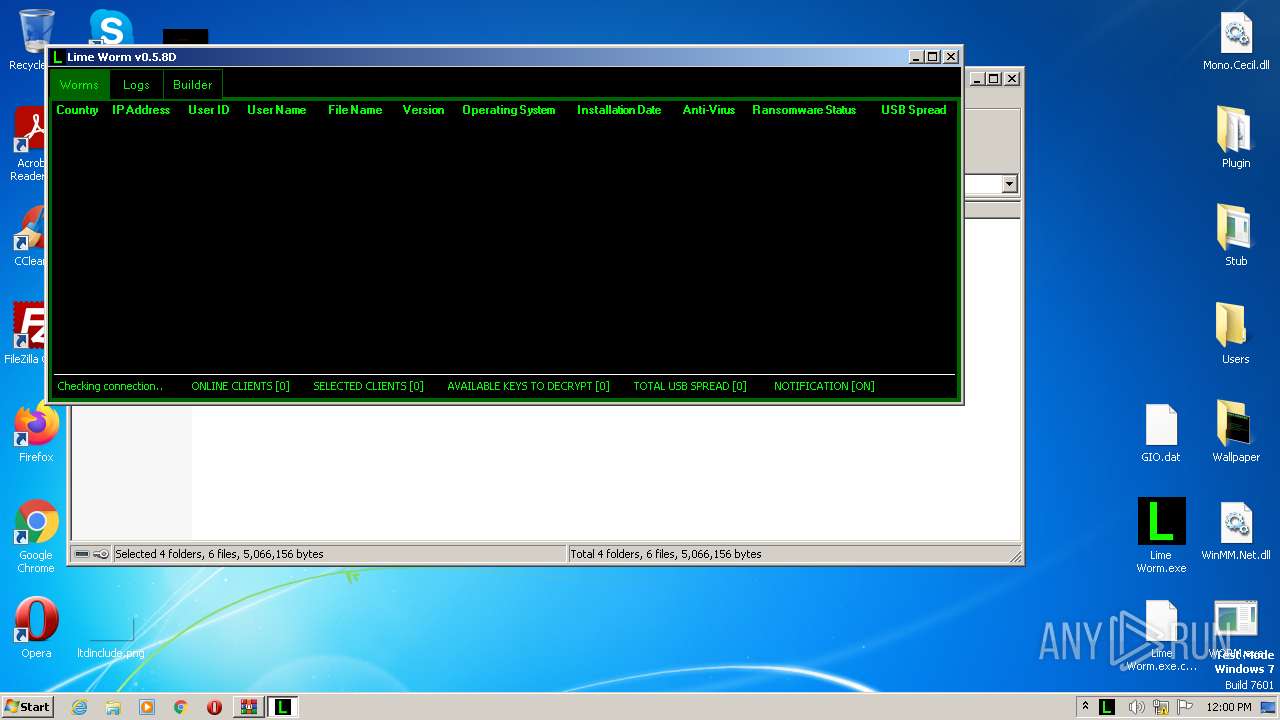
RevengeRat
(PID) Process(2064) Lime Worm.exe
C2 (1)updrive.ddnsking.com
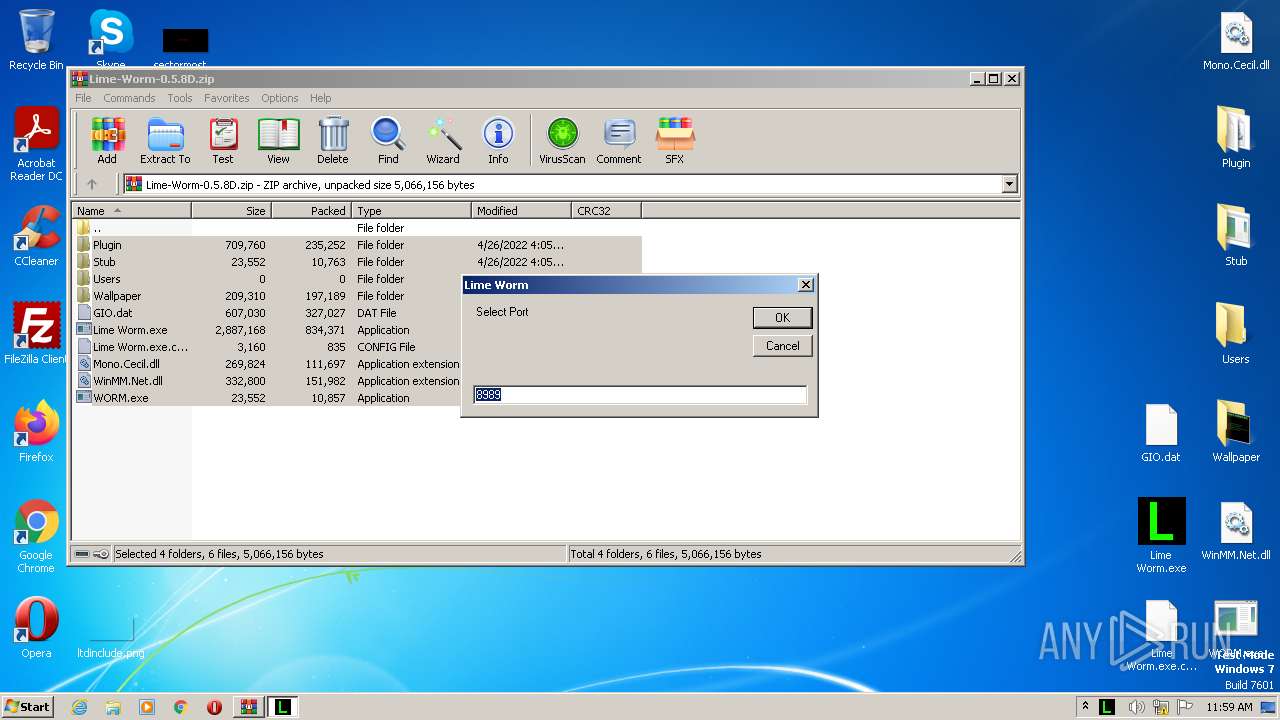
Ports (1)4747
BotnetGuest
Options
MutexRV_MUTEX
Splitter*-]NK[-*
KeyRevenge-RAT
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | GIO.dat |
|---|---|
| ZipUncompressedSize: | 607030 |
| ZipCompressedSize: | 327027 |
| ZipCRC: | 0x4c0a86d7 |
| ZipModifyDate: | 2018:11:18 05:44:04 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
42
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1068 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1956 | "C:\Users\admin\Desktop\Lime Worm.exe" | C:\Users\admin\Desktop\Lime Worm.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Lime Worm Exit code: 0 Version: 0.5.8.0 Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\Desktop\Lime Worm.exe" | C:\Users\admin\Desktop\Lime Worm.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Lime Worm Exit code: 0 Version: 0.5.8.0 Modules
RevengeRat(PID) Process(2064) Lime Worm.exe C2 (1)updrive.ddnsking.com Ports (1)4747 BotnetGuest Options MutexRV_MUTEX Splitter*-]NK[-* KeyRevenge-RAT | |||||||||||||||
| 2452 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3820 | "C:\Users\admin\Desktop\WORM.exe" | C:\Users\admin\Desktop\WORM.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 0.5.8.0 | |||||||||||||||
| 4060 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Lime-Worm-0.5.8D.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 841
Read events
3 807
Write events
34
Delete events
0
Modification events
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1068) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (1068) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\JvaENE\JvaENE.rkr |
Value: 000000000700000005000000408A0000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFA0B93321CCFAD80100000000 | |||
Executable files
19
Suspicious files
10
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.4148\Lime Worm.exe.config | xml | |
MD5:39B1AD9CB375824DC6DE1F0F0663A3B1 | SHA256:082FCA89D4597B77455DE31A29A3510FE3B2AEEF11FA67303650F16BC72FD659 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.4148\GIO.dat | binary | |
MD5:1F897B5825CF91799831862620911AFF | SHA256:5F85518CF71E7B53544E0BD0C1874D1F89A0D6DE7A6AD50683517575AAA56301 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.4148\Plugin\DEC.pdb | binary | |
MD5:7CA7750A76904DE9F0661DA66633431E | SHA256:D2BFDF66EA4CB4892A5EBD278D314B313DCC0A15C15FBCE0FB7E54CBFC7412EB | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.4148\Plugin\DEC.dll | executable | |
MD5:2C0509AE8F4F7CFDF0A45C7018CCAFA9 | SHA256:B8FA8DA0990A4BF496602D1DD0F352148A3612C6BA34739F08CC62DEFFAFD0D5 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.4148\Plugin\DET.pdb | binary | |
MD5:4A627F544E4539F9D90A7B9EEC354356 | SHA256:40336B3289D212259A622479BC5CFFAC0576A46B6BCA2634EEC7411FA4A73192 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.4148\Plugin\ENC.pdb | binary | |
MD5:AB5022C4D7918CCE66D2CC5BA96130CE | SHA256:C28DEB702B9DA140EDF76977F126A3BC1E5D2598452E4911DB849DED394F03D8 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.4148\Lime Worm.exe | executable | |
MD5:7028559ABF0CCEBF9692EB24651B4BE1 | SHA256:B437592443E6C798AC25566400E1A1B4F29EF76A63BC5CD112316F5F4F34E45E | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.4148\Plugin\DET.xml | xml | |
MD5:044FE16A3E37DA552AB19F39975AA740 | SHA256:03EF70D0609F7C45A9E8A25D2527A5B0B07278FCB18560E6DEB559CB90FC76BC | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.4148\Plugin\ENC.dll | executable | |
MD5:133FEDA41E1F83417BBBA58012D45113 | SHA256:2BDA1203B984DEC579A00CD9501F438D53FD67B9C22370A8A982098FB87E5494 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.4148\Plugin\ENC.xml | xml | |
MD5:E68ED9A4DE7A57824F2A56C0740810AB | SHA256:BBD4B40988F73CF21E9FFACE4D745D09728207757DCE50CACE4B99EAA0355A81 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
4
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 158.101.44.242:80 | http://checkip.dyndns.org/ | US | html | 105 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
292 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 158.101.44.242:80 | checkip.dyndns.org | ORACLE-BMC-31898 | US | malicious |
— | — | 185.192.69.70:8989 | — | Clouvider Limited | GB | unknown |
— | — | 104.20.68.143:443 | pastebin.com | CLOUDFLARENET | — | malicious |
— | — | 104.20.67.143:443 | pastebin.com | CLOUDFLARENET | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
updrive.ddnsking.com |
| malicious |
pastebin.com |
| malicious |
checkip.dyndns.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1076 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddnsking .com |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
— | — | Misc activity | AV INFO Query to checkip.dyndns. Domain |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup - checkip.dyndns.org |
1 ETPRO signatures available at the full report