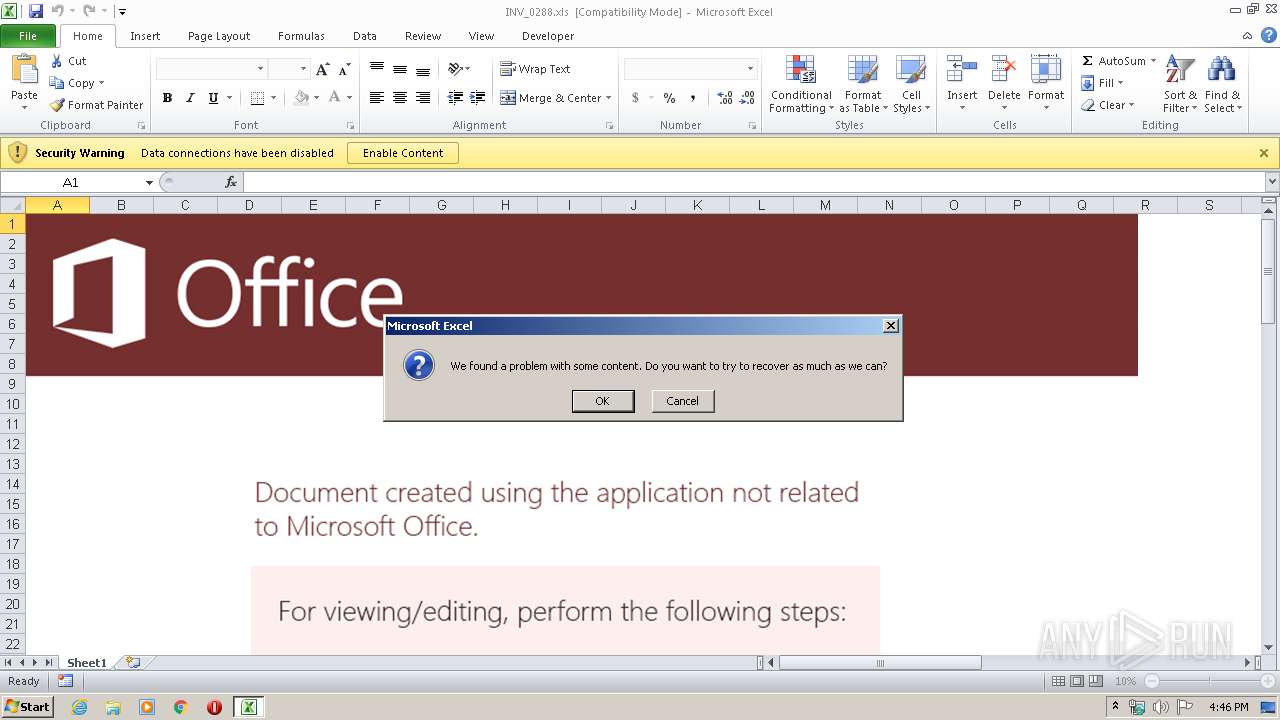
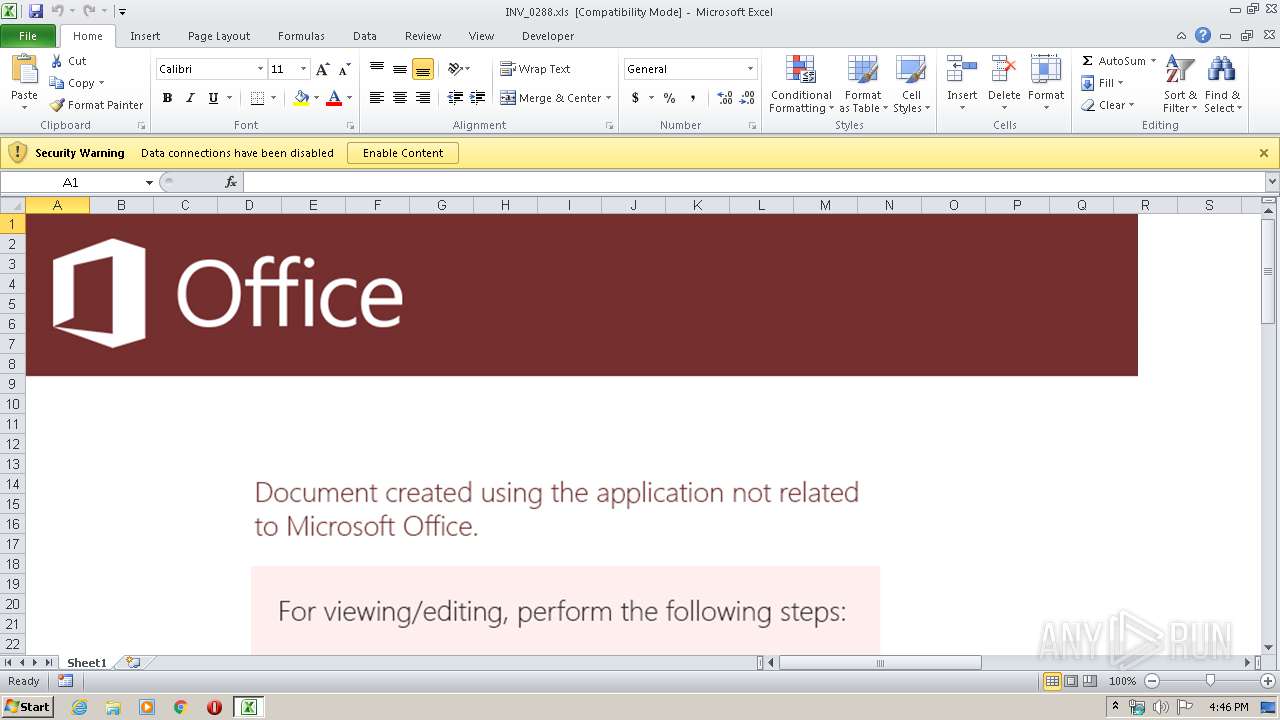
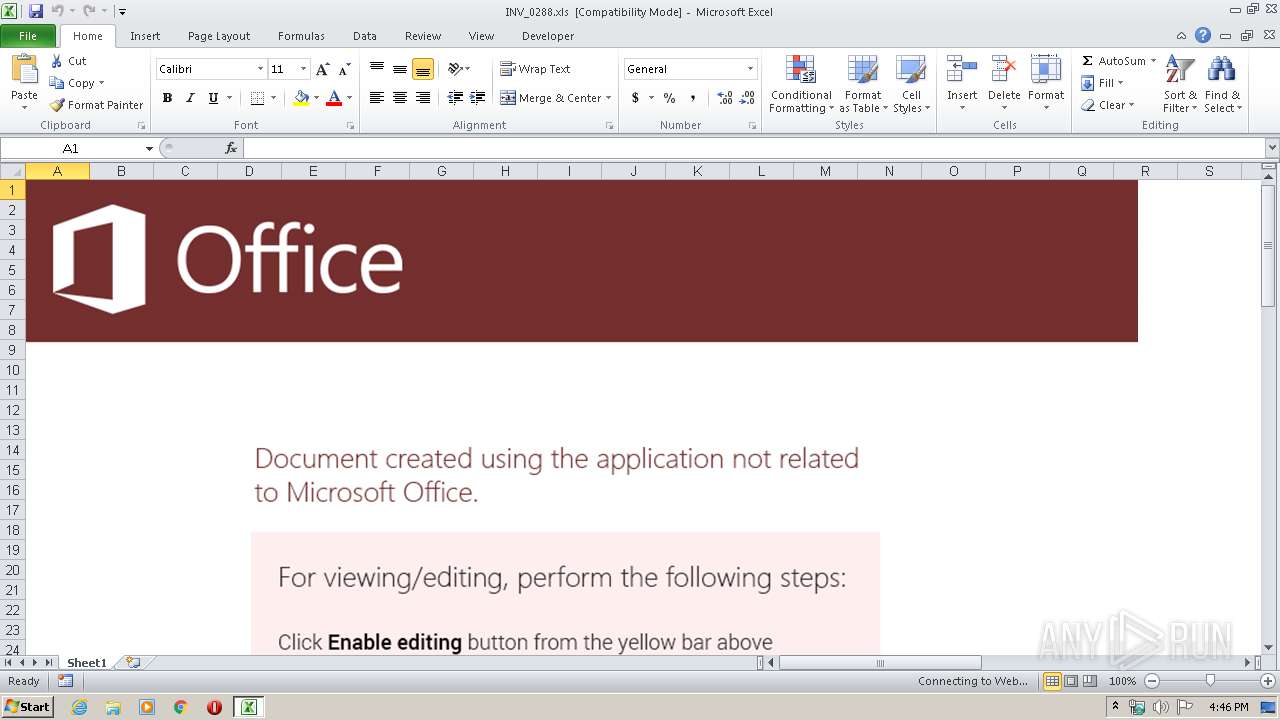
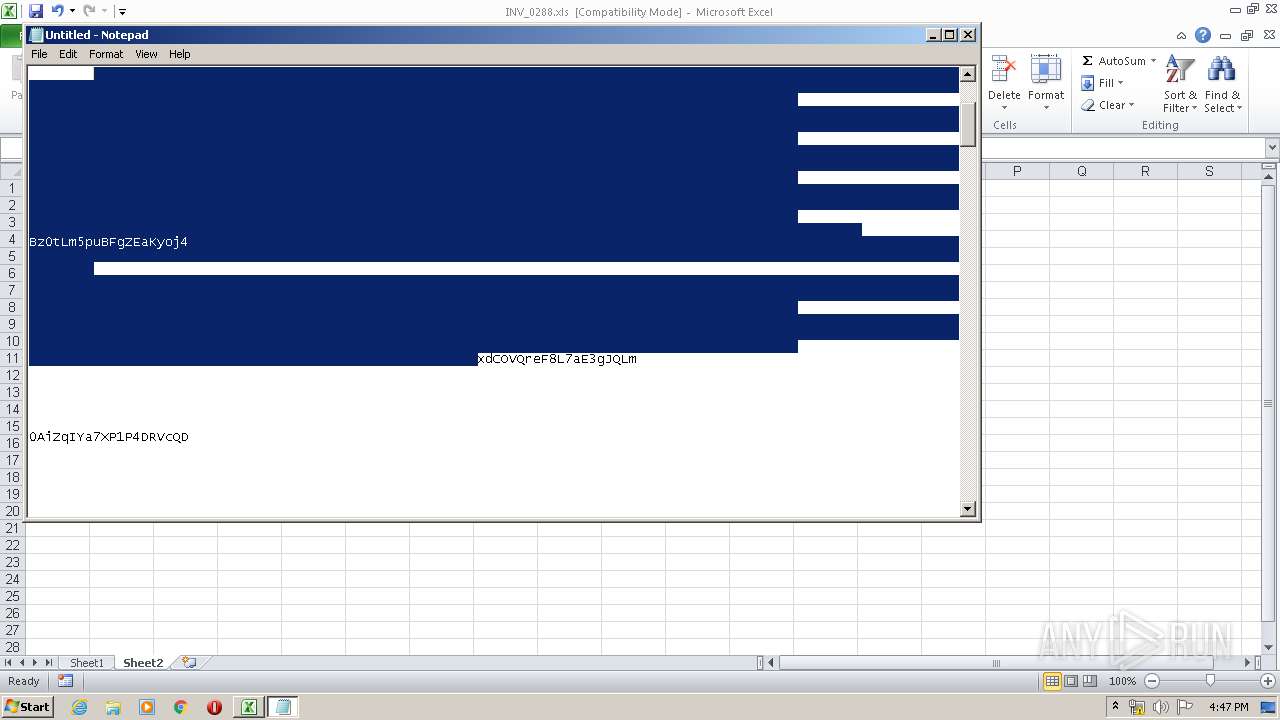
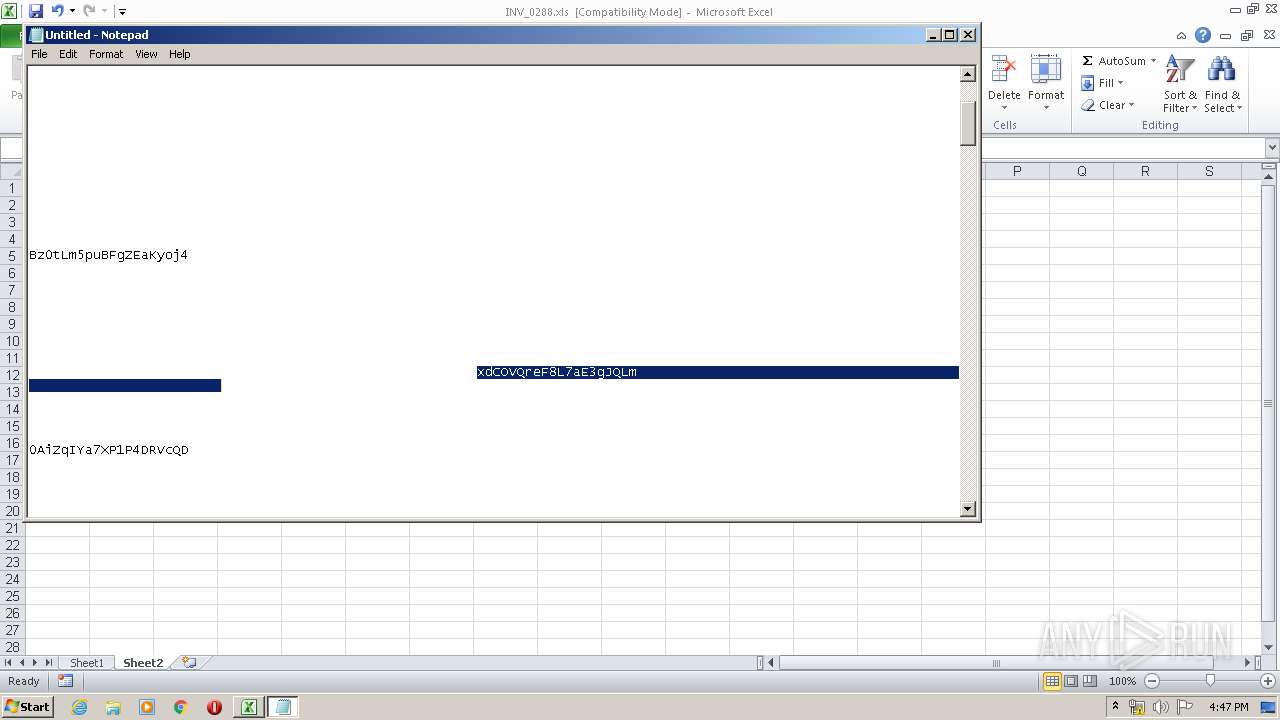
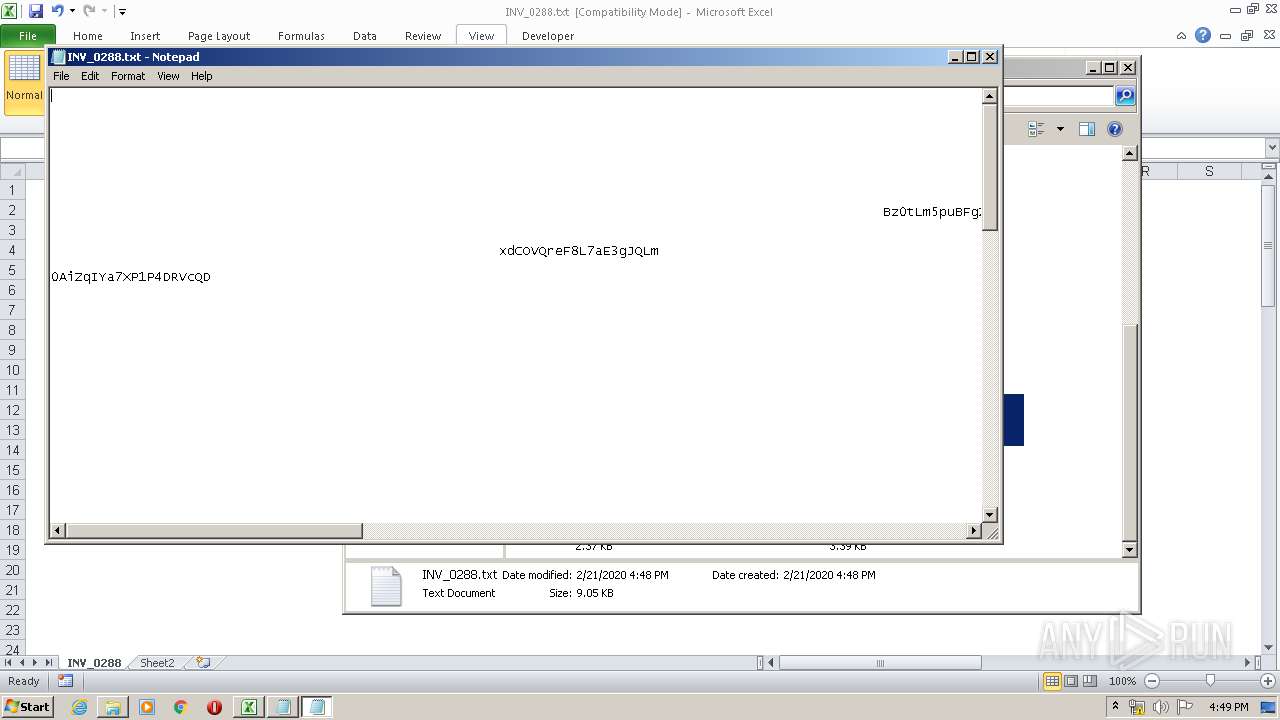
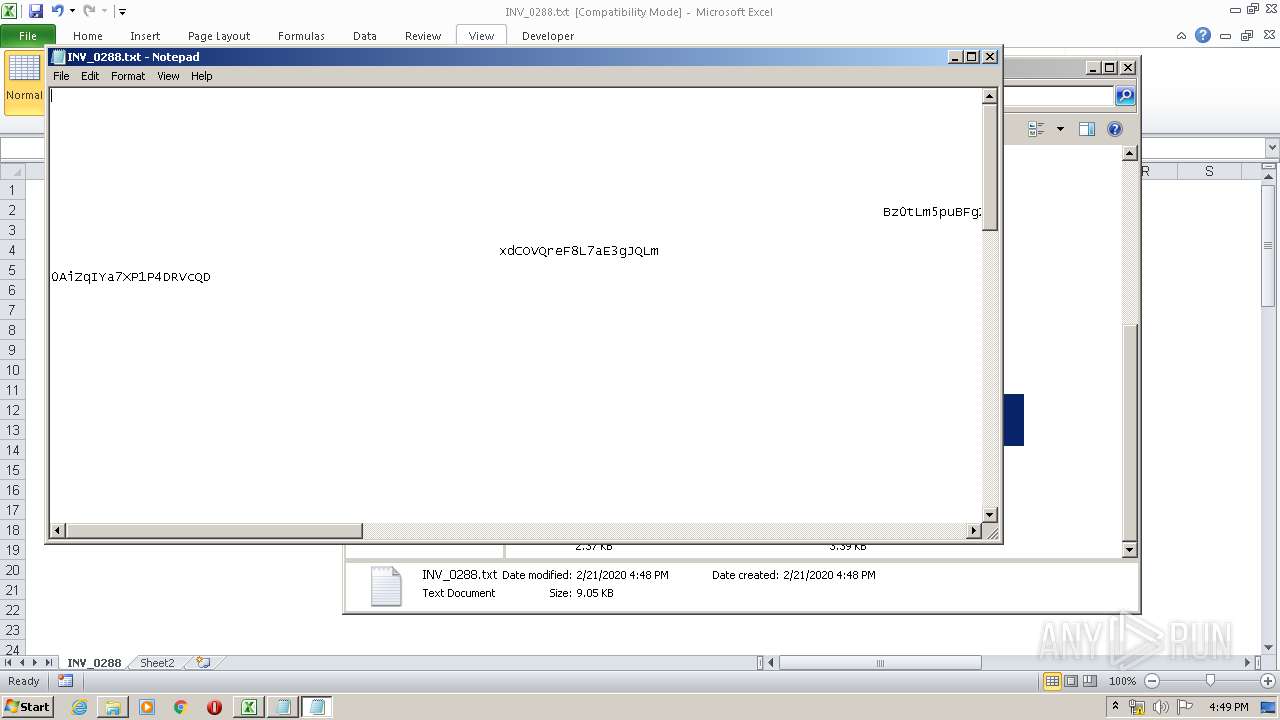
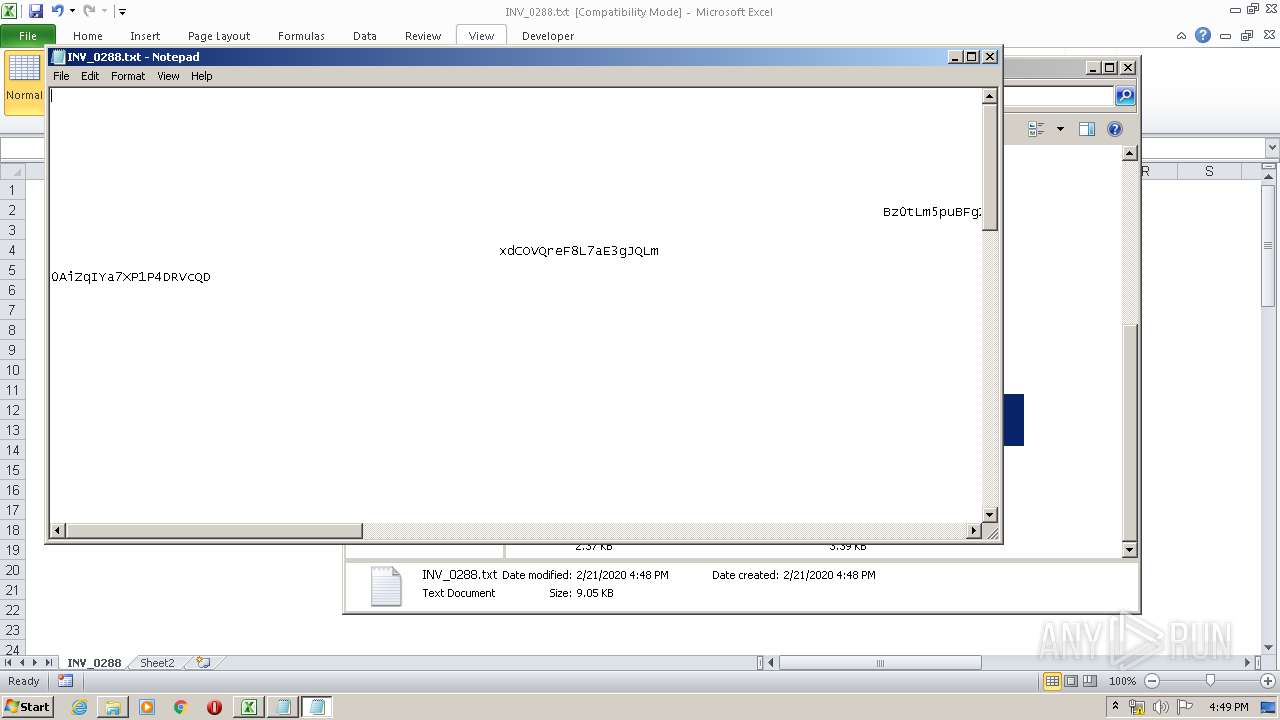
| File name: | C:\Users\admin\AppData\Local\Temp\Rar$DIb3240.26424\INV_0288.xls |
| Full analysis: | https://app.any.run/tasks/35f56fe3-fbcb-4716-9865-9f7fe53f7197 |
| Verdict: | Malicious activity |
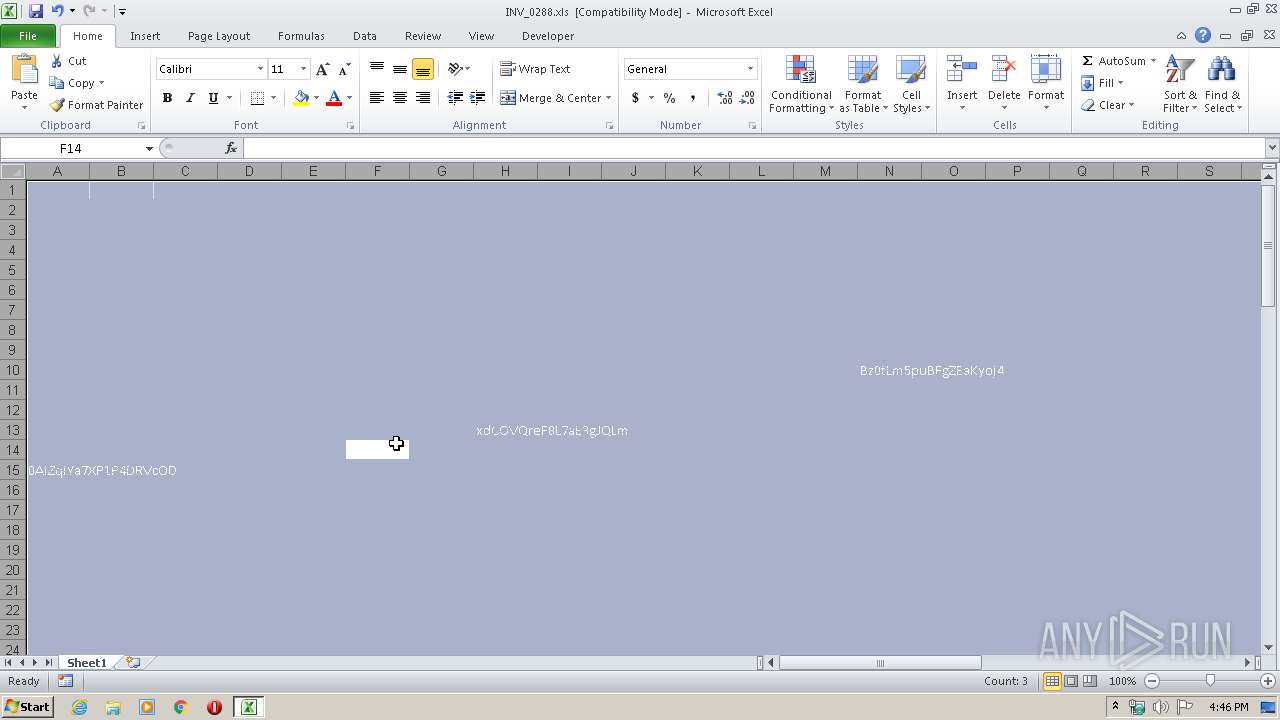
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | February 21, 2020, 16:46:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
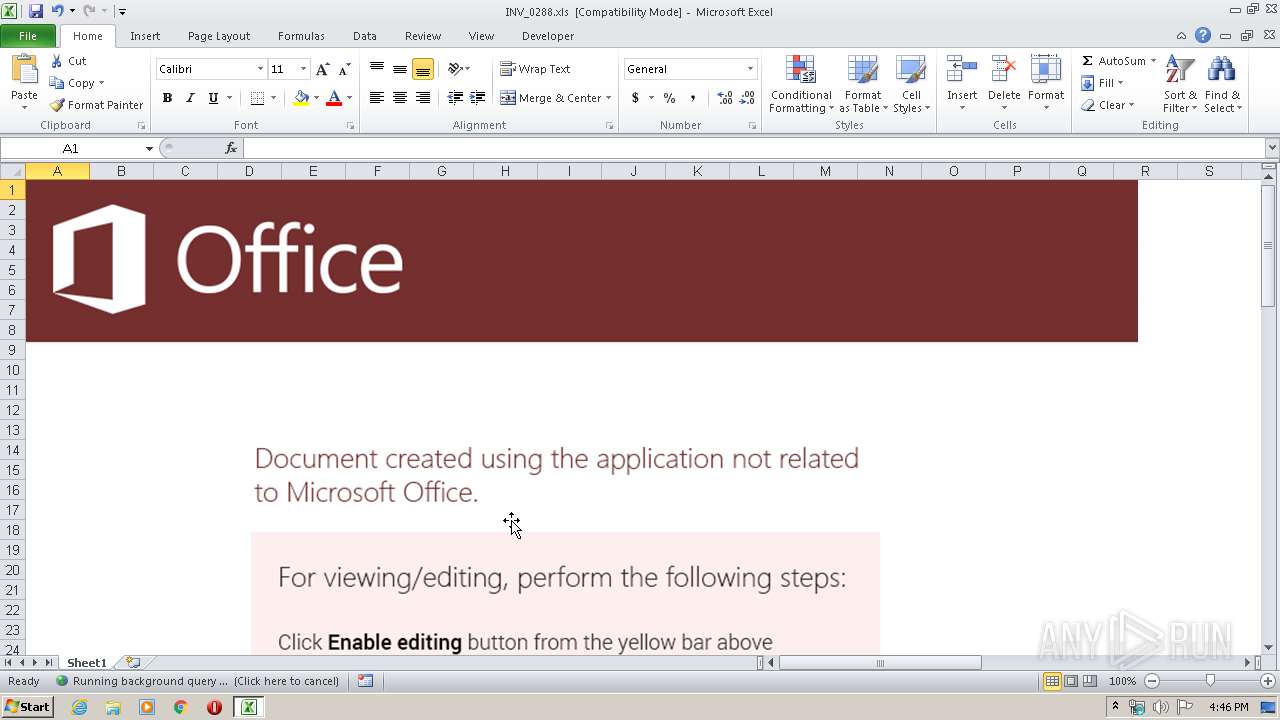
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Comments: UAxqU1aaI2NxFxZpukvF, Name of Creating Application: Microsoft Excel, Create Time/Date: Fri Feb 14 06:29:18 2020, Last Saved Time/Date: Thu Feb 20 12:08:58 2020, Security: 0 |
| MD5: | 87111B61B18AD928134DDC8D0517B60D |
| SHA1: | F120E5F35E2ECFE563DCC5EDB03EEA4868D862C8 |
| SHA256: | 92C10CCA0ACFBF10BBAEBEEDC34B3E9D5558BD58B4295BB6537B748C04759A37 |
| SSDEEP: | 3072:G0k3hbdlylKsgqopeJBWhZFGkE+cL2NdlzyF0Vi4m+Oi9l1isYgmNWl1oH2HUU:Rk3hbdlylKsgqopeJBWhZFVE+W2NdsFW |
MALICIOUS
No malicious indicators.SUSPICIOUS
Unusual connect from Microsoft Office
- EXCEL.EXE (PID: 3144)
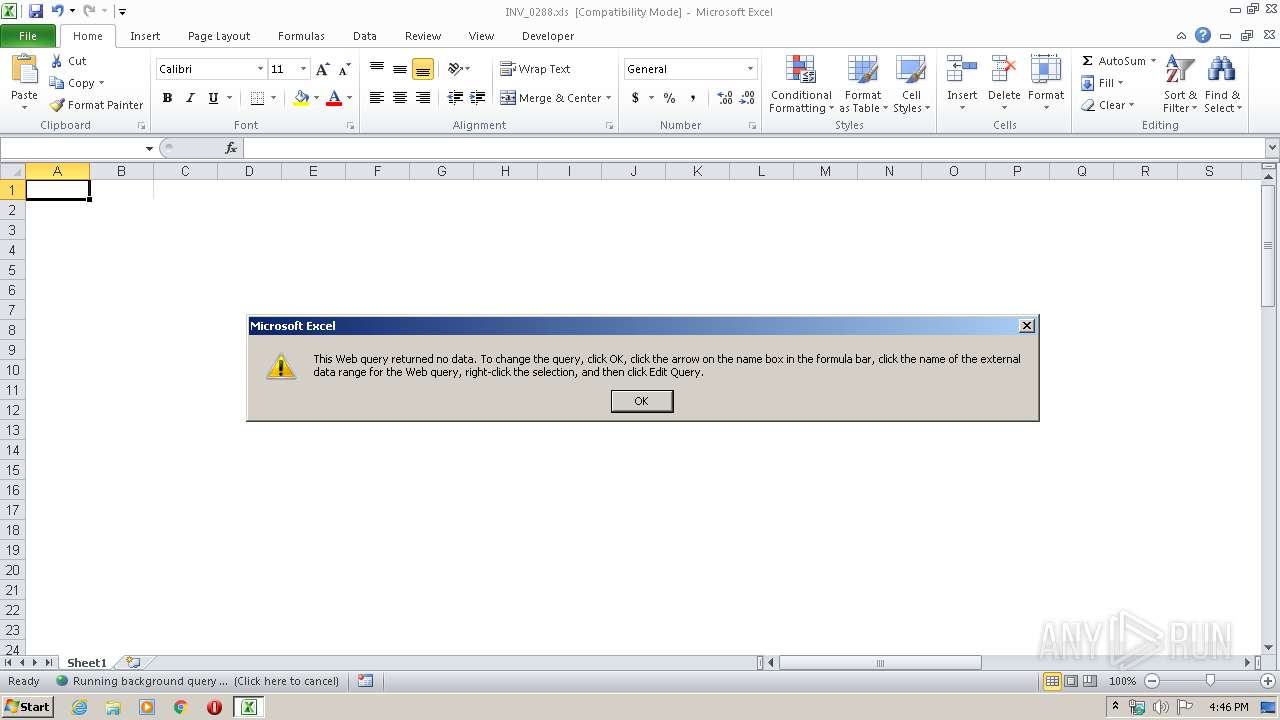
Reads Internet Cache Settings
- EXCEL.EXE (PID: 3144)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3144)
Manual execution by user
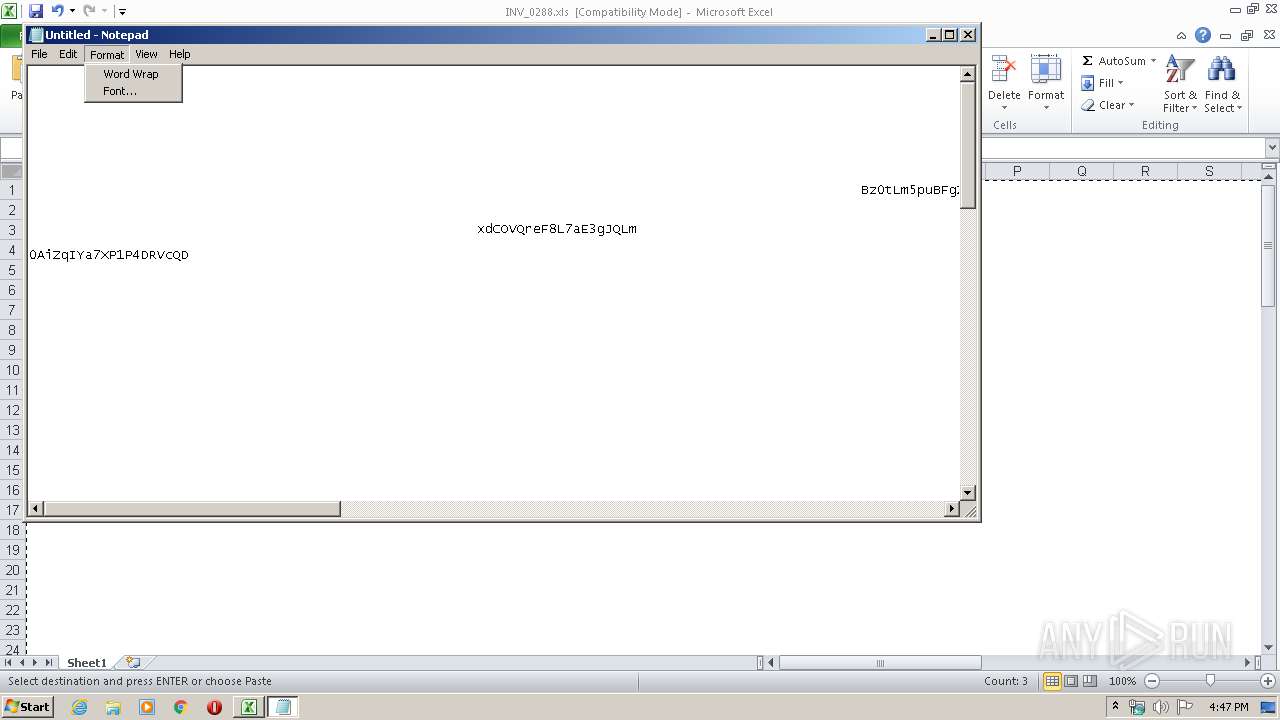
- explorer.exe (PID: 3392)
- NOTEPAD.EXE (PID: 3584)
- verclsid.exe (PID: 2888)
- notepad.exe (PID: 1784)
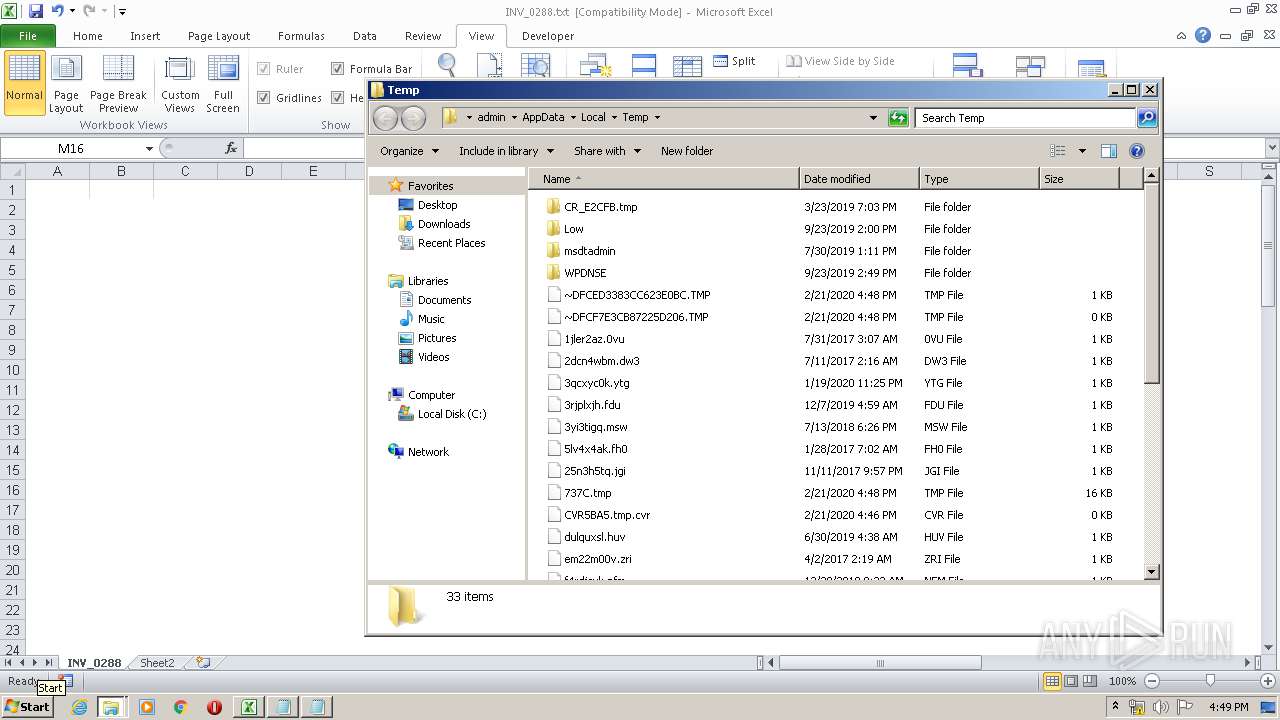
Creates files in the user directory
- EXCEL.EXE (PID: 3144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | - |
|---|---|
| Comments: | UAxqU1aaI2NxFxZpukvF |
| LastModifiedBy: | - |
| Software: | Microsoft Excel |
| CreateDate: | 2020:02:14 06:29:18 |
| ModifyDate: | 2020:02:20 12:08:58 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
44
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1784 | "C:\Windows\system32\notepad.exe" | C:\Windows\system32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2888 | "C:\Windows\system32\verclsid.exe" /S /C {0B2C9183-C9FA-4C53-AE21-C900B0C39965} /I {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} /X 0x401 | C:\Windows\system32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3144 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3392 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
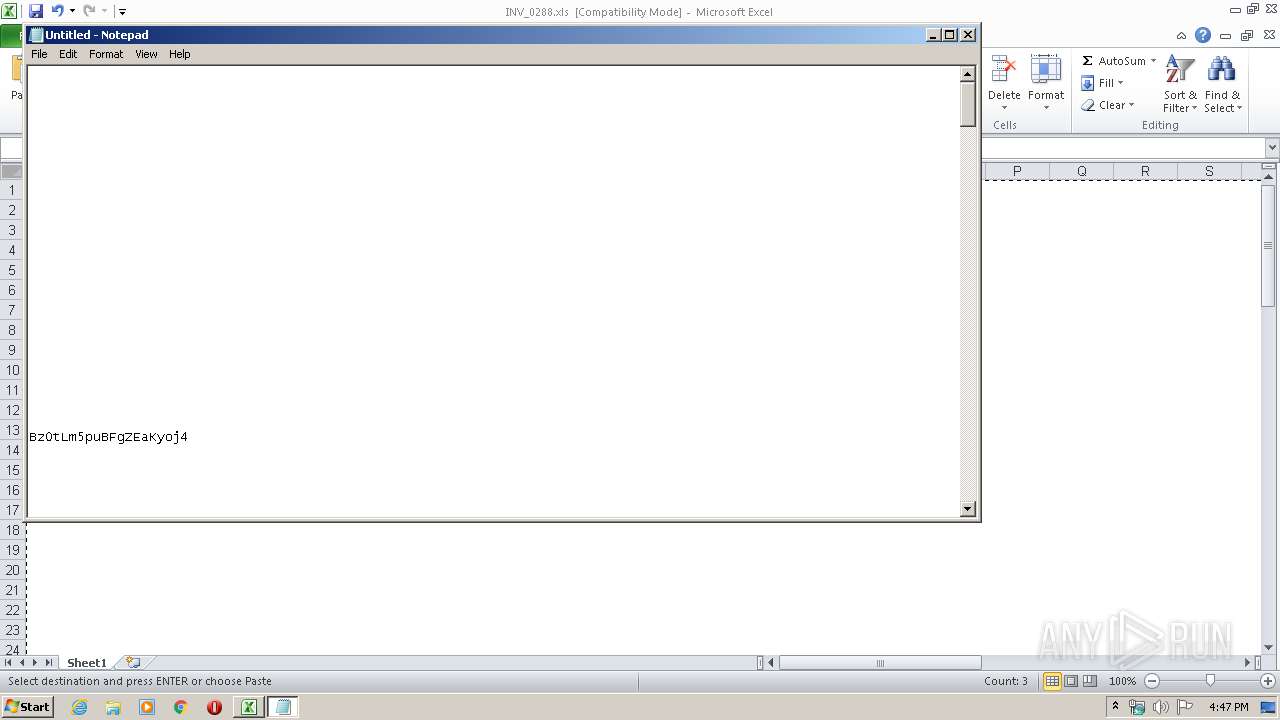
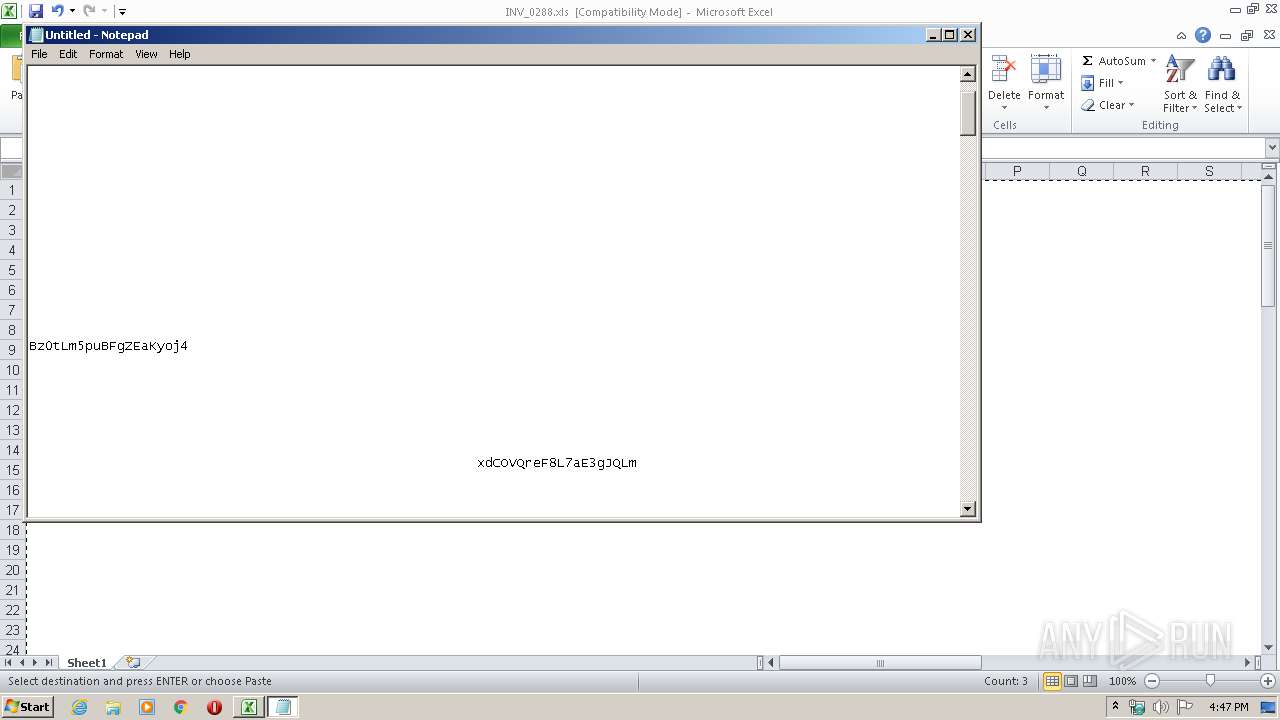
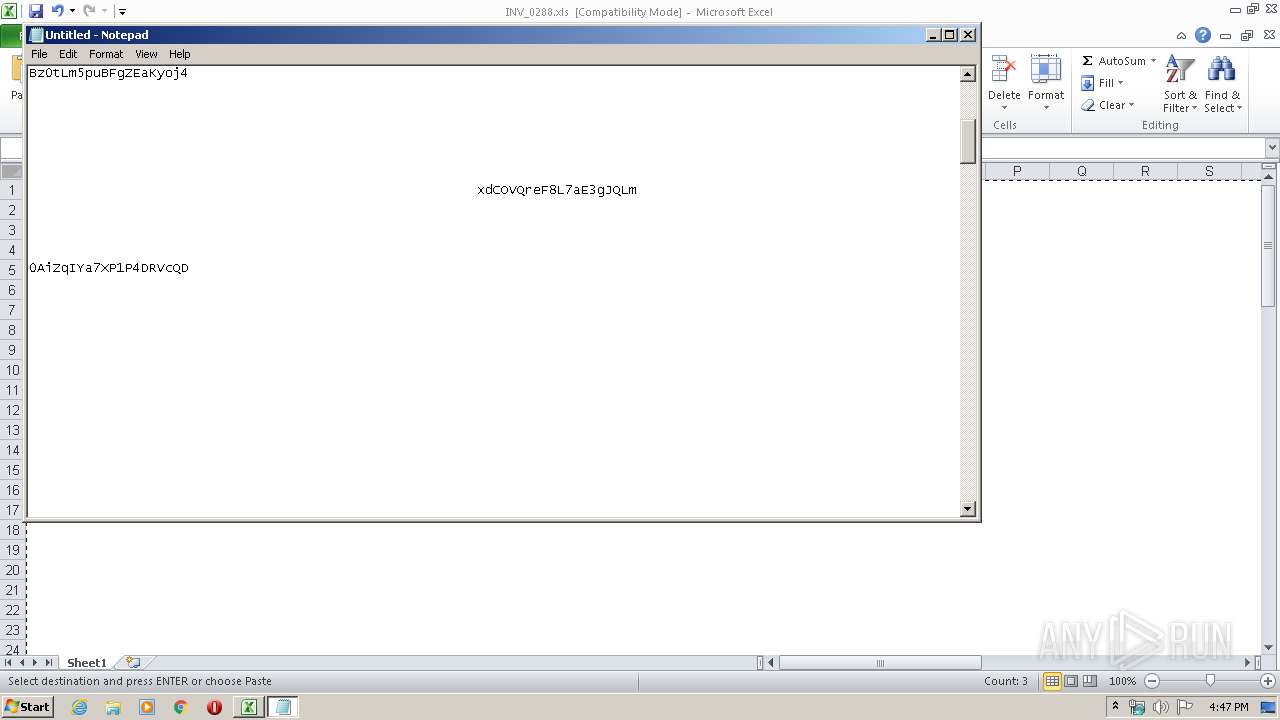
| 3584 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\INV_0288.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 756
Read events
1 572
Write events
157
Delete events
27
Modification events
| (PID) Process: | (3144) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | %{3 |
Value: 257B3300480C0000010000000000000000000000 | |||
| (PID) Process: | (3144) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3144) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3144) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3144) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3144) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3144) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3144) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3144) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3144) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
34
Text files
9
Unknown types
10
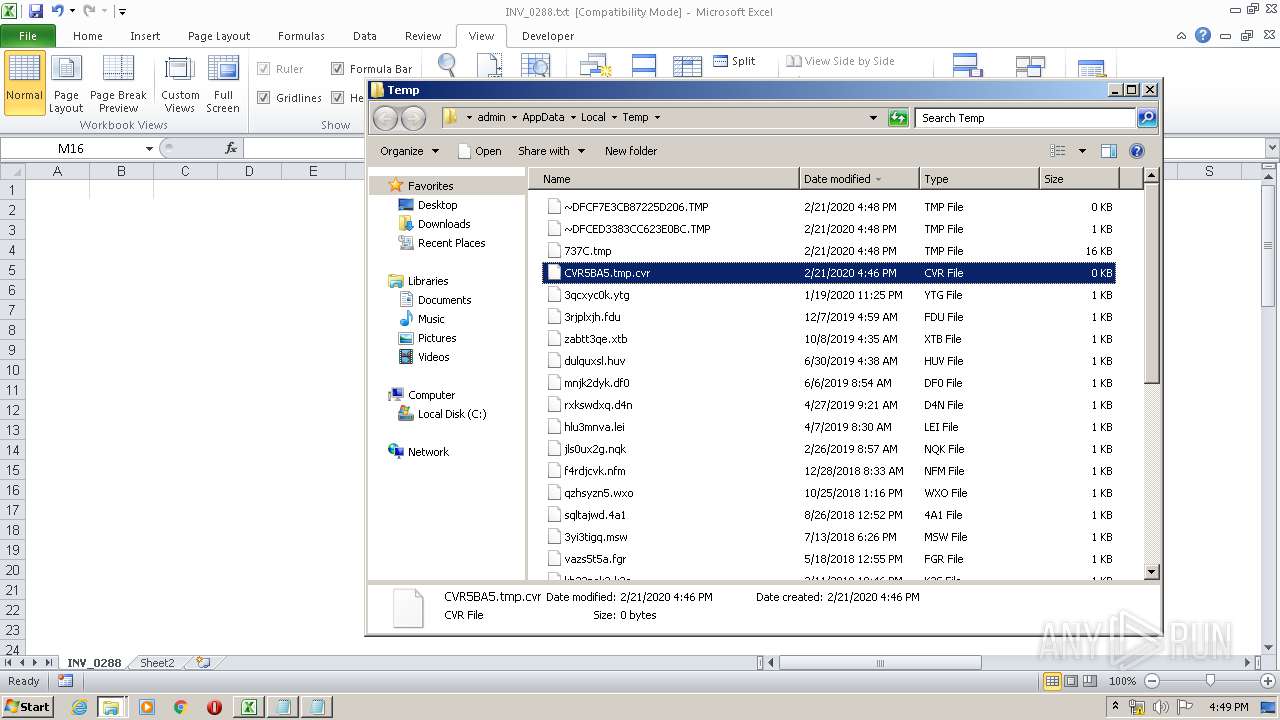
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3144 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR5BA5.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3144 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Cab92E3.tmp | — | |
MD5:— | SHA256:— | |||
| 3144 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Tar92E4.tmp | — | |
MD5:— | SHA256:— | |||
| 3144 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\{5CDD78E9-82C9-40CD-9E74-A7C2F8C0913C} | — | |
MD5:— | SHA256:— | |||
| 3144 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\{35E512DE-6EAA-4DA1-A2FF-B3F75DE88823} | — | |
MD5:— | SHA256:— | |||
| 3144 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\17KZOABL.txt | — | |
MD5:— | SHA256:— | |||
| 3144 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | binary | |
MD5:— | SHA256:— | |||
| 3144 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{79F4ECF9-2678-4400-B219-1D4BBFBEEA76}.FSD | binary | |
MD5:— | SHA256:— | |||
| 3144 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | der | |
MD5:— | SHA256:— | |||
| 3144 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFCF7E3CB87225D206.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
8
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3144 | EXCEL.EXE | GET | 200 | 195.138.255.24:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | DE | der | 1.37 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3144 | EXCEL.EXE | 161.117.177.248:443 | merystol.xyz | — | SG | suspicious |
3144 | EXCEL.EXE | 195.138.255.24:80 | isrg.trustid.ocsp.identrust.com | AS33891 Netzbetrieb GmbH | DE | whitelisted |
3144 | EXCEL.EXE | 195.138.255.17:80 | ocsp.int-x3.letsencrypt.org | AS33891 Netzbetrieb GmbH | DE | whitelisted |
3144 | EXCEL.EXE | 172.217.22.14:443 | google.com | Google Inc. | US | whitelisted |
3144 | EXCEL.EXE | 216.58.207.36:443 | www.google.com | Google Inc. | US | whitelisted |
3144 | EXCEL.EXE | 172.217.16.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
merystol.xyz |
| suspicious |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
google.com |
| malicious |
ocsp.pki.goog |
| whitelisted |
www.google.com |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3144 | EXCEL.EXE | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |