| File name: | UnderDDosV2.exe |
| Full analysis: | https://app.any.run/tasks/9e924a6f-ac64-4b4d-ace7-6aa19b1839be |
| Verdict: | Malicious activity |
| Analysis date: | August 28, 2024, 18:41:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 8AD5BA1986C42FBCEF52A7B408924E6B |
| SHA1: | FB40BC7B38FDBE82E9CE34143C09815BB7EF136E |
| SHA256: | 92A664AF27C47DE5DC5831BF2C4C44A621255E7795BCF1B115F3774E023F0C79 |
| SSDEEP: | 98304:kRKBAOX8JGHna2M0GGRRPSolBySmsEDC0o883EJ8xCTwCMvYK+0HI6jdoRpl89a4:PcTeRi/BqnnnywBBX3 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- UnderDDosV2.exe (PID: 964)
Process drops legitimate windows executable
- UnderDDosV2.exe (PID: 964)
Process drops python dynamic module
- UnderDDosV2.exe (PID: 964)
The process drops C-runtime libraries
- UnderDDosV2.exe (PID: 964)
Executable content was dropped or overwritten
- UnderDDosV2.exe (PID: 964)
Application launched itself
- UnderDDosV2.exe (PID: 964)
Loads Python modules
- UnderDDosV2.exe (PID: 6684)
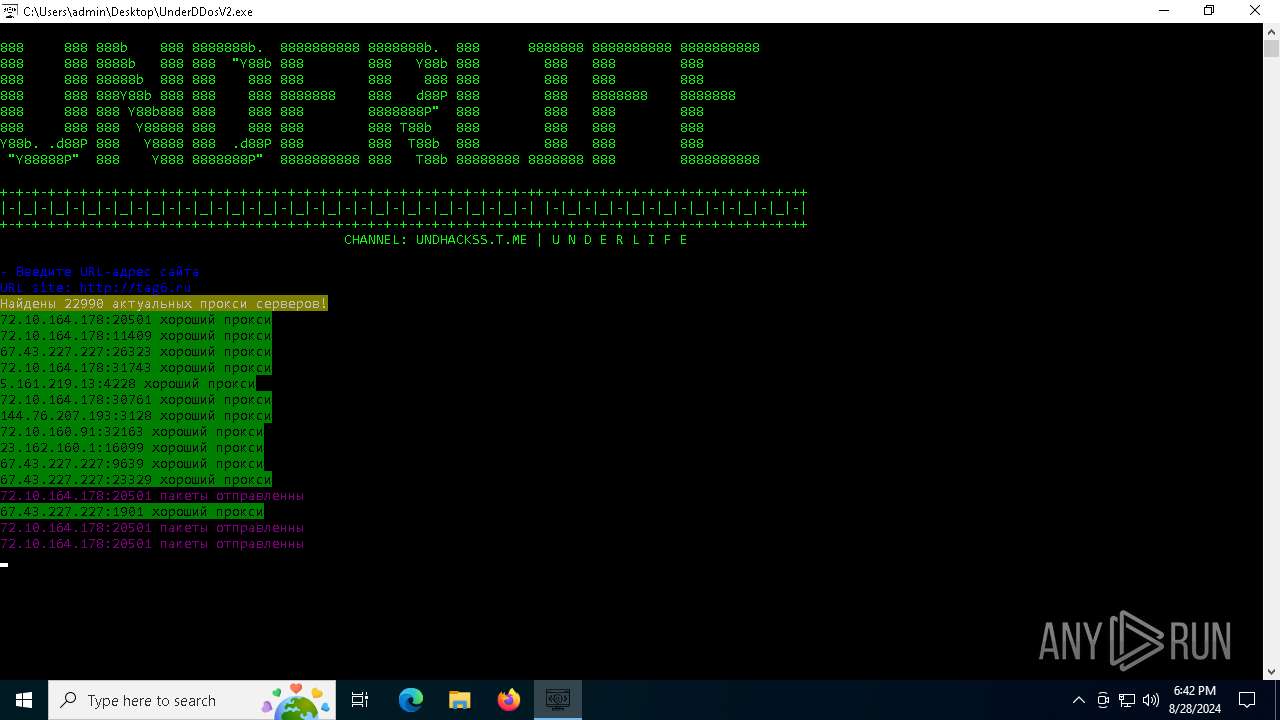
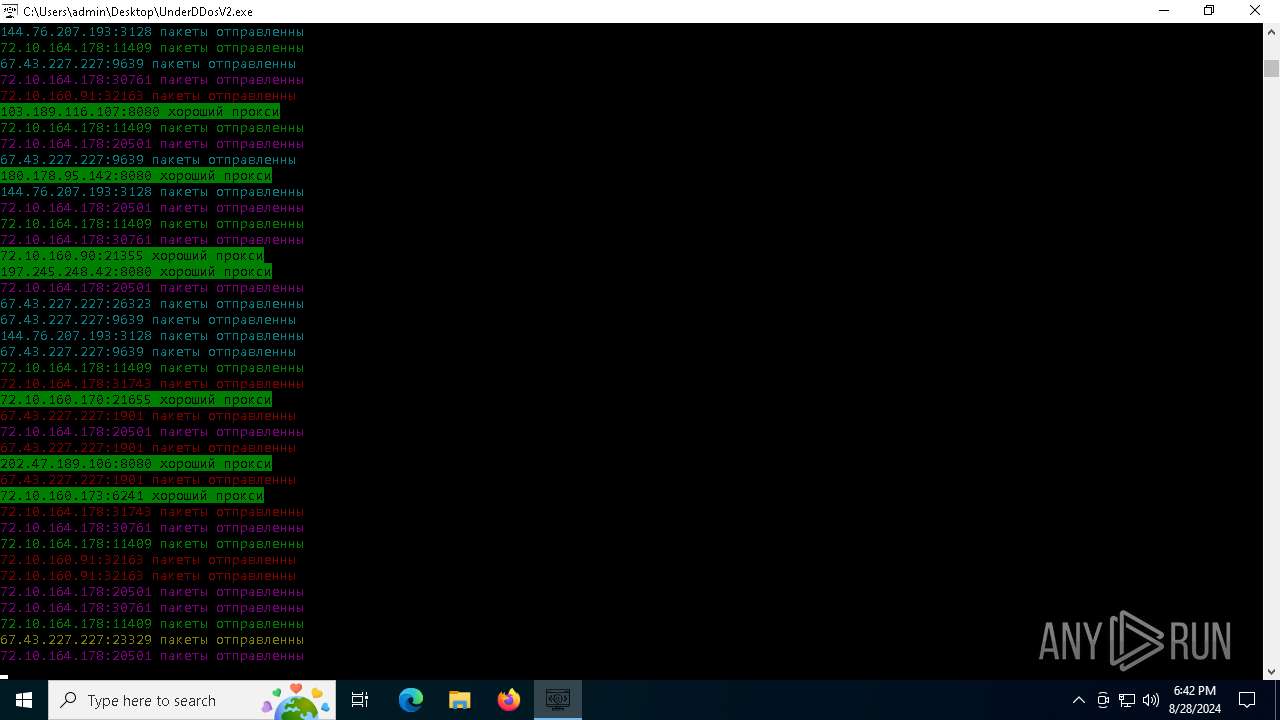
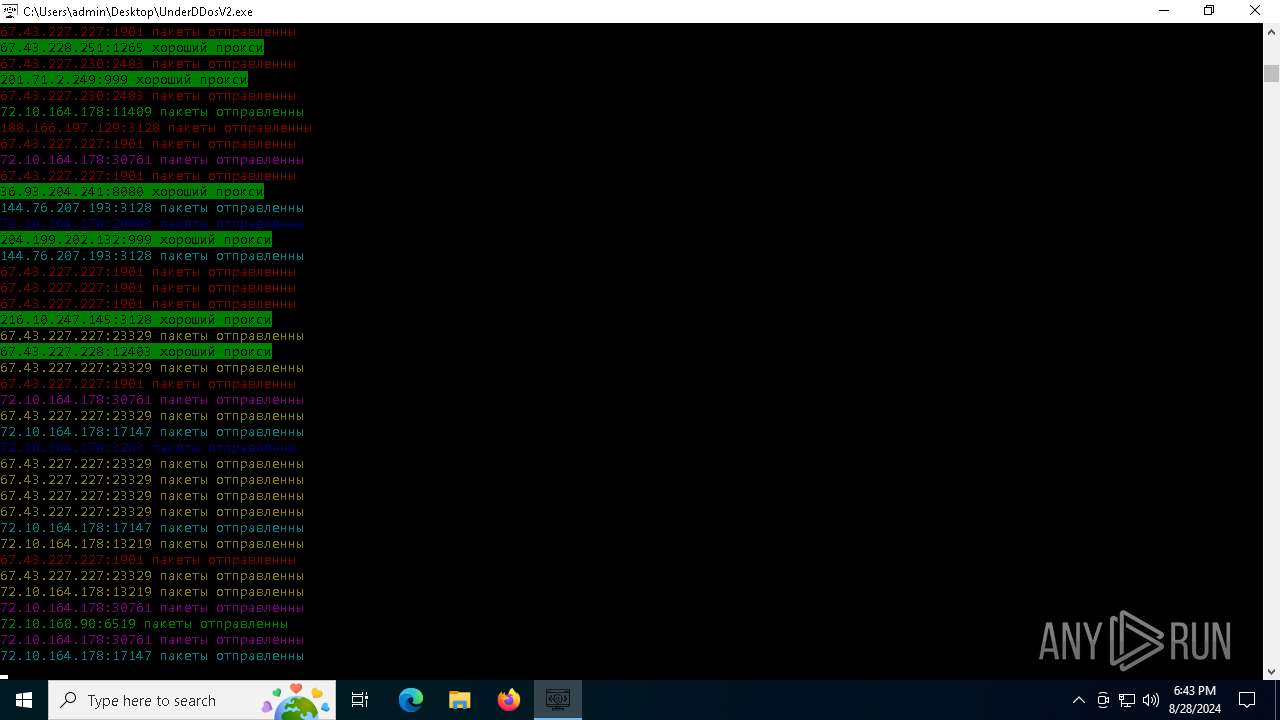
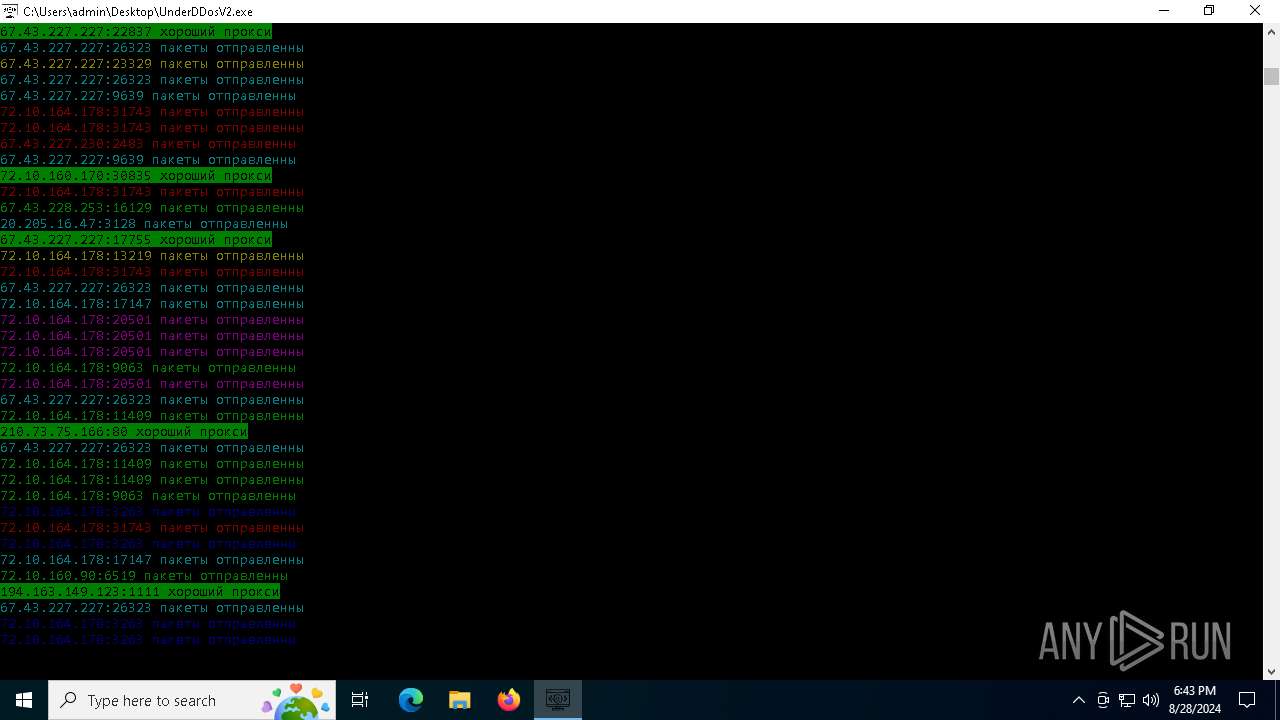
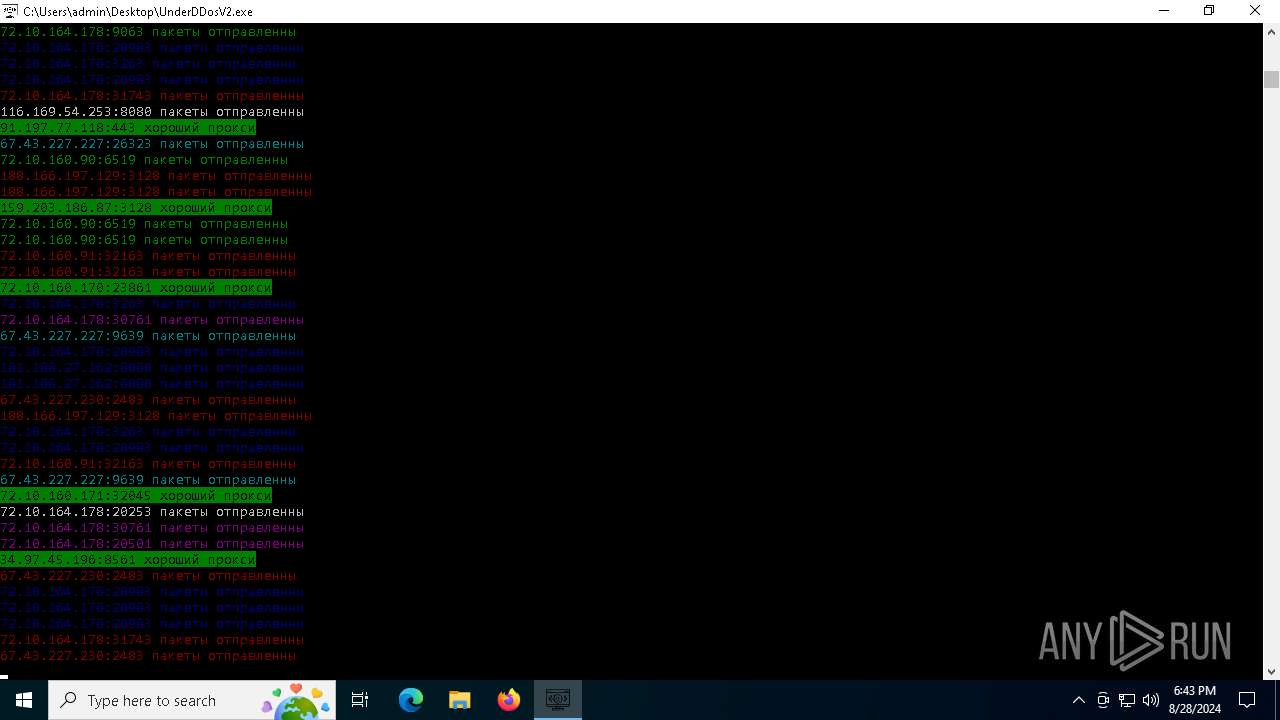
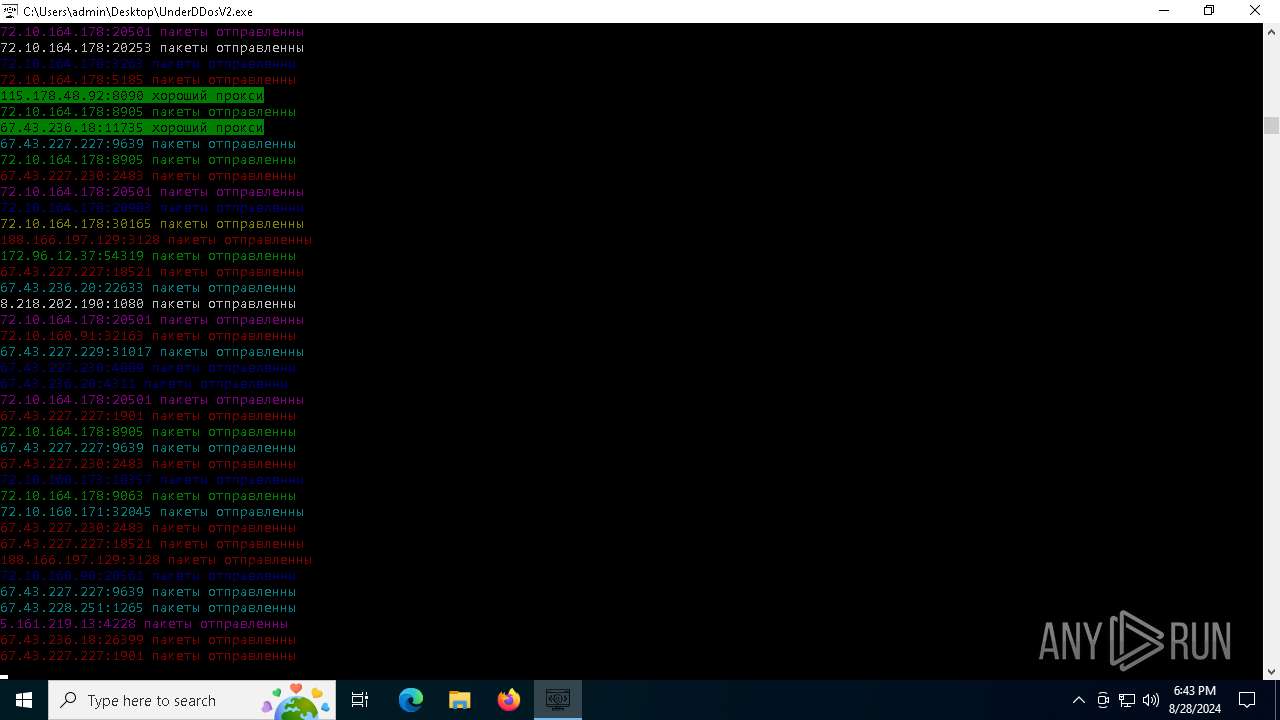
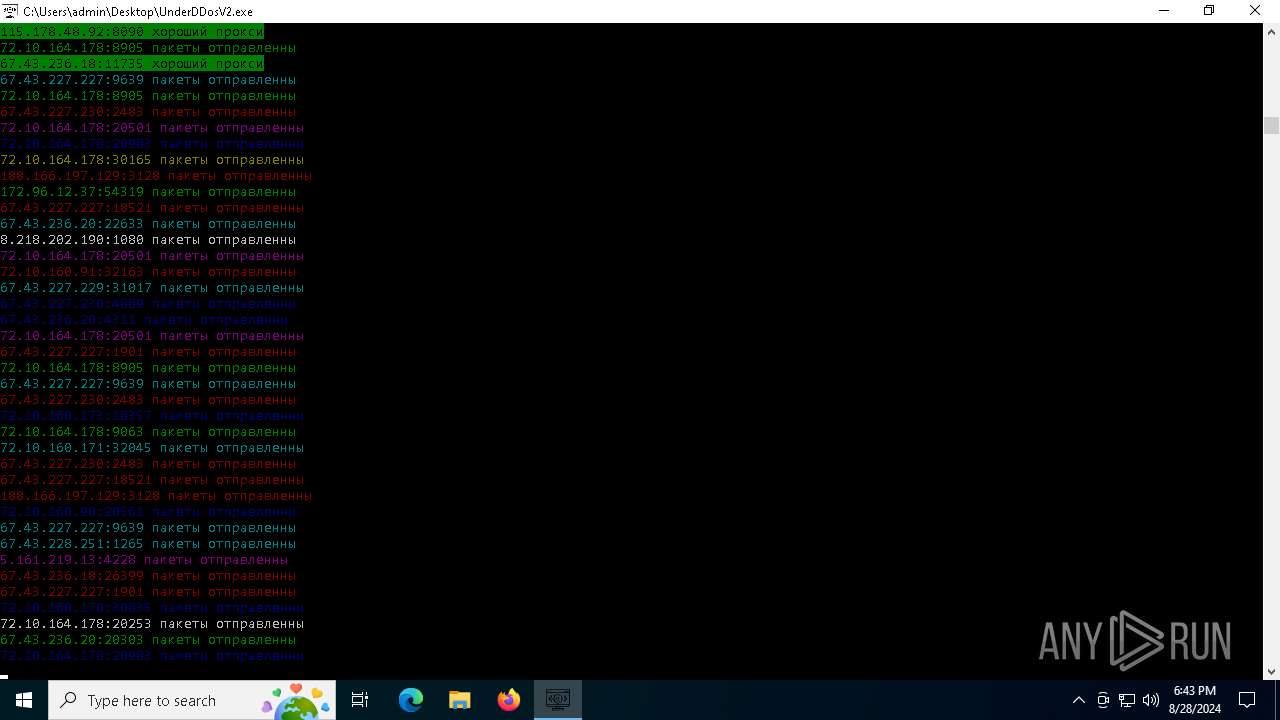
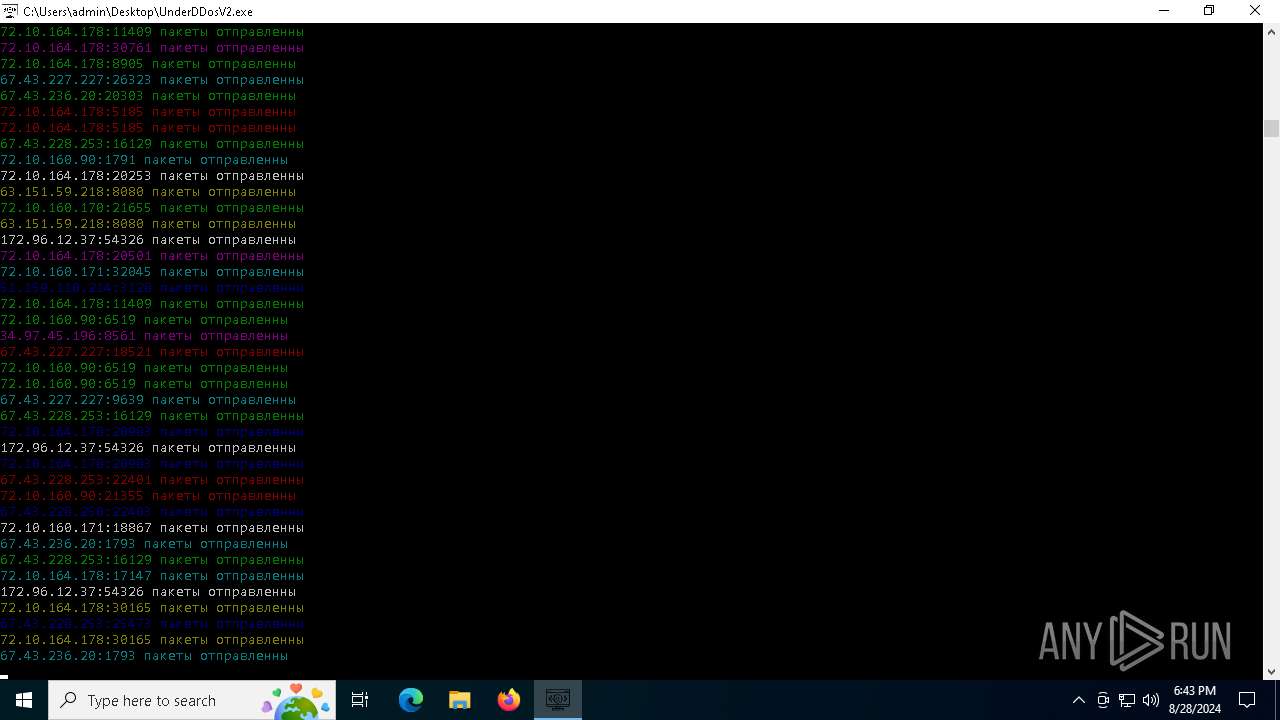
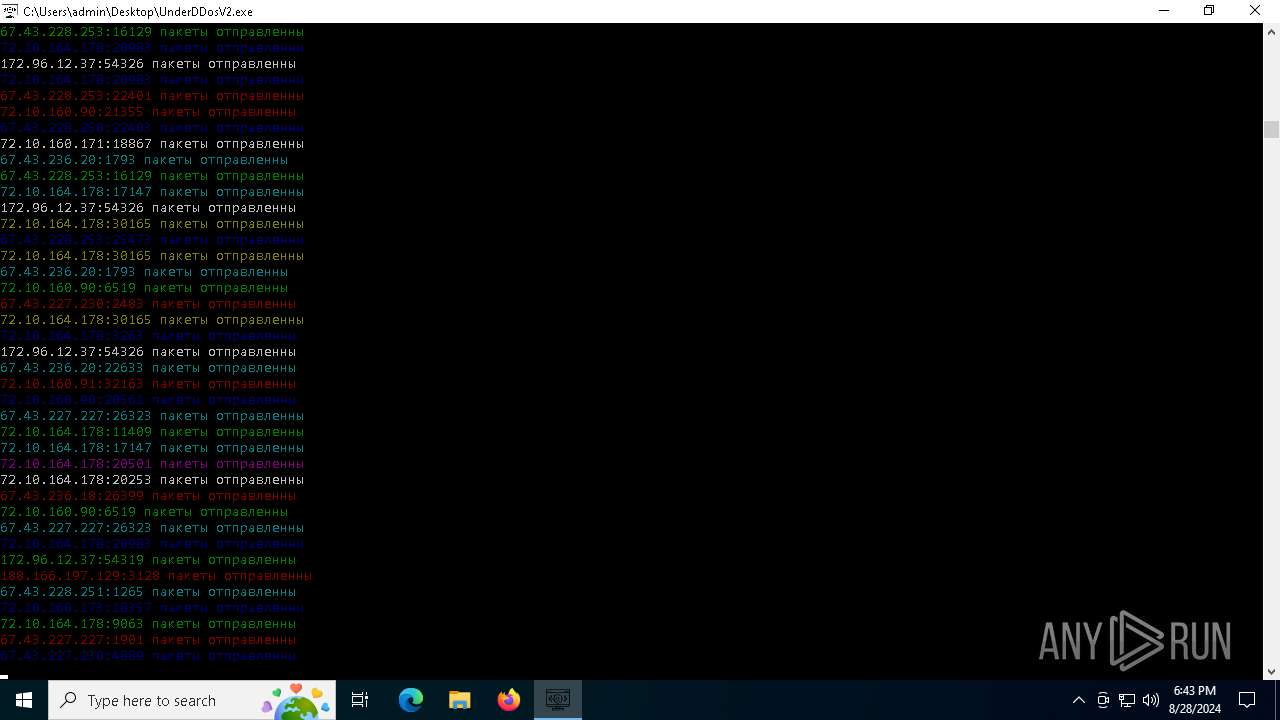
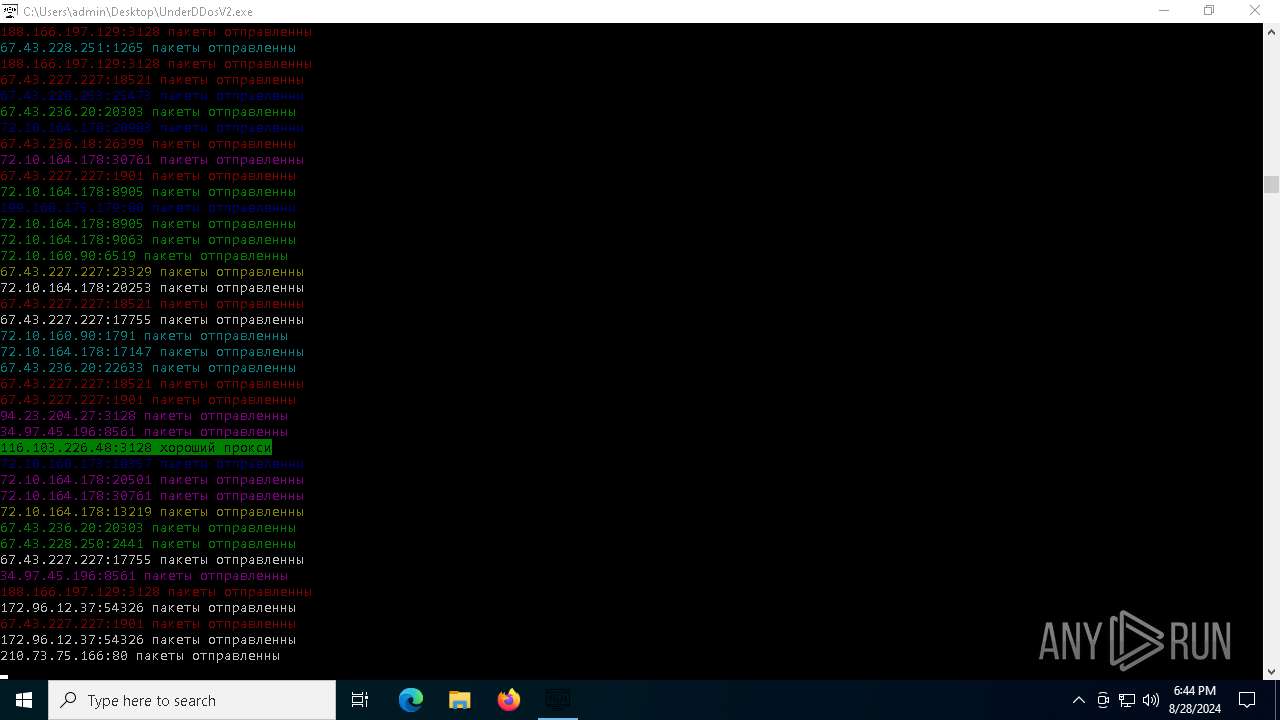
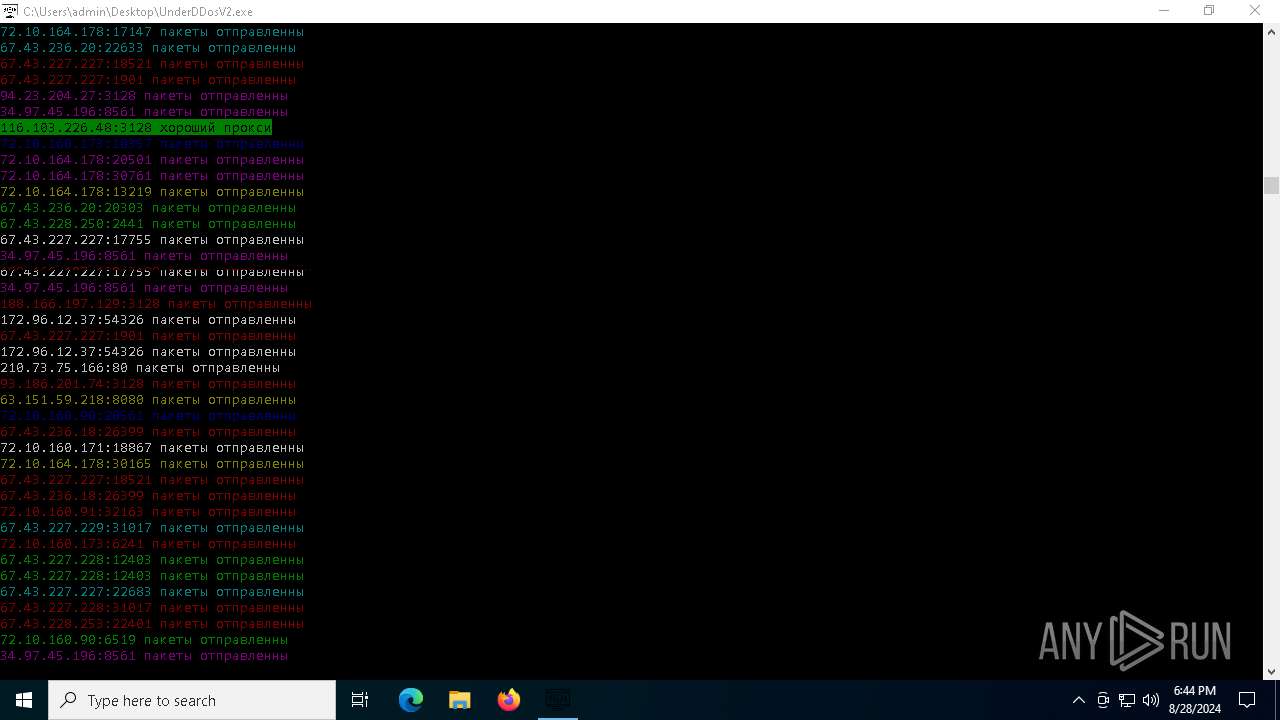
Checks for external IP
- svchost.exe (PID: 2256)
- UnderDDosV2.exe (PID: 6684)
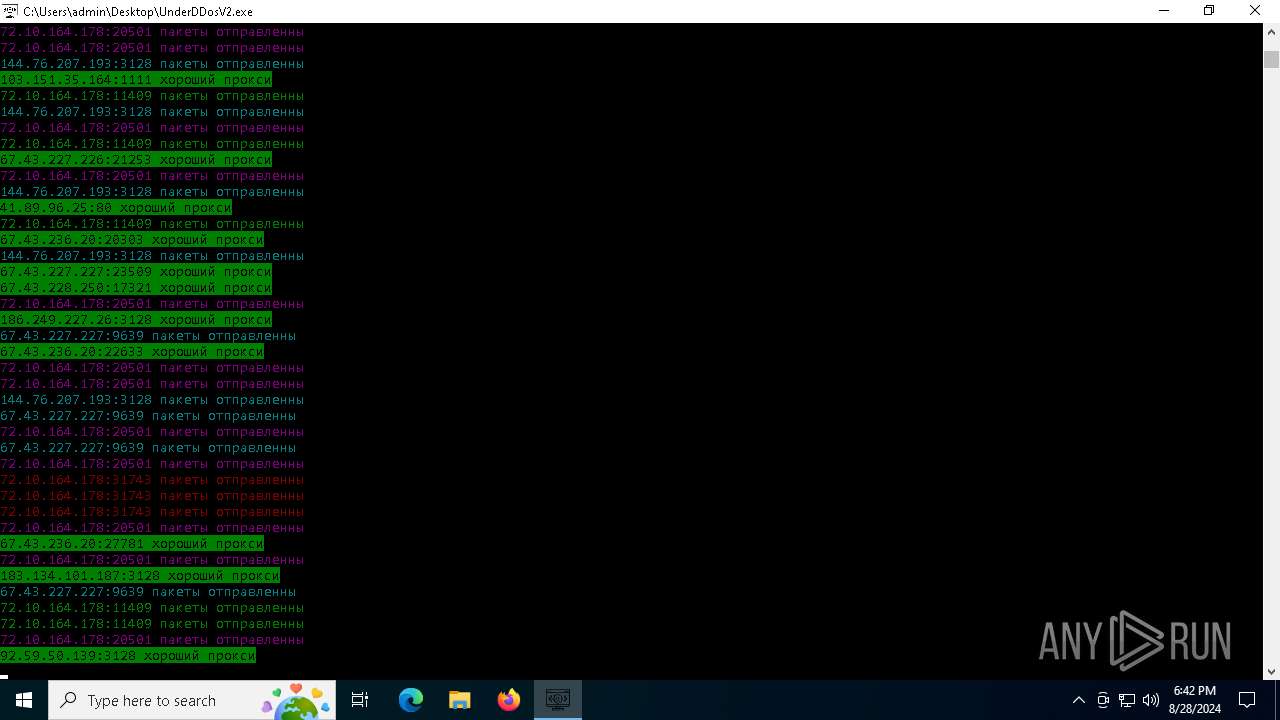
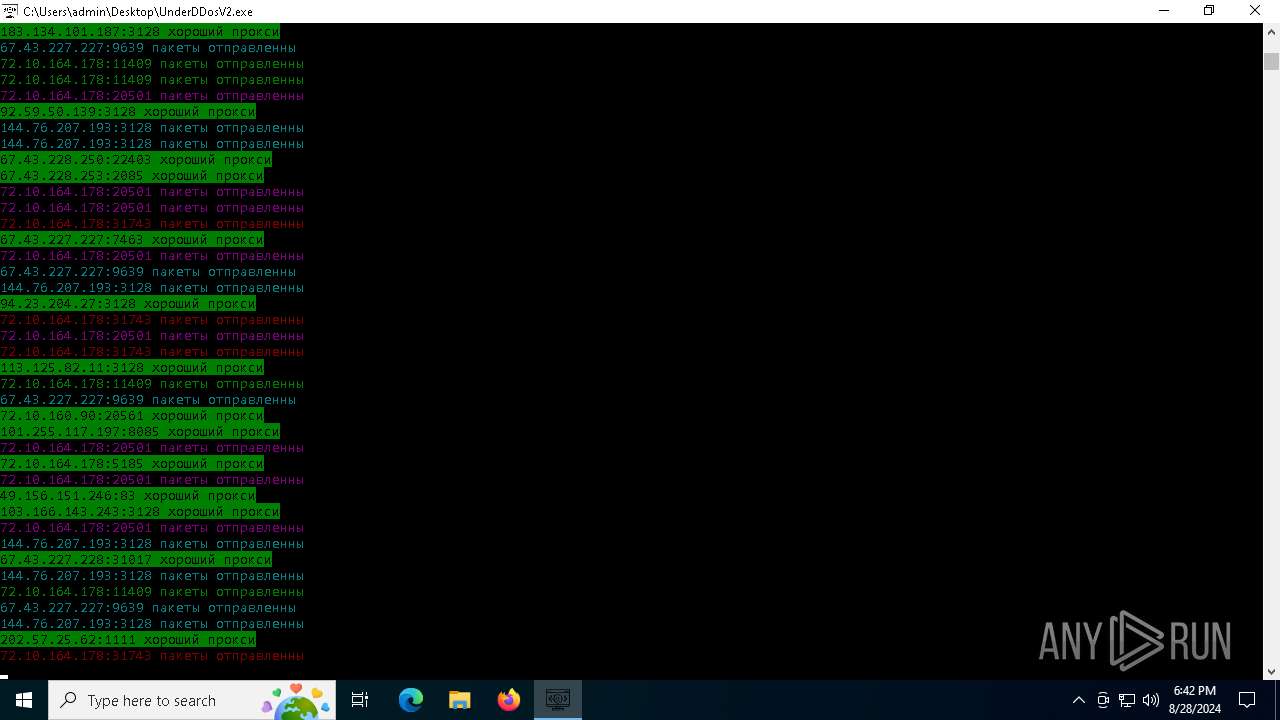
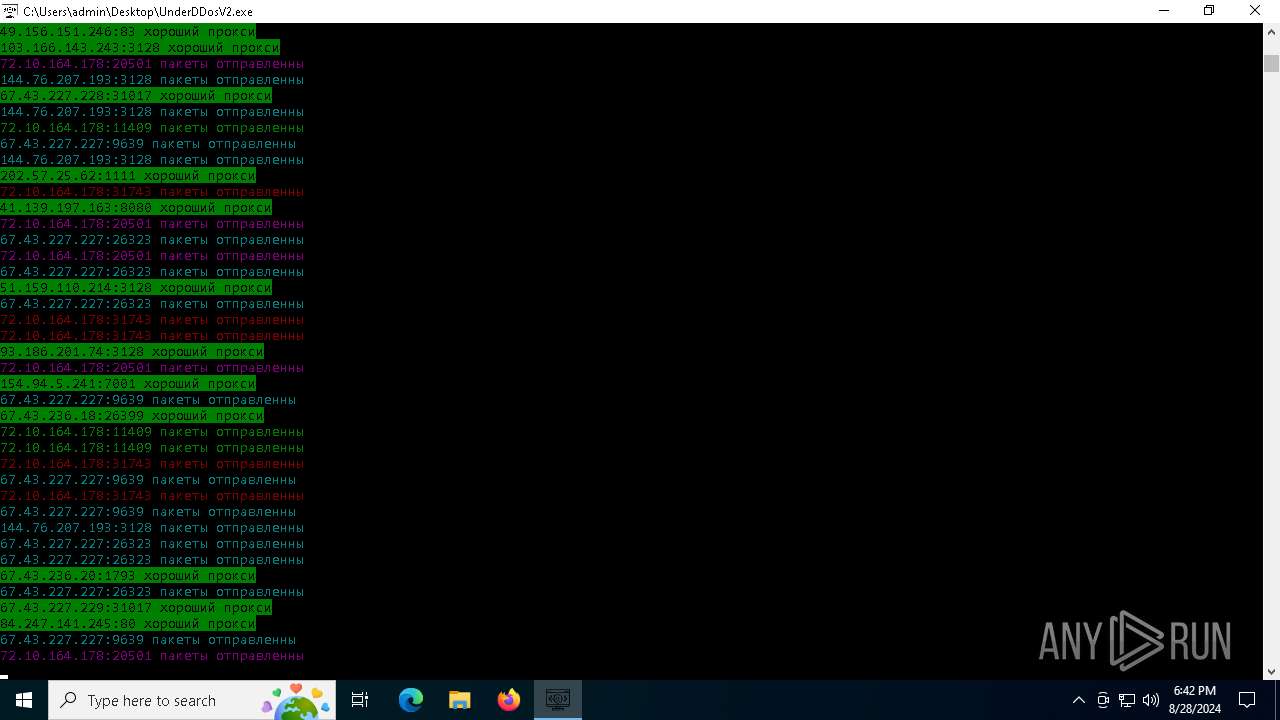
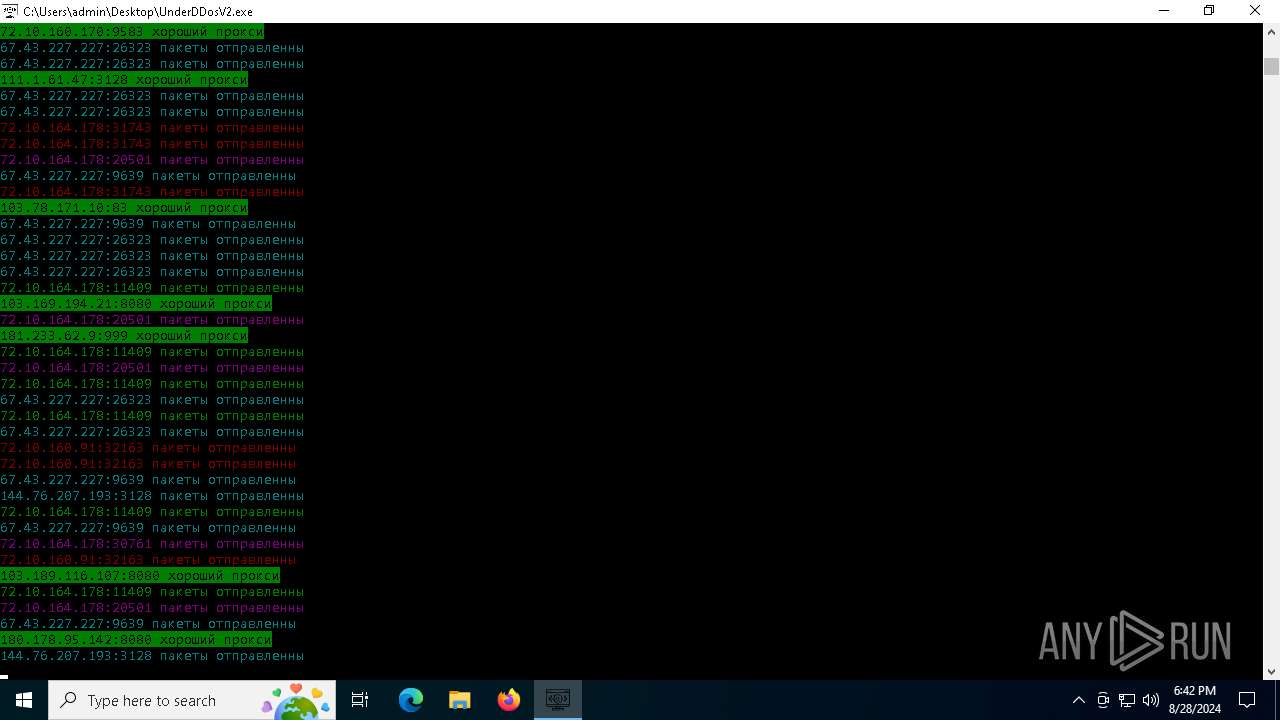
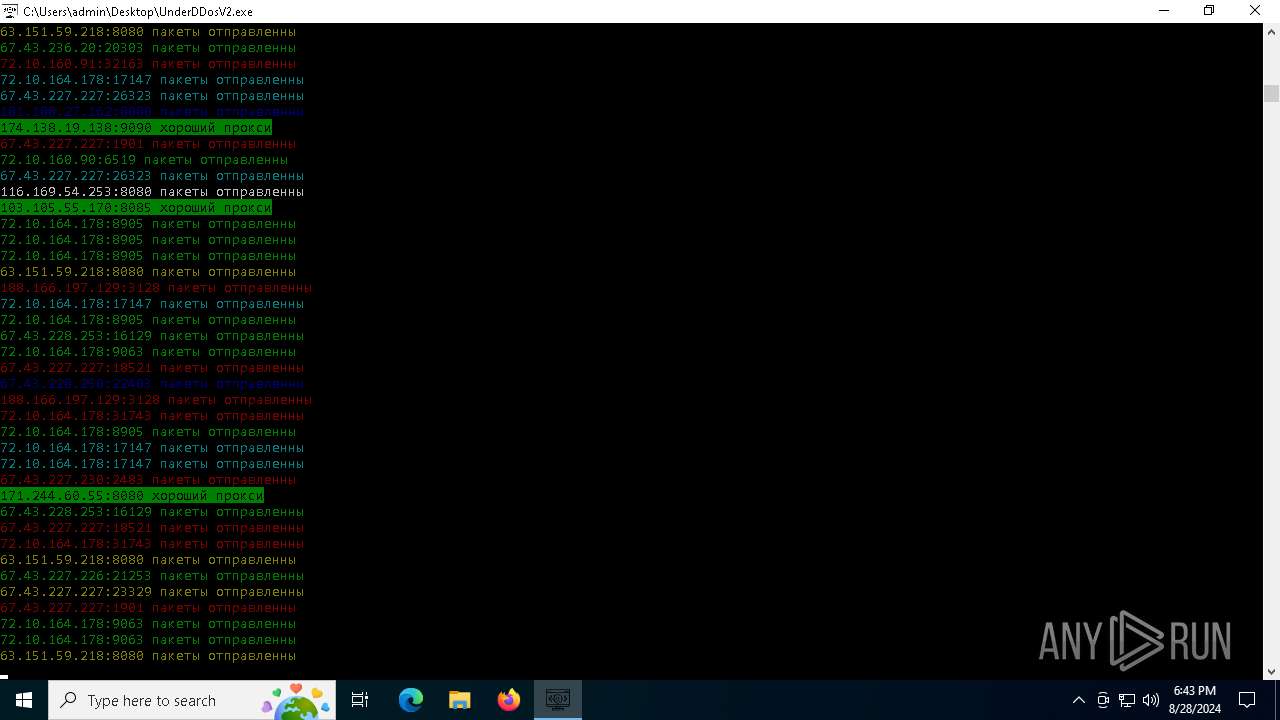
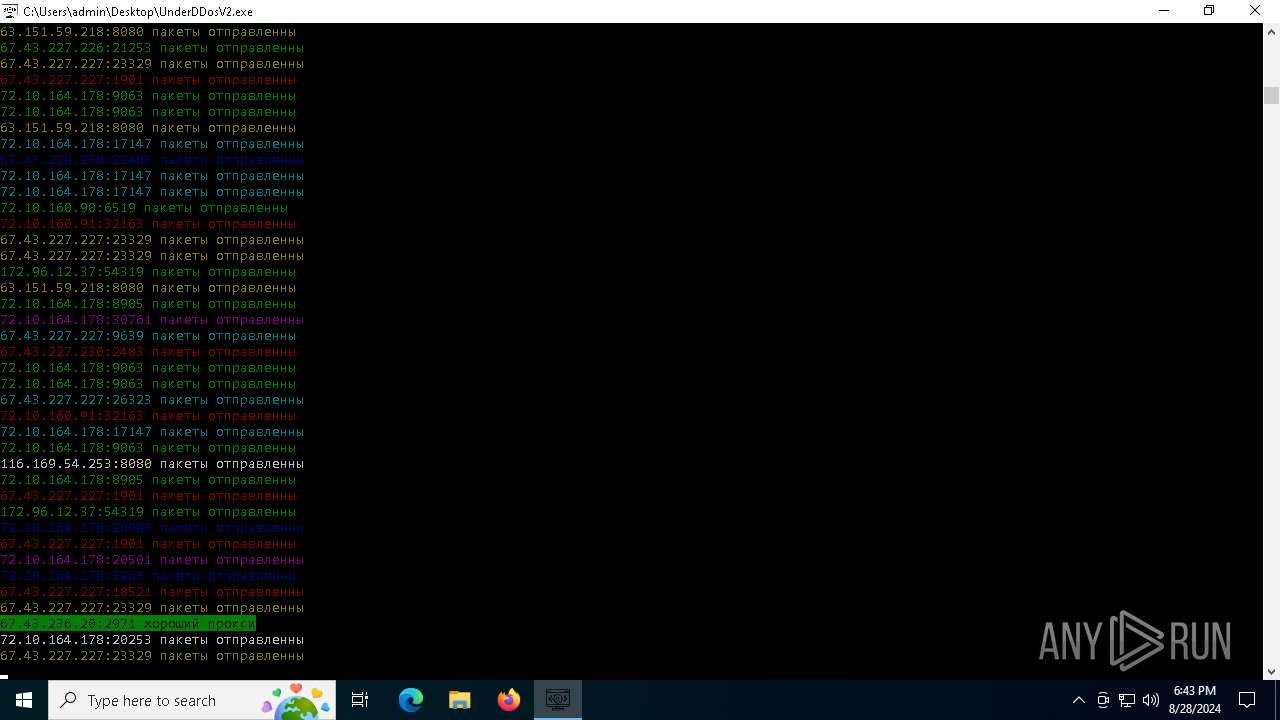
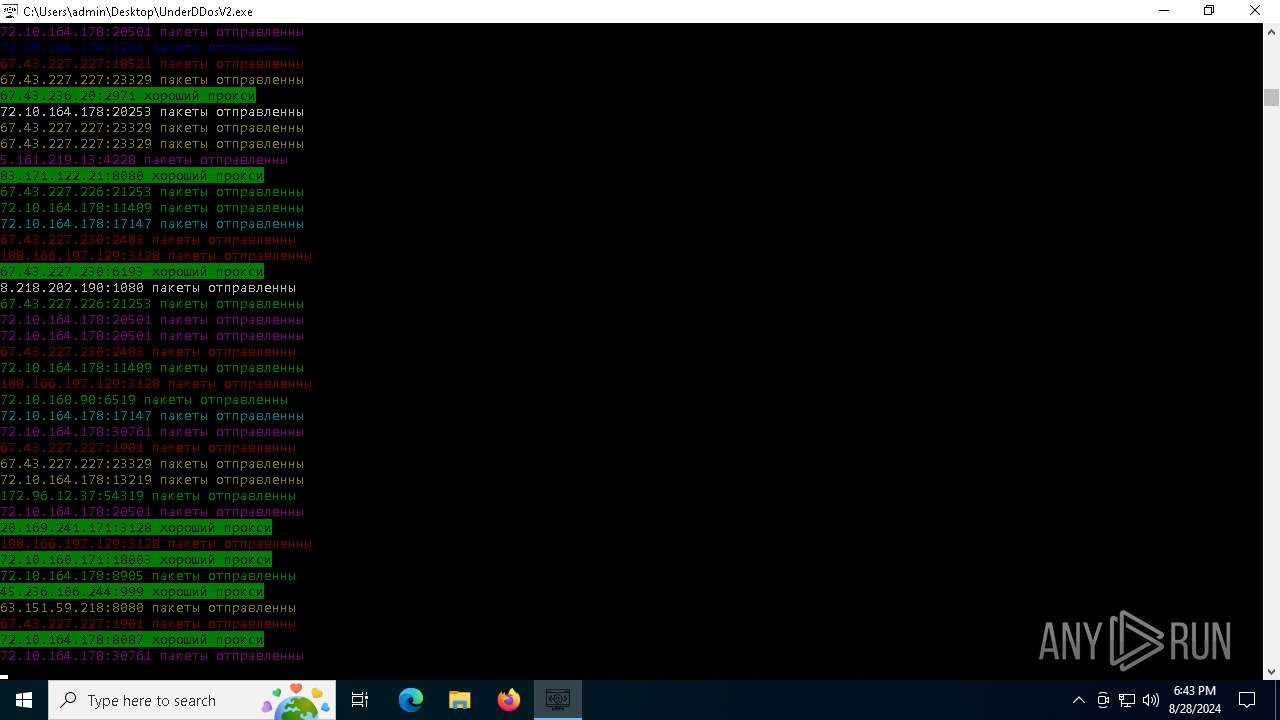
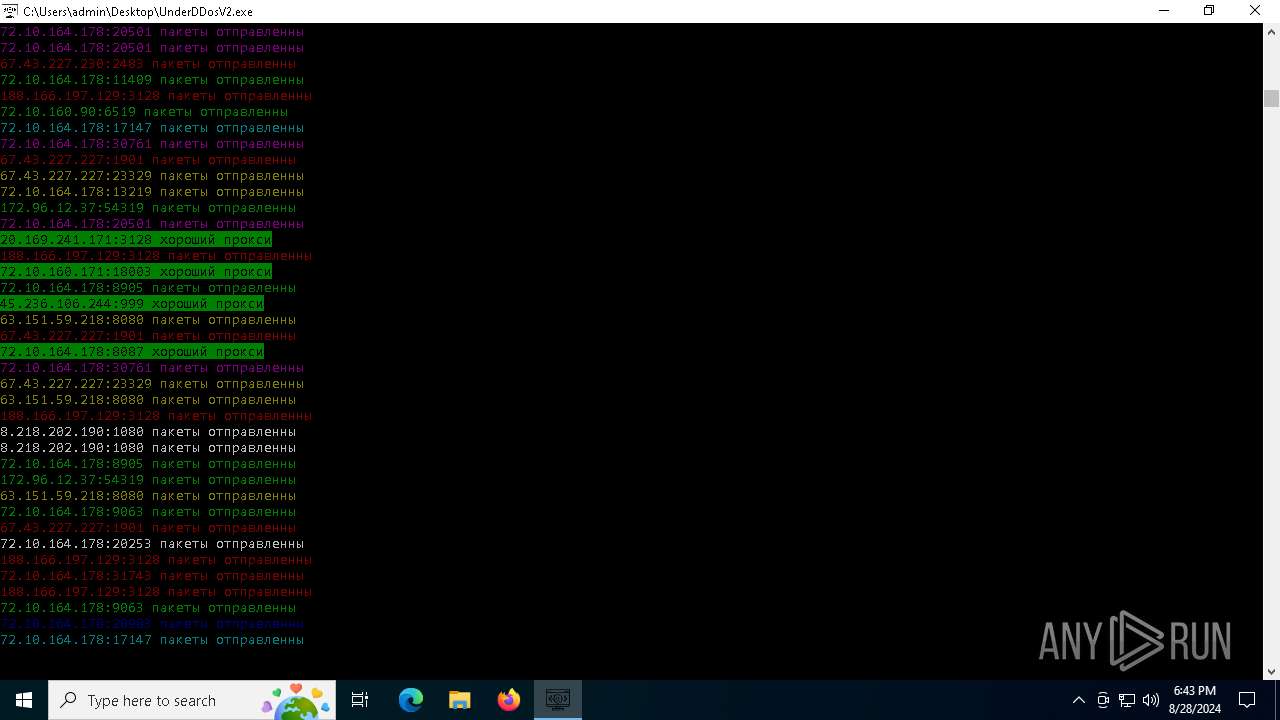
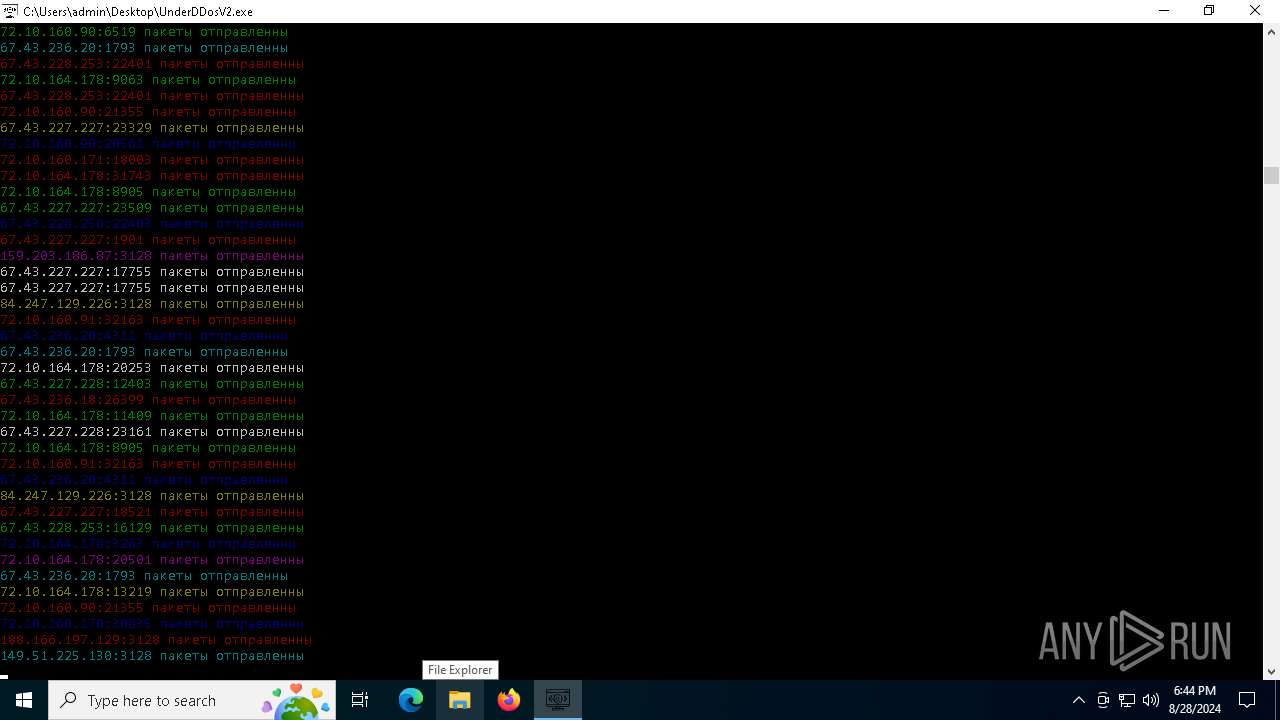
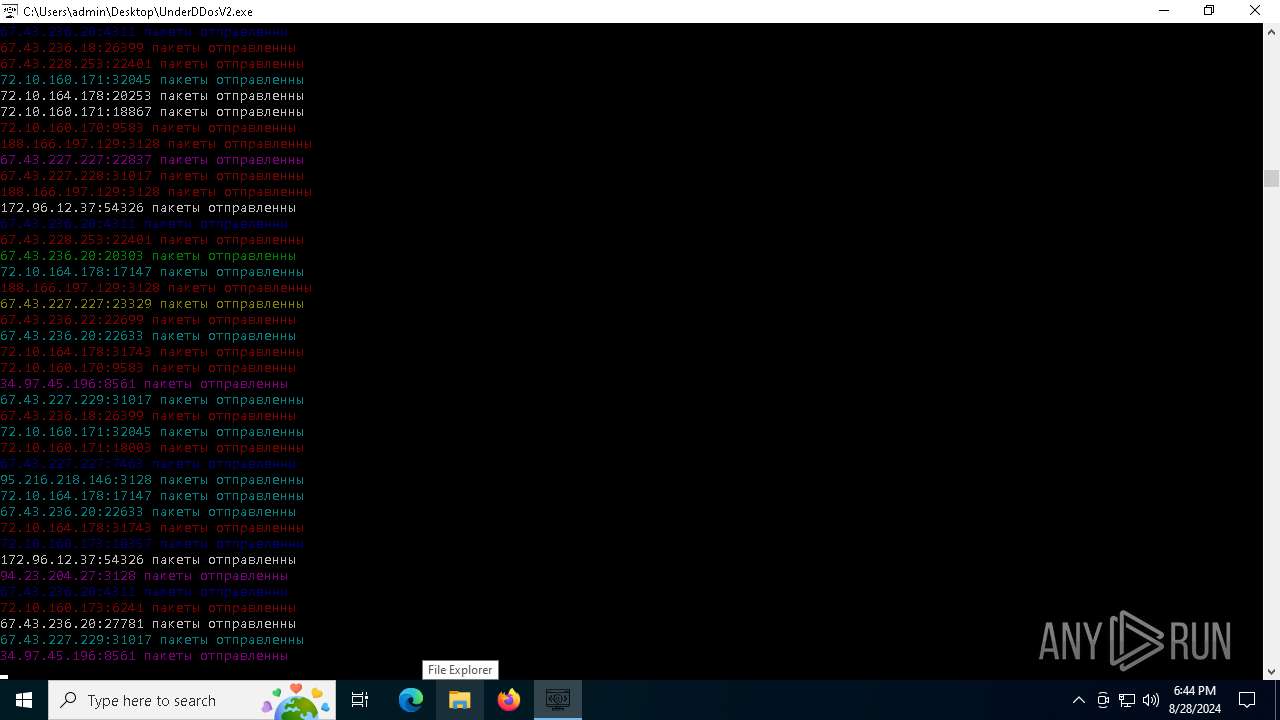
Connects to FTP
- UnderDDosV2.exe (PID: 6684)
Starts CMD.EXE for commands execution
- UnderDDosV2.exe (PID: 6684)
Potential Corporate Privacy Violation
- UnderDDosV2.exe (PID: 6684)
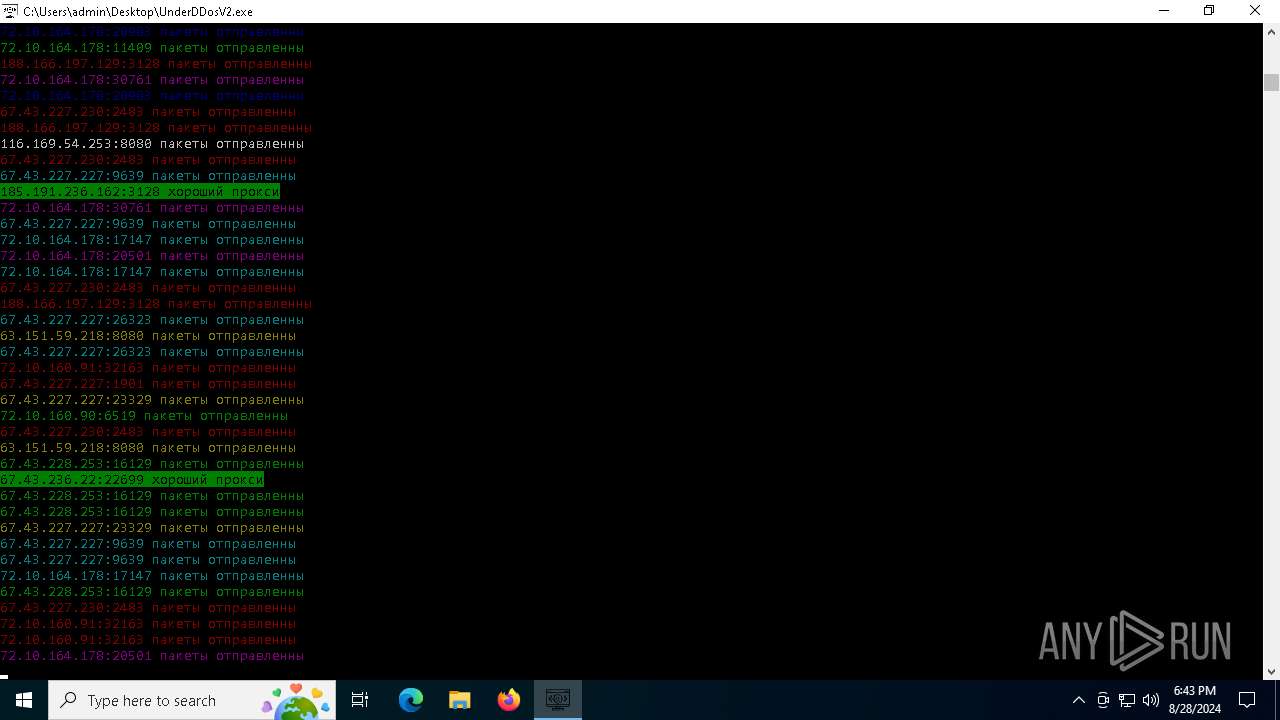
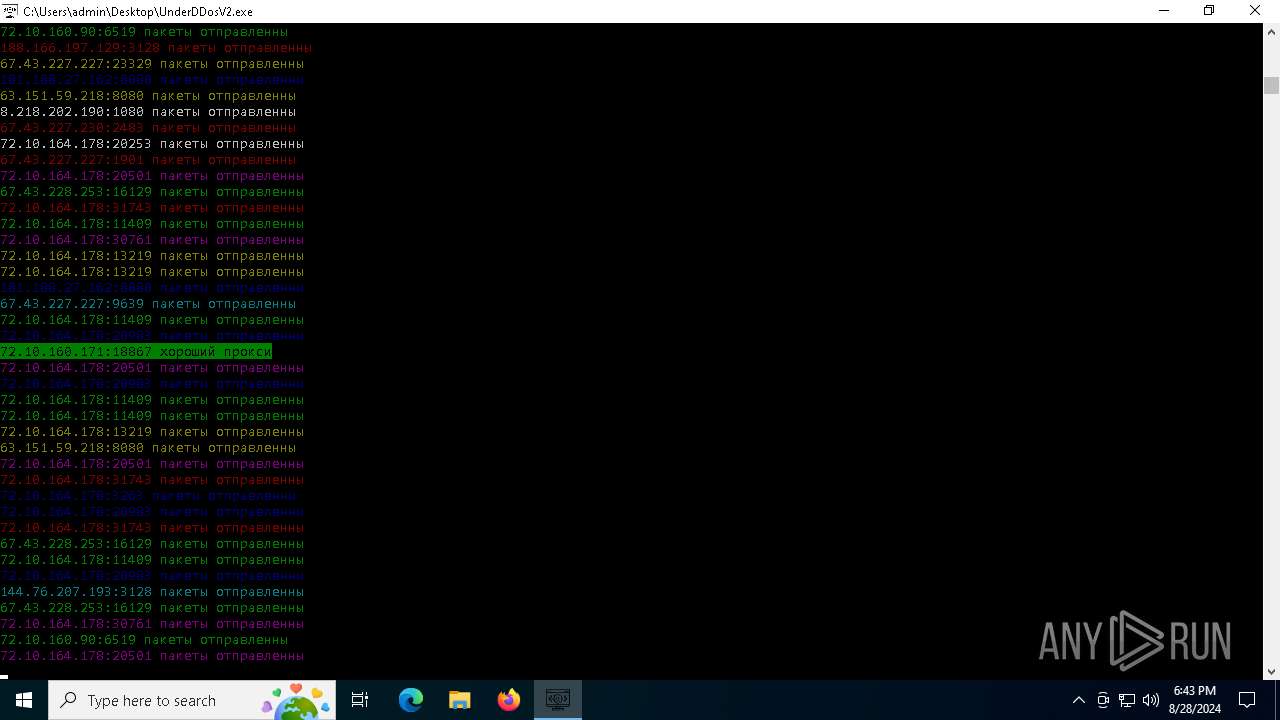
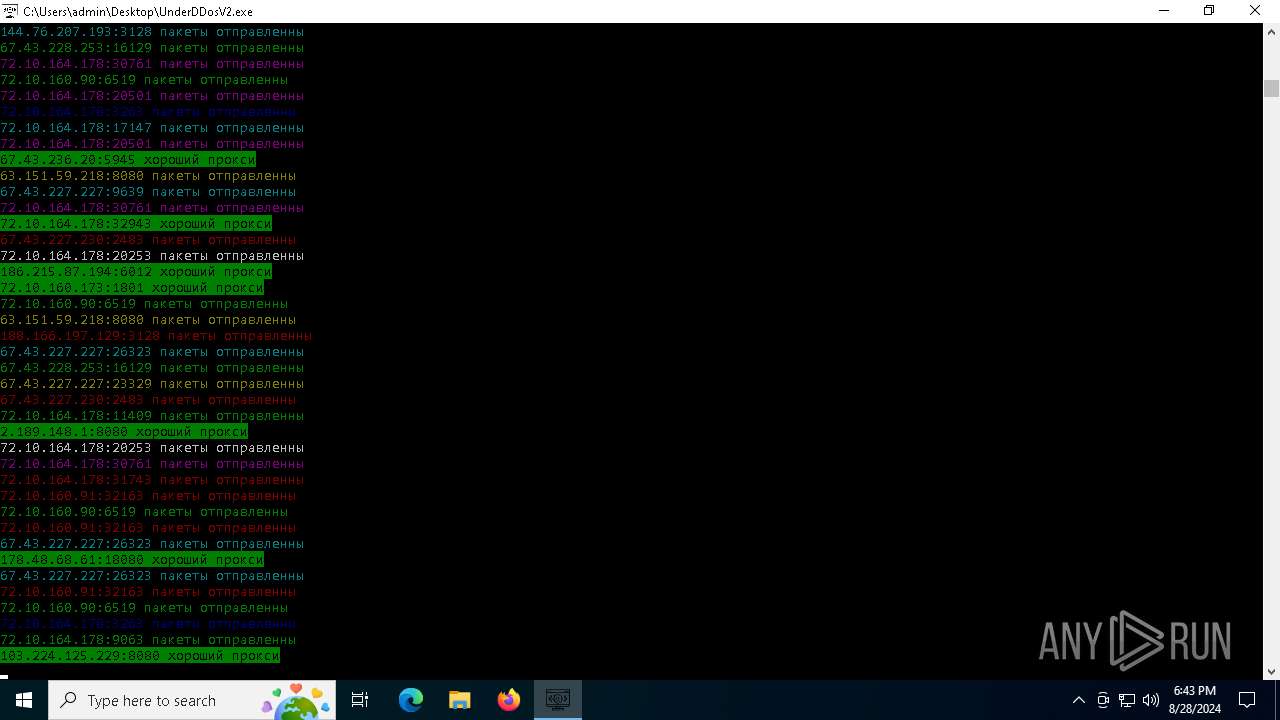
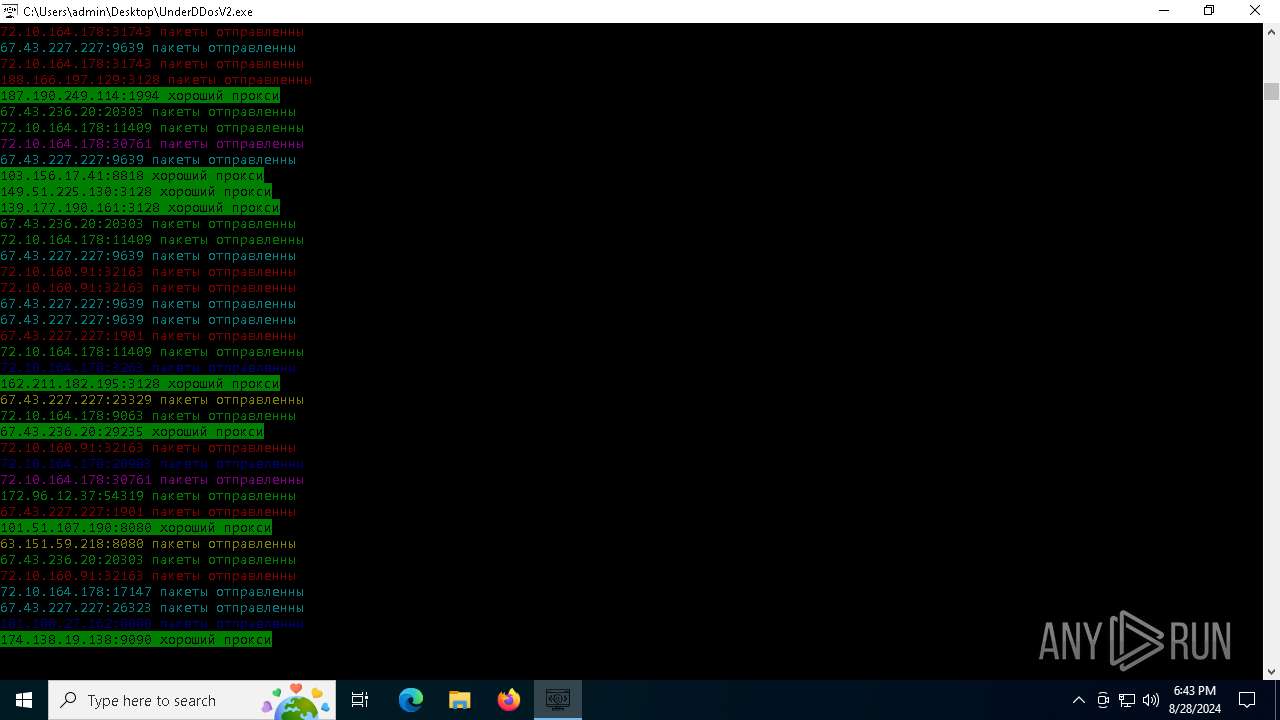
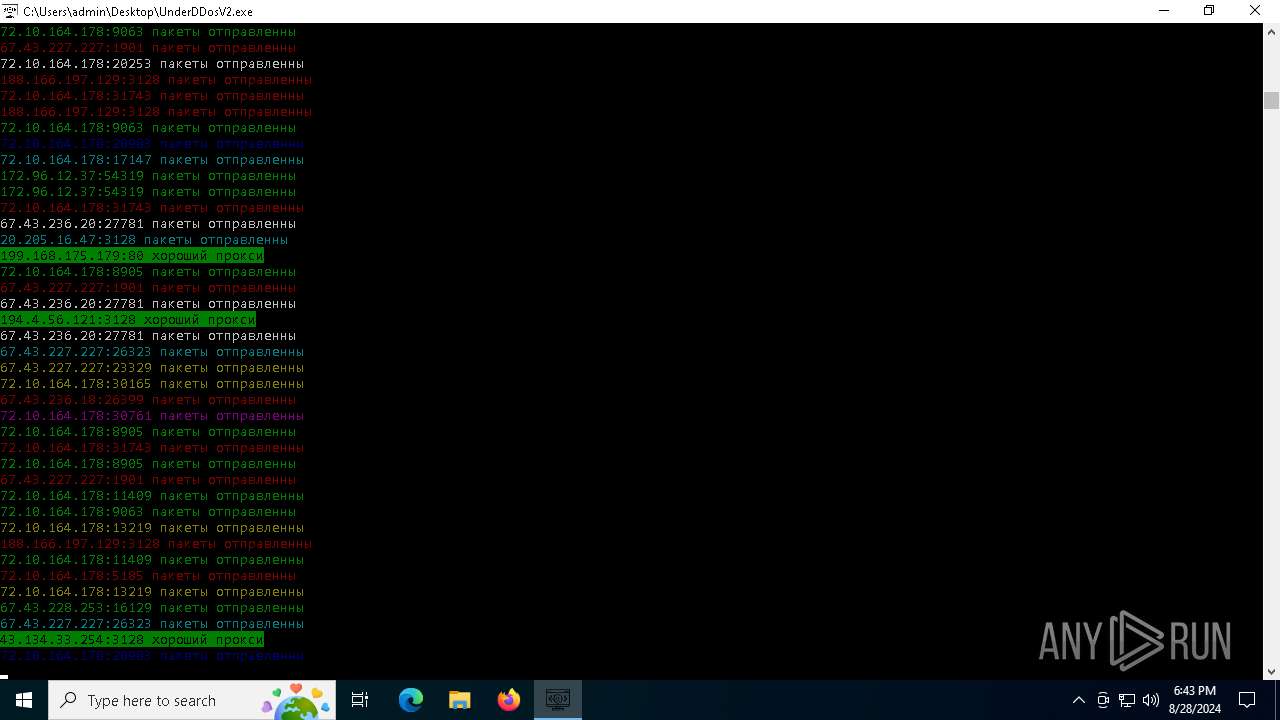
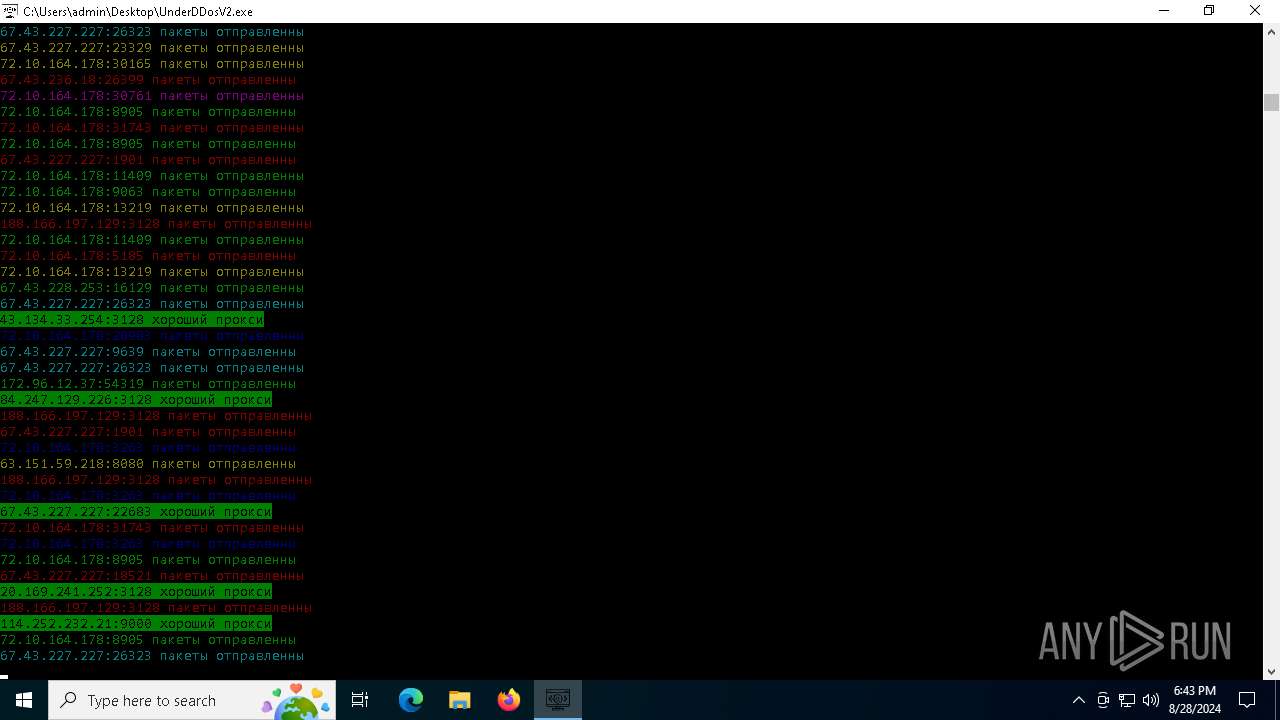
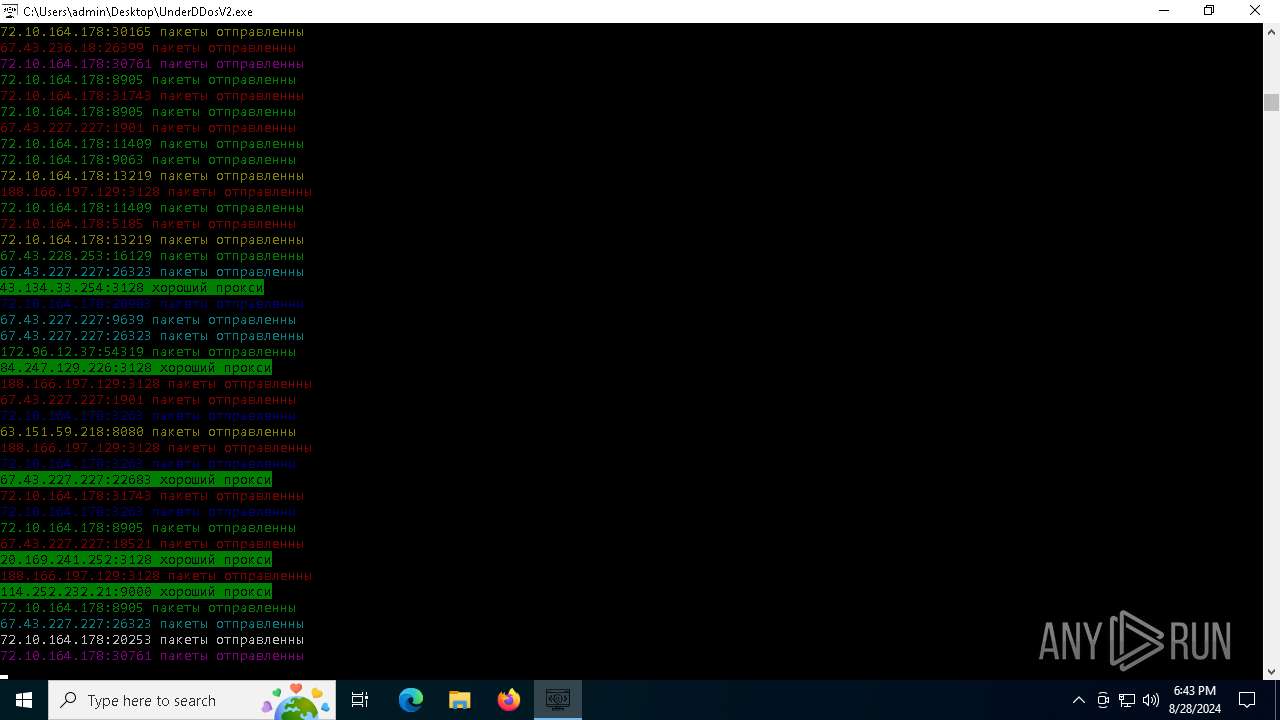
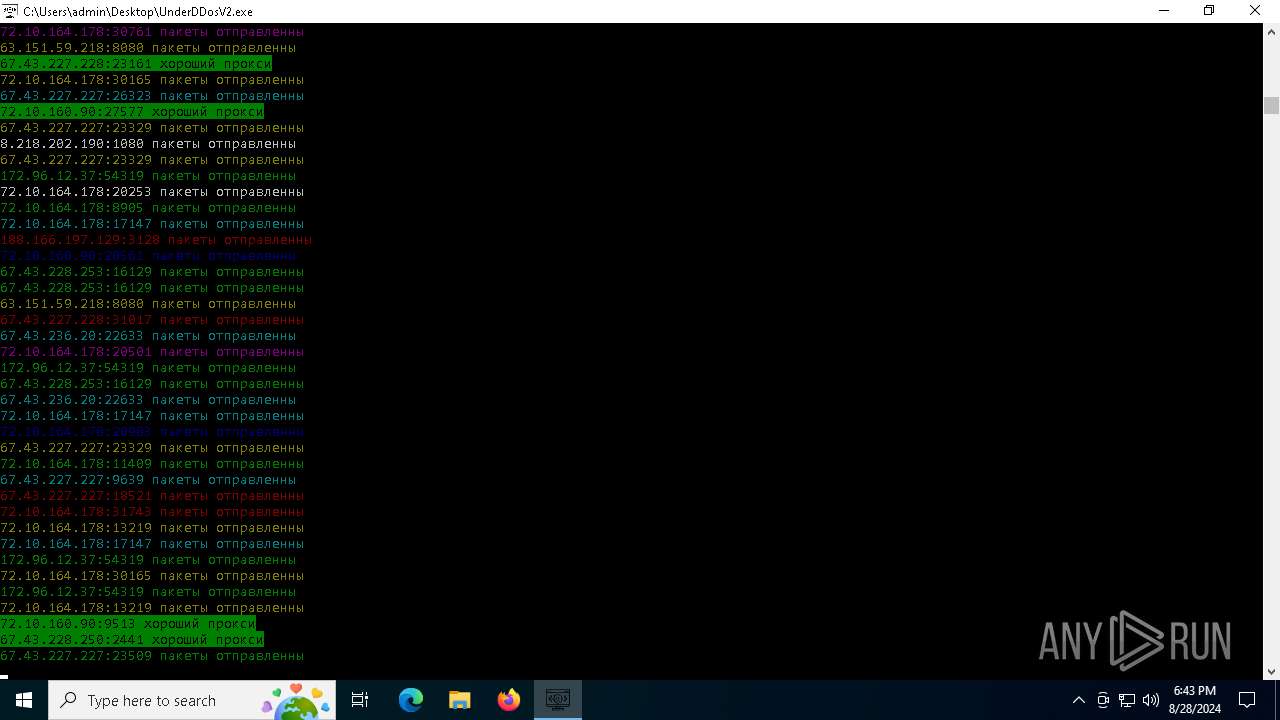
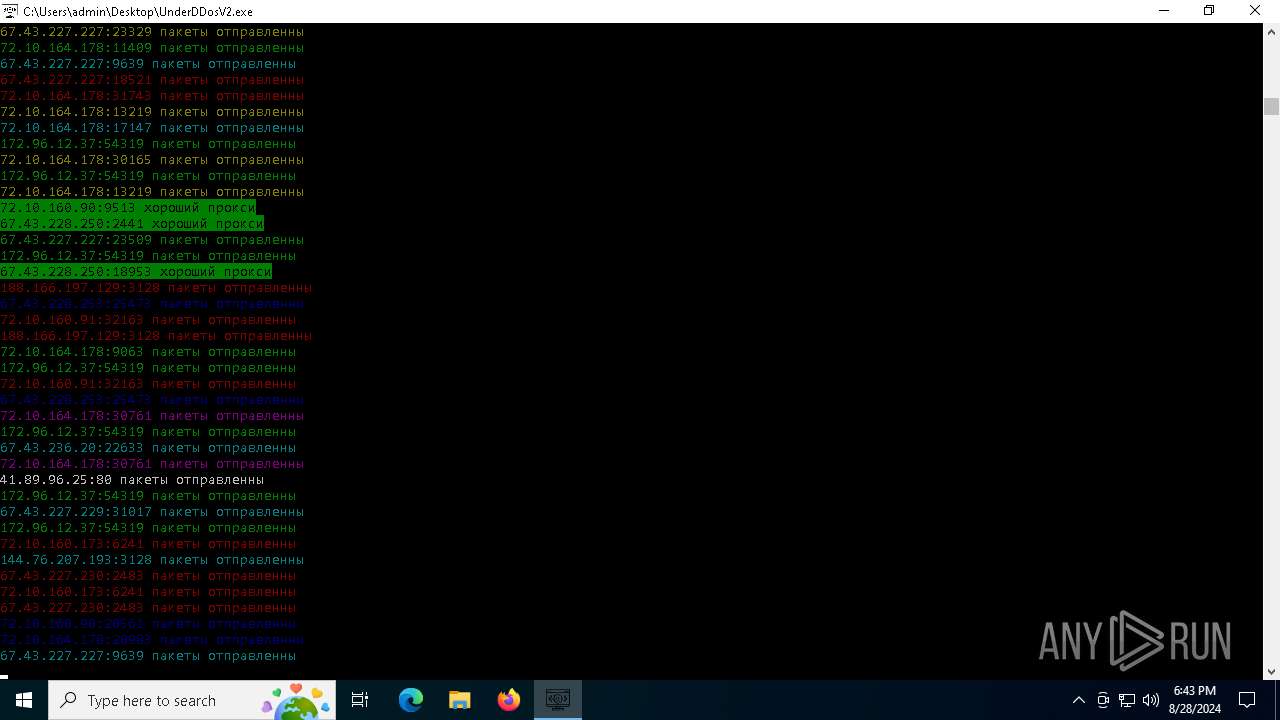
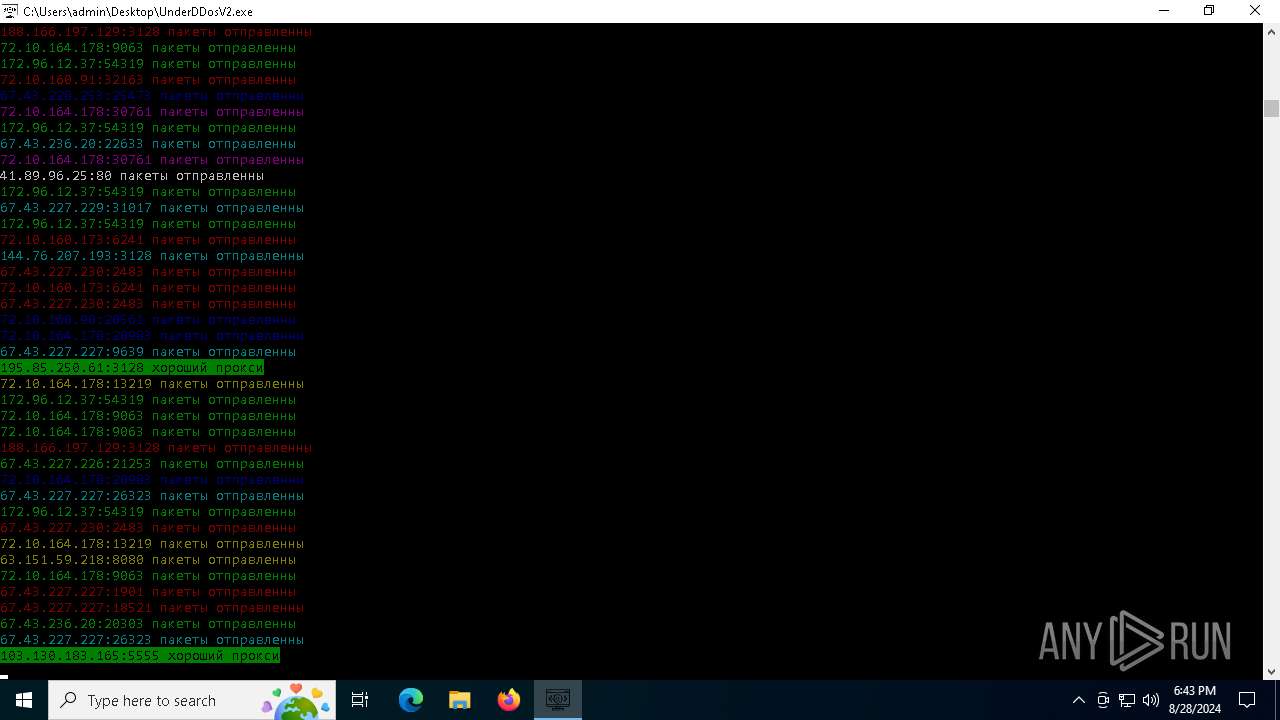
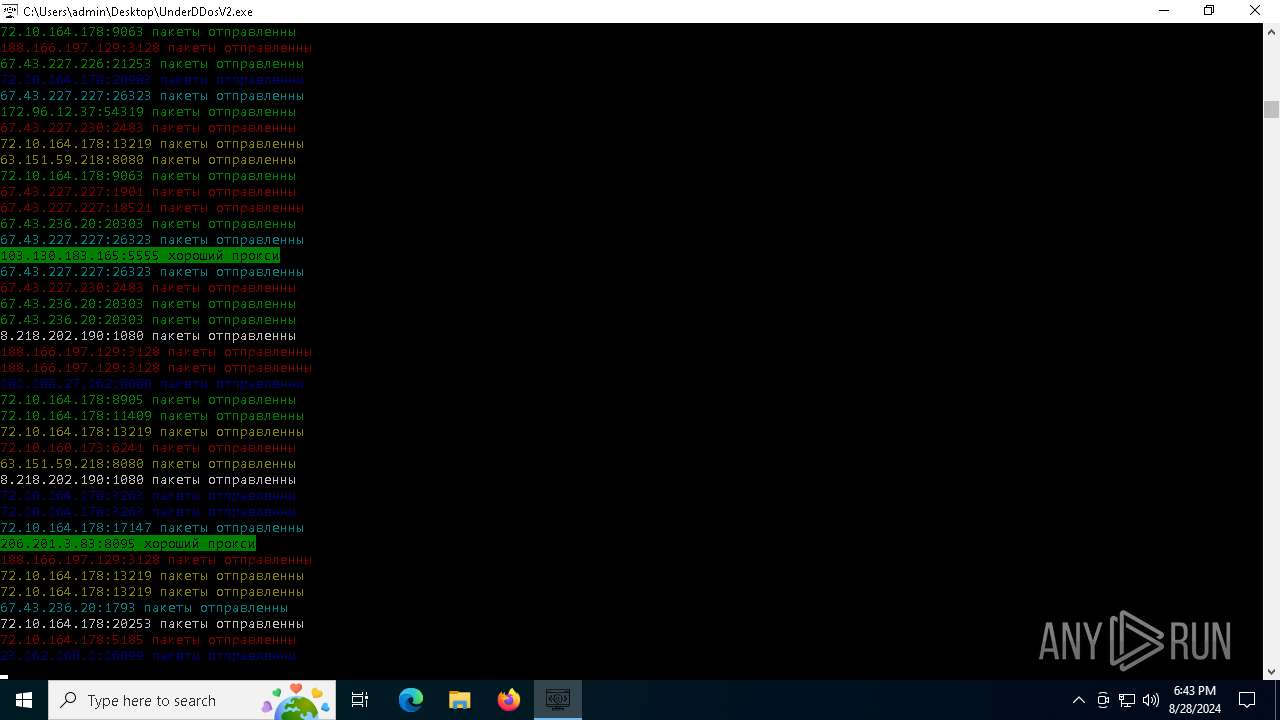
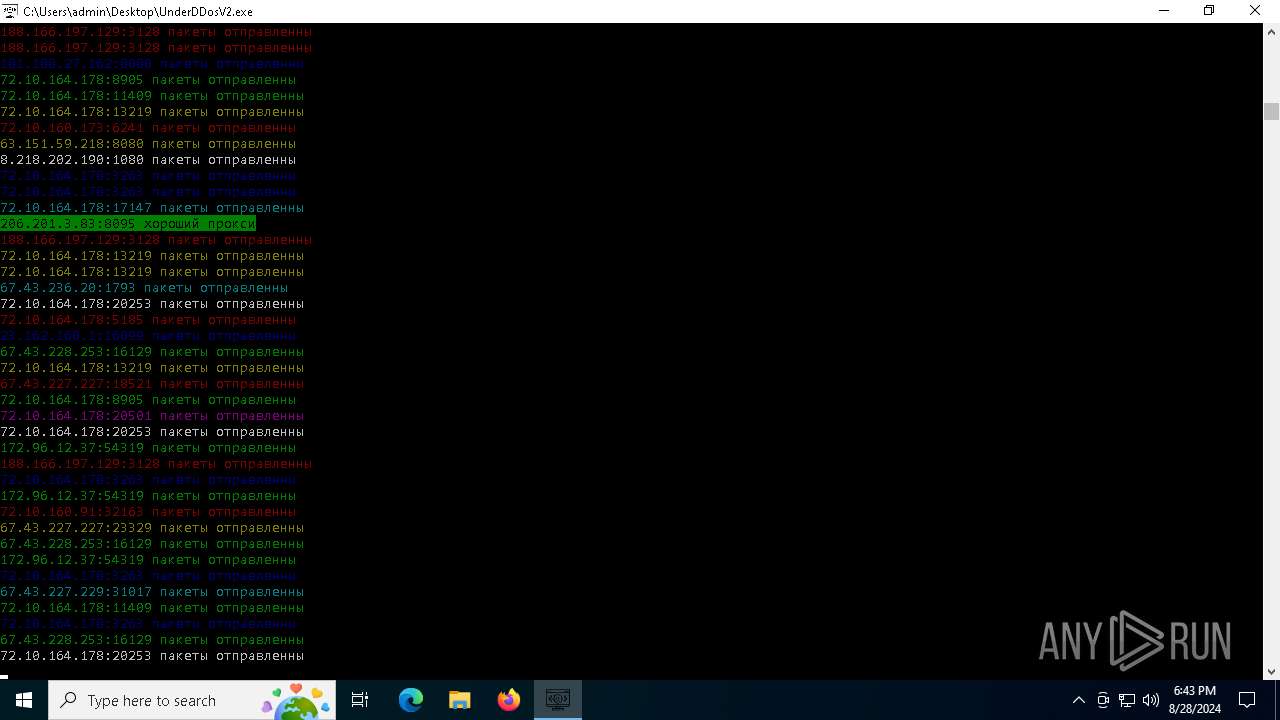
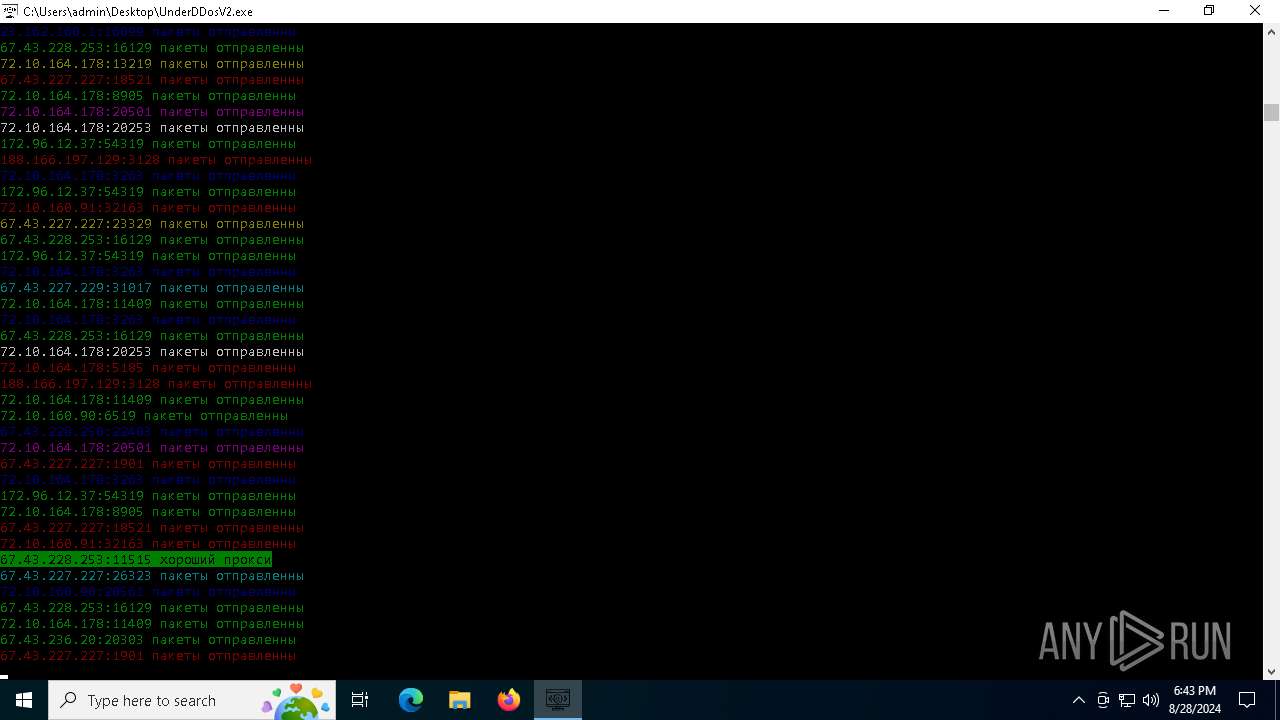
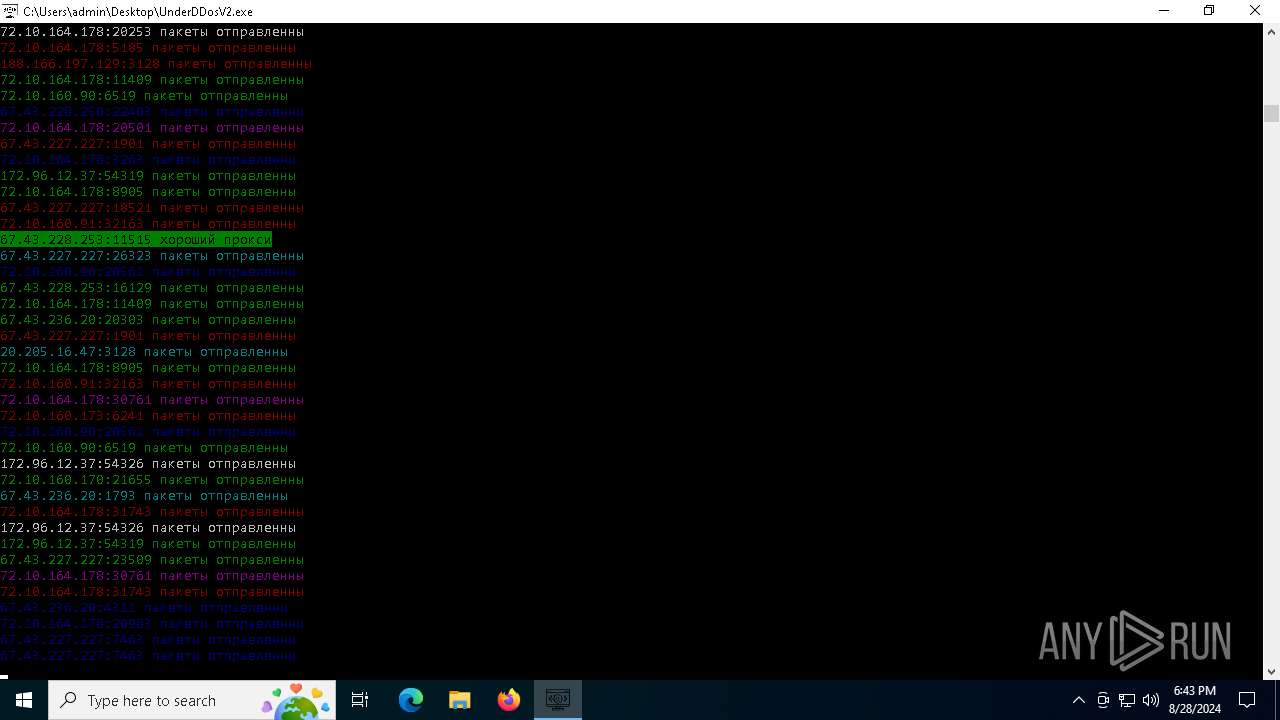
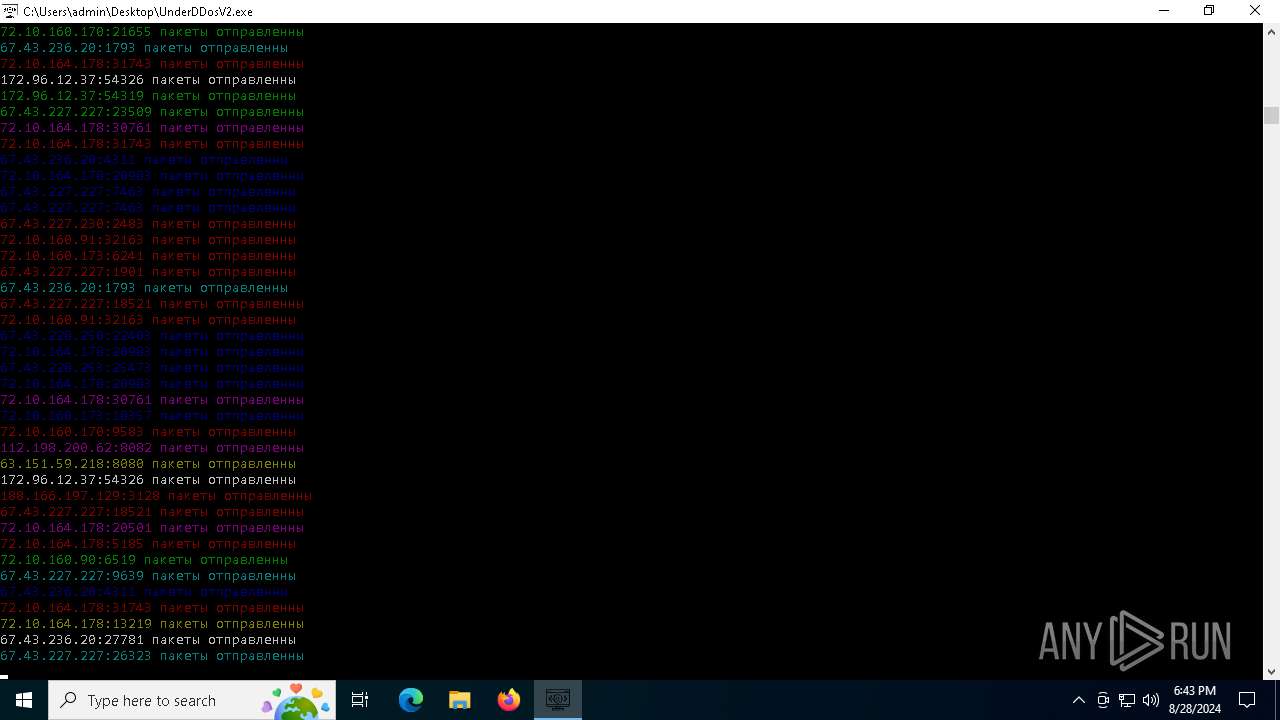
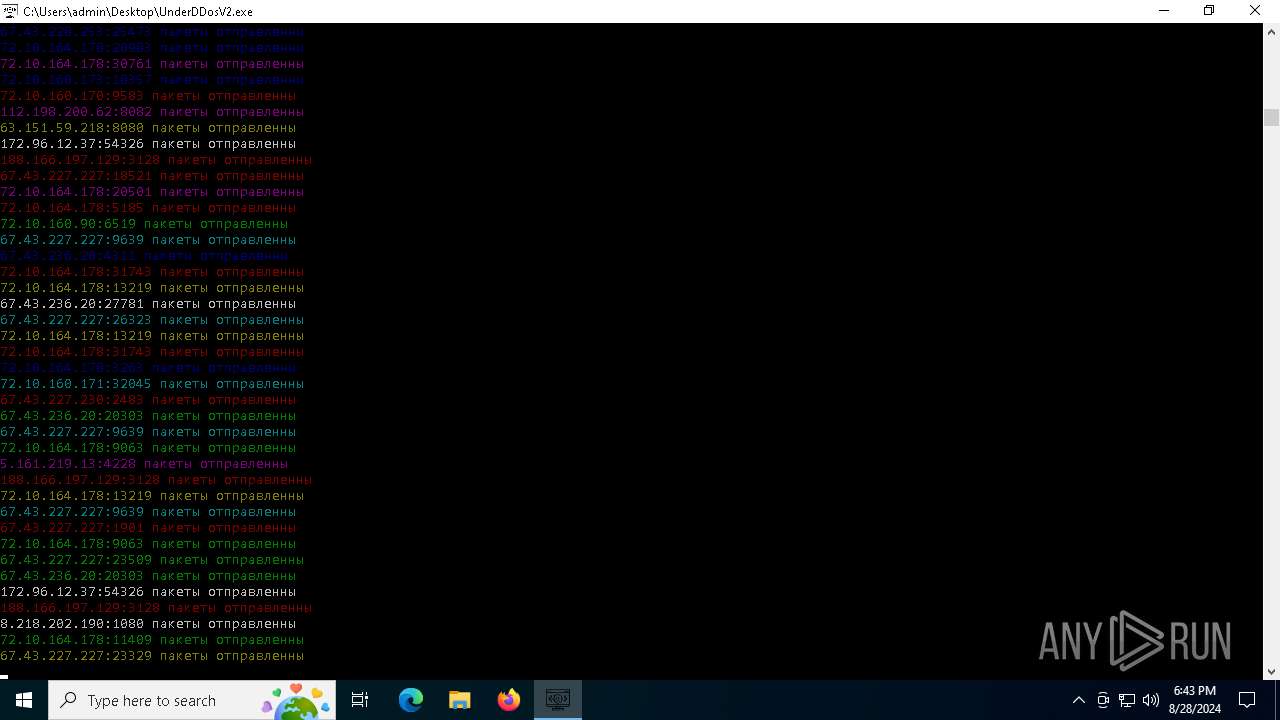
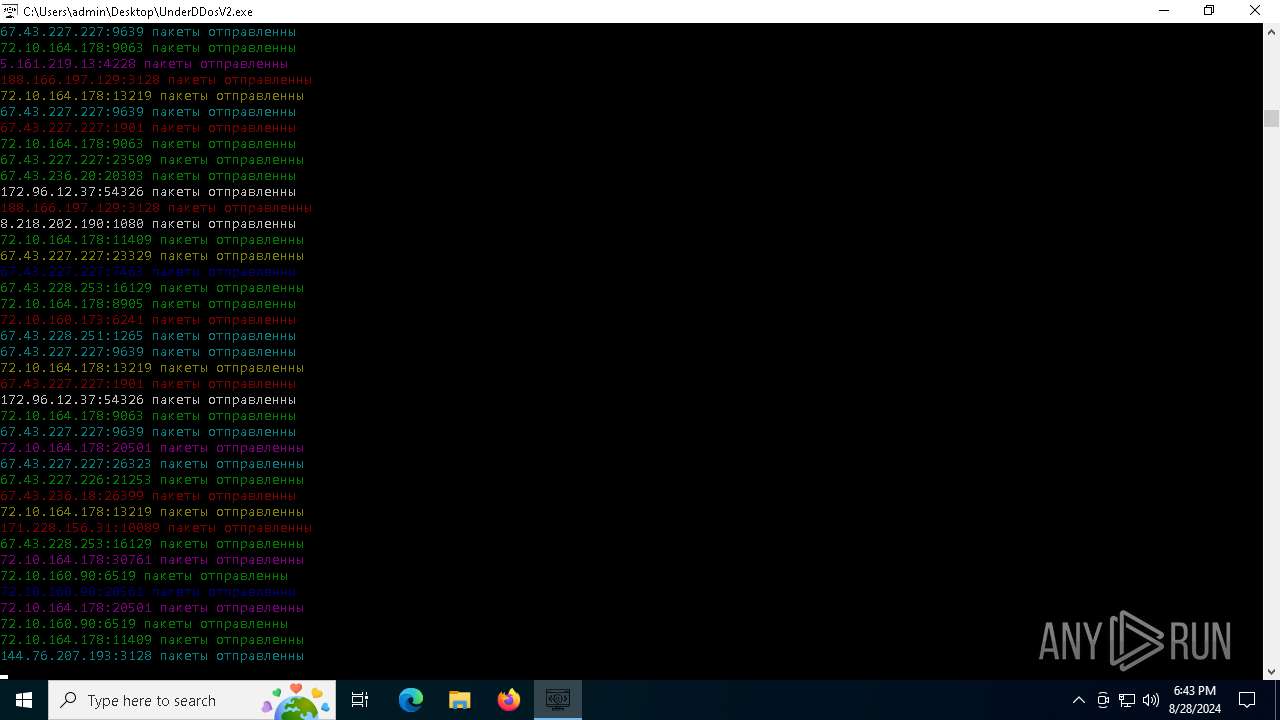
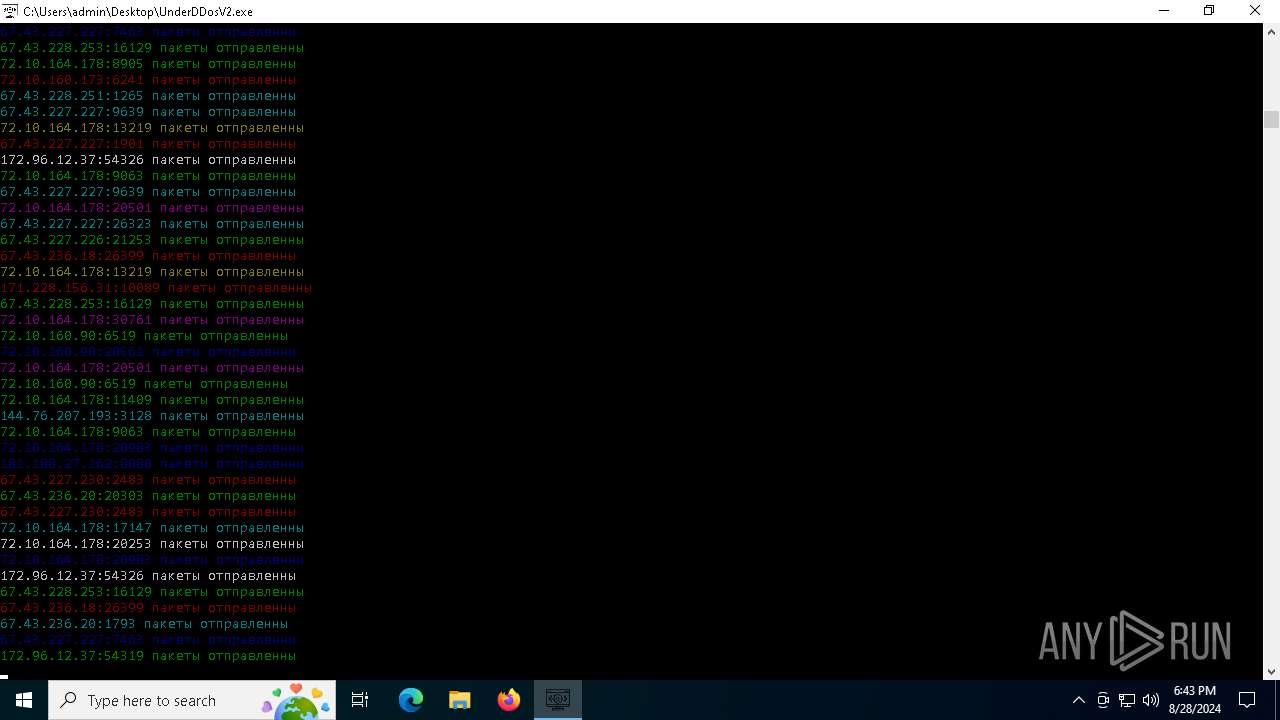
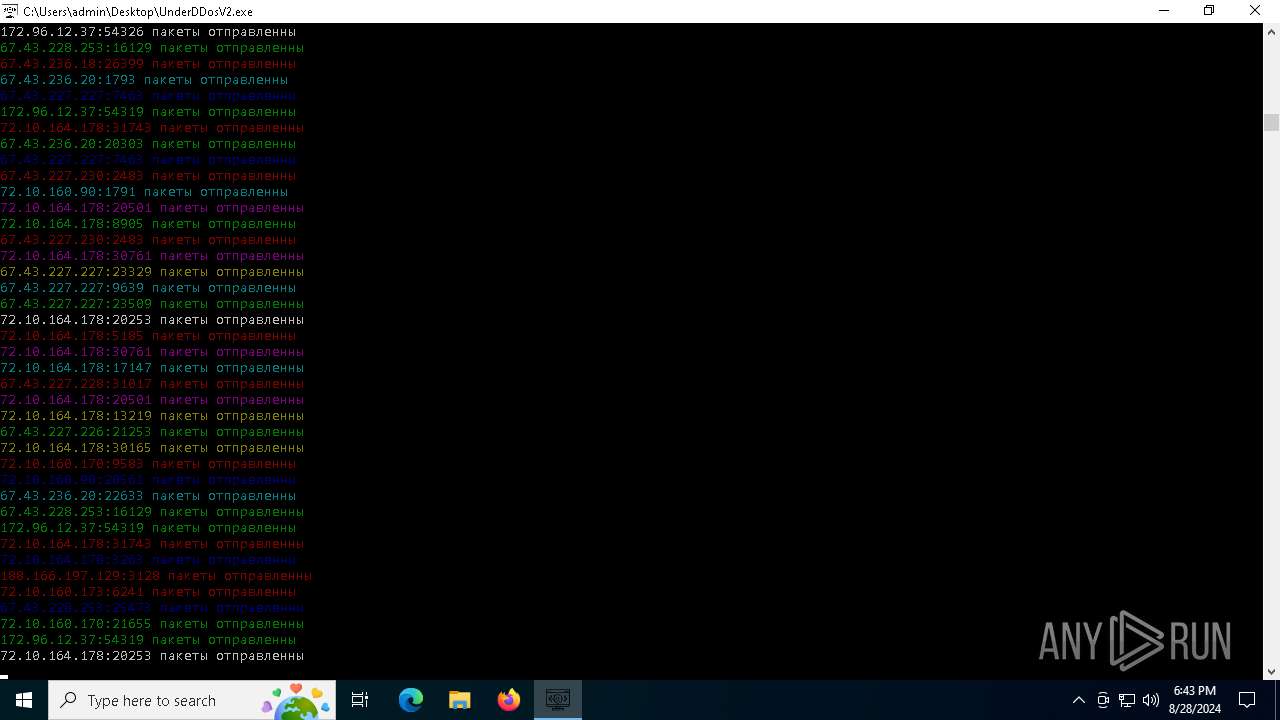
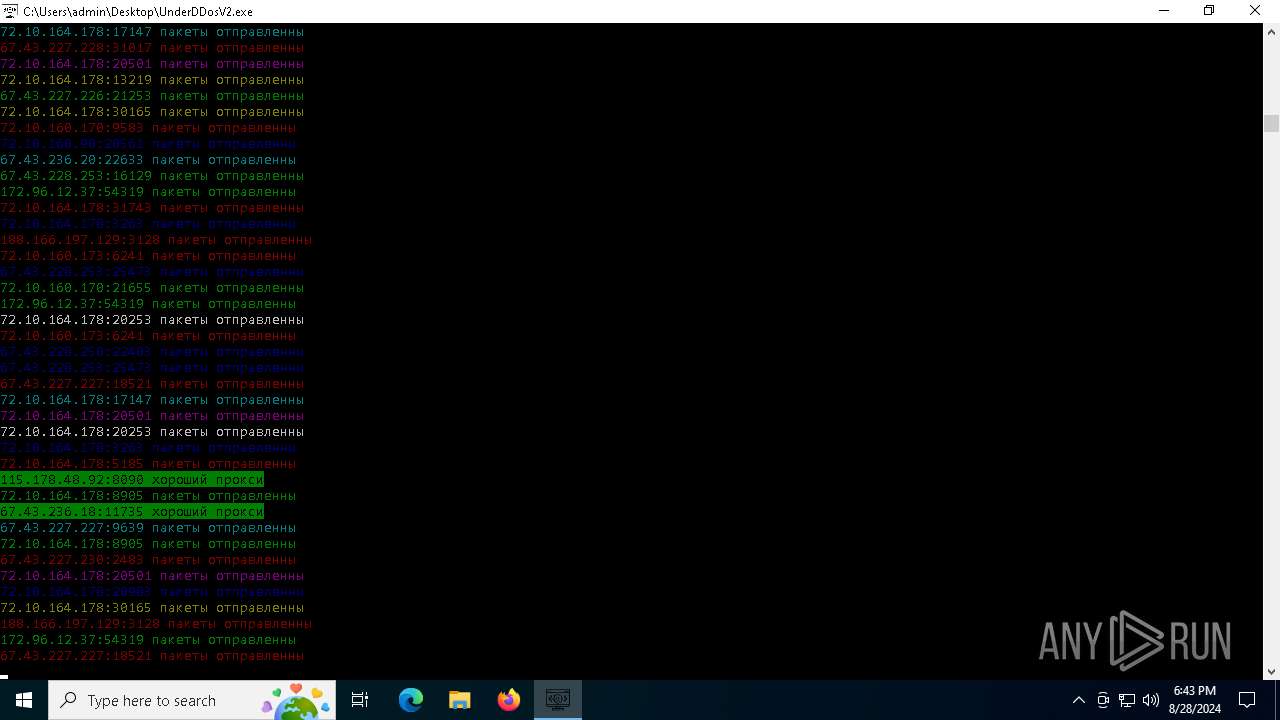
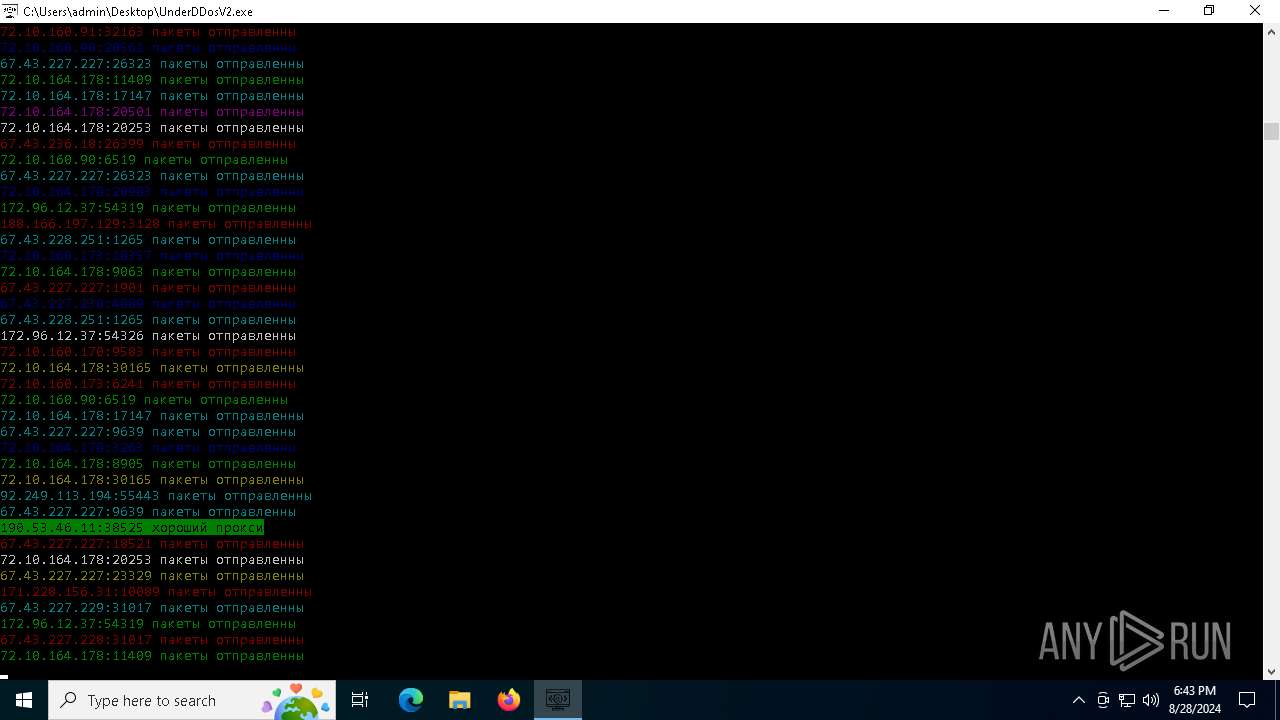
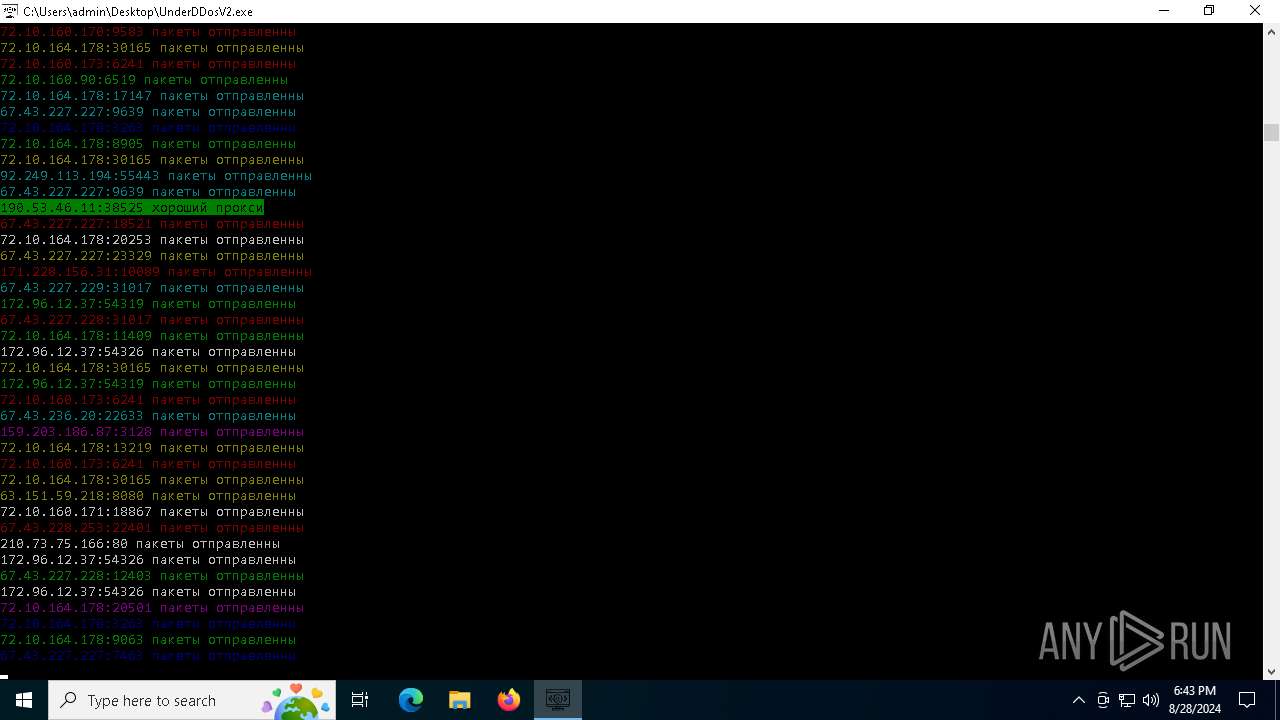
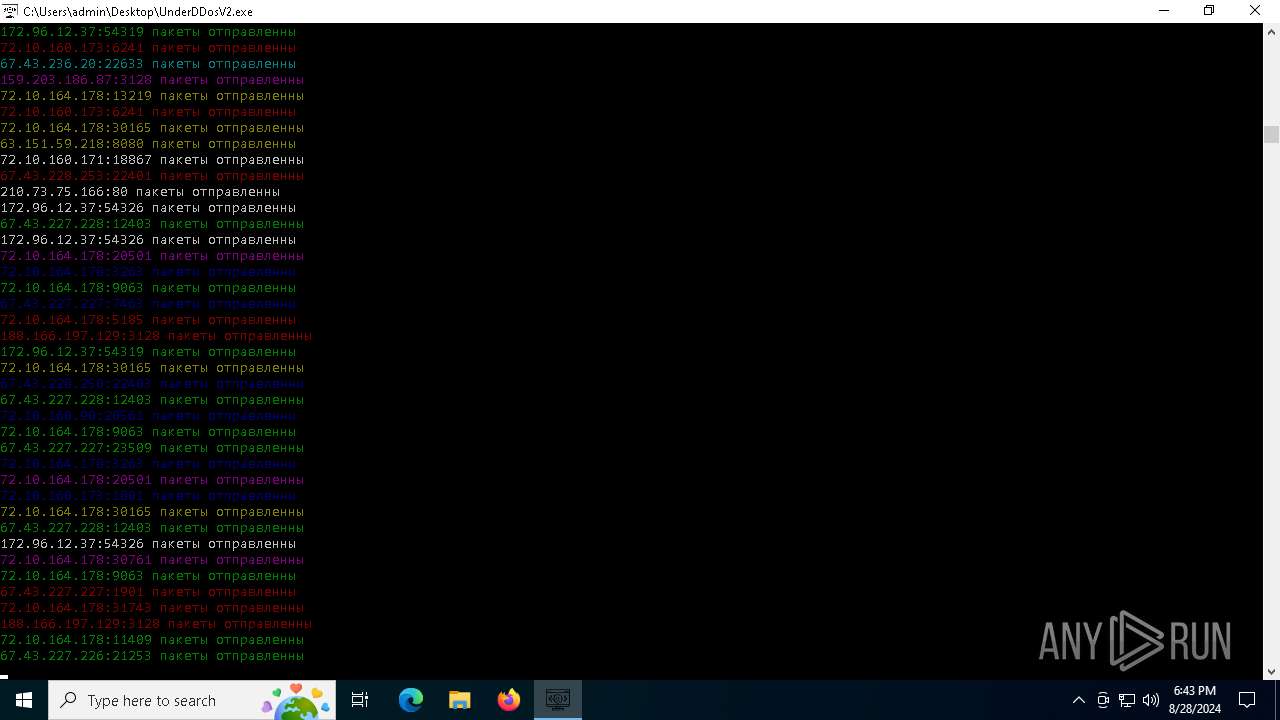
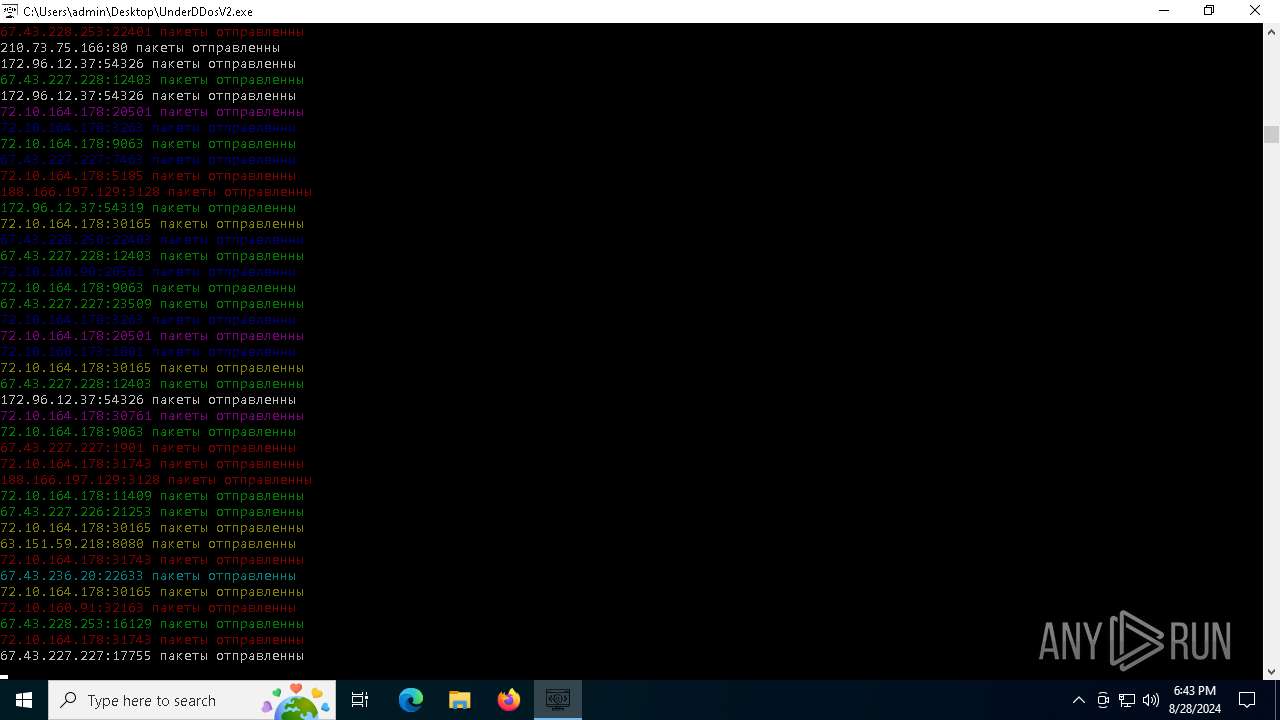
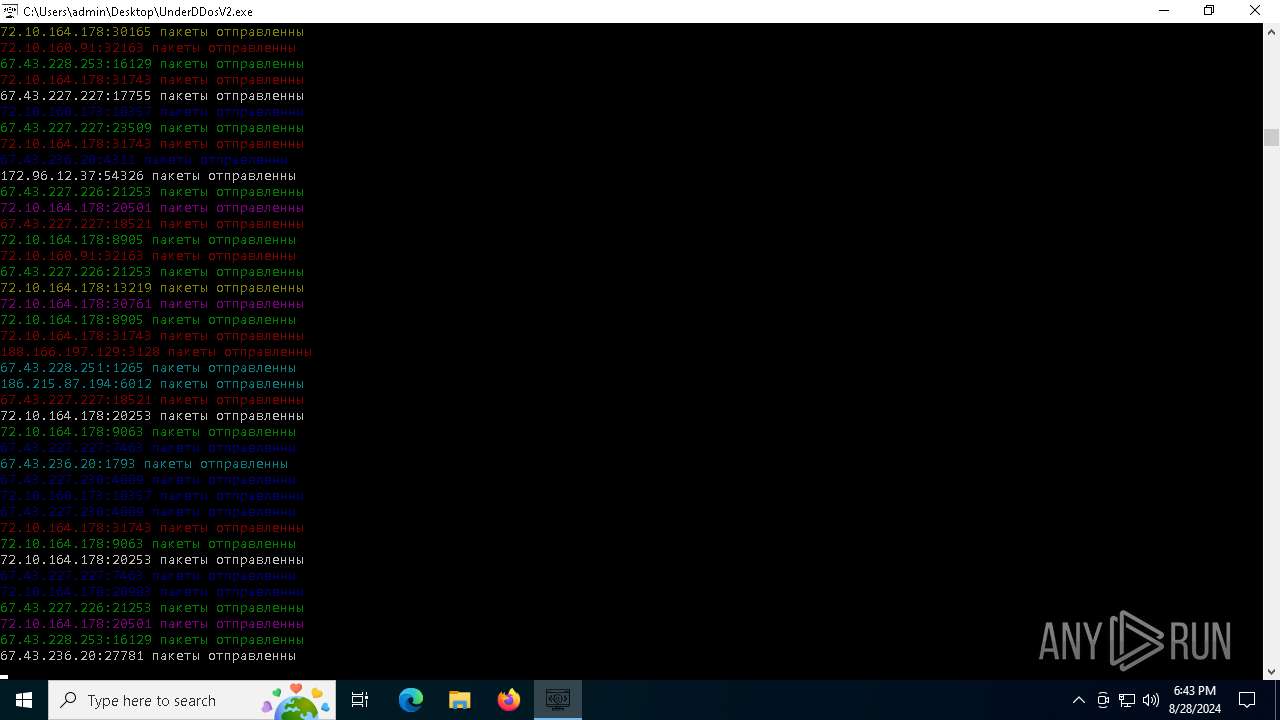
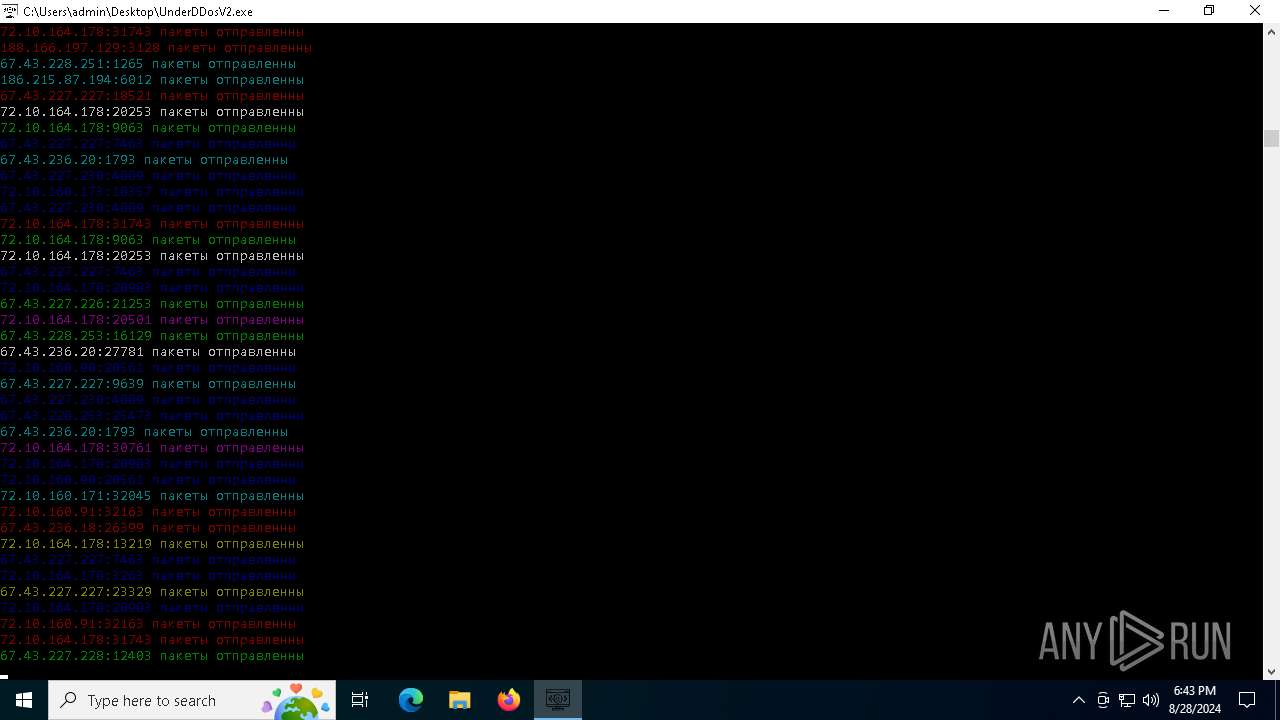
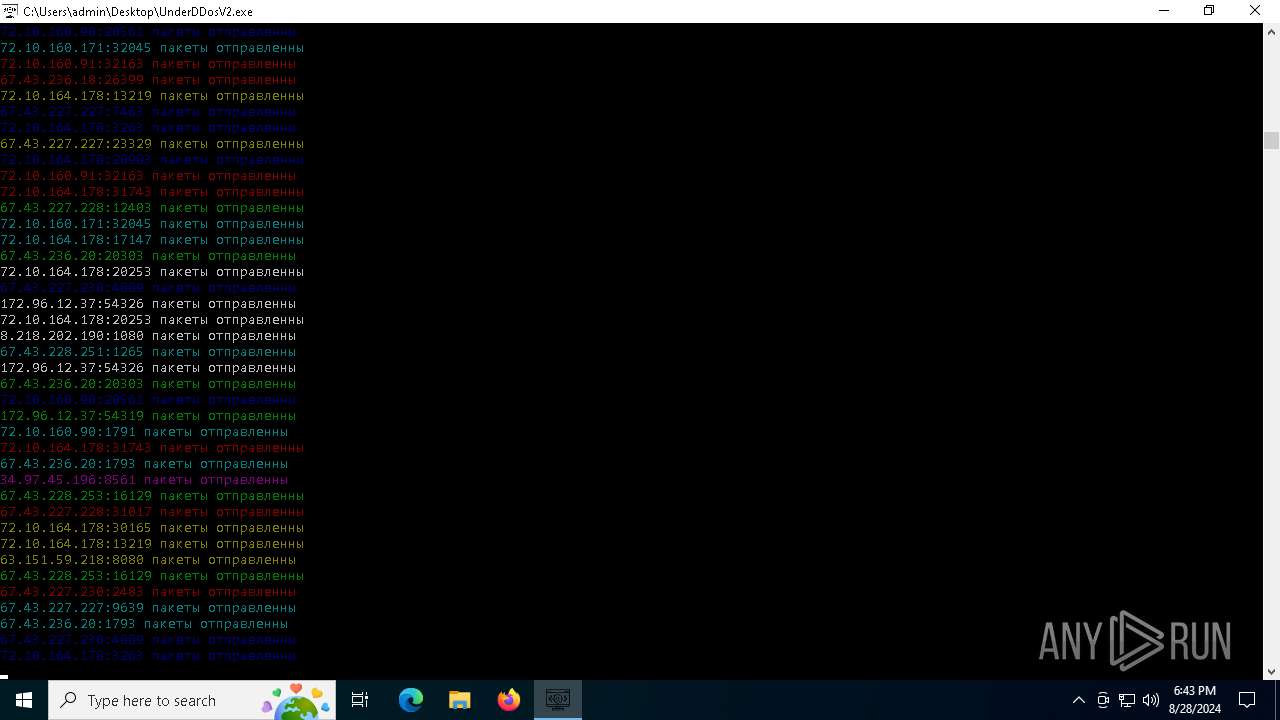
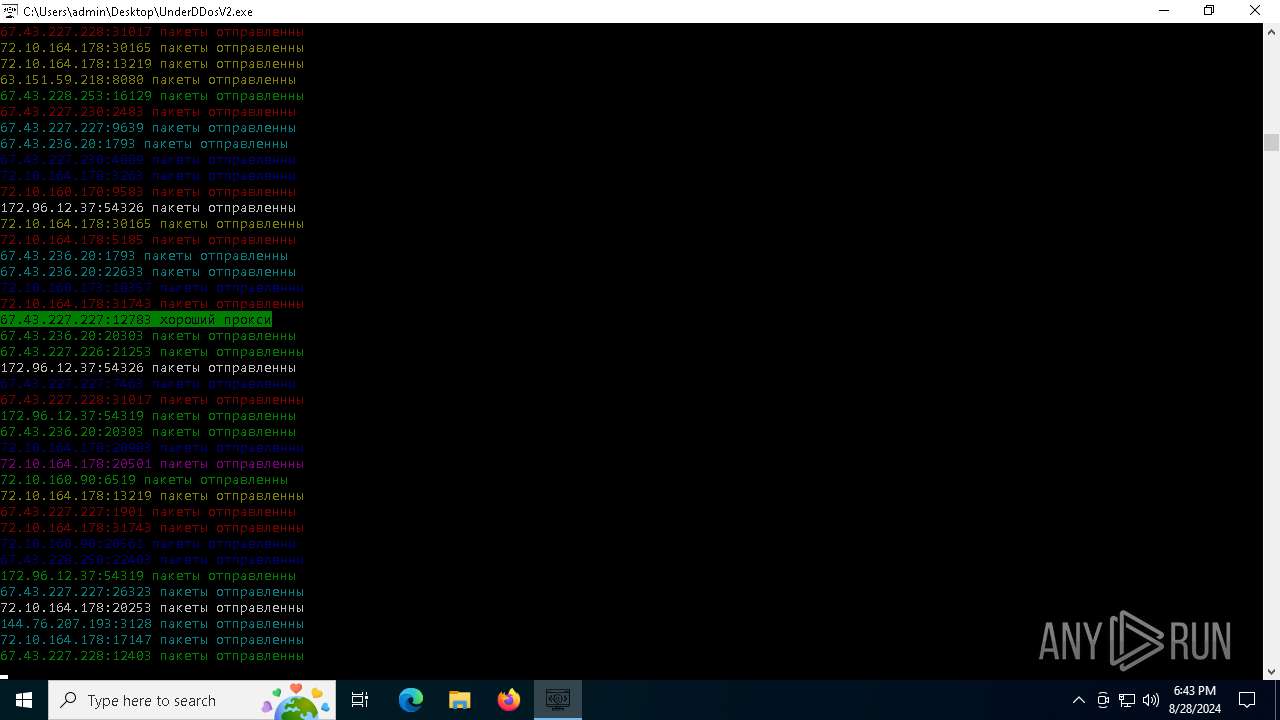
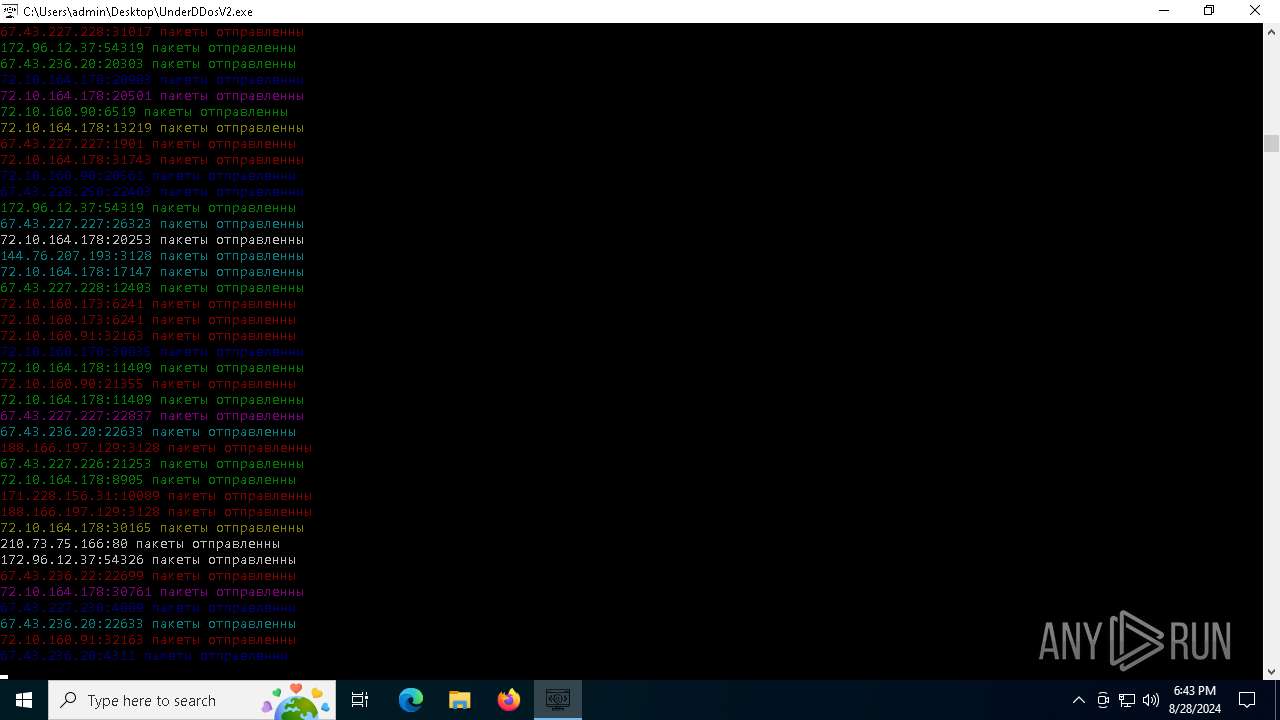
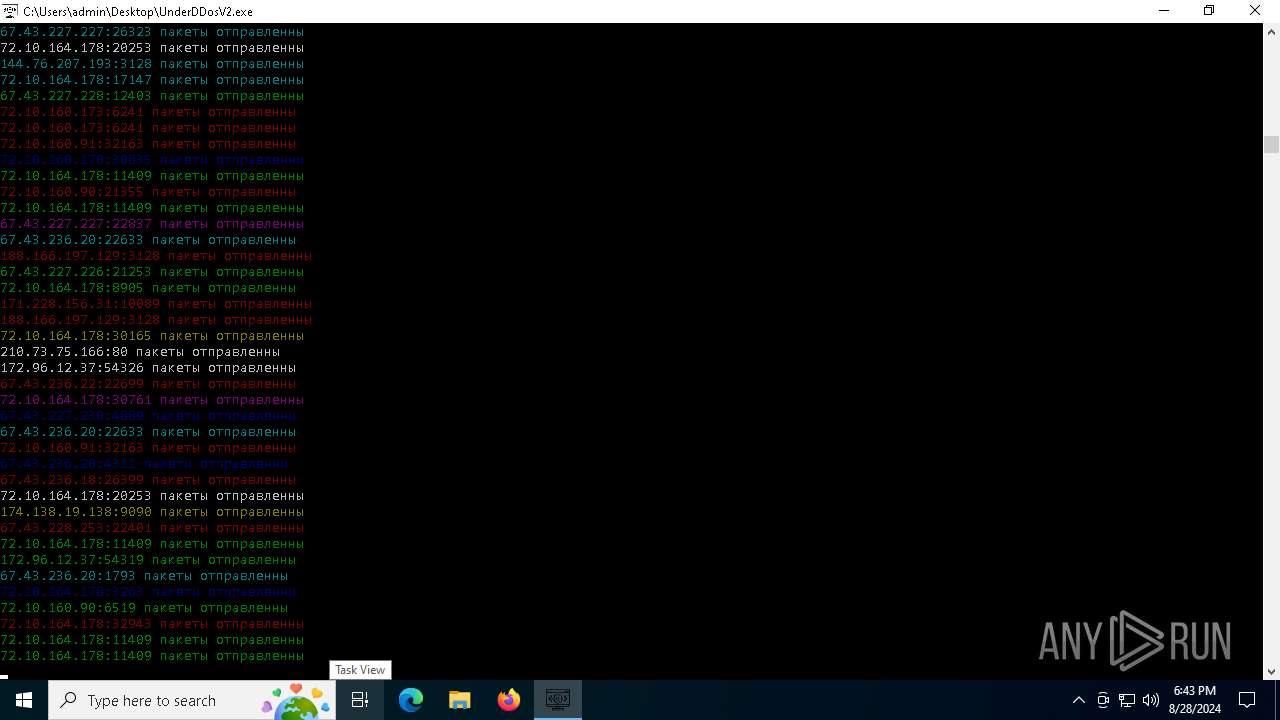
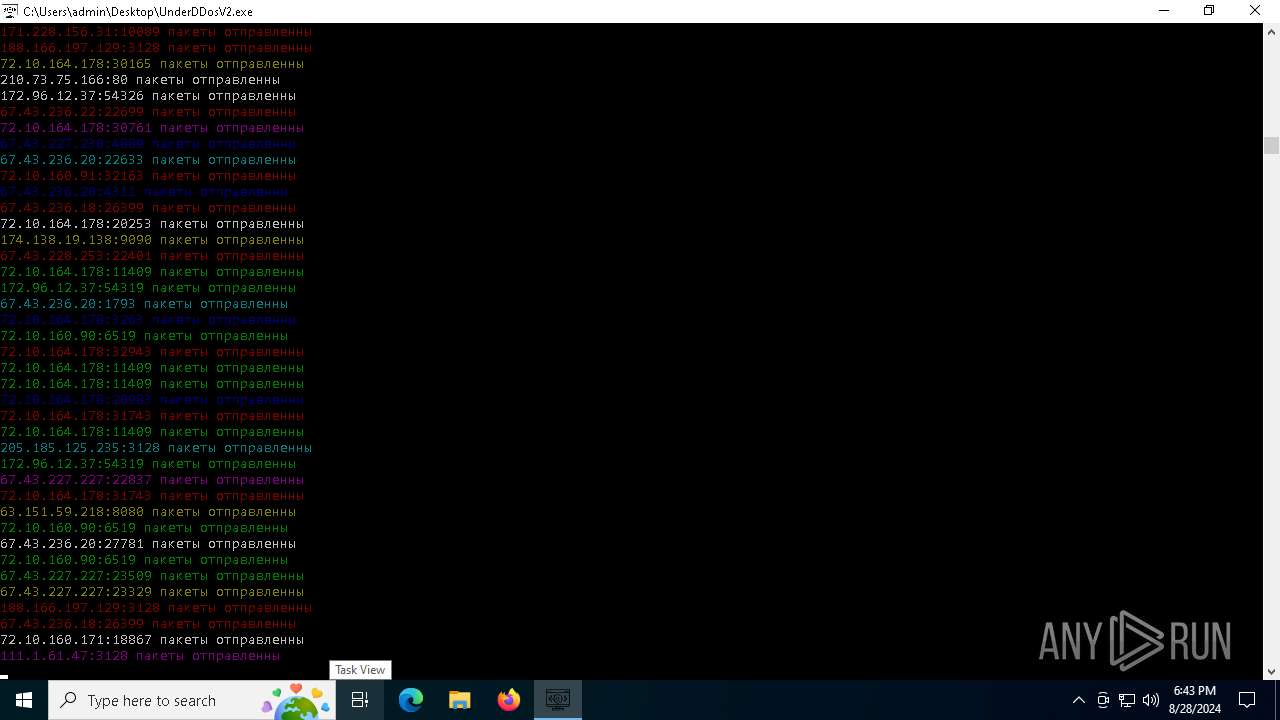
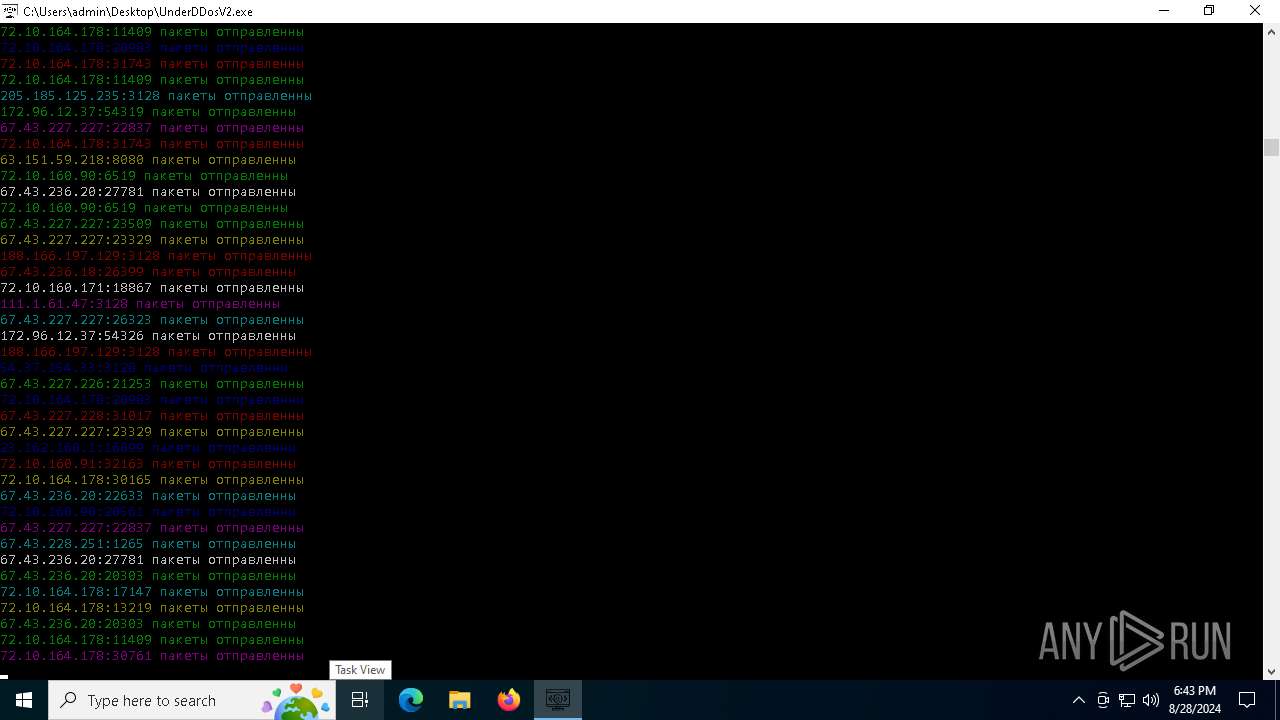
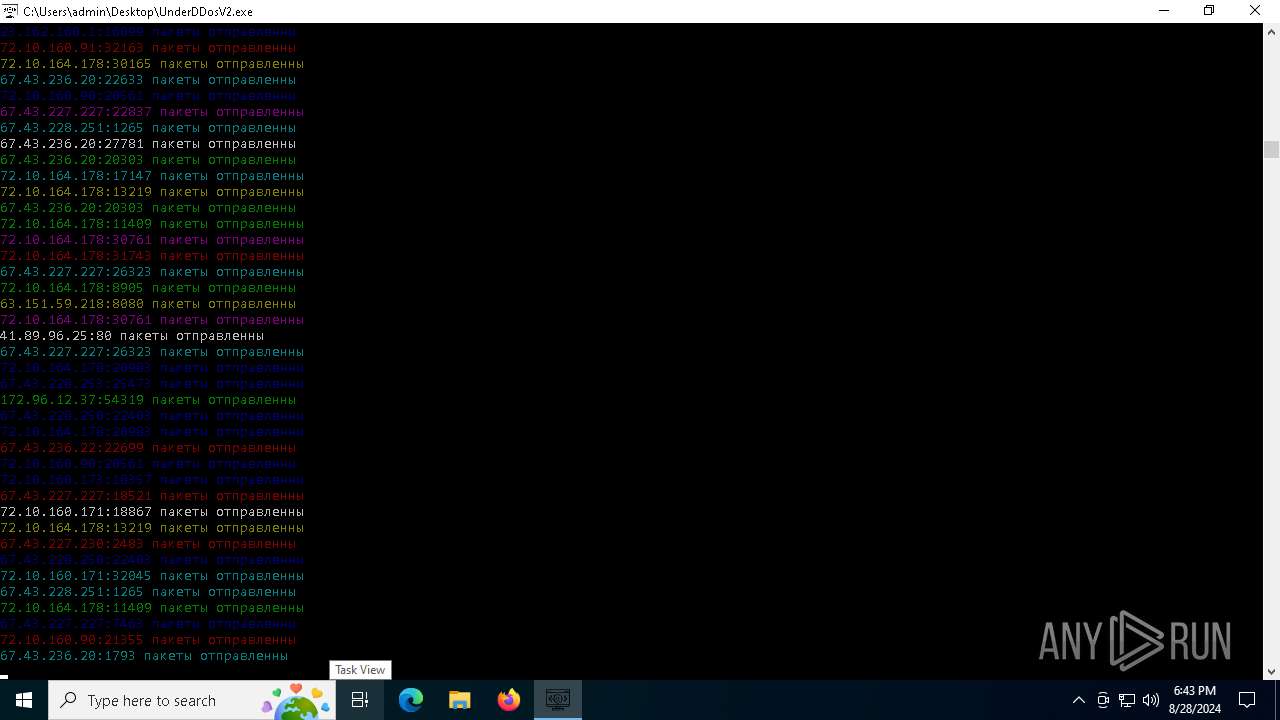
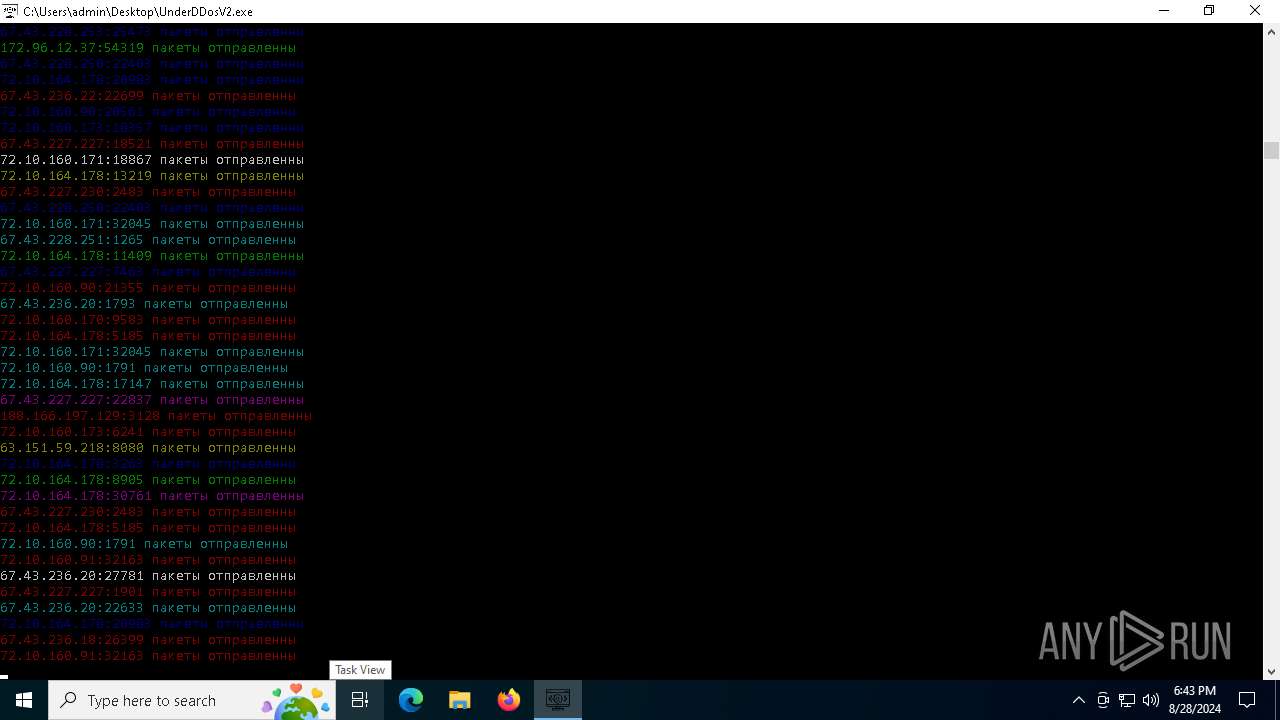
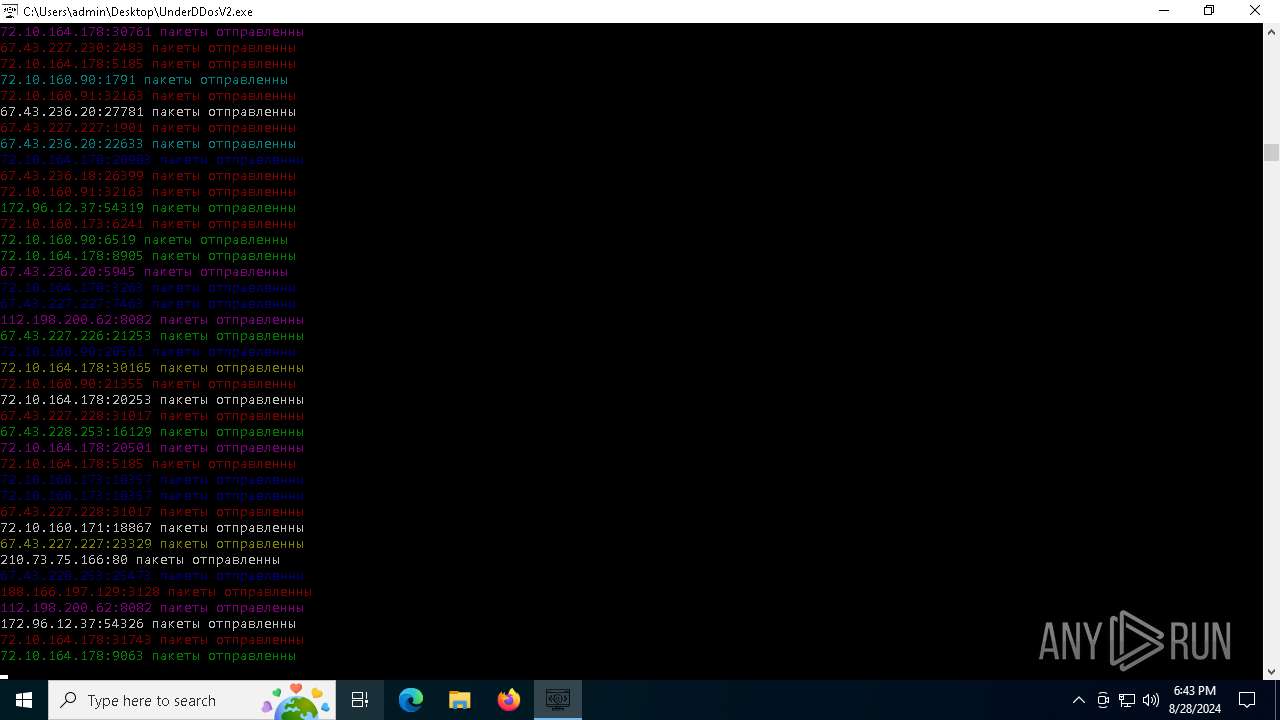
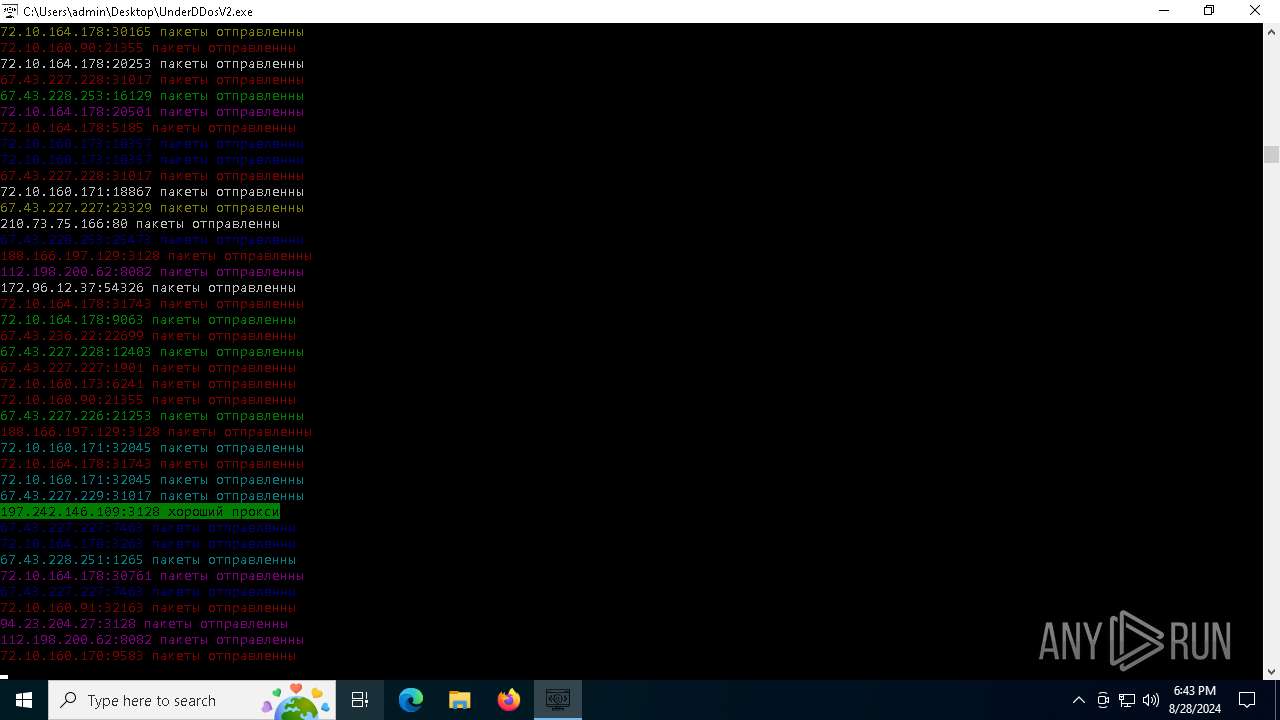
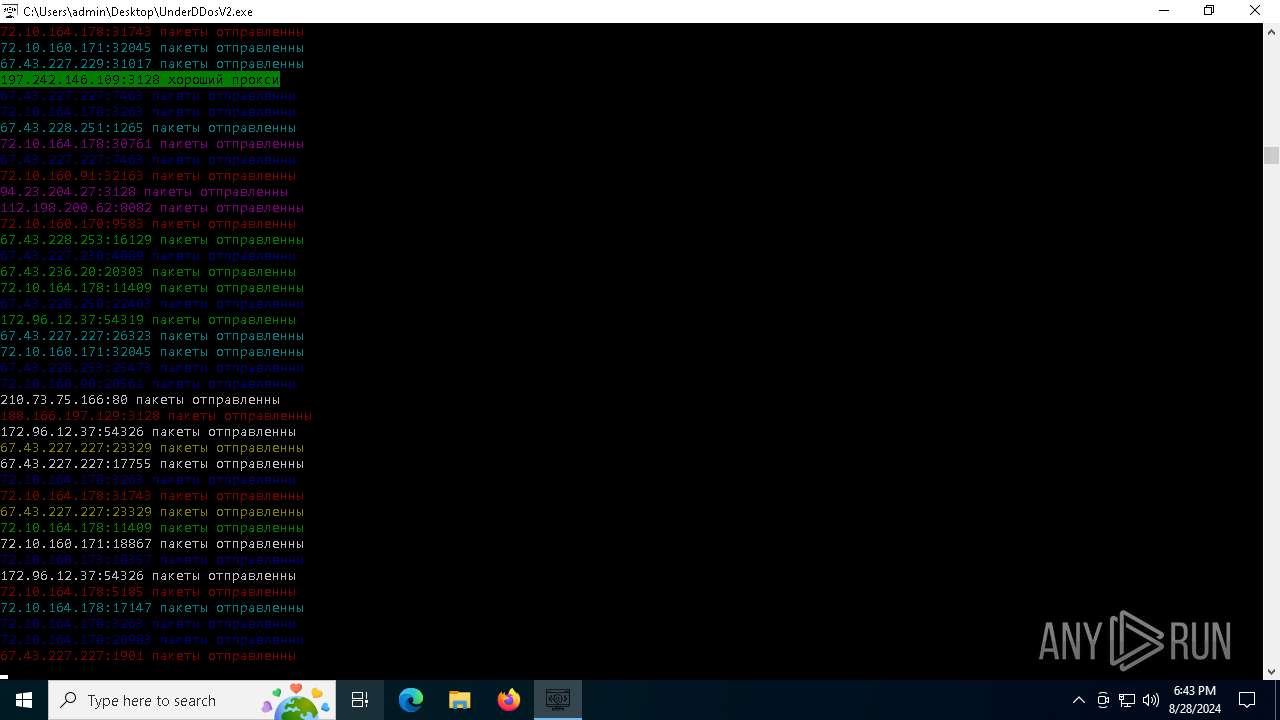
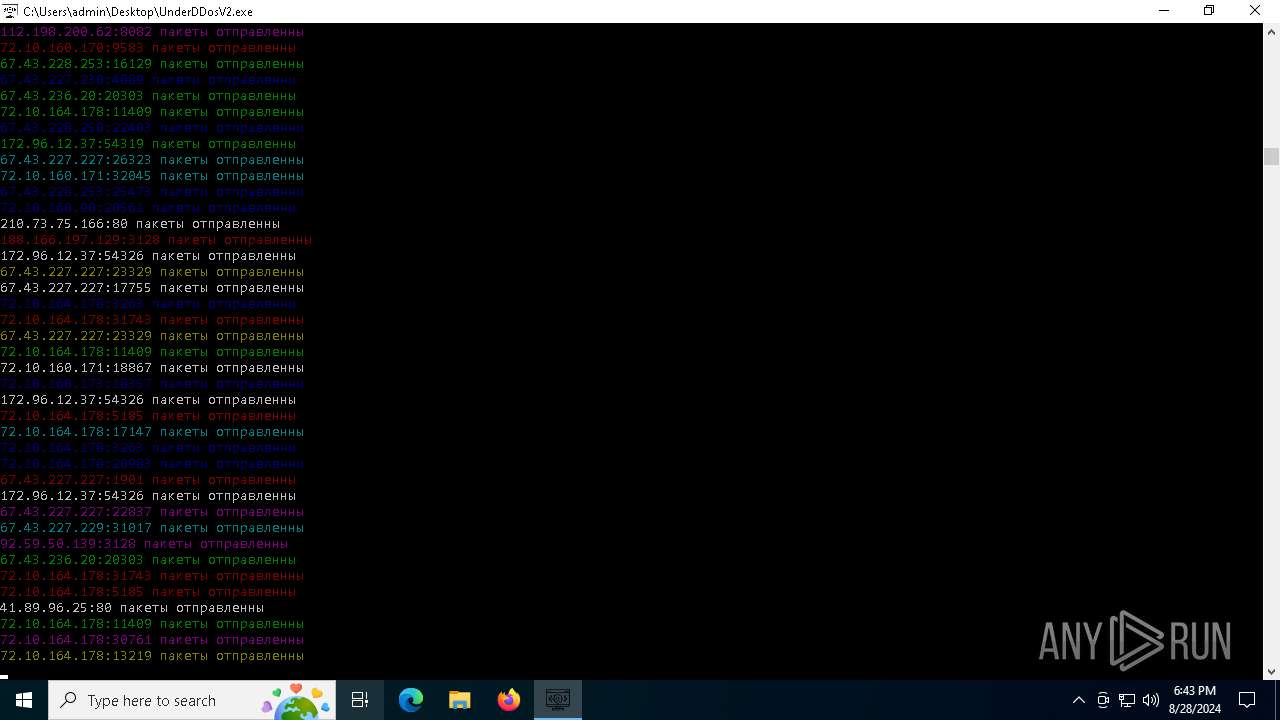
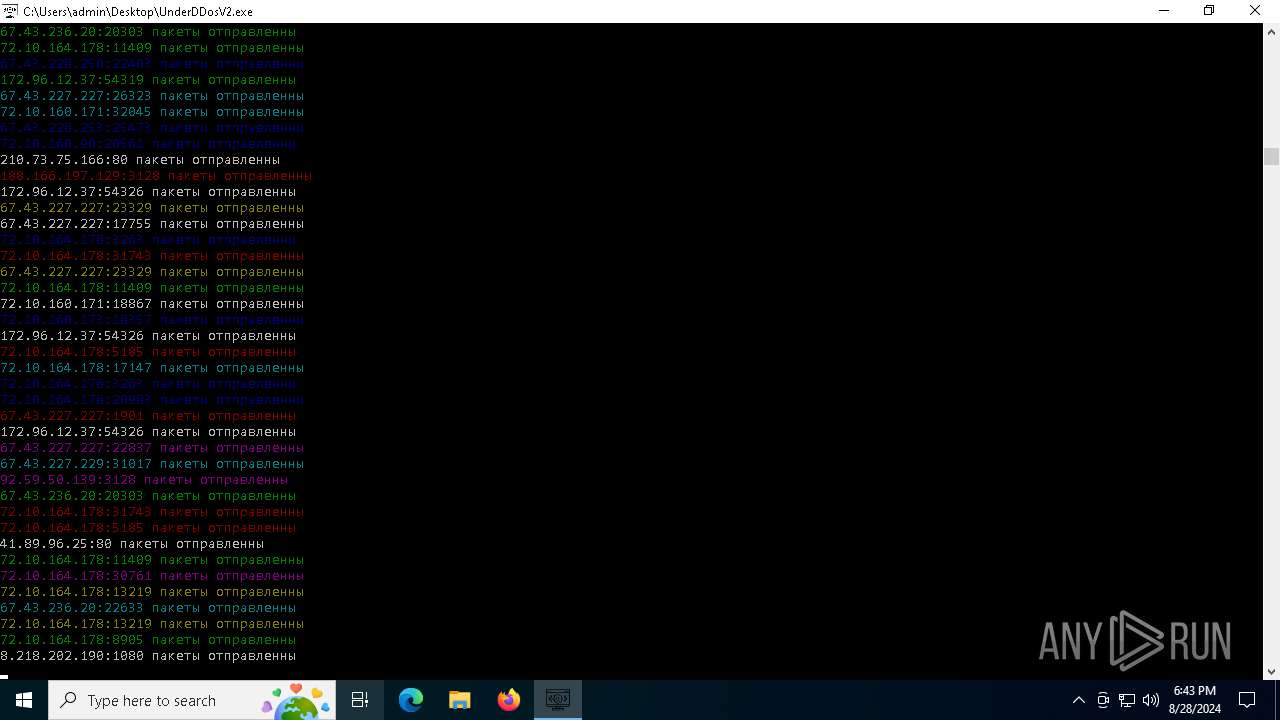
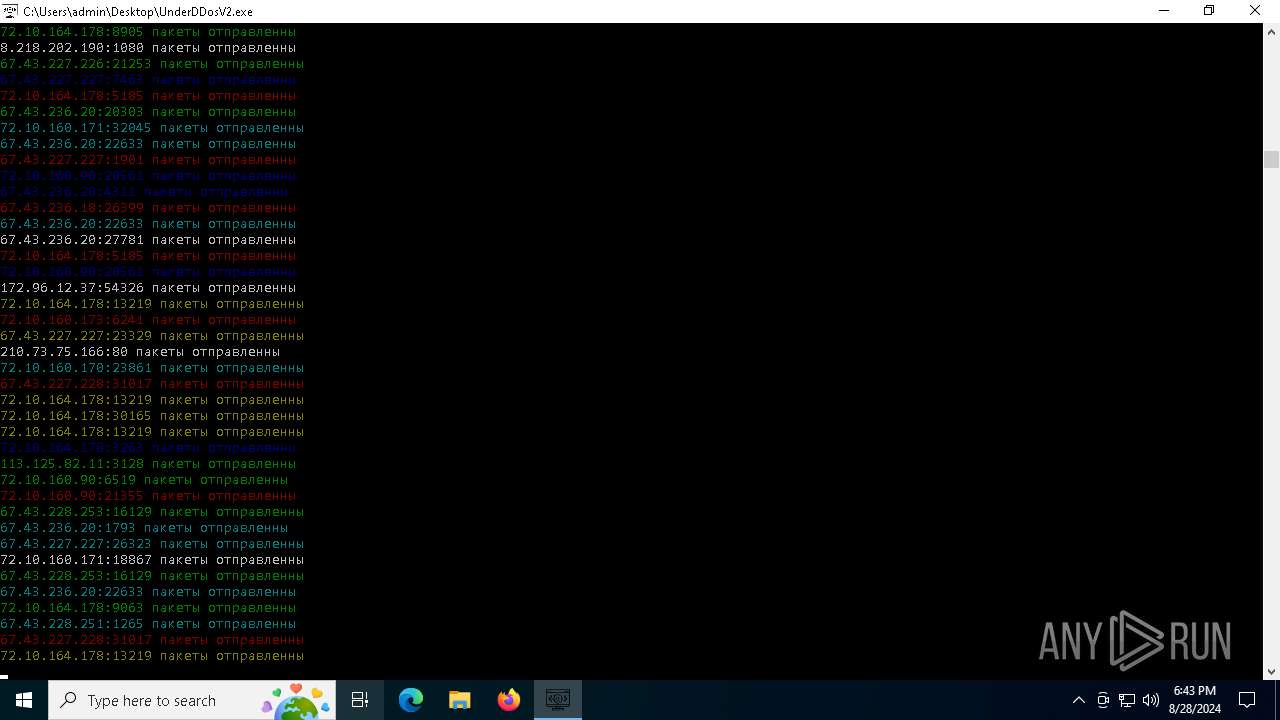
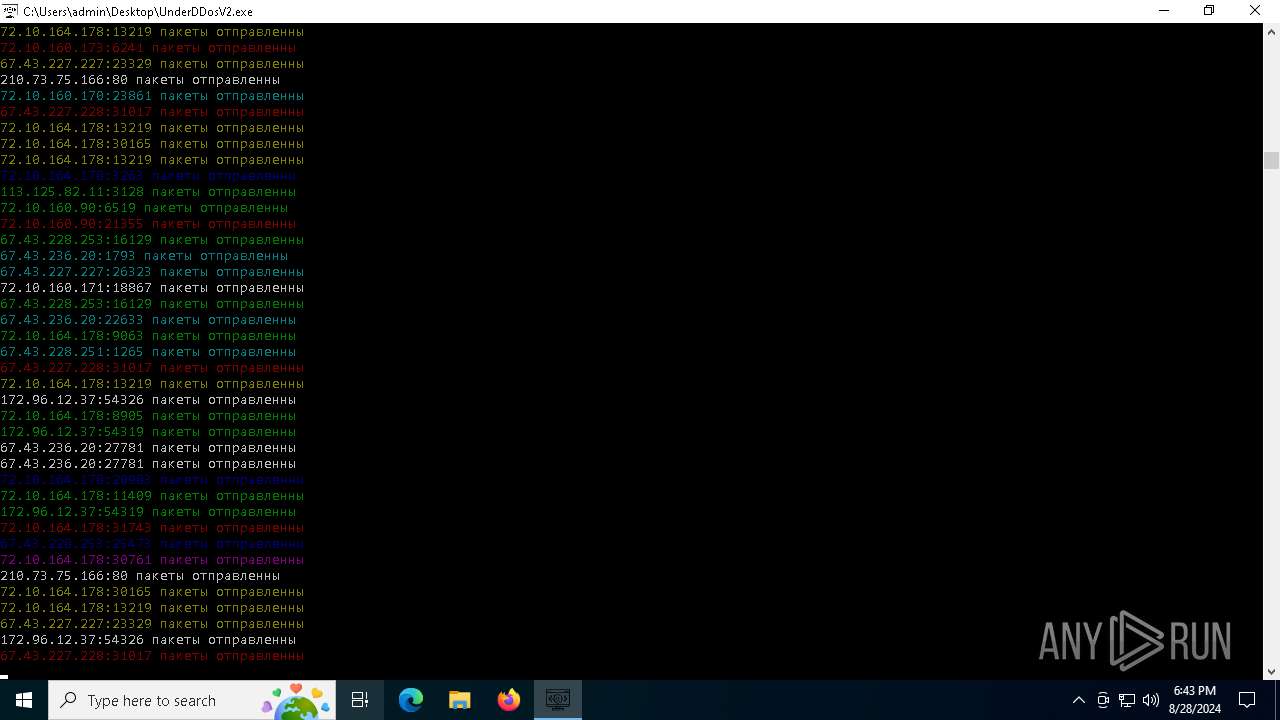
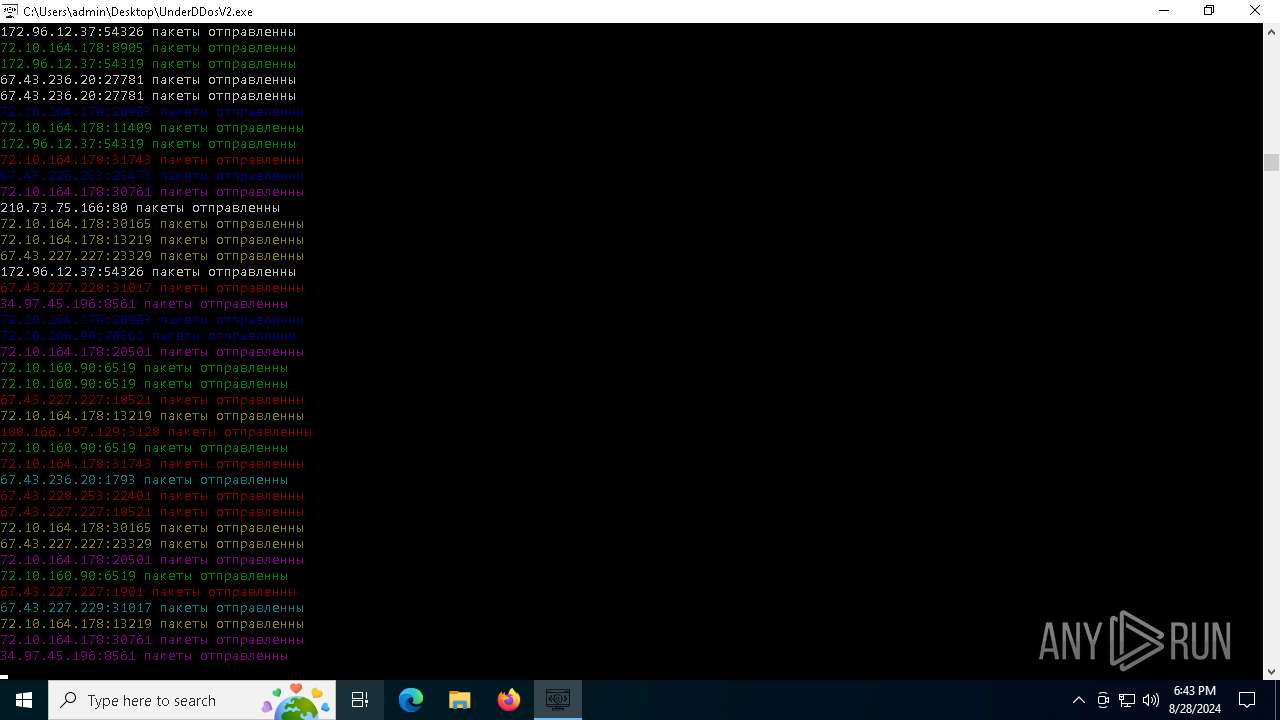
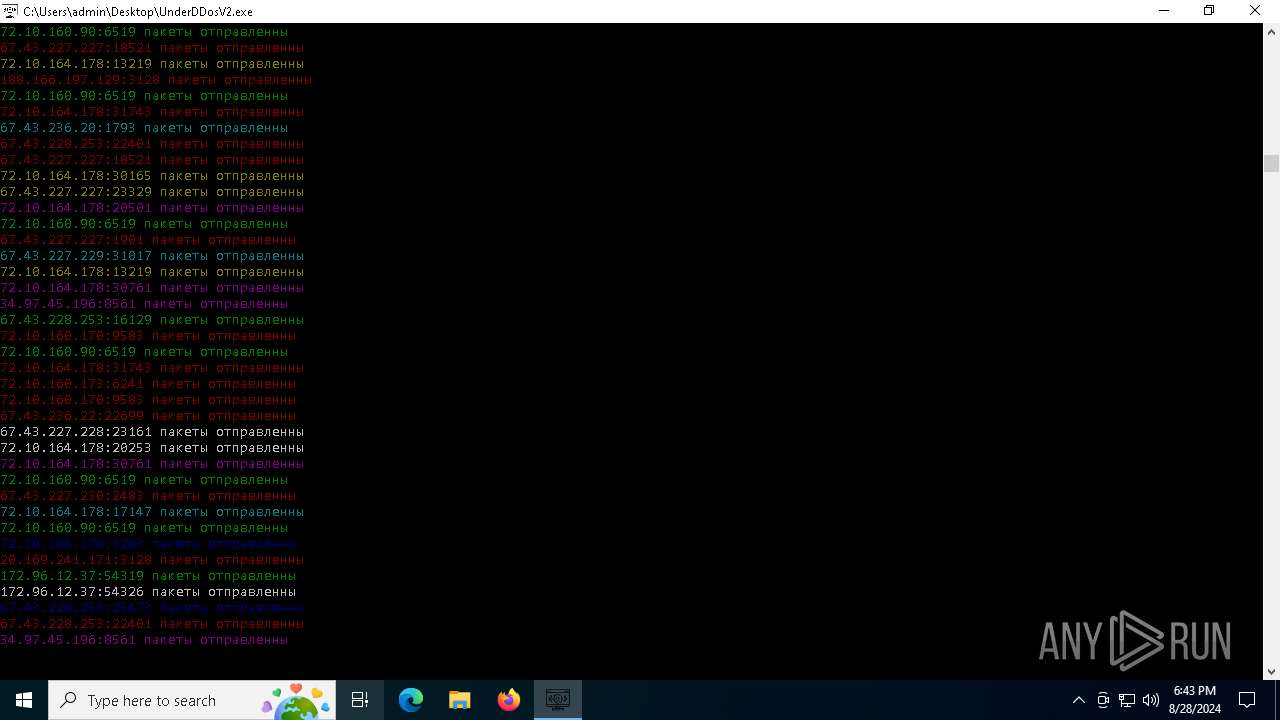
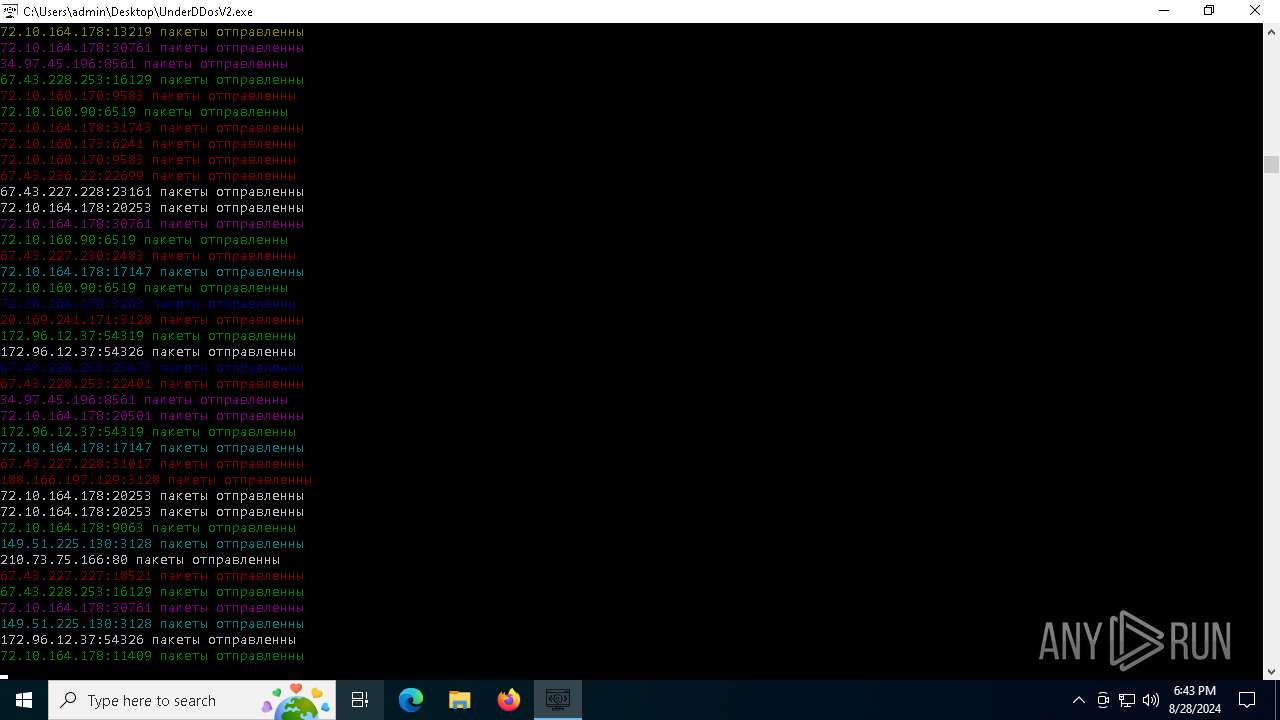
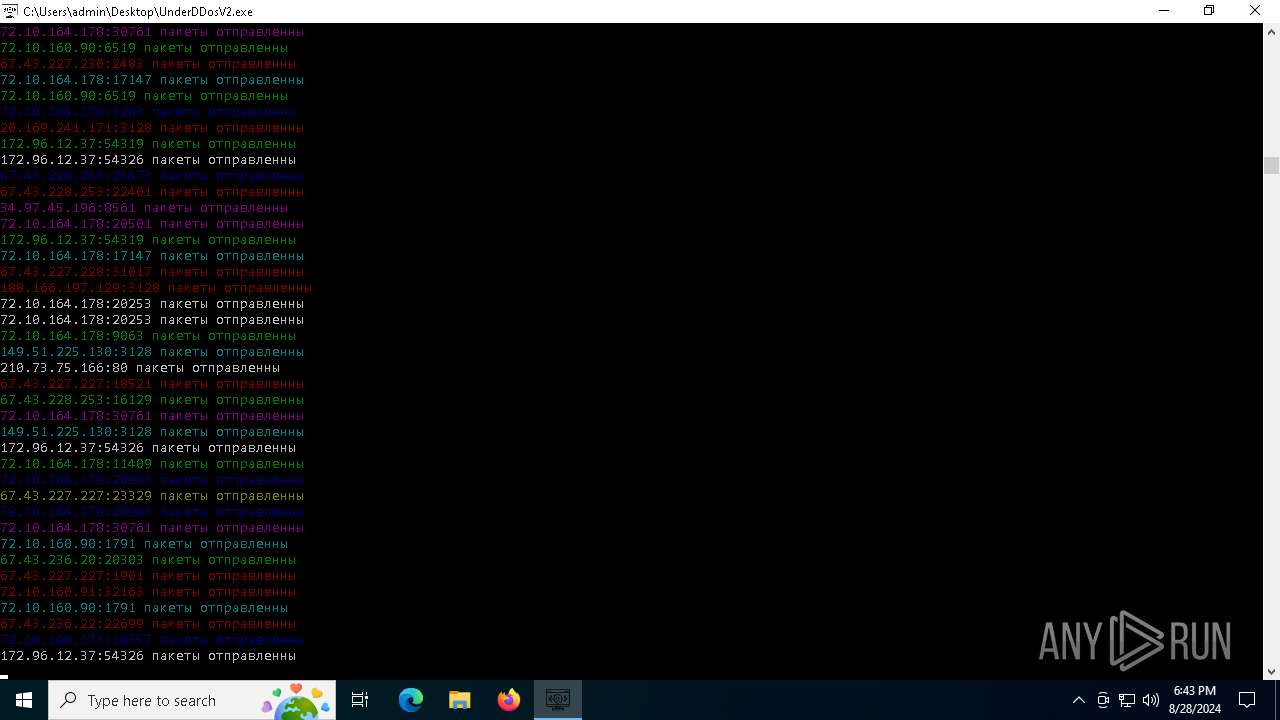
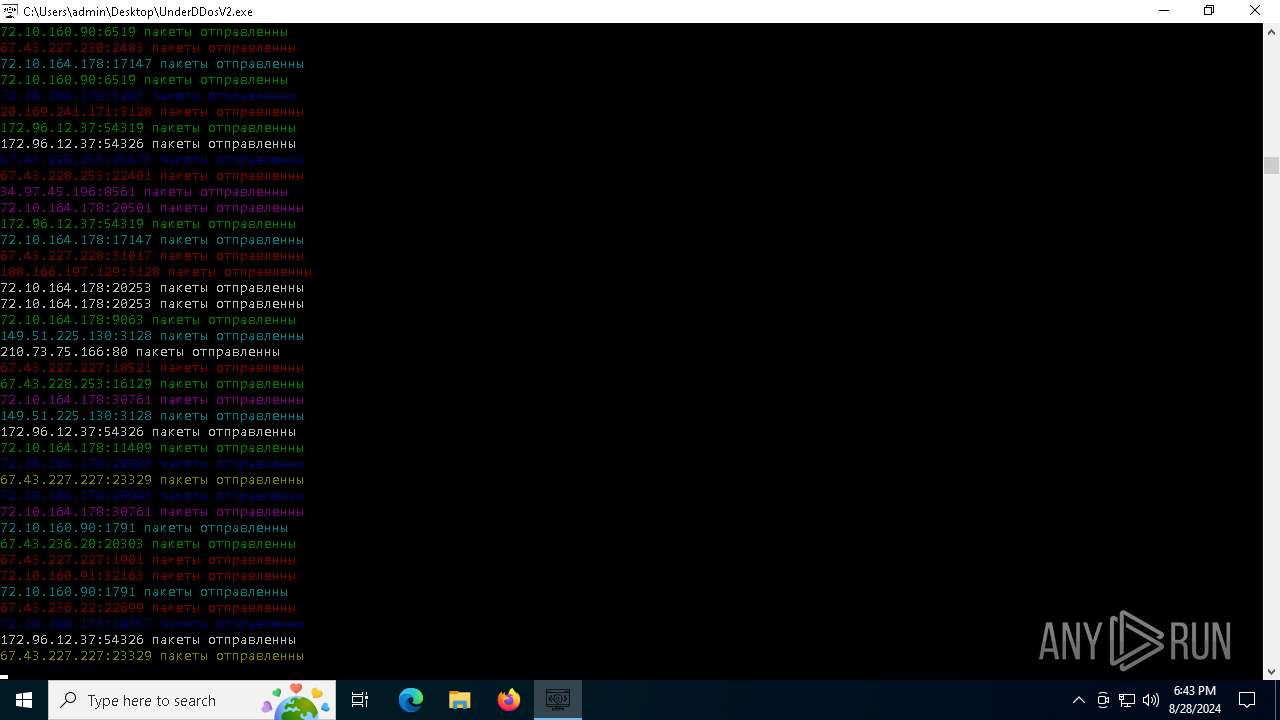
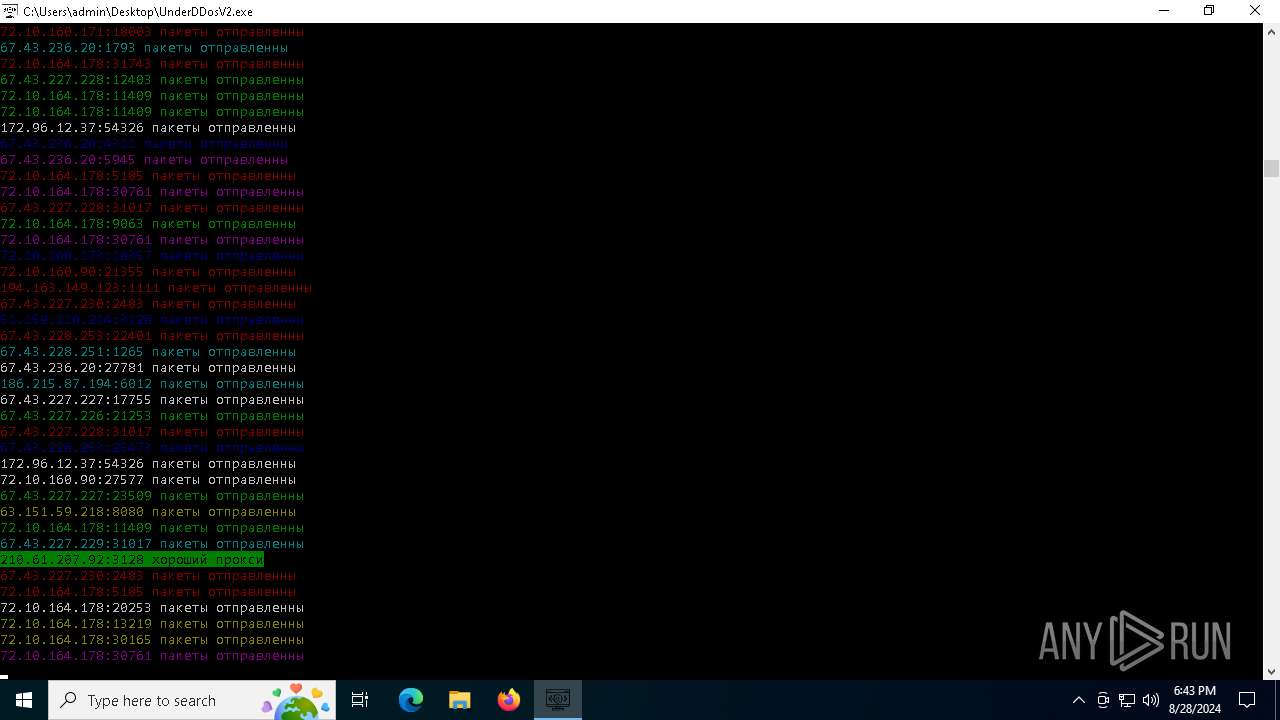
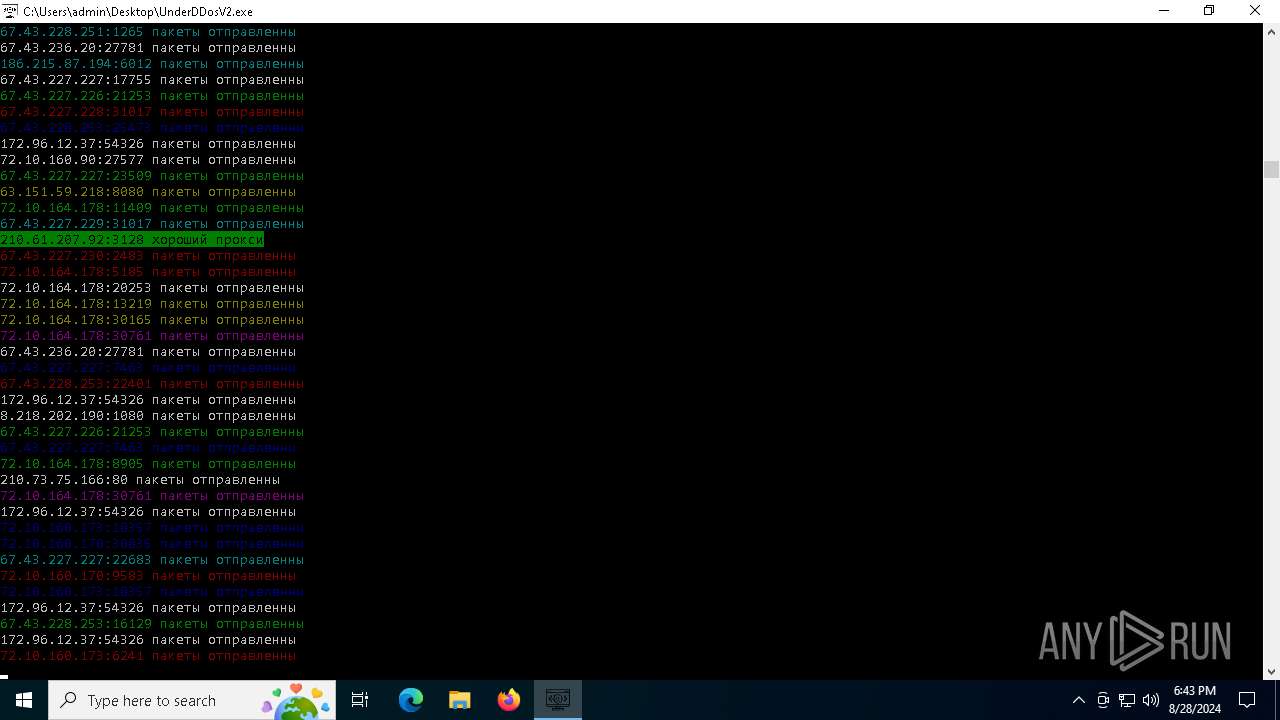
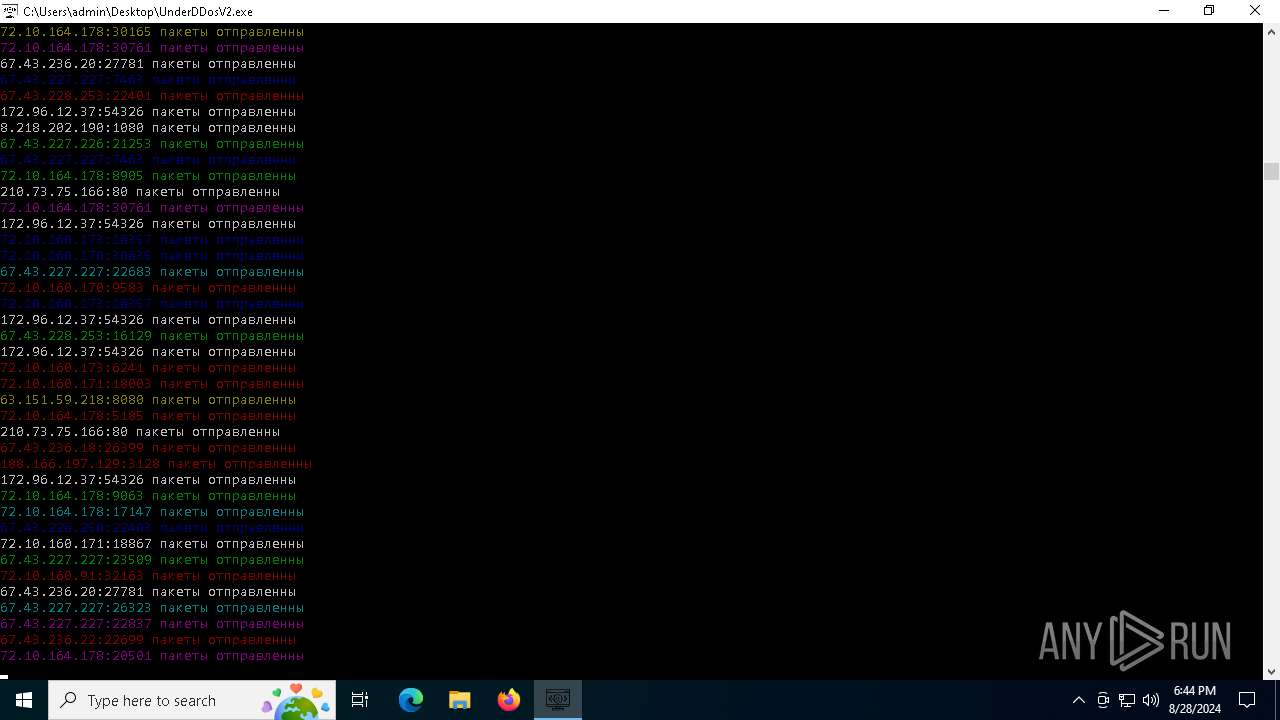
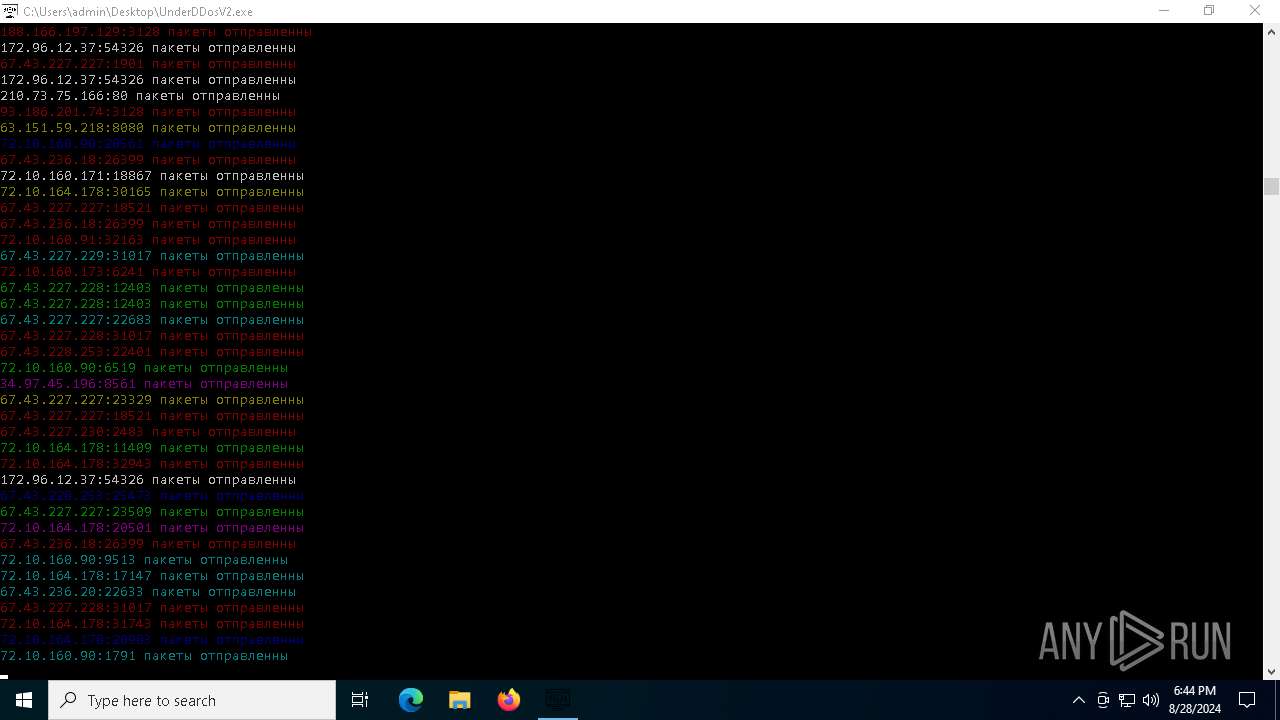
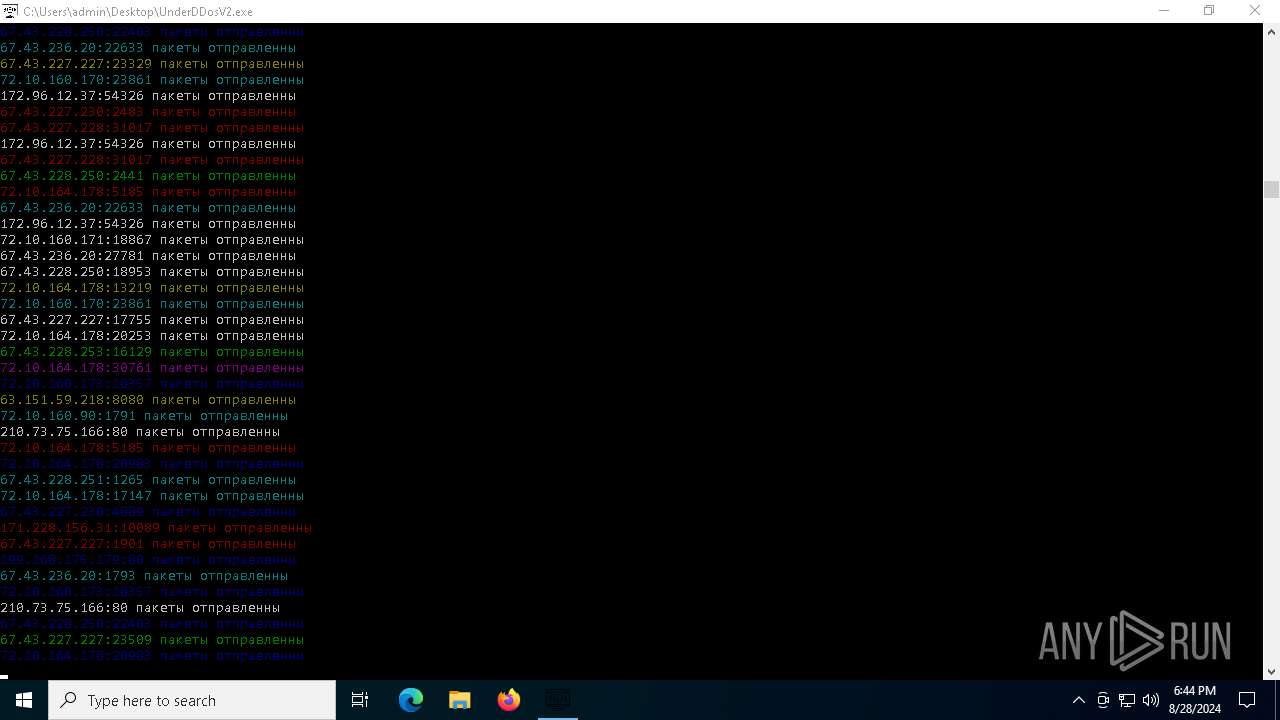
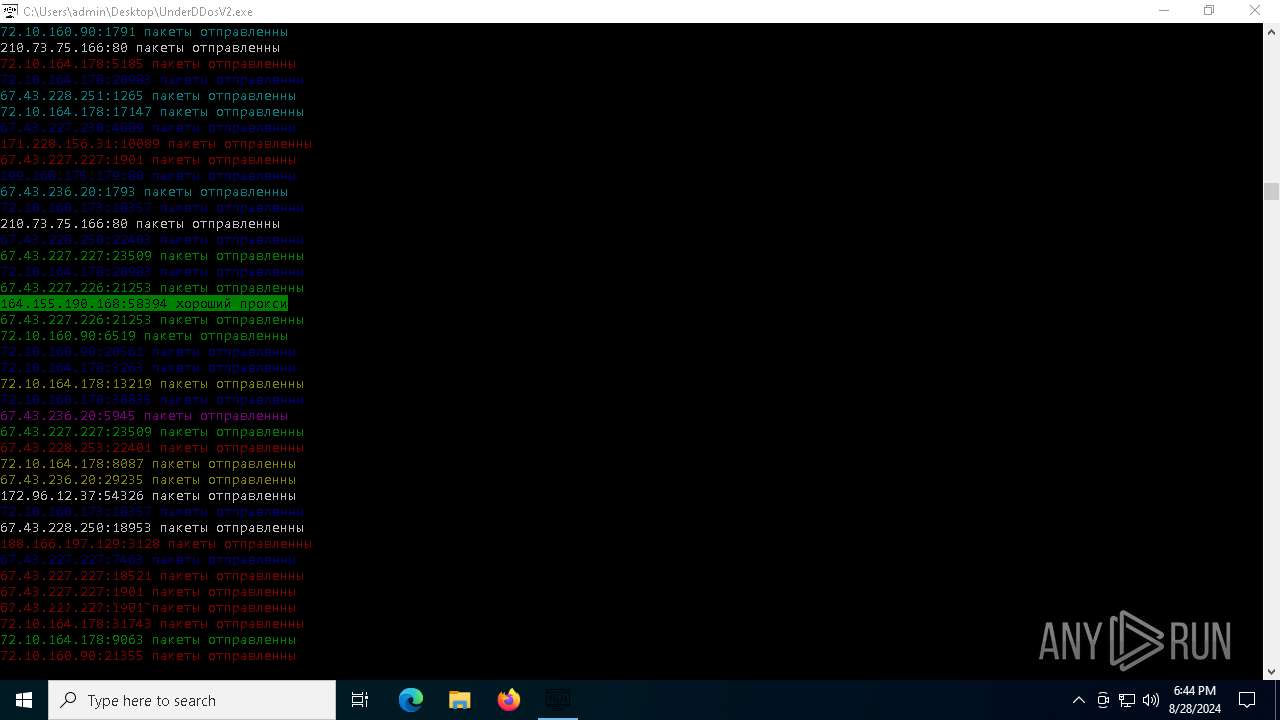
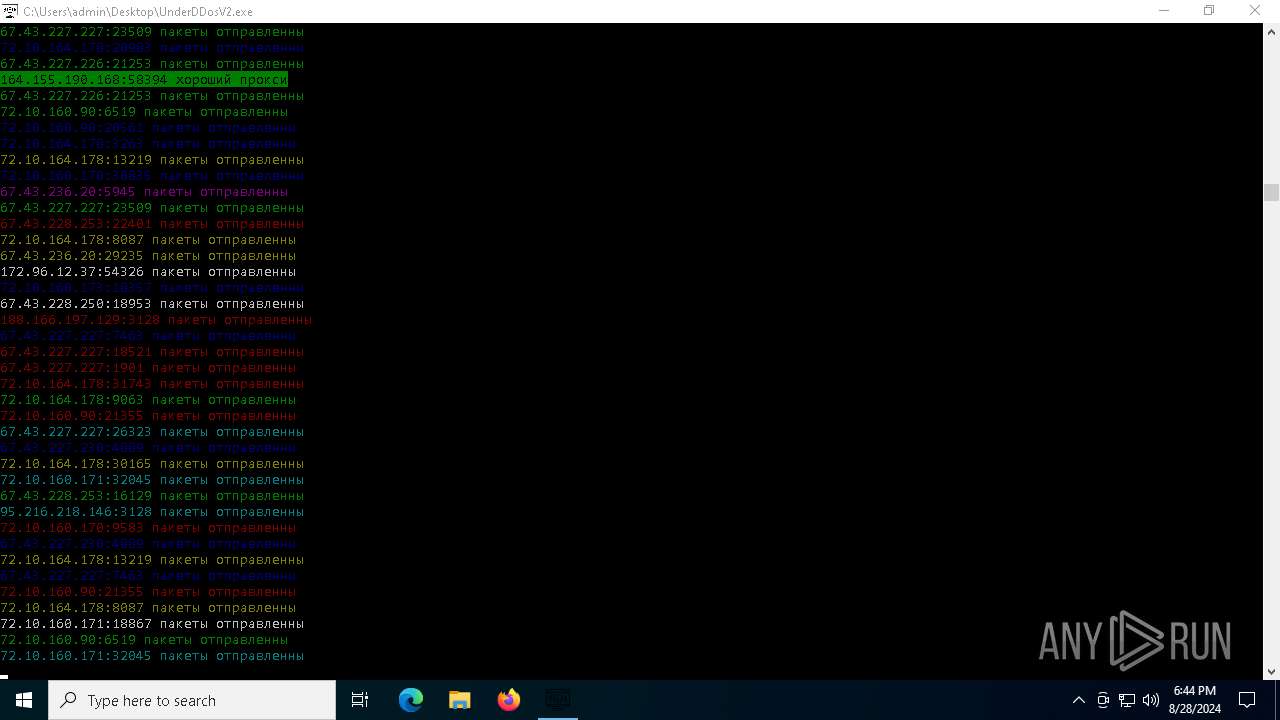
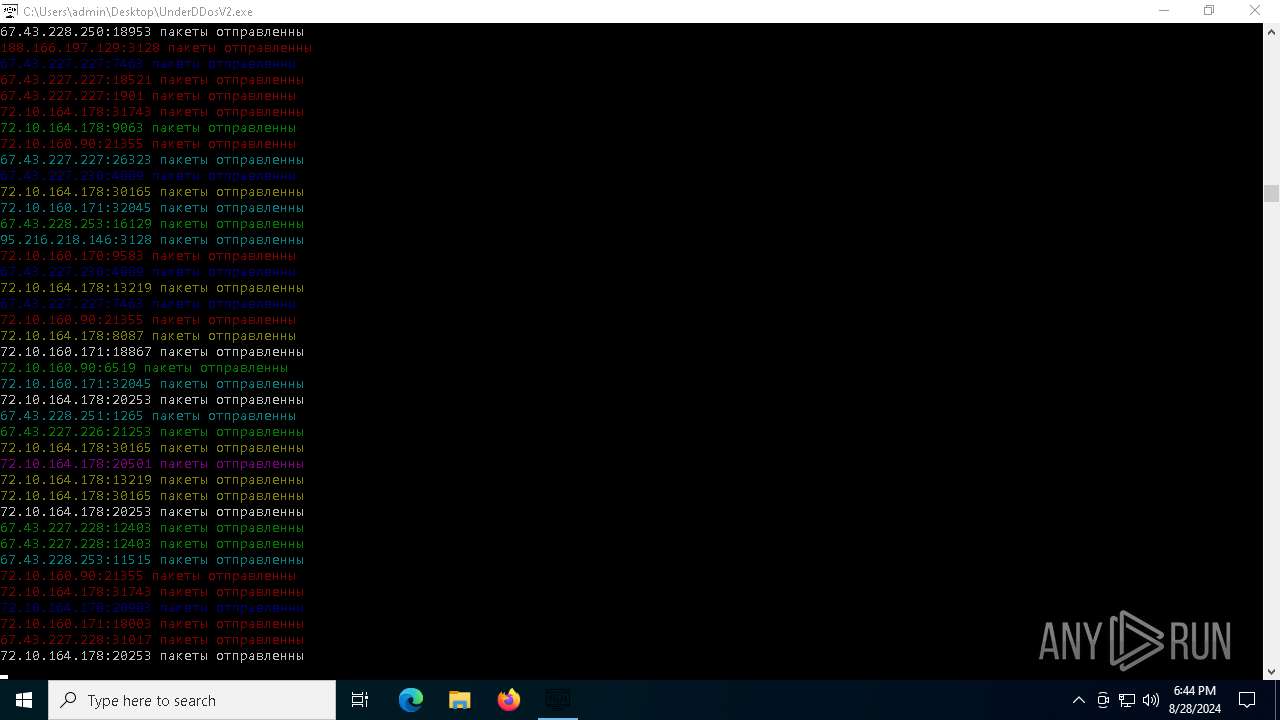
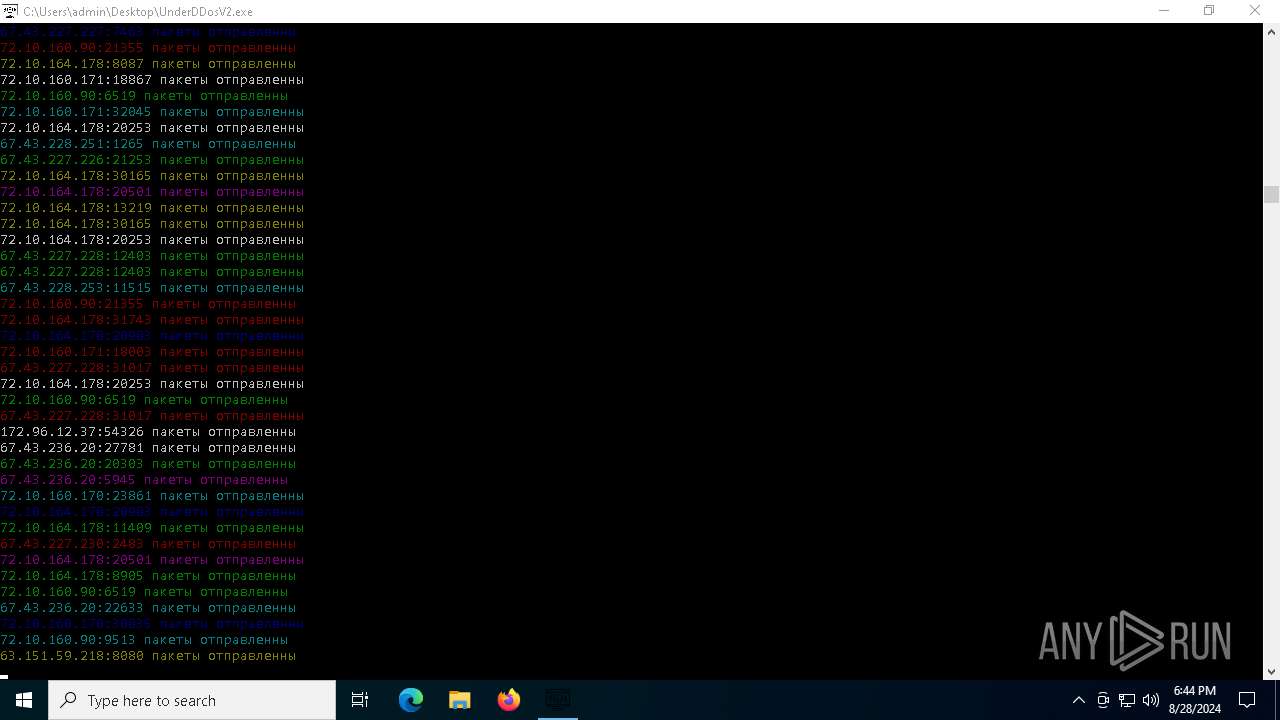
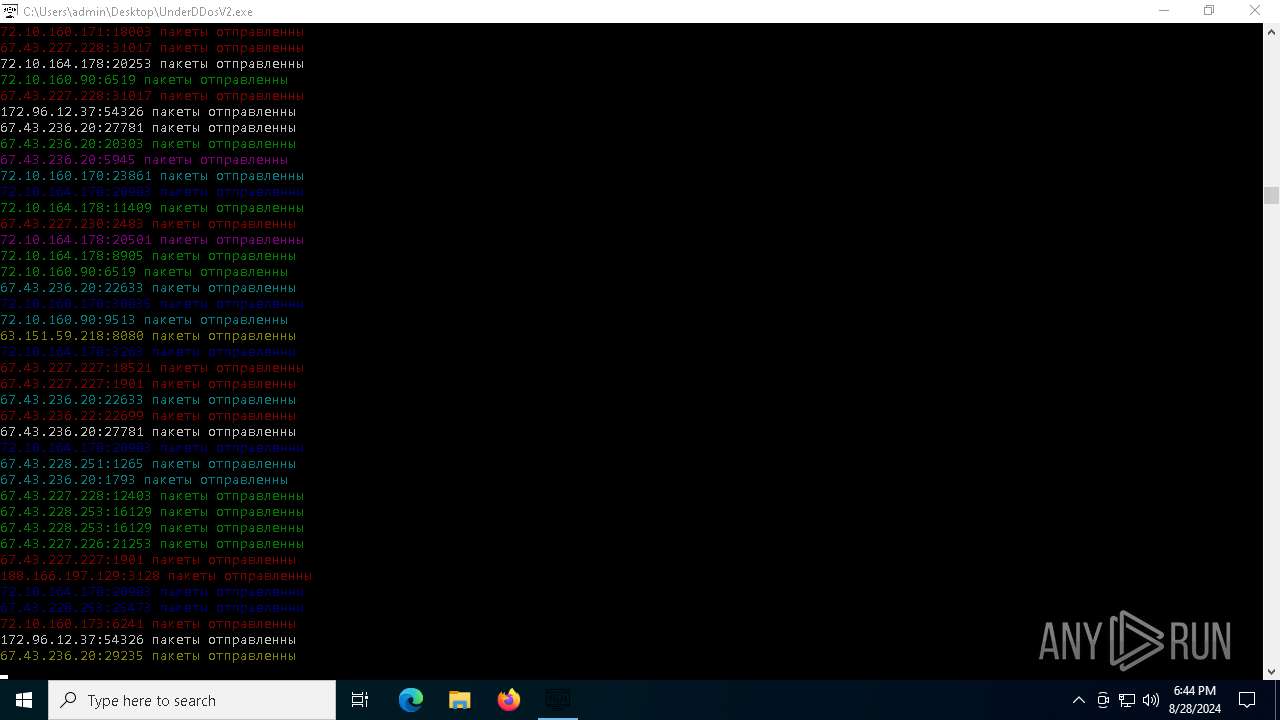
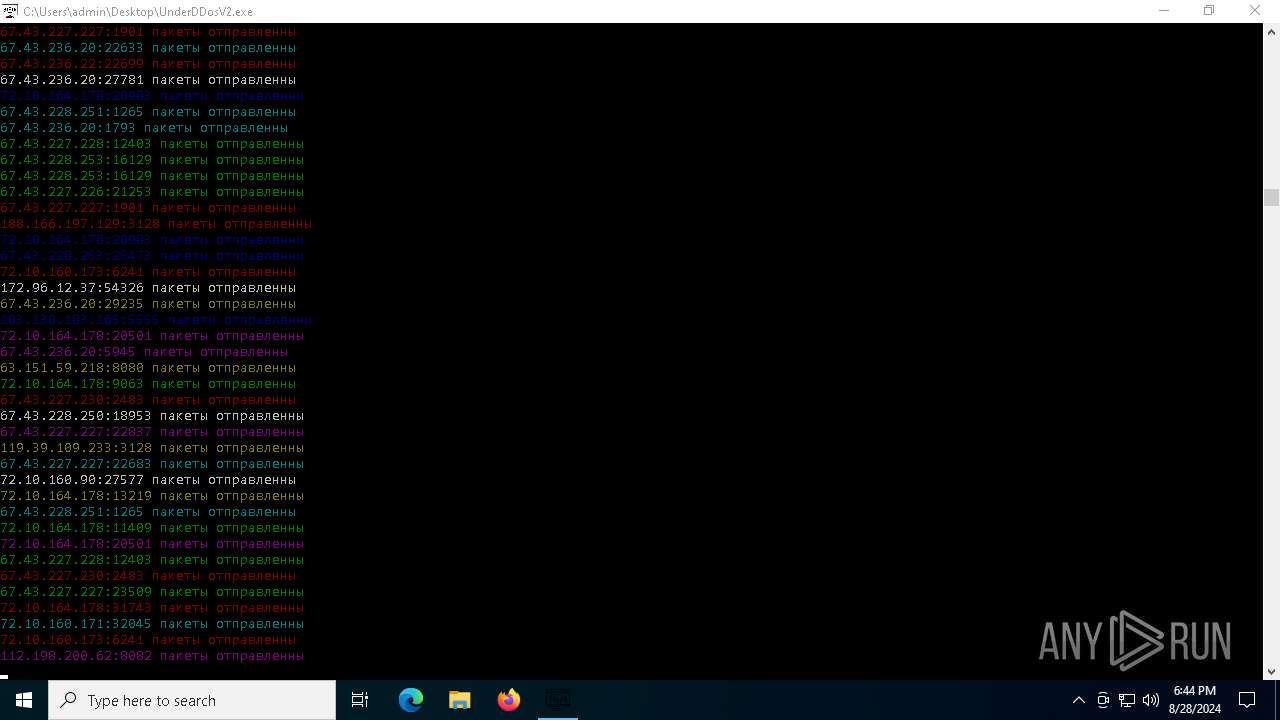
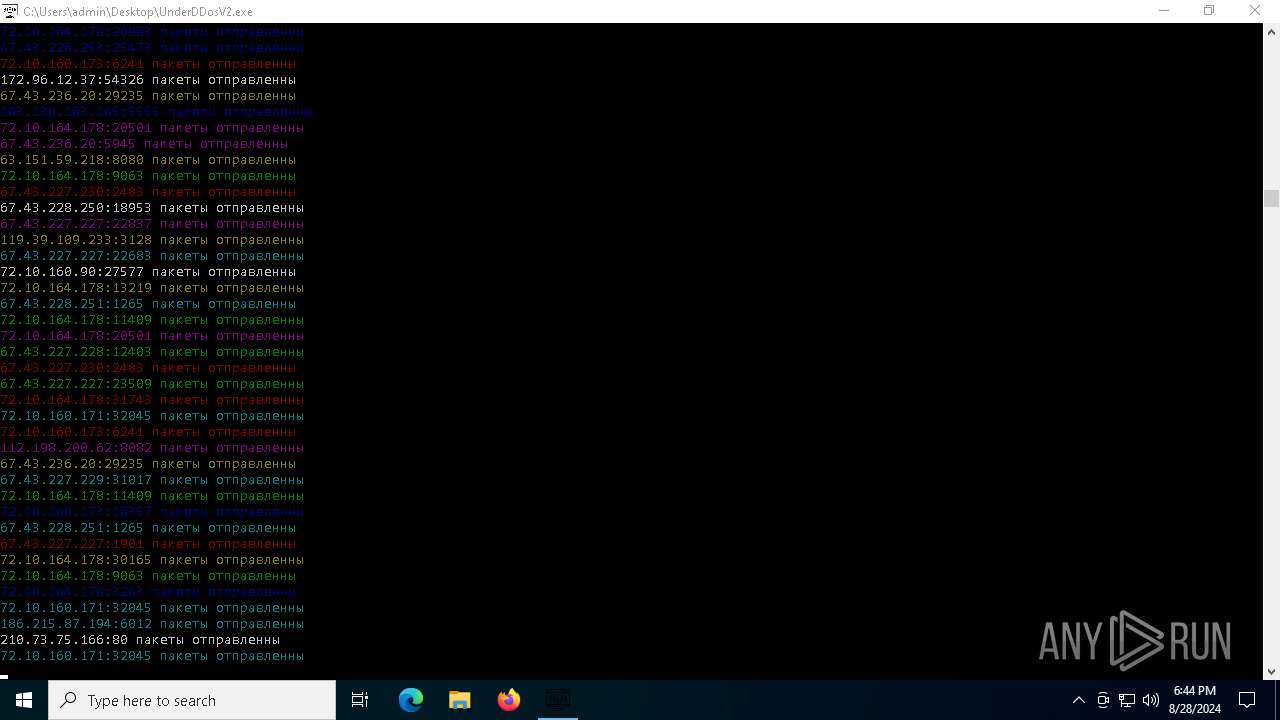
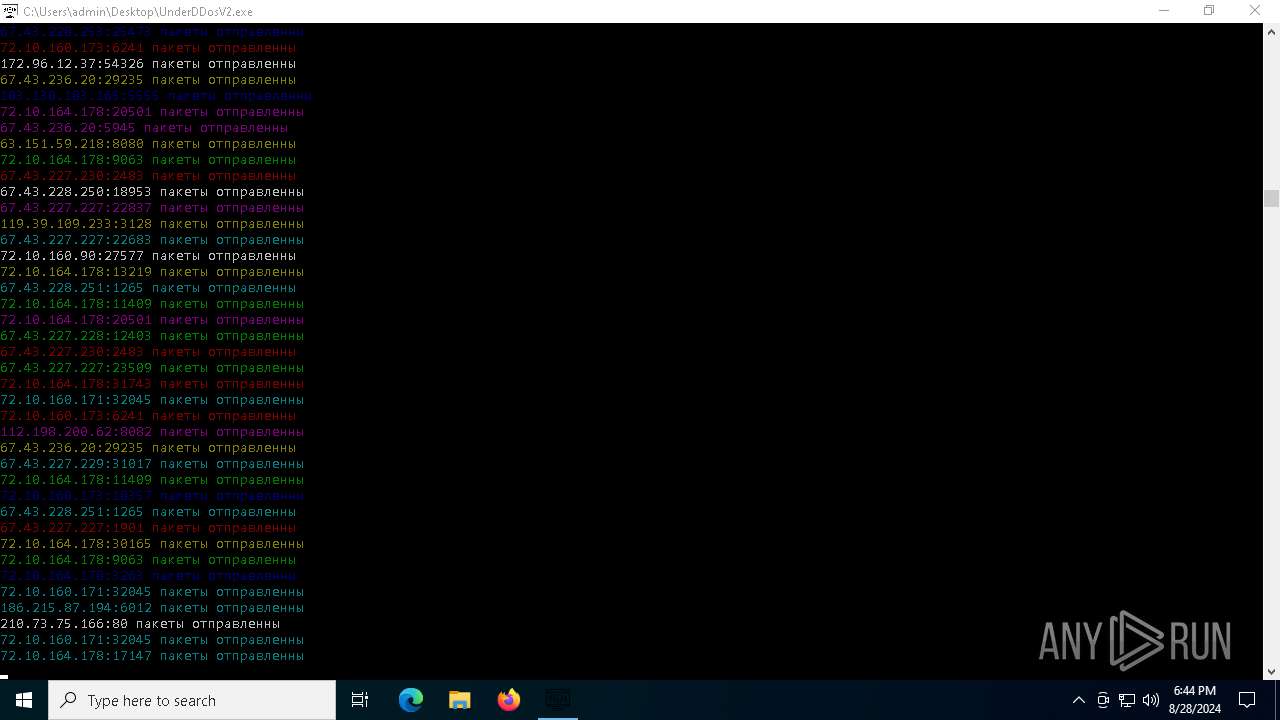
Connects to unusual port
- UnderDDosV2.exe (PID: 6684)
INFO
Reads the computer name
- UnderDDosV2.exe (PID: 964)
- UnderDDosV2.exe (PID: 6684)
Checks supported languages
- UnderDDosV2.exe (PID: 964)
- UnderDDosV2.exe (PID: 6684)
Create files in a temporary directory
- UnderDDosV2.exe (PID: 964)
PyInstaller has been detected (YARA)
- UnderDDosV2.exe (PID: 964)
- UnderDDosV2.exe (PID: 6684)
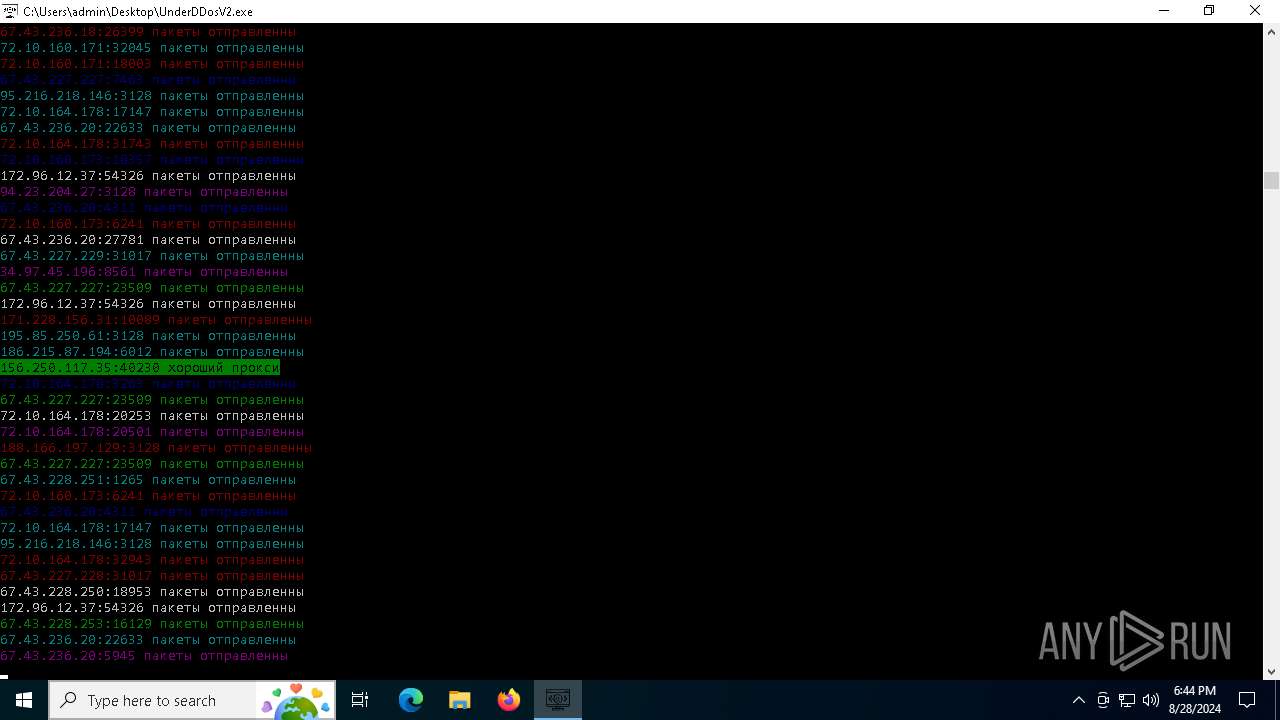
Checks proxy server information
- UnderDDosV2.exe (PID: 6684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:04:30 22:22:14+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.37 |
| CodeSize: | 172032 |
| InitializedDataSize: | 103424 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb7d0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
131
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | "C:\Users\admin\Desktop\UnderDDosV2.exe" | C:\Users\admin\Desktop\UnderDDosV2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | UnderDDosV2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UnderDDosV2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6536 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6684 | "C:\Users\admin\Desktop\UnderDDosV2.exe" | C:\Users\admin\Desktop\UnderDDosV2.exe | UnderDDosV2.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6876 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 42232 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
145 236
Read events
145 236
Write events
0
Delete events
0
Modification events
Executable files
17
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 964 | UnderDDosV2.exe | C:\Users\admin\AppData\Local\Temp\_MEI9642\_hashlib.pyd | executable | |
MD5:DE4D104EA13B70C093B07219D2EFF6CB | SHA256:39BC615842A176DB72D4E0558F3CDCAE23AB0623AD132F815D21DCFBFD4B110E | |||
| 964 | UnderDDosV2.exe | C:\Users\admin\AppData\Local\Temp\_MEI9642\_queue.pyd | executable | |
MD5:FF8300999335C939FCCE94F2E7F039C0 | SHA256:2F71046891BA279B00B70EB031FE90B379DBE84559CF49CE5D1297EA6BF47A78 | |||
| 964 | UnderDDosV2.exe | C:\Users\admin\AppData\Local\Temp\_MEI9642\_lzma.pyd | executable | |
MD5:337B0E65A856568778E25660F77BC80A | SHA256:613DE58E4A9A80EFF8F8BC45C350A6EAEBF89F85FFD2D7E3B0B266BF0888A60A | |||
| 964 | UnderDDosV2.exe | C:\Users\admin\AppData\Local\Temp\_MEI9642\_decimal.pyd | executable | |
MD5:D47E6ACF09EAD5774D5B471AB3AB96FF | SHA256:D0DF57988A74ACD50B2D261E8B5F2C25DA7B940EC2AAFBEE444C277552421E6E | |||
| 964 | UnderDDosV2.exe | C:\Users\admin\AppData\Local\Temp\_MEI9642\VCRUNTIME140.dll | executable | |
MD5:F12681A472B9DD04A812E16096514974 | SHA256:D66C3B47091CEB3F8D3CC165A43D285AE919211A0C0FCB74491EE574D8D464F8 | |||
| 964 | UnderDDosV2.exe | C:\Users\admin\AppData\Local\Temp\_MEI9642\_ssl.pyd | executable | |
MD5:069BCCC9F31F57616E88C92650589BDD | SHA256:CB42E8598E3FA53EEEBF63F2AF1730B9EC64614BDA276AB2CD1F1C196B3D7E32 | |||
| 964 | UnderDDosV2.exe | C:\Users\admin\AppData\Local\Temp\_MEI9642\_bz2.pyd | executable | |
MD5:4101128E19134A4733028CFAAFC2F3BB | SHA256:5843872D5E2B08F138A71FE9BA94813AFEE59C8B48166D4A8EB0F606107A7E80 | |||
| 964 | UnderDDosV2.exe | C:\Users\admin\AppData\Local\Temp\_MEI9642\select.pyd | executable | |
MD5:97EE623F1217A7B4B7DE5769B7B665D6 | SHA256:0046EB32F873CDE62CF29AF02687B1DD43154E9FD10E0AA3D8353D3DEBB38790 | |||
| 964 | UnderDDosV2.exe | C:\Users\admin\AppData\Local\Temp\_MEI9642\libcrypto-1_1.dll | executable | |
MD5:6F4B8EB45A965372156086201207C81F | SHA256:976CE72EFD0A8AEEB6E21AD441AA9138434314EA07F777432205947CDB149541 | |||
| 964 | UnderDDosV2.exe | C:\Users\admin\AppData\Local\Temp\_MEI9642\libssl-1_1.dll | executable | |
MD5:8769ADAFCA3A6FC6EF26F01FD31AFA84 | SHA256:2AEBB73530D21A2273692A5A3D57235B770DAF1C35F60C74E01754A5DAC05071 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15 229
TCP/UDP connections
29 697
DNS requests
27
Threats
328
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1764 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7088 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7088 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6684 | UnderDDosV2.exe | CONNECT | — | 188.40.59.208:3128 | http://188.40.59.208:3128myexternalip.com:443 | unknown | — | — | unknown |
6684 | UnderDDosV2.exe | CONNECT | — | 51.254.78.223:80 | http://51.254.78.223:80ipv4.icanhazip.com:443 | unknown | — | — | unknown |
6684 | UnderDDosV2.exe | CONNECT | 400 | 194.147.33.5:8080 | http://194.147.33.5:8080myexternalip.com:443 | unknown | — | — | unknown |
6684 | UnderDDosV2.exe | CONNECT | 400 | 185.105.88.63:4444 | http://185.105.88.63:4444myexternalip.com:443 | unknown | — | — | unknown |
6684 | UnderDDosV2.exe | CONNECT | 400 | 185.217.199.176:4444 | http://185.217.199.176:4444wtfismyip.com:443 | unknown | — | — | unknown |
6684 | UnderDDosV2.exe | CONNECT | — | 185.217.143.96:80 | http://185.217.143.96:80ipv4.icanhazip.com:443 | unknown | — | — | unknown |
6684 | UnderDDosV2.exe | CONNECT | — | 194.182.187.78:3128 | http://194.182.187.78:3128ipv4.icanhazip.com:443 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
6856 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1764 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1764 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7088 | SIHClient.exe | 13.85.23.86:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
ipv4.icanhazip.com |
| whitelisted |
api.proxyscrape.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO Public Proxy Service Domain in DNS Lookup (api .proxyscrape .com) |
6684 | UnderDDosV2.exe | Potentially Bad Traffic | ET INFO Observed Public Proxy Service Domain (api .proxyscrape .com in TLS SNI) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ifconfig .io) |
6684 | UnderDDosV2.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain (ifconfig .io) in TLS SNI |
6684 | UnderDDosV2.exe | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |
6684 | UnderDDosV2.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup - ipecho.net |
6684 | UnderDDosV2.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup - ipecho.net |
6684 | UnderDDosV2.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup - ipecho.net |
6684 | UnderDDosV2.exe | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |
35 ETPRO signatures available at the full report