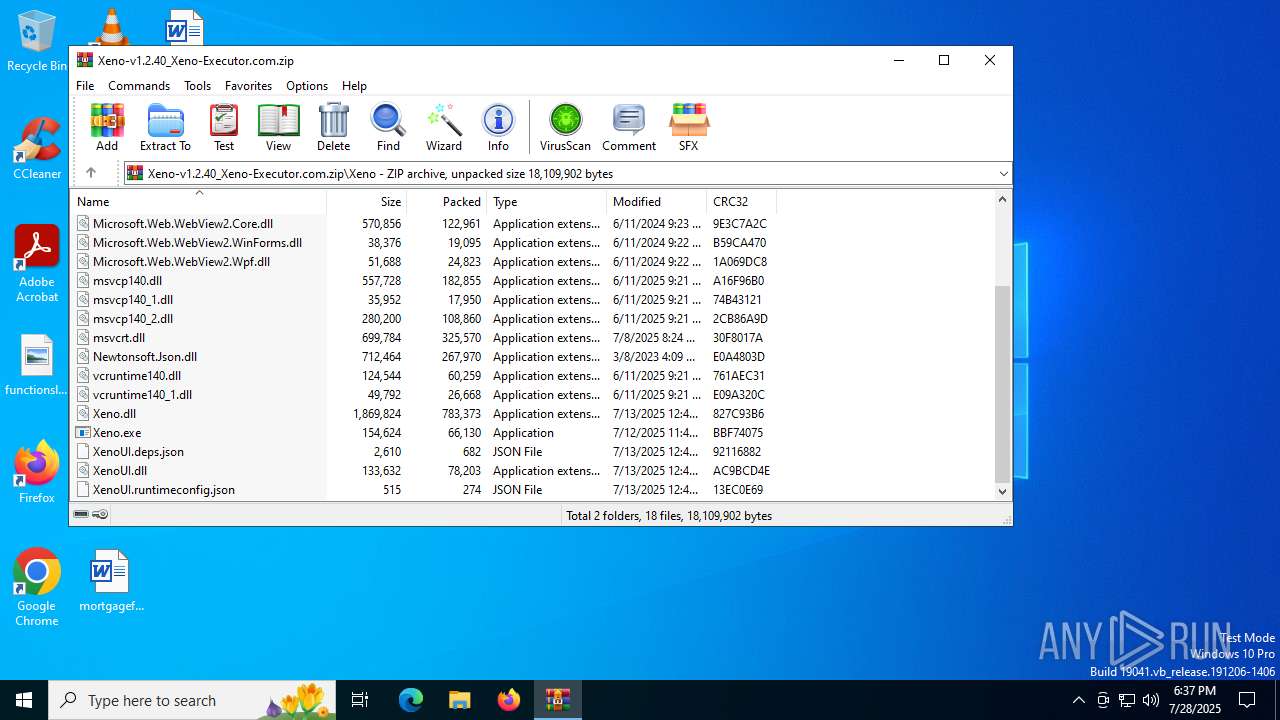
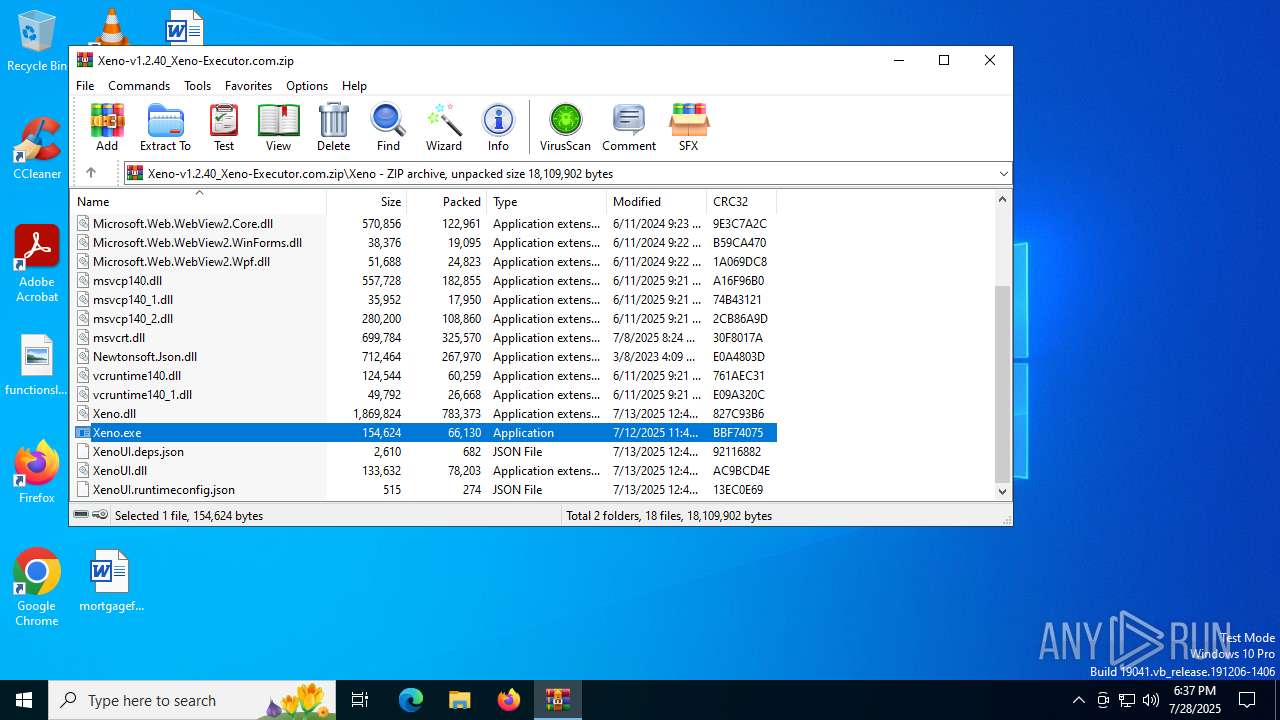
| File name: | Xeno-v1.2.40_Xeno-Executor.com.zip |
| Full analysis: | https://app.any.run/tasks/a047baea-12f1-4fb5-93f2-fffc825687d5 |
| Verdict: | Malicious activity |
| Analysis date: | July 28, 2025, 18:37:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 2F1D6B389BF04B49C0F7FD4273A827AC |
| SHA1: | 4B82622B3D805643DFFFFADCEE648EB6BEAB82CF |
| SHA256: | 92840F89185B62BA4ED58877BBC2AEBA50601DFA011AF56B3F3D5BCA856D2EE0 |
| SSDEEP: | 98304:Ge3QYFliTnX4eK0lJBSJc0uULODXKetT283FMZwyivrzga4RqNQccmTgaJons1yW:8QYSRei58oql |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6868)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6868)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6868)
The sample compiled with english language support
- WinRAR.exe (PID: 6868)
Checks supported languages
- Xeno.exe (PID: 640)
Reads the computer name
- Xeno.exe (PID: 640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:07:12 20:40:44 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Xeno/ |
Total processes
135
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\Xeno.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\Xeno.exe | WinRAR.exe | ||||||||||||
User: admin Company: XenoUI Integrity Level: MEDIUM Description: XenoUI Exit code: 2147516547 Version: 1.2.40 Modules
| |||||||||||||||
| 6868 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Xeno-v1.2.40_Xeno-Executor.com.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 107
Read events
2 099
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Xeno-v1.2.40_Xeno-Executor.com.zip | |||
| (PID) Process: | (6868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
19
Suspicious files
2
Text files
12
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\concrt140.dll | executable | |
MD5:5FE9A647921DED8A2FAD92DEB9EC4AB2 | SHA256:2405355F0A58067B258F8DF33C327E3A3D716EAAC5A3A5AEBB757842D85BD376 | |||
| 6868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\editor\vs\base\worker\workerMain.js | s | |
MD5:D0AC5294C58E523CDDF25BC6D785FA48 | SHA256:E90D1A8F116FA74431117A3AD78DDE16DDE060A4BF7528DFE3D5A3AD6156504B | |||
| 6868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\editor\vs\basic-languages\lua\lua.js | s | |
MD5:EEBDA1FDD970433750C115EAE2F03865 | SHA256:AC729EFB3164F48D6B08F74D4B15060C126A30D40FB4CD4FC9CC94F2E19BD7C7 | |||
| 6868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\editor\index.html | html | |
MD5:29BCAC034B9184CD9591FCE907FDE756 | SHA256:ABA8980039A05486FBD66FABCC4BA7858916CC89E6B50186BE777FD5E4B62A50 | |||
| 6868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\editor\vs\loader.js | s | |
MD5:BC15BB48D4D5C60CE7F16819F4D988C4 | SHA256:5C3CF09973404BA31D760952F267751EF2BB09F315331D13CA432B65CE2C480B | |||
| 6868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\editor\vs\editor\editor.main.nls.ru.js | text | |
MD5:6E7D5B984917B00F131C47473CE2B866 | SHA256:1BB069D95A395BF258D1F262814591AA762C4B30529ADDE32CCBCAA7C7CA508D | |||
| 6868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\libssl-3-x64.dll | executable | |
MD5:C9D3855AD553349D8B4AAC65325D25F9 | SHA256:A52992ADCDC61D06D45AC5D4E090F493C2AF33B34B014F7173FC8B1D5A46DBE5 | |||
| 6868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\editor\vs\editor\editor.main.nls.zh-tw.js | text | |
MD5:BECBF441D95B0BC1565FAF47CE9DE373 | SHA256:94A7FF81B8EC3217A46BC5CDEBE2C6AEE98F73E6E902B7D9CF394836D052BBE5 | |||
| 6868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\editor\vs\editor\editor.main.nls.es.js | text | |
MD5:36F546B28CA17ECE9F8EB9BCF8344E13 | SHA256:327437EE3793E9AE0686C78196B459592C282ED2E86F95CE28D32693B76D7654 | |||
| 6868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\editor\vs\editor\editor.main.nls.fr.js | text | |
MD5:1A29080733878DD44E0C118E84CD0C39 | SHA256:6ED837DC1905C06A20D102921FF06A0BDA003C5368ED0576BF7E69494E889AE8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
17
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6756 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2992 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6756 | svchost.exe | 40.126.31.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6756 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
Process | Message |
|---|---|
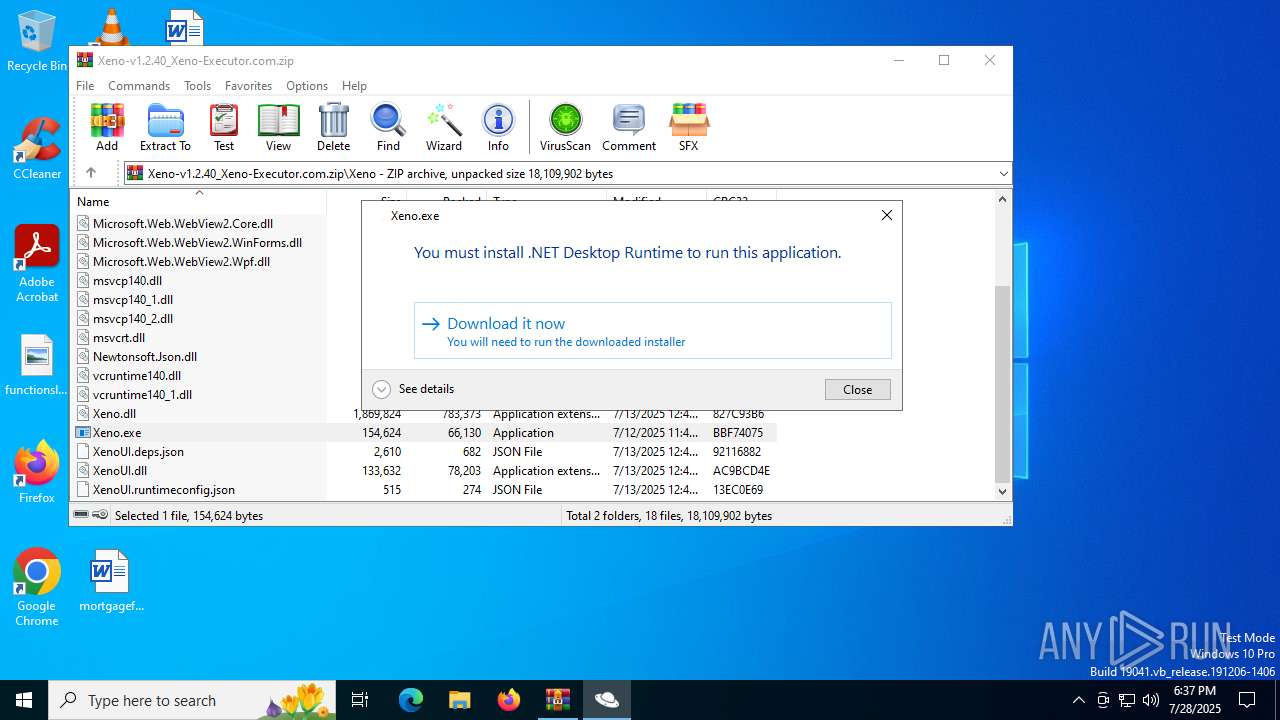
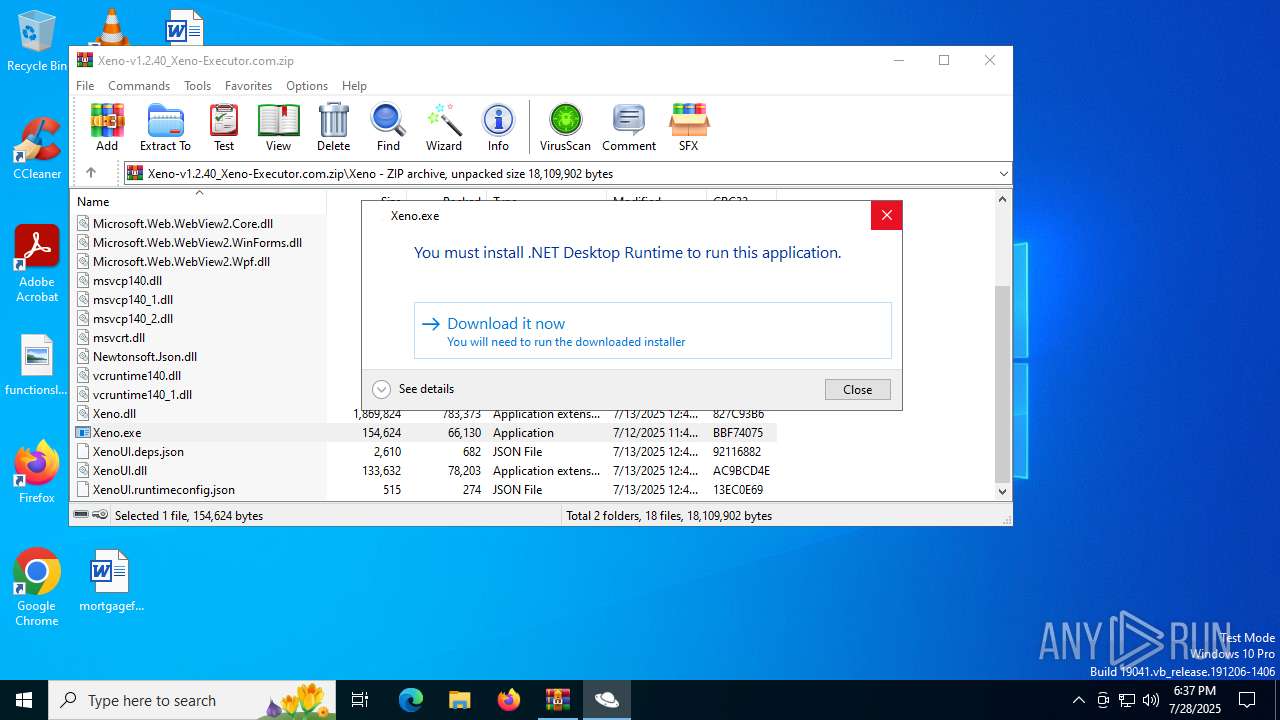
Xeno.exe | You must install .NET to run this application.
App: C:\Users\admin\AppData\Local\Temp\Rar$EXa6868.16610\Xeno\Xeno.exe
Architecture: x64
App host version: 8.0.18
.NET location: Not found
Learn more:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win-x64&os=win10&apphost_version=8.0.18 |