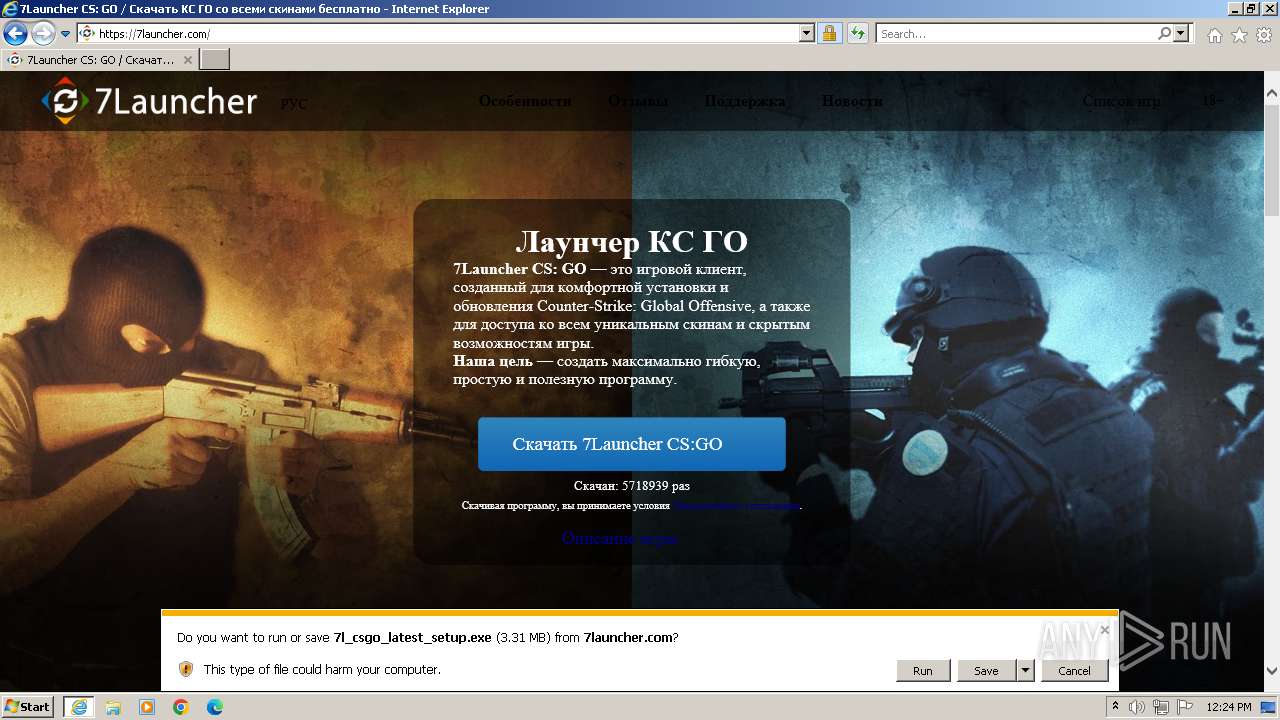
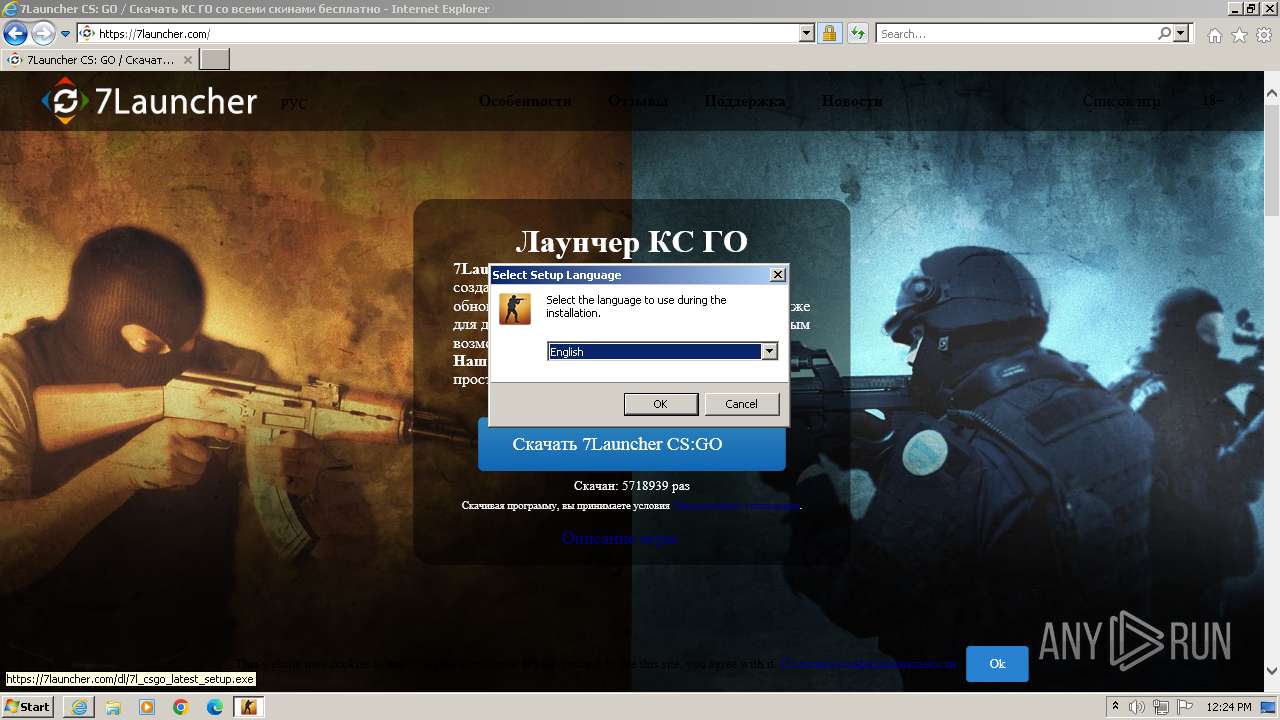
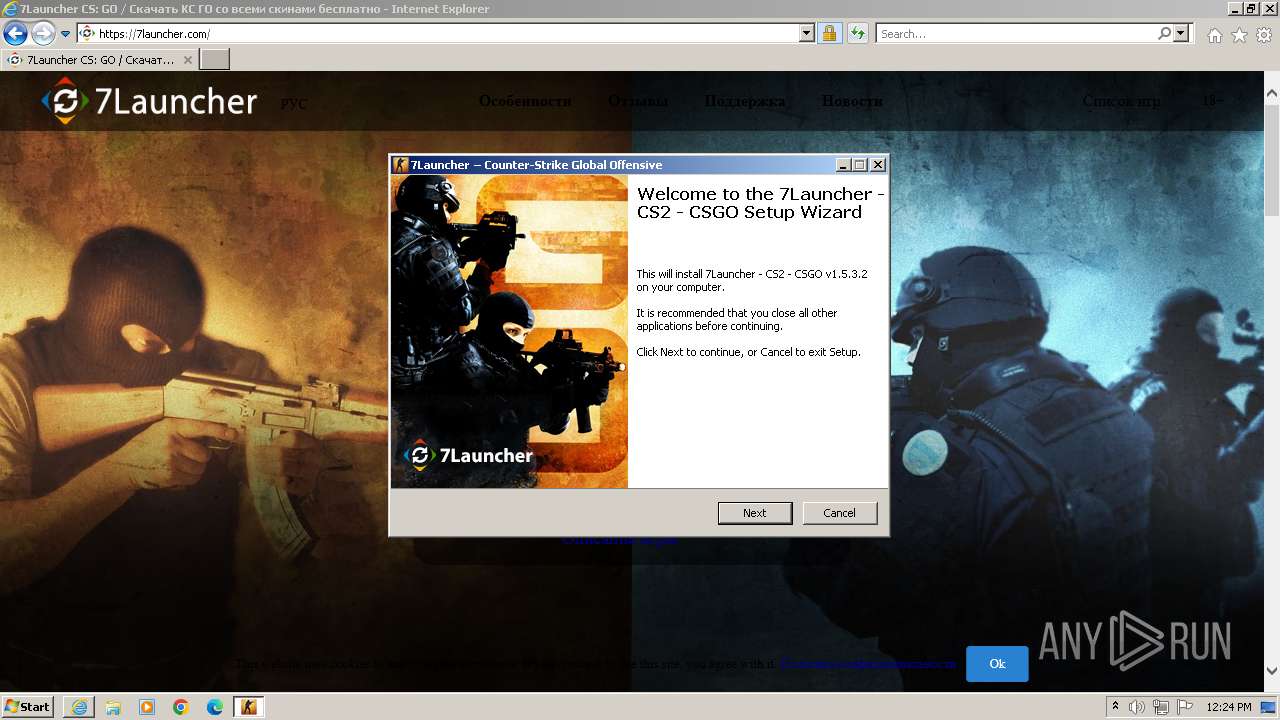
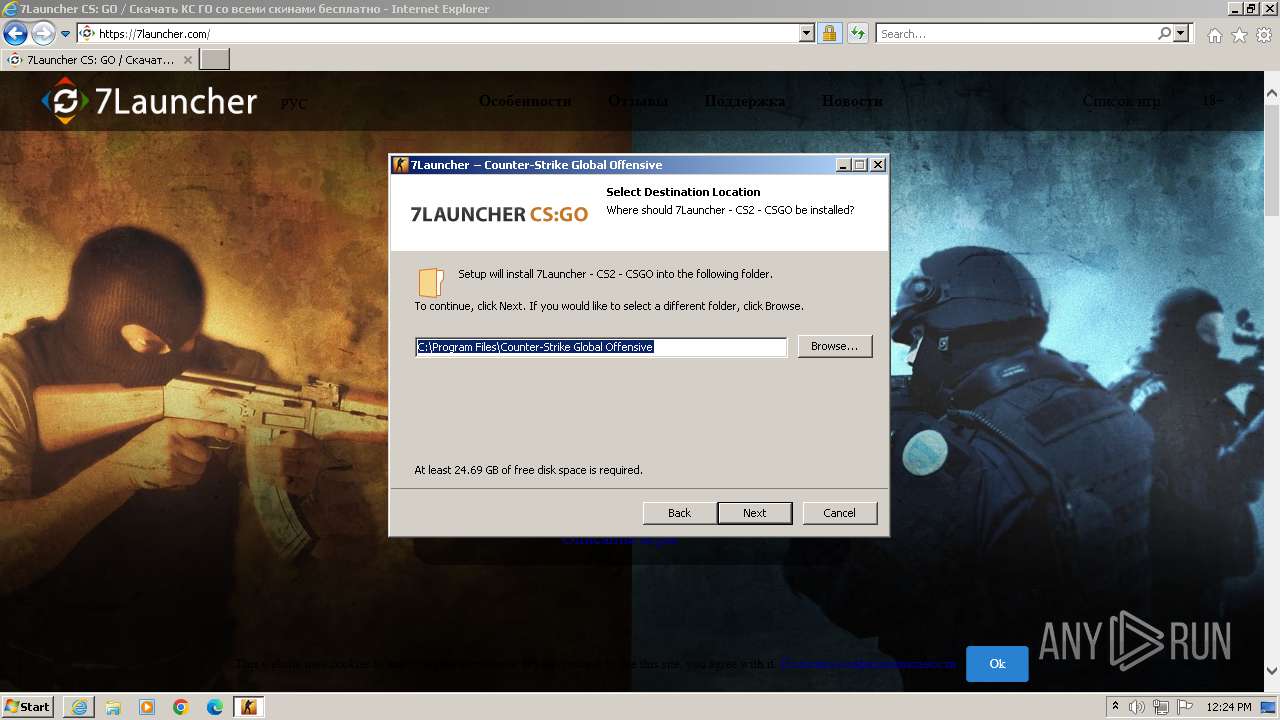
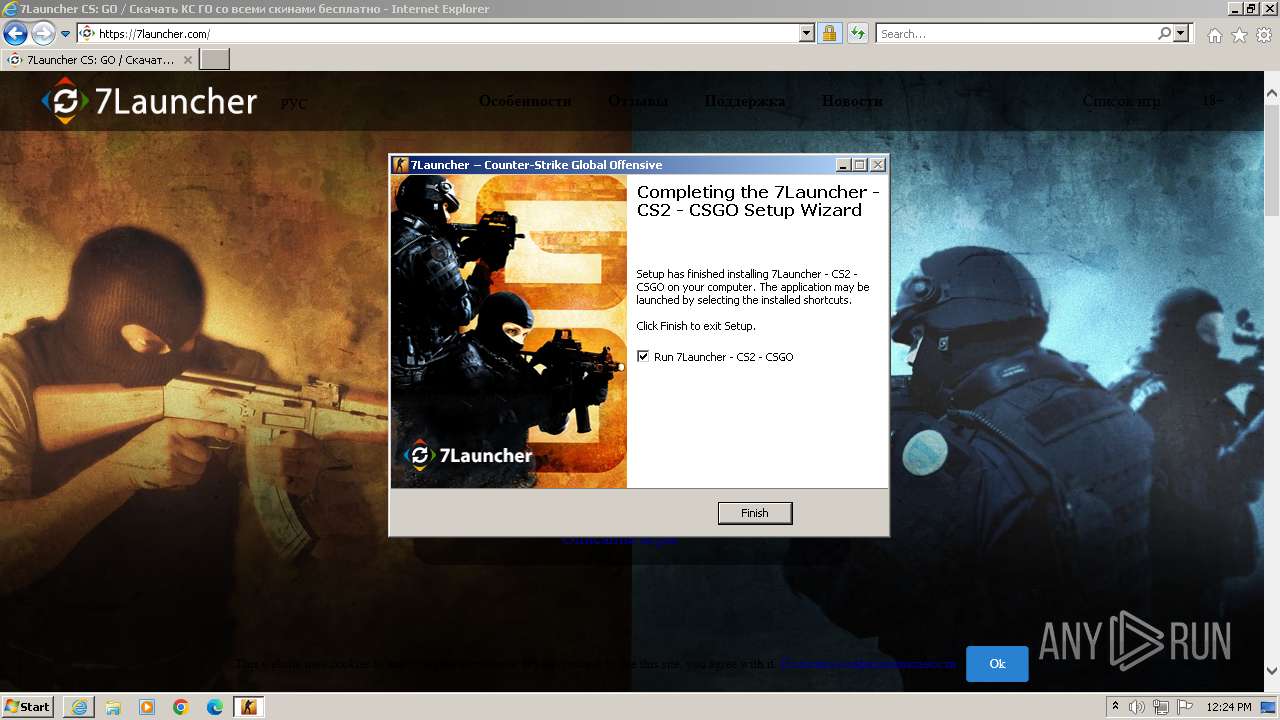
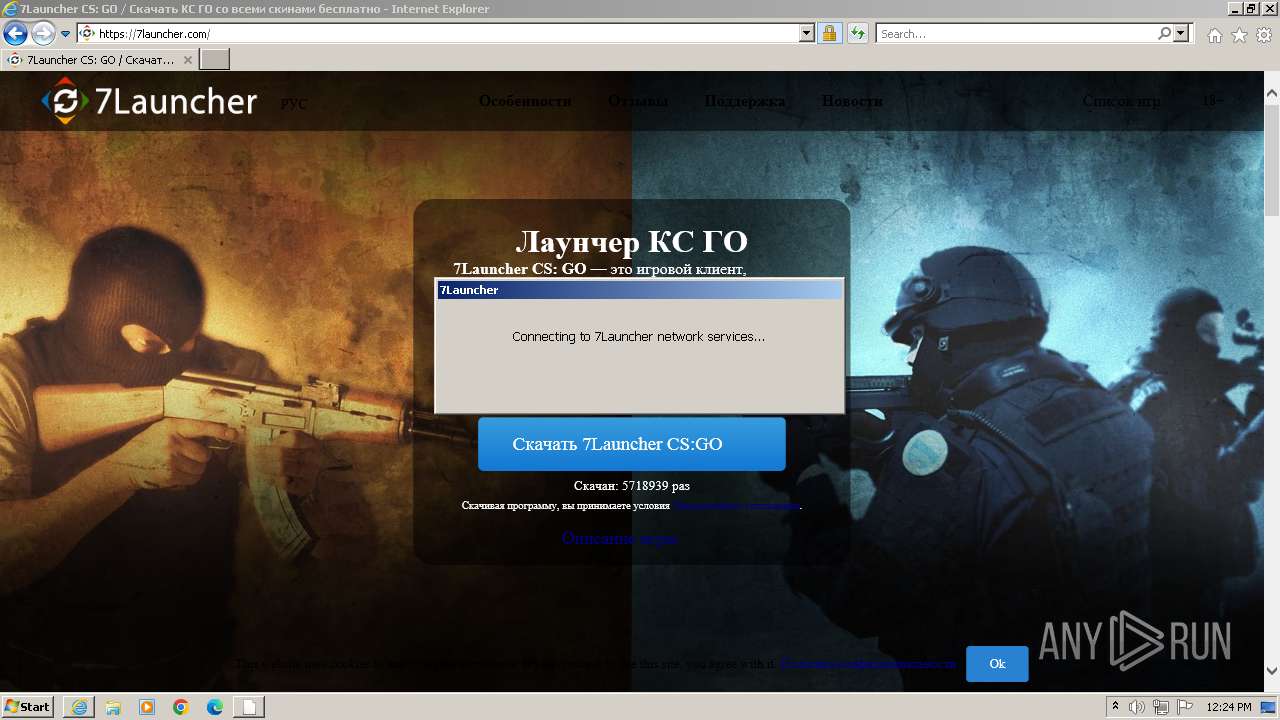
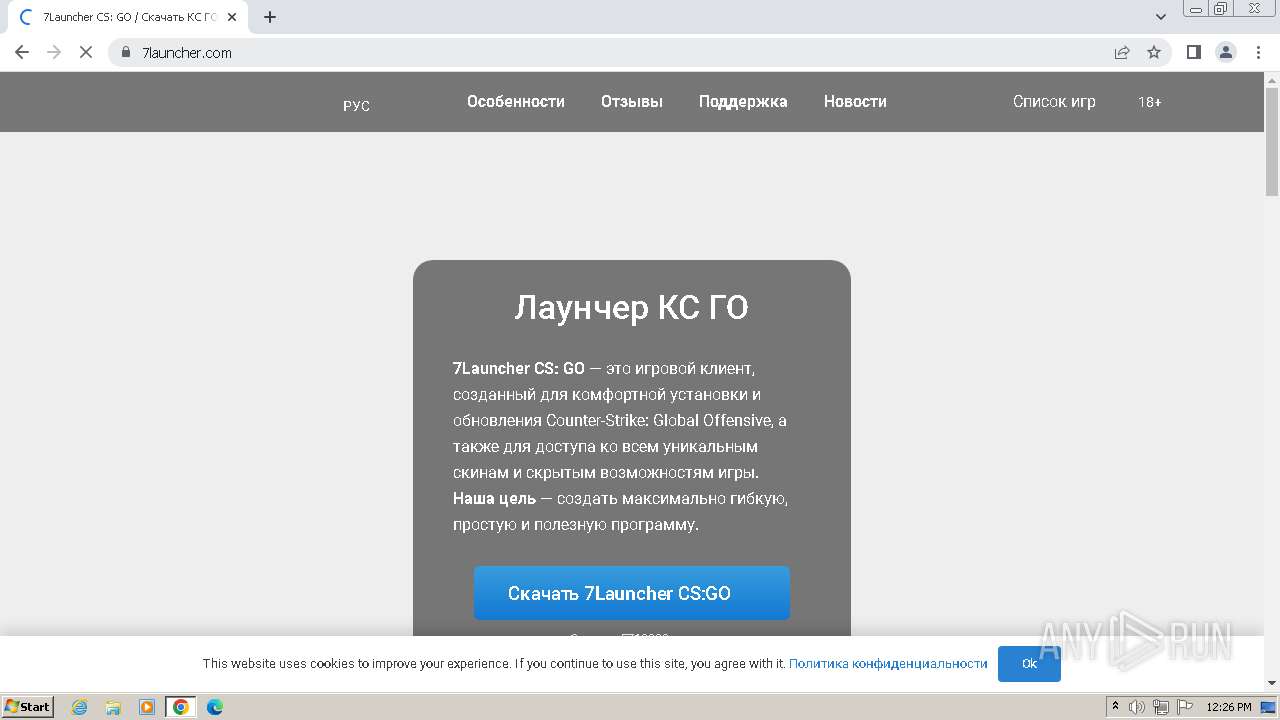
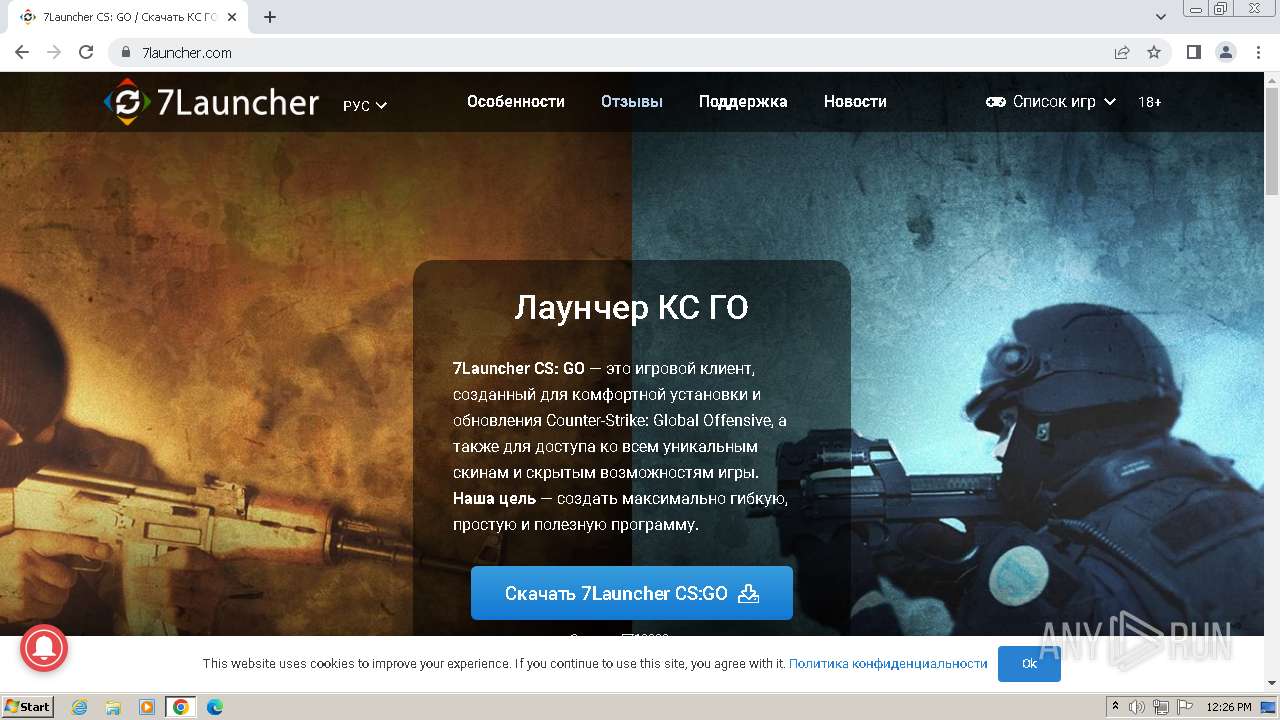
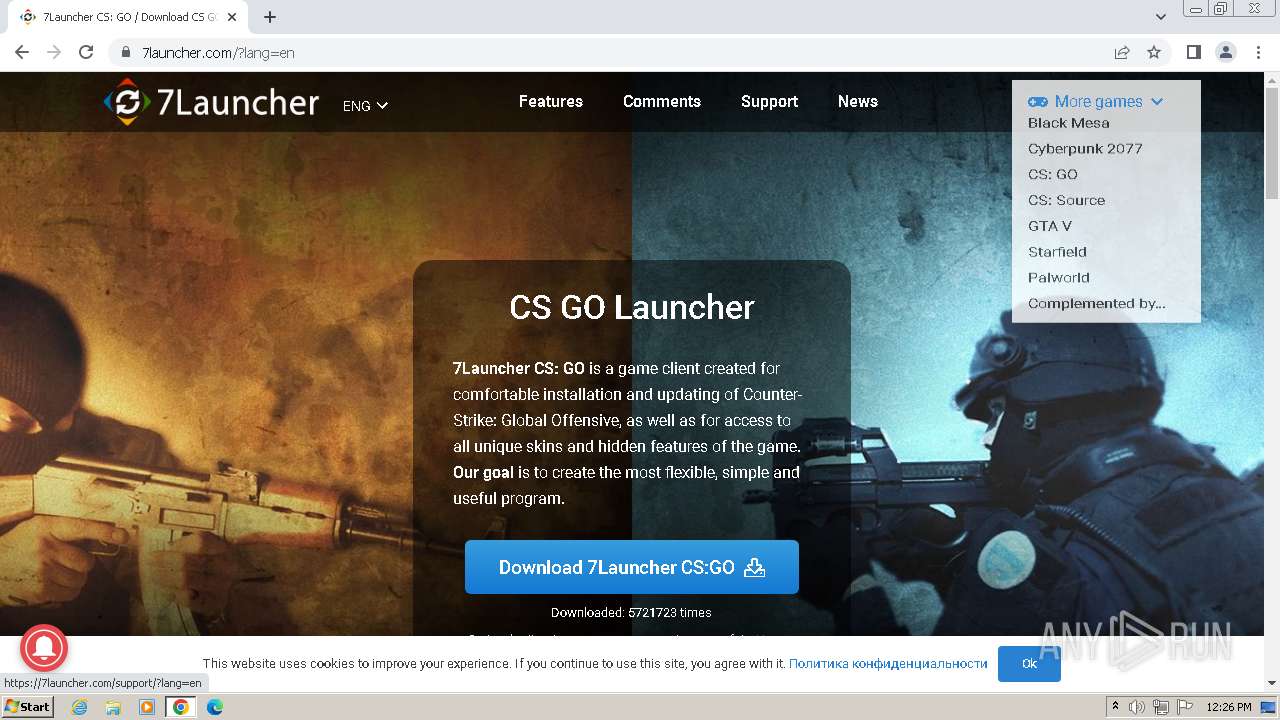
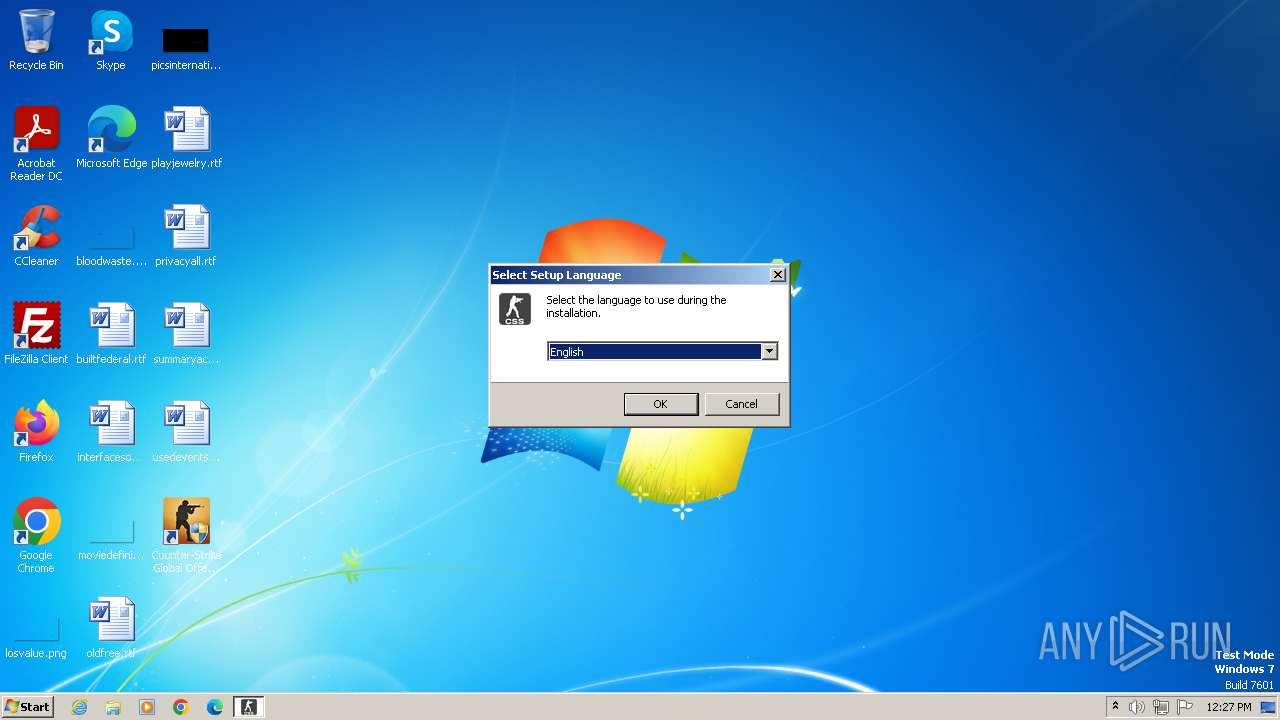
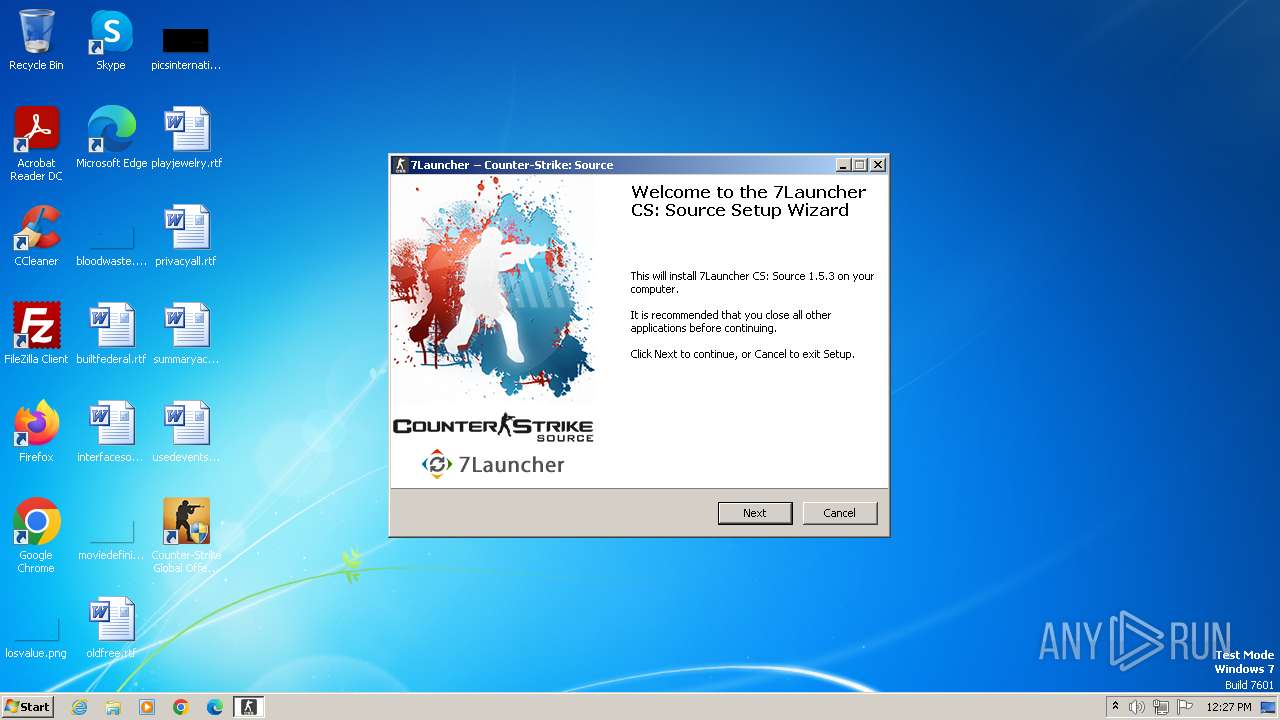
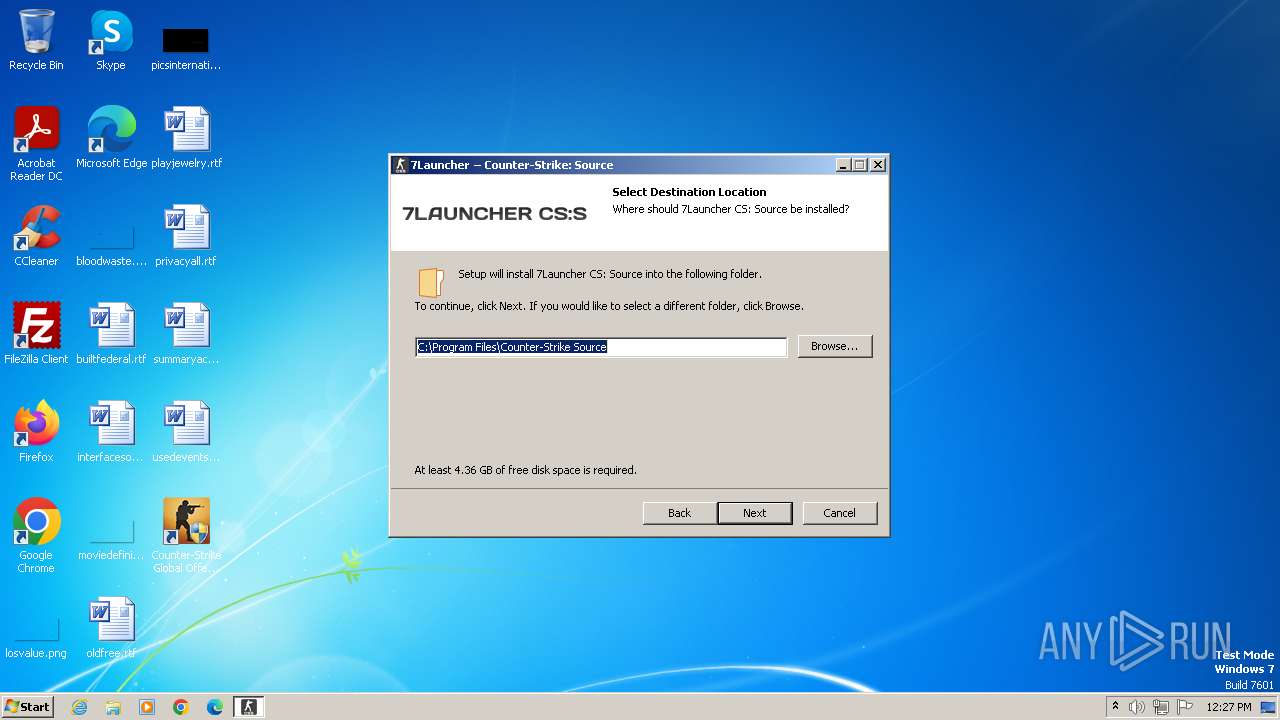
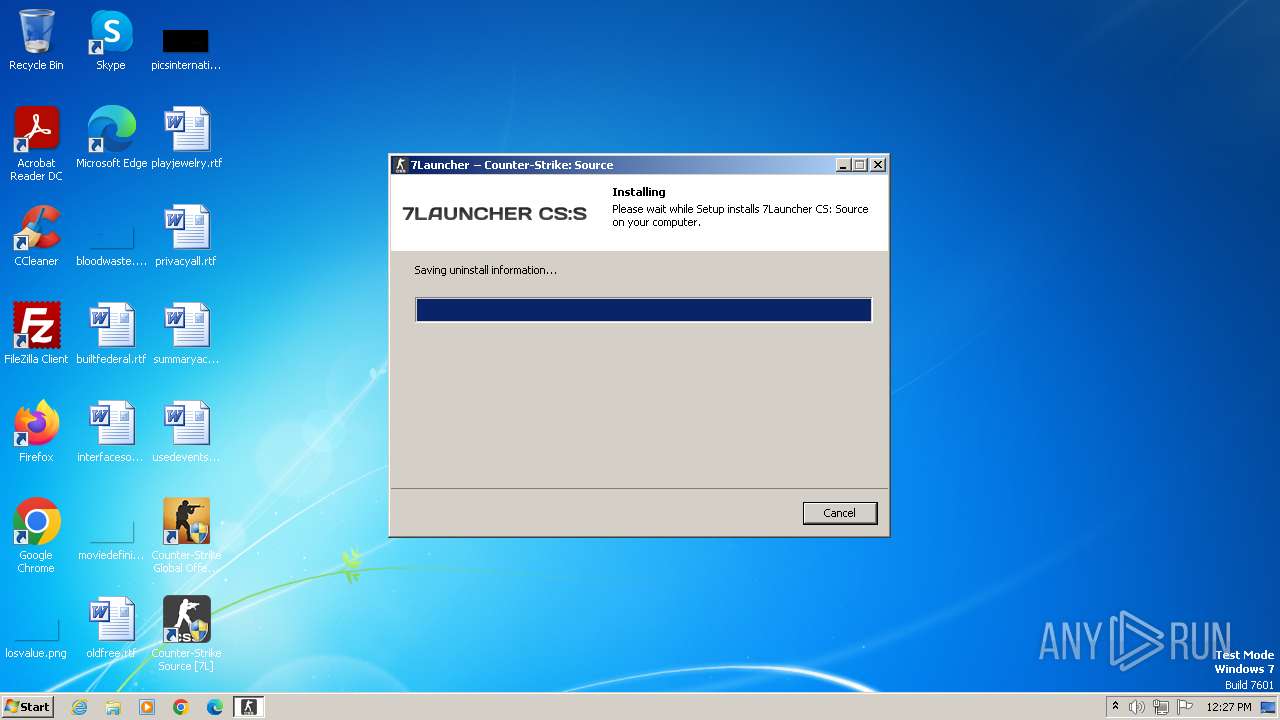
| URL: | https://7launcher.com/ù |
| Full analysis: | https://app.any.run/tasks/3fa451e7-92d7-47bd-8b13-990a06547026 |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2024, 11:24:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | BBAF8E454CB2593BD96CBD419C7AE164 |
| SHA1: | 89DB27F5CF9C19E5BA2FBFA5884F0FBB611F5FFD |
| SHA256: | 924BFDDB769E62CFC6D9023482670024BA67B41641CCA243A0F0D487C0B2D173 |
| SSDEEP: | 3:N80aAia:2Na |
MALICIOUS
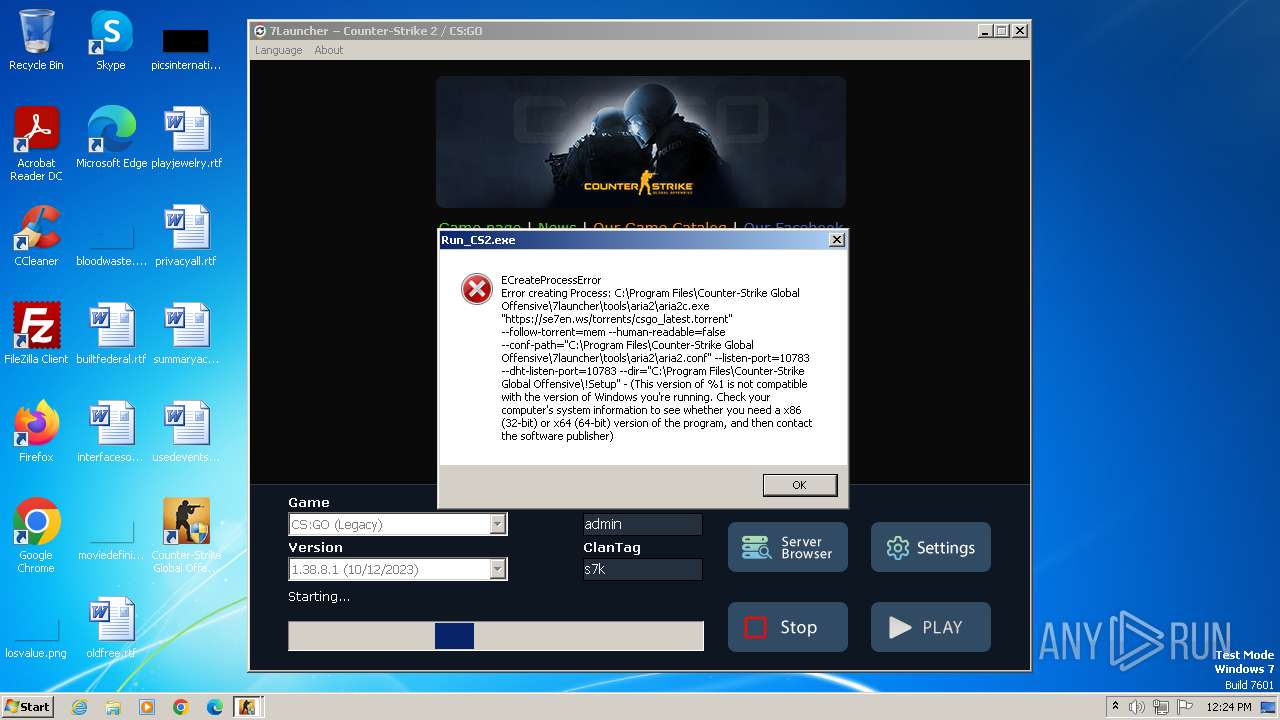
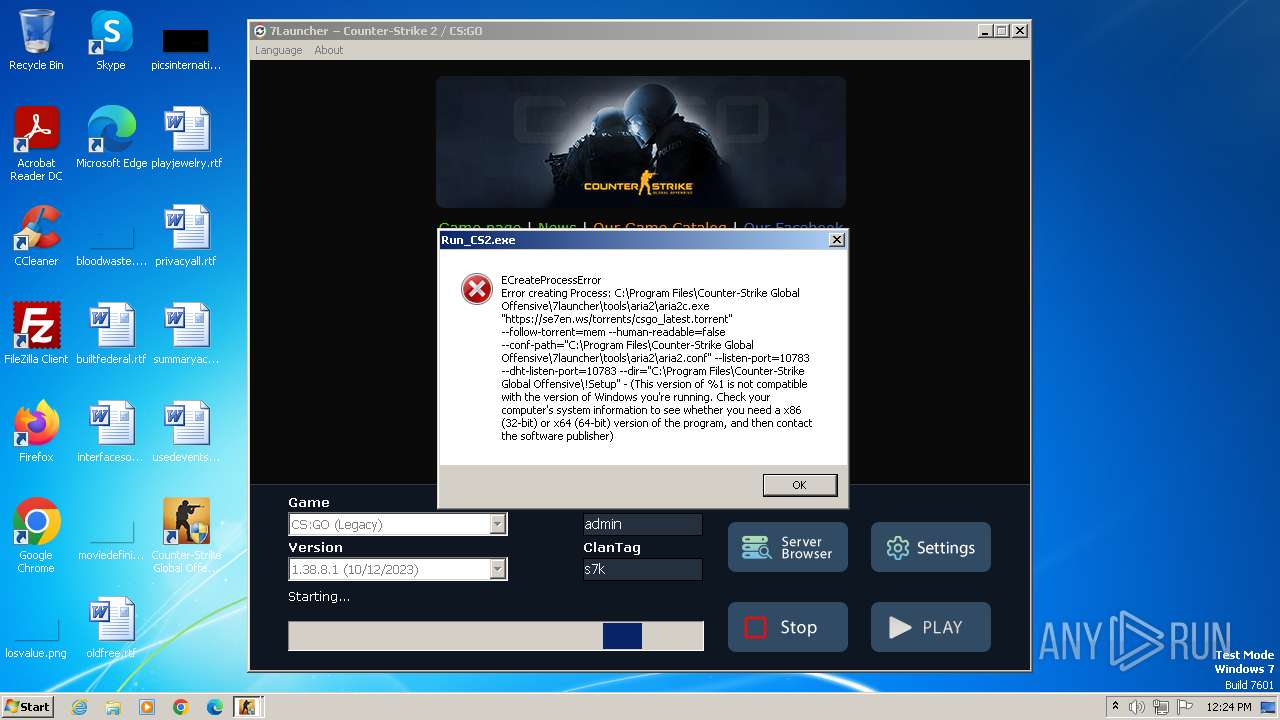
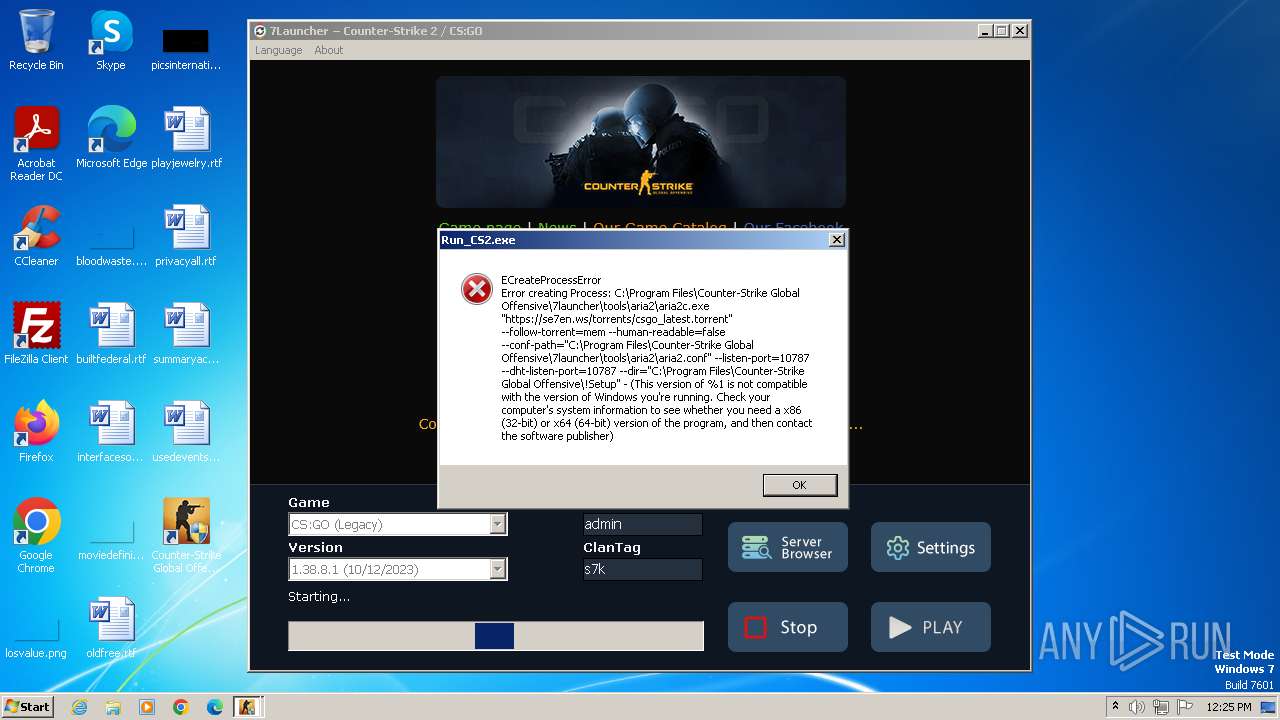
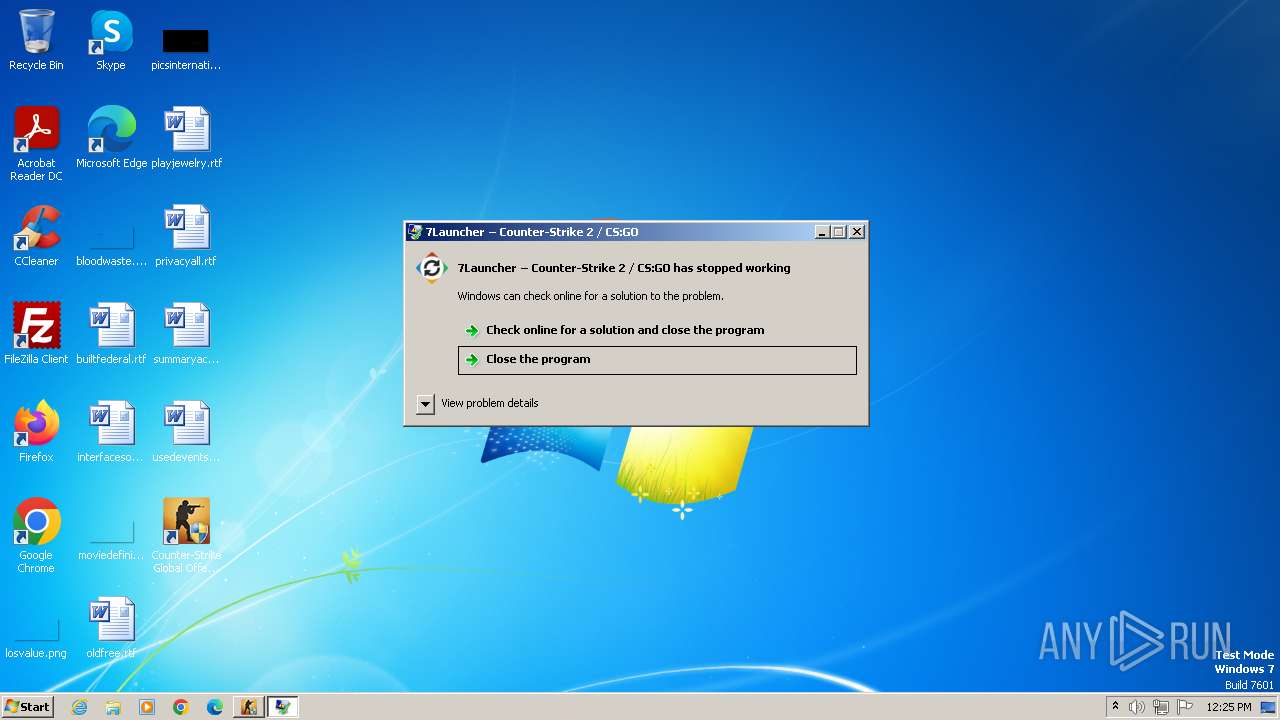
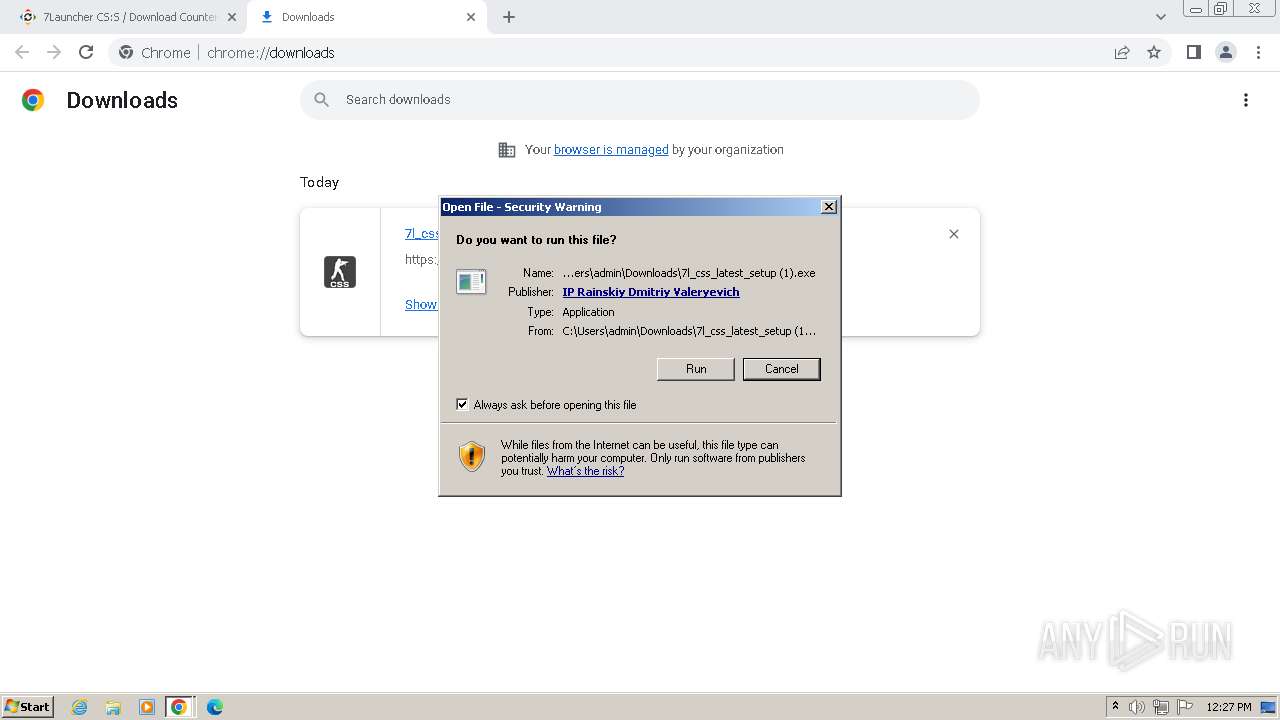
Drops the executable file immediately after the start
- 7l_csgo_latest_setup.tmp (PID: 1072)
- 7l_csgo_latest_setup.exe (PID: 1792)
- 7l_csgo_latest_setup.exe (PID: 1600)
- Run_CS2.exe (PID: 992)
- 7l_css_latest_setup (1).exe (PID: 3672)
- 7l_css_latest_setup (1).exe (PID: 3252)
- 7l_css_latest_setup (1).tmp (PID: 2652)
- Run_CSS.exe (PID: 2676)
SUSPICIOUS
Reads the Windows owner or organization settings
- 7l_csgo_latest_setup.tmp (PID: 1072)
- 7l_css_latest_setup (1).tmp (PID: 2652)
Executable content was dropped or overwritten
- 7l_csgo_latest_setup.exe (PID: 1792)
- 7l_csgo_latest_setup.exe (PID: 1600)
- 7l_csgo_latest_setup.tmp (PID: 1072)
- Run_CS2.exe (PID: 992)
- 7l_css_latest_setup (1).exe (PID: 3672)
- 7l_css_latest_setup (1).exe (PID: 3252)
- 7l_css_latest_setup (1).tmp (PID: 2652)
- Run_CSS.exe (PID: 2676)
Uses TASKKILL.EXE to kill process
- 7l_csgo_latest_setup.tmp (PID: 1072)
- 7l_css_latest_setup (1).tmp (PID: 2652)
Reads the Internet Settings
- 7l_csgo_latest_setup.tmp (PID: 1072)
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
- 7l_css_latest_setup (1).tmp (PID: 2652)
Reads security settings of Internet Explorer
- 7l_csgo_latest_setup.tmp (PID: 1072)
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
- 7l_css_latest_setup (1).tmp (PID: 2652)
Changes Internet Explorer settings (feature browser emulation)
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
Reads Internet Explorer settings
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
Checks Windows Trust Settings
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
Reads Microsoft Outlook installation path
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
Reads settings of System Certificates
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
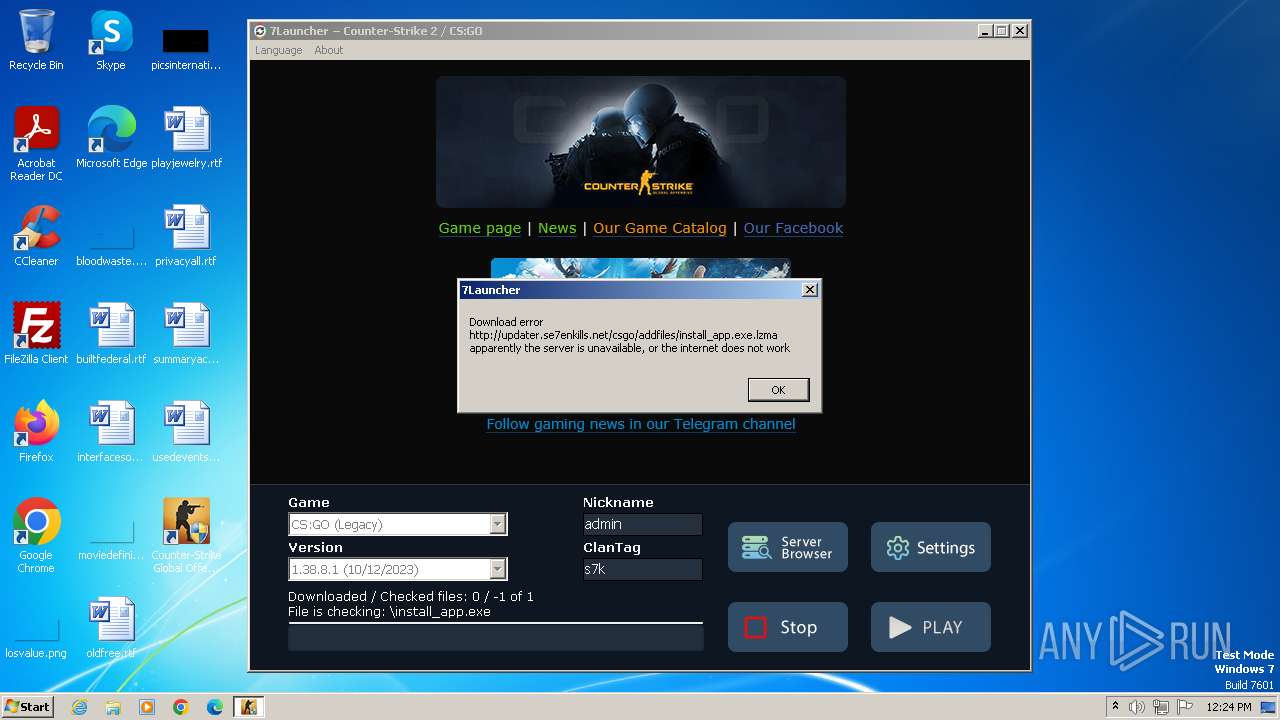
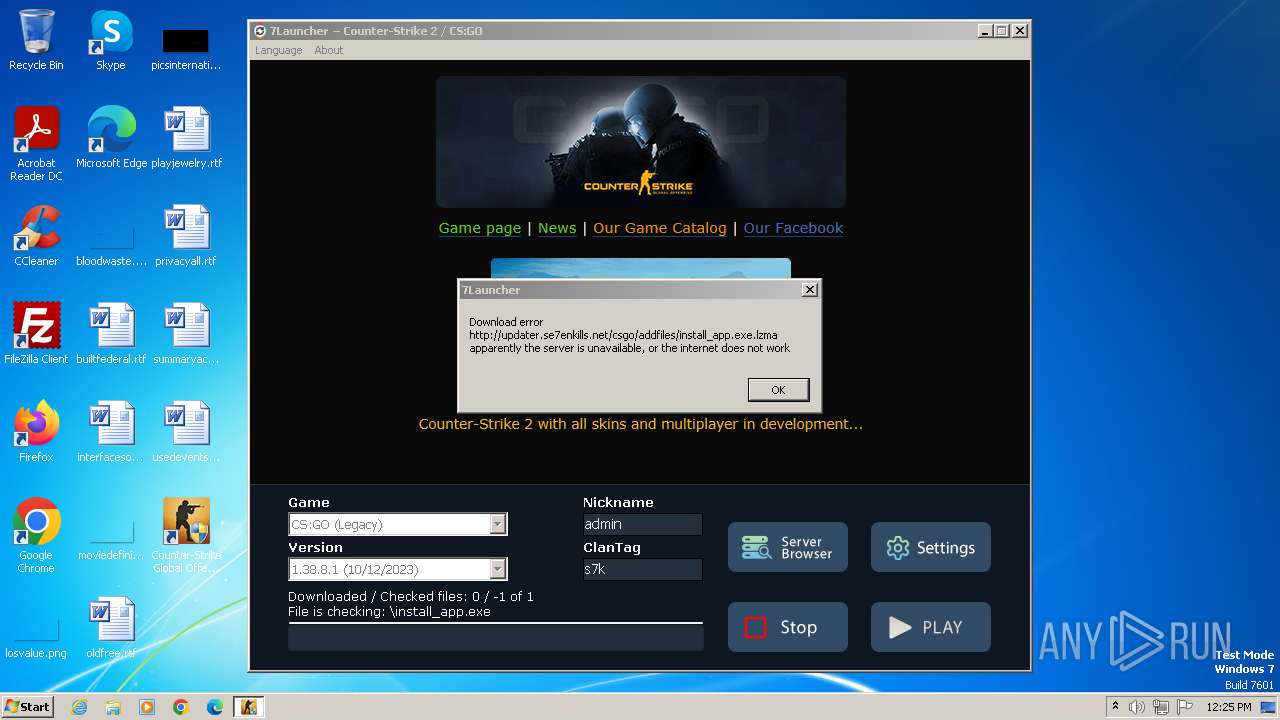
Process requests binary or script from the Internet
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
The process drops C-runtime libraries
- Run_CSS.exe (PID: 2676)
Process drops legitimate windows executable
- Run_CSS.exe (PID: 2676)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 1664)
- Run_CS2.exe (PID: 2816)
- Run_CS2.exe (PID: 2552)
- msedge.exe (PID: 3064)
- chrome.exe (PID: 2444)
Application launched itself
- iexplore.exe (PID: 3984)
- msedge.exe (PID: 3064)
- chrome.exe (PID: 2444)
Checks supported languages
- wmpnscfg.exe (PID: 1664)
- 7l_csgo_latest_setup.exe (PID: 1792)
- 7l_csgo_latest_setup.tmp (PID: 1072)
- 7l_csgo_latest_setup.tmp (PID: 1824)
- 7l_csgo_latest_setup.exe (PID: 1600)
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- 7l_css_latest_setup (1).exe (PID: 3672)
- 7l_css_latest_setup (1).tmp (PID: 3516)
- 7l_css_latest_setup (1).exe (PID: 3252)
- 7l_css_latest_setup (1).tmp (PID: 2652)
- Run_CSS.exe (PID: 2676)
Reads the computer name
- wmpnscfg.exe (PID: 1664)
- 7l_csgo_latest_setup.tmp (PID: 1072)
- 7l_csgo_latest_setup.tmp (PID: 1824)
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- 7l_css_latest_setup (1).tmp (PID: 3516)
- 7l_css_latest_setup (1).tmp (PID: 2652)
- Run_CSS.exe (PID: 2676)
Executable content was dropped or overwritten
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3984)
- msedge.exe (PID: 3064)
- msedge.exe (PID: 3800)
- chrome.exe (PID: 2792)
- chrome.exe (PID: 2444)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3984)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 4044)
- msedge.exe (PID: 3064)
- msedge.exe (PID: 3800)
- chrome.exe (PID: 2444)
- chrome.exe (PID: 2792)
The process uses the downloaded file
- iexplore.exe (PID: 3984)
- msedge.exe (PID: 1880)
- msedge.exe (PID: 3064)
- chrome.exe (PID: 1236)
- chrome.exe (PID: 2444)
Create files in a temporary directory
- 7l_csgo_latest_setup.exe (PID: 1792)
- 7l_csgo_latest_setup.exe (PID: 1600)
- 7l_csgo_latest_setup.tmp (PID: 1072)
- 7l_css_latest_setup (1).exe (PID: 3672)
- 7l_css_latest_setup (1).exe (PID: 3252)
- 7l_css_latest_setup (1).tmp (PID: 2652)
Creates a software uninstall entry
- 7l_csgo_latest_setup.tmp (PID: 1072)
- 7l_css_latest_setup (1).tmp (PID: 2652)
Creates files in the program directory
- 7l_csgo_latest_setup.tmp (PID: 1072)
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- 7l_css_latest_setup (1).tmp (PID: 2652)
- Run_CSS.exe (PID: 2676)
Checks proxy server information
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
Reads the machine GUID from the registry
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
Creates files or folders in the user directory
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
Process checks whether UAC notifications are on
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
Reads the software policy settings
- Run_CS2.exe (PID: 992)
- Run_CS2.exe (PID: 2552)
- Run_CSS.exe (PID: 2676)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
118
Monitored processes
60
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3372 --field-trial-handle=1180,i,11991966652288003493,7275090723871672432,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3764 --field-trial-handle=1180,i,11991966652288003493,7275090723871672432,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 820 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1264 --field-trial-handle=1336,i,8460594565974936894,3603802869971876336,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 956 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4376 --field-trial-handle=1336,i,8460594565974936894,3603802869971876336,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
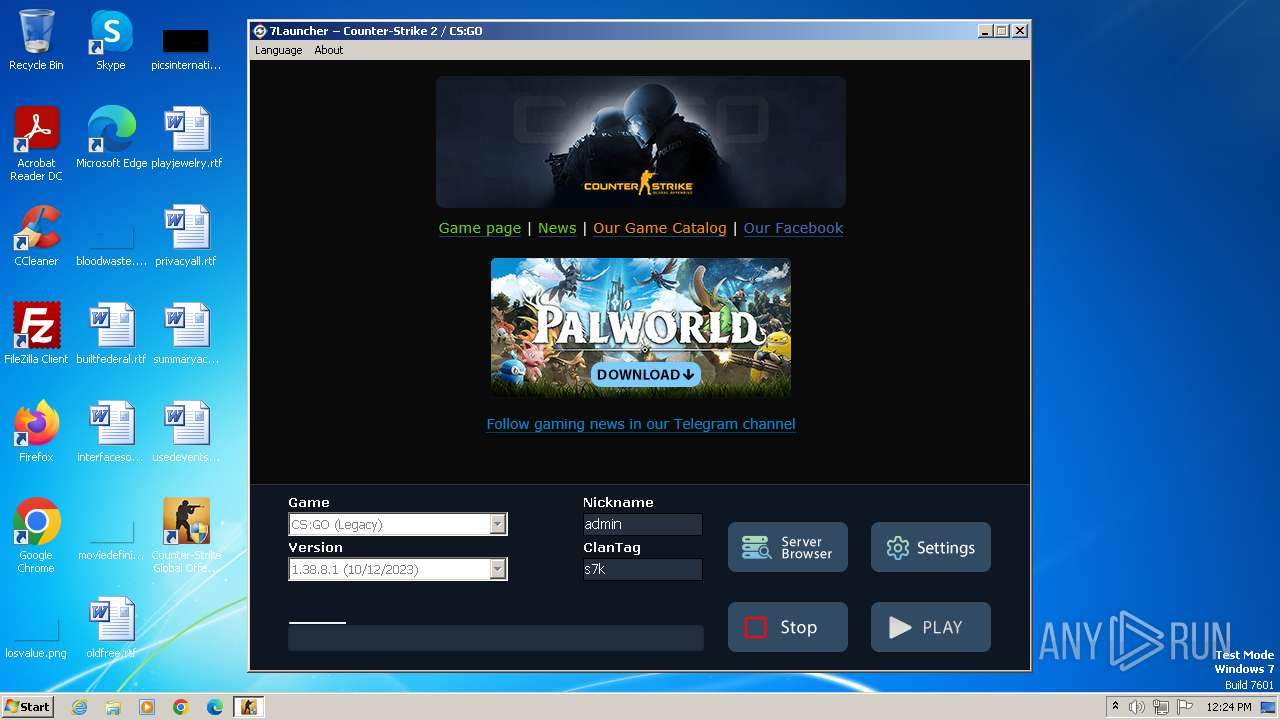
| 992 | "C:\Program Files\Counter-Strike Global Offensive\Run_CS2.exe" - installp2p /gnp 2 | C:\Program Files\Counter-Strike Global Offensive\Run_CS2.exe | 7l_csgo_latest_setup.tmp | ||||||||||||
User: admin Company: SE7EN Solutions Ltd. Integrity Level: HIGH Description: 7Launcher − Counter-Strike 2 / CS:GO Exit code: 0 Version: 1.5.3.2 Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --mojo-platform-channel-handle=4444 --field-trial-handle=1180,i,11991966652288003493,7275090723871672432,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
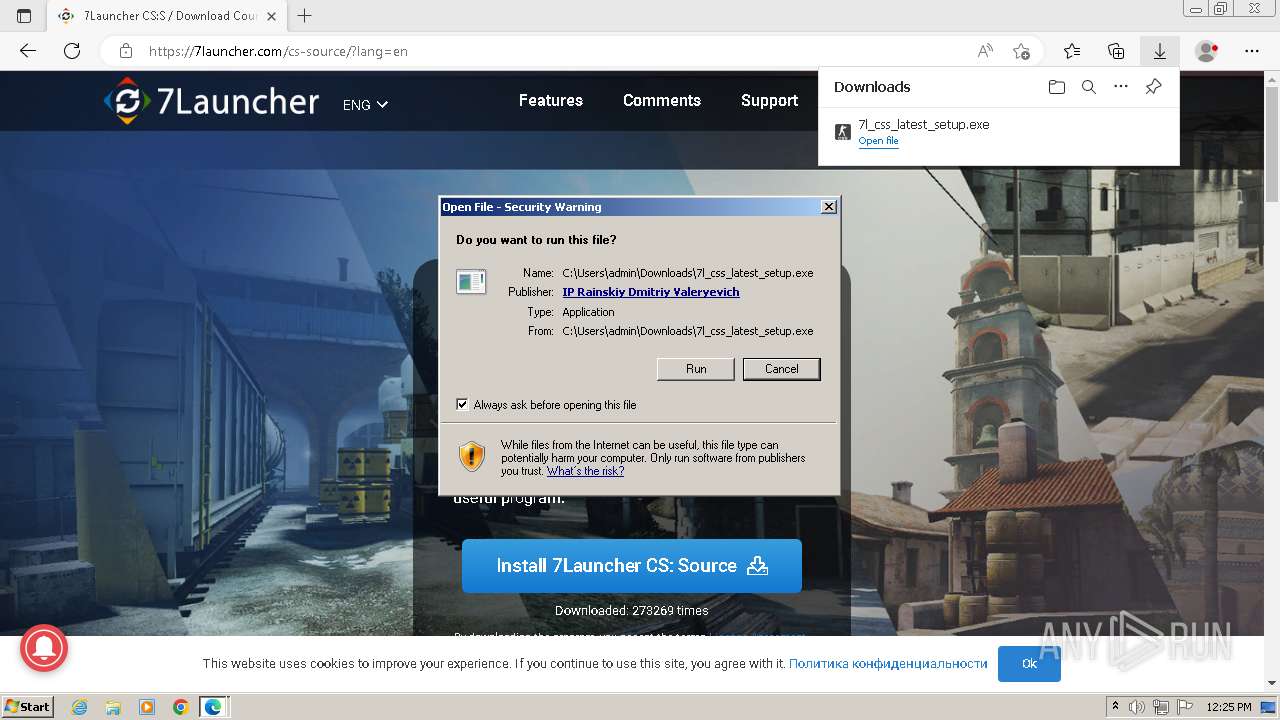
| 1072 | "C:\Users\admin\AppData\Local\Temp\is-FQT9A.tmp\7l_csgo_latest_setup.tmp" /SL5="$20216,2336354,928256,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\7l_csgo_latest_setup.exe" /SPAWNWND=$10214 /NOTIFYWND=$501BC | C:\Users\admin\AppData\Local\Temp\is-FQT9A.tmp\7l_csgo_latest_setup.tmp | 7l_csgo_latest_setup.exe | ||||||||||||
User: admin Company: SE7EN Solutions Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1212 | "taskkill.exe" /f /im "Run_CS2.exe" | C:\Windows\System32\taskkill.exe | — | 7l_csgo_latest_setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1212 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=2852 --field-trial-handle=1336,i,8460594565974936894,3603802869971876336,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4240 --field-trial-handle=1180,i,11991966652288003493,7275090723871672432,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
75 747
Read events
74 865
Write events
654
Delete events
228
Modification events
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31108556 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31108556 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
86
Suspicious files
701
Text files
290
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:7BB5A14437331AAD24915A3D8546FBC1 | SHA256:42397D9F3C8164D4CEF19FC169D7BCEA77A3EA7E9BCB8CFA7DB2FF0BBD3A7E00 | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:E234A1AAF7CA7CE6D21E901998C22E97 | SHA256:6A7336FED1E4B89E088C3F83757013E503BDA666401B9B6ED0A3F53419B1F138 | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:C699370C5242B1D55E02AC6EA670431A | SHA256:568A3CC1B0C19698B7DBD5C86E3785AD1D2F0D539E65C8A0AB4384E83A73D31C | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\7l-logo-w[1].png | image | |
MD5:A8EA1A61AA3B9B7B3B3CF535FAFE47AB | SHA256:A613A88BDB373C28F895F1E2F71FFECD03D42546867368BF9B8189EA52D075AB | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\7launcher.com[1].css | text | |
MD5:1C7F53770833625C39B7756D761AA635 | SHA256:5F2C033C9D9FAA0BCA26B9F7A71AFCD7135BBD5E9A4B1D52A5E89AAA98887A6A | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\index[1].js | binary | |
MD5:EFC27E253FAE1B7B891FB5A40E687768 | SHA256:46E36DD6CA93014E4915C723632BF180D27CC96CCFB7C26E69213E1A82129A62 | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\likely[1].css | text | |
MD5:83E7D74D8D40B4E2FF4ABB2D07C73688 | SHA256:C6A25510CB0ADD4261DA2F0D699BA89CFA3E63BB161E7FC54B844455408DB9A3 | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\likely[1].js | s | |
MD5:6DCDE1DDAB130142612F333D2DEB71F6 | SHA256:1303FB181796D506F24D52E844B0BA28FE83F28FAEC0A995C3DF8C9C0C2F7D1E | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:5226F41B436839CC358FF8481C0C0259 | SHA256:295790725A49D494B449D0A75886DD5C5DA339C9742319C30849D12B7859A96D | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\7l-logo-b[1].png | image | |
MD5:C5FEA832AE407A6347EDABD03B39D0CD | SHA256:72AD732511A305559C7F8EE2C79D766536E223AEF167E48364CD41D13E569C05 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
99
TCP/UDP connections
183
DNS requests
177
Threats
73
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4044 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?098b2ca3f74ef2d4 | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?aa27c982be707355 | unknown | — | — | unknown |
3984 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 301 | 104.26.0.175:80 | http://7launcher.com/ | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQD52znXgmjnXwogfY0LOz7q | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHUeP1PjGFkz6V8I7O6tApc%3D | unknown | — | — | unknown |
4044 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr5/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQiD0S5cIHyfrLTJ1fvAkJWflH%2B2QQUPeYpSJvqB8ohREom3m7e0oPQn1kCDQHuXyKVQkkF%2BQGRqNw%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4044 | iexplore.exe | 104.26.0.175:443 | 7launcher.com | CLOUDFLARENET | US | unknown |
4044 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
4044 | iexplore.exe | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
4044 | iexplore.exe | 142.250.186.40:443 | www.googletagmanager.com | GOOGLE | US | unknown |
4044 | iexplore.exe | 104.17.111.223:443 | cdn.onesignal.com | CLOUDFLARENET | — | unknown |
4044 | iexplore.exe | 95.213.129.125:443 | cackle.me | OOO Network of data-centers Selectel | RU | unknown |
4044 | iexplore.exe | 2.19.34.40:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
7launcher.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
cdn.onesignal.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
c.pki.goog |
| unknown |
o.pki.goog |
| unknown |
cackle.me |
| unknown |
x1.c.lencr.org |
| whitelisted |
mc.yandex.ru |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
2676 | Run_CSS.exe | A Network Trojan was detected | ET HUNTING SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
2676 | Run_CSS.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
2676 | Run_CSS.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
— | — | Misc activity | ET INFO HTTP Request to a *.pw domain |
— | — | Misc activity | ET INFO HTTP Request to a *.pw domain |
— | — | Misc activity | ET INFO HTTP Request to a *.pw domain |
— | — | Misc activity | ET INFO HTTP Request to a *.pw domain |
— | — | Misc activity | ET INFO HTTP Request to a *.pw domain |
— | — | Misc activity | ET INFO HTTP Request to a *.pw domain |