| File name: | 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN |
| Full analysis: | https://app.any.run/tasks/4f8fecb4-6c7f-45de-9ebf-216dc39a8dd2 |
| Verdict: | Malicious activity |
| Analysis date: | October 10, 2024, 23:06:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, MZ for MS-DOS |
| MD5: | 0DD7FB56520F5BA4ED467C16D416DD80 |
| SHA1: | AB305D62C49D0440F64BF7EDCE1941201D2DB307 |
| SHA256: | 924893A9785D94137E15BE048C8FCE7266B6BFA428325F5133CD93F83AFD6FAF |
| SSDEEP: | 768:Ep7XrhkSsV+mNr1zQm/ETFGX/+MIxtl6zNm7zAAkSsV+mNa7Xrs:qmr1zQ0ETgXIxtl6zo7zAtks |
MALICIOUS
DUCDUN has been detected (YARA)
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 6564)
SUSPICIOUS
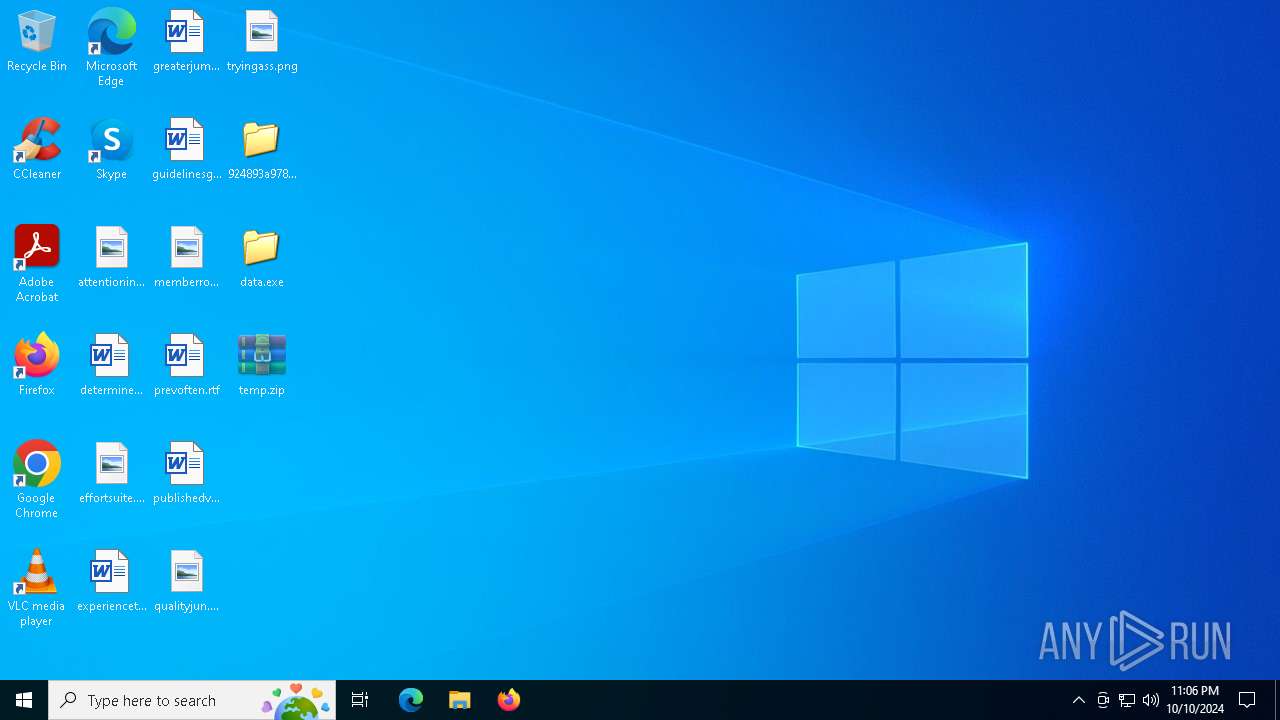
Creates file in the systems drive root
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 6564)
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 7080)
Executable content was dropped or overwritten
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 6564)
INFO
Checks supported languages
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 6564)
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 7080)
Create files in a temporary directory
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 6564)
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 7080)
Manual execution by a user
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 7080)
Reads the computer name
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 7080)
- 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe (PID: 6564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | DOS Executable Generic (100) |
|---|
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:01:06 03:42:02+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 45056 |
| InitializedDataSize: | 28672 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1134 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.54 |
| ProductVersionNumber: | 1.0.0.54 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Microsoft Windows |
| FileVersion: | 1.00.0054 |
| ProductVersion: | 1.00.0054 |
| InternalName: | musicvn |
| OriginalFileName: | musicvn.exe |
Total processes
127
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6564 | "C:\Users\admin\Desktop\924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe" | C:\Users\admin\Desktop\924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.00.0054 Modules
| |||||||||||||||
| 7080 | "C:\Users\admin\Desktop\924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe" | C:\Users\admin\Desktop\924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00.0054 Modules
| |||||||||||||||
Total events
376
Read events
372
Write events
2
Delete events
2
Modification events
| (PID) Process: | (6564) 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoFolderOptions |
Value: 1 | |||
| (PID) Process: | (6564) 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Streams |
| Operation: | delete value | Name: | Settings |
Value: | |||
| (PID) Process: | (7080) 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoFolderOptions |
Value: 1 | |||
| (PID) Process: | (7080) 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Streams |
| Operation: | delete value | Name: | Settings |
Value: | |||
Executable files
1
Suspicious files
8
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7080 | 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | C:\Users\admin\AppData\Local\Temp\~DF5081C3D658C71D0F.TMP | binary | |
MD5:A516D7C727297CE9D2B28D63C2E2E328 | SHA256:0EE8AA331EAB518E91024DF87474DFD4E7D899AC0810158AB837820FD1060FBF | |||
| 6564 | 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | C:\Users\admin\Desktop\924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.zip | binary | |
MD5:2AA9EDF2B200733A7751B09AFEDA4854 | SHA256:18190AB8832BA520A964F6875CE8C40C88B4B198DBE572FD7E5161FCF0C3BA04 | |||
| 7080 | 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | C:\Users\admin\Desktop\924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.dat | binary | |
MD5:F9575614387B2862D4E678197B9A7226 | SHA256:D50D12D8BC3D004DB64660548B9562D0EAFA8EF37892D8FFB5C042C5AB9ED98F | |||
| 6564 | 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | C:\Users\admin\AppData\Local\Temp\3La06256 | compressed | |
MD5:54F352AE372F0441C6235BFF271083C0 | SHA256:BA437DF22B38199BB3486AE7CEF014DAEFF0BD225CE059B8C165070A04DD51C1 | |||
| 6564 | 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | C:\Users\admin\Desktop\temp.zip~RF8b5eb.TMP | compressed | |
MD5:76CDB2BAD9582D23C1F6F4D868218D6C | SHA256:8739C76E681F900923B900C9DF0EF75CF421D39CABB54650C4B9AD19B6A76D85 | |||
| 6564 | 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | C:\Users\admin\Desktop\924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.dat | binary | |
MD5:95C9137098A6920D4E785C4AEF07825D | SHA256:2A6C1E8C14CD84B0CD45B308693908E3CAA1729748B521868D60FEB9224C1A88 | |||
| 6564 | 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | C:\Users\admin\Desktop\data.exe | executable | |
MD5:E7DEC613B845387A0C1FE12B2D9F85EF | SHA256:8F799F26F9CBCB8CF52E57755C088ACAECB072737B0E740B058BCCBF8675F059 | |||
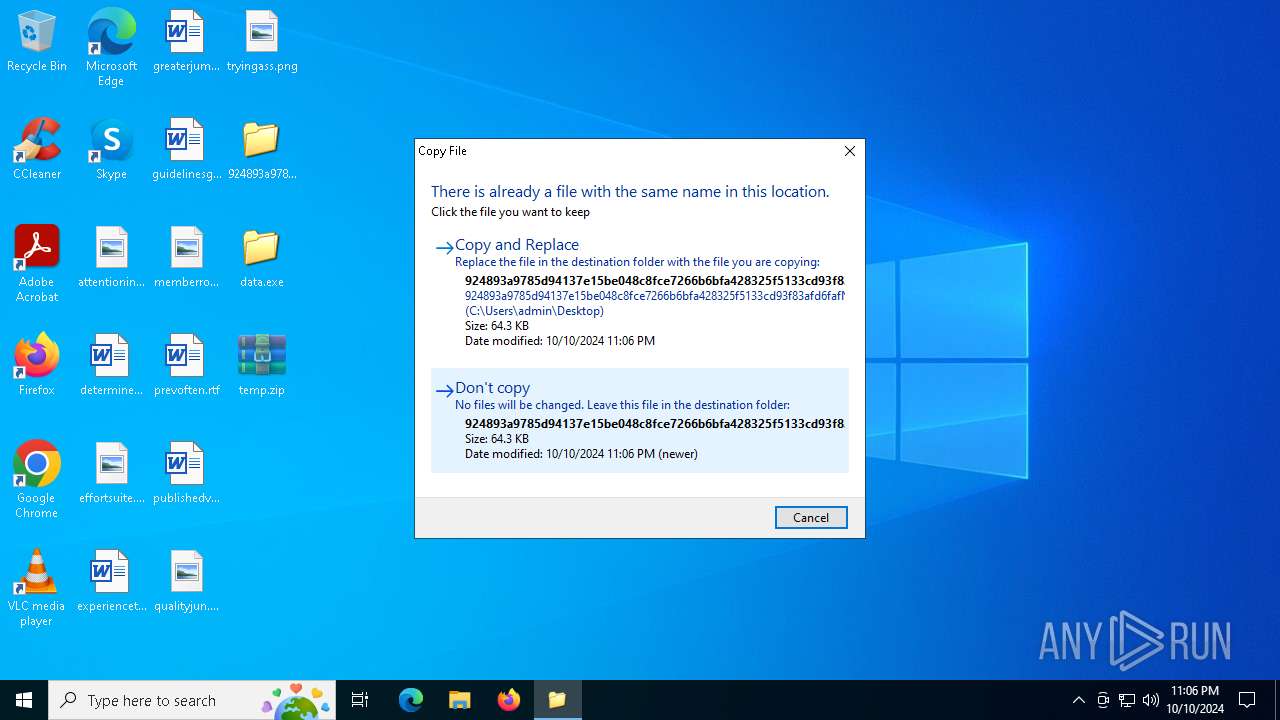
| 6564 | 924893a9785d94137e15be048c8fce7266b6bfa428325f5133cd93f83afd6fafN.exe | C:\Users\admin\Desktop\temp.zip | compressed | |
MD5:76CDB2BAD9582D23C1F6F4D868218D6C | SHA256:8739C76E681F900923B900C9DF0EF75CF421D39CABB54650C4B9AD19B6A76D85 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
27
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1764 | RUXIMICS.exe | GET | 200 | 2.21.20.133:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.21.20.133:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1764 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.21.20.133:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1764 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1764 | RUXIMICS.exe | 2.21.20.133:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.21.20.133:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 2.21.20.133:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1764 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |