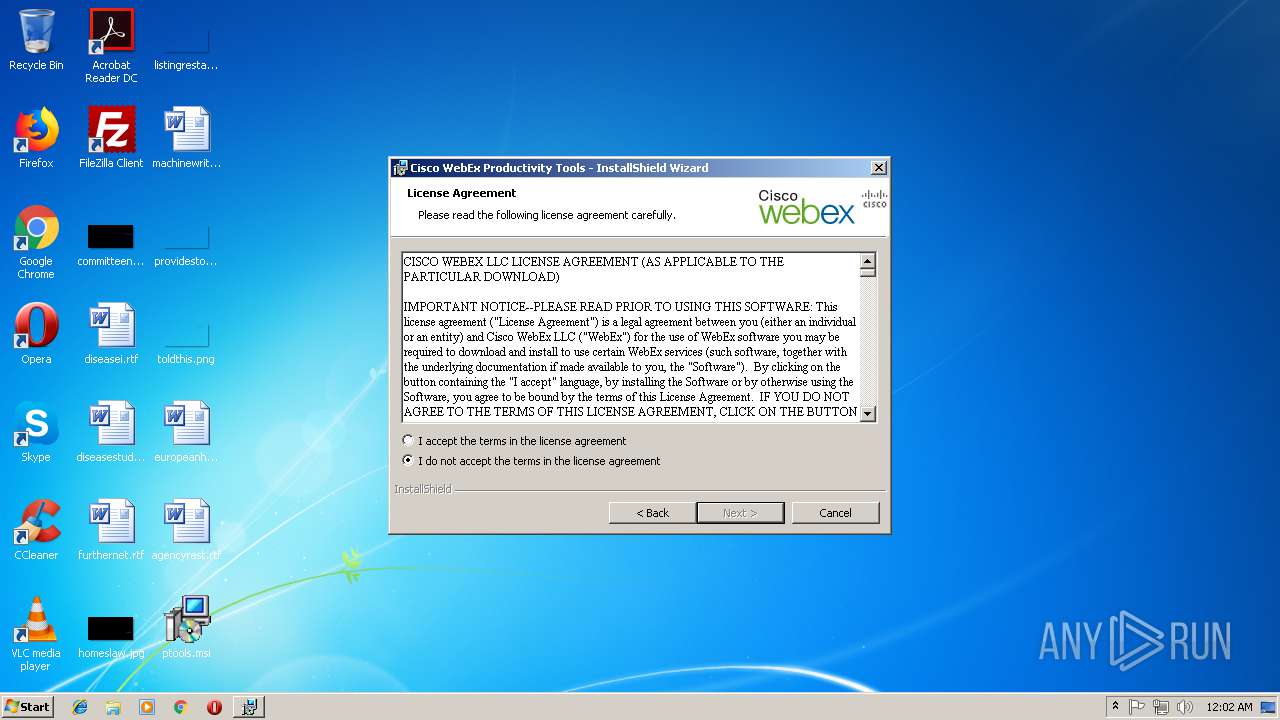
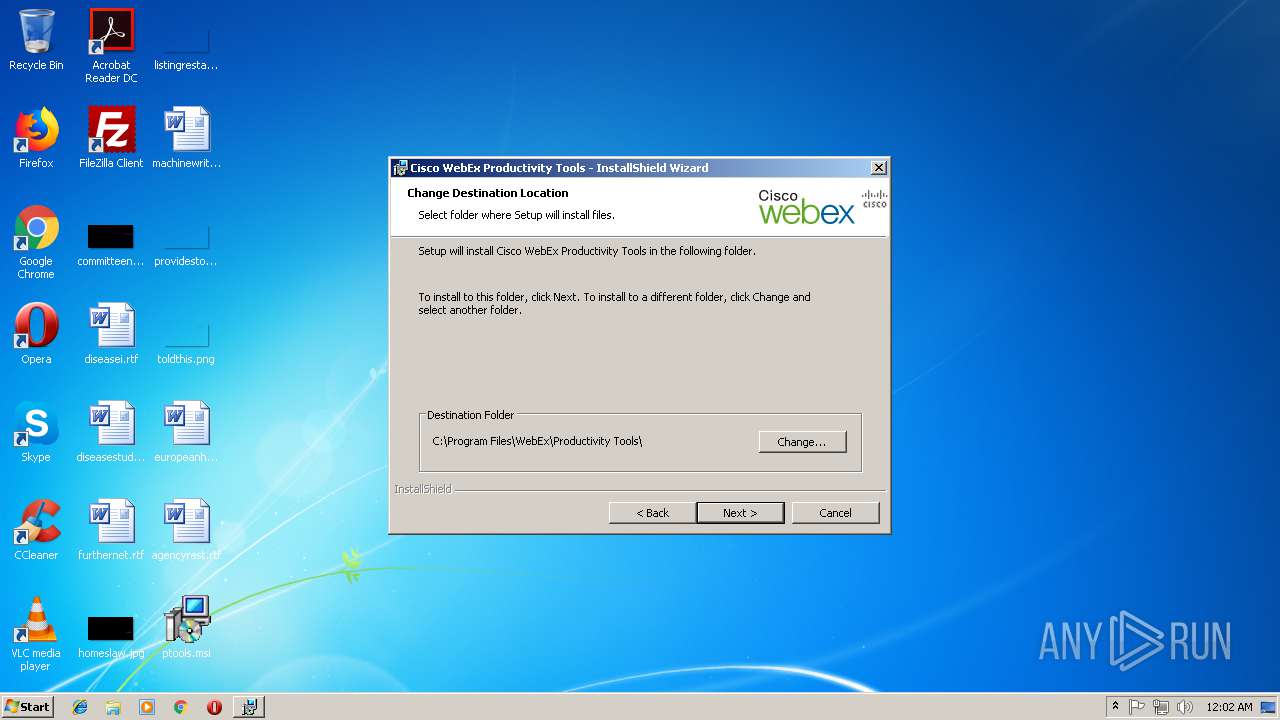
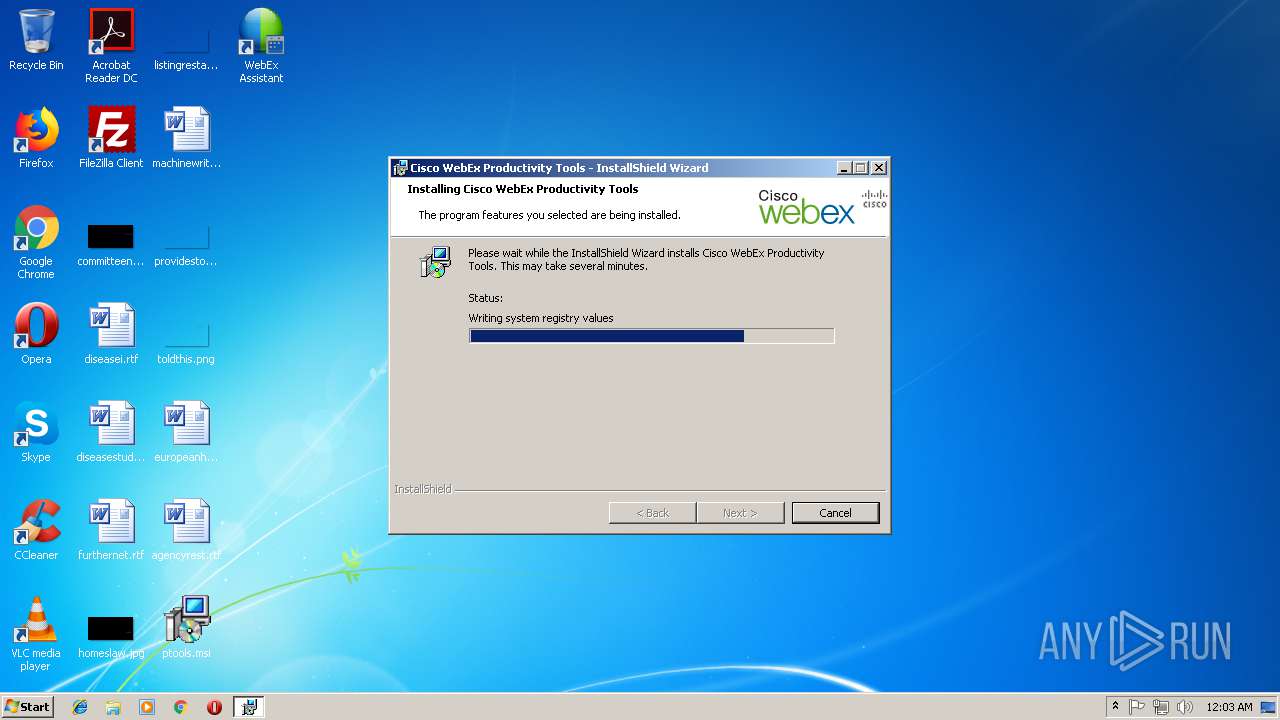
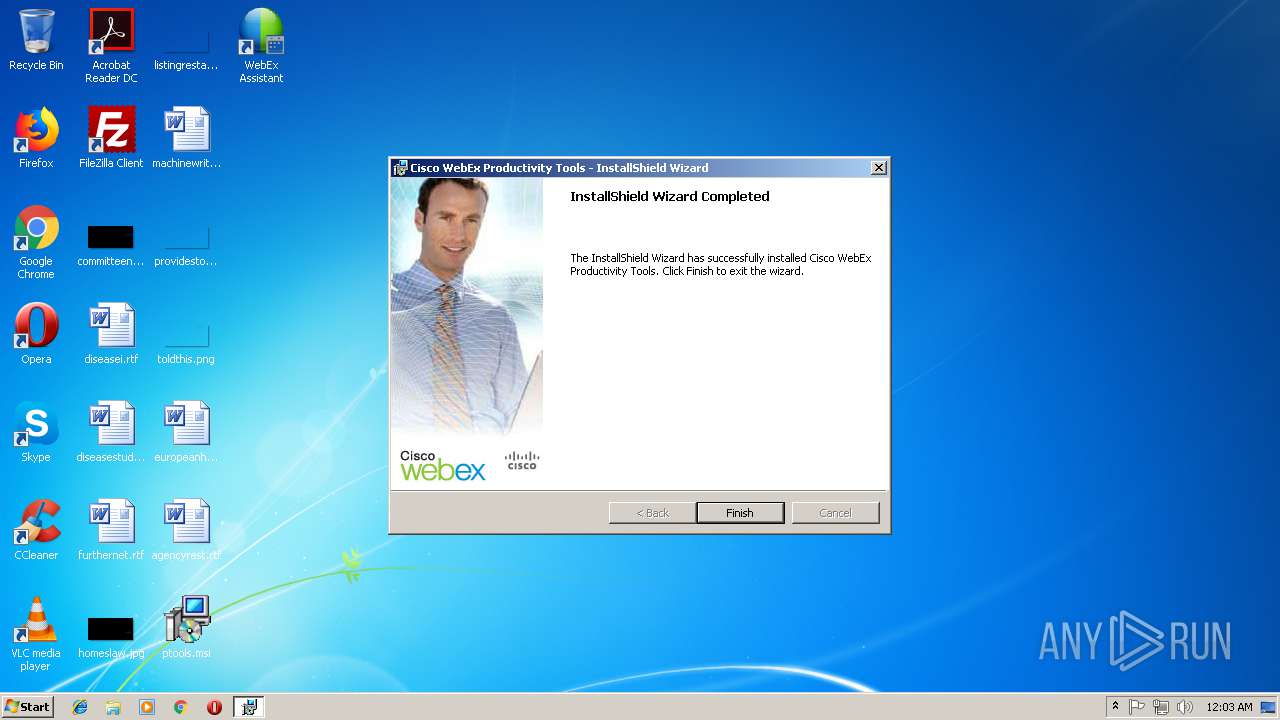
| File name: | ptools.msi |
| Full analysis: | https://app.any.run/tasks/8efac477-35b1-4b31-84f3-44d9453f2a51 |
| Verdict: | Malicious activity |
| Analysis date: | October 24, 2018, 23:01:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Last Saved By: InstallShield , Number of Characters: 0, Security: 1, Number of Words: 0, Title: Installation Database, Keywords: Installer,MSI,Database, Author: InstallShield Software Corporation, Number of Pages: 200, Name of Creating Application: InstallShield Developer 8.0, Revision Number: {C0875B62-BA53-40B4-8762-A52B36B1C6ED}, Last Saved Time/Date: Fri Sep 15 02:58:11 2017, Create Time/Date: Fri Sep 15 02:58:11 2017, Last Printed: Fri Sep 15 02:58:11 2017, Code page: 1252, Template: Intel;1033, Subject: Cisco WebEx Productivity Tools, Comments: Version 11.1.33100.550 |
| MD5: | AEF91A39FB65073C529F7F8FF67695C1 |
| SHA1: | F5972423DE07FE9ADF911F44770CC28B6D1F3E75 |
| SHA256: | 922ED5BB8CEE355D954491A34162448E996E488CBA7EE534BDA7AEBACFB63A9E |
| SSDEEP: | 196608:GAi4Bsl6L9PuiYtiAxoiSqVm3lenKFjXgTzpITZnNhi0fWqjM:GALBsl6LJuiMuw6fZ3OqI |
MALICIOUS
Application was dropped or rewritten from another process
- ptSrv.exe (PID: 2056)
- ptoneclk.exe (PID: 3600)
Loads dropped or rewritten executable
- ptoneclk.exe (PID: 3600)
- ptSrv.exe (PID: 2056)
Changes the autorun value in the registry
- ptoneclk.exe (PID: 3600)
SUSPICIOUS
Executable content was dropped or overwritten
- MsiExec.exe (PID: 2528)
- msiexec.exe (PID: 664)
Creates files in the user directory
- MsiExec.exe (PID: 2528)
Creates COM task schedule object
- msiexec.exe (PID: 664)
Reads internet explorer settings
- ptoneclk.exe (PID: 3600)
INFO
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2528)
Application launched itself
- msiexec.exe (PID: 664)
Searches for installed software
- msiexec.exe (PID: 664)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3760)
Creates or modifies windows services
- msiexec.exe (PID: 664)
- vssvc.exe (PID: 3760)
Creates files in the program directory
- msiexec.exe (PID: 664)
Creates a software uninstall entry
- msiexec.exe (PID: 664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (82) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .pps/ppt | | | Microsoft PowerPoint document (4.6) |
| .doc | | | Microsoft Word document (old ver.) (2.8) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastModifiedBy: | InstallShield |
|---|---|
| Characters: | - |
| Security: | Password protected |
| Words: | - |
| Title: | Installation Database |
| Keywords: | Installer,MSI,Database |
| Author: | InstallShield Software Corporation |
| Pages: | 200 |
| Software: | InstallShield? Developer 8.0 |
| RevisionNumber: | {C0875B62-BA53-40B4-8762-A52B36B1C6ED} |
| ModifyDate: | 2017:09:15 01:58:11 |
| CreateDate: | 2017:09:15 01:58:11 |
| LastPrinted: | 2017:09:15 01:58:11 |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | Intel;1033 |
| Subject: | Cisco WebEx Productivity Tools |
| Comments: | Version 11.1.33100.550 |
Total processes
44
Monitored processes
8
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 600 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\ptools.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1908 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "00000060" "000004AC" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | C:\PROGRA~1\WebEx\PRODUC~1\ptSrv.exe -Embedding | C:\PROGRA~1\WebEx\PRODUC~1\ptSrv.exe | svchost.exe | ||||||||||||
User: admin Company: Cisco WebEx LLC Integrity Level: MEDIUM Description: WebEx Productivity Tools Exit code: 0 Version: 102, 2013, 9, 21 Modules
| |||||||||||||||
| 2528 | C:\Windows\system32\MsiExec.exe -Embedding A1DFC0ADF51BDD32B21858E1CE5785B2 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3600 | "C:\Program Files\WebEx\Productivity Tools\ptoneclk.exe" /INSTALL /USERMAIL="" /SITEURL="" /USERNAME="" /PASSWORD="" /BUILDNUMBER="11.1.33100-550" /PASSTYPE="1" /WBXSSO="-1" | C:\Program Files\WebEx\Productivity Tools\ptoneclk.exe | msiexec.exe | ||||||||||||
User: admin Company: Cisco WebEx LLC Integrity Level: MEDIUM Description: WebEx Productivity Tools Exit code: 0 Version: 27, 2017, 3, 24 Modules
| |||||||||||||||
| 3760 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3992 | C:\Windows\system32\MsiExec.exe -Embedding CF5203F8B10F91F3A45E88A7516396C2 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 210
Read events
605
Write events
588
Delete events
17
Modification events
| (PID) Process: | (600) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000A41052B5ED6BD40198020000F00A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000A41052B5ED6BD40198020000F00A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 20 | |||
| (PID) Process: | (664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000765ABDB5ED6BD40198020000F00A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D0BCBFB5ED6BD40198020000B80A0000E803000001000000000000000000000049BEC389148DFF439996F7E678B710DA0000000000000000 | |||
| (PID) Process: | (3760) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000000859DCB5ED6BD401B00E00002C090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3760) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000000859DCB5ED6BD401B00E000000060000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3760) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000000859DCB5ED6BD401B00E0000D00B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3760) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000000859DCB5ED6BD401B00E0000480A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
70
Suspicious files
8
Text files
86
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 600 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA2A9.tmp | — | |
MD5:— | SHA256:— | |||
| 600 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA3F2.tmp | — | |
MD5:— | SHA256:— | |||
| 600 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA402.tmp | — | |
MD5:— | SHA256:— | |||
| 3992 | MsiExec.exe | C:\Users\admin\AppData\Local\Temp\WbxMsi.dll | — | |
MD5:— | SHA256:— | |||
| 600 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA413.tmp | — | |
MD5:— | SHA256:— | |||
| 664 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 664 | msiexec.exe | C:\Windows\Installer\5d438c.msi | — | |
MD5:— | SHA256:— | |||
| 664 | msiexec.exe | C:\Windows\Installer\MSI489D.tmp | — | |
MD5:— | SHA256:— | |||
| 664 | msiexec.exe | C:\Windows\Installer\MSI49A8.tmp | — | |
MD5:— | SHA256:— | |||
| 664 | msiexec.exe | C:\Windows\Installer\MSI49B8.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
MsiExec.exe | CPTCommon::SavePTInstallFileTemp: GetPTInstallPath FAILED!
|
MsiExec.exe | CPTCommon::LoadNewPTInstCkForMSI: GetPTInstallPath FAILED!
|
MsiExec.exe | C:\Program Files\WebEx\Productivity Tools\PTInstCk.dll |
MsiExec.exe | C:\Users\admin\AppData\Roaming\Webex\Productivity Tools\PTInstCk_Tmp.dll |
MsiExec.exe | CPTCommon::LoadNewPTInstCkForMSI: PTInstCk.dll was not existed!
|
MsiExec.exe | MSICheckAppsExist: -----Call Old CheckAppsExistEx() |
MsiExec.exe | CPTCommon::SavePTIMFileTemp: GetPTInstallPath FAILED!
|
MsiExec.exe | Can not open Event!!!
|
MsiExec.exe | Global\EVENT_WEBEXPT_OI_20578 |
MsiExec.exe | CPTCommon::IsPTWithNI: can not find msitype from register!
|