| File name: | Dont do it.bat |
| Full analysis: | https://app.any.run/tasks/f7912b20-88b5-4c6f-b711-3139ece692b7 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 01:02:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 81C4BF69ABF545DCBC5C4BF32126AAF1 |
| SHA1: | DE7E0455A2546D3D45D1684A10C605F8C299F856 |
| SHA256: | 9222FB5EDFFE66306208F03F1BC5A0581145C6E55D01C3C08930FCACC62E9FAA |
| SSDEEP: | 24:v2qqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqW:vu |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- cmd.exe (PID: 2312)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2408)
- iexplore.exe (PID: 3532)
- iexplore.exe (PID: 2884)
- iexplore.exe (PID: 1436)
- iexplore.exe (PID: 3508)
- iexplore.exe (PID: 1920)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 2844)
- iexplore.exe (PID: 976)
- iexplore.exe (PID: 2000)
- iexplore.exe (PID: 560)
- iexplore.exe (PID: 2796)
- iexplore.exe (PID: 3036)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 2900)
- iexplore.exe (PID: 700)
- iexplore.exe (PID: 2572)
- iexplore.exe (PID: 2792)
- iexplore.exe (PID: 2492)
- iexplore.exe (PID: 2560)
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 2520)
- iexplore.exe (PID: 3108)
- iexplore.exe (PID: 2712)
- iexplore.exe (PID: 2728)
- iexplore.exe (PID: 2096)
- iexplore.exe (PID: 3048)
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 3020)
- iexplore.exe (PID: 3248)
- iexplore.exe (PID: 5072)
- iexplore.exe (PID: 4620)
- iexplore.exe (PID: 4604)
- iexplore.exe (PID: 5936)
- iexplore.exe (PID: 5320)
- iexplore.exe (PID: 5720)
- iexplore.exe (PID: 4744)
- iexplore.exe (PID: 6000)
- iexplore.exe (PID: 4668)
Changes internet zones settings
- iexplore.exe (PID: 2884)
- iexplore.exe (PID: 2408)
- iexplore.exe (PID: 3532)
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 2844)
- iexplore.exe (PID: 2000)
- iexplore.exe (PID: 976)
- iexplore.exe (PID: 560)
Application launched itself
- iexplore.exe (PID: 2884)
- iexplore.exe (PID: 2408)
- iexplore.exe (PID: 3532)
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 976)
- iexplore.exe (PID: 2844)
- iexplore.exe (PID: 2000)
- iexplore.exe (PID: 560)
Reads settings of System Certificates
- iexplore.exe (PID: 3508)
- iexplore.exe (PID: 1920)
- iexplore.exe (PID: 1436)
- iexplore.exe (PID: 3532)
- iexplore.exe (PID: 2492)
- iexplore.exe (PID: 2844)
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 2000)
- iexplore.exe (PID: 976)
Creates files in the user directory
- iexplore.exe (PID: 3508)
- iexplore.exe (PID: 1920)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 2900)
- iexplore.exe (PID: 2792)
- iexplore.exe (PID: 3036)
Reads internet explorer settings
- iexplore.exe (PID: 1920)
- iexplore.exe (PID: 3508)
- iexplore.exe (PID: 2900)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 3036)
- iexplore.exe (PID: 2792)
- iexplore.exe (PID: 2492)
- iexplore.exe (PID: 2728)
- iexplore.exe (PID: 5072)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2792)
- iexplore.exe (PID: 3508)
- iexplore.exe (PID: 2492)
- iexplore.exe (PID: 2900)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3532)
- iexplore.exe (PID: 2000)
- iexplore.exe (PID: 976)
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 2844)
Changes settings of System certificates
- iexplore.exe (PID: 3532)
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 2000)
- iexplore.exe (PID: 976)
- iexplore.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
76
Monitored processes
42
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
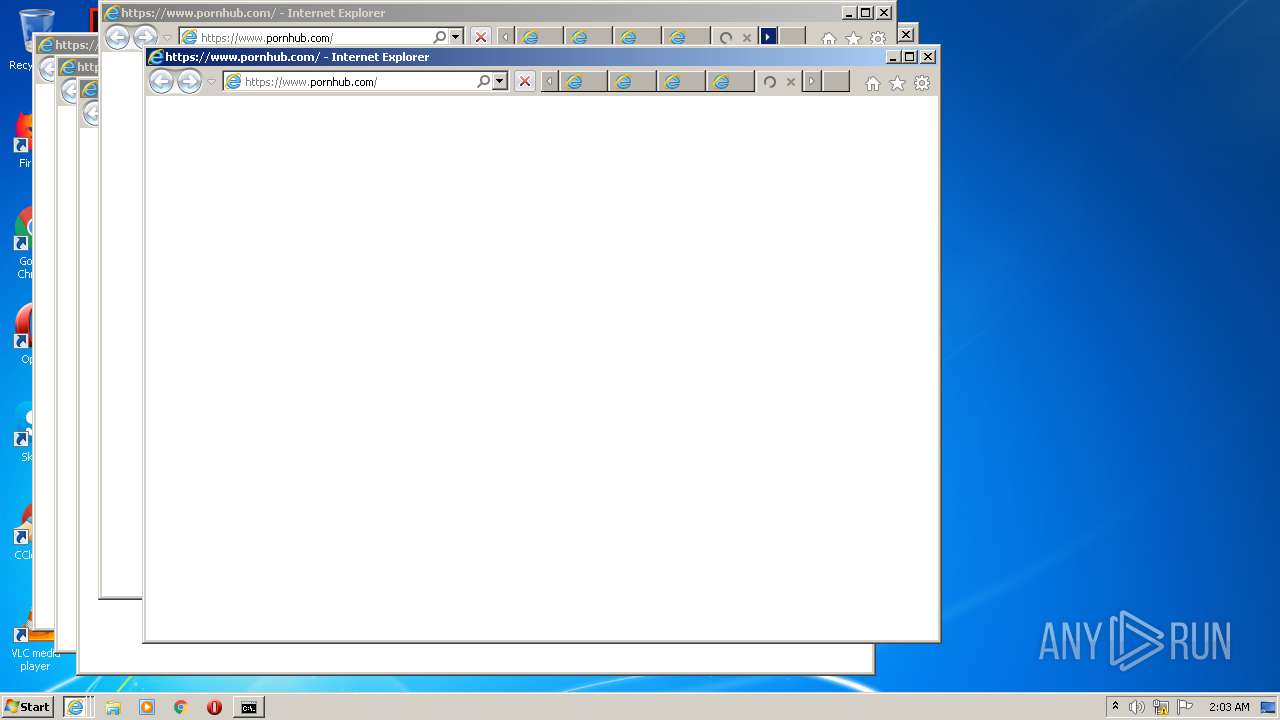
| 560 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.pornhub.com/ | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 700 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2408 CREDAT:3544327 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 976 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.pornhub.com/ | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1436 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2408 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1516 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3532 CREDAT:529665 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1920 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2884 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2000 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.pornhub.com/ | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2000 CREDAT:201996 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.pornhub.com/ | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2312 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Dont do it.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
6 231
Read events
4 106
Write events
2 120
Delete events
5
Modification events
| (PID) Process: | (2312) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {17FE9752-0B5A-4665-84CD-569794602F5C} {7F9185B0-CB92-43C5-80A9-92277A4F7B54} 0xFFFF |
Value: 01000000000000003E57C46CC596D601 | |||
| (PID) Process: | (2408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2127306718 | |||
| (PID) Process: | (2408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30840517 | |||
| (PID) Process: | (2408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
53
Text files
202
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3532 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3532 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[2].ico | — | |
MD5:— | SHA256:— | |||
| 2408 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1920 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarE1F6.tmp | — | |
MD5:— | SHA256:— | |||
| 3508 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabE224.tmp | — | |
MD5:— | SHA256:— | |||
| 1436 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabE233.tmp | — | |
MD5:— | SHA256:— | |||
| 3508 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | der | |
MD5:— | SHA256:— | |||
| 3104 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabE262.tmp | — | |
MD5:— | SHA256:— | |||
| 1436 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarE234.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
127
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1516 | iexplore.exe | GET | 304 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | — | — | whitelisted |
3508 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAx6iHYQ0JilgBc9YW1vcMQ%3D | US | der | 471 b | whitelisted |
1920 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAx6iHYQ0JilgBc9YW1vcMQ%3D | US | der | 471 b | whitelisted |
2796 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
1920 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAx6iHYQ0JilgBc9YW1vcMQ%3D | US | der | 471 b | whitelisted |
1436 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAx6iHYQ0JilgBc9YW1vcMQ%3D | US | der | 471 b | whitelisted |
1436 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAx6iHYQ0JilgBc9YW1vcMQ%3D | US | der | 471 b | whitelisted |
3508 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAx6iHYQ0JilgBc9YW1vcMQ%3D | US | der | 471 b | whitelisted |
1920 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
3508 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1516 | iexplore.exe | 66.254.114.41:443 | www.pornhub.com | Reflected Networks, Inc. | US | malicious |
1436 | iexplore.exe | 66.254.114.41:443 | www.pornhub.com | Reflected Networks, Inc. | US | malicious |
3104 | iexplore.exe | 66.254.114.41:443 | www.pornhub.com | Reflected Networks, Inc. | US | malicious |
2796 | iexplore.exe | 66.254.114.41:443 | www.pornhub.com | Reflected Networks, Inc. | US | malicious |
— | — | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1920 | iexplore.exe | 66.254.114.41:443 | www.pornhub.com | Reflected Networks, Inc. | US | malicious |
3508 | iexplore.exe | 66.254.114.41:443 | www.pornhub.com | Reflected Networks, Inc. | US | malicious |
1516 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3508 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3036 | iexplore.exe | 66.254.114.41:443 | www.pornhub.com | Reflected Networks, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.pornhub.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ci.phncdn.com |
| whitelisted |
static.trafficjunky.com |
| whitelisted |
di.phncdn.com |
| whitelisted |
www.google.com |
| malicious |
ocsp.pki.goog |
| whitelisted |
hubt.pornhub.com |
| whitelisted |