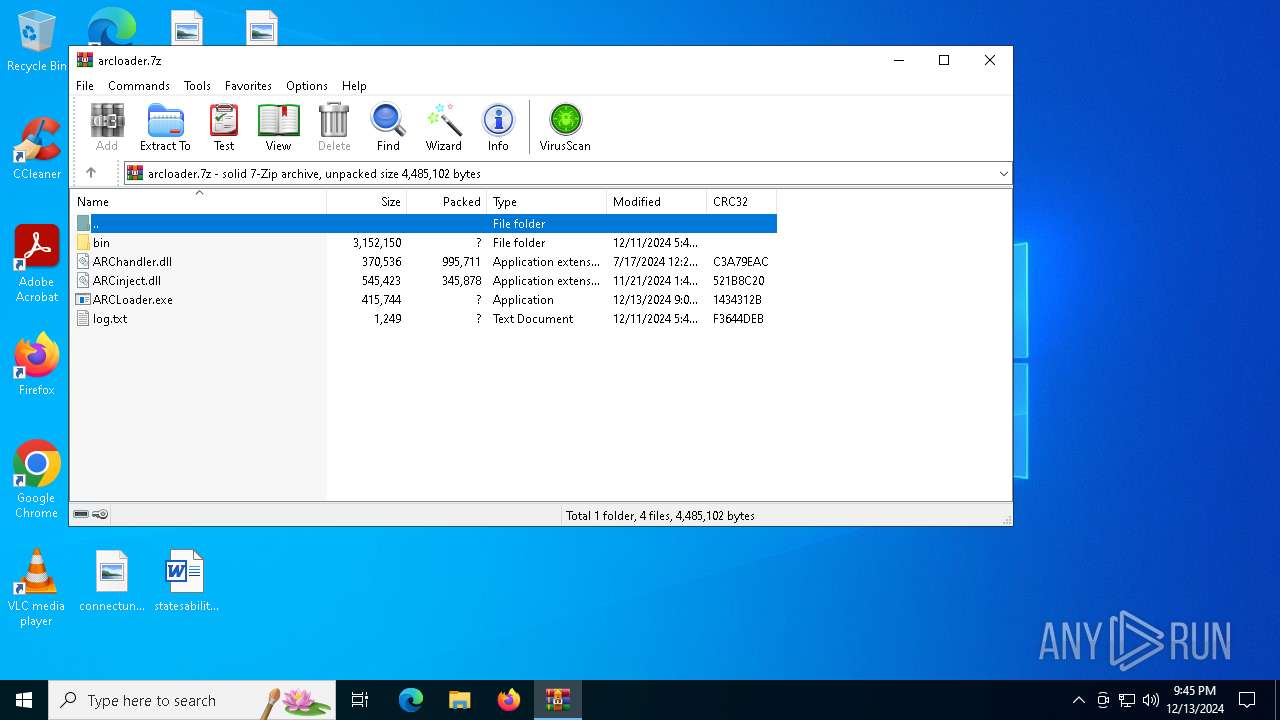
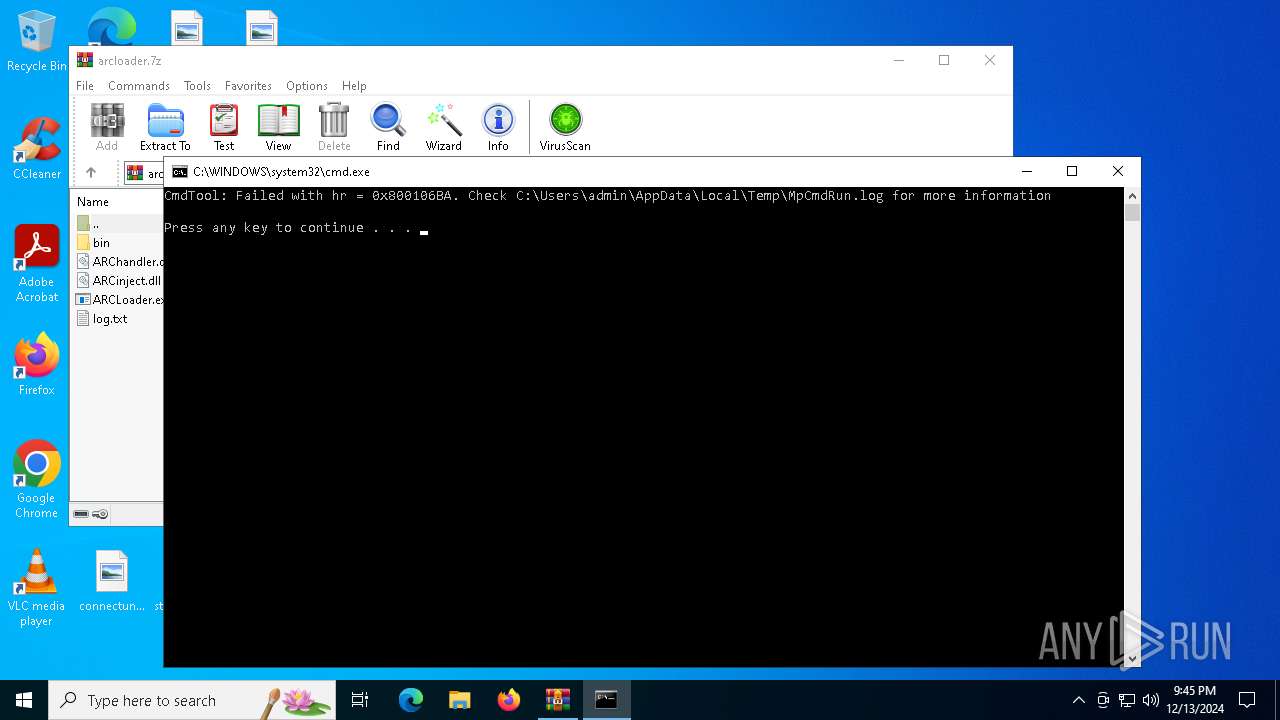
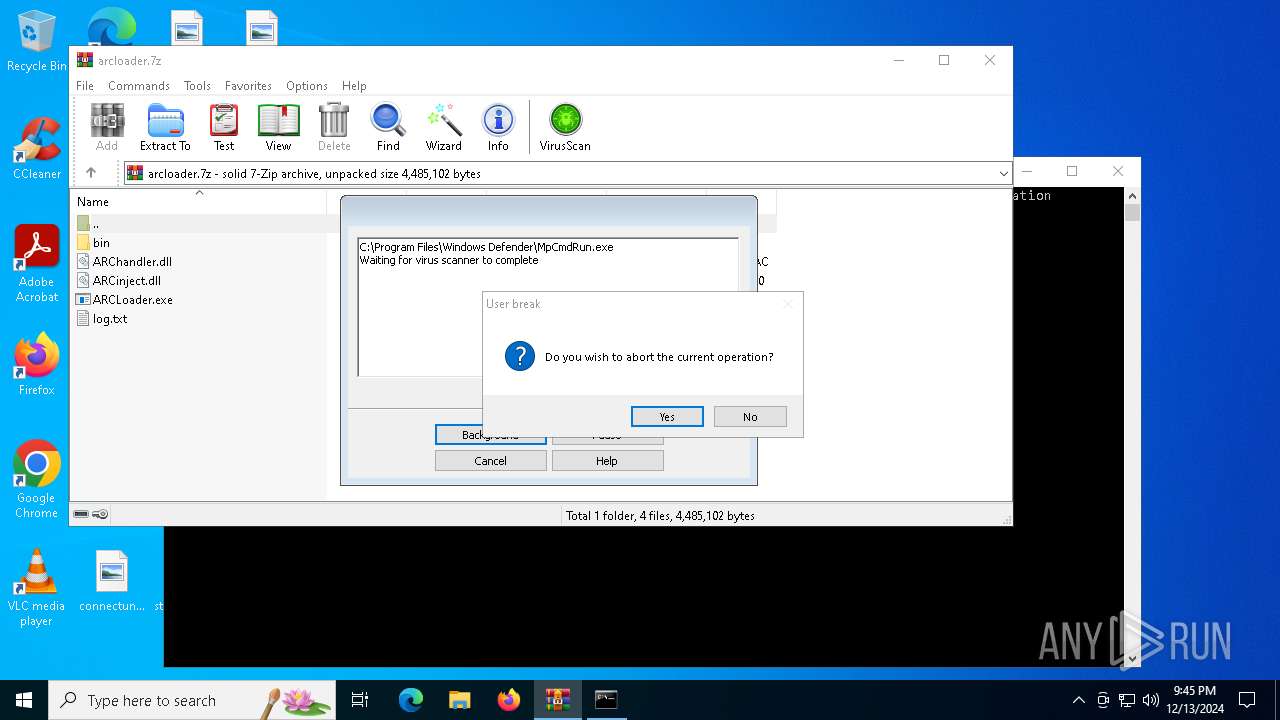
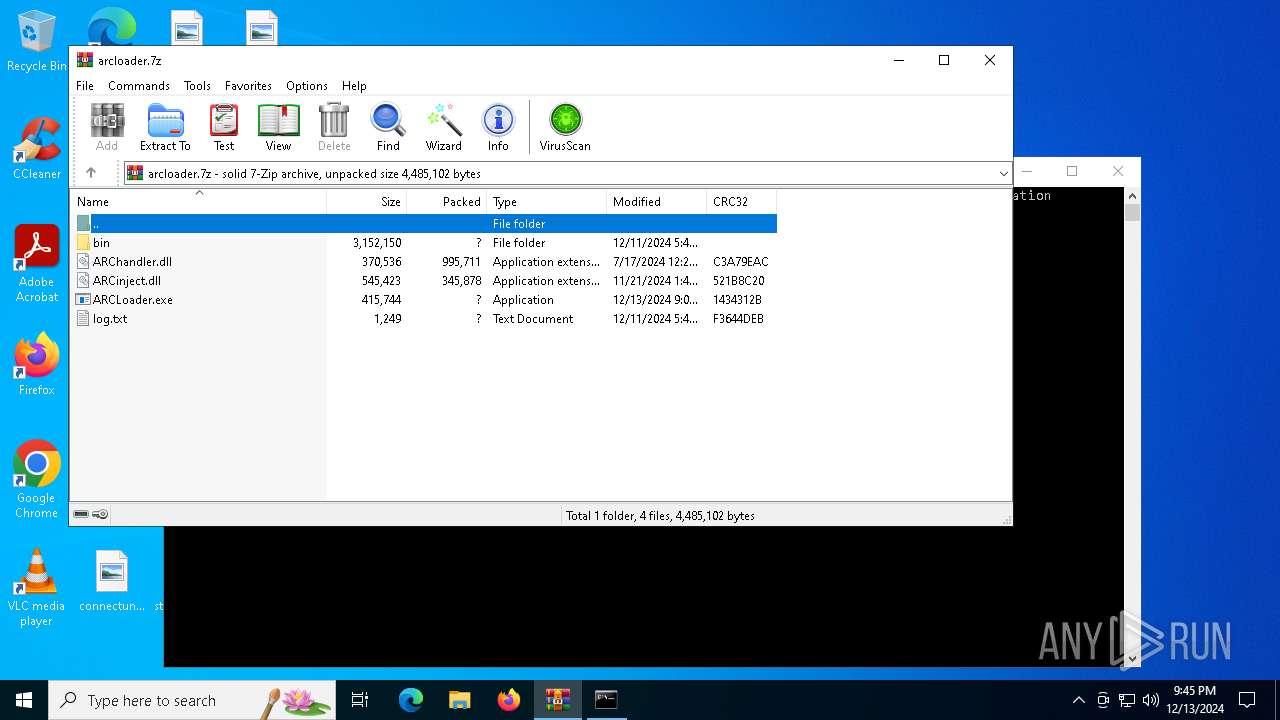
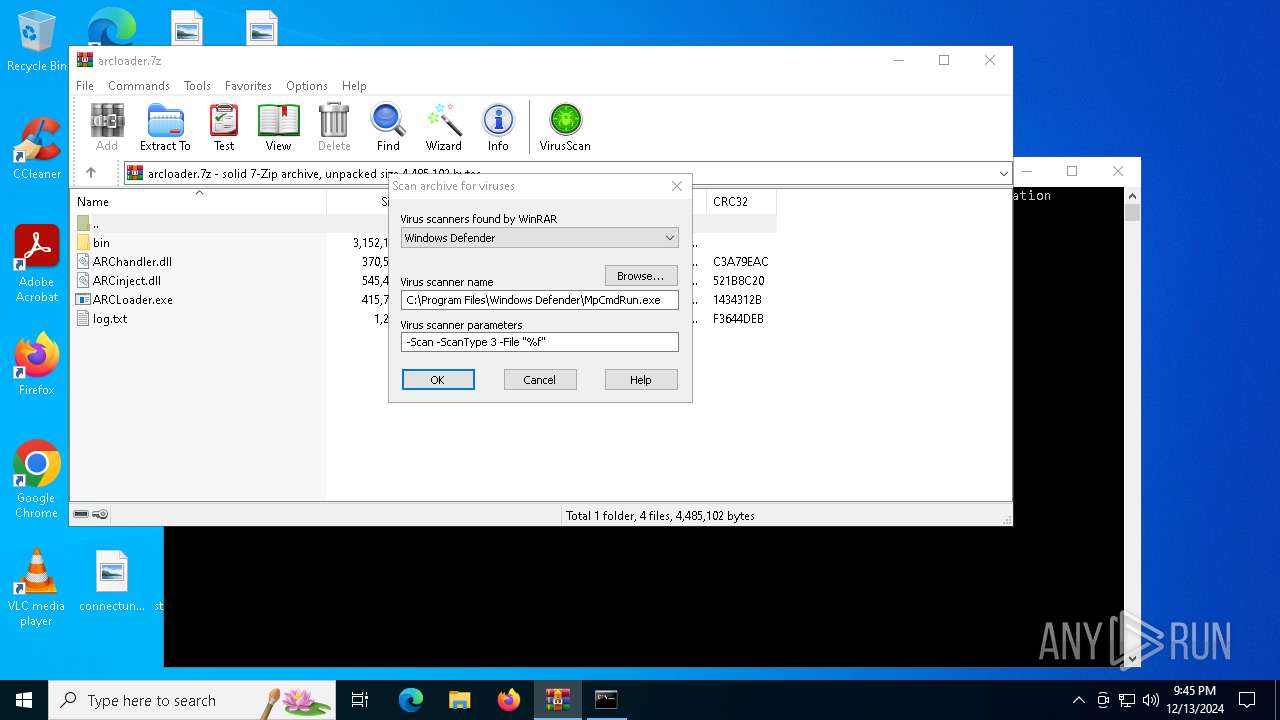
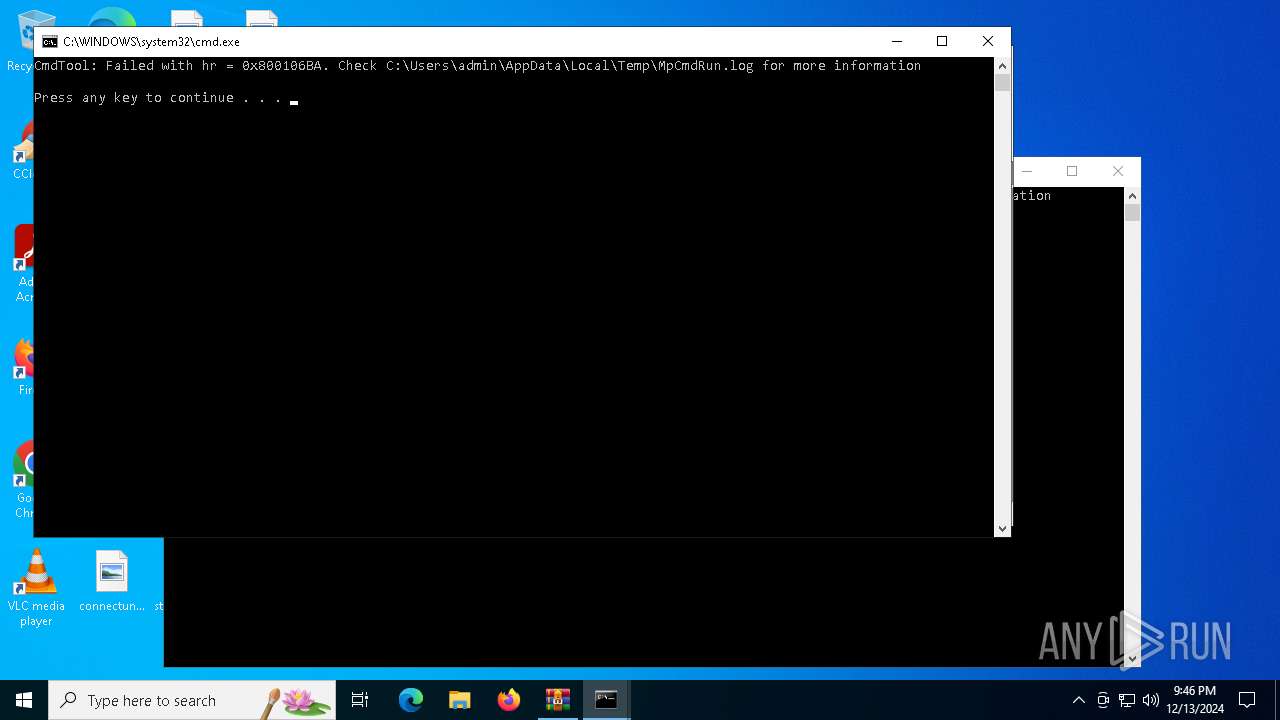
| File name: | arcloader.7z |
| Full analysis: | https://app.any.run/tasks/6f56f812-cd6c-4c24-83e2-d0a7cd1c439c |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 21:45:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 2B90E293AAB42C180E52A368E8ACFA7A |
| SHA1: | 860E85B46947160E64C505C6541EB54FFFB834F1 |
| SHA256: | 921FF01EF17CF7B9168263BC66E99675629F3744D68FBE5216AE204F6BCED03C |
| SSDEEP: | 49152:CFWkyGxzICw4d6AoN9Oy9YlBsfjpYLDuwpQdT3jfSW/HGxcLa0F61VlwYXTC8mtc:CFWT+9Ssy9Yo1SD7KdbGWz+0F6lpDX+Y |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4504)
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 2124)
- MpCmdRun.exe (PID: 3832)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4504)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4504)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4504)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4504)
Reads the computer name
- MpCmdRun.exe (PID: 2124)
- MpCmdRun.exe (PID: 3832)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4504)
The process uses the downloaded file
- WinRAR.exe (PID: 4504)
Checks supported languages
- MpCmdRun.exe (PID: 2124)
- MpCmdRun.exe (PID: 3832)
Create files in a temporary directory
- MpCmdRun.exe (PID: 2124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:12:11 17:44:32+00:00 |
| ArchivedFileName: | bin |
Total processes
124
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR4504.13718" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2956 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3652 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4504.17291\Rar$Scan42605.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3832 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR4504.17291" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4504 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\arcloader.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5036 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4504.13718\Rar$Scan6869.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 768
Read events
1 758
Write events
10
Delete events
0
Modification events
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\arcloader.7z | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
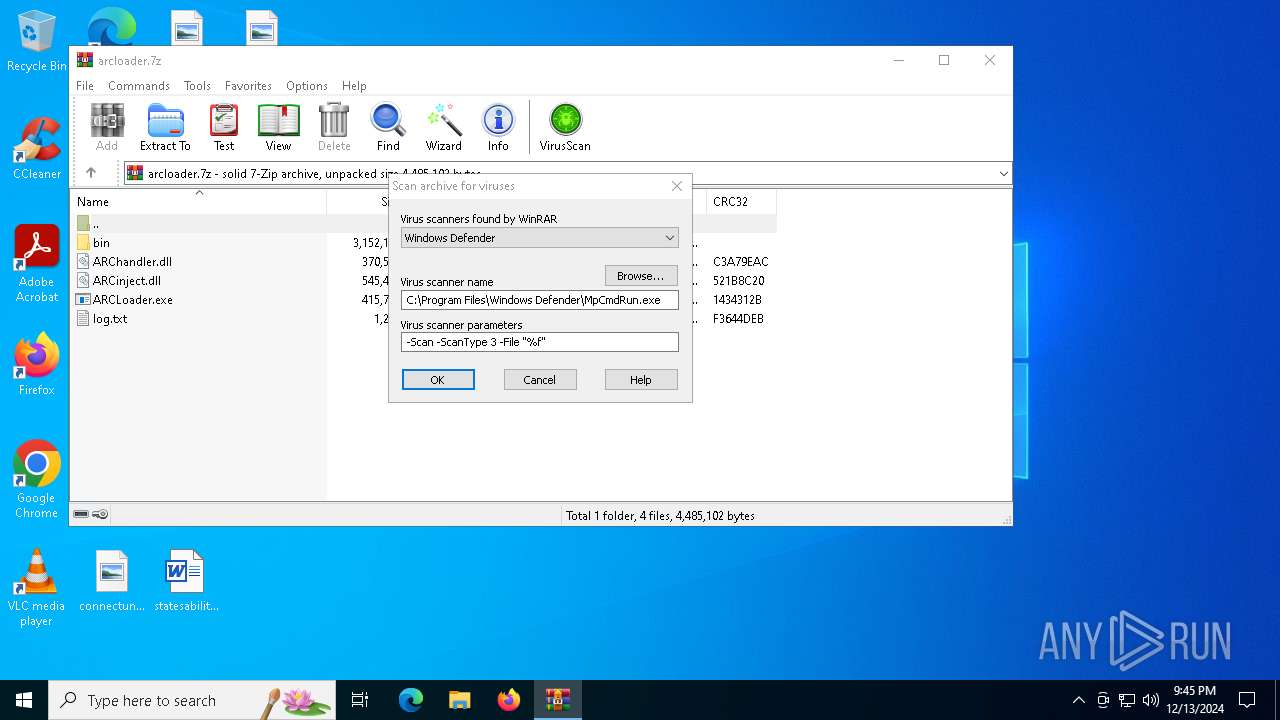
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
10
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.17291\arcloader.7z\ARChandler.dll | executable | |
MD5:7FD9C99282F84CB7895B1461C5B6C903 | SHA256:C57CDC261C15B4C6872E39B6EECF60A0EF7E09632B7FFF34C38C3C7B8F715B19 | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.13718\arcloader.7z\ARChandler.dll | executable | |
MD5:7FD9C99282F84CB7895B1461C5B6C903 | SHA256:C57CDC261C15B4C6872E39B6EECF60A0EF7E09632B7FFF34C38C3C7B8F715B19 | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.13718\arcloader.7z\bin\SLib3NET7.dll | executable | |
MD5:7599FD427F7ADCAFFE7C7D71F0D64A8C | SHA256:528837E2522323C54013C99DCE62A9E98844293960D0B603AF14AA23E6641A7A | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.13718\Rar$Scan6869.bat | text | |
MD5:A50AB2F6B469FBEF82D8AC9CA83D3EB2 | SHA256:67DFA55A2EA5925BAE3914878CFC1DE9C51B3995DC94EADD37305C81576045A0 | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.13718\arcloader.7z\log.txt | text | |
MD5:F54925CAA532D155EF59CD56B661DCB0 | SHA256:A3C11742AC09F6A571964FF818CE7309481A89AAF3463E2C003DA18183764ECD | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.17291\arcloader.7z\ARCinject.dll | executable | |
MD5:E8E275EC48E8C812630908B33234071B | SHA256:95896C0B5DF81B5C01914D264D8A04B88741A7D836983FA9DFF381ED9350686B | |||
| 2124 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:6AE42BAD8D90B7B0D7B7EF6BDF027518 | SHA256:35E120860D706966DDAB4FE9B07391E586C3C5D0BD96999EBF66ED7934BF6E7A | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.17291\arcloader.7z\log.txt | text | |
MD5:F54925CAA532D155EF59CD56B661DCB0 | SHA256:A3C11742AC09F6A571964FF818CE7309481A89AAF3463E2C003DA18183764ECD | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.17291\arcloader.7z\bin\SLib3NET7.dll | executable | |
MD5:7599FD427F7ADCAFFE7C7D71F0D64A8C | SHA256:528837E2522323C54013C99DCE62A9E98844293960D0B603AF14AA23E6641A7A | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.13718\arcloader.7z\ARCLoader.exe | executable | |
MD5:878D4832250E3D2B8CEB5F47A186FE6A | SHA256:BECE1D082AFEFB1AE3B7D683B4450D2E95F592F58819F757FF5120E8E27F30C6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5580 | svchost.exe | GET | 200 | 23.48.23.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5580 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5580 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.155:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.141:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5580 | svchost.exe | 23.48.23.141:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5580 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |