| URL: | https://cdn.exponea.com/slido-admin/e/.eJyFkc9KG1EUxolVsKMgnVIQqXCFIkoxNxljMgkVtIhQxAeoIQxn7pxMrs4_7z0z6Yhd6SO48xVEBN_BlRuzELoqpetCHsBCp7NyUejufL_v41t8x2RLv1YXZ17fjK8vf3ylnYf9u82f4_HF_dzv4-vjzLj6sPB2QJToDufD4bCqA-nFVRGHHDOMSNdvPr-3vqtv250ZYyLV5lQZ6MwVQpgvwziiQZBb7dINzSkMQQYHKedu7OXck1nX6nECN0BOJSLFyfsv6dq9Z_B5QHU3ev9uAHev1RKW1ezX7XatYTVq_VOFvtSECr0ODELwqnACOWZbLkRHCnWSuoE8goKeNiwUXrPp2uu23d9otQ9nD168-3I22bh9Op98HFXqxrxwkgAih_IEHY1-WMwDJOPIfPMRtBRsje3GqlhNMfevHlWWjQXhgCCZScodF_uF7QgIE5B-ZE5_ikoPR5Vd45VwRFENykdyfBWniVnfLl1Wlmu2kmr0WKyYUAhUnOV_mIxYAJpYu7az-gfBxLAu.xqwQwVqOl28hRQ/click |
| Full analysis: | https://app.any.run/tasks/8b24666c-b120-4cbd-a062-98b915c0d135 |
| Verdict: | Malicious activity |
| Analysis date: | February 14, 2024, 05:18:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C99D3293F7D6082F276303CD1048CEFD |
| SHA1: | D2DC83798CC6826B84972E91A40F3854DF2574BF |
| SHA256: | 9208C30B8EEA63A2C97EAD4933FD6918C19EB85C5000878AA04B2C9AC1A2F4CD |
| SSDEEP: | 12:2clKU/Pkx1SOWDTqjZq/eaFYdR4xrtcZJdHjB:2cZPk1WQq/exSxyJdHF |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- msdt.exe (PID: 116)
- msdt.exe (PID: 2592)
Reads settings of System Certificates
- msdt.exe (PID: 116)
- msdt.exe (PID: 2592)
Reads the Internet Settings
- sdiagnhost.exe (PID: 2756)
- msdt.exe (PID: 116)
- sdiagnhost.exe (PID: 880)
Uses ROUTE.EXE to obtain the routing table information
- sdiagnhost.exe (PID: 880)
Process uses IPCONFIG to discover network configuration
- sdiagnhost.exe (PID: 880)
INFO
Application launched itself
- iexplore.exe (PID: 2472)
Drops the executable file immediately after the start
- msdt.exe (PID: 116)
- msdt.exe (PID: 2592)
Create files in a temporary directory
- msdt.exe (PID: 116)
- msdt.exe (PID: 2592)
- makecab.exe (PID: 2172)
- sdiagnhost.exe (PID: 880)
Reads the software policy settings
- msdt.exe (PID: 116)
- msdt.exe (PID: 2592)
Reads security settings of Internet Explorer
- msdt.exe (PID: 116)
- sdiagnhost.exe (PID: 2756)
- msdt.exe (PID: 2592)
- sdiagnhost.exe (PID: 880)
Creates files or folders in the user directory
- msdt.exe (PID: 116)
- msdt.exe (PID: 2592)
Manual execution by a user
- rundll32.exe (PID: 2644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
49
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | -modal 1114548 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDF6A2.tmp -ep NetworkDiagnosticsWeb | C:\Windows\System32\msdt.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 880 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1784 | "C:\Windows\system32\ROUTE.EXE" print | C:\Windows\System32\ROUTE.EXE | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Route Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2172 | "C:\Windows\system32\makecab.exe" /f NetworkConfiguration.ddf | C:\Windows\System32\makecab.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Cabinet Maker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2472 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://cdn.exponea.com/slido-admin/e/.eJyFkc9KG1EUxolVsKMgnVIQqXCFIkoxNxljMgkVtIhQxAeoIQxn7pxMrs4_7z0z6Yhd6SO48xVEBN_BlRuzELoqpetCHsBCp7NyUejufL_v41t8x2RLv1YXZ17fjK8vf3ylnYf9u82f4_HF_dzv4-vjzLj6sPB2QJToDufD4bCqA-nFVRGHHDOMSNdvPr-3vqtv250ZYyLV5lQZ6MwVQpgvwziiQZBb7dINzSkMQQYHKedu7OXck1nX6nECN0BOJSLFyfsv6dq9Z_B5QHU3ev9uAHev1RKW1ezX7XatYTVq_VOFvtSECr0ODELwqnACOWZbLkRHCnWSuoE8goKeNiwUXrPp2uu23d9otQ9nD168-3I22bh9Op98HFXqxrxwkgAih_IEHY1-WMwDJOPIfPMRtBRsje3GqlhNMfevHlWWjQXhgCCZScodF_uF7QgIE5B-ZE5_ikoPR5Vd45VwRFENykdyfBWniVnfLl1Wlmu2kmr0WKyYUAhUnOV_mIxYAJpYu7az-gfBxLAu.xqwQwVqOl28hRQ/click" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2592 | -modal 1114548 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDFC001.tmp -ep NetworkDiagnosticsWeb | C:\Windows\System32\msdt.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2644 | "C:\Windows\System32\rundll32.exe" werconcpl.dll, LaunchErcApp -queuereporting | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3088 | "C:\Windows\system32\ipconfig.exe" /all | C:\Windows\System32\ipconfig.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3684 | "C:\Windows\System32\control.exe" /name Microsoft.Troubleshooting /page "resultPage?keywords=+;NetworkDiagnostics" | C:\Windows\System32\control.exe | — | msdt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
29 900
Read events
29 709
Write events
155
Delete events
36
Modification events
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31088389 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31088389 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
4
Suspicious files
57
Text files
53
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:FC1F6728A9A0E82236FF4DF4743DDE70 | SHA256:B7C167B3E1E210C5DA180F7ABDEE82E0190A183CBF805EBCEEB1B5EBE5B39955 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:BB8DCD8EFF65987E4B4ED16CC38ED8DD | SHA256:5CCCA3AE611BAB192AFA35D4E5AE53A1FB5D2751990C2C1138A38FBE128A03CD | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_45E3C223BCF135987E4038FB6B0DBA13 | der | |
MD5:037AE8164352CA91E80AD33054D1906D | SHA256:07C018EB07002663D5248DAA8A65EAF587955E3DB45735E7E3AC9CB13D7D664E | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:5E95AE21A6EDE1C6B2F41924BC5AEBD2 | SHA256:5532F24F1CC1888A24C35C5DB8C4B6AABDAFC841C25B9726819A3EB85C7ACC38 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_45E3C223BCF135987E4038FB6B0DBA13 | binary | |
MD5:A16D025E8FF52D95B73E2C7F25CA7F87 | SHA256:596D8BCC37E15C3922694A5FBF415238E81BFAFF1312B457AEC60515132B36C1 | |||
| 116 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_ebd3f071-d570-4a5a-81a6-448f19badd6a\NetworkDiagnosticsResolve.ps1 | text | |
MD5:A7B957F221C643580184665BE57E6AC8 | SHA256:8582EF50174CB74233F196F193E04C0CCBBEE2AED5CE50964CBB95822C218E7F | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\NDF6A2.tmp | binary | |
MD5:34356131CC270A461A5094634934CCAA | SHA256:F01FB6D99CE0C054B80C5B6DDB9C7136FBD5F41B83B0B002D8542C71715924D0 | |||
| 116 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_ebd3f071-d570-4a5a-81a6-448f19badd6a\HTInteractiveRes.ps1 | text | |
MD5:C25ED2111C6EE9299E6D9BF51012F2F5 | SHA256:8E326EE0475208D4C943D885035058FAD7146BBA02B66305F7C9F31F6A57E81B | |||
| 116 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_ebd3f071-d570-4a5a-81a6-448f19badd6a\DiagPackage.diagpkg | xml | |
MD5:C9FB87FA3460FAE6D5D599236CFD77E2 | SHA256:CDE728C08A4E50A02FCFF35C90EE2B3B33AB24C8B858F180B6A67BFA94DEF35F | |||
| 116 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_ebd3f071-d570-4a5a-81a6-448f19badd6a\NetworkDiagnosticsVerify.ps1 | text | |
MD5:C0BB6343BD0F6F9B46B33E4B66106953 | SHA256:EB9BC61668A93759D0127A11CDFC03E924100D69C7E6457FEAA89330474C90C3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
36
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3916 | iexplore.exe | GET | 304 | 2.23.82.48:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a08f35fbea17b647 | unknown | — | — | unknown |
3916 | iexplore.exe | GET | 304 | 2.23.82.48:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
3916 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3916 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | unknown | binary | 724 b | unknown |
3916 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/s/gts1d4/QCM7sNa6KdE/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEQCBUCSOFTU6WxBjcY18iZxY | unknown | binary | 472 b | unknown |
2472 | iexplore.exe | GET | 304 | 2.23.82.48:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?70d85e3b0e586cab | unknown | — | — | unknown |
2472 | iexplore.exe | GET | 304 | 2.23.82.48:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?96c8eb5dfc595a04 | unknown | — | — | unknown |
2472 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
1080 | svchost.exe | GET | 200 | 2.23.82.48:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fc91d912a85a08d5 | unknown | compressed | 65.2 Kb | unknown |
2472 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3916 | iexplore.exe | 34.95.115.244:443 | cdn.exponea.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
3916 | iexplore.exe | 2.23.82.48:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3916 | iexplore.exe | 172.217.18.3:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
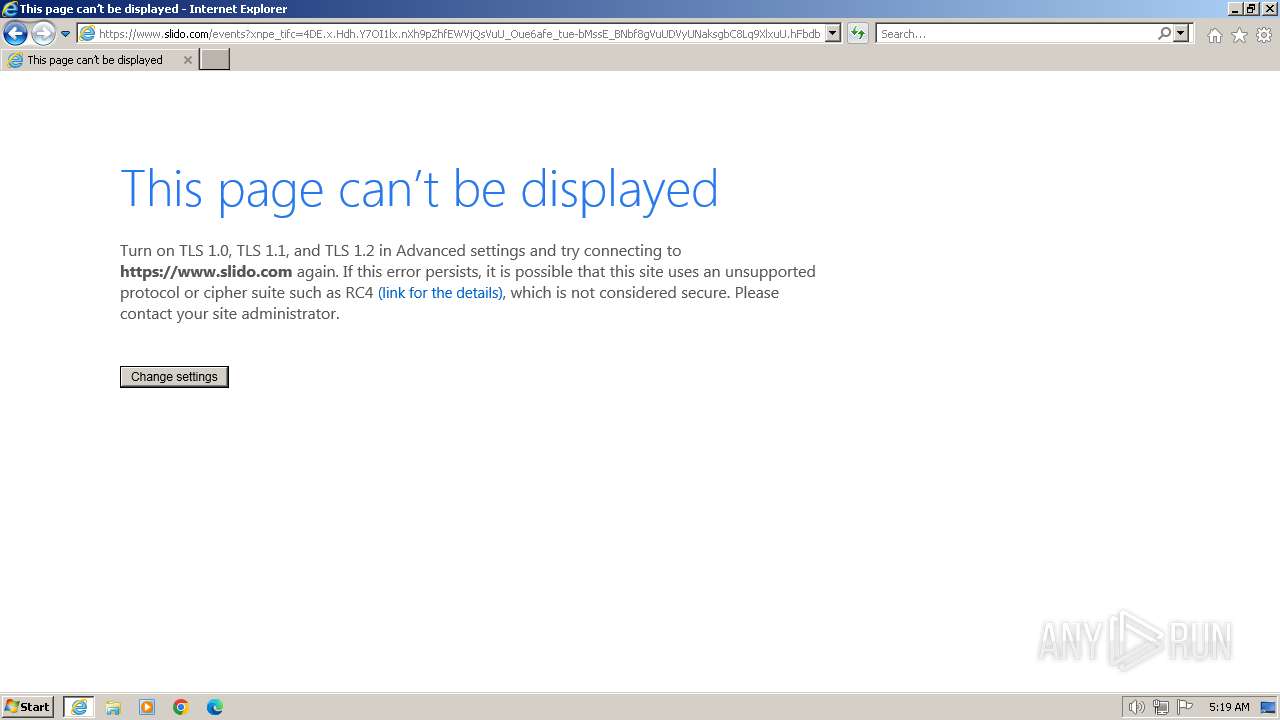
3916 | iexplore.exe | 18.173.187.19:443 | www.slido.com | — | US | unknown |
2472 | iexplore.exe | 2.17.112.32:443 | www.bing.com | Akamai International B.V. | NL | unknown |
2472 | iexplore.exe | 2.23.82.48:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2472 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.exponea.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.slido.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |