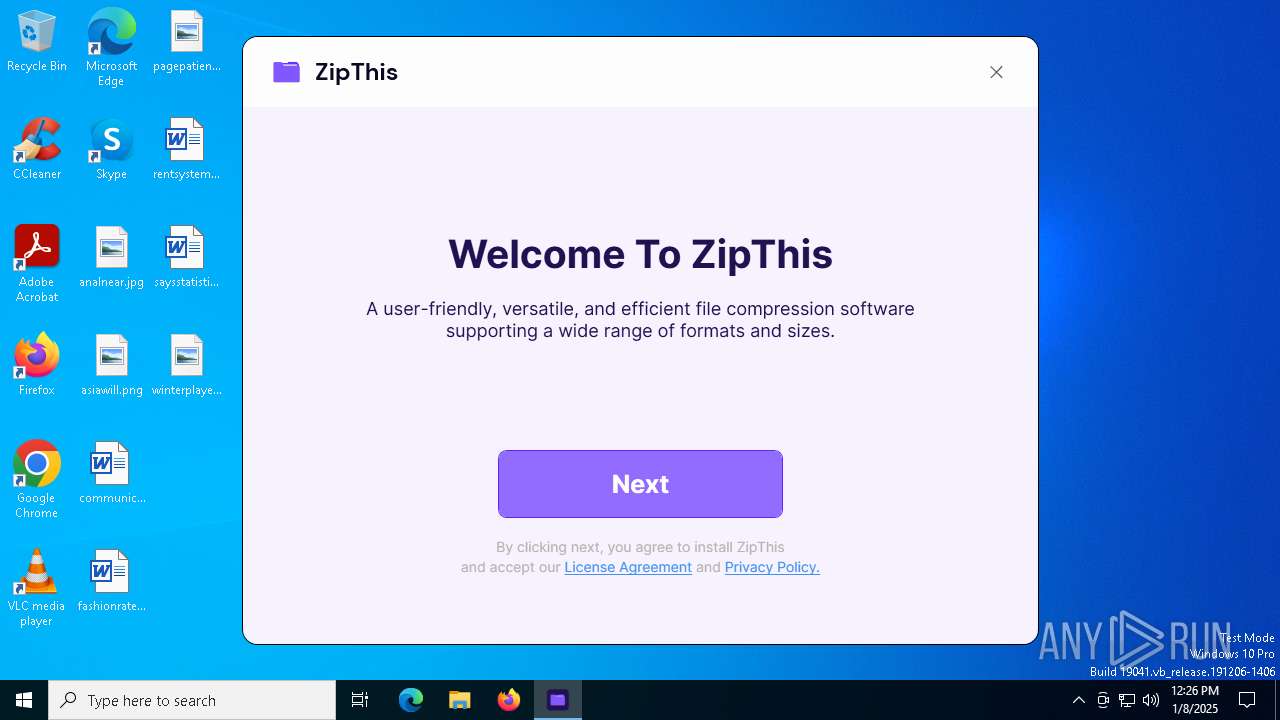
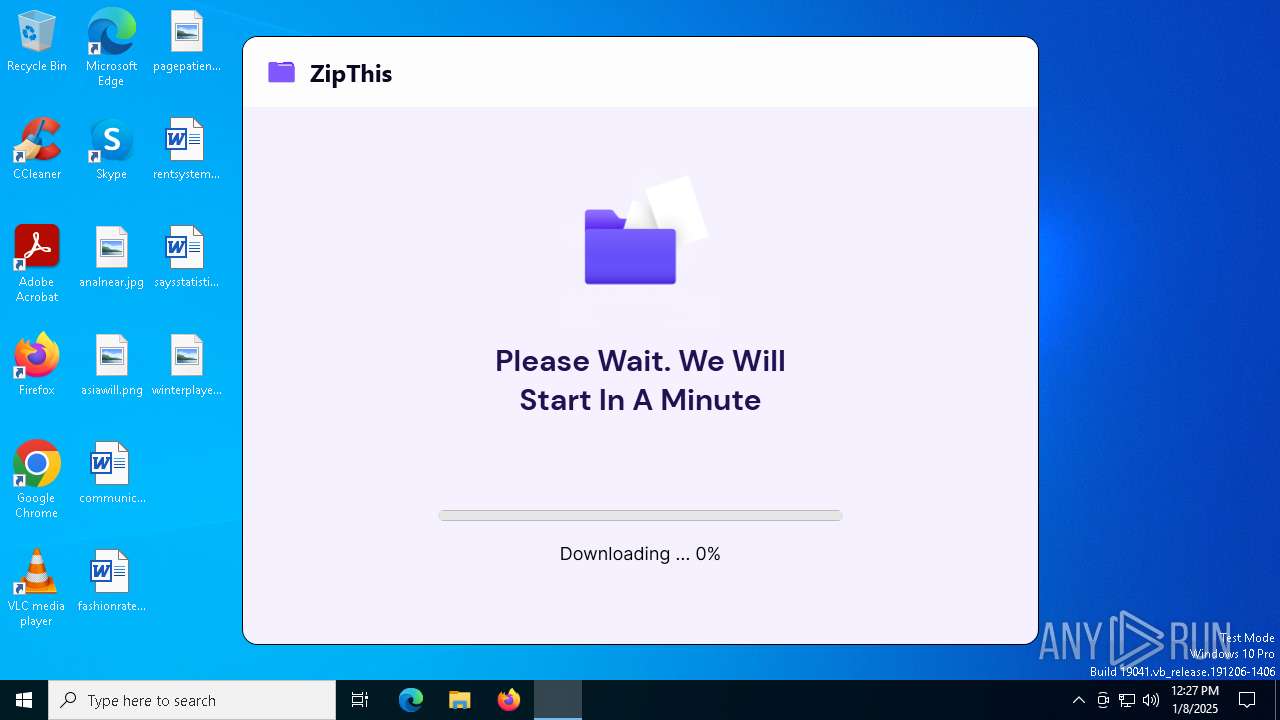
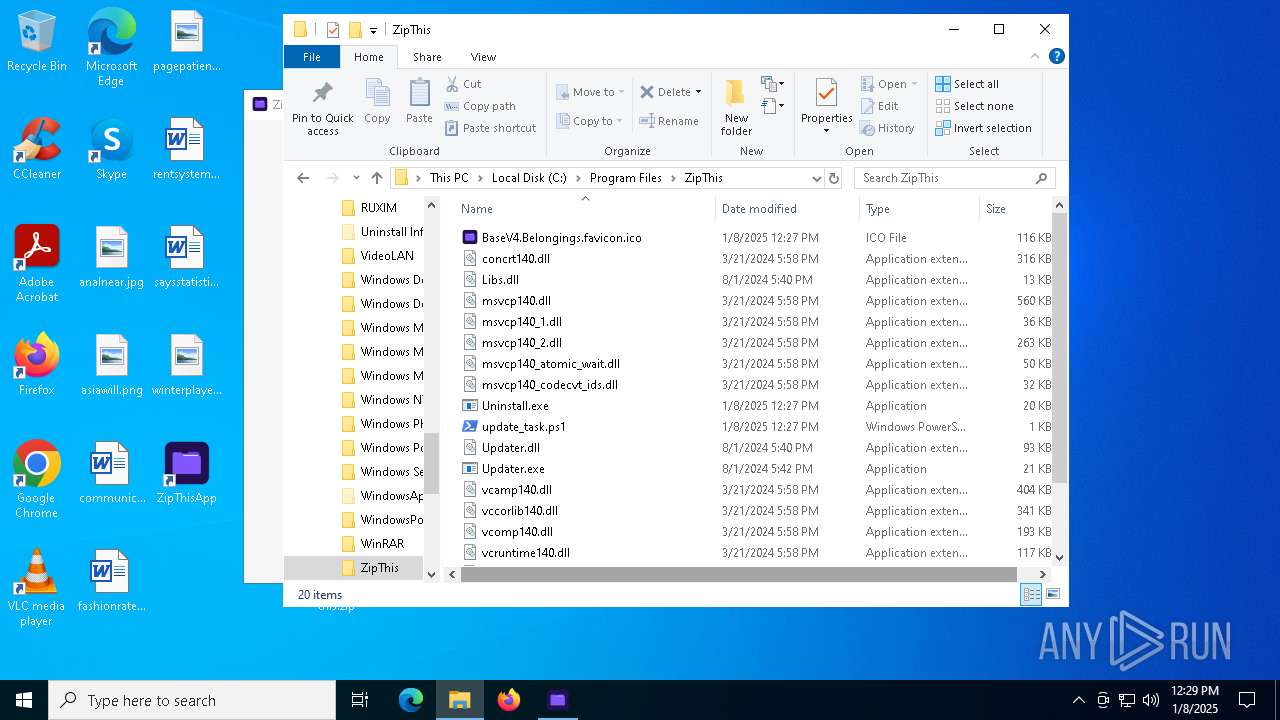
| File name: | ZipThis.exe |
| Full analysis: | https://app.any.run/tasks/4a756656-2553-460d-80d2-f415ed7d04b0 |
| Verdict: | Malicious activity |
| Analysis date: | January 08, 2025, 12:26:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows, 2 sections |
| MD5: | B00E6B651799ADE8DA83DE8DEF7C11B3 |
| SHA1: | 6C8017F07FE67A051825E31E1C9C4639C1C092B9 |
| SHA256: | 91F329CC468BFE5740E3A35D659F03C85F80D404ED0551C608E1EE50C3212B1F |
| SSDEEP: | 98304:4w4Duw4xT2ZyydrN7phb9dFqtq1lpI2zkymGeIPyPn7bWLRIhc35MaiGqF25ekAS:m |
MALICIOUS
Changes powershell execution policy (RemoteSigned)
- ZipThis.exe (PID: 6948)
SUSPICIOUS
Reads security settings of Internet Explorer
- ZipThis.exe (PID: 4952)
- ZipThis.exe (PID: 6948)
- ZipThisApp.exe (PID: 6284)
Reads the date of Windows installation
- ZipThis.exe (PID: 4952)
- ZipThis.exe (PID: 6948)
Application launched itself
- ZipThis.exe (PID: 4952)
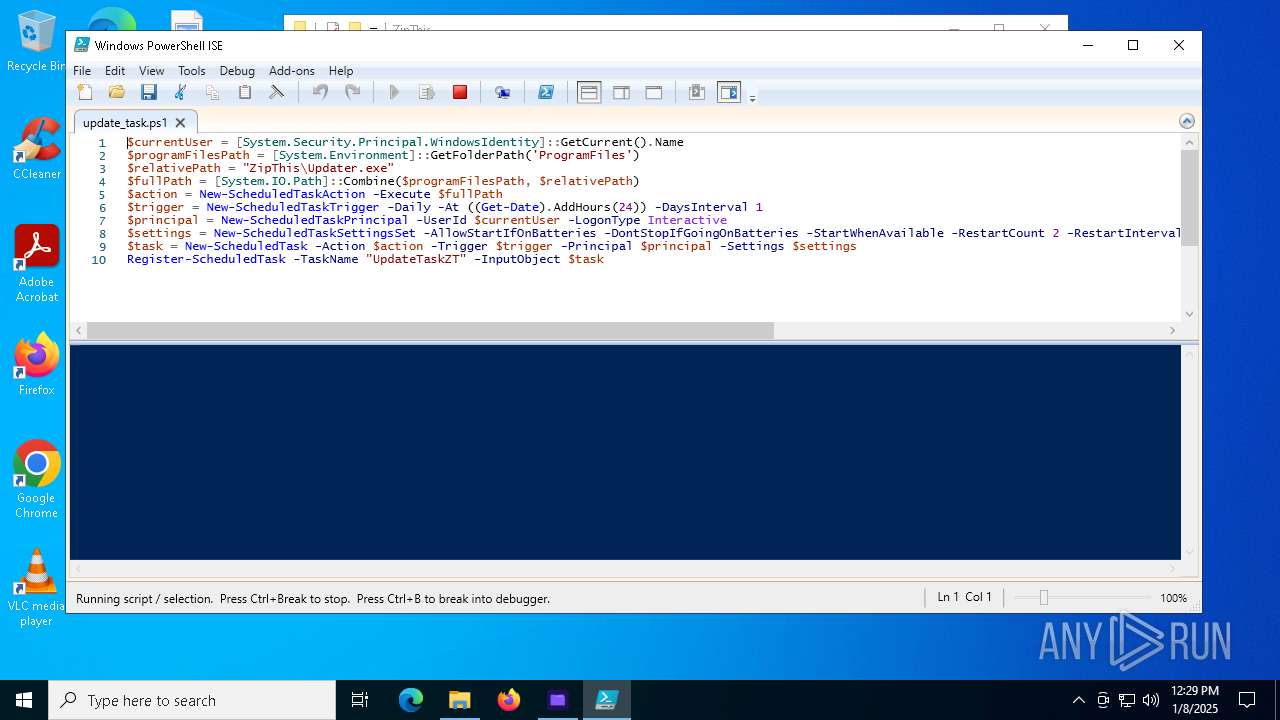
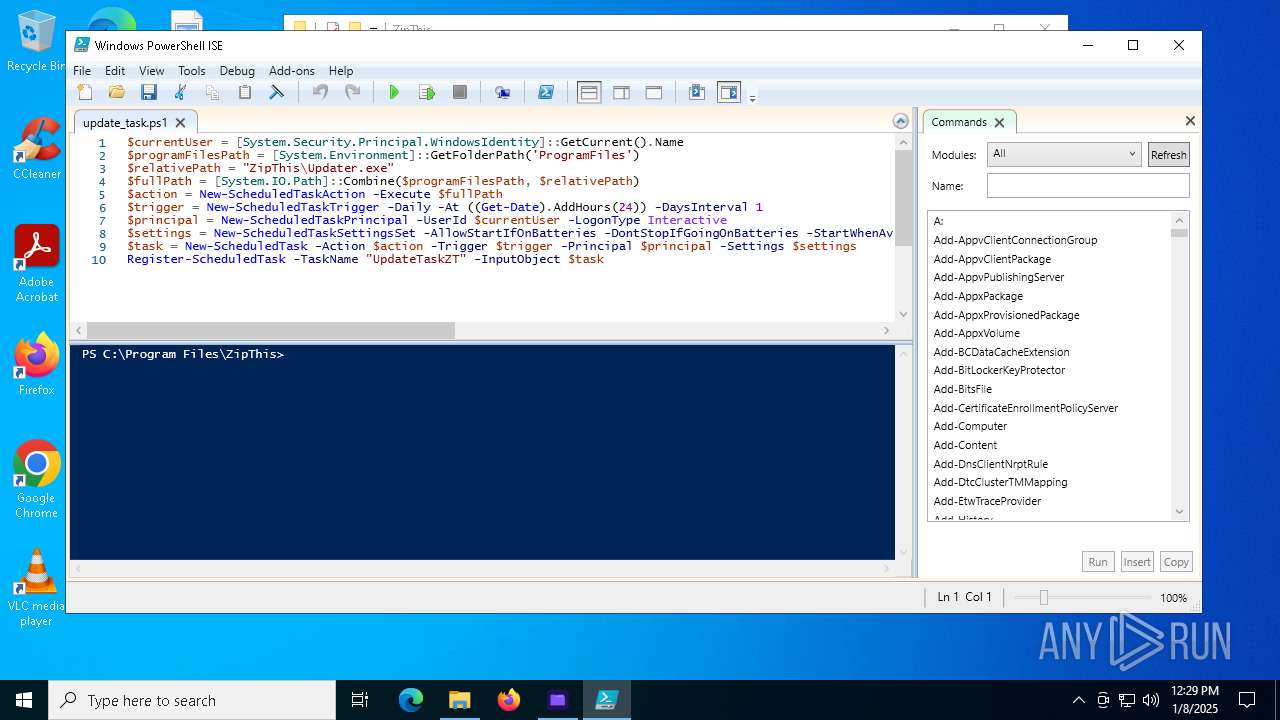
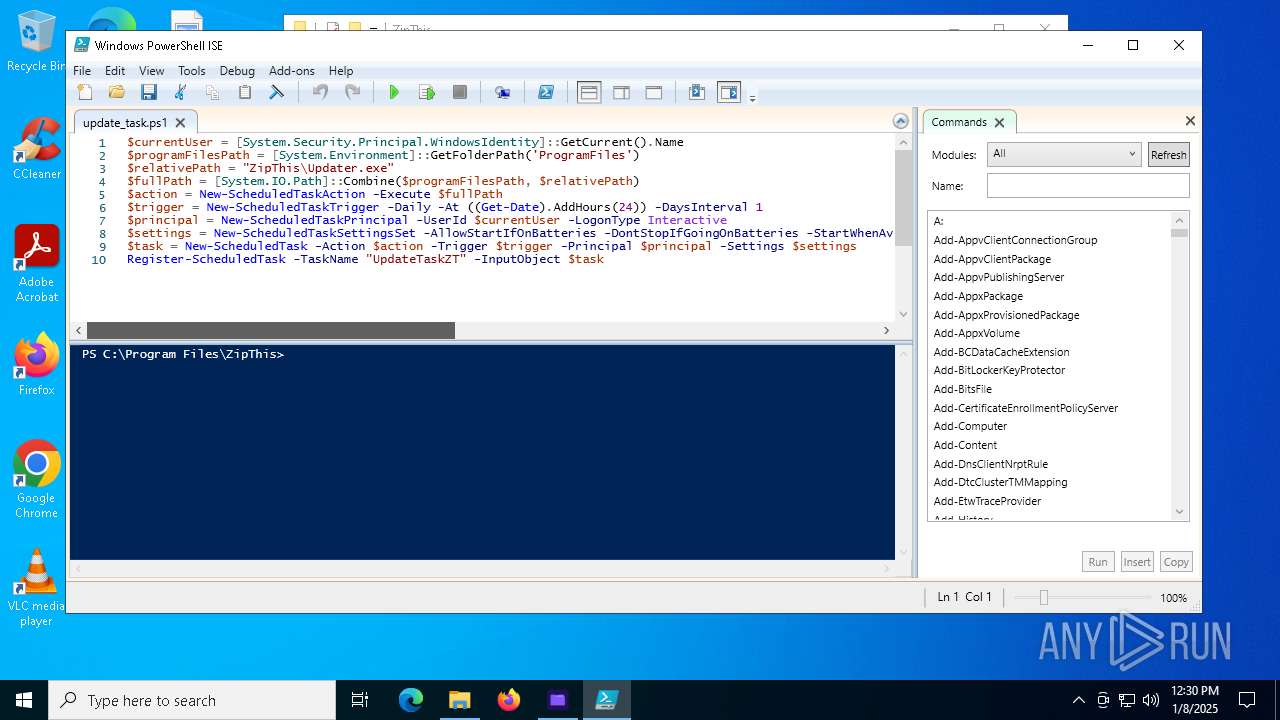
The process executes Powershell scripts
- ZipThis.exe (PID: 6948)
Starts POWERSHELL.EXE for commands execution
- ZipThis.exe (PID: 6948)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 7072)
The process drops C-runtime libraries
- ZipThis.exe (PID: 6948)
Executable content was dropped or overwritten
- ZipThis.exe (PID: 6948)
Creates a software uninstall entry
- ZipThis.exe (PID: 6948)
Searches for installed software
- ZipThis.exe (PID: 6948)
Process drops legitimate windows executable
- ZipThis.exe (PID: 6948)
INFO
Reads the software policy settings
- ZipThis.exe (PID: 4952)
- ZipThis.exe (PID: 6948)
- ZipThisApp.exe (PID: 6284)
Checks supported languages
- ZipThis.exe (PID: 4952)
- ZipThis.exe (PID: 6948)
- ZipThisApp.exe (PID: 6284)
Reads the computer name
- ZipThis.exe (PID: 4952)
- ZipThis.exe (PID: 6948)
- ZipThisApp.exe (PID: 6284)
The process uses the downloaded file
- ZipThis.exe (PID: 4952)
- powershell.exe (PID: 7072)
- ZipThis.exe (PID: 6948)
- powershell_ise.exe (PID: 4976)
Reads the machine GUID from the registry
- ZipThis.exe (PID: 4952)
- ZipThis.exe (PID: 6948)
- ZipThisApp.exe (PID: 6284)
Process checks computer location settings
- ZipThis.exe (PID: 4952)
- ZipThis.exe (PID: 6948)
Checks proxy server information
- ZipThis.exe (PID: 6948)
- ZipThisApp.exe (PID: 6284)
Disables trace logs
- ZipThis.exe (PID: 6948)
- ZipThisApp.exe (PID: 6284)
Reads Environment values
- ZipThis.exe (PID: 6948)
- ZipThisApp.exe (PID: 6284)
The sample compiled with english language support
- ZipThis.exe (PID: 6948)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7072)
Creates files in the program directory
- ZipThis.exe (PID: 6948)
Application launched itself
- chrome.exe (PID: 4128)
Create files in a temporary directory
- ZipThisApp.exe (PID: 6284)
- powershell_ise.exe (PID: 4976)
Manual execution by a user
- powershell_ise.exe (PID: 4976)
Creates files or folders in the user directory
- powershell_ise.exe (PID: 4976)
Reads security settings of Internet Explorer
- powershell_ise.exe (PID: 4976)
Checks current location (POWERSHELL)
- powershell_ise.exe (PID: 4976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2064:01:19 15:32:14+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 2749440 |
| InitializedDataSize: | 120320 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.1.24.110 |
| ProductVersionNumber: | 10.1.24.110 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | ZipThis |
| FileVersion: | 10.1.24.110 |
| InternalName: | ZipThis.exe |
| LegalCopyright: | Copyright © 2015-2023 Lightner Tok All rights reserved |
| LegalTrademarks: | - |
| OriginalFileName: | ZipThis.exe |
| ProductName: | ZipThis |
| ProductVersion: | 10.1.24.110 |
| AssemblyVersion: | 10.1.24.110 |
Total processes
148
Monitored processes
18
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1512 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x214,0x218,0x21c,0x1f0,0x220,0x7ff8215adc40,0x7ff8215adc4c,0x7ff8215adc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3280 --field-trial-handle=1880,i,13544093640856564800,1620150543019640036,262144 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://www.zipthisapp.com/success?u=f16c5d72-42d8-4c02-9bc9-6e2f522269c1 | C:\Program Files\Google\Chrome\Application\chrome.exe | ZipThis.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4512 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3700 --field-trial-handle=1880,i,13544093640856564800,1620150543019640036,262144 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4592 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2224 --field-trial-handle=1880,i,13544093640856564800,1620150543019640036,262144 --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4876 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5288 --field-trial-handle=1880,i,13544093640856564800,1620150543019640036,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4952 | "C:\Users\admin\AppData\Local\Temp\ZipThis.exe" | C:\Users\admin\AppData\Local\Temp\ZipThis.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ZipThis Exit code: 0 Version: 10.1.24.110 Modules
| |||||||||||||||
| 4976 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe" "C:\Program Files\ZipThis\update_task.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell ISE Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1868 --field-trial-handle=1880,i,13544093640856564800,1620150543019640036,262144 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 5256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2300 --field-trial-handle=1880,i,13544093640856564800,1620150543019640036,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
26 314
Read events
26 188
Write events
121
Delete events
5
Modification events
| (PID) Process: | (4952) ZipThis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ZipThis_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4952) ZipThis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ZipThis_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4952) ZipThis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ZipThis_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4952) ZipThis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ZipThis_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4952) ZipThis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ZipThis_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4952) ZipThis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ZipThis_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4952) ZipThis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ZipThis_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4952) ZipThis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ZipThis_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4952) ZipThis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ZipThis_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4952) ZipThis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ZipThis_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
17
Suspicious files
72
Text files
48
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4952 | ZipThis.exe | C:\Users\admin\AppData\Roaming\SMCR\userId.txt | text | |
MD5:3F7B9D80E43524AE2B653A2D431B9151 | SHA256:CC8BF91ADCCC3CCA3A7216E47AA9D3C99671E98CA80A26683700703B271C84A7 | |||
| 7072 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x42icbgw.biq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
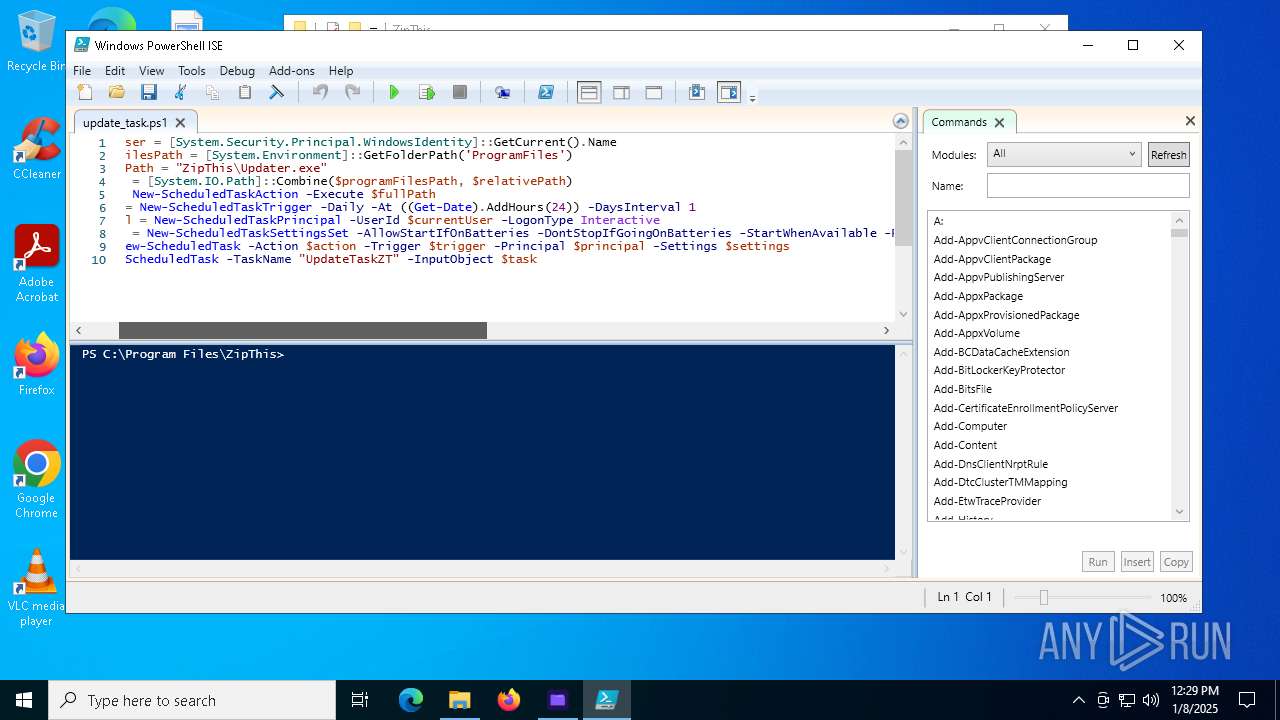
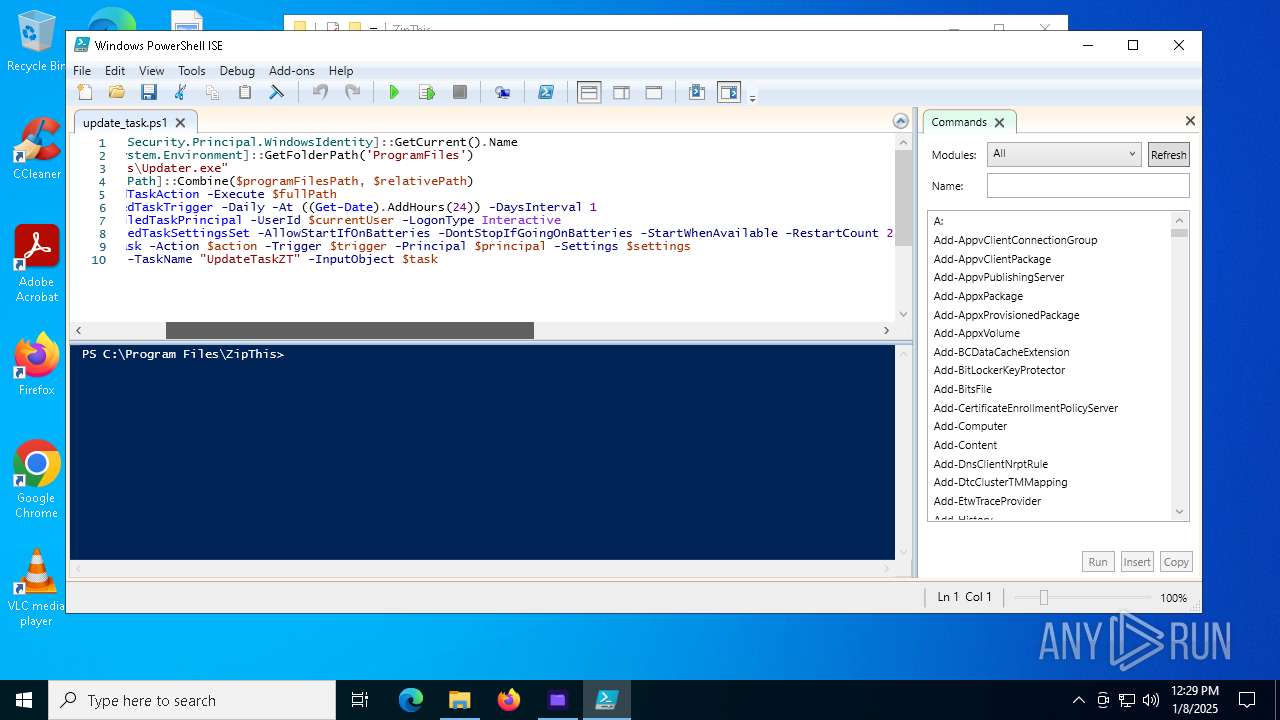
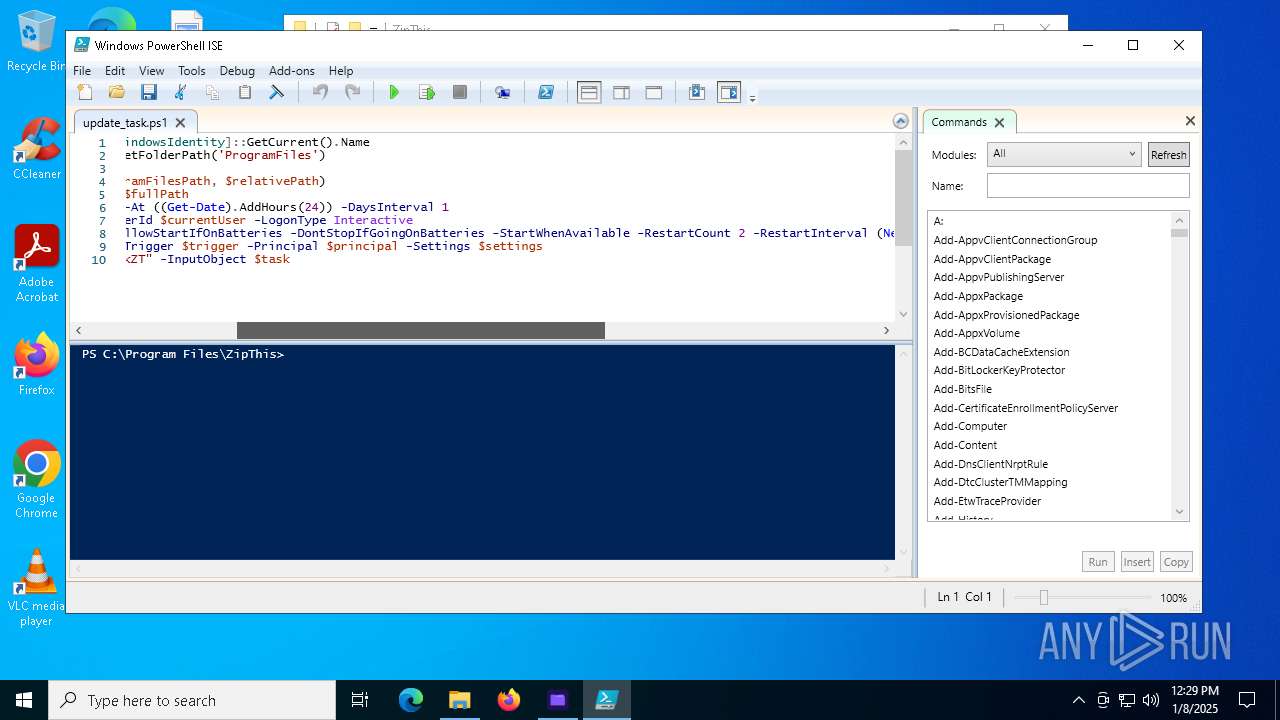
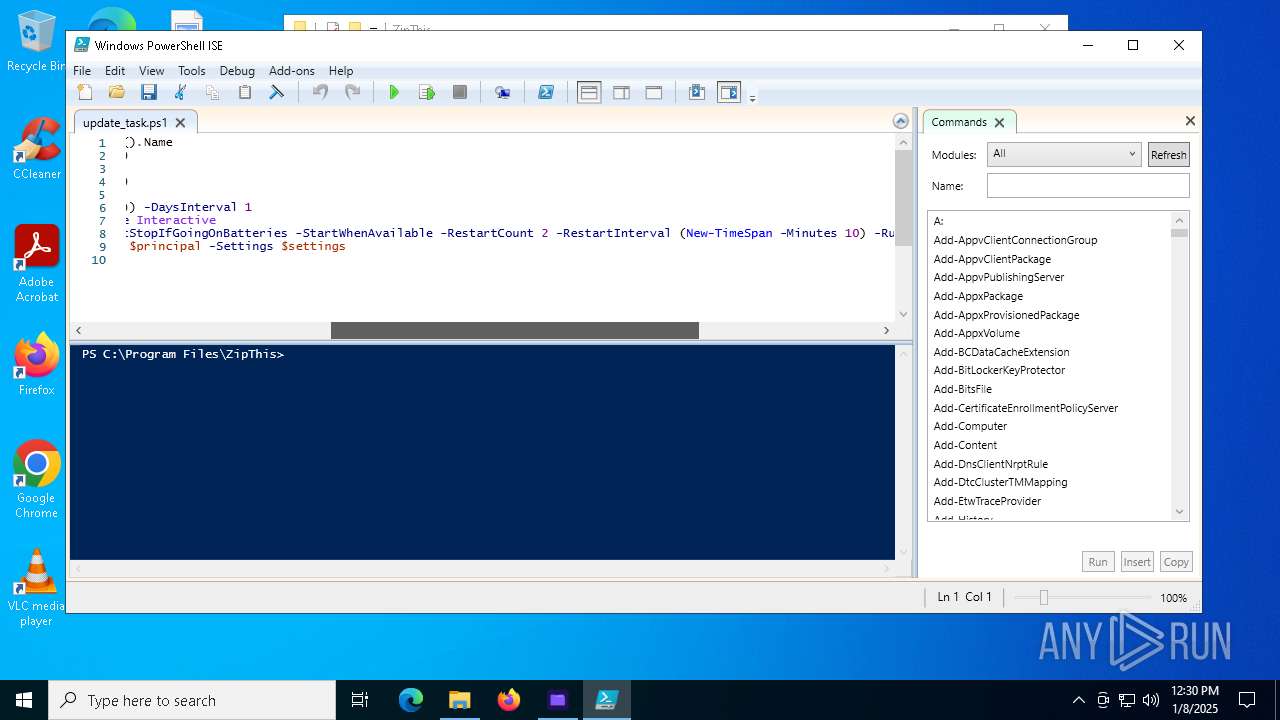
| 6948 | ZipThis.exe | C:\Program Files\ZipThis\update_task.ps1 | text | |
MD5:2E5B6F2E387430EF627CF666FBBE0D12 | SHA256:94BBDE99705BF63A3110D592967BE352DC087D4B36AF71B2F0CC7579507CD520 | |||
| 6948 | ZipThis.exe | C:\Program Files\ZipThis\Updates.zip | compressed | |
MD5:7D7BA0D8F434806AF1BF8D5BC4A7A24D | SHA256:89EC24BA9EF706931C92B09D204552966D90F9456C8D95FB40B431349FB80BCB | |||
| 6948 | ZipThis.exe | C:\Program Files\ZipThis\Updater.exe | executable | |
MD5:9E422FC4D80CBE24A897B5A662ABC231 | SHA256:2ECBF92A5F8DC19A1482649B496C2FE35E25093CE4306C3DAA58D8D10BDD9CFB | |||
| 6948 | ZipThis.exe | C:\Program Files\ZipThis\Updater.dll | executable | |
MD5:DDB033FE6D3A637C139E50F8E02F2A46 | SHA256:F4E2FA0CFA28C629D68D7CBE17394BAE54B7EADB563A3EA56D152769914832CD | |||
| 6948 | ZipThis.exe | C:\Program Files\ZipThis\msvcp140.dll | executable | |
MD5:C3D497B0AFEF4BD7E09C7559E1C75B05 | SHA256:1E57A6DF9E3742E31A1C6D9BFF81EBEEAE8A7DE3B45A26E5079D5E1CCE54CD98 | |||
| 6948 | ZipThis.exe | C:\Program Files\ZipThis\vcamp140.dll | executable | |
MD5:8441A618D2CEF67BDEDCA224FD61AFA2 | SHA256:6CD300E597C477260809C5CA036993D923CD8BE304AE323C9C4D7776115FE62D | |||
| 6948 | ZipThis.exe | C:\Program Files\ZipThis\vcomp140.dll | executable | |
MD5:EF76327FF132A48F3BAC24598C99B373 | SHA256:D49B394DE1154176B39611C37C669EBFF50AA5A818DBD5FF3D2214A299368DDD | |||
| 6948 | ZipThis.exe | C:\Program Files\ZipThis\msvcp140_1.dll | executable | |
MD5:7B0A25EEE764D8747F02CB3ED980F07A | SHA256:1274292F4CC655F295272B37E08A9683B8BB8C419B61EA2E1F43EB4D22F02F90 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
79
DNS requests
84
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4536 | svchost.exe | GET | 200 | 95.101.142.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.142.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4536 | svchost.exe | GET | 200 | 95.101.172.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.172.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4976 | powershell_ise.exe | GET | 200 | 104.84.152.74:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6168 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4976 | powershell_ise.exe | GET | 200 | 95.101.172.129:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
6940 | SIHClient.exe | GET | 200 | 95.101.172.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4712 | MoUsoCoreWorker.exe | 95.101.142.8:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
4536 | svchost.exe | 95.101.142.8:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
4536 | svchost.exe | 95.101.172.129:80 | www.microsoft.com | AKAMAI-AS | SE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.172.129:80 | www.microsoft.com | AKAMAI-AS | SE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.18.29.123:443 | www.bing.com | Akamai International B.V. | PL | whitelisted |
4952 | ZipThis.exe | 45.33.84.9:443 | apb.thisilient.com | Linode, LLC | US | unknown |
1176 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
apb.thisilient.com |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4592 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] BootstrapCDN (stackpath .bootstrapcdn .com) |
4592 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
4592 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
4592 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
4592 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] BootstrapCDN (stackpath .bootstrapcdn .com) |
4592 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
4592 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
4592 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
4592 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
4592 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |