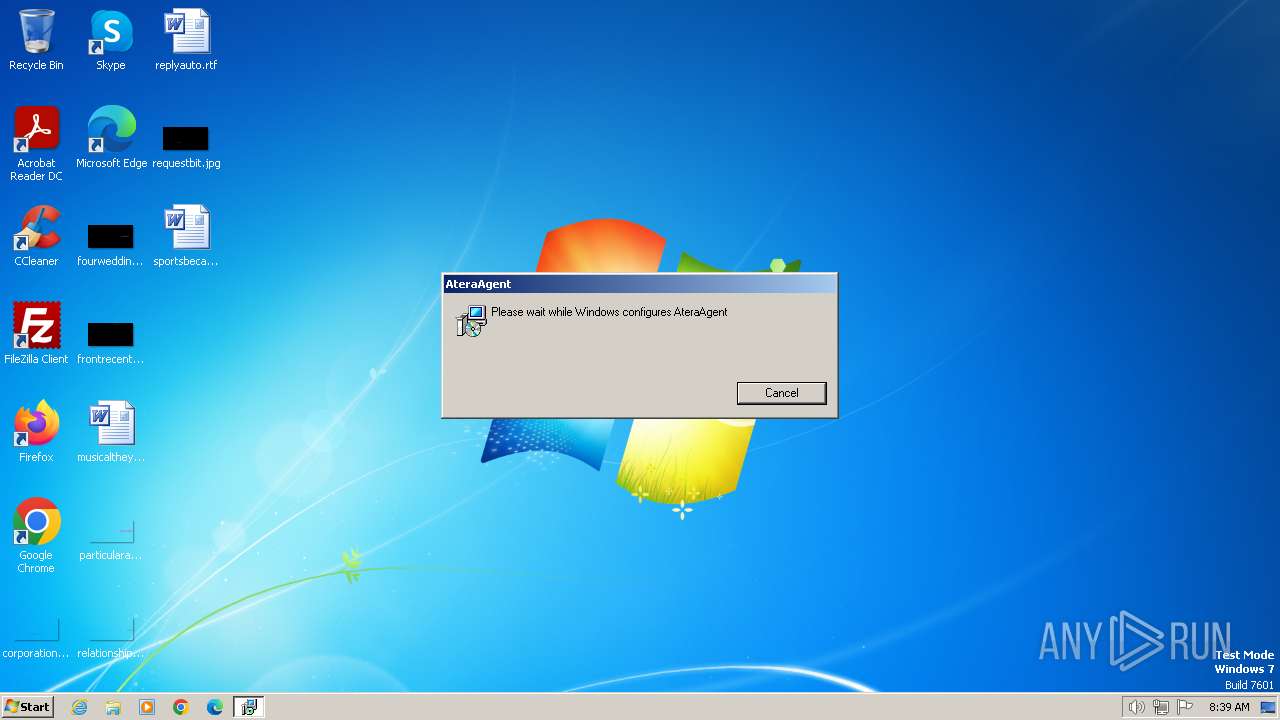
| File name: | setup.msi |
| Full analysis: | https://app.any.run/tasks/573debb2-f716-4599-90df-4957e108422d |
| Verdict: | Malicious activity |
| Analysis date: | March 29, 2024, 08:39:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: AteraAgent, Author: Atera networks, Keywords: Installer, Comments: This installer database contains the logic and data required to install AteraAgent., Template: Intel;1033, Revision Number: {721AD955-79FD-4019-BBF5-9DCC4C1175BB}, Create Time/Date: Wed Feb 28 10:52:02 2024, Last Saved Time/Date: Wed Feb 28 10:52:02 2024, Number of Pages: 200, Number of Words: 6, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | CE1F52A3BC7007D5B7AF096B89B39252 |
| SHA1: | A575CAFD73FC9AB5E5D0D6AECA3341E5D05F7EFF |
| SHA256: | 91C4F308AEDBD3C2DD1B21C40A3393DE0BB5F0C6C28BA56F64F6BE8BDCCBF6D2 |
| SSDEEP: | 98304:4IZTffzvns6eLKLdpRwznfsJb+7J7ERXndiWaKzPtSjXmbABY/lT8vjkZBvrePVv:93XP9No |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 4008)
- AteraAgent.exe (PID: 2640)
- AgentPackageUpgradeAgent.exe (PID: 1596)
- AgentPackageTicketing.exe (PID: 1636)
- SplashtopStreamer.exe (PID: 3912)
- PreVerCheck.exe (PID: 2540)
- uninst.exe (PID: 3204)
- Au_.exe (PID: 2108)
- AteraAgent.exe (PID: 3872)
Creates a writable file in the system directory
- AteraAgent.exe (PID: 2640)
- AteraAgent.exe (PID: 3872)
- powershell.exe (PID: 3816)
- SRManager.exe (PID: 908)
- SRServer.exe (PID: 3768)
Accesses system services(Win32_Service) via WMI (SCRIPT)
- cscript.exe (PID: 1236)
- cscript.exe (PID: 1336)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 3768)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 2572)
- AteraAgent.exe (PID: 2640)
- AteraAgent.exe (PID: 3872)
- SSUService.exe (PID: 1936)
- SRService.exe (PID: 3972)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 2640)
- AteraAgent.exe (PID: 3872)
- cmd.exe (PID: 3816)
- cmd.exe (PID: 2500)
Reads security settings of Internet Explorer
- AteraAgent.exe (PID: 2640)
- AteraAgent.exe (PID: 3872)
- AgentPackageAgentInformation.exe (PID: 3548)
- AgentPackageAgentInformation.exe (PID: 2948)
- AgentPackageAgentInformation.exe (PID: 1732)
- SplashtopStreamer.exe (PID: 3912)
- SRServer.exe (PID: 3768)
Searches for installed software
- AgentPackageAgentInformation.exe (PID: 2948)
- AgentPackageAgentInformation.exe (PID: 3548)
- AgentPackageAgentInformation.exe (PID: 1732)
- AgentPackageProgramManagement.exe (PID: 2244)
The process executes VB scripts
- cmd.exe (PID: 2832)
- cmd.exe (PID: 1844)
- cmd.exe (PID: 1592)
- cmd.exe (PID: 2548)
- cmd.exe (PID: 2524)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 1236)
- cscript.exe (PID: 1336)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 3768)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 1236)
- cscript.exe (PID: 1336)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 3768)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 1236)
- cscript.exe (PID: 1336)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 3768)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 1236)
- cscript.exe (PID: 1336)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 3768)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 1236)
- cscript.exe (PID: 1336)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 3768)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 1236)
- cscript.exe (PID: 1336)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 3768)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 3548)
- AgentPackageAgentInformation.exe (PID: 2948)
- AgentPackageAgentInformation.exe (PID: 1732)
- SRServer.exe (PID: 3768)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 1236)
- cscript.exe (PID: 1336)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 3768)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 1336)
- cscript.exe (PID: 1236)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 3768)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- cscript.exe (PID: 1336)
- cscript.exe (PID: 1236)
Process drops legitimate windows executable
- AteraAgent.exe (PID: 2640)
- AteraAgent.exe (PID: 3872)
- AgentPackageUpgradeAgent.exe (PID: 1596)
Starts itself from another location
- AgentPackageUpgradeAgent.exe (PID: 1596)
- uninst.exe (PID: 3204)
The process creates files with name similar to system file names
- AteraAgent.exe (PID: 3872)
- Au_.exe (PID: 2108)
Identifying current user with WHOAMI command
- powershell.exe (PID: 3816)
Starts POWERSHELL.EXE for commands execution
- AgentPackageRunCommandInteractive.exe (PID: 3608)
- AgentPackageRunCommandInteractive.exe (PID: 3628)
Checks Windows Trust Settings
- SRManager.exe (PID: 908)
Creates or modifies Windows services
- SRManager.exe (PID: 908)
Starts NET.EXE to map network drives
- powershell.exe (PID: 2024)
INFO
Reads the software policy settings
- msiexec.exe (PID: 4008)
- AgentPackageAgentInformation.exe (PID: 2080)
- AgentPackageAgentInformation.exe (PID: 2880)
- AteraAgent.exe (PID: 2640)
- AteraAgent.exe (PID: 3872)
- AgentPackageAgentInformation.exe (PID: 908)
- AgentPackageAgentInformation.exe (PID: 3600)
- AgentPackageMonitoring.exe (PID: 916)
- AgentPackageAgentInformation.exe (PID: 2948)
- AgentPackageMonitoring.exe (PID: 992)
- AgentPackageAgentInformation.exe (PID: 3548)
- AgentPackageInternalPoller.exe (PID: 2000)
- AgentPackageProgramManagement.exe (PID: 2244)
- AgentPackageSTRemote.exe (PID: 2904)
- AgentPackageAgentInformation.exe (PID: 1732)
- AgentPackageHeartbeat.exe (PID: 896)
- AgentPackageTicketing.exe (PID: 1636)
- AgentPackageMonitoring.exe (PID: 3536)
- AgentPackageMarketplace.exe (PID: 268)
- AgentPackageHeartbeat.exe (PID: 2260)
- AgentPackageRunCommandInteractive.exe (PID: 3608)
- SRManager.exe (PID: 908)
- AgentPackageHeartbeat.exe (PID: 1172)
- AgentPackageHeartbeat.exe (PID: 3012)
- AgentPackageTaskManagement.exe (PID: 4028)
- AgentPackageServicesCommands.exe (PID: 1028)
- AgentPackageSystemTools.exe (PID: 2056)
- AgentPackageHeartbeat.exe (PID: 2368)
- AgentPackageHeartbeat.exe (PID: 4024)
- AgentPackageRunCommandInteractive.exe (PID: 3628)
- AgentPackageHeartbeat.exe (PID: 2364)
Checks supported languages
- AteraAgent.exe (PID: 2640)
- AgentPackageAgentInformation.exe (PID: 2880)
- AgentPackageAgentInformation.exe (PID: 2080)
- AgentPackageAgentInformation.exe (PID: 3576)
- AgentPackageAgentInformation.exe (PID: 3548)
- AgentPackageAgentInformation.exe (PID: 2948)
- AgentPackageAgentInformation.exe (PID: 908)
- AgentPackageAgentInformation.exe (PID: 3600)
- AteraAgent.exe (PID: 3872)
- AgentPackageMonitoring.exe (PID: 992)
- AgentPackageMonitoring.exe (PID: 916)
- wmpnscfg.exe (PID: 3576)
- AgentPackageAgentInformation.exe (PID: 1732)
- AgentPackageInternalPoller.exe (PID: 2000)
- AgentPackageUpgradeAgent.exe (PID: 1596)
- AgentPackageSTRemote.exe (PID: 2904)
- AgentPackageTicketing.exe (PID: 1636)
- AgentPackageUpgradeAgent.exe (PID: 1368)
- AgentPackageProgramManagement.exe (PID: 2244)
- AgentPackageOsUpdates.exe (PID: 2092)
- AgentPackageHeartbeat.exe (PID: 896)
- AgentPackageSystemTools.exe (PID: 2768)
- AgentPackageRuntimeInstaller.exe (PID: 2856)
- AgentPackageMarketplace.exe (PID: 268)
- AgentPackageMonitoring.exe (PID: 3536)
- AgentPackageRunCommandInteractive.exe (PID: 3608)
- AgentPackageADRemote.exe (PID: 4032)
- SplashtopStreamer.exe (PID: 3912)
- AgentPackageHeartbeat.exe (PID: 2260)
- SRService.exe (PID: 3972)
- SRManager.exe (PID: 908)
- PreVerCheck.exe (PID: 2540)
- AgentPackageHeartbeat.exe (PID: 1172)
- SSUService.exe (PID: 1936)
- SRAgent.exe (PID: 3496)
- SRAppPB.exe (PID: 3068)
- SRServer.exe (PID: 3768)
- SRDetect.exe (PID: 2900)
- Au_.exe (PID: 2108)
- SRUtility.exe (PID: 2016)
- SRUtility.exe (PID: 900)
- SRFeature.exe (PID: 3236)
- uninst.exe (PID: 3204)
- AgentPackageMonitoring.exe (PID: 2592)
- AgentPackageTaskManagement.exe (PID: 4028)
- BdEpSDK_x86.exe (PID: 3652)
- AgentPackageSTRemote.exe (PID: 2172)
- AgentPackageInternalPoller.exe (PID: 3876)
- SRVirtualDisplay.exe (PID: 912)
- AgentPackageHeartbeat.exe (PID: 3012)
- AgentPackageSystemTools.exe (PID: 2056)
- AgentPackageServicesCommands.exe (PID: 1028)
- AgentPackageHeartbeat.exe (PID: 4024)
- AgentPackageHeartbeat.exe (PID: 2368)
- AgentPackageSTRemote.exe (PID: 1036)
- AgentPackageRunCommandInteractive.exe (PID: 3628)
- AgentPackageMonitoring.exe (PID: 1636)
- AgentPackageSTRemote.exe (PID: 4088)
- AgentPackageHeartbeat.exe (PID: 2364)
- IdleTimeFinder.exe (PID: 316)
Reads the computer name
- AteraAgent.exe (PID: 2640)
- AgentPackageAgentInformation.exe (PID: 2080)
- AgentPackageAgentInformation.exe (PID: 2880)
- AgentPackageAgentInformation.exe (PID: 3600)
- AgentPackageAgentInformation.exe (PID: 3576)
- AgentPackageAgentInformation.exe (PID: 3548)
- AgentPackageAgentInformation.exe (PID: 908)
- AteraAgent.exe (PID: 3872)
- AgentPackageAgentInformation.exe (PID: 2948)
- AgentPackageMonitoring.exe (PID: 916)
- AgentPackageMonitoring.exe (PID: 992)
- wmpnscfg.exe (PID: 3576)
- AgentPackageAgentInformation.exe (PID: 1732)
- AgentPackageInternalPoller.exe (PID: 2000)
- AgentPackageUpgradeAgent.exe (PID: 1596)
- AgentPackageSTRemote.exe (PID: 2904)
- AgentPackageTicketing.exe (PID: 1636)
- AgentPackageUpgradeAgent.exe (PID: 1368)
- AgentPackageProgramManagement.exe (PID: 2244)
- AgentPackageOsUpdates.exe (PID: 2092)
- AgentPackageSystemTools.exe (PID: 2768)
- AgentPackageHeartbeat.exe (PID: 896)
- AgentPackageMarketplace.exe (PID: 268)
- AgentPackageMonitoring.exe (PID: 3536)
- AgentPackageRuntimeInstaller.exe (PID: 2856)
- AgentPackageRunCommandInteractive.exe (PID: 3608)
- AgentPackageADRemote.exe (PID: 4032)
- SplashtopStreamer.exe (PID: 3912)
- AgentPackageHeartbeat.exe (PID: 2260)
- SRService.exe (PID: 3972)
- SSUService.exe (PID: 1936)
- AgentPackageHeartbeat.exe (PID: 1172)
- SRAgent.exe (PID: 3496)
- SRAppPB.exe (PID: 3068)
- SRManager.exe (PID: 908)
- SRServer.exe (PID: 3768)
- SRFeature.exe (PID: 3236)
- Au_.exe (PID: 2108)
- uninst.exe (PID: 3204)
- AgentPackageMonitoring.exe (PID: 2592)
- AgentPackageSTRemote.exe (PID: 2172)
- AgentPackageInternalPoller.exe (PID: 3876)
- AgentPackageTaskManagement.exe (PID: 4028)
- AgentPackageHeartbeat.exe (PID: 3012)
- AgentPackageSystemTools.exe (PID: 2056)
- IdleTimeFinder.exe (PID: 316)
- AgentPackageServicesCommands.exe (PID: 1028)
- AgentPackageHeartbeat.exe (PID: 4024)
- AgentPackageSTRemote.exe (PID: 1036)
- AgentPackageHeartbeat.exe (PID: 2368)
- AgentPackageRunCommandInteractive.exe (PID: 3628)
- AgentPackageMonitoring.exe (PID: 1636)
- AgentPackageHeartbeat.exe (PID: 2364)
- AgentPackageSTRemote.exe (PID: 4088)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 4008)
Reads the machine GUID from the registry
- AteraAgent.exe (PID: 2640)
- AgentPackageAgentInformation.exe (PID: 2080)
- AgentPackageAgentInformation.exe (PID: 2880)
- AgentPackageAgentInformation.exe (PID: 3600)
- AgentPackageAgentInformation.exe (PID: 3548)
- AgentPackageAgentInformation.exe (PID: 3576)
- AgentPackageAgentInformation.exe (PID: 908)
- AgentPackageAgentInformation.exe (PID: 2948)
- AteraAgent.exe (PID: 3872)
- AgentPackageMonitoring.exe (PID: 916)
- AgentPackageMonitoring.exe (PID: 992)
- AgentPackageAgentInformation.exe (PID: 1732)
- AgentPackageInternalPoller.exe (PID: 2000)
- AgentPackageUpgradeAgent.exe (PID: 1596)
- AgentPackageSTRemote.exe (PID: 2904)
- AgentPackageUpgradeAgent.exe (PID: 1368)
- AgentPackageProgramManagement.exe (PID: 2244)
- AgentPackageTicketing.exe (PID: 1636)
- AgentPackageHeartbeat.exe (PID: 896)
- AgentPackageOsUpdates.exe (PID: 2092)
- AgentPackageMonitoring.exe (PID: 3536)
- AgentPackageRuntimeInstaller.exe (PID: 2856)
- AgentPackageSystemTools.exe (PID: 2768)
- AgentPackageADRemote.exe (PID: 4032)
- AgentPackageRunCommandInteractive.exe (PID: 3608)
- AgentPackageMarketplace.exe (PID: 268)
- AgentPackageHeartbeat.exe (PID: 2260)
- SRManager.exe (PID: 908)
- AgentPackageHeartbeat.exe (PID: 1172)
- SSUService.exe (PID: 1936)
- SRAgent.exe (PID: 3496)
- AgentPackageSTRemote.exe (PID: 2172)
- AgentPackageMonitoring.exe (PID: 2592)
- AgentPackageTaskManagement.exe (PID: 4028)
- AgentPackageInternalPoller.exe (PID: 3876)
- AgentPackageHeartbeat.exe (PID: 3012)
- AgentPackageSystemTools.exe (PID: 2056)
- IdleTimeFinder.exe (PID: 316)
- AgentPackageServicesCommands.exe (PID: 1028)
- AgentPackageSTRemote.exe (PID: 1036)
- AgentPackageHeartbeat.exe (PID: 2368)
- AgentPackageRunCommandInteractive.exe (PID: 3628)
- AgentPackageHeartbeat.exe (PID: 4024)
- AgentPackageMonitoring.exe (PID: 1636)
- AgentPackageSTRemote.exe (PID: 4088)
- AgentPackageHeartbeat.exe (PID: 2364)
Reads Environment values
- AgentPackageAgentInformation.exe (PID: 2080)
- AteraAgent.exe (PID: 2640)
- AgentPackageAgentInformation.exe (PID: 2880)
- AgentPackageAgentInformation.exe (PID: 908)
- AgentPackageAgentInformation.exe (PID: 3600)
- AgentPackageAgentInformation.exe (PID: 3576)
- AgentPackageAgentInformation.exe (PID: 3548)
- AgentPackageAgentInformation.exe (PID: 2948)
- AteraAgent.exe (PID: 3872)
- AgentPackageMonitoring.exe (PID: 916)
- AgentPackageMonitoring.exe (PID: 992)
- AgentPackageAgentInformation.exe (PID: 1732)
- AgentPackageInternalPoller.exe (PID: 2000)
- AgentPackageUpgradeAgent.exe (PID: 1596)
- AgentPackageUpgradeAgent.exe (PID: 1368)
- AgentPackageSTRemote.exe (PID: 2904)
- AgentPackageProgramManagement.exe (PID: 2244)
- AgentPackageTicketing.exe (PID: 1636)
- AgentPackageHeartbeat.exe (PID: 896)
- AgentPackageOsUpdates.exe (PID: 2092)
- AgentPackageMonitoring.exe (PID: 3536)
- AgentPackageSystemTools.exe (PID: 2768)
- AgentPackageRunCommandInteractive.exe (PID: 3608)
- AgentPackageMarketplace.exe (PID: 268)
- AgentPackageADRemote.exe (PID: 4032)
- AgentPackageHeartbeat.exe (PID: 2260)
- AgentPackageHeartbeat.exe (PID: 1172)
- AgentPackageMonitoring.exe (PID: 2592)
- SRManager.exe (PID: 908)
- AgentPackageSTRemote.exe (PID: 2172)
- AgentPackageHeartbeat.exe (PID: 3012)
- AgentPackageTaskManagement.exe (PID: 4028)
- AgentPackageInternalPoller.exe (PID: 3876)
- AgentPackageServicesCommands.exe (PID: 1028)
- AgentPackageSystemTools.exe (PID: 2056)
- AgentPackageSTRemote.exe (PID: 1036)
- AgentPackageHeartbeat.exe (PID: 2368)
- AgentPackageRunCommandInteractive.exe (PID: 3628)
- AgentPackageHeartbeat.exe (PID: 4024)
- AgentPackageMonitoring.exe (PID: 1636)
- AgentPackageHeartbeat.exe (PID: 2364)
- AgentPackageSTRemote.exe (PID: 4088)
Creates files in the program directory
- AteraAgent.exe (PID: 2640)
- AgentPackageMonitoring.exe (PID: 992)
- AgentPackageMonitoring.exe (PID: 916)
- AgentPackageAgentInformation.exe (PID: 2948)
- AteraAgent.exe (PID: 3872)
- AgentPackageInternalPoller.exe (PID: 2000)
- AgentPackageProgramManagement.exe (PID: 2244)
- AgentPackageAgentInformation.exe (PID: 1732)
- AgentPackageSTRemote.exe (PID: 2904)
- AgentPackageTicketing.exe (PID: 1636)
- AgentPackageRuntimeInstaller.exe (PID: 2856)
- AgentPackageOsUpdates.exe (PID: 2092)
- AgentPackageMonitoring.exe (PID: 3536)
- AgentPackageRunCommandInteractive.exe (PID: 3608)
- SRManager.exe (PID: 908)
- SRServer.exe (PID: 3768)
- SRAgent.exe (PID: 3496)
- AgentPackageMonitoring.exe (PID: 2592)
- SRVirtualDisplay.exe (PID: 912)
- AgentPackageSystemTools.exe (PID: 2056)
- AgentPackageMonitoring.exe (PID: 1636)
Reads Microsoft Office registry keys
- AgentPackageAgentInformation.exe (PID: 3548)
- AgentPackageAgentInformation.exe (PID: 2948)
- AgentPackageAgentInformation.exe (PID: 1732)
Manual execution by a user
- wmpnscfg.exe (PID: 3576)
Process checks Powershell version
- AgentPackageRunCommandInteractive.exe (PID: 3608)
- AgentPackageRunCommandInteractive.exe (PID: 3628)
Reads product name
- SRManager.exe (PID: 908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | AteraAgent |
| Author: | Atera networks |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install AteraAgent. |
| Template: | Intel;1033 |
| RevisionNumber: | {721AD955-79FD-4019-BBF5-9DCC4C1175BB} |
| CreateDate: | 2024:02:28 10:52:02 |
| ModifyDate: | 2024:02:28 10:52:02 |
| Pages: | 200 |
| Words: | 6 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
233
Monitored processes
84
Malicious processes
17
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMarketplace\AgentPackageMarketplace.exe" 211260b7-b550-4dfb-9f30-265314e81f24 "dc459b92-576b-474e-9787-61cb31041b34" agent-api.atera.com/Production 443 or8ixLi90Mf "agentprovision" 001Q300000AHAJlIAP | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMarketplace\AgentPackageMarketplace.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageMarketplace Exit code: 0 Version: 1.4.0.0 Modules
| |||||||||||||||
| 316 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageSystemTools\IdleTimeFinder.exe" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageSystemTools\IdleTimeFinder.exe | — | AgentPackageSystemTools.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: ConsoleApp1 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 896 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageHeartbeat\AgentPackageHeartbeat.exe" 211260b7-b550-4dfb-9f30-265314e81f24 "de26c503-58f1-4470-89b9-170817c13823" agent-api.atera.com/Production 443 or8ixLi90Mf "heartbeat" 001Q300000AHAJlIAP | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageHeartbeat\AgentPackageHeartbeat.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageHeartbeat Exit code: 0 Version: 17.14.0.0 Modules
| |||||||||||||||
| 900 | "C:\Program Files\Splashtop\Splashtop Remote\Server\SRUtility.exe" -a "st-streamer://com.splashtop.streamer/?rmm_session_pwd=0253780d69c3859475ba972f16573df3&rmm_session_pwd_ttl=86400" | C:\Program Files\Splashtop\Splashtop Remote\Server\SRUtility.exe | — | AgentPackageSTRemote.exe | |||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop® Streamer Utility Exit code: 0 Version: 3.64.1.122 Modules
| |||||||||||||||
| 908 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe" 211260b7-b550-4dfb-9f30-265314e81f24 "2aad265d-7143-4f81-b52e-34c02c89f0b5" agent-api.atera.com/Production 443 or8ixLi90Mf "minimalIdentification" 001Q300000AHAJlIAP | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageAgentInformation Exit code: 0 Version: 36.3.0.0 Modules
| |||||||||||||||
| 908 | "C:\Program Files\Splashtop\Splashtop Remote\Server\SRManager.exe" | C:\Program Files\Splashtop\Splashtop Remote\Server\SRManager.exe | SRService.exe | ||||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop® Streamer SRManager Version: 3.64.1.122 Modules
| |||||||||||||||
| 912 | "C:\Program Files\Splashtop\Splashtop Remote\Server\SRVirtualDisplay.exe" | C:\Program Files\Splashtop\Splashtop Remote\Server\SRVirtualDisplay.exe | — | SRManager.exe | |||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop Streamer Virtual Monitor Utility Version: 3.64.1.122 Modules
| |||||||||||||||
| 916 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\AgentPackageMonitoring.exe" 211260b7-b550-4dfb-9f30-265314e81f24 "c886d556-165b-4d35-879d-38ba1ce59672" agent-api.atera.com/Production 443 or8ixLi90Mf "syncprofile" 001Q300000AHAJlIAP | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\AgentPackageMonitoring.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageMonitoring Exit code: 0 Version: 36.4.0.0 Modules
| |||||||||||||||
| 992 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\AgentPackageMonitoring.exe" 211260b7-b550-4dfb-9f30-265314e81f24 "6df87ade-9cdc-4cf5-bcf8-b62da233787f" agent-api.atera.com/Production 443 or8ixLi90Mf "syncprofile" 001Q300000AHAJlIAP | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\AgentPackageMonitoring.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageMonitoring Exit code: 0 Version: 36.4.0.0 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageServicesCommands\AgentPackageServicesCommands.exe" 211260b7-b550-4dfb-9f30-265314e81f24 "bc06f741-1428-4552-9738-acfc393459f8" agent-api.atera.com/Production 443 or8ixLi90Mf "query_services" 001Q300000AHAJlIAP | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageServicesCommands\AgentPackageServicesCommands.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageServicesCommands Exit code: 0 Version: 16.1.0.0 Modules
| |||||||||||||||
Total events
177 038
Read events
175 944
Write events
1 001
Delete events
93
Modification events
| (PID) Process: | (4008) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2572) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000005A2C81A4B481DA010C0A000074090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2572) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000005A2C81A4B481DA010C0A0000840A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2572) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000005A2C81A4B481DA010C0A0000A00D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2572) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000005A2C81A4B481DA010C0A0000C40A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2572) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000B48E83A4B481DA010C0A0000840A0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2572) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000000EF185A4B481DA010C0A000074090000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2572) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000000EF185A4B481DA010C0A0000A00D0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2572) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000000EF185A4B481DA010C0A0000C40A0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2572) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SwProvider_{b5946137-7b9f-4925-af80-51abd60b20d5} |
| Operation: | write | Name: | PROVIDER_BEGINPREPARE (Enter) |
Value: 4000000000000000D47773A6B481DA010C0A0000C40A000001040000010000000000000000000000F527F2C889F54D4083AAB092D1797F6B0000000000000000 | |||
Executable files
365
Suspicious files
26
Text files
72
Unknown types
89
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2640 | AteraAgent.exe | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation.zip | compressed | |
MD5:— | SHA256:— | |||
| 2640 | AteraAgent.exe | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe | executable | |
MD5:— | SHA256:— | |||
| 2640 | AteraAgent.exe | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe.config | xml | |
MD5:— | SHA256:— | |||
| 2640 | AteraAgent.exe | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.ini | text | |
MD5:— | SHA256:— | |||
| 2640 | AteraAgent.exe | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\Atera.AgentPackage.Common.dll | executable | |
MD5:— | SHA256:— | |||
| 2640 | AteraAgent.exe | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\Newtonsoft.Json.dll | executable | |
MD5:— | SHA256:— | |||
| 2640 | AteraAgent.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C56C4404C4DEF0DC88E5FCD9F09CB2F1 | binary | |
MD5:— | SHA256:— | |||
| 2640 | AteraAgent.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C56C4404C4DEF0DC88E5FCD9F09CB2F1 | binary | |
MD5:— | SHA256:— | |||
| 2640 | AteraAgent.exe | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring.zip | compressed | |
MD5:— | SHA256:— | |||
| 2640 | AteraAgent.exe | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\AgentPackageMonitoring.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
88
DNS requests
35
Threats
69
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2760 | AteraAgent.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c42953dd5e0c3a4f | unknown | — | — | unknown |
2760 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
2760 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAooSZl45YmN9AojjrilUug%3D | unknown | — | — | unknown |
2760 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | unknown |
2640 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA3842021CA1.crt | unknown | — | — | unknown |
3872 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAZ%2FYEeVZiSnFZlhdD2BlJM%3D | unknown | — | — | unknown |
908 | SRManager.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAx%2B7MjF4dH7UpJWotMQ8HE%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2488 | rundll32.exe | 40.119.152.241:443 | agent-api.atera.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2760 | AteraAgent.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2760 | AteraAgent.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2640 | AteraAgent.exe | 40.119.152.241:443 | agent-api.atera.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2956 | rundll32.exe | 40.119.152.241:443 | agent-api.atera.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2640 | AteraAgent.exe | 35.157.63.227:443 | ps.pndsn.com | AMAZON-02 | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
agent-api.atera.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ps.pndsn.com |
| unknown |
ps.atera.com |
| unknown |
cacerts.digicert.com |
| whitelisted |
my.splashtop.com |
| unknown |
download.splashtop.com |
| unknown |
api.nuget.org |
| whitelisted |
atera-agent-heartbeat-cus.servicebus.windows.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
2904 | AgentPackageSTRemote.exe | Misc activity | ET INFO Splashtop Domain (splashtop .com) in TLS SNI |
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
2904 | AgentPackageSTRemote.exe | Misc activity | ET INFO Splashtop Domain (splashtop .com) in TLS SNI |
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
908 | SRManager.exe | Misc activity | ET INFO Splashtop Domain (splashtop .com) in TLS SNI |
908 | SRManager.exe | Misc activity | ET INFO Splashtop Domain (splashtop .com) in TLS SNI |
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
1080 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
43 ETPRO signatures available at the full report
Process | Message |
|---|---|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x86\SQLite.Interop.dll"...
|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x86\SQLite.Interop.dll"...
|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x86\SQLite.Interop.dll"...
|
SplashtopStreamer.exe | [3912]2024-03-29 08:41:51 [CUnPack::UnPackFiles] (1/5)UnPack file name:C:\Windows\TEMP\unpack\setup.msi (51506176) (Last=0) |
SplashtopStreamer.exe | [3912]2024-03-29 08:41:51 [CUnPack::UnPackFiles] FreeSpace:233162358784 FileSize:51506176 (Last=0) |
SplashtopStreamer.exe | [3912]2024-03-29 08:41:51 [CUnPack::FindHeader] Sign Size:10248 (Last=0) |
SplashtopStreamer.exe | [3912]2024-03-29 08:41:51 [CUnPack::FindHeader] Header offset:434176 (Last=183) |
SplashtopStreamer.exe | [3912]2024-03-29 08:41:51 [CUnPack::FindHeader] Name:C:\Windows\TEMP\SplashtopStreamer.exe (Last=0) |
SplashtopStreamer.exe | [3912]2024-03-29 08:41:51 [CUtility::OSInfo] OS 6.1(7601) Service Pack 1 x64:0 (Last=0) |
SplashtopStreamer.exe | [3912]2024-03-29 08:41:52 [CUnPack::UnPackFiles] FreeSpace:233110847488 FileSize:1528 (Last=183) |