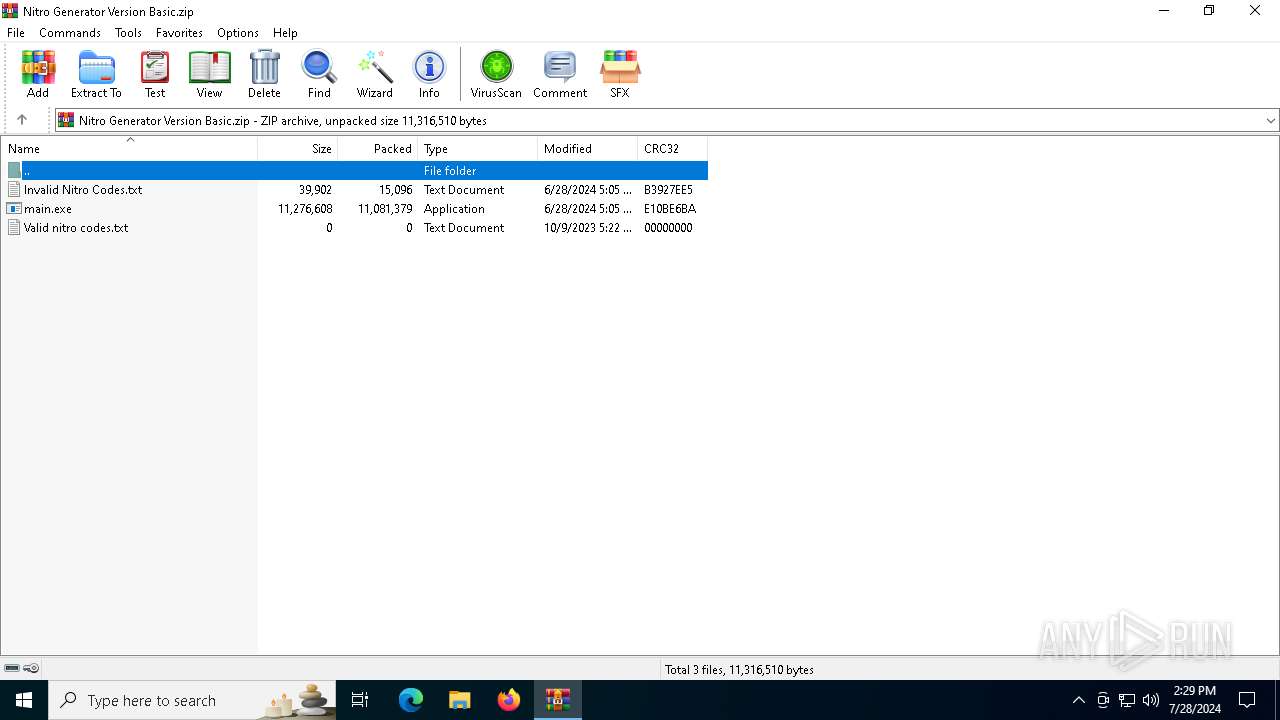
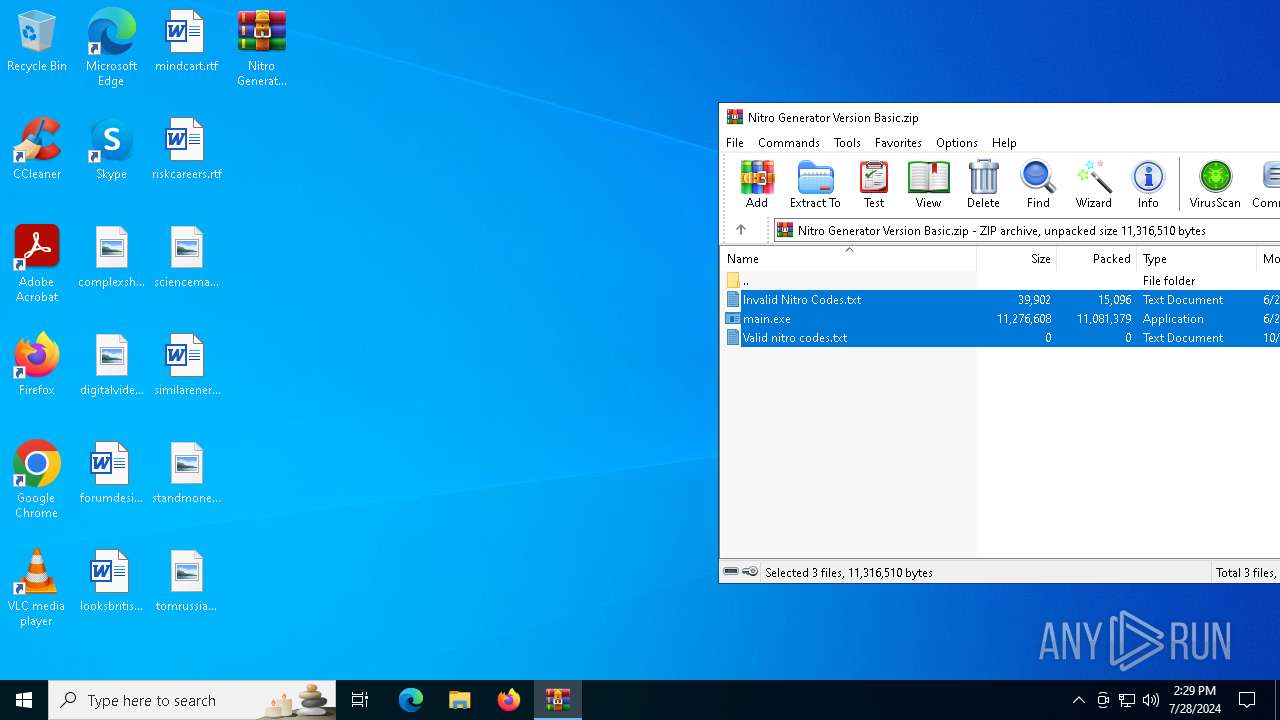
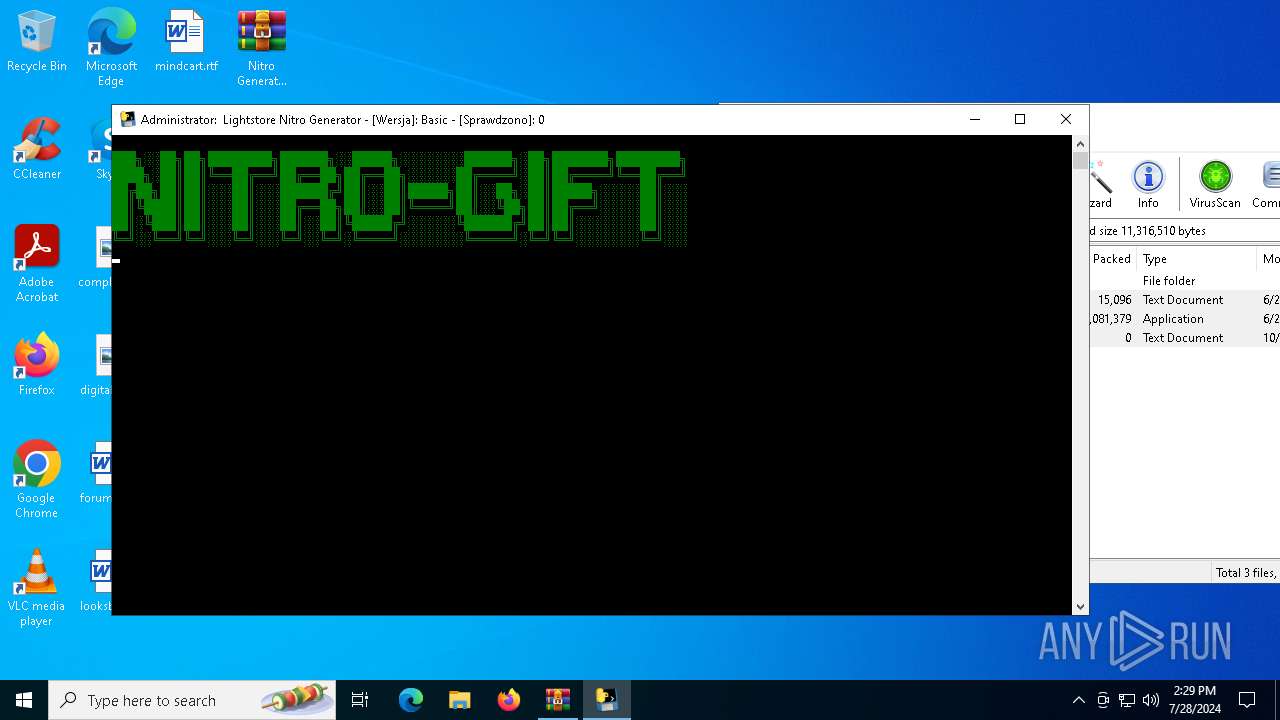
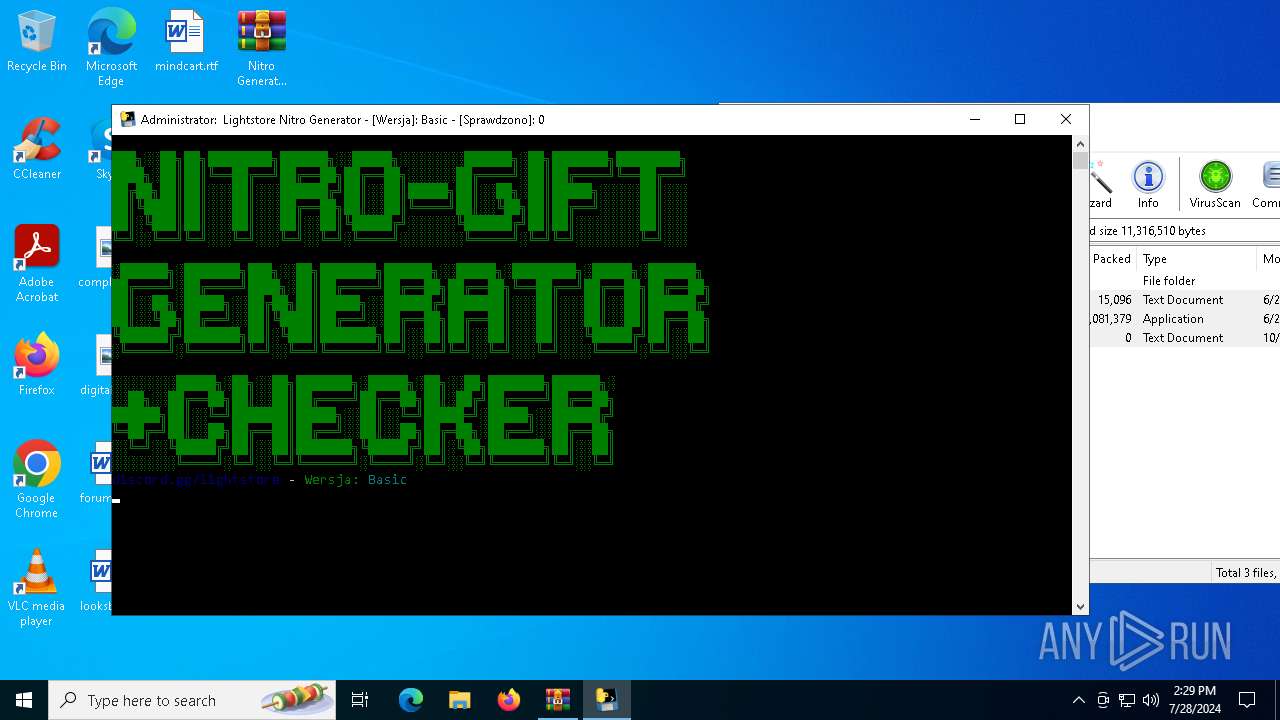
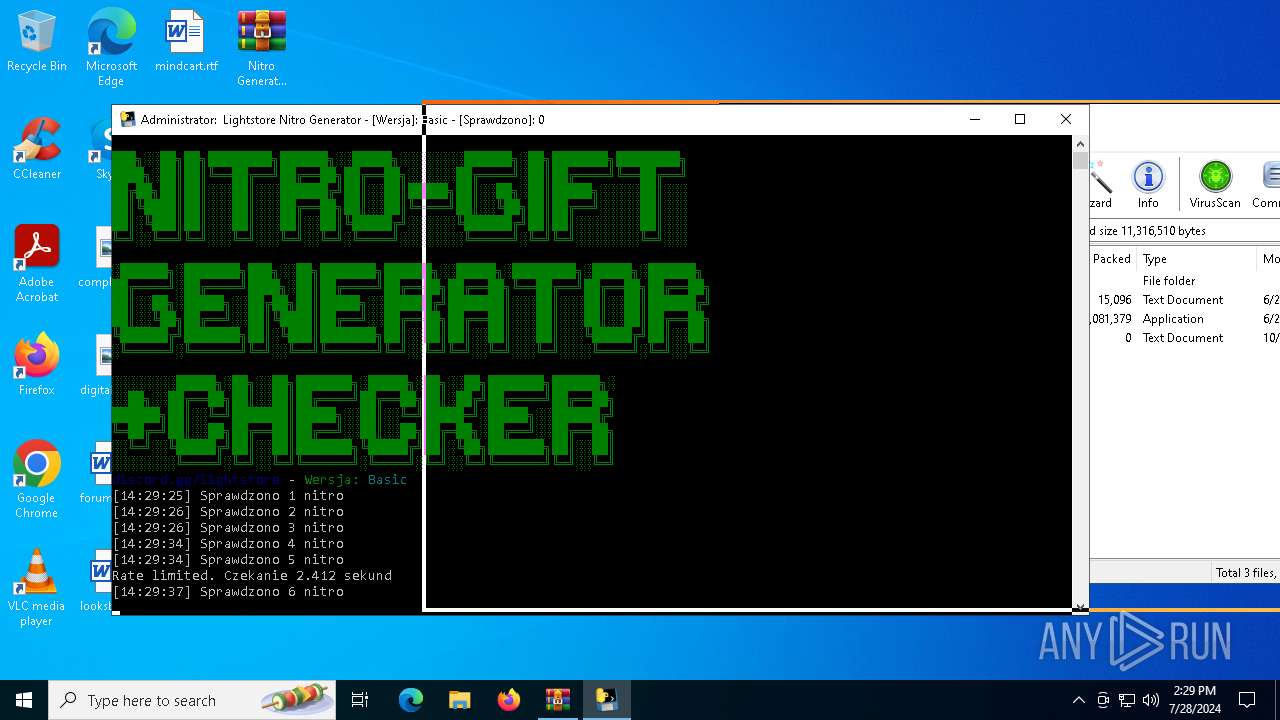
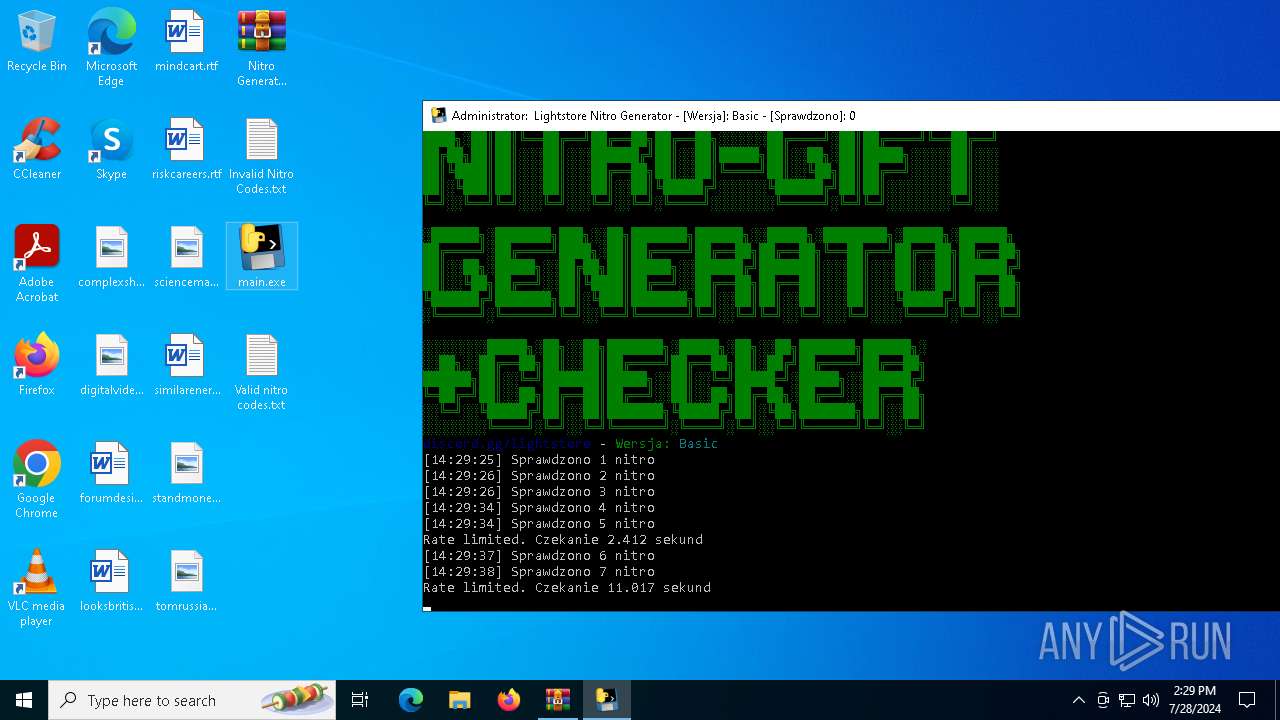
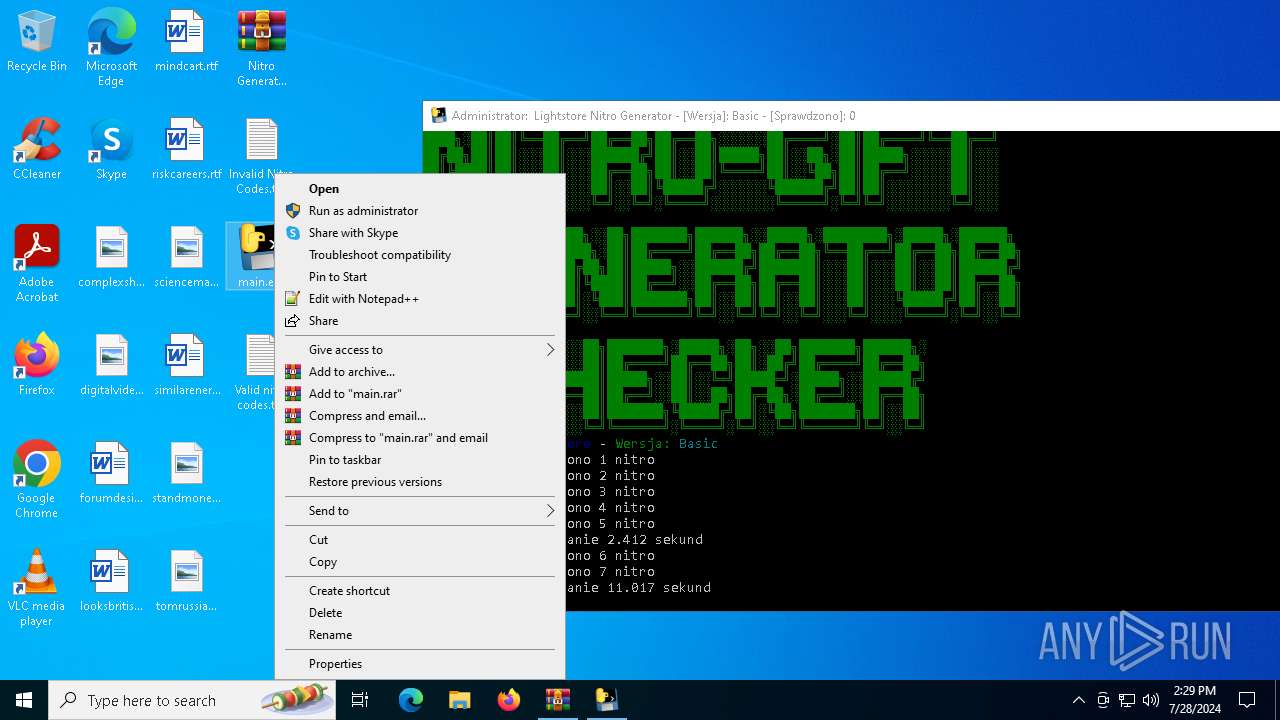
| File name: | Nitro Generator Version Basic.zip |
| Full analysis: | https://app.any.run/tasks/772f0a08-e11b-4717-ab53-3444d87eb7a1 |
| Verdict: | Malicious activity |
| Analysis date: | July 28, 2024, 14:28:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 63A74FB44329355FD2F0887D31AB1F84 |
| SHA1: | 519BF3C33D6F447F4471D906ADA6B91F3FB8BBE9 |
| SHA256: | 91BF6EDCF467BFBFC2F6B2BF0800CBAEAAFB5F67413175C1DB270893AAA22693 |
| SSDEEP: | 98304:xnjcuwMUB8EWJsEjk/Rv4VTcBtm0epG5UuIZ+/CRgLOI+Z7UVb0VP6kdLgYug/HP:mVy/R1Mjm6y |
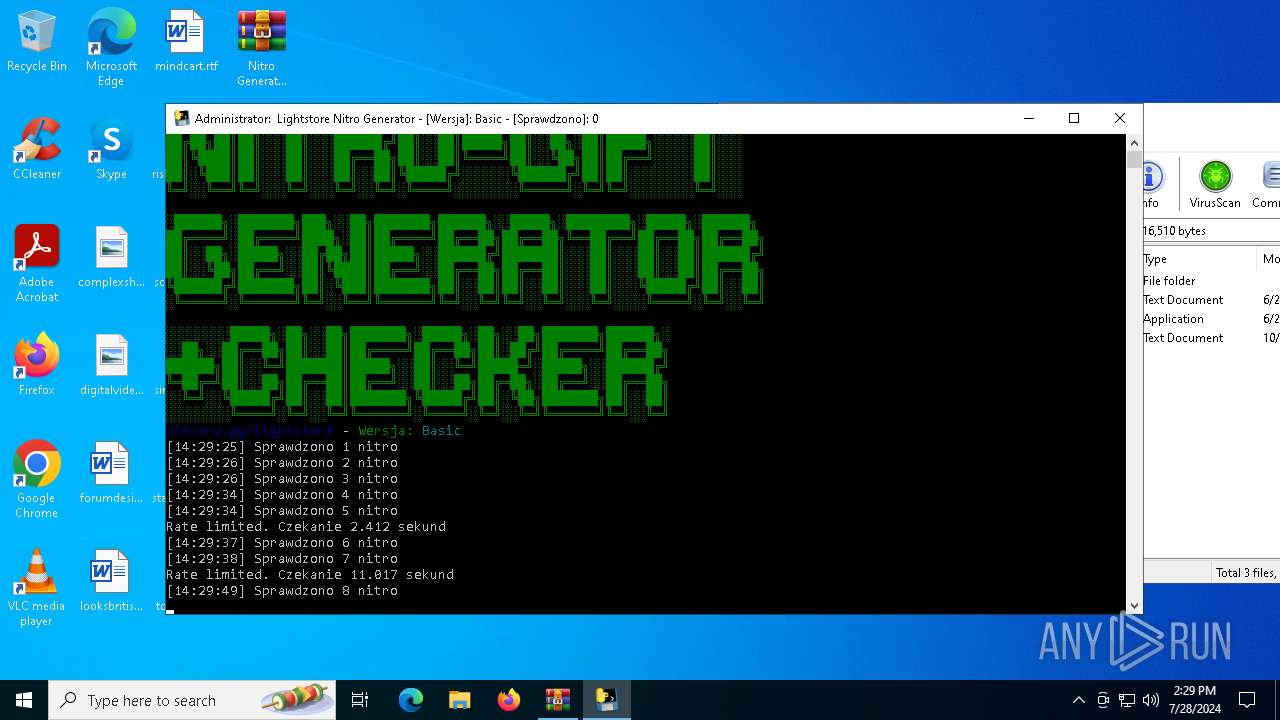
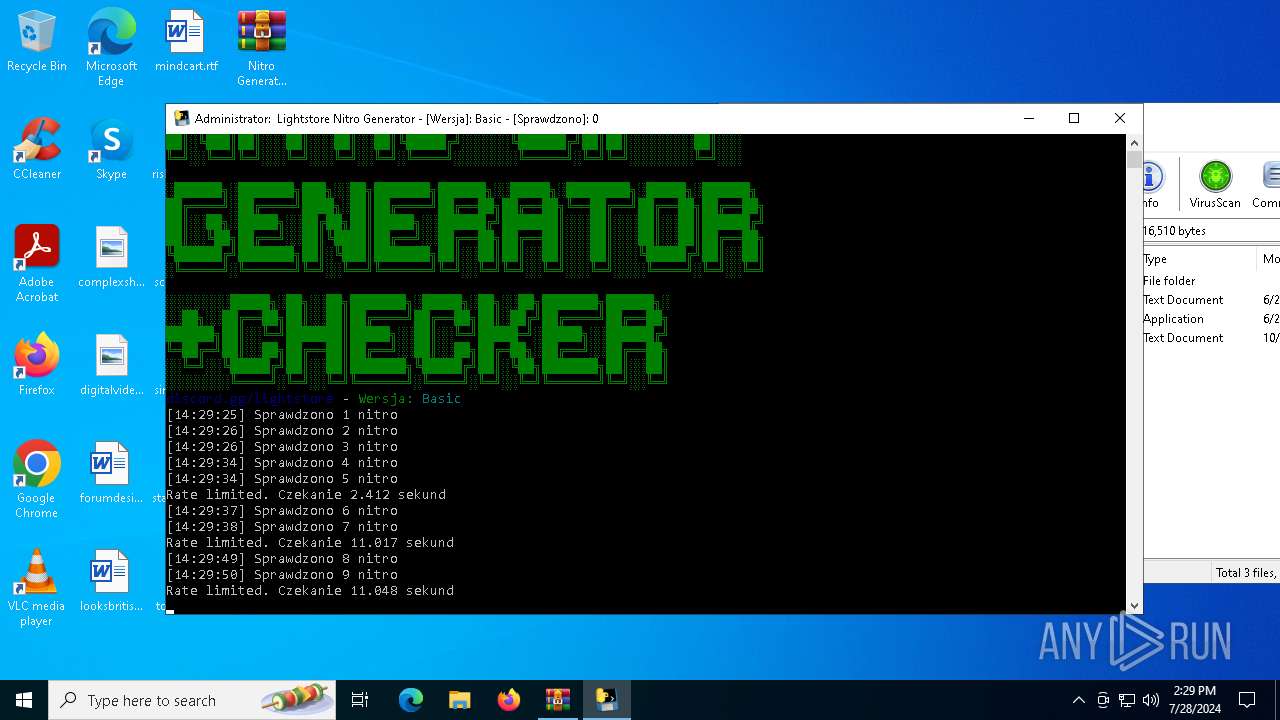
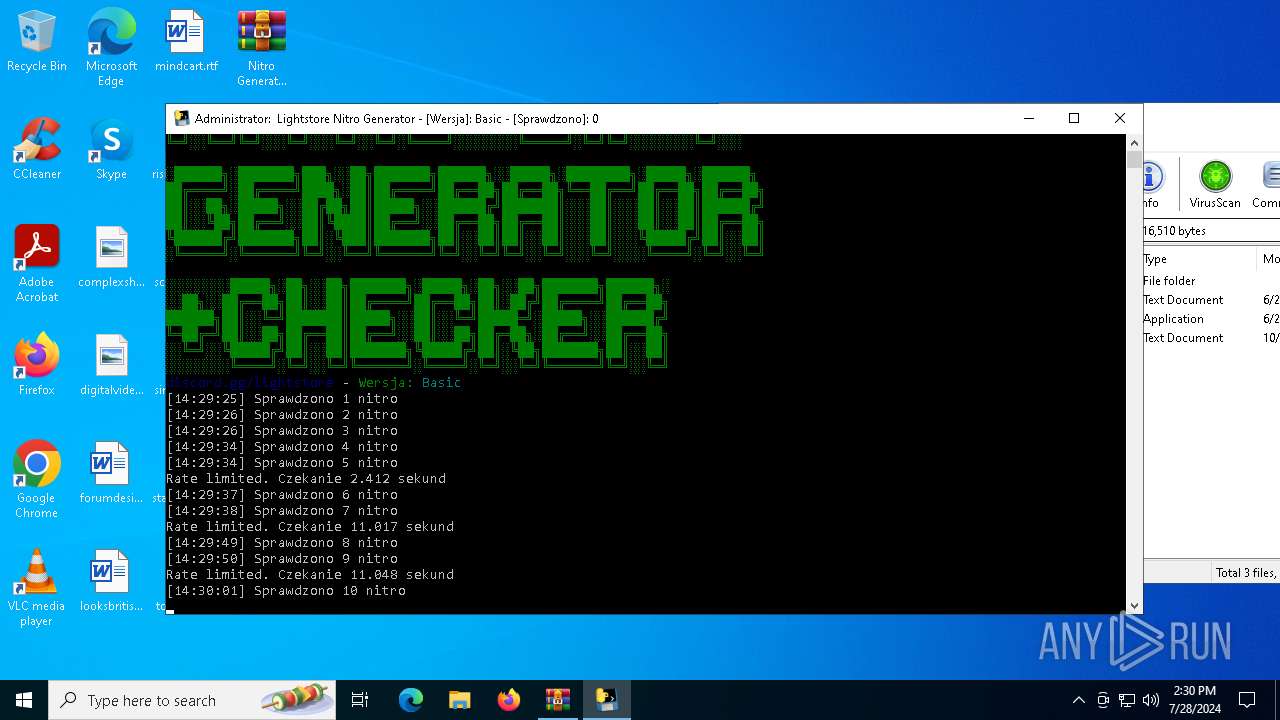
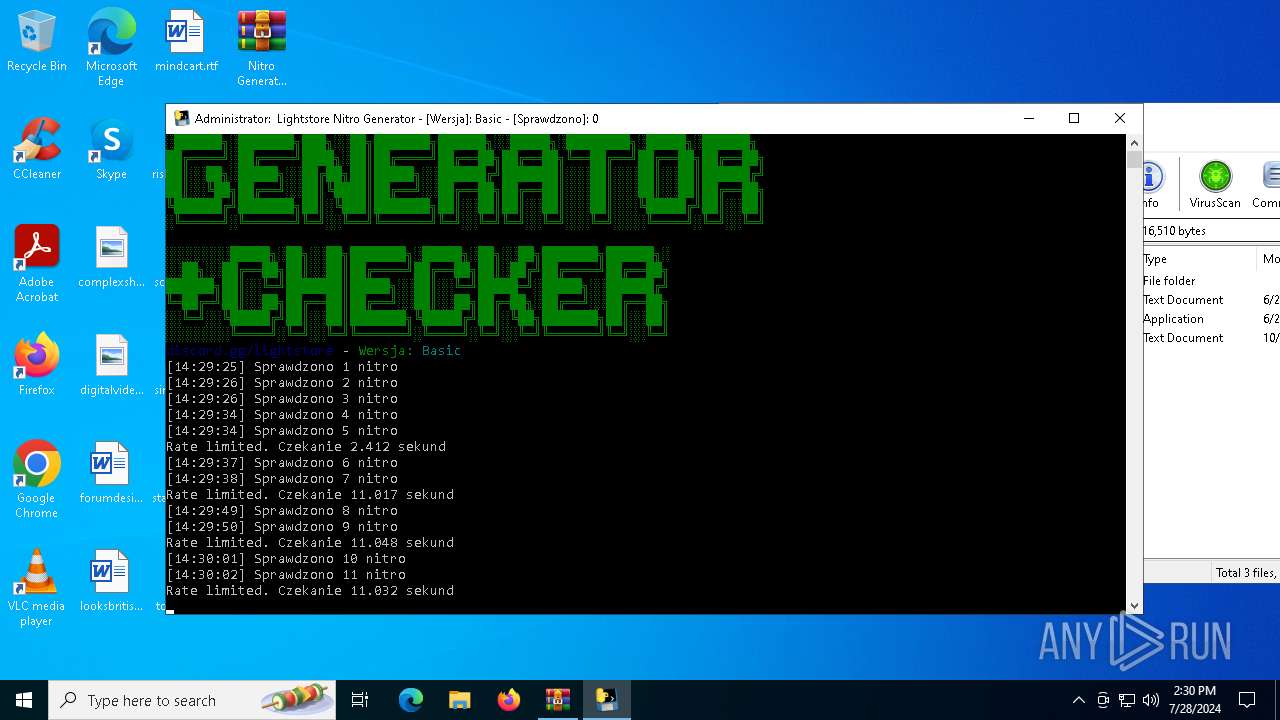
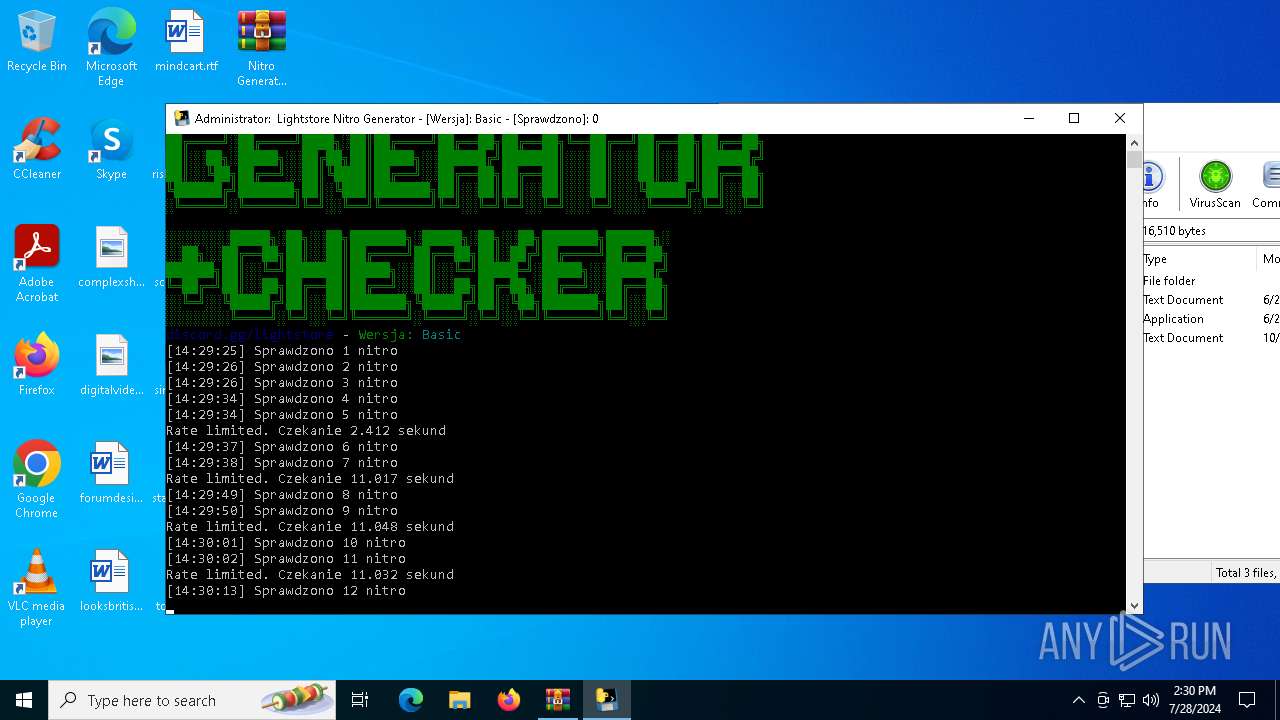
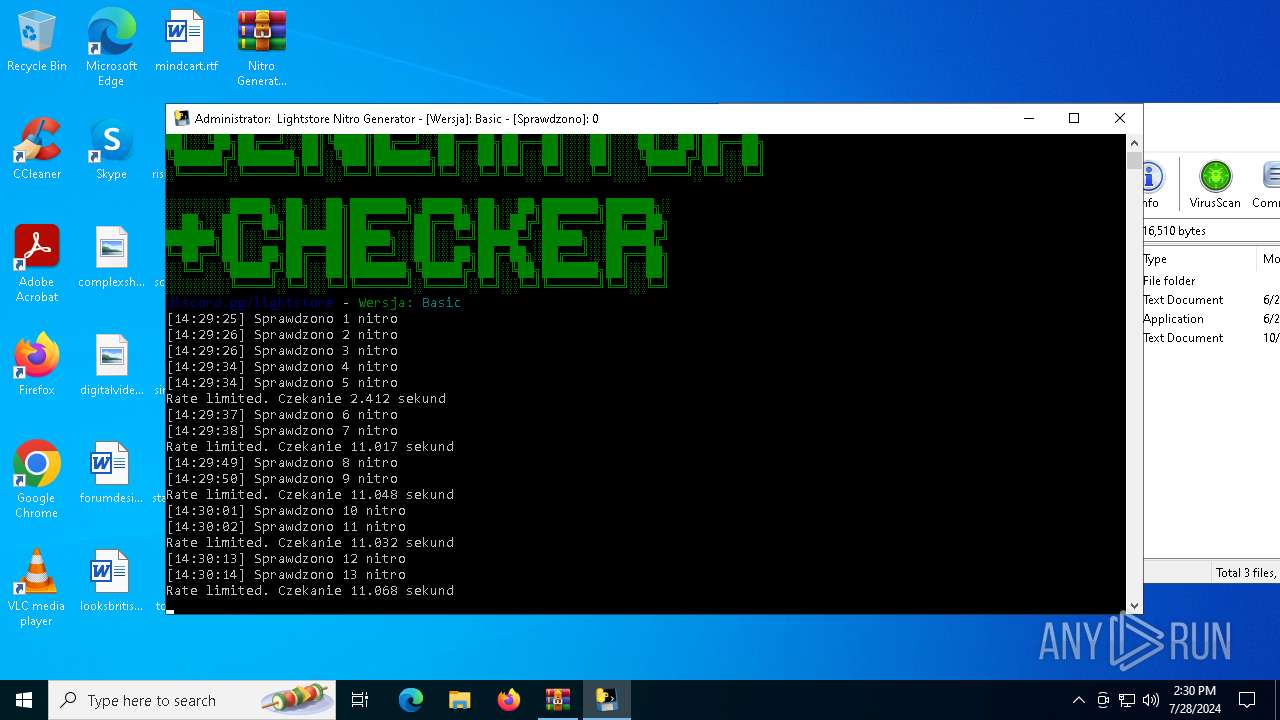
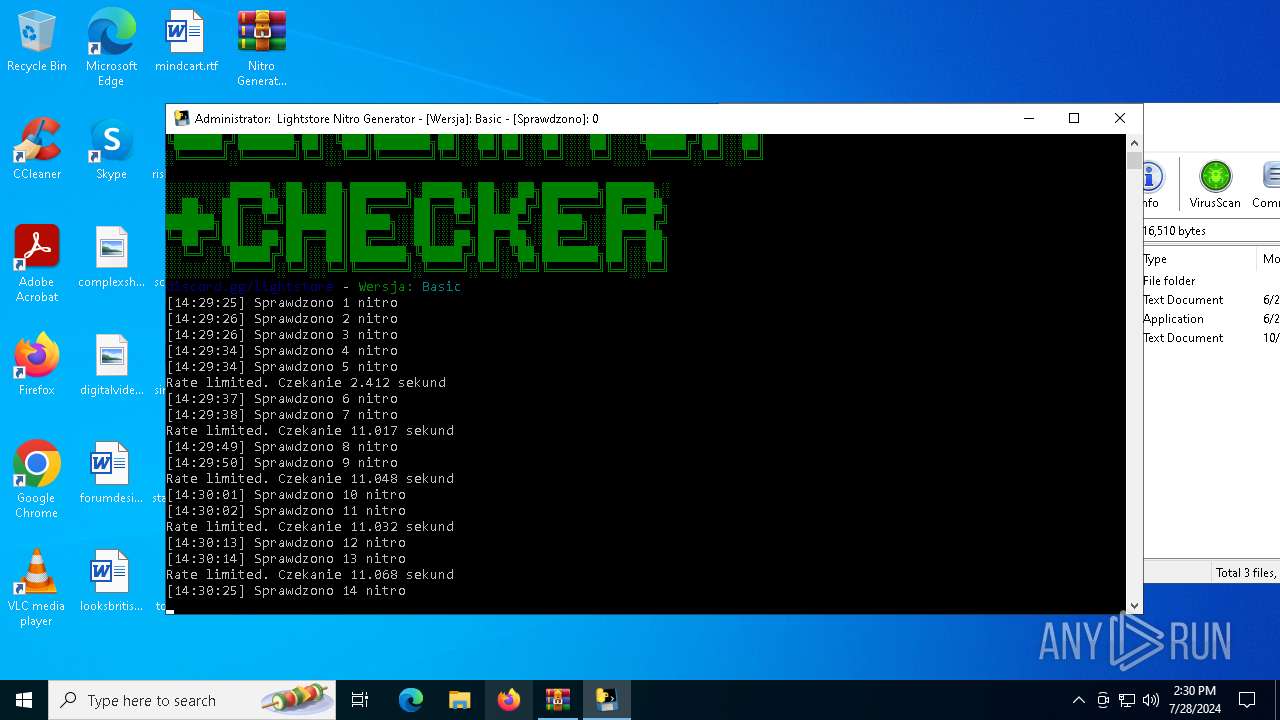
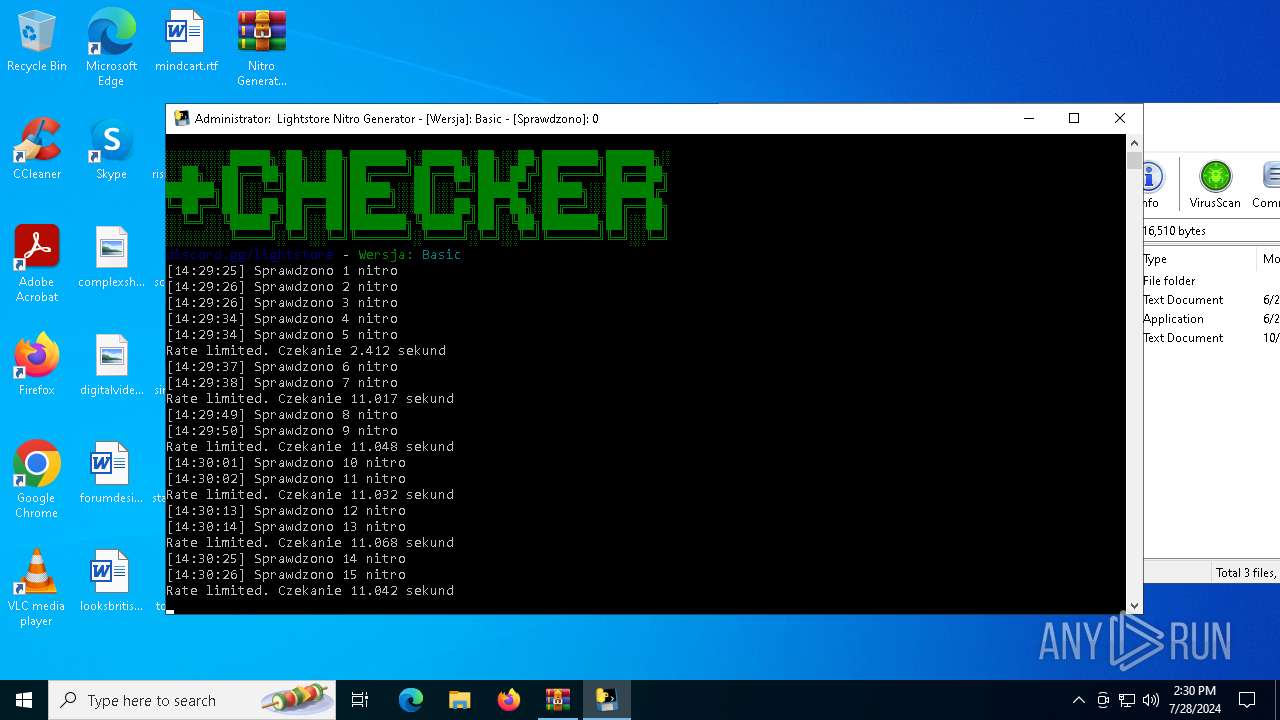
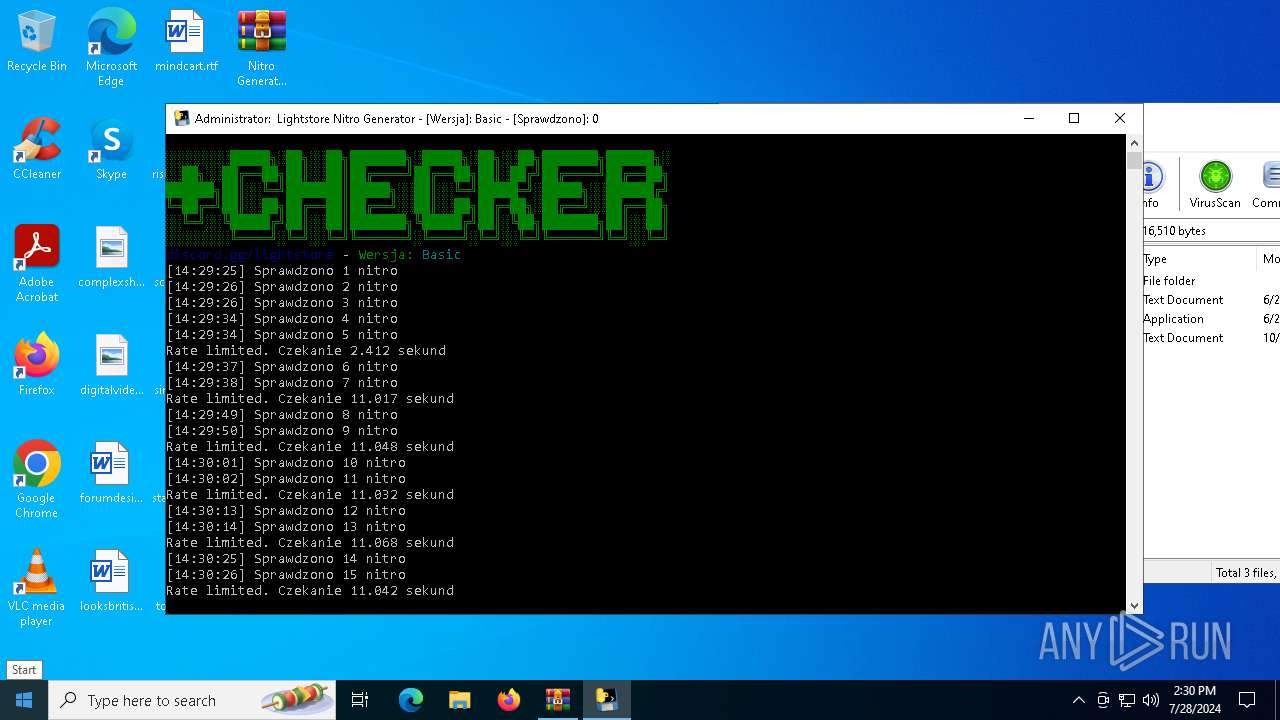
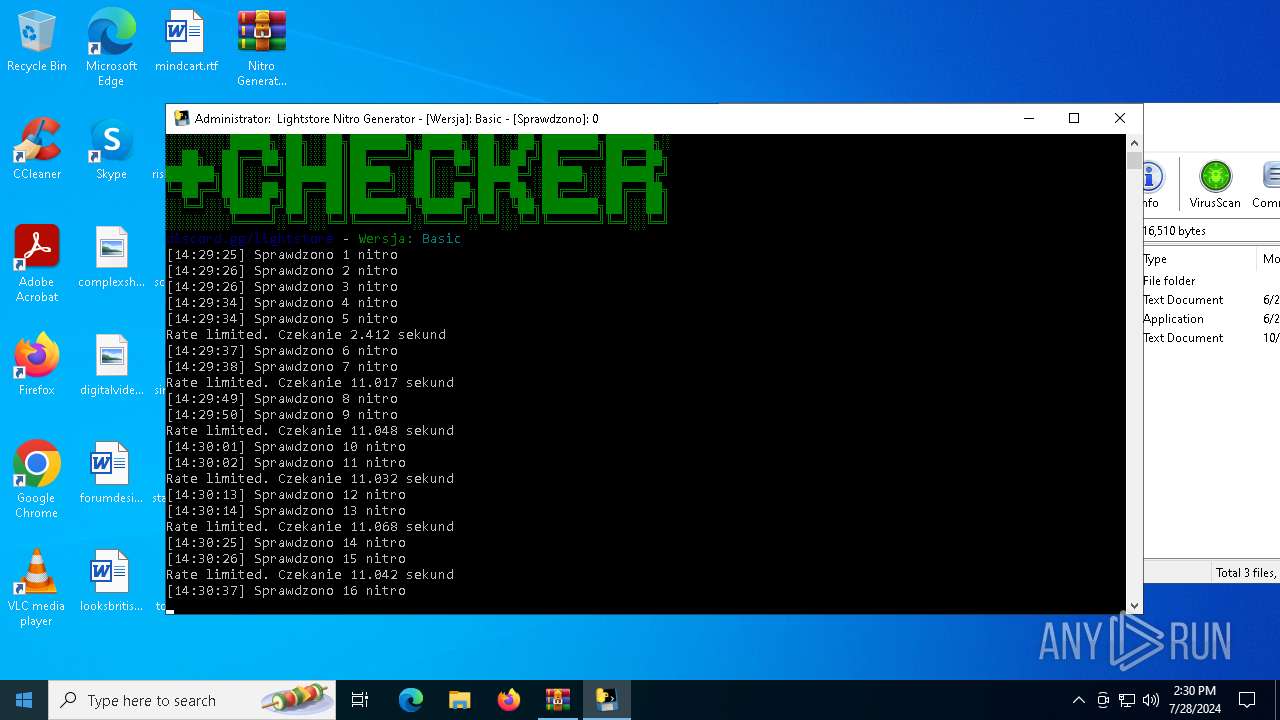
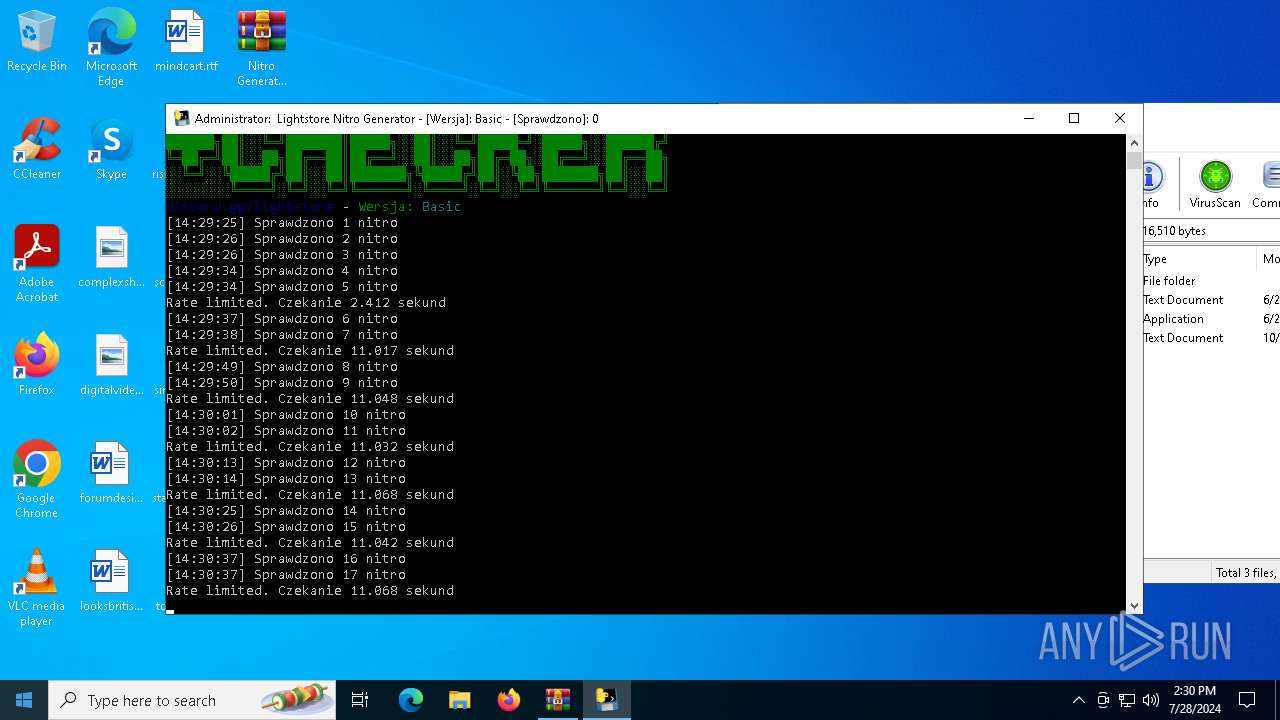
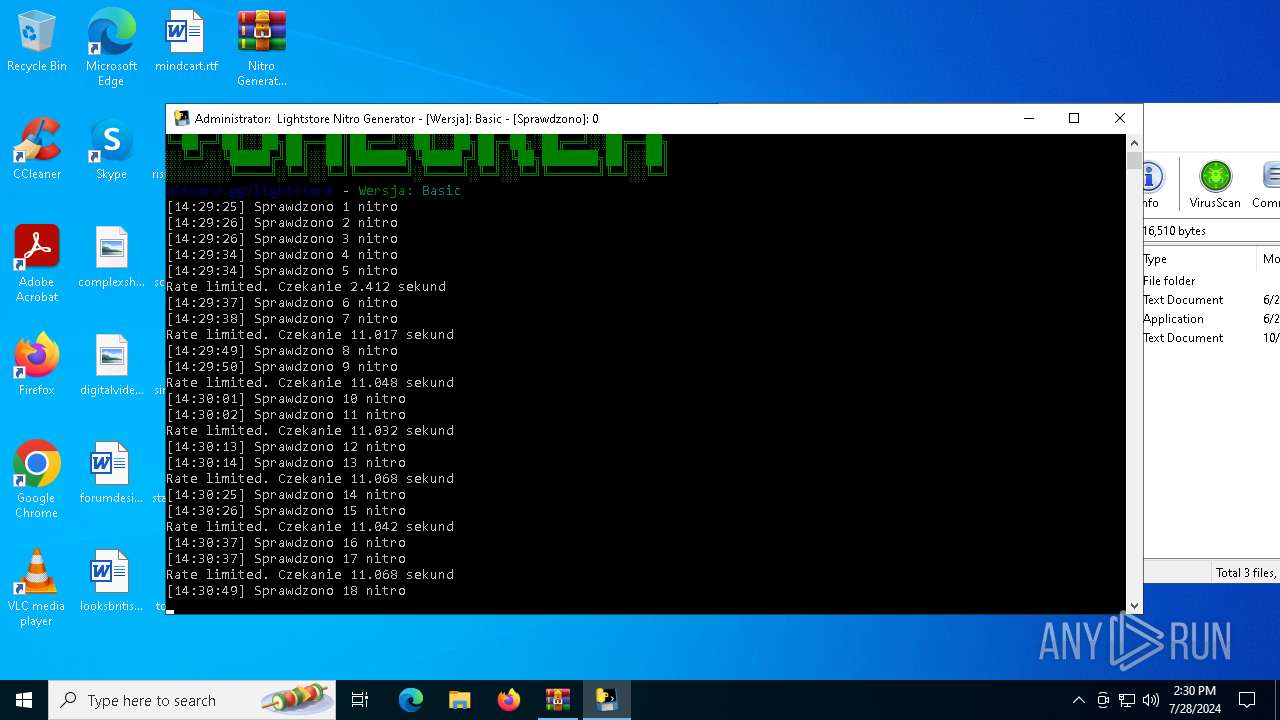
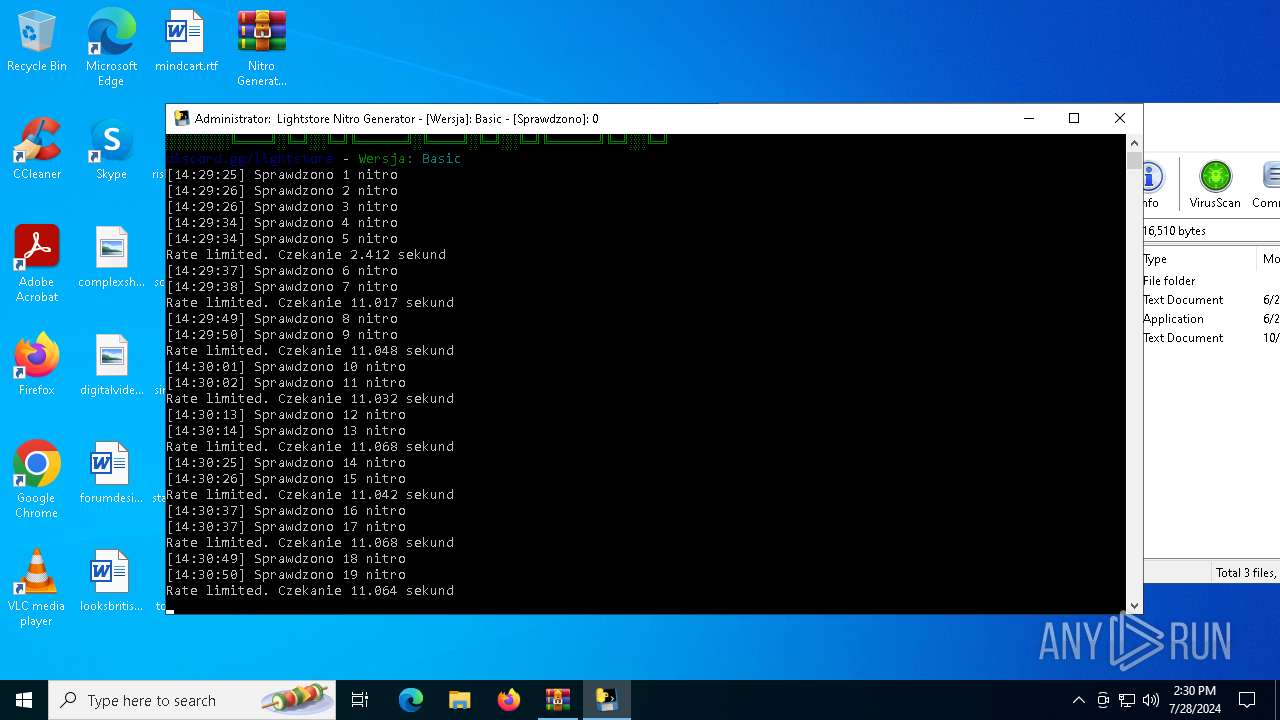
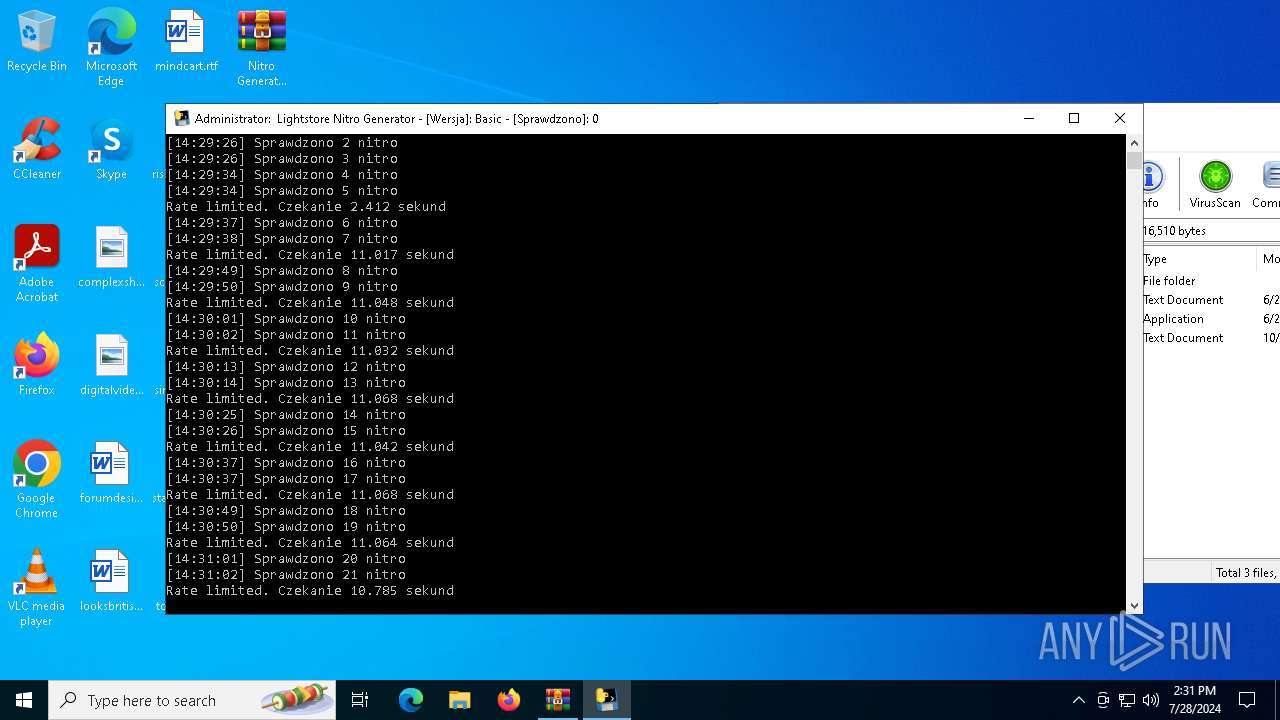
MALICIOUS
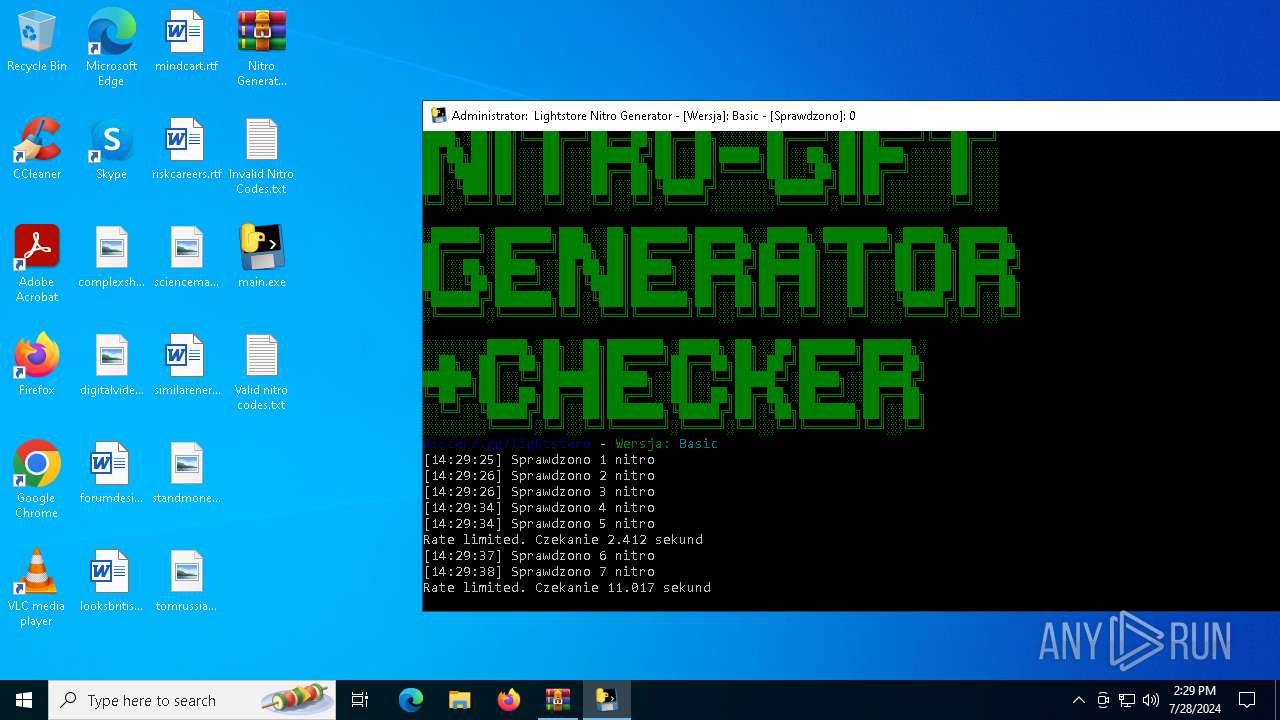
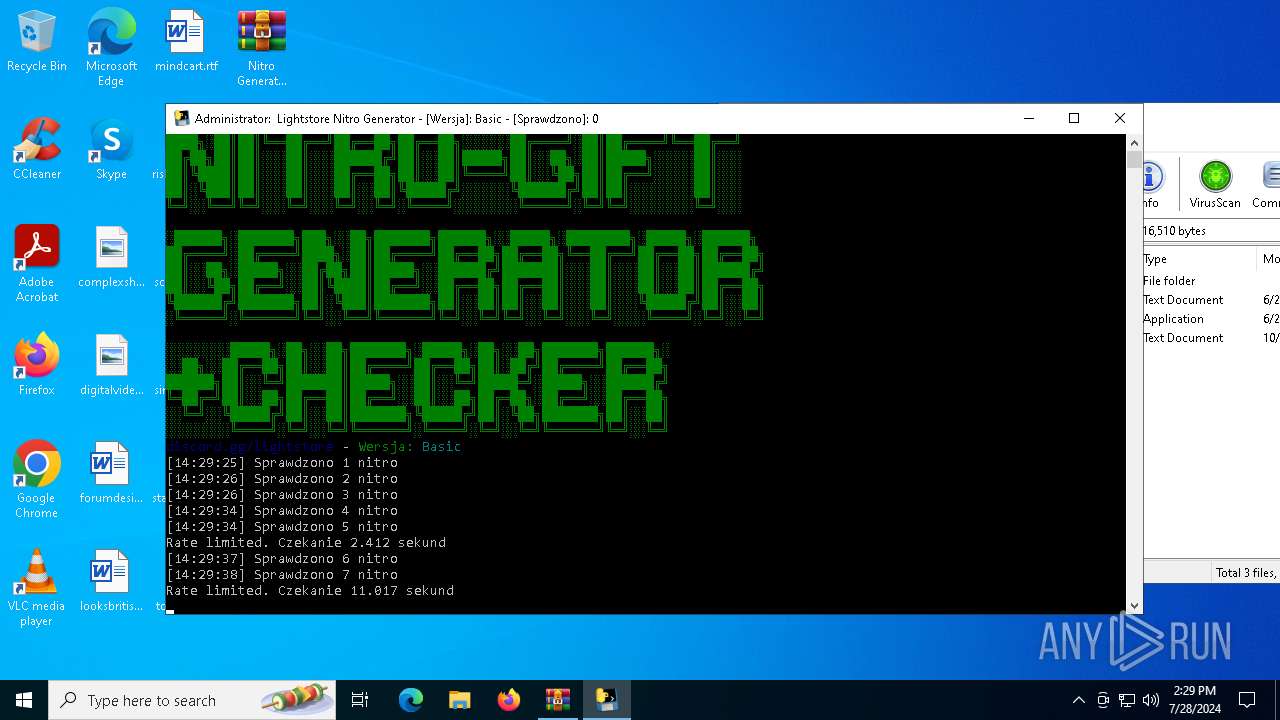
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4128)
- main.exe (PID: 2456)
SUSPICIOUS
The process drops C-runtime libraries
- main.exe (PID: 2456)
Executable content was dropped or overwritten
- main.exe (PID: 2456)
Process drops legitimate windows executable
- main.exe (PID: 2456)
Process drops python dynamic module
- main.exe (PID: 2456)
Application launched itself
- main.exe (PID: 2456)
Loads Python modules
- main.exe (PID: 1468)
Starts CMD.EXE for commands execution
- main.exe (PID: 1468)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4128)
Reads the computer name
- main.exe (PID: 2456)
- main.exe (PID: 1468)
Checks supported languages
- main.exe (PID: 2456)
- main.exe (PID: 1468)
Create files in a temporary directory
- main.exe (PID: 2456)
Manual execution by a user
- main.exe (PID: 2456)
- notepad++.exe (PID: 3588)
Checks proxy server information
- main.exe (PID: 1468)
- slui.exe (PID: 5080)
Attempting to use instant messaging service
- main.exe (PID: 1468)
Reads the software policy settings
- slui.exe (PID: 5080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:28 17:05:16 |
| ZipCRC: | 0xb3927ee5 |
| ZipCompressedSize: | 15096 |
| ZipUncompressedSize: | 39902 |
| ZipFileName: | Invalid Nitro Codes.txt |
Total processes
161
Monitored processes
17
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1468 | "C:\Users\admin\Desktop\main.exe" | C:\Users\admin\Desktop\main.exe | main.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1780 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2112 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | "C:\Users\admin\Desktop\main.exe" | C:\Users\admin\Desktop\main.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2692 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2736 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2952 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3588 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\main.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 3992 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 223
Read events
5 215
Write events
8
Delete events
0
Modification events
| (PID) Process: | (4128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Nitro Generator Version Basic.zip | |||
| (PID) Process: | (4128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
22
Suspicious files
1
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4128.26048\Invalid Nitro Codes.txt | text | |
MD5:1586C01E81D7E276BCE3D7F5BDA5AC50 | SHA256:6589B8D77FF2D0B312DE9DE4958F82133DE20676029E8B383434060D398B0CD8 | |||
| 2456 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24562\_bz2.pyd | executable | |
MD5:3859239CED9A45399B967EBCE5A6BA23 | SHA256:A4DD883257A7ACE84F96BCC6CD59E22D843D0DB080606DEFAE32923FC712C75A | |||
| 2456 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24562\_lzma.pyd | executable | |
MD5:E5ABC3A72996F8FDE0BCF709E6577D9D | SHA256:1796038480754A680F33A4E37C8B5673CC86C49281A287DC0C5CAE984D0CB4BB | |||
| 2456 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24562\_ctypes.pyd | executable | |
MD5:BD36F7D64660D120C6FB98C8F536D369 | SHA256:EE543453AC1A2B9B52E80DC66207D3767012CA24CE2B44206804767F37443902 | |||
| 2456 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24562\_cffi_backend.cp311-win_amd64.pyd | executable | |
MD5:210DEF84BB2C35115A2B2AC25E3FFD8F | SHA256:59767B0918859BEDDF28A7D66A50431411FFD940C32B3E8347E6D938B60FACDF | |||
| 2456 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24562\_socket.pyd | executable | |
MD5:1EEA9568D6FDEF29B9963783827F5867 | SHA256:74181072392A3727049EA3681FE9E59516373809CED53E08F6DA7C496B76E117 | |||
| 2456 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24562\_hashlib.pyd | executable | |
MD5:4255C44DC64F11F32C961BF275AAB3A2 | SHA256:E557873D5AD59FD6BD29D0F801AD0651DBB8D9AC21545DEFE508089E92A15E29 | |||
| 2456 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24562\_queue.pyd | executable | |
MD5:F00133F7758627A15F2D98C034CF1657 | SHA256:35609869EDC57D806925EC52CCA9BC5A035E30D5F40549647D4DA6D7983F8659 | |||
| 2456 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24562\_ssl.pyd | executable | |
MD5:208B0108172E59542260934A2E7CFA85 | SHA256:5160500474EC95D4F3AF7E467CC70CB37BEC1D12545F0299AAB6D69CEA106C69 | |||
| 2456 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24562\cryptography-42.0.5.dist-info\LICENSE.APACHE | text | |
MD5:4E168CCE331E5C827D4C2B68A6200E1B | SHA256:AAC73B3148F6D1D7111DBCA32099F68D26C644C6813AE1E4F05F6579AA2663FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
58
DNS requests
29
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3720 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 95.100.146.27:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
6572 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
484 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1292 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
720 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
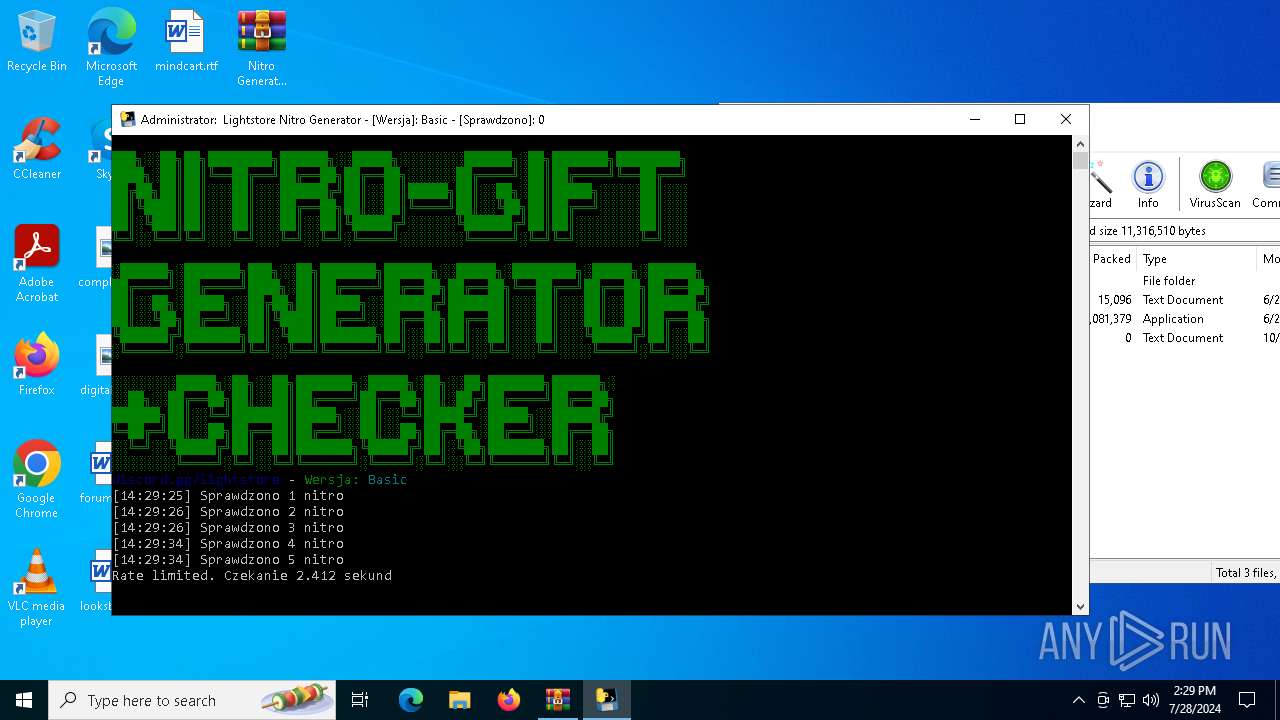
1468 | main.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2284 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|